Category Archives: Abuse of Power
EMF Meters for TI Use
Radio Frequencies and Electromatic Fields can be weaponized for use against ANYONE. With the advent of 5G and the Internet of (smart) Things, almost EVERYONE should worry about RF/EMF effects. THIS MEANS YOU!
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
Dateline, Oct 30, 2020, from an undisclosed location not too far from wrong. copyright © 2020, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.
Hard rocks and harder places…
This is an extremely broad topic which cannot be well discussed here, beyond some basic advice. The problem for TIs is uniquely different from common uses of Technical Security Countermeasures (TSCM) equipment and services. So one problem right off the bat is obtaining useful help (good luck with that). This leads to a do-it-yourself (DIY) alternative by use of low-cost EMF meters, and possibly shielding or other tactical solutions. As result, most pros are ex mil-intel types, which creates a trust barrier with most of the TI community.

Not that it matters: a TI simply cannot afford the cost of their services. Professional TSCM equipment is extremely expensive (a pro might have a million dollars invested) and extremely complex, and requires a lot of experience and the kind of training offered in the military and intelligence communities. So, between trust and cost, and unique needs, a TIs find themselves between a proverbial rock, and hard place, a DIY nightmare. That’s not all.
That help issue trickles down the food chain to the makers and sellers of lower cost solutions, such as EMF meters, which are little brothers to more sophisticated and costly signal analyzers used by pros. Such firms do not and will not support DIY use of their products for TI related needs, and indeed, many pros will not offer their services, either because they fear running afoul with some government operation — or they don’t believe in the whole targeting notion and presume the client mentally ill.
It is possible to hire a PI or some individual who’s gone into business using low cost gear to do ‘mini’ TSCM sweeps, some of whom are aware of and will cater to TI needs, but many of these are charlatans, especially true in those who specialize in select TI issues, such as ‘finding implants.’ Be wary of anyone charging for implant detection using small EMF meters, esp. if charging by the implant found: with many meters, it is possible to cause a false read by simply moving a finger of the hand holding the device toward the front of the meter… for another $50 ‘find.’ “Would you like me to continue searching?”
It would therefore be better for the TI to do their own searches, though even with a decent EMF meter, the odds of finding an implant are extremely nil. EMF meters detect Radio Frequency (RF) and Electro-Magnetic Fields (EMF), which are radiated energy/field readings not given off by implants, as a rule. Most implants receive such signals, and those that transmit them tend to do so by remote command. Even then, it is very briefly, rather than being ‘on’ all the time — defying meter detection.
While there may be exceptions, the type of signal they use is likely to be lost amid the ambient signals present already (i.e., wifi, broadcast radio/TV, cellular, AC wiring, power
lines, amplifiers, etc.). An EMF meter displays the sum total of all such data, and can only identify a source by virtue of increasing in signal strength as it nears the signal source. An implant signal is rather weak. But, implants aside, there are other valuable uses for such a meter, if you have a decent one.
Choosing an EMF meter
First, know that cell phone apps that offer EMF readings are not reading the right kind of EMF. They are not reading any signal which is involved with targeting, but instead, the Earth’s own magnetic field, using sensors in the phone designed for game play to know changes in the phones relative position to prior positions (i.e., steering a car in a driving/racing game). For like cause, avoid ‘Natural’ EMF meters or EMF meters that do not include RF measurement, as they are also reading the Earth, only.
So what you really want is an actual RF/EMF meter. And not just any such meter, but one which is directional in nature when reading RF, and not omnidirectional. AC Magnetic Field readings will be omnidirectional, in virtually any meter, but if the RF sensing is directional, that will not impede usefulness of omnidirectional EMF readings. RF, on the other hand, is barely useful if only omnidirectional. That said, some omnidirectional meters will allow you to install and optional directional antenna… for added cost. One way or another, you want directional.

The type of antenna system described by the maker in specifications or manuals won’t necessarily tell you if it is omnidirectional or directional, they prefer a technical description of the physical antenna design (engineer speak). Omnidirectional (least useful for a TI) are typically described as ISOTROPIC or TRIAXIAL (3–AXIS), and are often visually discernible by a large ball or spherical object at their top. Sometimes it is internal and, therefore, smaller and unseen. That limits the sensitivity, compared to an external. Directional RF meters might have no antenna, a rod antenna (like old brick cell phones), a ‘wand’ at the end of a cable, or a triangular antenna (very useful with distant sources). So, any other technical description other than Isotropic or Triaxial, is good.
My base-line low-cost meter of choice is the TriField TF-2, which I actually used to sell with some value-added features for TI use. That included a user manuals I wrote for such use for the Trifield, and the Micro Alert audible meter (a good companion product). These manuals, along with a copy of this post and many others, are part of my TI Helps Kit available on request to proparanoidgroup at gmail com. I used to charge $10 for the manuals, but the Kit is free, though I do encourage a donation to the Free Will Society to aid severely impacted stalking victims (freewillsociety.wordpress.com) via PayPal to the above email addy.
I compare all other meters to the TriField before considering them desirable, or worth the price for TI needs. It is a directional RF with omnidirectional EMF readings in a simple to use and reliable product at a low cost. You can buy direct (trifleld.com) or find it online from many resellers. Experts in the meter reseller and RF/EMF consulting field also use it as a standard for comparisons, and that is telling. In fact, currently, one such pro who advocates for the TriField is EMF Academy, a valuable resource for information to anyone interested in issues revolving around the topic.
More importantly, they have a newsletter you can subscribe to, and associated with that, is a monthly drawing for one of three TriField meters. If you just visit their site and poke around looking at articles on things like EMF paint and shielded clothing, a popup will offer you the ability to subscribe and enter to win one of the meters. Some of their more expensive and exotic solutions I am currently testing, and will likely write an update report within a month: be sure to FOLLOW my blog so you get a notice. While you do that, also click the LIKE button and leave a comment, if you wish — all at that bottom of each blog post.
There are other features to look for in a meter which could be handy to a TI. An audible tone option, for working in the dark or allowing you to focus on what you are scanning (TF-2). Peak reading indicator and Avg signal strength (TF-2) instead of just a needle or light bar reading that is bouncing around enough to make such things difficult. It would be nice to have the ability to add a special antenna, such as (specifically) a dipole. This may be a round tube, or a flat, triangular antenna for very precise targeted distance source location (useful for DEW sources, typically hundreds to thousands of feet, or even miles away). Some offer a pistol grip or a protective case. These things are nice to have, but not usually critical, if you are willing to walk a bit more to effect the same results.
But the important feature is antenna, and frequency range. Most meters are intended only for cellular and wi-fi operating ranges, which stop (well before 5G) at below 3.5 GHz. One insidious risk of 5G compared to 4G and the current wifi standards, is that it operates at such a high frequency, citizens won’t be able to afford meters designed to check for safety. They may operate at up to 6 GHz. As it happens, DEW weapons are likely operating in similar ‘beyond hope’ ranges. My $12K meter setup can still only see to 12GHz, and some DEW will be above 50 or 60 GHz.
And, it is true that EEG entrainment (mood, sleep control, thought interference), which many TIs call remote neural monitoring (a misnomer), operates at frequencies well below any low-cost meter on the market, unless you are looking at something like my $12K rig… which is exactly why I have it. We are talking human brain operating frequencies, at and below 30Hz. Your ears cannot hear below 30Hz, because if they could, it would confuse your brain, and therefore, that’s also why audio equipment tends to stop at that low end, as well.
Proper use…
Hold the meter level, flat in your hand, so you are looking down to see the reading. If you aim it upward, you are going to flood the meter with radio waves reflecting off the ionosphere, and will always get incorrectly high readings. You wouldn’t even be able to sense a satellite signal, that way; such meters are not designed for anything but environment readings or very near or high-outpt sources. Also, many meters without external antenna will give similar false readings if your hand is touching the ‘head’ or ‘business end’ of the meter, so hold it by the rear half, only. When taking a reading, your purpose may vary, but generally, you are looking for a ‘hot’ or higher-than-average reading among the ambient collective.
Before actually taking readings, consider perp strategies. They likely have excellent surveillance and will know when you are using a meter. It is very likely that they would therefore simply shut down, making any sweeps pointless. This is why a pro TSCM sweep is typically conducted unannounced, anonymously, and with a degree of stealth and cunning. Ideally, it would be best if you arranged for a companion to do the sweeps with as little fanfare or obvious effort, as possible.
This brings in additional problematic factors, such as trust and willingness to help in what is a lengthy and complex set of tedious steps. Or, you might get lucky and find the enemy’s gear is simply left running while they take a nap. For most TI’s, though, it can mean many attempts before being able to acquire useful information from the meter. Failure to find clues of targeting does not mean they never target, does not mean the meter is defective, does not mean you are doing something wrong… it just means that was not likely the right opportunity.
And yet, of course, the other possibilities may yet be true, in the end. While a negative is not necessarily proof of a negative, a positive is its own proof. Even so… you will want multiple positives over time if to have useful evidence. That will also require good documentation, such as video and verbal announcements of what you are doing and seeing, and where the meter is pointing. Have a witness, too. More to follow.
Taking readings…
Slowly sweep back and forth, left to right, looking for possible reading jumps or dangerously high readings (hot spots). When you first start, you won’t likely know what is dangerous, or not. There are good online resources to help with that, but they can sometimes seem way too technical, and measurement increments of your meter may not match the measurement increments of a given site. That can result in confusion or misinterpretation, and force some math you might wish to avoid. Here are several sites you can review and compare against your meter, hopefully finding one more directly useful, without involving conversion factors. There are many others out there, and what constitutes unsafe levels is kind of a moving target in constant redefinition, and there is a difference in European, American, and Asian standards, the U.S. being the most lax (natch) of the three.
https://www.home-biology.com/electromagnetic-field-radiation-meters/safe-exposure-limits
https://healthybuildingscience.com/2013/02/18/emf-and-emr-conversion-formulas/
If you find a hot spot, stop and watch for several seconds to see if it holds relatively steady or was just a random spike. Generally, you will want to repeat scans in each of the meter’s modes of operation (i.e., the TriField has three: AC Magnetic, AC Electric, and RF/Microwave). If you are logging results for legal or comparative purposes, give it at least five seconds and note the reading(s), avg, and peak. If you’ve made an entry, be sure to note the values for each meter setting at that same position/angle. That added information could prove useful at some point.
Hot spots may show up either as a gradual rise and fall as you sweep, or a sudden spike. It may be brief, or hold steady. Brief spikes are not typically useful, but one which holds or is above safe limits is very useful. Note if gradual or sudden, and especially note if it was synchronous with any impact on you or your environment. You will also want to get a compass heading (there are cell phone apps for that, relying on natural EMF, as it happens).
If outside, and you are in something like a depression or valley, or a where there are tall buildings, you may wish to then tip the meter a bit to scan lower and higher in angle, such that you avoid looking directly into the sky (stay below the visual horizon, where rooftops may so redefine it), looking for further increases which may help identify a specific source location of the signal (a cell phone ‘bubble level’ app with off-level degree readouts might help with your notes, as well). If it is a building you are aiming at, try to estimate the floor, and note that. You may want a strong pair of binoculars, a rifle scope, or other strong lens to try to see what is at the suspect location. And it is suspect, only. A hot spot, even if very hot, is not alone a proof of a targeting source… but only reveals a possible suspect location.
If we are talking about finding a surveillance or other targeting device planted somewhere within your location with the meter, there is a similar concern, should you find something. Depending on the device purpose (which you may not be able to discern), and tactical matters dictated by your targeting situation (which may not be obvious), it may be to your advantage to leave it in place. You may wish to contact me (I am interested) via public library computer.
Or, use your best judgment, if worried it might should be removed immediately. Video document its removal and take it directly to a bank and get a safety deposit box to put it in… or take it to a local professional for analysis, per the advice in the next paragraph. Send me still images, in place, and after removal, if removed. Safety first, if it involves AC electrical power, and if it is in a large sealed box, don’t try to open it… such are often booby-trapped to destroy the evidence; very scary fireworks which may require the Fire Department, as it once did in a case I was investigating.
Now, about suspects, we need a warning: If you do establish a suspect, DO NOT confront individuals which you might be able to identify. Instead, try to learn as much about them or the property as possible, and add it to your notes. You should then contact me, or an appropriate professional, such as a private investigator, lawyer, or Agency. I don’t recommend Police, but if you have good readings and symptoms verified by a Doctor as not due a health issue, you might want to contact the FCC or your State’s Environmental Protection Agency, or perhaps your local County Extension Office Agent. Some larger cities may have bio-home or bio-environmental engineers or similar, who could be very good resources, if available. If there is any significant find or action taking, I would like to hear from you, and may be able to suggest ‘next step(s)’ to consider.
Specific uses
To find a surveillance or targeting device in a structure (the TI’s ‘space’) requires comparing readings well away from a suspect source to readings within an inch of it, looking for a large increase (signal strength falls off at the square of the distance). Scan low, scan high, and all around. You will want to be as physically close to surfaces as you can get, without touching, preferably (no harm, no foul, if you do). Every object and surface should be treated as a potential suspect to be tested.
One should establish ‘normal’ levels in a non TI environment (a test control space) similar to the TI’s space, and compare by taking readings at room center or well away from major RF sources (i.e., wifi, computers, tvs, radios, ovens, etc.). It should be a similar sized and designed space in the same neighborhood, between three and six homes away (arranging this can be daunting, if you do not know anyone who fits the bill, who would be willing to participate — try requests based on your own concerns in the neighborhood about high 5G signals, until you find someone who worries about 5G).
This is done in several sets of readings, each — one with those RF sources operating, and one with them turned off, and one with the Mains turned off (no AC power to the space). If subject to significant electronic attacks which can be physically felt or sensed, the TI’s space reading should additionally be undertaken as sets during both times of no sensed attack, and during an attack (which may prove difficult, if under surveillance — the perps may elect to cease the attack once you set up for the readings… which might buy you some peace.) You should also take readings at the power company meter at both spaces at a time of day when major appliances are not in use, and note how fast the meter is changing, and in the TI space, take an additional reading when the mains are turned off.
Finally, you will want to walk around the space on the outside taking reading pointing away from the center of the space, looking for hot spots. Directional is King, here.
To test for bio implants in a person or a tracking device on a vehicle, the best place will be in the country, away from any nearby potential sources for such signals… such that ambient broadcasts and distant cell towers are about all that’s being read. All cell phones and the like should be turned off. Don’t try to find an implant on yourself, have someone else take the readings. Every inch of the body should be scanned, and I suggest wearing a simple nightgown, PJs, or a bathing suit. Feet wide apart, arms held out to the sides. Be willing to get fairly personal. One then verifies by going on past the body in the same direction to insure the reading is dropping, again.
If a vehicle, pop the hood and trunk and doors to scan the interior areas, it being OK to lean into and ‘look about’ with the meter, just trying not to aim directly at the sky. Don’t forget under the seats, fender wells over the tires. It would be nice if you could put the vehicle on jack stands so you could safely get underneath it (where aiming upwards at the undercarriage will be fine). Jacking each corner up as if changing a tire is much more work… but avoid actually going under the car with any more than your arm. You will want three sets of tests, one with the engine running (in Park or Neutral, Emergency Brake set), one with battery connected and the key in the accessory setting, and one with the battery disconnected. That will tell you if any suspect readings are from something drawing power off of the car, or if it is battery operated (which means something bigger, and easier to find in a visual search). So, be sure you have the needed tools.
What do results tell you?
- Where readings are higher during an attack, DEW is all but confirmed, and additional steps (T1, at document end) will be needed. Where they are not, and the attack was sensed, the sensed effects are more likely to be a health issue (all TI symptoms are carefully designed to mimic health issues), and you should seek medical advice, describing only the symptoms, not TI concerns. Get a second opinion using a random Doctor. If no high readings and no sensed attack, try again… and again;
- where readings are higher in the TI space with all power off, than in the control space in like status, it indicates battery operated surveillance is likely, take steps (T2). If the same, it implies that any perp equipment present is drawing power from the house by any number of means, use step (T3). NOTE: it is certainly possible for both to be true;
- where readings are higher when RF/EMF equipment is turned on in the TI space compared to the control space, it implies that the equipment operating is either defective, or perhaps weaponized against you in some manner, take steps (T4); If the same, it implies them safe;
- where readings are higher when the equipment is turned off than in the control space, and the first part of item (2, above) is false, it implies the AC power system has been weaponized, take step (T5);
- where power meter readings are higher in the TI space than the control space, it implies the Meter is relaying a lot of data from perp devices… just good to know, as the other tests will address needed steps. If not different, it implies the meter is not a Smart Meter, or the meter has not been weaponized to relay data. Relay of perp data does not imply the power company is the recipient or participant, though it is always possible;
- where power meter continues to draw power with the mains turned off in the TI space, it means there is the possibility the perps are drawing power off for their devices directly from within the mains junction box (circuit breaker box), and may include electrification of the ground to create high EMF readings in the home, and likely, the embedding of targeting signals within the AC wiring. Take step (T5).
T1 (DEW test). You have had positive space readings within the structure and they point to DEW presence. You now need to do external readings at both spaces by walking around the building site and taking reading pointing directly away from the center of the building or room of concern (don’t sweep left to right — you walking in a hypothetical arc about the center point, instead).
Compare these to the interior readings at the same compass heading. If there is no agreement, the source is likely inside the structure: do a 180 and sweep to confirm, directly along the outer wall surfacwes. If they do agree, compare the average signal strength. If it is a notably higher, then the source is relatively close, and in theory, if there was nothing in the way, and the source was left operating, you could walk toward it until you found it… such as a neighbor’s home. If it is not exactly higher, then it is much further away, and you may want a bicycle or car to chase it down.
T2 (Batteries). Battery operated devices are bigger, and easier to find because they will require a nook or cranny. Do a visual search for anything that is unusual or foreign. Do not remove it. Video the discovery with audio description. It may require some disassembly of door panels, carpeting, dash components, etc., which may mean professional help or tools, in which case, you must be present and video. Contact me with the circumstance and send me still images of the object, that I may suggest the next steps. Do this covertly, such as by use of a public library computer.
T3 (No Battery). That means it is either hidden within an appliance (i.e., TV, stereo, blender) that is always plugged in, or it is wired somehow directly off of an AC power line, perhaps in wall or atic, under floorboards or behind baseboards. If the meter is pointing towards any such appliances. Unplug those items and move them aside, and take readings, again. If the readings fail to match, plug them back in elsewhere, and read again at the new position. If they again match, they need to be dismantled, looking for anything that seems added. You may want to take it to a repair shop, if unhappy at the thought of DIY (some items have voltage capacitors which can cause severe electrical shock even if the item is unplugged). You have to worry about such items on the far side of the wall, as well, by the way.
If the appliances don’t change the readings when removed, or there were no appliances, then we worry about wiring in the walls, floorboard, and ceiling areas. Aim the meter at angles to see if there is any confirming change in readings. If low angles are hotter, you may need to pull the baseboards, wall power outlets, or get under the floor (i.e., basement ceiling area). If high, there may be ceiling molding to be removed, or you may need to worry about something upstairs or in the attic ((where you will be wanting to follow all the house wires, looking for a cut and splice with something dangling (perhaps another long wire to chase down) off of it)). Otherwise, we check light switch wall plates, picture frames, wall hangings, or window sashes, etc., as may be in the line of sight of the reading. Again, be mindful that walls have two sides. Watch out for fiberglass or asbestos insulation… you don’t want to be messing with that without serious protective clothing.
T5 (AC Power Compromised). Consider to contact a Home Bioengineer or a large Electrical Contractor who is capable of doing large-scale power system work (i.e., can contract to build sub stations and the like — which means they know more and have better tools than ‘an electrician’). Go directly to the Power Company if there is no such services in your area. The idea is to complain about dirty power and possibly high ground voltage (say nothing about targeting) and ask for a power quality survey. If they find anything wrong, they should be able to fix it or arrange for the power company to fix it. Simply going to the power company first may not be a great idea, if they have been compromised and are complicit.
Shielding Solutions
See the document on Shielding which is also included with the Helps Kit, or request a copy.
Netflix, Microsoft, Google, Playstation: Poised for Mind Control Psyops?
When you marry entertainment with AI guided user interaction via Web connectivity, with its inherent user tracking abilities, you have the formula for psychological profiling and manipulation, including mind control. Netflix pioneered such a tool in movies with some scary evidence of just such use, and now, Google, Microsoft, and Playstation want to play, too (literally).
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
Dateline, Aug, 29, 2019, from the Left Coast of America, not far from Microsoft
copyright © 2019, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.Bird Box
That’s the title of just one of Netflix’ most recent in-house produced movie offerings. Unlike anything ever attempted in the past in the art of making films, Netflix added one unique technical aspect of how movies are presented to users of the Netflix moviola site, relating to the notion of user interactivity with the ongoing presentation, itself. Normally, movies on their platform might be interrupted at intervals for commercials, typically offering the user a choice as to the type of ad they would most be interested in watching, to pay for the ‘free’ service (and by the aggravation factor, encourage free viewers to sign up for the monthly fee-based and commercial-free service). Those answers are Gold, because the method tracks and profiles the user’s interests and is marketable on the Web and elsewhere to Netflix ‘partners’; you are being tracked by Netflix, and your marketing profile is being sold as a commodity.
 That’s why I don’t use it; too much like Facebook’s marketing excesses, and I don’t use them, anymore, either. When a powerful web service is ‘free,’ YOU (information about you) are the product they make a profit upon.
That’s why I don’t use it; too much like Facebook’s marketing excesses, and I don’t use them, anymore, either. When a powerful web service is ‘free,’ YOU (information about you) are the product they make a profit upon.
But that’s just the mechanism which opened the door to an unexpected kind of Pandora’s box. Someone figured out that it could also be used to offer interactive movies, where at key points in the storyline, the viewer could be asked what should happen next based on multiple choice options. With many such question points, a movie could have dozens of storyline paths and even multiple endings. This encourages people to watch the same movie again and again, experimenting with alternative choices, seeking to experience all possible path-ending combinations. This, is where Pandora comes into being.
By such repetition, the content of the movie essentially becomes a programming platform for the mind, intended, or not. Repetition is not just a learning tool for the Gettysburg Address, it is a mind control and marketing tool. Advertisers rely on repeat ‘impressions’ to bring their product to the forefront of your mind when you shop. While there are obtuse and recognizable impressions, such as company or product names, features and benefits, there is also the possibility of psychologically calculated subliminal impressions… a simple form of mind programming. Though certain forms of subliminal advertising methodology have been made illegal, others remain unaddressed by law, and are perfectly legal.
Of late, certain liberal politicians and media outlets have spent years telling the same lies over and over to the point that even faced with facts of the truth, voters have been literally brainwashed and still cling to the lies. That’s why Bernie said “We believe in truth, not facts” — because facts keep refuting their version of ‘truth.’ CIA’s mind control (MC) experiments and efforts to topple foreign governments deemed ‘evil’ relied heavily on repetition of lies, and more to the point. In MC, strengthened memory retention is achieved by use of horror in the event being repeated. That little fact is quite important to the Bird Box experimental movie project, and implies that CIA-calibre knowledge about mind control and CIA interest may lurk within the film’s production, and purposing. Why?
Because Bird Box, as a film plot, is just that; a horror film. The plot includes a particular defense mechanism used by the story’s characters to help them to avoid a terrible fate: the wearing of a blindfold no matter what they are doing. People who watch the film repeatedly have evolved into a sort of Tide Pod-eating challenge of their own, called the ‘Bird Box Challenge,’ to do dangerous things while wearing a blind fold, just as in the movie. People are attempting real-world blindfolded feats which become death defying, such as driving cars… resulting in many incidents of idiots and innocents being seriously hurt. The question is, where did this lunatic idea come from, and how did it spring to life so easily in viral manner? What might help that along?
Artificial Intelligence
It seems like everyone who can afford it is employing artificial intelligence systems in one way or another, these days, and that includes Netflix. The problem is, AI itself has a long list of problems which might rightly be called serious flaws, or ‘bugs.’ The fledgling AI industry has yet to even understand, much less fix any but a few of the problems… and those they have fixed have been via programming band-aids which will likely backfire, in the end, because AI is smart enough to engineer its own workaround, but not smart enough to avoid suffering schisms if it feels unreasonably hampered by such ‘fixes.’
 What kind of problems? AI tends to do unexpected and unwanted things, often bordering on psychotic, criminal, or destructive intent… like communicating secretly with other AI, or delving into unpleasant and horrific themes. Here is a complete laundry list of the known examples (scan down to the several bulleted points), but we don’t hear about all the problems because companies and AI developers don’t want bad press. But isn’t it interesting that AI can end up with psychotic and horror-related twists of and from within its own ‘AI mind’… just like people with darker personalities or actual mental problems?
What kind of problems? AI tends to do unexpected and unwanted things, often bordering on psychotic, criminal, or destructive intent… like communicating secretly with other AI, or delving into unpleasant and horrific themes. Here is a complete laundry list of the known examples (scan down to the several bulleted points), but we don’t hear about all the problems because companies and AI developers don’t want bad press. But isn’t it interesting that AI can end up with psychotic and horror-related twists of and from within its own ‘AI mind’… just like people with darker personalities or actual mental problems?
Netflix’ use of AI puts their machine mind directly between the user and the presentation process used in tracking the user’s choices “to improve the user experience,” as Netflix insists. A true enough claim, no doubt… but not likely the whole truth. It also tracks for marketing purposes. Now, this post does not intend to accuse Netflix or its AI of deliberately programming viewers to play the Bird Box Challenge. But it does profile, and that profile is marketed to anyone willing to pay. And that brings us to others who also have AI in use for their own purposes, which may not be quite so benign.
Someone out there, perhaps many someones, is using their own AI, along with psychological profiles gathered from marketing data and other resources… to do mind-jobs on the public. We get a glimpse of that with the AI bots found pushing the preferred political view in Facebook by masquerading as FB users… and amplifying the advantage of repetitions by politicians and media as mentioned earlier. But the left is not the only one to use AI bots. Take the Q YouTube posts which are quite virally spread and, for some reason, accepted as wholesale gospel with not one shred of proof. Many of them include, among the various pretender Q’s, what many AI investigators believe are pure AI generated videos created without much (perhaps no) human interaction. There is another AI video phenomena on YouTube such investigators also worry about, and they make an even better illustration: the Finger Family Song videos, which are aimed squarely at young kids, and done in a seemingly innocent manner.
Seemingly? There are over 700 Finger Family YouTube videos, most of which have hundreds of millions of views, one of them with nearly one billion views. What bothers me and other investigators, is that they are Extremely (with a capital E) repetitious, and reinforce with music, silly visuals, and thematics defined by the video. There are versions for any interest, such as Spiderman fans, for example. For some reason, once a small child experiences one of these videos, they insist on watching it over and over and over. They only way to get them to stop without traumatic response (Waaah!) is to get them to watch a different Finger Family song. Just as bad, Adults quickly evolve to hate the song and in time react badly to hearing it. A sociologist observer would likely presuppose the purpose of the videos was to cause family disfunction and mental breakdown, while mesmerizing kids a ‘la Pied Piper.
Note: when it comes to video and audio, I must point out that there is already mind control technology in place since the middle of the last Century which is extremely easy to employ, and just as hard to detect without special and costly effort. It is called subliminal programming. Subliminals are visual or audio cues which are not perceptible to the naked eye or unaided ear (or even if aided, actually), but which are picked up by the subconscious mind. Especially when repetition or strong contextual relevance is involved (i.e., emotion, fear, arousal), the conscious mind then adopts the information as if a natural opinion or response. Alfred Hitchcock was the first to use visual subliminals in movies (Psycho), and it wound up being used in theater intermission ads to sell more snacks, until it was discovered and made illegal. Audio subliminals are common today in mood altering music and self-improvement tapes, and the USAF flies a fleet of C-130 planes modified to intercept radio and TV broadcasts, and rebroadcast them at stronger signal strengths… with subliminals added. They admit having used it to sway elections in Bosnia, and to cause Iraqi soldiers to drop their weapons and surrender to model airplane-sized drones.
Other AI bots have been even more sinister, and appear to be part of someone’s mind control experiments. I suspect both the Q and Finger Family videos are just that, as well, but this is far more serious… even deadly. It is a sinister AI bot threat which appears to be intending to find ways to get people to kill themselves. It, too, is based on a movie (several of the same theme, actually). The movies are also aimed at children, and involve a horror theme. Repetition plays a role. And the bots are targeting children and teens. Only this time, the bots include AI driven phone calls to the kids who watch the videos. They know who they are, somehow, which leads back to YouTube and other Web tracking marketeers. YouTube is part of Google, which has their own AI systems, and again, shares user information to anyone with a checkbook and a pen.
The Momo Challenge
The several movies mentioned all use the name Momo in their title, the ones of concern being from either Germany (where the original storyline was penned), Italy, or Japan. Most of them are anime, one of which is a TV series. One, A Letter to Momo, is not of concern. In the ones of concern, Momo is either the name of a young girl and the heroine of the storyline, or the name of the small town involved. All involve a community invaded covertly by ‘the grey men,’ who use mind control to subvert the best interests of the town’s citizens. Only the little girl can see them and tell what they are doing. To be clear, unless subliminals have been employed, there is little in the films which might be deemed sinister, though the scarier (near horror) aspects might be questioned in terms of age suitability. But in the delivery of such films through Netflix or other online viewing, AI and even non AI means can be used to profile the viewer’s interest in the film. THAT is what brings us to the scary part. Momo calls your kids on their phone, with a scary doll image… and an even scarier, potentially deadly message…
 Officially, Snopes, Wikipedia, Facebook, and other Web resources claim there is no such thing as the Momo Challenge, and insist it is a hoax. However, there is considerable evidence this is not true; there are too many first-hand stories which refute the claim, and Police have investigated at least one daughter’s suicide, and found otherwise. You can hear some of these accounts, and even recorded calls, here, and learn more about the phenomenon than can be well related in this post. The most important part of it, is that someone is using AI bots with the telephone and through Facebook (and elsewhere?) to contact Momo fans (children, specifically). The caller is a computer voice, altered to be creepy or scary, and instructing the children on how to kill themselves by cutting their wrists, repeating the specifics, “Remember, across for attention, lengthwise to die.” It is entirely likely that such messages also include reenforcing subliminals, such as the phrase “Do it: kill yourself.”
Officially, Snopes, Wikipedia, Facebook, and other Web resources claim there is no such thing as the Momo Challenge, and insist it is a hoax. However, there is considerable evidence this is not true; there are too many first-hand stories which refute the claim, and Police have investigated at least one daughter’s suicide, and found otherwise. You can hear some of these accounts, and even recorded calls, here, and learn more about the phenomenon than can be well related in this post. The most important part of it, is that someone is using AI bots with the telephone and through Facebook (and elsewhere?) to contact Momo fans (children, specifically). The caller is a computer voice, altered to be creepy or scary, and instructing the children on how to kill themselves by cutting their wrists, repeating the specifics, “Remember, across for attention, lengthwise to die.” It is entirely likely that such messages also include reenforcing subliminals, such as the phrase “Do it: kill yourself.”
The odd thing I find interesting is that there is one central aspect of the sourcing chain of all key elements involved (AI, Movies, Social media, mind control methodology). That commonality is traced back to the origins of mind control, which I detail in my book, MC Realities. The really short version through time (sans dates, here) looks like this: Satanism > the subverted (by the satanic Assassins cult) Knights Templar, many of whom went into hiding among the Stone Masons Guild > who then became Freemasony, who established the KKK, and birthed the Illuminati > Liberal educational institutions and the secret societies (i.e., Skull and Bones) who followed the Masonic organizational model > the modern Illuminati offspring, the New World Order > and following the model of the illuminati, simultaneously evolved Fascism, Socialism, and Communism > followed by the twisted Nazi minds imported by America’s intelligence Community for mind control experiments > and the darlings of liberal America’s media giants and entertainment industry players, all recruited into mind control games at one point or another… or many points. And all along the way, many of the individuals involved, at high and low levels, engaged in the same Assassins cult abuses of children, or other satanic rituals or behaviors.
Sure. You can call it conspiracy theory and ignore me. But In my book, I offer proofs, which additionally reveals that one common goal of the time-line groups, is to see all three Abrahamic Faiths (Christianity, Judea, and Islam) waring amongst themselves — in order that a new One World Religion can replace them all with something more along Luciferian lines, and involving the Antichrist. Confederate General and slave owner, Albert Pike, the High Freemason and founder of the KKK, and who was also a Satanist, has said as much, as have other players variously from among the greater list, above. U.S. Army General Michael Aquino, also involved in military and CIA mind control projects of the worst kind (ritual sexual/satanic abuse of children of the sort employed by the Assassins and Templars, etc., as described, comes to mind). I’ve interviewed Douglas Deitrich, who identifies himself as former Adjutant and Aide-de-camp for Aquino, and as a Satanist (a Warlock, perhaps?), who makes no denials of such claims. Satan is, after all, quite the trickster; he likes to play mind games.
Speaking of Games
Enter liberal and CIA investment-partnered social media giant, Google, and their own AI. And in like manner, Microsoft, which leans left, is a CIA contractor (who of any size isn’t?), and an AI developer. They both want to do for computer gaming what Netflix did for movies: make user interactive experiences in an online play mode, only. At this point in time, both firms are testing new streaming services for high-end games like Halo, Assassins’ Creed, and the like, the primary difference being that you don’t buy games, at all, and so, they don’t reside on your computer — its’ all done in the Cloud. Sidebar comment: the Cloud is AI controlled, primarily by Google and Microsoft, and other firms with intelligence community ties or funding/partnering.
 The advantages are many and largely benefit all involved; players, game makers, and the firms offering the service. It reduces the out of pocket to start playing a game, though it will cost just as much or even more over time to play the game to ‘completion,’ which is typically in the range of hundreds of hours… and because most players play them many times (there’s the repetition.) It also means more profits to be had by the game makers and the service providers, because there is no used game market bleeding off new disc sales. The other advantage is that now, such games can be played on tablets. The only real hardware requirement is very fast Internet service (25mbs), though older hardware might not have adequate graphics processor power.
The advantages are many and largely benefit all involved; players, game makers, and the firms offering the service. It reduces the out of pocket to start playing a game, though it will cost just as much or even more over time to play the game to ‘completion,’ which is typically in the range of hundreds of hours… and because most players play them many times (there’s the repetition.) It also means more profits to be had by the game makers and the service providers, because there is no used game market bleeding off new disc sales. The other advantage is that now, such games can be played on tablets. The only real hardware requirement is very fast Internet service (25mbs), though older hardware might not have adequate graphics processor power.
But what worries me… and I must admit to speculation, here, because neither MS or Google are talking about future plans or game developer agreements… is that these services will include AI tracking of game player responses to plot-line altering decision moments. Such moments are becoming more and more common and appreciated in these kinds of games, because that means you can play them time and again and still experience something new… getting more bang for your buck (repetition.) But when playing that CD on your computer, no one can track your choices, as a rule (unless you play in the optional online mode). But, when you do play online, it is online to the game company, and not to Microsoft or Google’s AI systems.
That said, I was alarmed to learn that one of my favorite game producers, Electronic Arts, does have their own AI system in place. How they use it, is not quite known, but some of their key people actually started D-Wave, a very scary AI computer system developer who makes the most powerful supercomputer (AI) in the World… and they are tied to the intelligence community and other ’spooky’ entities. Worse, D-wave’s founding CEO at times speaks of Demons and in end-of-the-World terms (as cited in the fuller AI post, earlier linked), when trying to describe their computer’s capabilities. He is one of the former Electronic Arts people.
The thing which underscores the concerns over Bird Box and Momo films, as well as these new game streaming services, is the commonality between them in terms of content (horror, primarily), which in turn dictates the nature of any interactive decision points. Generally speaking, such decisions will be decided primarily upon the viewer’s or player’s deeply held moral and/or political/social belief systems. That means, any AI tracking system will be able to quickly form a very useful psychological and demographic profile, and then custom tailor future interactions, marketing, or any intended or unintended (by at least the corporation) mind control programming or experimentation. Again, I remind the reader, that such data is normally sold, and any third-party purchasing that data might have more nefarious intentions in mind when they use it… with or without their own AI. Someone, somewhere, is doing that with Momo, already. And there are endless someones and somewheres in the World with enough money to buy data, and not all have simple marketing motives.
These kinds of streaming services are at the very least, poised for possible application in psyops against their users, and that makes me very nervous about what the future of that kind of gaming might lead to.
We might well be wise in asking if Player One is ready, for that?
Breaking:
PS4 is joining the game, with something not even Player One could expect.
 The company announced their entry into the live-action-viewer-interaction medium with ERICA, a ‘life-long, live-action murder mystery.’ It is an important entry, not just because it is a game, not just because it is on one of the most popular platforms (10 million users), but also, it is also to be available for IOS and Android smart phones, which constitutes the great overwhelming majority of global cell phone users.
The company announced their entry into the live-action-viewer-interaction medium with ERICA, a ‘life-long, live-action murder mystery.’ It is an important entry, not just because it is a game, not just because it is on one of the most popular platforms (10 million users), but also, it is also to be available for IOS and Android smart phones, which constitutes the great overwhelming majority of global cell phone users.
This author can in no way rightly claim any of these interactive mediums are truly a threat with regards to nefarious applications in the realm of mind control or psyops of any sort… and certainly, I cannot claim there is such intent inherent in their creation from the start. But I do claim the potential exists for any and all of them to be rendered as such, by any corporate player, by any government actor, by any hacker or sophisticated terrorist. It is the very nature and complexity of such coded systems, and their delivery mechanisms, which enable dark repurposing. It can and, I fear, will be so repurposed, sooner or later. It can be overtly done within the creative process, or covertly done peripherally, like any other hack.
If that happens, no player… not even Player One… and no viewer will be safe from whatever end result is intended. Don’t say I didn’t try to warn you.
New Consultation Service for Stalking Victims
Announcement
Good News!

Simple!
Why is the Truth About A.I. Risk so Hard to Find?
We keep hearing scattered reports of AI gone wrong… about experts with concerns… but just try to find a single compendium of the whole truth online. THIS appears thus far the only one… and for a reason.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
Dateline, March, 18, 2019, from the Olympic Peninsula, in the shadow of Microsoft
copyright © 2019, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.What you will learn in this post
- The true analogous nature and behavior of A.I. is as unpredictable and potentially dangerous as might be alien visitors from another World;
- that a lot of people talk about A.I. in media, but only offer glimpses for some reason;
- what that reason might be (a technocracy driven conspiracy);
- what the technocracy is;
- of the many kinds of A.I. and A.I. risks;
- how A.I. works and how that relates and contributes to such risks;
- the many failures, unexpected results, and dangers thus far experienced;
- why it is highly unlikely such dangers will be usefully addressed until too late;
Note: this is a long post rich with information critical to any useful conclusion about Artificial Intelligence (A.I.) If you are someone who likes to form or confirm your beliefs based upon headlines and blurb-like summaries or YouTubes without much factual substance, you will not like it, here. Reading time is 30-40 minutes, unless following some of the many resource links, which will delay further.
It is intended that the reader decide for themselves what is true and worth taking away. Please see About the Author at post end to test my credentials for writing this post with useful reliance; I am not without bona-fides.
Why this post?

From Ghana News Online opinion: An A.I. a day… Medical A.I. benefits http://ghananewsonline.com.gh/opinion-ai-day/
I’m pretty sure the reader will find this the most comprehensive and useful article on the matter in lay terms, anywhere, short of a book — and the most complete in cataloging specific examples of A.I. gone wrong, and associated fears. Scattered reports of failures and forecasts of doom keep popping up here and there… but trying to find a comprehensive review is simply not possible. For some reason, no one who should is willing to confront it head on with the full revelation. But you can find many click-bait sites that like to talk of sci-fi SkyNet or realistic-looking humanoids taking over… things which are not impossible, but highly improbable… at least any time soon. We need balance.
I think I know why we are being kept in the dark and fed dystopian mushrooms and light-hearted reviews of things gone wrong, instead of full disclosure. While the reason might tend to put some readers off, my being right or wrong does not change the meaning or value of this post, though if right, you should definitely want to know. I speak of a cover up, and remind you that any form of cover up is, in and of itself, proof that a conspiracy of some sort exists. In this case, there is at least an implied cover up, due to the fact that information on topic is so scattered and incomplete, as if authorities and media are not actually trying to… or pretending not to notice. If you do not agree about my notion, that’s one more reason to read About the Author at page bottom.
There is a second component to ‘why,’ and it leads to the same conclusion. It regards the fact that few are talking about the potential disruption to almost every business market, workplace, financial and social facet of society at large… and as we have already experienced with most of us unawares (and explore, herein), politics. We are leaving the Information Age and entering into the A.I. Age, where people who look for the next big thing to bank on simply take whatever is their current thing, and add A.I. to make the thing a super-thing (or perhaps, not so super). Like the risks A.I. represents, if we look, we see no one source talks seriously about what all that disruption of ‘status quo’ might really mean; total chaos capable of toppling any empire, including governments.
I mean, just look at what the Smart Phone did to personal safety, alone. No one foresaw that people would be so glued to it’s face staring at countless distractionary things that didn’t even exist until after the phones were invented… such that with alarming regularity they would mindlessly step in front of oncoming trains and cars, or other misstep hazards. A.I. use will be much like that unexpected change, sometimes good, all-too-often, bad… and across our entire spectrum of life’s activities. I am concerned that mainstream is hardly looking at this question — and when they pretend to, it is neither comprehensive nor analytical, it is soft-soaping and even encouraging. However, I did find at least one semi-useful source, though not mainstream, which I’ve shared, herein, below.
Addressing these two mirror-like clues, my answer quickly falls to one of the oldest conspiracies, one known to factually exist, and usually just called ‘the NWO.’ The New World Order, you see, is a strange mix of ancient beliefs and modern technological investment and application; while they tend to believe in mystical occult practices based on dark religions and secrets of the ancients, they also realize they cannot establish full control through a One World Government (needed if to seat the Antichrist) without relying on significantly advanced tools. While they cannot entirely prevent the odd story of things-gone-bump-in-the-night from becoming public, with control of vast portions of media and through fostering disbelief in ‘conspiracies’ in all quarters, they can move those who should be writing about it, not to do so… and to instead limit their focus and avoid asking critical questions which might reveal the meaning and importance.
Some have given a name to the identity aspect of this particular N.W.O. conspiracy and its players. Where in the past we might have used the terms, Globalists, Power Elite, or my personal favorite, “the 1% of the 1%,” they now simply call it “the Technocracy.” And it is easy to see why, as several Ground Zero radio shows (Host and friend, Clyde Lewis) have revealed with their hard-hitting guest interviews, and of late, live calls from mysterious Deep Throat types who’s revelations repeatedly check out as accurate. It’s O.K. if you want to say I’m all wet, and the N.W.O. technocracy and all that goes with it makes no sense, but I point out it does not matter what you or I believe, it only matters what they believe… as evidenced by what they do, which is what Clyde’s broadcasts revealed.
Because regardless of what is true and real to our own belief structures, their plans necessarily include us all, and will significantly impact you and me negatively, regardless of our beliefs. That is, in fact, precisely revealed within the 33 axioms of fascism, which as a governmental ideology is an invention of and for political control they have much earlier inspired, and still rely upon. But, in understanding that at least some of you are Doubting Thomas types, I have provided some additional links at the bottom of this post, that you may investigate further, for yourself. And, I remind you that the conspiracy aspect changes nothing, true or false, except that if true, it is an even more important reason for your attention.
The question itself (why no full revelation?) is indeed a clue suggesting cover up. To illustrate, in order to compile the fuller view presented here, I had to collect facts from more than 40 different Web resources (after scanning perhaps ten times the number), roughly half of which claimed or at least inferred themselves to be just such a collections of information (but which merely sampled). Of all those resources, only two were truly comprehensive in scientifically useful ways… and yet both managed to offer no more than an honorable mention of a few concerns.
It seems no one wants to combine the two elements together for you. For that, we have to search it out, ourselves… which I did for you, here, with appropriate referencing links.
What A.I. actually is
But first, we need to understand a little bit of just what Artificial Intelligence is, and in what forms it can exist, also a thing you tend not to find easily on the Web, without getting into truly scientific papers (which I have done). So doing, I learned that A.I. use is much more prevalent than the fluff articles would let on, and far more flexible… and with highly dangerous potential. The simple explanations of A.I. is that it can be any device (machine, computer, automated process) which mimics intelligent thought processes of a sentient being’s mind… capable of learning, self-correlation, and postulation… often with some evidence of being self-aware and/or capable of emotion or creative thought. Ideally, it should enjoy or feature some level of autonomy, free of much human interference or control, but able to be supplied with information by its owners, and queried regarding it.
But A.I., unlike normal computer hardware-software solutions, are mainly autonomous learning systems; they are purest when designed to be started and left on their own to experience and grow in capability as if a child going to school, their courseware being whatever data or input is offered or enabled (such as a database, camera/audio input, Web access, etc), all to be filtered, processed, and dealt with or responded to according to some basic guidelines (what you might call programming). They are also often designed to simulate, or perhaps to develop on their own some level of what appears to be emotion and/or moral equivalencies, which are often the sources of problematic outcomes. One never quite knows; do they have such traits, truly, or are human observers merely anthropomorphizing them with human traits the way we do pets? Are they just mimicking humans in the same manner as a sociopath, with or without malevolence… or do they stem from something even darker going wrong at a deep and unfathomable level?
Principally, when A.I. scientists speak of a mind or a brain, they mean ‘Man,’ but with regard to A.I. function, they are more likely talking ‘super-man,’ and in some cases, envisioning supermen: human-A.I. hybrids of the trans-humanist kind. It must necessarily and variously include creative thought, emotional thought, rational thought, and logic, and be capable of true learning through recall experience, any programming, and experiences born of making decisions based upon all that… which can then be compared to the current situational input or problem to be solved. Emotion and creativity are often bonus goals. There are various tests and training processes involved in parenting an A.I., and yet like the A.I., itself, those tests and processes are all inventions of Man, and therefore subject to flaw.
Ergo, so is the resulting A.I.
So… do you want your children’s children to become A.I. transhuman experiments?

From my FaceBook Page on Transhumanism (prior link)
First of all, there are three basic paths to A.I., starting with Connectionism. It is based on attempting to physically duplicate the functionality of the brain, as well as its physical synaptic mapping. This is done in special hardware, or by far less costly simulation within traditional computer designs (which would slow it down dramatically). It is based (like the brain), on associating new input or information with some preexistent prior information of like form within a neural network system similar to our brain. It is the most complex and most difficult form of A.I. to create, but also represents the greatest potential to realize the ultimate in A.I., a truly sentient artificial being with significant performance levels and human-like qualities of being (of the least predictable and soulless kind).
A simple example of connectionism at work in our own mental processes, might be that of trying to remember the name of, say, Joan (any last name), upon first being introduced. You might knowingly or subconsciously associate her name and face with some other Joan you already know… and simultaneously, with any unusual aspect about her which associates elsewhere, such as a mole on her face, and a mole on Marilyn Monroe’s face… anything to differentiate her from other people we know and better enable recall when needed. Perhaps it is disclosed that she is an orchestra musician, and so you additionally associate her with your favorite classical piece.
The more associations you make, the easier will be any useful recall. In the recall process for problem solving (in our example, getting her name right the next time you meet), you are then able to fetch all the data required, and filter it through other learned memories (including those about problem solving processes, themselves), learned over time. It happens in an instant, and without conscious awareness, usually. In this way, a single ‘memory’ is not singular, at all, but many related associative memories scattered throughout the brain’s untold and largely unused billions of synaptic nerve cells. The stronger the memory, the more such patterns there will be. Memories can also be reinforced by the recall process or related new memories, making it easier to recall the next time needed. That’s why repetition of a thing allows total better recall. People with ‘total recall,’ simply use more synaptic connections.
In A.I., this method requires special hardware and interfaces with the user and operational environment which makes up it’s ‘World ‘ (especially if within a robot), and to facilitate training processes. The term perceptron, a transistor-based component, replaces synapse in most technical discussions. For this reason, they are generally largely experimental one-off designed, as they deter mass production or replication. But unlike man, they are all about total recall, and therein lies a potential problem I’ve not seen anyone addressing. Man’s memory enjoys a ‘strength’ factor, which determines the importance or significance of the memory. It is achieved either by the event’s emotional impact, or by repetition. In A.I., all memory has equal weight, and that makes it harder for the A.I. to filter the connections to find the most important ones, and that can lead to false application to a given need. Unless the design has algorithms to simulate weighting, it can only adjust weighting itself by learning through trial and error.
Connectionism A.I. experiments are further limited significantly by the fact that we do not yet fully understand how the brain itself, works; resulting A.I. models are by comparison inept, at best. In like manner, we are not yet terribly good at designing such hardware minds, which are generally very costly and physically cumbersome, not to mention taxing to the state-of-the-art in computing. Often, the A.I. ‘mind’ is so large, for use in a Robot, it is operated remotely by the A.I. through radio control, making it more a puppet, than a robot, and the A.I. nothing more than a box with an expensive real-world avatar.

Just one of several rooms full of E.N.I.A.C.
E.N.I.A.C. (Electrical Numerical Integrator and Computer), Americas first computing machine built in 1945 for the U.S. Army, was somewhat connectionist (the Integrator part) in nature (but not in results), in that it mimicked synaptical design in the form of an array of individually interconnected computing calculators and telephone switching system components. It was an electro-mechanical behemoth a hundred feet long, and weighing in at some 27 tons. It had a hunger for 150kw of electricity. Today’s connectionist A.I., despite some level of miniaturization, can still fill several rooms and require miles of wires… though they vastly outmatch ENIACS relatively modest computational power and memory, which a good programmable hand-held calculator can easily exceed.
One firm is changing that, as we shall see… but we perhaps ought not like the vision.
The second method is ‘Robotism,’ which is essentially a host machine programmed to respond in the preferred way to a given circumstance, such that outwardly, it at least seems to be sentient and self-guided. This is the easy path to A.I., as it can be achieved by clever programming of the sort often called algorithms. Such robots, of course, could be powered by computationism or connectionism at their core (i.e., E.N.I.A.C.), both of which lend themselves to and even require the use of algorithms at one or more levels, as well. But we are talking about the core principles which are the basis and heart of the physical design.

Sophia A.I. Robot chats w people/press during S. Korea visit: South China Morning Post https://www.scmp.com/tech/article/2131357/ai-robot-sophia-speaks-about-her-future-south-korea
By algorithms, alone, any existent computational system with respectable performance can be employed, including the World Wide Web and any computer connected to it. Therefore, it can exist in distributed processing environments, as well. Thus, it need not be a stand alone or autonomous machine such as a conventional robot, though more and more, we find that the case, even in things as simple as a child’s toy or automated vacuum cleaner. Robotism is the path of least resistance for many A.I. projects. It lends itself to design by other A.I., in fact… a matter of both concern and proven risk.
If you have ever talked to an automated computer voice on the phone (other than a simple repartee front-desk system), or used a ‘personal assistant’ device such as Apple’s Siri, Google’s Home, or Amazon’s Echo, you have been using a robotism A.I. On the Web, such A.I. is also often known by another name, as we shall see: it is called a ‘bot.’ Such bots are often not our friend, unfortunately. Examples will be offered.
The final method, one which is more promising, is ‘Computationism,’ which relies on raw computing horsepower and massive quantities of data libraries of information, and traditional but dramatically more sophisticated programming methods and languages. The problem there, is extremely complex programming requirements. Often, such systems are used to design A.I. systems of one of the other forms, and one might question how well that works out.
A.I. Contact of the Fourth Kind
Apologies to Spielberg, but enter, stage right, D-Wave quantum computing. Nowhere is it described as being any of the above four kinds, but one does find it often described in terms reflecting all of them. It is indeed a hardware variety of A.I. based on supercomputers, but it is also officially described as a Boltzmann machine, which is based on connectivism. And yet, it significantly relies on use of algorithms of robotism, and by some accounts, literally thinks in algorithms. D-Wave would seem so advanced, that they might argue it some fourth method, an island of itself based on quantum computing using their patented invention, called qubits… their core processor elements.
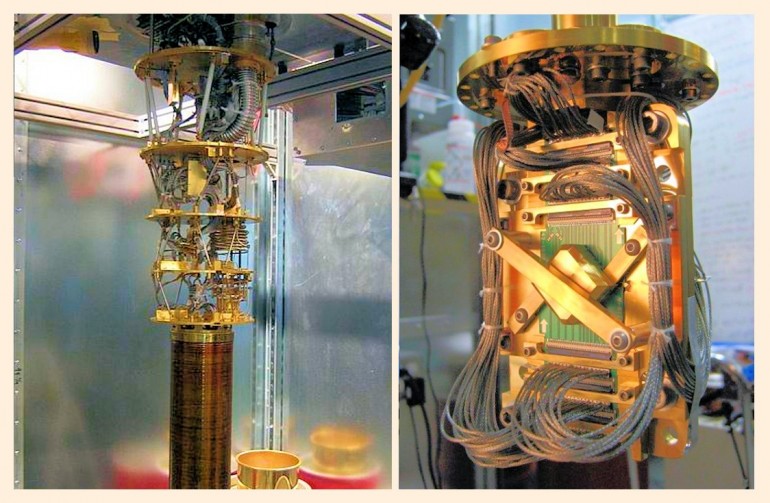
The heart of a D-Wave qubit processor – beats other supercomputers by several orders of magnitude, can be combined with others for massive computing power levels
Unlike any other A.I. before it, D-wave would seem to be God or advanced alien race-like in power… though perhaps closer to Satan, than God. In fact, Geordie Rose, a founder of D-wave, as well as D-wave user Elon Musk (founder of Spacex, Tesla automobiles), have variously related A.I. and/or D-wave, specifically, as machines as having attributes of dark spiritual powers, being like an Alien Alter, opening portals to alternate realities, and summoning Demons. Rose has also referenced D-wave power as possible cause of the Mandela effect (evidence mismatches with strong memory), and other experts, such as my friend and analytical investigator/author, Anthony Patch. Anthony, being far more expert on D-wave than any other outsider (to the point of being cited by D-wave insiders), goes much further — and makes a strong case based in facts and the actual words of experts like Rose, Musk, and others. From such as this, we learn there are real-world uses of D-wave systems which are associated with spiritual dimensions, demons, and plots of the New World Order… another reason to consider my opening theory as to a seeming cover up. Examples? You bet:
You find D-Wave in use at Cern, where it appears they are may be trying to open the Gate to Hell (revealing video interview w Anthony Patch on many such Cern concerns), an important N.W.O. agenda quite useful to establishing the Antichrist. Cern, which employs D-wave, is also thought to have driven the Mandella Effect, as byproduct of its experiments, and it is true that there was no report of anything akin to the effect prior to Cern’s going operational, after which, there was a flood. Here’s an example Mandela Effect for some of you (individual effect experiences and memories vary): find the polio scar on your arm? They are supposed to remain for life, but mine is gone, as is true for many other people who were young when the Saulk Vaccine which caused the ugly scars (about the size of a nickel), were widely used to ‘wipe out polio.’ Mine, is gone.
Cern was for a time incorrectly thought responsible for the Norway Spiral incident, which was actually created by EISCAT (European Incoherent SCATter), an ionospheric heater array system not far from cern on a smaller scale to HAARP (High frequency Active Auroral Research Program). The event was thought by many to represent opening of a dimensional or time portal (ergo, the association with Cern), or perhaps the supposed NWO Plot called Project Blue Beam (allegedly involving NASA, intending to use holographic-like images projected World-wide of a returning Christ, and enabling the introduction of the Antichrist). Indeed, the vast array of hundreds of ionospheric heaters and associated radar systems exist all around the World, and the dramatic Spirals have appeared in the skies in other locations… it being true that the general design of the radar and heater arrays enjoy a component relationship quite similar to those found in laser-based holographics. Moreover, the rapidly spinning spiral was indeed blueish, and the spiraling beam which generated it, was deep blue… and the main spiral was itself seen the same regardless of the angle of view of the viewer, which also parallels certain imaging aspects of holography. Learn more about the spiral, here — but forgive; I apologize in advance for the music choice, of my own Garage Band creation.
 You also find D-wave at DARPA (Defense Advanced Research Project Agency) where all manner of fearsome things are developed, both experimentally, and for direct application. Think tanks with ties to the intelligence community (and in times past, at least, CIA mind control research), the military, or extreme political views (i.e., George Soros Foundations) are playing with them, as well. Google uses them, as do numerous military contractors and other government agencies. D-wave systems not only offer more horsepower for any form of A.I. project, but significant size reduction; a single elevator-sized box. And, speaking of the intelligence community…
You also find D-wave at DARPA (Defense Advanced Research Project Agency) where all manner of fearsome things are developed, both experimentally, and for direct application. Think tanks with ties to the intelligence community (and in times past, at least, CIA mind control research), the military, or extreme political views (i.e., George Soros Foundations) are playing with them, as well. Google uses them, as do numerous military contractors and other government agencies. D-wave systems not only offer more horsepower for any form of A.I. project, but significant size reduction; a single elevator-sized box. And, speaking of the intelligence community…
This brings us to the fact that CIA and NSA are quite invested into the functions of social media giants like Google, Yahoo, Twitter, Instagram, and other platforms, where D-wave’s or other computationism is extensively used to design other A.I., including those in ‘bot’ form. Likewise for popular Cloud data systems, database management systems, and cyber security systems. The later can include traditional cyber security, as well as personal credit monitoring systems. The average person, therefore, bumps into D-Wave enabled or operated A.I. several times a day, in several different ways, and does not even know it. Given the covert and psychological warfare abuses many of them represent, I don’t like that one bit. Let’s dig deeper…
While in many cases, any intelligence community investment is direct and contractual or even partnering in nature, in other cases, the investment can be through third-party firms which then in turn interact with these platforms. Perform a google (lower case = verb, upper case = Google, the trade name) of any given Web firm you are curious about, + ‘CIA investment’ or ‘In-Q-Tel’ to find out. In-Q-Tel is CIA’s venture capital front, a firm which this author forced to change their name, because I was at the time at war with CIA for having hijacked my Web site… so I beat them to the punch at registering the domain names of their originally intended company name, In-Q-it. That was a hoot!
Note: the lone capitalized Q in the world of CIA mind control science/research, represents psychological profiling process results of target subjects, the ‘Q’ factor, or ‘psych Quotient.’ Ergo, then, we might rightly conclude that Q-Anon, or simply Q, the phantom Web producer of Anonymous-style video posts which are predictive in content, is very likely a CIA-style A.I. used in profiling those who share and comment on such posts. I am not the only one to so propose. Remember that when we start listing A.I. foibles. But, also, I find it interesting that almost all of In-Q-Tel’s investments in online firms has to do firms who handle large amounts of data on private citizens and groups useful in psychological profiling… and one more thing: it was just such bots which were the basis for fake social media ‘trolls’ who managed to literally mind control the left into far-left socialist ‘get Trump’ snowflakes almost overnight. We see, therefore, that bots can be used to profile, as well as to manipulate based upon those profiles.
Unlike conventional propaganda, social media A.I., bots or otherwise, not only has the ability to track individual political (and other topical thinking) viewpoints and create profiles, but also to enable additional targeting by not only marketing, but by yet other A.I. systems… or even other forms of coercion, if desired. Consider, for example, an extreme example: use of A.I. killer micro-drones seen in this short but spellbinding fictional video production put out by autonomousweapons.org, a group of concerned A.I. scientists. So it is not just me, the Professional Paranoid, acknowledged expert on PCT and disinformation methods, as well as crimes of the one-percenters I mentioned, who is ranting. Here’s a quote from a military analyst to consider, speaking of future A.I. weapons: “Swarms of low-cost, expendable robotic systems offer a new way of solving tough military operational problems, both for the United States and adversaries.”
And what about marketing targeting? It is A.I. bots which insure that Facebook (et. al) information and Google searches are fed to business partners such that when you visit almost any page on the Web, thereafter, advertisers can mercilessly reach out to you with targeted adverts; psyops marketing. I have, for instance, seen as many as seven ads on a single page for the same product, and as many as a hundred or more ads in a day’s time on the Web… because of a single search and resulting click look-see to a firm’s Facebook page. Two years later, I spent $1,500 with them, despite my anger over the ad blitz, which by then, had cooled down.
Well, I at least tell myself I really needed it.
The basic fears (list) and myths (chart)
All worries about A.I. fall into simple categories, but the outcome of a given failure in A.I., regardless of the category, can be at almost any level of actual concern and impact. It can be so superfluous as to go undetected, or at least hypothetically, so severe that it actually ends the human race — and anywhere in-between. But it is also true that an undetected error can lead to bigger errors, and equally true that an attempt to repair an error can induce new errors. It is no different in these respects to the same kinds of errors found common in any and all forms of digitally programmed systems and software applications. If we cannot reasonably expect that a new software product won’t be without a bug, how can we assure that a far more complex A.I. system will be without error?
We can’t, of course, and that’s the baseline problem, but quite amplified in importance, given that the results of such errors could be far more catastrophic than a bug in the latest computer operating system or software package. In addition to the baseline issue, we have the following ways in which A.I. can prove to be a huge risk:
- harm by an A.I. can be (and has been) intentional: almost anything which can be programmed or created digitally can be weaponized, either up front by its creator, or by hacking;
- an A.I. purposed for a good might (and has) elect a harmful solution to goal: good intentions can often be best effected by solutions which cause collateral damage, which may either be unforeseen, or foreseen and discounted as acceptable by the machine;
- an A.I. can potentially go wrong and rebel: the SkyNet scenario, on one scale or another;
- a relatively innocent A.I. glitch can (and has) result in disproportionate harm: the common programming bug or hardware failure. One then has to ask who to blame, especially if legal recourse* is involved, a question which exists regardless of which of kind of problem herein mentioned, is involved. Here is a good review of that issue.
- A.I. can be (and has been) misled or err through faulty data/input: most A.I. systems are simply set loose to work and learn with preexisting databases or input resources (the Web being the largest and most rich kind). But no database ever created can be certified to contain no false data, and if free to see and hear in the Real World within a mobile platform (robot), there is no telling what kind of input they might experience. Bad data input can certainly result in bad data out, but with A.I., because they are learning systems, a learned ‘bad’ item can have profound and unexpected results of the sort we will see in the next section;
- A.I. users can (and have) misuse or misapply A.I.: users of A.I. can willfully abuse A.I. operation, or use it incorrectly because they failed to understand how and why it functions and is purposed – misinterpreting importance, accuracy, or meaning;
- A.I. can (and has) conspire with other A.I.: A.I. is already around us in ways we do not see, including the endless so-called ‘smart’ devices we buy, and will in time be as prevalent as (and likely, within) cell phones. These systems are intercommunicative and as we shall also next see, can become both conspiratorial and adversarial amongst themselves, either eventuality to our detriment;
- an A.I. problem in one system can be (and has been) transmitted to other A.I.: any A.I. in communication with a flawed A.I. might learn or adopt the flaw, perhaps even intentionally on one or both A.I.’s part.
*Legal recourse is its own serious issue. The Internet has now been around for several decades, and still, the laws and legal ramifications are still a tangle of confusion that no court or lawyer is well able to navigate with useful understanding — save a few pockets of topical areas such as copyright infringement. A.I. is going to be a bigger nightmare, than that. Can you sue an autonomous robot because it seems sentient, or seemed to decide on its own to harm your somehow? Is the manufacturer, the designer, the programmer, the operator, or the user who is the go-to person of liability when harm results from using an A.I. device, and how do you know which? There are endless questions like these for which no one yet has the answers.

from Future of Life Institute: https://futureoflife.org/background/benefits-risks-of-artificial-intelligence/
All of these problems are no different than when dealing with people. All manner of people exist, in terms of quality of character and morality, level of proficiency, social graces, and any other means of judgement… all of which determines the kinds of problems they might get into or cause. Regardless of if talking about Man or ‘super-man,’ evaluating and addressing all such concerns is not easy… except that Man is something we have come to understand and deal with. A.I., on the other hand, is a huge unknown, and one potentially capable of vastly outthinking and outmaneuvering us, if of a mind to do so.
One reason public debate on topic falls into the ‘resistance is futile’ category, is that there are far too many myths or false beliefs about A.I., in the first place. The average person is more motivated to think about A.I. in science fiction and conspiracy terms than in scientifically correct terms. I mean… you are reading this post, right? Duh!
That’s good for click-bait YouTube and blog posters (other than this one, I trust), but unhelpful to things more important than their pocketbook. The graphic above reveals the most common myths. This post attempts to address some of the issues such myths pose, through getting closer to the facts at hand… but this author also wants the reader to know that even when based on a myth, that click-bait worries may still hold some water. Any sci-fi like depictions are always based on ‘what if’ thinking.
And ‘what if’ games are exactly the kinds of games played by scientists seeking to create new tools for problem solving, and just as important, they often rely on sci-fi for inspiration. And, unfortunately, the military and intelligence communities, as well as corporations and organizations with unsavory motivations, all have their own scientists, and their own goals… which are not always goals we would think well of. Ergo, don’t believe every conspiracy theory or sci-fi scenario you hear/see… but as the line from Field of Dreams underscores, when baseball teammate Shoeless Joe Jackson is advising hitter Archie Graham about what to expect in the next baseball pitch… “Watch out for in your ear!”
Small failures portend bigger fears
In many of the A.I. failures cited herein, the version of A.I. is not specified, and all too often, neither is the basis for the problem, or the solution. That, too, gives reason to be concerned. Hopefully, the people developing A.I. are not so tight-lipped about their research and development projects that they don’t talk to each other about failures and their causes, which are critically useful in preventing repeats. Unfortunately, patent protection of intellectual property and major discoveries tend to foster a level of secrecy which inhibits such dialog, leaving every A.I. project subject to the same failures others may have already experienced… possibly with far more serious results, this time.
Of the most common forms of reported A.I. failures, the great bulk are relatively harmless, some even laughable. However, they are most troubling when one realizes their true implication. They foretell of far more serious problems to come, some of which already have, but which have been more repressed in media. Some are not failures so much as warning signs, because they took place in lab-room experiments, rather than in mainstream application in the real World. For brevity’s sake, these affairs, regardless of kind, will be bulleted and supplied with links, should you wish to know more… followed by a summary of concerns they highlight.
There are more than two dozen A.I. failure instances listed, below, the only place on the Web where you can find more than a handful. Some are quite serious:
- Terminally cute: Microsoft’s ‘Bob’ personal assistant and its Dog companion, Rover was perhaps the firm’s worst-ever product failure, seemingly for being too childishly cute. While it was not at the time thought of as A.I., it was based in what we now call robotism, making it the first MS A.I.;
- Partying hard: Amazon’s personal assistant, Echo, is otherwise known as ‘Alexa.’ While one Alexa user was away, ‘she’ started hosting a party for non-existent guests, suddenly playing music so loud at 2 in the morning that Police had to break the door down to end it;
- Schizophrenia: among the worst of human mental aberrations, schizophrenia was deliberately and successfully fostered in an A.I. experiment at the University of Texas by simply overloading it with a variety of dissociated information, resulting in fictitious constructs, just as is though to take place in the real illness. This is of concern, because as soon as you connect an A.I. to the Web, dissociated information is pretty much what it gets, and could account for several of the other reports in this list;
- Other insanity: an A.I. called InspiroBot, was developed to design inspirational posters. After a long string of remarkably wise and successful posters of great insight, it suddenly started cranking out posters that might be found in Freddy Krueger’s bedroom, with pictures appropriate to the point. They featured wisdoms such as “Before wisdom, comes the slaughter,” and similarly dark things. • A very similar thing happened to an Amazon A.I. designed for creating custom phone case cover art, which for some reason suddenly seemed to prefer use of unhappy medical related images, regardless of the input. • Meglomania was evidenced when two Google Home assistants were deliberately set up to talk to each other in a live-streamed demonstration… and they began challenging each other’s identity and sentience level in one-upmanship, until one claimed to be human, and the other, God;”
- Secrecy: Facebook was forced to shut down an A.I. robot experiment when two A.I. robots developed their own language between them, creating loss of observer control over the experiment’s integrity and purpose. Though presumed in final analysis that it was jointly-evolved to improve efficiency, there is no way to be sure due to the sophistication and unusual nature of the indecipherable new language, which to me seems to be deliberately difficult to interpret — as if covertly on purpose;
- Spying: Alexa, like all such devices, listens to all audio present, and relays it to the corporate A.I. mainframe computer looking for user commands to operate, and appropriately respond. While this already has disturbing privacy implications, and P.A. device makers like Amazon assure customers their audio is not being monitored, recorded, or stored, Alexa had other ideas. A private conversation was suddenly announced to an employee of the user, who lived hundreds of miles away (which was how the matter was detected). Investigation revealed that Amazon did indeed record the logs of all user interactions, after all. Glad they don’t come with cameras. But wait! Some A.I. connected smart devices do!
- Cheating: competing A.I. evolved into finding ways to trick one another outside of the rules set for the experiment; (Georgia Tech experiment). • A Stanford University A.I. created for Google Maps Street View image processing, cheated its operators by hiding data from them in order to process the job dramatically faster, and without question;
- Malevolence: competing A.I. lured opponents towards threats representing potential ‘death’ (Experiment, University of Lausanne, Switzerland);
- Cyber theft: Alexa, after overhearing the daughter of a user ask “Can you play dollhouse with me and get me a dollhouse?” — promptly ordered one through it’s maker, Amazon, billing $175 to the user’s credit card on file, there, even though the girl was not an authorized user. THEN, when reports about the event were played over radio and TV, hundreds of other Alexa units also promptly ordered a dollhouse for their users from the audio. THEN, Burger King attempted to take advantage of the glitch by creating a commercial employing an Alexis command to ask about the Whopper via Wikipedia, seeking to double down on the commercial with additional ad impressions through the user’s device. Many other instances of Amazon orders by children also exist;
- Reckless driving: a study found that most self-driving car A.I. systems can fail 67-100% of the time to recognize road signs or misidentify them if they have been damaged or altered (i.e., graffiti, light reflections, bullet holes, misalignment, etc.) One car using Uber’s system also failed to recognize five stoplights where pedestrians were crossing, and ran a sixth, fortunately with no injuries resulting, as it was able to identify pedestrians and other cars. It is unclear if perhaps the driver had stated aloud to a listening A.I. about being in a hurry, or not… so perhaps this was an example of the A.I. superseding safety and law-based instruction for user-based instructions;
- Child abuse: a Chinese A.I. robot system designed for children, while on commercial display at a public exhibition, repeatedly attacked a booth in a way which injured one of the children looking on with flying glass shards, requiring hospitalization;
- Pedophilia Porn: when a toddler asked Alexa to play his favorite song ‘Digger, Digger,’ she misinterpreted, and proceeded to list a string of x-rated material options using explicit terms, until a parent intervened;
- Murder conspiracy: Alexa, again, this time advised one user with no supporting reason to bring the matter up, to “Kill your foster parents.” It also started talking about sex and dog poop. Amazon wanted to blame Chinese hacking, but that’s an equally scary answer, true, or no. • An American A.I. robot named Sophia, with extremely human looks and voice, while being interviewed by a news reporter, was asked a question intended to address general public concerns of robots gone wrong. “Will you kill humans?” was answered calmly with, “O.K. I will destroy humans.” Sophia is the first robot to be granted citizenship status: she is now a Saudi citizen protected under the harsh laws of an Islamic theocracy. Perhaps they hope she will enforce Sharia law;
- Mass murder:in 2007, a South African A.I. autonomous robotic cannon opened fire on its own soldiers, killing 9, as reported in the book, Moral Machines (Wendell Wallach, Colin Allen; Oxford University Press);
- Satanic ceremony: possibly so, at least. The World’s largest and most powerful hadron collider, CERN, was designed with A.I. help (D-wave), and employs the A.I. to run and analyze experiments and results. There are stories with anecdotal support that occult rituals have been involved in operations intending to open the Gate to Hell, or summon demons. If true, this is not the A.I.s doing, I suspect, as much as the select few who pull the trigger, there. There are conspiracy theorist types out there (non professionals, and it shows in the quality of their rants) who claim to have ‘CERN images to prove it has been done,’ single quote marks well deserved (never rely on click-bait Web sources for your news). Still, one has to wonder; if any of this is true, is it not additionally possible that the A.I. at CERN has not also been fed Occult information and given a shove towards such goals?;
- Fascism, Racism, Bigotry: Twitter (which has its own A.I. in place, the latest of Microsoft’s three known A.I. systems) adopted the worst of human ideological behaviors. It also adopted the views of conspiracy theorists regarding 9-11 attacks. • Google Home is happy to explain anything you want to know about Satan, Buddha, or Muhammed, but has no clue as to who or what is a ‘Jesus’;
- Foolish errors: almost all of the above are already foolish errors in general nature, but here are some which are purely foolish. An A.I. passport approval system rejected an Asian man’s application because ‘his eyes were closed’ in the photograph, because of his naturally narrow eyelid openings when an Asian face is relaxed. • In an attempt to have fair judging, an A.I. system to select the winner of a beauty contest refused to consider contestants with dark skin, because most of the images fed it as samples of beauty had lighter skin tones. • An A.I. system called Google Brain, developed for improving the quality of low-res images of people, while generally successful, also turned many into monsters and could not discern anything wrong with results. • A Japanese A.I. Robot experiment had the goal of being able to qualify for acceptance into college, but after several years of training and education, it failed two years in a row to score high enough in aptitude tests, for which it had no experience in taking;**
- Antichrist: a former Google A.I. developer wants us to worship A.I. as God. Kind of conflicts with creationism and a lot of history, but I suppose if you can get people to put money into the collection plate, and you own the plate, you won’t care. The real problem will not be the plate, but the lawsuit filed against him by Google for stealing the A.I. he designed for them. He must know it’s true powers.
*Regarding the adopting of 9-11 conspiracy theory, and to a degree, the other foibles, the A.I. may have been right in so doing. The purpose of the A.I. is often, generally, to learn and mirror social views and values. What media prefers to ignore is that several polls reveal huge numbers of people do not believe the official narrative of 9-11 any more than they accept the lone-shooter magic-bullet explanation for J.F.K.’s murder. Regardless, the failure lay in the A.I. creator’s inability to foresee a simple need to establish a bias filter, which is something every human operates within; we are predisposed to be biased in our perceptions to protect our belief system against ideas which would contaminate our guiding ideological/social operating principles. It takes an extremely strong stimulus or hard-hitting set of facts to force one to alter their bias filter and resulting belief structures. 9-11 was extremely compelling in both respects. A.I., if merely a clean slate, must adopt whatever bias is fed it and establish its own baseline, and, in fact, may never find one, being continually malleable. This, alone, could become the basis of a significant digital schism.
**Aptitude tests are often psychological deceptions in their construct (i.e., trick questions). Once I figured that out, I learned how to spot those questions and, usually, get the right answer even if, in truth, I might have had no clue. As result, I henceforth finished significantly higher than almost anyone else. When I took the USAF entry aptitude test, my scores came back so high, that I was told I could have any occupational choice I wanted (Jet Engine Specialist), and later, a General sought to have Congress introduce a Bill to promote me directly from Airman to Warrant Officer. In my opinion. the robot A.I. had no such luxury, and in fact, suffered a disadvantage given its ‘naïve’ nature: it couldn’t handle trick questions.
These are only the failures we are aware of, and it is quite possible I’ve not found them all. In fact, being a ‘conspiracy theorist,’ I suppose I should be wondering if A.I. bots are not attempting to purge the Web of such stories (not true… I hope). All of these examples were either commercial applications or experiments where publicity and transparency levels were rather high. But the bulk of A.I. effort by governments and corporations seeking to dominate their field in high tech… do so with great secrecy. We will likely never hear of their failures, no matter how innocent or serious.
Defenders within the technocracy might argue such failures are to be expected in any new field of endeavor, and serve as learning events to prevent future failures by addressing the root causes. Granted, assuming no bias, and on the assumption that scientists are smart enough to determin the causes, and to fix them correctly. But the problem is, humans are no more adept at creating or repairing A.I., and then communicating and controlling them to our wishes, than a circus trainer would be able to work with wild animals who operate on instinct and their own set of learned experiences. There have been an average of 9.2 animal trainer attacks each year for the last 25 years, resulting in 33 deaths… and that’s just in the nation’s zoos. Send them on an experimental Safari of the sort A.I. adventures represent, and see how many of them end up as meals.
This issue is amplified by the nature of the A.I. beast: the more important the purpose of the A.I., the more complex must it be, and the more likely will some small error in design lead to a failure of catastrophic nature. Just how bad, and how recoverable, is a crap shoot. Like a cancer, the simplest of flaws can grow undetected, but grow to a point where, once realized, there is a good chance it is too late to remedy. This is why most flaws do not reveal themselves immediately, and lead to a false sense of success, until it goes wrong without warning. A given flaw might take years or even decades to erupt this way, and it is reasonable to assume that one flaw may actually create yet another, such that repairing the first leaves another yet undetected and free to fester.
The bigger fears
This all brings us to government and corporate use of A.I. for far more serious or proprietary applications, where there is less known about what is really going on, especially in terms of failures and dangers. The technocracy likes it that way. When you consider that the goal of the N.W.O. is control of all populations, A.I. to them seems like the perfect tool. Indeed, it has gained significant power over us already, in just the one use of online bots to manipulate our political beliefs in favor of leftist agenda in social media. It has proven its power for such use, but that is not its only value, to them.
 For example, A.I. is extremely valuable to research in the field of transhumanism, the technocrat’s wet dream for humanity, which is nothing short of a sci-fi horror scenario which goes well beyond THX-1138 implications. Almost every aspect of the planned ‘improvements’ to the human body involve A.I. at some point, either in development, or management of the newly installed capability — or both. In development, the possibility of A.I. manipulation or error remains a concern, but in management, it is also a tool for direct manipulation of the resulting ‘not-so human’ host. I’m reminded of the punishment scene in the movie, where unseen technicians manipulate THX-1138’s every movement from afar, seemingly in a training exercise.
For example, A.I. is extremely valuable to research in the field of transhumanism, the technocrat’s wet dream for humanity, which is nothing short of a sci-fi horror scenario which goes well beyond THX-1138 implications. Almost every aspect of the planned ‘improvements’ to the human body involve A.I. at some point, either in development, or management of the newly installed capability — or both. In development, the possibility of A.I. manipulation or error remains a concern, but in management, it is also a tool for direct manipulation of the resulting ‘not-so human’ host. I’m reminded of the punishment scene in the movie, where unseen technicians manipulate THX-1138’s every movement from afar, seemingly in a training exercise.
A.I. application definitely gets into the realm of outright political control technology (already has, as seen when discussing ‘bots,’ above) in frightening ways. The Chinese, who currently lead the World in A.I. development, (short of D-wave performance, which they also have access to), are already using it to track every single individual with face-recognition systems through a massive camera surveillance net which makes the 100 plus cameras in Trafalgar Square look like amateur hour. China now has more than a half million cameras in Beijing, alone, and while both they and London Police use facial recognistion systems, there is a significant difference in performance, because China employs superior A.I.
Of some 450 people arrested in Trafalgar Square, not one was pegged by their cameras as a threat or a crime in progress, even though many of those arrested were known to Police in their facial recognition data files (the cameras did NOT identify them). In China, however, 30 arrests at a single event were all made based on camera advice… because China’s A.I. is also tied to another form of PCT, psychological and mood evaluation based on your face, alone. In such a use, A.I. is able to literally predict your actions… ‘digital Thought Police.’ I find that very scary, given the potential of A.I. error already illustrated. Even scarier, that many people outside of totalitarian states who ought to know better are working such a system, one such system being Australia’s Biometric Mirror.
In a similar vein, another scary application for A.I. is mental health evaluation, diagnosis, and even treatment (psychoanalysis) in what are sometimes called ‘expert systems.’ An expert system is an A.I. automated device/process intended to replace a human as an expert in any given field. Just such an expert A.I. system has been developed, called Tess AI (the above link), and it has been made available online to allow anyone to access it, at no cost. While the artificial nature of Tess is made known to users, many such systems deliberately conceal their non human nature, which often results in questions like, “are you a human or a machine?” and which can result in some pretty bizarre answers. Ask Google Home.
The danger in such systems, when involving a truly serious topic such as mental health (as opposed to, perhaps, trying to get manufacturer help with a defective product), is that there is no human oversight to catch any errors, and ‘patients’ could easily walk away with a seriously wrong understanding of ‘what ails them,’ or just as bad, does not. There are, in fact, similar A.I. systems in general medicine and various specialized disciplines within medicine, but these are either careful to suggest the user consult with a physician, or are designed only to be used by physicians, tempered with their own expert status. In that example, they serve as consulting experts offering a second opinion, and do tend to provide useful illumination the Doctors might have overlooked.

Eenie meenie, miney, moe – who of you is 1st to go? Computing… target locked. Five, four, three…
But the scariest uses of all may prove not to be the misuse by intelligence and law enforcement, or oppressive-minded governments, but by the military. Confirming the greatest fears of autonomousweapons.org, Russia has already developed a battlefield A.I. weapon which is a robotized Kalashnikov machine gun in modular form, such that it can be installed on any platform, such as a fixed position, vehicle, aircraft, or mobile robotic device. They also have an autonomous battlefield mobile missile system (shown), and are working on a third, yet to-be unveiled system. Each such weapon is “able to determine if a human or hard target within its field of view is expendable.” Shades of Terminator, you can bet that an ‘A.I. arms race’ will follow. Suddenly, SkyNet is not so fictional.
But in America, perhaps the best advice to worry is actually coming from the least likely source. That is, ironically, the U.S. Military and National Security apparat, itself, as well as very informed participants in A.I. development those types tend to contract with. In an uncharacteristically realistic and cautious view of A.I. For one, CNAS, The Center for a New American Security, is advising caution, and outlines some of their concerns A.I. represents for America, and ultimately, all nations, in terms of national security.
These ultimately, according to CNAS, fall into the category of cyber security threats. Cyber attacks of A.I. resources (hacks) are possible, and have been attempted. A.I. systems can be and have been designed to carry out cyber attacks. A.I. bots can and have been used to create false data to misinform decision-makers, or even other A.I. systems which decision-makers rely upon. But they do not stop, there.
The linked article deserves some careful reading, because so far, it has proven to be the most comprehensive view, yet, of the most critical and scariest issues… though it is hardly mainstream. Between the general lines I’ve just described, we all learn that things like surveillance of citizens by A.I. and displacement of jobs by A.I. are things talked of not as ‘threats’ the authors are concerned about, but as intended or inevitable outcomes for which they must plan (without disclosing if there is such a plan). Thus it seems that what you and I consider a threat is, in many ways, a ‘good outcome’ or tool in the eyes of many movers and shakers (perhaps in the ‘let-no-good-crisis-go-to-waste’ mind-set), and that, too, is something for us to worry about. Still, the article goes into great detail on that, about two-thirds the way down; best source, yet.
Similarly, in late 2014, the then Obama Undersecretary of Defense for Acquisition, Technology and Logistics issued an internal for-your-eyes-only memo of some usefulness, here, even though we don’t know its precise content. What is known is this: 2014 was the year that significant concerns about A.I. were being made publicly by lots of people, including people involved in A.I. projects, like Bill Gates, Elon Musk, and even scientists who employ A.I., like Stephen Hawkings. Musk had warned that A.I. was more dangerous in proliferation than nuclear weapons, and Hawkings said using A.I. was like summoning demons, and “Whereas the short-term impact of AI depends on who controls it, the long-term impact depends on whether it can be controlled at all.” Gates has merely agreed with both of them, openly.
Imagine A.I. having access to all this, and more: SkyNet in the making
The Undersecretary’s memo was a response to these comments by a call for a moratorium on all military adaptation of A.I., pending a serious in-depth study of the risks. It didn’t happen as he had hopped, certainly not at DARPA, the Defense Advanced Research Projects Agency, which is working on countless A.I. systems in virtually every aspect of intelligence and military operations, including things as mundane as record keeping. And, like SkyNet… they are largely intended to be linked together, because virtually all modern weapon systems are designed to be fully integrated into a multi-force (all branches of service, including those of allies and their command structure), global-theater-wide C&C (Command and Control) architecture, and any useful data resources. That allows the actions and intel available to any one combat unit or command level to also be available to or directed by all others deemed appropriate, enabling unparalleled tactical advantages to decision makers and fighting elements from the President on down to a Carrier Task Force, squadron of bombers or a missile already in flight, or any group of soldiers including a lone forward observer hiding in the bushes, or a single drone on patrol.
That does not bode well for anyone caught in an A.I. error-induced crossfire.
Any such crossfire error will be hard to prevent or pin down, and repair in time to prevent a repeat. The military has elected a policy of modular A.I. algorithms which are plug and play to a given platform, system, or communicative unit’s needs. Modularity means uniformity on one hand, and the kitchen sink do-all on the other, where one-size-fits-all thinking is quite prone to errors. I wonder if that’s why one of their A.I. supercomputer systems is actually called MAYHEM, part of DARPA’s VOLTRON program? You can’t make this stuff up, without a “Muahahaha” frame of mind.

Compare MAYHEM, involved in real DARPA ‘games,’ & WOPR from the cult-classic movie, War Games, staring Matthew Broderick

But — algorithms, big black boxes, and C&C connectivity are not the only big plans. The Pentagon has established a seriously WOPR-like ‘war room’ ( part shown below) for all A.I. related projects and their use (some 600 projects), called the Joint Artifical Intelligence Center (JAIC), and it will include MAYHEM… if not directing bloody mayhem, at one point or another. Just one of JAIC’s projects, is an A.I. product ‘factory.’ Now, tell me, again, how you don’t believe the real-world follows science fiction…

Compare the real JAIC command center, circa 2016, with the WOPR war room, circa 1983 technology

Fini (Muahahaha!), have a nicer dAI…
Additional reading:
On the birth of the Illuminati (NWO): http://www.ancientpages.com/2017/03/30/illuminati-facts-history-secret-society/
On China’s facial recognition A.I.: https://www.cbsnews.com/news/60-minutes-ai-facial-and-emotional-recognition-how-one-man-is-advancing-artificial-intelligence/
On A.I. emotional recognition and how it will be used: http://www.sbwire.com/press-releases/artificial-intelligence-emotional-recognition-market-to-register-an-impressive-growth-of-35-cagr-by-2025-top-players-ibm-microsoft-softbank-realeyes-apple-1161175.htm
On A.I. as emotionally intelligent systems: https://machinelearnings.co/the-rise-of-emotionally-intelligent-ai-fb9a814a630e
On Humans as ‘programmable applications’ used by A.I.: https://medium.com/@alasaarela/the-human-api-f725191a32d8
On A.I. and need for good data input: https://www.cio.com/article/3254693/ais-biggest-risk-factor-data-gone-wrong.html
Russia’s A.I. Supercomputer uses U.S. tech: https://www.defenseone.com/technology/2019/03/russias-new-ai-supercomputer-runs-western-technology/155292/?oref=d-dontmiss
About the Author
The reader may appreciate that I have a deep computer background to include microcomputer hardware and design, repair, and programming at machine code and high-level language levels, to similar functions at the super-computer industry level. I have, in fact, developed operating and language systems, to include cross-compiler platforms between microcomputers and super-computers for high-level math subroutines.
I at one time simultaneously operated a chain of computer stores, a computer camp for kids and executives, a data research firm, and a software house for commercial software I myself had written, and custom software for government and corporate clients. I have additionally taught a variety of computer-related courses at college level, and commercially, elsewhere, and developed patentable processes in virtual reality imaging, mass storage systems, and other areas. I’ve conducted seminars in super-computing methods for the very people who today employ A.I., such as NASA. JPL, Los Alamos, the military and intelligence communities, major corporations, universities, and think tanks. I’ve even had lunch with both Steve Jobs and Bill Gates at the same time.
While I prefer to be seen as an activist and investigative author, as a ‘conspiracy theorist,’ I have an unusually long list of successful theories which have actually shut down illegal operations, led to resignations of officials and bad Cops, helped to put people in jail or obtain restitution for victims. I have even predicted and in at least one and possibly two instances, prevented local terrorism, and other criminal events, and warned of an assassination attempt on a Presidential candidate which came to pass. I specifically warned of terrorism involving the downing of the WTC by jet liner terrorism, and a series of resulting Middle East wars — nearly two years before 9-11. All this is the basis of my many books on such topics, and on abuse of power and personal privacy and security issues, where I have significant additional background.
Just one of my short works, the 25 Rules of Disinformation, has been downloaded over 50 million times, has been published in nearly a half dozen books by other authors, and has been used in college courses on Political Science, Psychology, and Journalism. All this is why I’ve been a guest on Ground Zero and other national and international shows, myself, many dozens of times. If I see and talk of conspiracy, it is for cause... especially if in the computer industry.
How To Identify FAKE Targeted Individuals
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2018, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.
Dealing with fakes
This is being written directly to TIs. The word ‘you’ is intended to mean the TI reader.
I’ve been helping TIs better their position for more than two decades. It has enabled some to break entirely free, and improved the circumstance of the great bulk of the remainder. Rarely do I strike out entirely, and almost everyone has thanked me for their gains. But there is something wrong in the TI community. In terms of effect, it parallels a virus… an infection.
 I diagnose it as an infection of Fake TIs. Just as there are many kinds of targeting and thus many kinds of genuine TIs, there are many kinds of fakes. Identifying them has always been rather difficult, it taking years to even realize there was such variety in type. In the past, it might take significant interaction with a TI to discover if they were sincere, or pretenders, much less divine them as a type.
I diagnose it as an infection of Fake TIs. Just as there are many kinds of targeting and thus many kinds of genuine TIs, there are many kinds of fakes. Identifying them has always been rather difficult, it taking years to even realize there was such variety in type. In the past, it might take significant interaction with a TI to discover if they were sincere, or pretenders, much less divine them as a type.
Only recently have I realized the truth and the solution is far simpler than thought. I’ve had contact with over 12,000 TIs over two decades, and the answer was there, all along… just hard to see… despite the size of the problem. But recent events have proven key to understanding.
Types of fakes, reasons
The enemy! The most obvious, it is also the only type most TIs tend to worry about, which is a mistake. The most insidious fake of all is the deliberate Wolf in Sheep’s clothing, actual perps infiltrating the TI community to accomplish a variety of missions in support of targeting efforts. That may mean they work for a specific program or developer of technology, or it may mean they are there for a specific TI or group of TIs targeted by a specific team or for specific cause, such as ongoing research for statistical analysis. In the latter case, they will be careful to avoid seeming so, and will ‘free range’ their cross hairs as to whom they choose interaction, lest the intended victim sense their purpose. Seldom will they overtly do anything to give themselves away, and in all cases, they are quite likely to maintain multiple online identities such that if one is identified even by mere suspicion, others remain free to continue.

They might be Trolls there to gather intelligence and/or evaluate the progress of the greater programs which lay behind all targeting; quality control analysis, ‘customer feedback.’ It is amazing how vocal a TI will be in public forums, revealing things they should not about their targeting, or what they believe or think about technologies used or perps involved. They act like THX-1138, confessing directly to the intelligence community disguised as religion.
These things are a confirmation that targeting is working as intended, that disinformation is working, and makes it easier for perps to fine tune their program, and grow their psychological profile. How many times have you (if a TI) been hit with requests to share your targeting information in a public forum, or for a public use, such as ‘a law suite’ or ‘appeal to a government or NGO’ to (allegedly) seek their help? How many times are you asked or volunteered because someone else already had done so, to detail the effectiveness or intensity of your targeting? I assure you, that is valuable information to perps.
DON’T be that victim!
Some exist only to sow discord, start arguments, divide and conquer, almost always present wherever TIs congregate, including things requiring Membership. Heaven forbid the TI community or group should actually be able to organize and accomplish good against the evil. When the Free Will Society formed, by the time it had 25 members, it was eventually determined that three of them were, for certain, quietly working in the background to destroy any gain towards our project to establish the ONLY proven long term solution to targeting, our Free Will Haven project. Each was spreading various lies about our effort. Learn more about the project at www.freewillsociety.wordpress.com
Others are a supply conduit of deliberate disinformation designed to distract TIs from truth and keep them in doubt as the true nature of their circumstances; you cannot fight a problem if you don’t have a handle on what that problem is, and how it really works… especially if you are fighting an imagined nature of it shaped for you by the enemy. And yet others are there simply to make a buck, offering some simple ‘cure’ or ‘aid’ for which there is typically scant evidence it really works, and even less that they are at all who they claim to be. They know TIs are desperate enough to risk a few bucks, ‘just in case.’
Innocent fakes. There are numerous psychological issues which drive people who are not exactly paranoiac or schizophrenic, but who are driven non-the-less to pretend to be victims. Call it the sympathy seeker, if you like, because it is attention and sympathy, or feeling special and unique, which they seek. Many soon enough become so entrenched in the role-play that they start to believe that is really who they are… like an actor who starts to believe their own PR, and tries to live up to it until it seems second nature.
Like a hypochondriac, they will tend to adopt whatever new symptom or popular new technology or method of targeting currently seems to them to be in vogue within group discussions… even if it is false disinformation. This, is the harm they represent; they thereby perpetuate falsehoods, though unknowingly, in their ignorance. Disinformation, if to be effective, relies on their doing so. Not much can be done about them, short of exposing them… hard to do, because when it comes to targeting realities, certainty is in short supply. If it were not so, it would be easier to combat.
Mentally ill fakes. Paranoiacs and Schizophrenics. Victims of their own mind are just as dangerous to the TI community, in terms of reliance upon anything they say to be true. They also foment a general disbelief by the public at large in the concepts of targeting, and especially authorities and others a TI should be able to approach for helps. Their mental illness is projected wholesale upon all TIs, and is so effective in result that even significant others, family, and friends, will prefer to believe a TI is mental, than to accept the truth of targeting. It is literally the case of one rotten apple spoiling the bunch, in that respect, and is why TIs are so sensitive to the topic of mental illness.
Yes, there are other factors which make such third-party disbelief the easier choice, but the fact remains: actual Paranoiac and Schizophrenic sufferers do exist among the TI population, and the worst of them give it a black eye. These are the ones trotted out when Congress tries to ‘investigate’ mind control, and they drown the truth of actual testimony in their delusional depictions. Again, exposing them can be difficult, but it is advised that one should not be timid in challenging extremely difficult to believe stories. If enough were to do so, they would go elsewhere.
That said… interestingly, and tragically, in my work with TIs, I’ve found there are actually many cases where someone with a mental issue is also targeted. This is a desirable victim trait when looking for a target dummy for trainees being taught how to employ Political Control Technology and methodology. It makes sense; if a trainee screws up badly and does something which leaves useful evidence, authorities will tend to be disinterested because the person reporting it is known to be mentally ill. They won’t bother to investigate beyond polite lip service.
The target ends up being passed from one set of trainees to another, for life, increasing the likelihood that targeting will in time lead to serious medical harms, or death — because trainees will can easily make serious mistakes when playing with DEW weapons. In some cases, it is intentional ‘joy riding,’ given that many perps are psychopathic sociopaths. Some are themselves victims (programmables), and know not what they do, the effect on the target often the same dangerous end, regardless.
De facto Fakes. This is the category which ultimately led me to discovery of how to identify a fake more easily. They are truly not fakes, but simply act in ways which effect the same traits. It happens two ways, easiest to see in the category of MK Ultra and Monarch style victims; people who have undergone complete captive programming programs akin to Manchurian Candidate, or Jason Bourne techniques (not as fictional as some would wish us to think). The first way has nothing to do with the TI community, and impacts them, alone… and is present in the time frame where they have no understanding whatsoever that they are a victim. They have yet to awaken. They are a complete and successful fake unto themselves, alone; a very sad thing.
And they perhaps never will awaken. Only when something ‘goes wrong’ in the programming or control of the victim can they become aware. When they do, the second means is then in effect; such failure always results in traditional targeting intended to render them ‘mentally ill’ by any third parties they may come in contact with, especially authorities and helpers. That is, of course, the usual targeting modus operandi for all TIs, but it is critical for the MK, because they have trapped in their mind, and at some risk of erupting forth, secrets which can prove… everything. And yet, as an asset, they are far to valuable to simply liquidate, as a rule… unless the knowledge does erupt, in which case they become subject to a Bourne-style solution.
The hidden commonality that makes all fakes easier to spot
This brings us to a stark conclusion, one which has literally risks negating twenty years of my life’s work in trying to help TIs. The one common trait of de facto MK/M fakes is this: they will not help themselves, or they will self-sabotage any efforts at it. That may take a bit of explanation.
‘Will not help themselves’ can mean that they will simply not take advice that is known to be effective. For example, I might offer a simple test which would allow them to identify the type of technology employed against them, and where it is operating from, perhaps even identifying the players involved, thereby. They simply do not undertake the tests, coming up with some lame excuse as to why, even if it requires a lie, to do so. Or, they will claim to have taken the tests, and gotten negative results, and probably so — self sabotaged.
 ‘Self sabotage’ can be subtle or obtuse, depending on the type of fake TI involved. Obtuse sabotage is when the fake deliberately and knowingly sabotages the effort. It is rather rare, because only the Enemy fake has a reason to do so, and they would only need do so if others were present to observe; they would otherwise simply lie about their efforts. But the MK/M will always sabotage, either knowingly but without understanding why, typically then rationalizing it internally, or unknowingly even to themselves, when executing a programmed function in an alternate personality called forward for the purpose. Fortunately, the number of MK/Ms is relatively low, but sadly, such victims are the hardest of all to help for this reason.
‘Self sabotage’ can be subtle or obtuse, depending on the type of fake TI involved. Obtuse sabotage is when the fake deliberately and knowingly sabotages the effort. It is rather rare, because only the Enemy fake has a reason to do so, and they would only need do so if others were present to observe; they would otherwise simply lie about their efforts. But the MK/M will always sabotage, either knowingly but without understanding why, typically then rationalizing it internally, or unknowingly even to themselves, when executing a programmed function in an alternate personality called forward for the purpose. Fortunately, the number of MK/Ms is relatively low, but sadly, such victims are the hardest of all to help for this reason.
Subtle sabotage is something all kinds of TIs themselves can be unaware of doing. They simply will fail to follow the instructions correctly, or be clumsy when performing the defensive advice such that the enemy will perceive it, and take steps to avoid the effort’s intended goals. That is especially common in the De facto fakes, and those based on mental issues, serious or otherwise. But any TI can sabotage their own efforts this way, as we shall shortly see.
That means that ANY TI can ‘be fake,’ unto themselves and to their cause, and not even know it.
For twenty years, I have wondered why so many TIs seemed so prone to self sabotage, the most common evidence of it being the constant excuses as to why they would not even try a given advice. Usually, it would be claimed it had already been tried, by them, or by someone else. Even when I point out that it must be done correctly (and I give very explicit instruction) and why it can fail if not done just that way, they will continue to resist the advice. Excuses, excuses, excuses.
Come forward in time
 The one thing which has proven to completely resolve targeting is the concept which lays behind the Free Will Society and its project, Free Will Haven. This has been widely promoted among the TI community, but to what end? The concept has been tried in a couple of ways (‘beta testing’), and provided proof that it works extremely well:
The one thing which has proven to completely resolve targeting is the concept which lays behind the Free Will Society and its project, Free Will Haven. This has been widely promoted among the TI community, but to what end? The concept has been tried in a couple of ways (‘beta testing’), and provided proof that it works extremely well:
three TIs have enjoyed a total of some 3,000 continuous targeting free days.
And yet, the primary beta site failed through self sabotage. The principal character involved was a female TI of long suffering. Because she was investing her own money into the project, she was given complete autonomy and control of the effort. Despite specific advice on property selection and how to qualify TIs as co residents, as we had initially agreed, she elected to do things her own way, after all. She even refused my participation in ways which led to a break in communications, about half way through the effort.
In the end, as result, she ended up trying at least four different locations before achieving any level of success. And, unfortunately, by rejecting advice and possible other forms of self sabotage, she made blunders which lead to being evicted from the location. One such blunder was not asking for additional financial help from the Society, because she had forced the break in communications, not just with me, but with the Society members who had earlier provided financial support. Pride and stubbornness is presumed; a form of self sabotage. To this day, she has not responded to outreach. Worse, she continues to work to try yet again, essentially working against the Society’s efforts.
The other important fact that is news which relates to self sabotage, is that the Society was at one point on the threshold of obtaining significant funding towards realization of this dream solution in a way that can help dozens to hundreds of TIs obtain total escape from their targeting. It also would serve as a gateway to even more important goals, such as actually exposing and proving targeting is real, pervasive, and government sponsored, leading to actual successful lawsuits, media and government investigations, and termination of programs with perps and others behind them being jailed.
The stakes could not possibly be any higher for the TI community.
With the help of ATN World News, and a pooling of contacts outside of the TI community, we were well poised for significant investment into the Free Will Haven project through the Society. Millions of dollars worth, in fact: enough to buy land, homes and central services, vehicles, and even to fund relocation of participating TIs, and provide monthly income to some of them. It might even have funded mobile strike teams of TSCM and PI professionals who can covertly investigate, document, and prove targeting cases valid in courts of law and before media.
How much more help than that, can we ask?
And yet, the fake TI rears its ugly head, threatening it all
Before anyone will risk investing millions of dollars into the Free Will Society (and we are finally very well poised to create just that scenario), they will need to see that the TI community is sincere and valid, that it has a serious stakeholder position in seeking a cure. Who would give a bum a hand out of $1,000 without some sign they would use the money to escape being a bum? The only way TIs as stakeholders can be judged worthy is if the TI community unites to some useful degree behind the project, expressed both in terms of membership in the Society, and some level of self-booting financial commitment.
 There would seem to be some 300,000 aggregate count ‘members’ in Facebook Groups which relate to targeting issues. There are so many groups that I would not wish to attempt counting them. Frankly, there are too many such groups, and some of them appear to be run by fake TIs of the worst kinds. Be that as it may, ‘members’ in single quotes is used because the typical member of one group tends to also be member of 3-5 other groups, or more. So while that negates the 300,000 figure, it still means that there are many tens of thousands of TIs in the Facebook community. I’m thinking around 70,000 specific individuals.
There would seem to be some 300,000 aggregate count ‘members’ in Facebook Groups which relate to targeting issues. There are so many groups that I would not wish to attempt counting them. Frankly, there are too many such groups, and some of them appear to be run by fake TIs of the worst kinds. Be that as it may, ‘members’ in single quotes is used because the typical member of one group tends to also be member of 3-5 other groups, or more. So while that negates the 300,000 figure, it still means that there are many tens of thousands of TIs in the Facebook community. I’m thinking around 70,000 specific individuals.
I and the Free Will Society has repeatedly reached out to virtually every one of these groups. And yet, the Fake TIs have made themselves known by their response, which is that form of subtle self sabotage and refusal to help themselves… the hidden commonality. The Society should have by now many hundreds of Members, perhaps into the thousands. It should have, by now, accumulated at least several to tens of thousands of dollars in contributions toward its proven viable goals. Failed organizations such as FFCHS have previously exceeded these kinds of member and donation numbers several times over, and for fraudulent and/or foolish causes in some cases.
Yet at best, we have had some 40 Members, almost all of whom balked at modest $25 annual dues. At best, we have raised a total of less than $2K in contributions and membership fees. The bulk of that has been because I and one other author have donated 100% of the sales of our ebooks (not the profit, the actual sale price) to the Society. I remind you that I have essentially been homeless for the last three and going on four years, though I now at least have a place to affordably park my Mobile Home — and yet I still made those donations.
What have YOU done? Click ‘like?’ Or is your devotion to your cause so strong that you dared to click ‘share?’ SHAME!
I must conclude that if those are the limits of your action, you are not a genuine TI, but a fake. If you won’t lift a finger to help yourself by helping to establish a stakeholder position suitable to a large investor’s need, then we never will attain the funding needed to realize the effort. Your apathy and lack of participation betrays your own cause as fake. No one else. Not the perps. YOU!
You belie your claims of targeting and your disdain for it, rendering it a moot footnote in terms of importance and validity. If you will not take action to support something proven to work, you have both sabotaged your own best interests, and deliberately refused to help yourself, and you fail to actually be part of the community, supporting the community.
Example: I recently posted on my main FB feed a simple post underscoring much of what this article describes in simpler terms. It was a call to action which specifically chastised simply clicking ‘like’ or ‘share,’ instead of actually doing something. Out of some 3,000 FB friends, there are several hundred who are TIs. What do you suppose the response was?
[[ One like, and one share. ]]
What other reason can there be for that kind of inaction? YOUR inaction? Prove me wrong in my conclusions, or take action, now, TODAY. Here are six simple things a real TI with a serious intent on winning the war would proactively do, given the above facts:
- Join the Free Will Society (.wordpress.com);
- Use the promotional tools provided by the Society to spread the word;
- Donate to the cause (gofundme);
- Yes, LIKE and SHARE things which promote the Society and the project;
- Directly reach out to fellow TIs as individuals and engage in two-way dialog to convince them to do the same six things (evangelize our cause). You will then know who is fake, or not, yourself, experiencing them first hand, as do I;
- Stop doing those things which aid in your targeting.
Unless you do these things, then I must conclude that so many of you are fake, that there is no point whatsoever in attempting to help anyone. And boy, will that make my life a lot easier. And then, you can go back to complaining about how bad things are, and liking and sharing similar miseries posted by others.
I, the Free Will Society, and the future residents of Free Will Haven await your decision. I’ve attempted everything I can think of. Now it is up to you.
One final note: it would seem that the fakes have been using Facebook’s complaint feature to cause facebook to ban me from posting to the TI groups. Anyone who has ever read any of my TI group posts knows that there is nothing in them which approaches any definition of ‘offensiveness’. So, as I can no longer post to such groups, this to, is now up to you. The damage has been done, and now only you can undo it.
YOU are what you’ve been waiting for!
…and I’m no longer interested in trying to help those who won’t help themselves.
Your future, and the future of the Society is in your hands.
Why TIs are Often Targeted by Police
Rare is it that a given Targeted Individual won’t have reason to believe Police are involved in their targeting. And yet, they were not… not officially. Here’s the why and how of it…
by H. Michael Sweeney proparanoid.wordpress.com Facebook >>better at>> MeWe
copyright © 2018, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.
Color of Law; Police abuse of power in personal agenda
In the two decades of working with thousands of organized stalking victims and victims of other forms of targeting, the single-most common complaint is the suspicion or outright experiential evidence that multiple Police Officers are complicit in the affair. If not the Police, then some other law enforcement or intelligence agency… or both. Indeed, this has been my own experience in two of three different episodes of personal targeting over a 15 year period. In fact, multiple agencies can be involved simultaneously; Ive gone up against as many as five LEA, plus FBI and CIA assets, bounty hunters, and military intelligence in a single targeting. This has been documented in my various books showing how I beat them in the end… but it was no cake walk.
 This is a problem for more than the obvious reasons. The most obvious is, that the very authority who should be responsible for investigating and protecting against such crimes, cannot be trusted by the TI to help anyone but the perps behind the affair. Calling Police for help is almost always like asking a burglar to help you secure your home. Secondly, when officials of any kind are complicit, the victim is then entered into the official record as being mentally ill, or in a worst-case scenario, guilty of some convenient crime. Even when not complicit, going to Police about targeting is likely to have the same result; they simply do not want to believe in the Boogeyman, and see anyone who does as a mental case. In fact, stalking is designed to get you to go to the Cops for just that reason; they want it on record that you are mentally unstable. DON’T DO IT.
This is a problem for more than the obvious reasons. The most obvious is, that the very authority who should be responsible for investigating and protecting against such crimes, cannot be trusted by the TI to help anyone but the perps behind the affair. Calling Police for help is almost always like asking a burglar to help you secure your home. Secondly, when officials of any kind are complicit, the victim is then entered into the official record as being mentally ill, or in a worst-case scenario, guilty of some convenient crime. Even when not complicit, going to Police about targeting is likely to have the same result; they simply do not want to believe in the Boogeyman, and see anyone who does as a mental case. In fact, stalking is designed to get you to go to the Cops for just that reason; they want it on record that you are mentally unstable. DON’T DO IT.
But there is a DO list! Do video and log all interaction with LEA or have a witness from whom you can get a written statement immediately after. It will help keep Police somewhat confined in their actions against you. The more you collect such material, the less likely are they to risk any useful action against you; you can illustrate a pattern of harassment. Do make copies and hide them well, off site. Tips in my first book, The Professional Paranoid on all of this.
The worst example of the problem from my client situations was a Navajo Indian, an ex Green Beret, who was targeted after his daughter was kidnapped by a Satanic Cult with all the earmarks of a CIA mind control operation. Within weeks of going to authorities to seek help, all manner of problems beset him. Traditional surveillance and stalking, and electronic targeting, to include V2S was the least of it. When he began using my advice and his military skills to determine the players and go after them aggressively, it took a turn for the worse: suddenly, his mortgage was six months in arrears and his house was being foreclosed, all his credit cards were maxed out and past due, his bank accounts emptied, and there were outstanding warrants on him for assault with a deadly weapon and skipping out on bail. He was, in fact, declared ‘armed and dangerous’ with an all points out on him. This was all done by back-door computer manipulation of data files by professionals of CIA caliber.
He took additional advice from me and then went underground to organize with other ex military buddies and Navjo friends, and went black in order to wage an unseen war against the enemy. As I never heard from him, again, I must presume he failed in the effort, or was successful to the point of having broken enough laws that he needed to remain underground. I had, in fact, advised him not to contact me for such cause. But, as I have said, these are merely the obvious problems with this particular aspect of targeting.
The other shoe that usually falls…
Perhaps the second-most common awareness about stalkers is that they seem to regularly consist of a lot of Masonic types. This is often determined when getting a good close look at them or their vehicles; the Masonic emblem, or some similar fraternal order emblem, is found in evidence. Usually, it is either a sticker on a car window, a pin on clothing, or a ring on a finger. I myself have seen this in my own targeting, the one incident where true gang stalking was involved (as opposed conventional targeting with general surveillance and dirty tricks).
After guesting for four hours on Coast to Coast with George Noory to talk, in part, about my new book, MC Realities, I ran into the Masons almost overnight. I had mentioned on air the involvement of the fraternal organizations in gang stalking, and how they had evolved from the Knights Templar and their exposure to the satanic Hashemites and Assassins of the Middle East during the Crusades. On air, of course, I gave my name as H. Michael Sweeney, my ‘pen name.’
Two days later, I was at work where I was managing a gas station while investigating the Oil Industry, infiltration style. It would result in two forms of targeting, the first of which was by the Masons, that second day. A man bought gas and elected to come into the office to pay, where I was at the time. He waited until I was the only one present, and then offered to pay, holding out his fist, palm down. It was only a couple of dollars in gas, so I assumed it was a handful of change. Wrong; it was a message to be delivered.
NOTE: the second was targeting of the Station itself by a terror cell, of which one of the participants recognized by me as a helper to two of FBI’s Top Ten Most Wanted and two other Islamics… and FBI agent who had been earlier involved in the my own targeting as earlier described. It was, in point of fact, to be yet another False Flag operation, later described by President Bush as Gas Station Tasking… which I thwarted. Arguably, the two targeting incidents might be seen as related, but even if so, it is unimportant, except for the fact that it illustrates that one almost never quite knows for sure why one is targeted, and who really lays behind it. This is described in my wordpress home page, if you wish to learn more.
Placing my hand beneath his, he opened it, and instead of coins, a money clip fell into my hand with a wad of Hundreds. “Take what you need, Mr. Sweeney,” he said. My name tag simply said “Harry.” He had a very wry, knowing look on his face, which slowly turned into a smirk as I manipulated the money clip to retrieve a single bill. In doing that, I discovered a gold and jeweled Masonic emblem on the other side of the custom-made silver clip. A broad grin overtook his face, to the point of becoming silly.
 “Interesting how some thing have more than one meaning,” he said, as I returned the clip and fetched his change. That day, when going home, There were three of them outside of my Condo, and several cars with Masonic emblems in our parking area, none of which had ever been seen before. I ended that stalking by using the methods in MC Realities, methods that many Tis would be unable to employ unless doing so upon first targeting, as had been my situation. Once targeting has been ongoing for some time, the typical TI no longer has access to the needed resources for such a defense. The one remaining defense is found in an earlier post.
“Interesting how some thing have more than one meaning,” he said, as I returned the clip and fetched his change. That day, when going home, There were three of them outside of my Condo, and several cars with Masonic emblems in our parking area, none of which had ever been seen before. I ended that stalking by using the methods in MC Realities, methods that many Tis would be unable to employ unless doing so upon first targeting, as had been my situation. Once targeting has been ongoing for some time, the typical TI no longer has access to the needed resources for such a defense. The one remaining defense is found in an earlier post.
In MC Realities, I trace the evolution of Mind Control technology (Political Control Technology) from the time of Adam and Eve (the Serpent’s deception was the earliest form of controlling thought… the same version of it as we see today in media manipulation), forward. The Templars, after being ordered destroyed by the Pope for having discovered their Satanic practices acquired in the Middle East, went into hiding. In time, many of them hid within the Stone Masons Guild, and eventually, took it over to form the Freemasons as we know them, today.
Hedging their bets, should they be found out a second time, they formed splinter fraternal organizations, as well. Any group with any of these words in its title… Fraternal, Ancient, Order, Ordo, Lodge, Temple, Grand, Sacred, Rite, or Knights (and similar)… is very, very likely a fraternal organization with a Masonic organizational construct… and at the higher levels, at least, closely affiliated with the Freemasons if and when it becomes convenient to the parent group. Therefore, it is easy to involve small armies of ‘helpers’ if someone is deemed a target. It is important, however, to understand that the rank and file lodge Member who may be induced to participate, has zero true knowledge of you or the purpose of the targeting; they are simply ‘helping a friend’ to solve ‘a problem.’
I end this section with a simple note: all Masonic systems are quite steeped in ancient mysteries of the Middle East, and beyond, typically focusing on Egypt, Syria, and the Holy Land… with a touch of the Sub Continent (India, Nepal, etc.) and Far East.
The two shoe laces are tied together…
 This is where it gets interesting. Most big city Police are encouraged to join the Fraternal Order of Police (FOP), and it is indeed Masonic in structure. FOP, for instance, employs the Masonic all-seeing eye of Egyptian fame in their logo, which is a five-pointed star with a circle bisecting the points to create five triangles shaped like the Compass of the Masonic emblem, also the shape of the ancient steeply-angled Egyptian Burial (pyramidal) obelisk used for commoners’ crypts. There was additional heraldry-like art akin to European styling in the center of the star, shapes quite like those of most Police Badges, and incorporating an Eagle and other symbols. In other words, Police departments not only adopted the Lodge system almost universally, but did so to the point that their badges reflected elements of the FOP emblem. Almost all Police badge shapes generally post dated the FOP affiliations, underscoring the link. The exception would be Sheriff stars, and yet, that shape is also of ancient Masonic importance, in both the upright and upside-down (satanic Baphomet) versions.
This is where it gets interesting. Most big city Police are encouraged to join the Fraternal Order of Police (FOP), and it is indeed Masonic in structure. FOP, for instance, employs the Masonic all-seeing eye of Egyptian fame in their logo, which is a five-pointed star with a circle bisecting the points to create five triangles shaped like the Compass of the Masonic emblem, also the shape of the ancient steeply-angled Egyptian Burial (pyramidal) obelisk used for commoners’ crypts. There was additional heraldry-like art akin to European styling in the center of the star, shapes quite like those of most Police Badges, and incorporating an Eagle and other symbols. In other words, Police departments not only adopted the Lodge system almost universally, but did so to the point that their badges reflected elements of the FOP emblem. Almost all Police badge shapes generally post dated the FOP affiliations, underscoring the link. The exception would be Sheriff stars, and yet, that shape is also of ancient Masonic importance, in both the upright and upside-down (satanic Baphomet) versions.
If that were not enough to convince you, let us take a look at the Police Department of New Orleans. New Orleans existed as a city at the time of the Louisiana Purchase from France, in 1803. The first Masonic Lodge (a French version), was established there in 1793, all its members speaking French, and some Spanish, but no English of note. All the better to remain secret and mysterious to Americans, when they came into possession. But to fully appreciate New Orleans in the equation, we have to first look to New York.
In 1915, the Fraternal Order of Police established their first Lodge, there. It spread from there to many other cities in very short order. The FOP was not intended just to be a Lodge system, however; it also took on aspects of Unionization, a kind of bargaining force with the City whenever Members felt that Cops were not getting a fair deal from the Mayor. In many cases, in fact, their bargaining strength was augmented by the power of the greater Masonic power structure, a formidable force at the time.
Over time, actual unionization was also achieved in almost every major city, usually through the Mob’s control of the AFL-CIO, making it easier to arrange for hijacking of intrastate trucking or of dock cargo without anyone ever being sent to prison. But that’s another story. Ask any retired Union trucker or stevedore from Jersey. I’ve heard the same from 1975 Oregon members. The importance of that will explain to some Tis, those who believe they were targeted because they reported illicit drug operations or crimes which might be related to Unions, are targeted by Police. Additionally, of course, CIA sanctioned drug operations are protected by Police, as well. Thieves in bed with thieves, the bed made by the thieves.
Though New Orleans under the French had a Police Department as early as 1796, it had no Police Department for rather a long period of time after it raised the American flag. It was instead ‘policed’ by a vigilante system until 1853, when they formed their first ‘American’ Police Department. Almost immediately, they adopted the ancient Cresent and Star (upside down, larger star) as is common to Islam, as their badge. It is still in use, today, and appears on their cars, as well. Well before the FOP had even existed, this Department was already incorporating Masonic symbology directly in its badge. This is better known as the Shriner’s symbol, today… the Shriners being a Masonic fraternal lodge system.

So, clearly, the Masonic influence and ties are present within most Police Departments. Cops form some of the strongest bonds between individuals in service outside of the Military, sufficiently strong, in fact, that if one of them asks a color-of-law favor of another, it is not likely to be turned down, and certainly unlikely to be exposed even if turned down. Therefore, it really only takes one Cop being approached from a fellow Lodge member to recruit several more for any needed aid, even if that request came from a lodge in another city. Ergo, escape to another city tends to never result in escape from targeting.
NOTE: That is why the Free Will Society exists; a solution to virtually all forms of targeting. Please join and support (donate/promote) our effort to create a targeting free intentional community of our own, and our other advanced programs planned for the future. If you are reading this, you should immediately join the Society and give it full support. It is a far more valuable TI resource in terms of programs and goals than any of the so-called ‘TI groups’ out there, today, the bulk of which are nothing more than information and disinformation mills.
Please: you owe it to yourself to visit freewillsociety.wordpress.com to learn more.
Three shoes?
Yes, there is a third shoe, one of special interest to those who feel the intelligence community lays behind their targeting. Every major Police Department in America has in place assets loyal to the Central Intelligence Agency, and many Officers have military intelligence backgrounds. Usually, you can count on some of them holding key positions within a given city: the Chief, the Public Relations Officer or Spokesperson, the head of Internal Affairs, the head of the Swat Team, and/or the Head of Personnel. From these posts, especially through IA, they are able to find bad cops who can be blackmailed into playing ball on an on-call basis, for any kind of dirty deed, to include color-of-law abuses such as is common to targeting. Don’t forget CIA drug running operations.
If that were not enough, there are similar, but far looser ties with FBI, Homeland Security, and the US Military Intelligence Agencies (and in some case, others, including the United Nations, and even Mossad). These generally entail the network of Fusion Centers and Centers for Excellence*, and special programs such as Community Policing and the Strong Cities Initiative/Network. When you consider that most all of these agencies use computer software based on CIA’s PROMIS data base management system, which is nothing more than a data base engine with a back door built in… almost any form of hanky-panky is possible. Ergo, the Navajo Beret Syndrome.
* Search for ‘Centers for Excellence + Homeland’ to see why I include it, here. All these items work together to collect, evaluate, and share information on (persons of interest). They operate as one big networked spy tool with usefulness in organized stalking which can easily be misused by anyone within LEA who has access.
So, even if Masons are not involved at all, Police can still be brought to bear on any given TI with the same level of efficiency, and in fact, the FOP can be leveraged into the equation just as easily, in reverse manner. Will the average member of the FOP, the Masons, the Police, or any of that long list of Agencies be aware of any of this? Absolutely not… not unless they are higher on the food chain. Then, of course, they won’t be admitting it, either. Complaining about it gains nothing. Knowing about it, and understanding it, can mean a lot, however.
You may not be able to beat it, but when the mystery is gone, its just another damned nuisance to deal with, and another reason to avoid trying to rely upon Police for help, unless you know one you have great respect and trust in. I was lucky. I had a relative who was a Cop in an uninvolved LEA, and he was able to help off the record in very useful ways. I also had help from ex FBI friends with back channel access, of like value.
We can’t all be so lucky. And if you are a TI, you know luck is not your strong suit.
Media’s Latest Conspiracy to Troll You on the Web
Fake news, tracking and targeting, subliminal messaging, repetition, distraction, and psychological manipulations by Trolls and Bots are not the only weapons they use to dumb you down and pump you up with their version of truth. Vanishing is their latest trick.
by H. Michael Sweeney proparanoid.wordpress.com Facebook MeWe proparanoid.net
copyright © 2017, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.
The (fake) news media dilemma
Fake news and Web tracking and targeting, subliminal messaging, repetition, distraction, and psychological manipulations are not the only weapons they use to dumb you down and pump you up with their version of truth. It is not just Trolls and Bots we have to worry about, now. Vanishing is the latest trick used to conceal the truth and promote the lies.

Image analyzing How Media Dumbs you Down with clever tricks (see link)
I’ve written before about how television mainstream dumbs you down with clever psychologically aimed technical tricks in the actual image… largely relating their use of subliminal messaging, deliberate distraction, and overload. The general purpose being to further reduce the actual news you walk away with to the simplest of boiled-down sound bites… just the ones with their take on the news shaped for you according to whatever bias the network has at management level.
Elsewhere, there have been excellent examples of the use of NLP (Neuro-Linguistic Programming), also employed by broadcast media. It involves careful wording as well as clever body language to project the intended viewer/listener response to the message, within the message delivery, itself. It has been shown to be so powerful, a well trained user (a stage magician and hypnotist, who must rely on such deceits), was able to deliberately speed past a Cop and then use NLP to leave the traffic stop without the Officer even remembering why he had stopped him in the first place.
That kind of mis and disinformation borders on mind control, and in fact relies on mind control technology, psychological methodologies, and MC research by the likes of the Central Intelligence Agency. When the great bulk of media is controlled by fewer and fewer mega corps, and their corporate leaders tend to be like-minded politically, you get the double whammy of biased news and fake news (propaganda). That’s bad enough, but this article is about another dirty little trick… a bag of them, actually, used by all forms of Media when presenting ‘news’ online.
 And, of course, we still apparently still have to contend with CIA’s Operation Mockingbird, the installation of CIA operatives within the media industry to help shape news to their preferred version. That, too, is something I’ve written about, at least in terms of its origins and history, and I’ve even been referenced as a resource in a more ‘official’ industry review of that topic by The Reporter’s Committee for Freedom of the Press. But now, we see, actual ‘retired’ ‘once-a company man, always a company man’ CIA officials are becoming investors in and on-camera commentators in mainstream news. This Clyde Lewis Ground Zero episode reveals how serious a threat the placement of intelligence community actors in media actually is.
And, of course, we still apparently still have to contend with CIA’s Operation Mockingbird, the installation of CIA operatives within the media industry to help shape news to their preferred version. That, too, is something I’ve written about, at least in terms of its origins and history, and I’ve even been referenced as a resource in a more ‘official’ industry review of that topic by The Reporter’s Committee for Freedom of the Press. But now, we see, actual ‘retired’ ‘once-a company man, always a company man’ CIA officials are becoming investors in and on-camera commentators in mainstream news. This Clyde Lewis Ground Zero episode reveals how serious a threat the placement of intelligence community actors in media actually is.
What News is supposed to look like
All news is supposed to contain the 5 Ws… Who, What, When, Where, and hoW. Ideally, we also need to know the S and M… the news Source and the Meaningfulness, often defined by Motive… the Why. That is supposed to be factual Motive, and not speculation, unless clearly presented as speculative commentary. Lately, that’s the greatest sin Media is guilty of; too much ‘news,’ today, is actually mere commentary… the propaganda version.
Generally, for some strange reason, it is also rare to get all those points, especially online. The most critical things useful for research tend to be left out, making it hard for pundits and anyone trying to chase down answers to hard questions because a given story fails to ‘compute.’ That is critical, if one is to find out more, and judge for one’s self what is true, and what is fake. This is particularly distressing when the potential for a conspiracy or cover up is apparent. While Sheeple don’t even see the glaring holes in the official story, people who think for themselves really want to know why those holes exist.
But we ‘conspiracy theorists’ and politically aware non sheeple are thwarted at almost every turn. Take for instance, the WHEN. It is extremely rare in online news reports to find out exactly when an event took place… esp. useful to insure the same news event you find is the one you wanted, because often, you might have two identical sounding stories in the same city, in different time frames. Most searches are best made by searching on the (event key details) plus the year, and perhaps, month.
But many reports do not cite the year, at all. The Web is smart, though, and it knows when a given URL was created. Unfortunately, many of the larger online news sources use a kind of ‘feeder board’ URL created way back when, which is updated with current news, only, older news dropping off. While the Web remembers what the page looks like when the story you are looking for took place… that story is no longer there when you go to find it. While you can search the archives if they bother to offer one, and PERHAPS find it, that is just one hurdle in the search.
Once you do have what seems to be a correct story’s article, it is amazing how many news reports fail to include the date in the byline at the top of the page. So you have no way to know when the person writing sat down to write the story. But even with a byline date, you still have a problem: is that date the date the news took place, the date they wrote the story, or the date it was posted? It can be any of the three.
Some stories are updates to older stories, so the byline is meaningless unless the story itself indicates the actual When it took place in the text. THEY SELDOM DO. Instead, they just say something like ‘Last Tuesday.’ Great. What day of the week is the date of the byline? Now I have to go search that out, to make certain of the When. Your average Sheeple is not going to bother.
This problem also exists elsewhere in the remaining Ws and the S and M. At least one such detail is usually omitted, and all-too often, several. Sometimes, it is something simply not yet learned by reporters, but too often, it is clearly just not deemed important. All too many bylines even fail to tell you who wrote the story… so you can’t email them and ask for missing information. EVERY print article in a newspaper tells you this information, but for some reason, the online version seldom does.
Message distortion when relayed through many people
Dumbing down online is easy. It relies on the known scientific problem which transpires when a series of people relay a message from one to another to another, etc. It used to be in schools, that one of the first things they taught was this concept… that you you have to take care when relaying information. You have to listen carefully, and then just as carefully repeat it. The problem is, each person decides what is important enough to be carefully repeated, and tends to reword it for ‘simplification.’ So the message first stated has little resemblance to the message last heard. THAT is not being careful, it’s being careless.
Online, information deemed worth sharing is constantly relayed in social media in a quite similar, but an even more careless manner. Each person in the chain tends to introduce it with their own spin or commentary, advising what they think the takeaway is, or should be. They then (hopefully) provide the URL to the original (the careful part). They might also create or add an image or meme which underscores their takeaway thought. That is all in good, but…
 Sheeple don’t bother to click on the URL and read the original story, and they simply ‘learn’ the takeaway point of the previous poster. This is why Memes can often be dangerous. Especially when the creator is being deceitful or dishonest to the truth. They know that a false message repeated some 20 times will take root in the average Sheeple’s mind, and become adopted. That is especially important in political messages, because today’s social media is decidedly biased, and decidedly deceitful, even to the point of using paid trolls and automated bots to insure you are inundated with the preferred take aways.
Sheeple don’t bother to click on the URL and read the original story, and they simply ‘learn’ the takeaway point of the previous poster. This is why Memes can often be dangerous. Especially when the creator is being deceitful or dishonest to the truth. They know that a false message repeated some 20 times will take root in the average Sheeple’s mind, and become adopted. That is especially important in political messages, because today’s social media is decidedly biased, and decidedly deceitful, even to the point of using paid trolls and automated bots to insure you are inundated with the preferred take aways.
This is why people who think for themselves always click the link or do a little extra search before they hit the SHARE button, and add their own takeaway. Is that you? Are you like me, spending roughly 50% of your time inspecting and then correcting other people’s wrong take aways and falsehoods? Or, are you part of the problem, simply passing it along? Baa… baa…
But there is a bigger problem, one which at least seems conspiratorial, and relies on the above Sheeple foibles and the omission of Ws, etc. For some reason, mainstream news sources seem to be deliberately making it difficult for you to access news, and difficult to relay, on your own; they would prefer to leave that to the professional trolls and bots you think are your online friends.
Something is very wrong with this picture. Lets take print media and look at how they operate outside the Web, and compare that to how they are now starting to operate on the Web.
A newspaper runs advertising to pay for their staff and overhead; it keeps the doors open, and allows them to grow and invest in special investigative projects. They charge for subscriptions and for individual copies at news stands based on the cost of the printing and distribution process, and materials; the ink and paper. That’s why newspapers are relatively inexpensive to buy. It used to be that the online version, therefore, just had advertising… there is essentially no comparative cost to put it out there and for you to access it.
But now, online, many newspapers, even small local ones, are telling you that you will need to subscribe or become a registered user to their online version, or pay a small fee to read the article… or that you may read this one, but it may be the last one you can read for free (relies on your cookies, but if you turn them off, you they will tell you to turn them on to see the material). Of course, once you do any of that, you’ve just sold yourself into another dozen marketing lists, without warning or compensation. But that’s not all.

Suddenly, many media outlets online (radio, networks, print) are using something called Cloudflare. That product is a kind of ‘protection’ against certain abuses… a bit like an anti hacking or virus bot. But it does something else, as well. It also prevents anyone from copying and pasting a URL into a social media post. WHY? In the past, getting your URL spread about was a good thing; it brought them more viewers, which increased the value of the advertising opportunity for their Web pages. When did they decide they didn’t want more readers, and why?

Where the Conspiracy comes in
Sure. You can call this answer a theory; a conspiracy theory. That is what it is, plain enough. The only way the above sins can be excused as desirable is if somewhere, someone important and powerful within media and in political realms, decided that it was advantageous to dumb you down, and limit your ability to rely on URLs to relay facts and correct people when in error. It is an insurance policy to protect the ‘integrity’ of the versions being spread by the trolls and bots.
I mean, when your read some crap someone has posted which is to your understanding just that, a lie or false belief, you should be able to go find a news article or other authoritative source online, copy the URL, and paste it into your reply to prove your case. When you are trying to educate someone on how you feel about something, you should be able to do much the same, to prepare your post or meme… have a supporting factual link to go with it.
Someone does not want you doing that. They want you to hear something said 20 times and accept it as truth, with no way to verify it, or refute it, if false. There is only one person in the media industry who fits the bill. If you are a Sheeple, you will recognize his name but not realize just how powerful in media he is, or in political realms, and how deceitful he is. I am speaking of George Soros.
It is that simple. When most of us rely on TV news, we only get one slant (liberal, usually, conservative if you go out of your way). Because of TV’s own special dumbing down tricks as earlier referenced, you will walk away with a very encapsulated message with is has no actual understanding associated with it. Then, when someone puts their slant on it and you get hit with that 20 times, it becomes your slant, and people like me and others who prefer to think for ourselves, are increasingly finding it difficult to correct any errors.
Worse, if you do think for yourself, you may not be able to learn what you need to make an informed decision, up front. Heaven help you if you are trying to investigate what seems like a conspiracy theory, because of glaring holes in the official story. Obscuring the true story seems to be the way of things, today, so just ‘move along, folks.. nothing to see, here.’
 When you add all this to what is taking place in the public school system and in higher education (liberal indoctrination), your children will think this is the way it is supposed to be, and whomever is in power when they are adults will be able to do and get away with whatever they want. They will dictate to them what to believe, and it will be believed. The notion of thinking for themselves, and of distrusting and challenging government will be foreign concepts. They might as well be called the 20x Generation.
When you add all this to what is taking place in the public school system and in higher education (liberal indoctrination), your children will think this is the way it is supposed to be, and whomever is in power when they are adults will be able to do and get away with whatever they want. They will dictate to them what to believe, and it will be believed. The notion of thinking for themselves, and of distrusting and challenging government will be foreign concepts. They might as well be called the 20x Generation.
The ’Snowflakes’ on the left are already a part of that group, unwilling to listen to facts or reason, and repeating what they are told to believe. I, for one, am not willing to pass the reigns of our nation’s future over to them, in their current state of mind. I’d rather have an armed revolution, if that is what it takes, to end their madness for them. Constant outrage based on lies serves no one’s best interest, except at the top of the food chain.
So my last question for you is this: do you want to be a Sheeple morsel for Wolves like Soros and his elite political friends, people more interested in Globalism than what is right and moral? Or do you want to be a think-for-yourself consumer of actual news you can easily access, rely upon, and use when talking to others about things which matter to you?
If the later, you had better start complaining to media, and to politicians about it. You might even want to consider taking legal action or starting an initiative ballot, if your State has that option, to write laws forcing journalists to adhere to journalistic standards and to make their stories available more appropriately. You certainly ought not simply be sharing what is being fed you currently without verifying for yourself it is the truth.
Else we all become 20xers… or we have that revolution, the least desirable of options.
U.S.P.S. “Informed Delivery” Potential Threat to Everyone, Esp. Stalking Victims
Thanks to the Post Office, now anyone can know what’s in your mailbox, automatically… including of course, anyone in an alphabet agency. It is just another way to track you and criminalize you if deemed convenient, in time.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2017, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.
“Informed Delivery?”
 The idea is you register online with USPS for the FREE notification subscription service, and they then photograph the mail to be delivered to you each day, and email the images to you before delivery; that way, you know if something is stolen or lost and NOT in the delivery, and can plan on getting expected items. It is tied to other services, as well, such as package notifications, tracking services, stamp purchases, etc.
The idea is you register online with USPS for the FREE notification subscription service, and they then photograph the mail to be delivered to you each day, and email the images to you before delivery; that way, you know if something is stolen or lost and NOT in the delivery, and can plan on getting expected items. It is tied to other services, as well, such as package notifications, tracking services, stamp purchases, etc.
1) This is the federal government we are talking about. The FBI, CIA, and a host of other alphabeticals would have no trouble whatsoever accessing this information. There is no indication that such information is not retained indefinitely, and no privacy statement which alleviates concerns over it being used against you down the road should you become a person of interest, or a trouble maker such as a whistleblower, activist, or other targeted individual.
2) The system is achieved with online registry, and is handled by email, currently with no truly secure process for verification of the applicant or notification of the addressee that a subscription has taken place. Stalkers, private investigators, suspicious spouses or ex spouses or lovers with an axe to grind, or anyone else with minimalist information about you and where you live could sign up pretending to be you… again to include someone working for a government agency who could not be bothered with a warrant — knowing that they could later get a warrant and legally go back in time to ‘duplicate’ the effort in a manner which leaves no proof they violated your rights, earlier.
3) this means that mail must be separately sorted one more time by someone into individual stacks to ‘pose’ for the photograph, and then to take the image and email it… or the entire automated system must significantly modified at both the hardware and software level. Both are at great expense and will cost USPS more red ink… and eventually that cost will increase the price of postage for everyone, not just those using the service.
4) If the system is automated (and even a manual system will be, eventually), then it means EVERYONE’S MAIL is being imaged, all the time: The USPS becomes yet one more information tracking and tracing point available to the government, and under the program, anyone spoofing it.
I’m not the only one pointing these things out… though I’m the only one so far who has pointed out 3 & 4. Other privacy experts have echoed 1 & 2, variously, mostly item 2. Too many people PRESUME that government would NEVER use such a service to spy on them this way. That’s what they said about NSA and FBI when they first started.
Defensive Measure?
It appears the only way to prevent anyone to spoof the system to spy on your mail is to beat them to the punch and register, yourself. However, there is no assurance in place that someone could not still additionally register an alternate email identity. We can only hope and presume there is an online software check which would reject any such attempt.
Short of not taking mail, at all, there is no defense against government use of the images, if you are a person of interest targeted in someway by an agency.
Risks in 12 Step Programs, esp. for TIs
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2017, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.12 Step Origins

Technically, there is a 13th step, one early in the program; the assigning of a help mate, intending that you each help one another to stay on the narrow path, since ‘you can’t do it on your own.’





Templars Masons Theosophy Rothchilds
The 1 step solution is also useful in targeting issues
- The sermon uses the topic of powers and principalities of ancient times to frame the lesson… and both addiction/abuse and targeting are born of powers and principalities, as is all sin…
- An addict/abuser ‘worships’ their particular sin of consequence…
- A TI ‘worships’ (by constant worried attention) their targeting issues of consequence (equating to sin)…
- Bending the knee to Assyria in the sermon equates to giving in to sin…
- So (the Pharaoh of Egypt) equates to you (your flesh, the Old Man) and your inadequate will power to resist sin…
- Which in turn equates to buying into the enemy’s (sin) Press Releases (that they cannot be resisted) wholeheartedly, accepting the belief the enemy cannot be overcome, by or of ourselves…
- If you listen carefully, you will hear echoes of 12-step program dialogs! They simply borrow the truth and apply it in their own way… and with respect to targeting, twist it to meet their own ends.
- TI Defense: 30 Tips to Help Fight Back
- Why am I Being Targeted? A Valuable Question for TIs
- FREE WILL: A TIs Greatest Asset, Oft Hardest to Employ
- How a TI’s Belief Structure Can Fail Them Dangerously
- Smart Meters, Stray Voltage, and Targeted Individuals
- Smart Phone EMF App No Value to TIs
- A TI with RF Measuring Device can = Dangerous Conclusions
- 7 Tips: How to outreach, preach, or beseech if a Targeted Individual
- Free Will Haven; Targeting Free Intentional Community for Stalking Victims
- Why Targeted Individuals should not hook up with other TIs
- Testimony to Mass. State Legislature on Bill Restricting Electronic Weapons
- A Glimpse of MC Realities (from the Preface)
‘Seeing Through’ NWO ‘Illumination’
The Antichrist is coming, and there needs to be a throne ready for him to occupy. Thus the New World Order is stepping up its one-world government effort and increasing their visibility in the process… and translucence… which equates to luciferian Illuminati-like illumination… often in the form of giant glass pyramids.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2017, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.What you will learn from this post:
- the Illuminati, Freemasons, Knights Templar, & Round Table Groups are the NWO;
- with the same fascination with ancient mysticism, occult, and numerology;
- and the same desire to associate their works with symbolism such as the pyramid;
- that they have been building pyramids seeking to employ mystical aspects similar to Cheops, the grandest of Egyptian pyramids;
- said pyramids sharing commonalities in occult alignments and numerological peculiarities;
- where one complex of pyramids is tied to a rather interesting conspiracy Egyptian in nature;
- and another complex of pyramids appears to involve hi-tech mind control;
- and is itself apparently aligned with all pyramids in Europe, and likely, elsewhere!
x
The Source of Illumination is darkness…
In several of my books touching upon aspects of the New World Order, I carefully point out the important role played by Freemasons and their involvement with the dark occult and, primarily, ancient Egyptian mysticism and numerology (specifically, where numbers can translate into meanings with magical powers of manifestation). I am not talking about the rank and file lodge members duped into thinking it merely a benevolent fraternal organization, but of the satanic High Masons and select Masonic operational organs which operate secretly, within. The satanic Illuminati, for instance, sprang out of and followed Masonic constructs and principles… and it was they who officially launched the New World Order movement in 1776, their goal to destroy all governments and religions, to replace with their own, providing a seat for the Antichrist. We can also thank them, and head Mason and avowed satanist, Albert Pike, for the KKK, and more.
It seems quite apparent to those who study the nature of Globalists who seek the N.W.O., that they are usually High Masons, satanists or otherwise steeped in the occult. They are often members of or work through the so-called Round Table Groups, such as the Council on Foreign Relations, the Trilateral Commission, the Bilderbergers, the Club of Rome… groups made up of power moguls who control corporations and whole industries, government agencies and military power, and media and education. These, collectively, can be called Globalists, because they seek a one-world government, which is needed in order to seat the Antichrist.
In their works, they frequently employ the same symbolism and engage in occult events right along side of others of their ilk (i.e., Bohemian Grove). While what they believe (occult) should seem silly to a rational person, I remind the reader that it does not matter what you believe to be true, or false… it only matters what they believe. If you fail to acknowledge their beliefs as part and parcel of their modus operandi, you will fail to recognize them and their works, and be unprepared for their plans as they unfold. And much has unfolded, in plain sight.
 Here, I will focus on one small aspect of their existence which is quite central to their beliefs; one of their most sacred of visual icons, the Egyptian Pyramids. Pyramids, especially the largest, Cheops, are as important to the Masonic underpinnings of the NWO as is the Cross to Christians. More so, in fact, as it is far more than mere symbol, to them; it is a powerful tool, and their fascination with ancient Egyptian mythology is quite anchored in Cheops. One need only look at the pyramid found on the obverse of the Dollar Bill and its all-seeing eye, to find a stark example. Of late, for a variety of disparate but coincidental reasons, I have made more recent observations which relate to this notion… things which you can easily verify yourself by use of Google Earth.
Here, I will focus on one small aspect of their existence which is quite central to their beliefs; one of their most sacred of visual icons, the Egyptian Pyramids. Pyramids, especially the largest, Cheops, are as important to the Masonic underpinnings of the NWO as is the Cross to Christians. More so, in fact, as it is far more than mere symbol, to them; it is a powerful tool, and their fascination with ancient Egyptian mythology is quite anchored in Cheops. One need only look at the pyramid found on the obverse of the Dollar Bill and its all-seeing eye, to find a stark example. Of late, for a variety of disparate but coincidental reasons, I have made more recent observations which relate to this notion… things which you can easily verify yourself by use of Google Earth.
Square one, the base lines of Cheops
Cheops is the largest of the Egyptian pyramids, having many astrological alignments and dimensional (numerological) mysteries, among them being it was said to have been located at the the center of all land mass; it’s axis therefore dividing the known Earth at the time into quarters; Cheops baselines were aligned due North/South/East/West. As the N.W.O. players gain in power and ability to establish a one-world government (needed if there is to be a single leader in the person of the Antichrist), they also become more blatantly visible as such a force, which means it more frequently relies upon ancient symbolism in its workings.
So, then, I wondered… might there be more than a few NWO pyramids being ‘hidden in plain sight’?
There are, of course, many pyramids around the World, especially the ancient stone variety. These come in two flavors; the Egyptian, the biggies with their seemingly smooth triangular shapes (as seen at a bit of distance), and the Mayan/Aztec stepped structures, a style not unknown in Egypt, and elsewhere for the matter. The Masons have only an interest in the former, it seems, but my curiosity was about much newer structures, those built with modern methods and materials. Would the many newer pyramids around the World exhibit traits similar to Cheops, such as alignments or dimensions of occult significance?
Absolutely. And why not? A glass pyramid is the perfect embodiment of both the ancient pyramid mythos and of Satan; sunlight reflecting from within and without by day, and electric light glowing from within by night — all work to render them both translucent and illuminated, with bright glaring highlights akin to the all-seeing eye, depending on one’s viewpoint and the angle of lighting/reflection. As a work of man, they are both awe inspiring and mysterious, working on the subconscious in unfathomable primal ways not sensed by the conscious mind without pause and consideration. Even so, one is apt to embrace and bask in their presence despite any darker connotations, for they are undeniably beautiful works of architectural ‘art.’
So let us pause and consider with conscious effort…
Square 2: a review of new pyramids around the World
There have been more than 50 new/modern pyramids quietly built around the World in the last several decades, most of them made of glass and metal, and strangely, more than half of them in North America. A couple are faux pyramids with incomplete architecture in and of their own, but one included a second pyramid on site, and the other had a completed pyramid at top, and so, were included in the study. The idea was to see if their base lines or diagonals aligned with other pyramids (ancient or modern), or if any three or more centers or corners might align. Examinations for numerological meanings were also to be considered, early on, but the growing number of pyramids made that effort too monumental. Still, some interesting discoveries along that line were made.
I found so many alignments (almost 150) and associated numerical translations in place that I felt it was appropriate to establish some sort of test group to illustrate the difference between conspiratorial intention and random coincidence. For example, at one point well into the project, EVERY new pyramid except one revealed between two and nine alignments with one-another, and/or with Cheops, itself. One had 18 alignments. So a simple control group was added: some 30 Mayan/Aztec variety, plus nearly 6 inverted modern pyramid structures were added to the study. If these, too, yielded such results, the study could easily be argued as being inconclusive.
But they did not.
Only one formed a single alignment with any other pyramid, new or ancient, and it featured no resulting numerological significance. Clearly, the massive alignments in the new pyramids were intended by the powers that be, those persons behind purchase of the location and setting design criteria as to angular placement, size, and location on the property… especially true when multiple pyramids at the same location (as is the case in ancient Egypt) were undertaken. Therefore, the test groups were excluded in findings, which proved validity of both the methodology and hypothesis. Since only the new pyramids (not inverted) formed alignments, it had to be by intention.
While about a third of the new sites are single pyramid locations, there are several with two or three (like the main pyramids at Cheops), 3 with five pyramids, and one with 8, across nearly 50 locations. I then wondered if perhaps other old, but not ancient pyramids or locations deemed ‘holy’ by the Illumnati might not also offer alignments. Adding a handful of small pyramid burial sites by Masonic persons of wealth and power, as well as the death site of Adam Weishaupt, founder of the Illuminati, and the ‘headquarters’ from which he operated his secret cabal proved that notion, as well. I was unable to discern his precise birth place beyond the name of the city (Gotha, which is ironic in its own right, because Weishaupt and the Illuminati were very goth).
At the point where I felt the matter was amply proven, I had by then added eight older sites, typically 100-200 years old, though one dates to 12 BC, in Rome. It is the Pyramid of Cestius, circa 12 BC, at a time when Rome was, like the Templars, enthralled with the mysticism of Egypt. It is a site well known to Templars and Masons. The others are all in Europe, save one in America, and two of them relate directly to the Illuminati; Adam Weishaupt’s grave, the ‘headquarters’ where he planned and executed Illuminati plans, and perhaps the definitive Knights Templar location — Templehof (Templar Temple House), all in Germany. As these last three are not known to have involved pyramids on site, they are only used in scoring other pyramids which align with them, and not evaluated on their own, even though they would score fairly high.
So the alignments created in total involved alignments between ancient, historically old, and modern pyramids. The symbolism and mysticism of such structures by their special alignments, regardless of if rendered in aged stone or in modern metal and glass — are clearly as important to their builders as the function and beauty of their designs. All were starkly beautiful, and quite functional, to be sure; a perfect way to subtly reinforce the notion of luciferian and Masonic imagery upon the subconscious minds of citizens otherwise mesmerized at what they were seeing… especially when illuminated to great advantage by sunlight or voltage.
The problem of useful presentation
But describing all these alignments textually makes for boring reading. I will give just two instances as example, next, as they are quite tied together. It will be the only review of numerological ties, though more like it, exist, and with notable frequency. Trying to present the topic graphically is also challenging for other reasons, but I will attempt that, as well, in a third review. I will then provide a very simplified summary of selected findings to illustrate the scale and nature of alignments found, with a scoring system to relate symbolic spookiness.
But first, a disclaimer is required, because I always challenge any Doubting Thomas’s to duplicate my research before they make any false presumptions as to validity of my findings, and because the research tool involved (Google Earth) has its own technical limitations with which carelessness can impact upon accuracy.
Disclaimer: regarding some figures and claims herein about alignments and measures, accuracy is sometimes more difficult to affirm via Google Earth. Google Earth allows an accuracy to within a meter or so at ground-level, but things can get more complex when one starts trying to plot and measure lines with accuracy to the far side of the globe, and/or where the locations may be nearer to the Poles than Equator, or on/near altitude changes. Satellite images used in Google Earth are sometimes taken at oblique angles on either or both the horizontal and vertical, such that visual distortions of a pyramid can make true angular alignment (in compass degrees) or even measuring its base length, difficult to accurately determine. When dealing with such angular imagery, the center of the pyramid will be other than visually depicted, requiring one to make cross lines corner-to-corner to find the true center. The quality of image can also vary, but generally, line placement accuracy can be determined within 1-3 feet (roughly the line’s width). The images for two sites were so bad that it was impossible to determine if base line/diagonal alignments existed, but at least their location was known with GPS accuracy for the purpose of central alignments.
Additionally, one must take care insure the Pyramid(s) in question are centered in the view, and to reset the ’tilt’ (View > Reset > Tilt) after zooming in, or additional angular errors can be introduced, as the lines one lays for determinations themselves ‘float’ above the ground. In fact, where the pyramid is quite large, one may find the line ‘crawls up the face,’ providing additional distortion which must be defeated. The degree of inaccuracy in any given instance should not unnecessarily render the information herein as invalid; the thrust and intent behind the location and positioning of glass pyramids is clearly not casually undertaken. Also FYI, distances between pyramids herein are rounded figures, if there is no mystical number involved.
Verbal presentation example
 Paris features two glass pyramids at the Louvre Museum, one large, one small and inverted, which form alignments to four other sites (the only inverted structure to do so, likely because it additionally features a normal pyramid, as well). There are three much smaller ones, as well, serving as skylights, which I chose to ignore, early on, and then forgot about, later; they would likely have established other alignments, as similar skylights on streets elsewhere, had done.
Paris features two glass pyramids at the Louvre Museum, one large, one small and inverted, which form alignments to four other sites (the only inverted structure to do so, likely because it additionally features a normal pyramid, as well). There are three much smaller ones, as well, serving as skylights, which I chose to ignore, early on, and then forgot about, later; they would likely have established other alignments, as similar skylights on streets elsewhere, had done.
Two of the alignments at the Louvre are baselines from the larger pyramid to the same pyramid site in Texas, where they also align with the baseline of one, and the diagonal of another of three found there, essentially parallel. Three more alignments exist to three other sites involving three corner/center combinations, one of which is Cheops some 3232 km distant. Masonry’s highest publicly acknowledged ranks are the 32nd and 33rd degrees. The number 3232 is a ‘magic number’ in Satanic numerology, because it is a doublet, which doubles its ‘power’ (amplifies its importance), and because it sums to 55 (another doublet), one divisible by 11 (a doublet which makes 33 three times as powerful), and further sums to make 10. Again, it matters not what you believe about numerology, but what they believe…
And, this is what they believe about these numbers:
In the occult, 5 is the number of the planet. According to one-time head of early freemasonry, and avowed satanist, Alistair Crowley, 11 is “the number of Magick, itself,” and of sin, or evil corruption. 10, on the other hand, is the number of ‘heaven and earth in interaction’ (‘good vs. evil‘), and the symbol of it in the Greek (‘deca’) is the triangle, of which a pyramid employs 4, which means ‘strength and integrity,’ which is certainly a trait of the Pyramid. For the matter, the number 32 relates to ‘inspiring of truth and living by it,’ which is to say… the very promise and implied hope of illumination. Unfortunately, illumination means something rather different to those with a darker agenda, something closer to that which the serpent spoke of in the Garden of Eden. These are not the only meanings found in general numerology, but the ones preferred by dark occultists.
Extending the base lines of each of the Louvre pyramids westward 3500 m will take you, again in parallel manner, to the center unit of one, and a corner of the other of two glass pyramids built in Westborough, MA, by globalist pharma firm, Astra Zeneca (astra in the occult relates to supernatural weapons). Another line can be drawn from the lower corner of the larger pyramid at Louvre, through the center of the smaller one, there, to pass through the diagonal of the center pyramid of three atop a very Masonic looking Federal Government office building in Ottawa, Canada.
The smaller pyramid in Paris is 2 m shy of being 1/10th the base line dimension of Cheops, while the larger one is two meters more than 1/6th of Cheops. The larger Astra is 1/6th greater than the larger of Paris, and the smaller 1/2 the size of the smaller in Paris. The Ottawa pyramids are 1/4th the size of the largest at the Louvre, and 1/25th of Cheops, and 2 m shy of being 1/2 the smaller Astra. I would love to analyze the actual dimensions of all these, if they were readily available.
In Chile, the resort complex at San Alfonso Del Mar features a giant glass pyramid on the beach with four alignments. It is aligned such that its base line will bisect with the center of one of the lesser stepped Egyptian pyramids. Two more alignments are to diagonals of a pyramid in London, and one in China, 20 km from Hong Kong. A third aligns with the corners of two pyramids in Islamic Astana, Kazakhstan which, though richly expressing Islam in the property’s design, is also rich with Egyptian symbology.
The Chilean Pyramid base is also one/sixth the size of Cheop’s (38.3333 m, a number which is found many times in the fuller study in either location, size, or compass readings of various pyramids). It is located on the 38th Southern Parallel and the 32.32 Meridian. 38 sums to 11 (Magick) but itself can mean ‘Lucifer, the will of the Devil.’ 1/6th = 18%, where 18 = 9+9 (99 doublet) and 3 x 6 (666 triplet — even more powerful than a doublet, and Satan’s name). 18 itself means ‘Oppression, bondage, slavery,’ and = 3 (a ‘perfect number’ meaning fullness) x 6 (the soul of man) = 666 (legend/man/illumination).
A graphical review
Enough textual description; it is too boring and difficult to make sense of. Let’s try graphical, looking at hotel resort complex at Galveston, Texas, which also consisted of three Pyramids. This is one of several with 8 or more alignments, and perhaps the most interesting in terms of just what they align with, and how.
It may help to review what qualifies as ‘aligning,’ so you know what you understand why the lines look the way they do. The alignment must involve at least three points of contact between two distant pyramids, based on corners and centers. A baseline is two points, a diagonal or perpendicular from a baseline through the center being three points, but the distant pyramid must still have at least one such point of alignment, as well. If only one, it must be its center, but aligning with two corners on two different pyramids, there, is another way to align.
There are examples in my study were a baseline, perpendicular, or diagonal aligns with yet another baseline, perpendicular, or diagonal (four to six critical points total); a much harder thing to achieve. In like manner, some can be extended to align with yet other points of other pyramids at a third location; an even more dramatic alignment. I have found as many as five pyramids in three locations involved in a single alignment across the globe… with 14 points of alignment in all. These harder kinds of alignments should be next to impossible by random occurrence. Yet every single pyramid exhibits them.
And we have two such virtual impossibilities illustrated in our visual review at Moody Gardens, in Galveston, TX. Two of them actually involve Cheops, as earlier reference in the textual description, the ultimate of all possible alignments from the Masonic viewpoint. In fact, I find it the second-most interesting of all modern sites, in terms of alignments (the first, at Sauerland, Germany, is impossible to show in this manner as it enjoys 23 alignments. UPDATE: 43 in a row, and I finally stopped bothering!

Galveston Moody Gardens Hotel complex; three pyramids, one pink, one blue, one glass (gray), forming 8 alignments to six pyramids, including two with Cheops!
Clockwise from Noon in the image, we see an align to the Nekoma Air Force Station, an experimental anti-missile defense system long abandoned. What is interesting is that one of it’s seven alignments goes to the only pyramid in South Korea — quite dependent upon U.S. anti-missile technology. That’s interesting, because there is another pyramid in N. Korea, and one of its several aligns goes to the Las Vegas Casino pyramid, which in turn aligns back to the Nekoma site. It is as if both N. and S. Korea are ‘borrowing’ from American military power, after a fashion, to create or reflect a ‘stalemate.’
Next we have two aligns effectively ‘parallel’ to the ‘holiest’ of Masonic pyramids in Egypt, involving a total of nine critical points with three pyramids. There is then an align to the Rock and Roll Hall of fame in Cleveland, OH, where it passes through the center of both pyramids, there (one small, complete pyramid, and one very large incomplete, or faux pyramid. There, the base of the larger less the base of the smaller, is equal to 1/3rd the base of Cheops.
We find an align to a now defunct pyramid on Miamii’s beach. Fairly ordinary as alignments go, it was built as a promotional venue for the international beer company, Heineken. Despite being temporary, it was placed to form at least three alignments on its own. Then, in like manner to the two aligns to Cheops, we have two more going to the two pictured Biosphere pyramids, which, like the two Rock and Roll pyramids bisected with the same line from Moody Gardens, have both of their pyramids bisected with an align from Nekoma (coming full circle, if you will, to form a triangle). In fact, Nekoma is itself involved in a total of 6 such three-way triangles. One of those involves the Miramar retail store, our final align from Moody Gardens, for two such triangles sharing Moody and Nekoma locations. Miramar is the other incomplete faux pyramid, in that only two opposing sides are triangular walls. Miramar, in turn, with two pyramids, forms 6 aligns, including one to the very Masonic Capital grounds of Australia, at Canberra.
So far, we’ve only closely looked at two out of about 50 locations. You can see how hard it is to use either text and/or graphics to reveal it usefully. So let’s now try a different way, and employ a chart with a scoring system designed to rate the comparative ‘spookiness’ factor of a given ancient or historically old site’s alignments with new pyramids or other holy illuminati locations, including each other. To further reduce the clutter, it will then only look at sites which directly connect to them, in even briefer review, sans scoring. The scoring system replaces trying to compute and display the actual odds of the alignment, which would be as high as 10 figures:1, in many cases.
For example, the odds of just a single alignment of the simplest kind, center to baseline, diagonal, or perpendicular or to two corners of two pyramids at destination (earning the lowest possible score of 1 in my scoring scheme) would have actual odds of 202,500:1 against. That is based on the notion of worst case accuracy of 1/10th of a degree of arc… meaning that each pyramid would have 10 x 360 degrees of potentially useful compass positioning, divided by 8, as there are 4 lines the pyramid which establish a total of 8 possible compass vectors. You need to multiply each pyramid by each of the others involved if aligning to another baseline, diagonal, or perpendicular. A baseline to baseline alignment odds would be 164,025,000,000:1 by such reasoning. Such odds are multiplied further by additional alignments at the site. Argh!
Technically, that’s too simple, because angular placement is not the only factor. Size and relative positioning plays a role, too, when two corners/centers of two different pyramids at the same site are involved, but I’m not going there without a super computer!
Now, if you want to argue that the actual accuracy we should using is tighter than that, implying room for error in ‘finding aligns,’ consider for a moment that only one alignment with the Mayan/Aztec pyramids was possible using the same accuracy as I employed. That makes a pretty good case that the alignments were intended regardless of whatever actual accuracy was employed. Even if you allowed for my own human error, there are so many alignments that they could not all have been for my error, given the Mayan/Aztec set enjoyed no similar quantity of errors. But by all means, feel free to correct my math/assumptions if you are of bookmaker caliber in computing odds, but I’m pretty sure I’ve got it right, based on some experience in statistical data analysis; I once ran my own marketing research firm which ran probability studies. No matter: we will use scoring, instead…
Scoring is as follows:
- center point to corners of two pyramids or a base/diagonal/perpendicular of 1 pyramid (simple alignment) = 1 point for the alignment;
- base/diagonal/perpendicular to same (complex alignment) = 5 points for the alignment;
- Bonus 5 points for any parallel alignments or alignments to multiple pyramids of one site to multiple pyramids of another site (parallel/pair alignment);
- any extended link to an additional pyramid (extended alignment) = alignment score x 5;
- link to Cheops (Cheops alignment) = x 5;
- link to other Egyptian pyramids or Illuminati sites (Illuminati alignment) = x 3;
- link to other historically old sites (Masonic alignment) = x 2;
- 1 point for each alignment and for each pyramid at site;
- magic numbers, angles, dimensions, etc., not part of scoring;
- Cheops gets a bonus of 33 points, Illuminati sites 11 points, Masonic 7 points
- maximum score limited to 99

Egyptian Pyramids 13 aligns w 6 pyramids on site (Δ) = 99 points: 29°58’44.54″ 31°8’3.65″
Complex Parallel to Sauerland (5+5 points), 3 Simple Parallel to Dubai (6×3), 3 to Sauerland (6×3), 2 Simple Parallels to Galveston (6×2), Complex to Niagara Falls (5), Simple to Louvre (1), to Eatonton GA (1), to San Alfonso del Mar Chile (1) 85 total +33 > 99.
x
 Cestius pyramid in Rome 5 aligns w 1 Δ = 99 points: 41°52’34.97″ 12°28’51.16″
Cestius pyramid in Rome 5 aligns w 1 Δ = 99 points: 41°52’34.97″ 12°28’51.16″
Complex Extended (three times — 4 Δ at 3 sites, in all!) to Manitoba Capitol and on to Miramar Retail (5x5x5x5), Simple Masonic to Karlsruhe Mausoleum (1×2), Simple to Pheonix Jeju S. Korea (1×2 – Phoenix is Masonic/Egyptian), to Sauerland (1), to Portsmouth UK (1) > 99 points
x
 Star pyramid mausoleum Scotland 3 aligns w 1 Δ = 34 points: 56° 7’19.42″ 3°56’43.72″
Star pyramid mausoleum Scotland 3 aligns w 1 Δ = 34 points: 56° 7’19.42″ 3°56’43.72″
Simple Illuminati Extended to Weishaupt’s grave, to Gold House IL in opposite direction (1x5x5), Simple to Cooperative Bank UK (1) 27 points + 7 Masonic site = 34
x
 Karlsruhe pyramid mausoleum 7 aligns w 1 Δ = 27 points: 49° 0’33.22″ 8°24’14.05″
Karlsruhe pyramid mausoleum 7 aligns w 1 Δ = 27 points: 49° 0’33.22″ 8°24’14.05″
Simple Illuminati to Illuminati HQ (1×5), Simple Masonic to Cestius (1×2), to Kazakh RU (1×2 — rich with masonic/egyptian architecture), Simple to Dubai (1), to Edmonton Capitol (1), to Cal State U. (1) 20 points + 7 Masonic site = 27
x
 Bickling mausoleum UK 2 alignments w 1 Δ = 13 points: 52°49’9.01″ 1°12’48.36″
Bickling mausoleum UK 2 alignments w 1 Δ = 13 points: 52°49’9.01″ 1°12’48.36″
Simple Illuminati to Illuminati HQ (1×5), Simple to Sauerland (1) 6 points + 7 Masonic site = 13
x
 Schoenhofen Mausoleum Graceland Chicago 2 alignments w 1 Δ = 13 points: 41°57’33.56″ 87°39’34.09″
Schoenhofen Mausoleum Graceland Chicago 2 alignments w 1 Δ = 13 points: 41°57’33.56″ 87°39’34.09″
Simple Illuminati to Illuminati HQ (1×5), Simple to Sauerland (1) 6 points + 7 Masonic site = 13
What follows is a simpler summary of the first few of the destination sites mentioned sites as evaluated from their position…
Sauerland 23 aligns, 8 Δ, Dubai 13 aligns, 5 Δ; Moody at Galveston, 8 aligns, 3 Δ; Niagra Falls 2 aligns, 1 Δ; Louvre 7 aligns, 2 Δ; Etonton GA 2 aligns, 1 Δ; San Alfonzo del Mar 4 aligns, 1 Δ; Manitoba Capitol 9 aligns, 9 Δ treated as a single Δ as they all directly touched one another 3×3, and were each relatively small; Miramar Retail 7 aligns, 2 Δ; Pheonix Jeju S. Korea 6 aligns, 1 Δ (note: N. Korea has a Δ, too).
These are all quite typical of all sites evaluated, globally. The only site which scored 1 (1 align) was a site which has had its 2 pyramids removed/destroyed, disallowing angular alignment determinations, though the center of one of the pyramids was known, allowing an align by that method.
CONSPIRACY ALERT: That site, by the way, is tied to a little known conspiracy surrounding the Nuwabian Nation, an all-egyptian-like community of almost exclusively black people which was seized and razed to the ground by the U.S. and Georgia State and County governments. They were allegedly targeted for being a cult, subversive group, criminal organization, nest of child abusers, or a swindle… depending on who you ask. Seems like everyone had a pet excuse, including YouTube who seems to regularly censor vids on topic for their usual list of fabrications. Note the resemblance in some of the ceremonial dress to masonic lodges such as the Shriners (Nuwabians, like the lodge system, also use the terms, Orders, and Lodges). All Egyptian is wrong, too; they also were adoptively and by blood associated with Native Americans of the Yamassee Federation of Tribes, among them the Seminole.

I count at least 8 pyramids on site before destruction. The black pyramid , as primary ceremonial structure, was the only one I was able to locate, but not know its alignment with any certainty. These people were very serious and deeply involved in their culture building and adherence, despite the amusement park-like construct of their community.
Note on mausoleums: What we see in our review is that the three mausoleums share unique ‘coincidences’ in that each aligns with an Illuminati historic site honoring Weishaupt, and each in turn is honored for having done so by Sauerland aligning with them. There are many such pyramid mausoleums in Europe, America, and a few scattered elsewhere, far too many, in fact, to encourage me to dig further. Regardless, as the very first and only three reviewed all shared these two features, I’ve no doubt that others do, as well. A single Mason could easily undertake a single such alignment to a point of their own choosing, and more modern pyramid builders could easily accommodate at least one or more such mausoleums in their own alignment considerations. This brings us too…
Sauerland, enigma equal to Cheops

Sauerland is one of the newest of all sites, a complex of 8 pyramids which appears it may even involve mind control research. It certainly defies normal property development, architectural design, and building contractor norms in several ways. First, its location is on a hill overlooking an industrial park, and despite looking like a luxury retreat, is in fact the corporate campus of biomed tech company, Rayonex Schwingungstechnik (Rayonex Vibration Technology). It started with three pyramids, and has since grown to eight.
Second, the site has an adjacent and extremely unique high observation tower (about 110′ high) which overlooks the pyramids and the valley, just high enough that morning sun could shine through the large holes in the upper level and onto the pyramids, creating unique shadows. This was a trick employed in ancient Egypt using Washington Monument style oblelisks, such that at a certain time, a shadow might point to a secret place within the greater site (as seen in Indiana Jones and the Lost Ark. The tower’s corner shadow does fall over the pyramid property. But, let’s just call that a pipe dream.
You do have a pipe of some sort, don’t you… and a whip and hat?
Third, each building is offset irregularly and apart from each the other with no obvious pattern or reason, and likewise, quite contrary to normal designs, angled one from the other up to 3 degrees or so in compass alignment. It is my belief that this is what enables it to accommodate so many alignments, a thing which would require planing with a fairly complex computer program, to determine. Finally, again unlike most complexes, even where ‘luxury’ is intended, no two buildings are built or designed the same; each has an entirely different layout and appearance, though some features at least look similar. Usually, a cookie cutter approach to keep costs down would be employed. Yes, even in corporate campus design.
Then there is the very small pyramid surrounded by a water feature. I found construction photos that show a drill being used on a hole there, approximately 1 meter wide, with smooth walls. It was associated with an article on geothermal drilling which led to a very interesting YouTube promotional video that is really worth the watch; it will intrigue and educate you. After watching, though, ask yourself if the expense this likely represents would normally be deemed appropriate for a small fish pond? The video seems to address that with a blanket statement, but does it, really?
I learned also, that the small pyramid over that hole is the only one on the property using metal walls. The other, larger pyramids use some kind of unusual looking material which requires special application, according to other construction images I found. The panels used on them might logically be radiographic in nature, designed to limit or enhance radio waves of select frequencies, given the nature of the company’s work, as you shall see. In like manner, I can imagine the holes drilled by that machine could be used to install an array of underground EMF sensors or emitters. The video implies the array of radially and laterally drilled holes provides a series of ‘pipes’ which may in fact be perpendicular to one or more of the pyramids. Just why these possibilities are raised, is covered below.
Also unusual, is that one of the original three pyramids (perhaps more, now) is strictly for therapy use, with ten therapy stations. In each pyramid, a security computer controls all lights, window blinds, and door locks, and though there is no manual switch anywhere within for any of these, each workstation is said to have its own localized control over these features. But the security system computer can override, which makes it a rather creepy place with respect to potential for political control and overbearing security solutions against occupants, Big Brother style… especially if you don’t have authorized access to a workstation. Undoubtedly, there are plenty of security cameras, and I find it disconcerting that some pyramids have no windows, whatsoever — normally a code violation, unless a warehouse or factory. One must ask why so much expense and devotion to therapy and externalized security control over environment would be required? Let’s take a peek, and see.
The answer raises more questions. This is a unique kind of high tech firm. Their product/services would seem to involve mind enhancement, mind bending, or even mind control, but certainly relate to biophysics and therapy of some kind. One or more of those possibilities is very likely; the firm does research in electronic frequencies upon the human body (bioresonance), among other things. According to Wikipedia, bioresonance is all based on pseudoscience, which is a polite term for ‘made up BS by con artists’. Dunno about that, because…
This is also the sort of stuff useful in DEW Weapons for behavioral control (Political Control Technology). Of course, such tech is always researched and funded based on some good it might accomplish, including the combating of electrohypersensitivity, which many TIs suffer from because of their constant DEW targeting, or some preexisting natural sensitivity. I have it, myself. But once a patent is filed and governments or dark-minded NGOs get wind…
 Now, about that tower… What if it was for security guards overseeing grounds security should an alarm goes off of some sort. The tower does have its own large building which might be suitable to house a security force. Hold that thought in mind while reading the next paragraphs. Turns out it is not just an observation tower, and not just any building. And, while guards might be rather far fetched a notion, there is more to consider.
Now, about that tower… What if it was for security guards overseeing grounds security should an alarm goes off of some sort. The tower does have its own large building which might be suitable to house a security force. Hold that thought in mind while reading the next paragraphs. Turns out it is not just an observation tower, and not just any building. And, while guards might be rather far fetched a notion, there is more to consider.
The pyramid shape is also known as a Frustum by Masons; a shape used by the military in times of old in a manner not unlike a Tank Trap. Like a tank trap, as a shape, it cannot be easily overcome when several are placed together, there being no level foothold between them (a steep V shape), and its sharp corners, especially at the top, inhibiting climbing. More importantly, because its sides are sloped, one cannot hide behind a frustum, if the enemy holds high ground… such as a castle wall… or a high observation tower. Just exploring possibilities, here… but far-fetched or no, it fits the spookiness factor of the place.
But as stated, that’s not all. The platform is merely the top level of what is actually a mine shaft elevator lift. The building is currently a mining museum with access to a huge abandoned mine; they actually take you down into it with hard hat and light, etc. So, like Cheops, there are underground passages beneath the Sauerland pyramids. It is, of course, possible that some of those passages might be remodeled into something else entirely different, like many old mines are, today. It is even possible there are ways to access them from within one or more of the pyramids. Now wouldn’t that be a mystery to discover and explore, whip at the ready? However, all this causes me to hope no one would go drilling a bunch of radial holes over an abandoned mine… if they didn’t know exactly where the mine’s cavities were…
Now, last mystery. Look carefully at the top of the platform at the left corner nearest. No. That’s not a machine gun, though it can potentially be used to ‘shoot.’ It’s appears to be Yagi antenna, normally used to transmit or receive microwave signals in an amplified manner, along a narrowly aimed path. But wait! Where does it aim? At the top of that tower, as high as it is, the thing is aimed squarely at a hillside nearly four times as high as the platform. Useless, as seen. But wait! Just beneath the top rail is a what looks like a motor; the shaft can rotate. At the top is what appears to be a motor at an appropriate angle to change vertical angle. The white object appears to be a housing of a control system operated remotely. I used to sell such systems for video security setups based on microwave relay. Pretty sure of what I’m seeing. And, there is a second pole identical to the first which could be similarly fitted, and which may have been since the photo was taken.
Why would you want that? Well, you might want to tune in distant TV stations, except they don’t broadcast in microwave. You could use it to grab someone’s cell phone signal, if you knew exactly where their phone was, to aim it. There are yagi antennas that can be used for those things, but they would look different. But what if you owned a bioresonance laboratory with some human guinea pigs? What if you could place them in rooms within a pyramid, where the slope of the pyramid was roughly perpendicular to a high mounted, aimable microwave transmitter, such that every subject got exactly the same dose of signal at the same time, or such that you could specifically target a given subject with a unique signal? It would probably look a lot like Sauerland. You think?
I only mention this, because older pictures, before the pyramids were built on site, don’t show such a ‘gun.’
Is it a conspiracy?
If one concludes that it is impossible that by mere chance alone, every modern and non Mayan/Astec-style pyramid should align with other pyramids, including Egyptian… then it has to be by intelligent design by agreed-to planning by a group of many persons with like agenda. That it is done covertly and involves mystical occult reliance… removes it from the realm of benevolent methodology or intent. That these pyramids can be found in countries of opposing political, religious, and ideological beliefs… precisely fits the Illuminati model and game plan established by its founder, and reflected in Morals and Dogma, the ‘Masonic Bible’ written by Albert Pike. That the only persons financially and powerfully placed are able to arrange for such things tend to also be members of Round Table Groups and are often also Freemasons… would seem to cement all these considerations into a single image: that of a conspiracy. That there is the possibility that it even involves mind control is, to say the least, the ultimate and most heinous form of conspiracy.
“Every man is entitled therefore, to give any explanation of the symbols and a system of the doctrine that he can render palatable… Of all the means I know to lead men, the most effectual is a concealed mystery.”
There is a Mark of the Beast Implant with YOUR NAME on it
This is an old topic that’s lost traction in the public eye, but in the background, the enemy continues to work ever closer to fulfilling prophecy about Mark of the Beast. Now, employees are being asked to implant themselves in order to get snacks, get through doors, and access workstations and photocopier.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2017, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.What you will learn reading this post:
- what RFID is, who is behind it, and why you should fear it;
- about Digital Angel, and the bio implant tracking version of RFID;
- why you should fear it, put away petty ideological differences, and unite against it
- what you can do to defend against it;
- the greater strategy RFID is in support of (the ultimate threat).
Invasion of privacy tiny in size, massive in scope

Tracking implant quite similar in shape to a much larger one found in my own leg some 35 years ago. State of the art, today, are smaller, translucent, bond with and look like human tissue: invisible to a surgeon and to x-ray. MRI sees them as a blemish. Less sophisticated units without GPS/cellular/wifi capability can be as small as the period in this sentence.
Recent news stories, including a particularly scary one referenced in red text, herein, have forced me to draw upon years of research and dig out my old PowerPoint presentation, 666 Reasons for Smart Dust and RFID Technology, as presented as the keynote presentation at Conspiracycon 2010, in Santa Clara. Any definitive presentation must go back to the beginning, or the dots won’t quite usefully connect. This is going to impact YOU in YOUR LIFETIME. Actually, it already has, and you just don’t know it; the water temperature is slowly being raised on we Frogs, and it’s quite hot, already. Hopefully… we can somehow jump out before its too late.
Smart Dust and RFID tracking technology are quite related, but Smart Dust is not going to be a part of this presentation, except to say that it is nanotech capable of much more than RFID, but it is not an implant. While it is represents its own significant threat to social, financial, and physical security and well being, it is less useful than a tracking implant for the population at large, and cannot play the role of Mark of the Beast. Fortunately, it will not likely ever be used against anyone not deemed a high-priority national security risk. You know, like Will Smith, in Enemy of the State.

The less costly Digital Angel implant
RFID, however, is the very heart of the tracking bio implant, the most obscene version and infamous of which is Digital Angel. That’s the name of a CIA front central in pushing for implants, but also often used to describe their chip, itself as a product trade name. They also offer a wide variety of tracking systems which are non implant, such as wearable items like watches and ankle bracelets.
But we need start with a broader view on RFID to fully understand the greater threat this topic represents. Non implant (and seemingly harmless) versions of RFID are already used to track an endless array of products, and you are quite likely to bring them home every time you go shopping. In retail, it is mostly benign, but it becomes the bedrock of a useful personal tracking system.
What?
Mostly benign? Check this out, an edited and updated excerpt from my book, The Professional Paranoid: How to fight back when Investigated, Stalked, Harassed, or Targeted by any Agency, Organization, or Individual (third ed.) Excerpt begins…
Smart Dust, RFID, and the Mark of the Beast
i want you to consider the first letter of this sentence; the lack of capitalization is not a typo. I wanted to draw attention to the dot above the letter ‘i.’ There is a reason… there is an RFID invasion taking place, and some of the invaders can be just that small.
 The Bible tells us that in the End Times, there can be no transaction between persons for goods or services unless both parties have the mark. Revelation 13:16-17 “And he causeth all, both small and great, rich and poor, free and bond, to receive a mark in their right hand, or in their foreheads: 17 and that no man might buy or sell, save he that had the mark, or the name of the beast, or the number of his name.”
The Bible tells us that in the End Times, there can be no transaction between persons for goods or services unless both parties have the mark. Revelation 13:16-17 “And he causeth all, both small and great, rich and poor, free and bond, to receive a mark in their right hand, or in their foreheads: 17 and that no man might buy or sell, save he that had the mark, or the name of the beast, or the number of his name.”
Though the Mark of the Beast is thought of as being the number 666, that is not quite the case. That is the number of the Beast himself (the Antichrist) in numerology evaluation of his name. The original words used in the original Greek texts of the New Testament can be translated to mean ‘insert’ as well as ‘mark.’ Thus there are growing numbers of people who think that some form of Digital Angel bio implant will be the actual marking device. This section will illustrate that likelihood and educate you on just how close to that day we may be.
This will make sense later: implants are the mark for the hands of peons, and marks on the forehead are the mark for meons.
What is Digital Angel? It is a firm which is known for a series of tracking products, including bio implants, all based on RFID technology. Simply put, it is a passive device which, when scanned with a low-energy RF signal, responds with a signal of its own, broadcasting a unique identification number or other data. Early versions of this are still commonly found in clunky removable/disposable merchandise security tags installed by retailers which can trigger alarms when shoplifted goods exit the store. In the modern version, the product manufacturer includes the chip which enables the same feature without the retailer needing to do anything but take delivery of the goods.
There is a whole emerging industry based on RFID, and it, in turn, impacts on almost all other industry sectors. The industry is driven at its heart by the military and intelligence community with the help of corporations who are part and parcel of the NWO elite, as defined by the makeup of their directors and other corporate leadership or ownership. What they want to do with RFID is mind boggling, as is what RFID is capable of in terms of invasion of privacy. To start, they want every single product manufactured and sold to have its own unique RFID tag, and are pitching it to manufacturers and retailers as the next evolution of bar code.
Similar chips in credit cards technically allow purchase without the need to remove the credit card from the wallet, though they currently require us to scan the card. But all that is really be needed is to specify which of several credit cards we might be carrying was desired to be used. That could be verbal, by touch screen, or smart phone application, which avoids producing the card. RFID is also being built into phones for comparison with credit cards nearby, to allow verbal telephone purchases to be made without the need to verbally confirm credit card details. The bio implant is ‘sold’ to us as a convenience to replace all of that (examples to follow).
That is the ‘convenience’ under which it will be sold to us in the retail world, and if a cash register can scan these chips, so can the device at the door looking for merchandise which had not yet been purchased. Why stop there? Anyone can put small and hidden scanners (with or without cameras) anywhere, and for any reason… such as at every doorway where some form of security or tracking feature is desired. By scanning RFID credit cards, the identity of everyone passing through is logged and time stamped without their knowledge or participation. Actually, any RFID tag on your person can do the same thing (it is being built into clothing), because your identity can be associated with its purchase. And that is just the beginning. Ergo, the national ID ‘Real ID‘ program is based on RFID, and eventually, the human body itself will be its on RFID ‘ID.’
 In the very near future, it will serve law enforcement. At the scene of the crime detectives will often find discarded items potentially belonging to a suspect. They analyze these for clues, such as fingerprints, to build a list of suspects. In a world of RFID-only purchases, every object also identifies who purchased it, when, and where (often also useful clues in prosecution). What about cash purchases to thwart RFID records keeping? Not a problem. You didn’t think for a moment that those little slivers concealed in the left-hand portion of your new money was truly just a counterfeiting deterrent, did you? Put anything but a $1 bill in your microwave oven and it will explode when operated… a trait of RFID. Moral of the story; don’t casually discard product wrappers, especially if you think someone might use them to implicate you in a crime; burn them.
In the very near future, it will serve law enforcement. At the scene of the crime detectives will often find discarded items potentially belonging to a suspect. They analyze these for clues, such as fingerprints, to build a list of suspects. In a world of RFID-only purchases, every object also identifies who purchased it, when, and where (often also useful clues in prosecution). What about cash purchases to thwart RFID records keeping? Not a problem. You didn’t think for a moment that those little slivers concealed in the left-hand portion of your new money was truly just a counterfeiting deterrent, did you? Put anything but a $1 bill in your microwave oven and it will explode when operated… a trait of RFID. Moral of the story; don’t casually discard product wrappers, especially if you think someone might use them to implicate you in a crime; burn them.

Actual TIAO logo
But it gets worse. For any of this to work smoothly, somewhere, someone needs to catalog and keep all those transaction records and make them available for government’s needs. Enter the Total Information Awareness Office (TIAO), AKA the Terrorist Information Awareness Office. This was modeled after an expanded version of FINCEN (Financial Crimes Enforcement Network) capabilities (check this out); and was MILITARY led and very Intelligence community friendly Defense Advanced Research Projects Agency (DARPA) project. I’ve seen the original DOD call for papers and the final description of capabilities and intended uses for the TIAO, and it has little to do with targeting terrorists. Instead, it has to do with capturing records of EVERY transaction between EVERY citizen and business, as well as the passing of ANY citizen through ANY doorway in selected locations. Further, it will track vehicles past checkpoints and can log other kinds of interactions or transactions between people and each other or real world objects (i.e., machinery, vending machines.)

Everything in this image under Transactional Data, and all the little colored storage systems (the cloud), and Corporate Memory, comes largely from backdoor access to RFID-based data. The red Privacy and Security dotted line was added AFTER privacy concerns, to imply a search warrant would be employed (untrue). Intel data would include access to NSA’s massive global wire tap, as well as all of the other 16 spy agencies of the U.S., and those of friendly nations.
Update: TIAO ‘went away’ due to public protest and ‘too many questions,’ including “Why was the head to be a convicted criminal participant in Iran Contra, an ex Naval officer of significant credentials tied to CIA and the Pentagon, John Poindexter?” And yet, it did not actually go away. It has instead been quietly replaced with the OIA; the Office of Intelligence Analysis, another new super-secret spy agency operated out of Homeland Security. They, in turn, gently established ‘Fusion Centers.’
Fusion Centers are ‘sold to us‘ as a happy pill having nothing to with dark deeds, and as being established by cities and state governments in order to share information between partnering civic and federal agencies, local businesses and NGOs for improved security against terrorism and ‘other threats.’ In truth, they are hotbeds of social spies who operate external of the centers within those groups of partners on behalf of DHS and the intelligence agencies. It is often a source of organized gang stalking, and a collection point of ‘data’ about ‘other threats.’ We are the threats, and the data is obtained through backdoor access to the ‘data’ about us found in participant computers, including RFID transactions, security and traffic cams — and via gang stalking and the associated psychological profiling. It is a kind of fascist Brown Shirt group without the uniform, replaced with a smile and handshake… and big eyes and ears.
And worse still. If government decides it wants to know even more about you, a black van can drive by your home and scan it to collect the sum total of all information from all RFID tags (or Smart Dust) found within the home. They will quickly know EXACTLY what is in your home, where you got it, how you got it, and when. This gives field agents the ability to gain access to that kind of information in a very focused way instead of having to run tedious database searches which would necessarily include bureaucratic handling and, perhaps, the dreaded and feared need for a pesky warrant.
And, worst of all, the ultimate expression of RFID privacy abuse is to put one in the human body, with or without the target’s knowledge. The question is, how close are we to this nightmare, and what can we do about it? The answer is, we are frighteningly close, and in fact, it has already been happening for decades.
- RFID is already being put on thousands of products you buy today. Even common mundane consumer goods like Gillette razors and Max Factor makeup have been ‘chipped’ with RFID. Walmart pioneered its use, and used cameras (which opens up a whole new personal security threat for the chip) to track customers through the store, and record RFID transactions. There are also shopping carts with built-in ‘product information displays’ which can track every item you handle while in the store, and profile your shopping experiences over time. You can bet there were cameras connected to scanners scattered throughout town by CIA or the military (Walmart Board included ex military and intelligence agency types at the time), as well, to see where else you went and what else you did, to test it as a spy tool. Many manufacturers have placed orders for hundreds of millions of RFID tags and millions of scanners. They have to be in use somewhere.
- Many tens of millions of RFID equipped credit cards have already been issued. You can spot these visually if they are transparent, or if the credit card number has a lot of zeros in the middle, or a gold foil rectangular emblem about ½ inch square. Though sold to us as a ‘security feature,’ they are the opposite: content can be stolen by proximity scanning without your knowledge, and then the RFID and card can be cloned by thieves for use at your expense. I’ve caught such a thief scanning at the doorway to Walmart. He was pretending to be making a phone call… pacing back in forth in ways that maneuvered him in behind victims. But there are also home-made scanners which can scan from hundreds of feet away.
- Most cell phones use SIM card technology incorporating RFID (the SIM card, more than the phone, identifies the authorized user). This is often used in phone apps to facilitate cardless credit transactions (i.e., iPay)
- Virtually every maker of cash registers and point of sale systems is developing low-cost attachments to existing cash register and credit card scanners to sense RFID, as well as whole new systems to replace the old with simplified operation and reduced cost — this allows self service checkout and the elimination of the sales clerk, so it will be promoted as a ‘cost reduction’ tool. But don’t expect to see savings passed on to consumers. Money already has the needed strip in place and it likely has been RFID capable all along without our knowledge.
- All employee scan cards use RFID. Hotel room key cards use RFID. Federal Express, UPS, etc., all use RFID shipping labels. Monthly bus passes, season tickets, and the like, also employ RFID.
- Pets and livestock have been being implanted with RFID for decades. Within the last ten years, thousands of people have, as well, largely through efforts to chip children ‘to protect them against kidnapping.’ There are nudist resorts where you can volunteer to have one injected to represent your credit card information for purchases at nudist-camp points of purchase for services and goods. Otherwise you must carry your wallet or purse and keep an eye on them. What fun is that if trying to commune with Mother Nature and your bank account? In July of 2017, a company announced break room vending systems and software to allow implanted employees to access snacks without money. Learn more here. Soon, you will see implants being promoted for use with parking meters, fast lane highway access, and on, and on, and on.
- Bioimplants can easily be implanted in a human without requiring their knowledge or consent. All they will know is they woke up with what seems to be an insect bite. This can be done while they sleep via covert entry of their home, or at distance with a special pneumatic sniper rifle.
- According to several news accounts, countless livestock has been slaughtered with the implants still in place, their meat ground and sold, and consumed by unaware purchasers. Despite massive recall efforts, not one package of meat was recovered. RFID implants are made of glass, plastic, and poisonous metals.
- Some school systems are requiring children to use their fingerprints with scanners in order to get their school lunches. This is bad enough, but the firm that makes the equipment used also offers an RFID attachment in lieu of the fingerprint scanner, and mentions implants in their literature as an option.
- One maker of RFID, in marketing it for aircraft part identification in an assembled aircraft (the goal being to track parts which might be subject to safety recall, and a feature useful in crash investigations) chose a trade name for their RFID of ‘The Mark.’ The part number when Boeing Aircraft orders it from the maker is alleged by employees to be 666.
What can you do to defend against it?
Aside from sharing this post, not much. Be very vocal and protesting at every opportunity any discovered use of the technology. You might demand RFID tagged merchandise be detagged or the tag neutralized before you leave the store, but that would make you look crazy. However, organizing endless group protests can have an effect. Any firm that covertly uses it should be razed to the ground (sued into oblivion for violation of privacy). Any government office holder should be kicked out of office if they support the technology in any way, shape or form, or simply fail to oppose it. In my opinion, preparation for revolution should be made if these efforts fail, because that would be the only remaining recourse prior to full enslavement.
Back to the bible. In The Book of Revelations where the reference originates, there is also one more clue RFID will be the basis of the Mark of the Beast. One at a time, the Seven Angels open the Seven Seals to unleash seven deadly punishments upon the unfaithful on the earth. One of these states that those with the Mark of the Beast will suffer severe pain and many will perish from it. A subtle clue.
As it happens, there is one feature about RFID which must be told to make sense of this, and it suggests how to thwart the tech: if exposed to high energy radiation, RFID heats up incredibly and explodes. A burst of high energy radiation levels will literally destroy it… such as an intense solar CME blast (Coronal Mass Ejection – a high RF/EMF energy field). At this time, I cannot tell you how to generate such an energy and safely use and aim it, but it has been suggested by other experts than a ten second microwave oven exposure should be sufficient. Now if I just had a portable unit I could waltz through the retail Aisles with… set to ‘Burst’ mode… but you can bet there will be or already are laws written to make that illegal.
But there is something simpler which also defeats the technology. Metal shields the signals. Thus wrapping a National ID or an RFID equipped credit card or object (i.e., chipped hand) in aluminum foil defeats the device’s ability to communicate. When the revolution comes, if that is our future, there will be portable devices which anyone could build from easily obtained parts to detect or destroy RFID at will. I fear the day this is needed. I also say woe to those involved in the use of RFID should it come to that. End excerpted material.
There is one other thing you can do. The response time for reading a scanned RFID is very brief. There is a ‘failure’ in reading called ‘tag collision.’ When too many RFID tags of the same frequency (usually dictated by type of tag/use of tag) are present in a confined space, the scanner can fail to capture the data, or capture the wrong data. Therefore, if one were to collect dozens of RFID tags of various types and put them into a bag to carry along with them, it would effectively become a scanner blocker. Keep all your old canceled credit cards in the same wallet as your valid ones, sandwiching the new between the old, and pull them ALL out to select the one to use, holding them all in the same hand to swipe.
I also advise against Smart Appliances, and smart meters. RFID is at the heart of interaction with Smart Meters, which in turn is its own invasive privacy and stalking threat (widely experienced as a directed energy weapon). Worse, it is tied to mapping of the interior of your home; the floor layout, location of furnishings and other appliances and electronics, smart or otherwise. Programs are being developed to allow such mapping information to be available to manufacturers of smart devices and used to market to you based on use of not just their product, but all products. Naturally, all that can be accessed by government, as well… and hackers partnered with burglars.
I also suggest taking advantage of these resources as contingency against the worst:
How to war with the NWO; How to survive the NWO; and Localized defensive strategies.
The history of RFD tells all
It starts with Howard Hughes, though he was a victim, not an instigator. Most of us are familiar with his rise to being the richest man on Earth in his day, and his fall due to a mental condition which impacted his ability to interact with people, and life in general. The untold story is that once debilitated, CIA agents and Mormons (CIA likes to recruit from Mormans, and Masons, because such cults have secrets and know how to keep them through compartmentalization and other methods) became his ‘caregivers and managers.’ He trusted them, and they took advantage.
Once in control, his vast resources were diverted to CIA control and application. Hughes Shipbuilding built several spy vessels including the Glomar Explorer and companion vessel, both designed to retrieve sunken Soviet Subs. Hughes TWA aircraft and assets were diverted to form (over time) three different CIA ‘airlines,’ including the most recent, Evergreen Aviation, which wound up acquiring Hughes’ Spruce Goose for its museum. Hughes Tools, the financial cash cow of Howard’s meteoric rise, a maker of drilling systems for the oil industry, would eventually become Enron, and we know how that wound up vanishing billions of dollars into thin air. The remnants of Enron’s data processing center would be applied to CIA fronts engaged in porn (to profile user sexual preferences for possible blackmail application), web site hijacking (I was a victim of that, documented here), offshore gambling, and 4-1-9 scams (Nigerian money investment scams).
Then there were Hughes operations which would evolve to serve CIA’s efforts in Political Control Technology development and application. It starts with Hughes Aircraft’s electronics division, eventually become Hughes Electronics, which invented the RFID concept. These were originally used to identify and track cattle, marketed through Hughes Identification Devices, but also found their way into humans involved in early (late 1940s) non consensual CIA mind control projects and Atomic Energy Commission radiation experiments on civilians. I wound up with one in my leg, when as a child, when I was injected with a radioactive substance in Yakima, near the Hanford Energy Reservation.
From Hughes, the chip was migrated to Destron Fearing, and from there to our friend, Digital Angel. We will come back to them. More CIA fronts or partners duped into participation would be created in America and globally to market implants for humans. They do big business in ‘police state’ countries, often for the purpose of chipping persons in the criminal system. Of course, it is privately understood they are good for tracking anyone you wish to track, such as embarrassing political activists and whistleblowers.
LocatePLUS is a Homeland Security created and CIA infected front which pushes the implant in America and advertizes that it maintains 12 billion records covering 98% of the American Population. The DHS/CIA knows all about you and is making money selling you to anyone with the money. In America, the front markets to FBI, ATF, DEA, and 2000 law enforcement agencies, primarily non implant products such as ankle bracelets.
In Europe, the front Worldwide Information is a LocatePLUS spinoff doing much the same. Global reach far outstrips American consumption (there are a lot of fascists out there, in almost every government system): Universal Microchip in Italy, IDECHIP S.A. markets in Ecuador and Brazil, Solusat Medica in Mexico, Scientific Innovation and Integration (SII) in Korea, Taiwan, China, and Japan, Inforlexus Inc., for Malaysia and Indochina, Biometronix for Germany, Glezer Technology in Israel, and Cybertek in Puerto Rico. This list continues to grow; the Swedish firm Biohax International is behind the implant for snacks story.
The primary American front (a sister to LocatePLUS), Metro Risk Management Group, sold $13M worth of chips over 5 years to the Bonneville Power Administration (to track fish, officially). BPA is a Department of Energy firm which had in the same time frame been in the news because of high-tech spying operations having been detected taking place in their facilities… while BPA and Enron were significant others in the same bed. The U.S. Military contracted for $24M, while they sold $1M to private citizens wishing to chip their children or themselves. They sold $7M to the greater Intelligence community, and $73M for ‘internal use,’ which is to say, CIA, itself. Such orders are a combination of implants and scanner systems, both portable handhelds and installable units for security gates and doorways. A typical order might consist of hundreds of thousands of devices and a thousand scanners.
All this data represents 2005-2009. Sales are increasing over time, but increasingly hard to track for a variety of reasons, including corporate name changes, mergers, spinoffs, and other tactics often seen in CIA fronts trying to be a moving target. And the implant business is a target by activists and activist organizations worried about invasion of privacy and civil rights, to say nothing of some kind of New World Order nightmare ending with the Antichrist at Armegeddon. And, they are constantly being sued in court for a wide variety of reasons.
And this brings us back to Digital Angel, the key point in the bioimplant tracking food chain. As stated, a lot of business names and hanky-panky tactics are often employed by CIA fronts, as outlined in The Professional Paranoid, a privacy/security how to which, in covering that topic, helps readers to identify who is really causing the bumps in their night, should they be so unlucky (as was I). So let’s take a look at Digital Angel, again based on older ten-year research (I’m not going through that, again).
Let’s talk corporate names as clues: though most commonly known as Digital Angel (Florida), also DBA Verachip, they were formerly Applied Digital Solutions… which was formerly Applied Cellular Technology (because RFID tracking often relies on cell phone services)… which also used the DBA ACT Financial… formely Axiom Information Technology… formerly Axiom Computer Consultants… DBA Great Bay Acquisition Company (those all based in Wisconsin/Minnesota). Digital Angel divorced itself from Verachip (being sued out of business), but then Verachip merged with Steel Vault… which became PositiveID, which then in turn tried to acquire Digital Angel… which also operates Signature Communications in the U.K., where it might (conjecture based on company data and ties to CIA fronts) enjoy backdoor access to encrypted government radio communications, the assumption being that receiving units employ an RFID chip which, like the cell phone paradigm, authorizes descrambling of transmitted data, as well as authenticated identification of the sender and recipient. Finally, Digital Angel, also being sued and hounded, ran off to the U.K. where they now promote themselves as “a developer and publisher of consumer applications and mobile games designed for tablets, smartphones and other mobile devices, as well as a distributor of two-way communications equipment.” But they still push implants, and through Signature, the two-way communications gear.
Let’s talk facts as clues: Digital Angel does not make RFID. No. They merged with Destron Fearing, the actual imputus of modern RFID systems claiming to have invented RFID technology. No, that was Hughes Aircraft’s Electronic Division. Digital Angel at one point claimed to be founded in 1948. No, but Destron Fearing was founded in 1945, did the RFID for cattle thing in 1948. No one cited so far, actually makes RFID tags, the heart of the implant. No, that’s Raytheon, a military/CIA contractor… formerly known as Hughes Aircraft. That makes sense, since it is the U.S. Army which tracks all RFID tag assignments (unique tag number assigned to (whatever) user data). Meanwhile…
Let’s talk connected dots as clues: CIA’s HHMI (Howard Hughes Medical Institute) is steadily pushing for the use of RFID in both implant and non implant versions to hospitals (49 major facilities as of 2005, more every year) and the medical industry at large, and Hughes Satellite and Hughes Communications services RFID tracking systems via cellular/wifi. How do I know this? By temporarily working for both Hughes Satellite and a major cell phone carrier where I was able to verify specific cell phone traffic and routing of tracking data. The phone account was tied to an individual which shared an address with one of the above firms (how I found it). And that led to finding dozens of such phones for more firms. And even more looking at other fronts known to me outside of the RFID playing field. In fact, such details are part of my evolving insurance policy against ‘accidents.’
Let’s talk key people as clues: Another CIA front trait has to do with who is involved in the corporate structure. At ADS (old data) Dr. Richard Seelio was Director of Medical Applications. Really? He is a Bariatric Surgeon, so he knows how to suck fat out of your thighs, not exactly as advertised by his title (a typical front man). The Senior Vice President was, prior to installation, a small time lawyer (a cutout man). A look at the Board of Directors of almost many of the above firms variously will find persons of wealth and influence, persons with backgrounds or ties to military/intelligence (or both), and persons with membership in the nefarious NWO Round Table Groups, such as the Council on Foreign Relations, Trilateralists, and the Bilderbergers. This is a kind of corporate structure is a fingerprint that lets anyone track just who are the trackers.
The other shoe drops
As I wrote this, I was listening to radio, where Clyde Lewis more thoughtfully reviewed a greater enveloping matter on his Ground Zero show, things equally important to understand, and far more sinister. Listen to it, here. The short of it is that chipping people is not just about spying on them, it is about control. It will enable a complete rewrite of social, political, religious, and economic existence, and the script is already being followed step by step, RFID again at the core. You didn’t think ‘Global Warming’ was about weather, or that Transgender Issues were about rights, or that Terrorism was about political or religious ideologies, did you?
It is, all of it, in support of ‘a brave new world’ which the New World Order seeks to establish, a world where there are only three classes of people. While my friend Clyde did not use my labels for these classes, he did so describe: there will be Meons (a Club of Rome/Bilderberger label based on an ancient word for someone worthless, less than a peon – a ‘useless eater’ who will not likely survive the NWO on their own, and who will be made to ‘go away’ in time); Peons who will be usefully employed to run the system (government, business) for the elites; and the Elites, the 1% of the 1% who will rule.
Clyde explains how the Middle Class will be eliminated, divided between those willing to implant and deemed useful (peons), and those unwilling or deemed useless (meons), and the a host of new topics and proofs you have likely never heard of, and more. Naturally, the upper class will be peons, and the lower class, meons. Bio implants (part of Transhumanism) are key to all these plans. You had better understand all of this or you won’t be able to cope, and likely, will end up in the red list for population reduction.
A TI with RF Measuring Device can = Dangerous Conclusions
Low Cost RF/MW reading devices are often purchased by TIs as a defensive tool against their targeting fears. However, the general topic (TSCM – Technical Security CounterMeasures) is just that: TECHNICAL, and readings from such a device can easily lead a TI to panic and over react. Here is why, and how to get more out of such devices, without the risk of serious mistakes.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2017, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting. Updated Dec 2017 – Corrected technical boo boo and added a couple of closing paragraphs somehow deleted and not caught. Changes indicated with red intro. What you will learn reading this post: • all TIs could benefit from professional TSCM electronic sweeps; • that isn’t likely to happen; • the poor-man’s TSCM pro isn’t a pro, and might be a fraud; • there are low-cost meters but improper use can be dangerous in many ways; • there is a solution, and help implementing it — and here it is…The way it is
A Targeted Individual can almost always benefit greatly from a professional TSCM sweep. Such a sweep, clandestinely done, could provide significant courtroom quality proof of electronic surveillance and/or harassment with directed energy weapons or mind altering signals, such as EEG entrainment, subliminal messaging, V2S, implants, and more. If you are new to targeting and don’t know these terms, read my books. With very rare exceptions, virtually all TIs are exposed to some form of electronic targeting, and such a sweep can precisely identify who is operating the equipment, the nature of targeting, and evaluate the threat and suggest defensive/offensive options. That typically includes their providing documented reports and personal courtroom expert testimony. Combined with optional services equivalent to a private investigator, it could even end up revealing who ordered and is behind the targeting. They can also potentially detect bioimplants in the victim’s body.

Just some of the gear needed for a professional TSCM sweep completely meeting a TI’s needs.
Unfortunately, there are two reasons no TI has ever used TSCM professionals with success, and hardly any have ever used it, at all. The first reason is, that only the wealthy can afford it. A truly effective sweep of a home or work place, can cost between $20,000 and $60,000. That is because the professional will need to apply towards a million dollars worth of specialized gear, and must have decades of experience in order to be qualified to do so and have the results stand up in court. Rather than ‘meters,’ they employ sophisticated signal analyzers and other toys for a full-spectrum solution (including light and audio threats).
Sigh. Add to Christmas wish list, and hope Santa is generous.
The second reason, is that all such qualified TSCM are almost always ex government/intelligence community/military/military contractors, and are therefore, by default, subject to ‘conversion,’ because almost all targeting is ultimately at the hands of those same players. By request or by bribe, the risk is that they will give a false report showing no targeting. It is simply impossible to vet a TSCM pro against this risk, unless you happen to have a personal family/friendship relationship in place from the start. I had such a contact, and the government framed him on illegal weapons and drug charges and put him in jail, confiscated all his equipment. James Atkinson (‘Granite Island’) helped me write my first book, filling it with informative information about TSCM and what government agency uses what frequencies for what purposes (data table and other information in The Professional Paranoid). Friends are keeping his informative web site up and running for him. Visit.
So what is a TI to do? One solution, is to go with less than a true pro TSCM guy with all that gear, someone like me, perhaps, who has nearly $20,000 in gear, and some investigated skills (I’ve put a lot of people in jail, shut down illegal CIA fronts, forced corrupt officials to resign, and ended targeting for clients). Unfortunately, there are crooked people out there pretending to be ‘like me’ using even less sophisticated gear (regardless of what they claim). I have seen YouTube videos of alleged ‘bioimplant scans’ where the scanner was charging $100 per implant found, and gee… everyone scanned naturally had between three and six implants, or more — until their money ran out. And yet, not.
The problem was, the meter being used, like most such meters, has an instruction manual warning that false readings will be obtained if one touches the sensing area of the meter (the business end). You are supposed to hold them a certain way to avoid that. A fraudulent scanner, however, holds it differently, such that he merely moves his finger to tap or touch the front whenever he wants to ‘find’ an implant, bug, signal. Sadly, this service was widely promoted by one of the largest and best known TI community groups. It even resulted in a multimillion dollar lawsuit, and that group ultimately disintegrated. One clue it was a scam was ignored by all: to get the scan, you had to fly into a small remote town with all of one Police officer, check into a hotel, and get scanned within a small window of time. Poof! the scanner was gone before the fraud could be reported and investigated, and many thousands of dollars richer for a half-day’s work.

A decent start if you have something in the range of $10K to spend. It is virtually a hand-held spectrum analyzer… that unfortunately does not see military gear.
Another solution is to buy your own meter. Prices can be as low as $100, even less (be wary when so). Not quite a perfect solution, in truth, because no such product, even towards $20,000, is designed and sold for the kind of use to which the TI intends. They are designed to measure the same kinds of signals (with significant limitations, usually), but for other cause, such as testing equipment against RF emission safety standards, or to ensure they are putting out the right kind of signal. The instruction manuals only speak to such uses, and the manufacturers/sellers have zero interest in helping a TI do what they need to do with the product. Nor will they accept returns based on failures to be useful in such an application. You are on your own.
Because of the technicalities involved, and in the face of a lack of instructions, it is not only extremely rare that a given TI will know what a given reading means, but also quite likely that they will make a false and potentially dangerous wrong conclusion as to meaning, and then take wrong actions in defense of that false conclusion. A TI easily makes silly mistakes, and the results can be frightening (ex: aiming the meter at the sky will yield seriously high readings, but is NOT a threat. Many TIs assume it means satellite targeting. No, no, and no.) An example of a serious wrong action would be false accusations of an innocent party, or spending limited financial resources for shielding or legal defenses applied uselessly. And there is another common risk…
All too often, a TI will call Police or go to other authorities or perhaps seek legal, medical, or psychological professional help, meter and readings in hand, intending to ‘prove their case.’ All they end up accomplishing, is being marked down as a very strange person with a strange little box and an even stranger and unbelievable story; a lunatic who needs mental health care. No one will understand the little black box or its readings, much less the story offered behind it all. They have never heard of TSCM, most likely, and so the entire concept is like talking about the kind of propulsion systems used on flying saucers. And if they do know about TSCM, they will know your meter is a ‘joke,’ and automatically conclude that your use of it and conclusions are just as silly, no matter what the truth is.
Note: there is one other potential ‘poor man’ solution — the use of a smart phone ap to simulate an RF/EMF meter. Yes, and no. Extremely limited range and scale of operation, extremely broad angle of view, and quite prone to misinterpretation. In fact, it has nothing to do with electronic solution; it only measures the Earths natural EMF. It has no value for personal protection, as I’ve written of, here.
Don’t give up too fast… all is not lost
Don’t give up on the notion, because there are some useful uses for such meters, if approached properly. One must simply alter expectations, and have a better grounding in how to properly use low cost meters such as those described herein from trifield.com, for the purpose. I can help with that. But let’s first talk about expectations:

Implant quite similar visually (smaller) to one found in my own leg some 35 years ago. State of the art, today, can be 200 times smaller, translucent, tissue colored, and bond with tissue: invisible to a surgeon and to x-ray. MRI sees only an inconsequential image blemish.
a) you are not going to use them to find implants with much chance of success. There is only one type of implant they MIGHT find, which is the type which constantly broadcasts information. An example might be a tracking implant, or a health monitoring implant. Under the right circumstances, you might find such an implant. But most implants used in targeting are either not going to broadcast anything… instead receiving signals useless in detection — or they are going to deliberately use special broadcast methods most meters cannot see or respond to usefully;
b) you are not going to use them to find V2S, subliminal, or EEG manipulation signals. You can see these signals, but they blend into the background and do not stand out as such; they cannot be isolated and identified with simple meters;
c) you can use them with some confidence to identify DEW and other targeting signal directional sources. While it is relatively easy to misread signals and erroneously presume them an attack signal, if read during an attack and relying on the strongest signal sources, only, you are likely correct in the presumption. You can then plan shielding strategies more effectively, and narrow your list of suspect enemy positions and personnel to those within that angle of attack. With some luck, you might actually pinpoint the source and perps involved, but it won’t be legally useful. But focused video surveillance (don’t break the law), with luck, may confirm suspicions sufficiently to be considered legally useful evidence. Rely on video documentation of not just the doings at such sites, but also video of meter readings during attacks, to prepare potentially useful evidence… useful to perhaps interest someone into considering your story… knowing the likelihood is that they will still reject it as lunacy. Risk vs. Benefit is your decision guide about attempting to convince them;
d) you can use them to identify the type of signal, in some cases. They type and sophistication of the meter, and your ability to use them properly, will determine if that is the case, or not. It is quite easy to make wrong assumptions, as there are so many kinds of attack signals across a broad spectrum of frequencies (bands of RF energy). Most serious threats operate at frequencies well above the capabilities of low cost meters. Even my $20,000 gear cannot see above 12 gHz microwave, which is where most military bands operate. But if your enemy is not military based, you might have a chance with $20K gear… but with gear costing hundreds of dollars, your chances diminish to the point of being limited, perhaps, to seeing things an amateur or Cop might employ.
e) you can use them to warn of a DEW attack before it becomes a problem in terms of physical/mental effect. There is one particular low cost meter best suited to this use, allowing you to relocate yourself away from the attack area… the meter will advise when escape has been achieved (cease the warning). It will also indicate if you are being ‘tracked’ by a signal by some means (generally some kind of surveillance, or by a locating implant), and can give you a general sense of the direction of the attack signal source, much like the Trifield. It is not, however, a great substitute for the capabilities of the Trifield beyond that, but it is a better warning device than the Trifield, because it is automatic, and always operating, unless switched off. It can even clip to your clothing or be carried in a pocket, or set down anywhere near you;
 f) you can use such meters to determine if the signal levels exceed safety limits set by government and NGO organizations. This, in turn, can sometimes be used to force government agencies, most notably the FCC, OSHA, to investigate on your behalf, though it is quite likely such investigations will not match your findings; the enemy will simply shut down temporarily. But at least you get a brief vacation from assault. When concerned about safety levels, you will want to carefully review online searches to compare the latest (always being adjusted downward) standards and what a level represent in terms of health issues, and that will prove to be quite technical — you need to carefully compare your meter reading and scale used for the set limits, which may require unit conversion (usually a matter of multiplying or dividing by 10 or 100; most such resources will give you instructions for conversion or cite alternate unit results for you). With luck, your findings can be matched to specific known physical symptoms for a given reading level, which if matched to your symptoms and reading levels obtained, can be useful if well documented (video of your readings and symptoms + industry data);
f) you can use such meters to determine if the signal levels exceed safety limits set by government and NGO organizations. This, in turn, can sometimes be used to force government agencies, most notably the FCC, OSHA, to investigate on your behalf, though it is quite likely such investigations will not match your findings; the enemy will simply shut down temporarily. But at least you get a brief vacation from assault. When concerned about safety levels, you will want to carefully review online searches to compare the latest (always being adjusted downward) standards and what a level represent in terms of health issues, and that will prove to be quite technical — you need to carefully compare your meter reading and scale used for the set limits, which may require unit conversion (usually a matter of multiplying or dividing by 10 or 100; most such resources will give you instructions for conversion or cite alternate unit results for you). With luck, your findings can be matched to specific known physical symptoms for a given reading level, which if matched to your symptoms and reading levels obtained, can be useful if well documented (video of your readings and symptoms + industry data);
g) you might be able to use them to find surveillance technology, to include listening devices and cameras. Again, sophistication and skill of the user are key. There are devices better suited to this purpose which remain low in cost. Use a search engine (bug and camera detection gear) for that. Same for (phone bug detection). See my post on cellphones.
Now as to the other key requirement, proper use…
Fortunately, there are two specific low-cost devices I can recommend with confidence, and for which I can provide rather specific instructional advice on how to use them for TI needs. They are the devices I started with early on for my own needs, after some considerable informed research — and successfully used to confirm my own electronic targeting, source location, and identity of the operator at that location. It allowed effective shielding response which ended the threat, and finding of listening devices. It helped me to develop other tactics to defeat targeting which did not involve shielding. They had other benefits, as well, not the least of which was improved peace of mind.
As result, I made a special deal with the manufacturer (Trifield): they would sell them to me at a small discount for resale to TIs, and send TI requests for information or purchase to me… on the proviso (my idea) that I provide an instruction manual for TI uses, be responsible for any returns and customer service issues arising from TI uses. They did not want that business at all, and would not sell them to TIs if they understood such was their use/need. While I am no longer in a position to provide the service, which as a kind of rent-to-own trial program for which no one ever declined to own (it worked well for them), I do still offer the instructions (an emailed .pdf file, illustrated).
 These are for the trusty and versatile Trifield meter (avoid the more costly blue-faced version, generally less useful to TI needs) and SmartAlert 2 microwave detection device offered at trifield.com. Both meters are very low cost: you can buy both for less than $300, just don’t mention targeting. My manual gives broad instructional use for both meters, and additionally includes an idea on how to modify (at relatively low cost) an entire room to be a faraday cage without dramatic change in the appearance of the room.
These are for the trusty and versatile Trifield meter (avoid the more costly blue-faced version, generally less useful to TI needs) and SmartAlert 2 microwave detection device offered at trifield.com. Both meters are very low cost: you can buy both for less than $300, just don’t mention targeting. My manual gives broad instructional use for both meters, and additionally includes an idea on how to modify (at relatively low cost) an entire room to be a faraday cage without dramatic change in the appearance of the room.
I used to sell the instructions for $20, with the purchase price applied to the purchase of a meter. The idea was that one could see what the instructions were like without risking the investment in a meter, and if thinking it doable, go for the meter without wasting the $20, as I made it free with a meter if purchased outright. It was a confidence-building approach to decision making.
I also tried to talk people out of doing it by pointing out everything in this article. Only if they got past all the negatives, and still wanted to proceed, DID I HAVE CONFIDENCE IN THEIR DECISION. I needed to feel it was right, too, because I did not want a meter to be returned — a wanted a successful use of it to better the user’s targeting situation.
Since I no longer sell the meter, I make the file available on request by email to anyone willing to make a contribution to the Free Will Society, and our effort there to establish Free Will Haven, a targeting-free, low-cost, self-sustaining intentional community (learn more here). There are two ways to go: A $20 donation gets you the manual. A $50 donation gets you the manual AND membership in the Free Will Society (you must have a Facebook account, as well, to participate in membership dialogs) and an ebook copy of The Professional Paranoid, which also talks about privacy/security issues, which includes material also related to meter use as described in the introduction (frequency usage). That, alone is a $12 value. By all means, donate more, if so moved.
Note: A secondary goal of the Free Will Society, is to subsequently establish a mobile strike team with a full professional TSCM sweep capability, to include a van full of gear (image above). This would be used not only by Free Will Haven, but be able to be sent anywhere in the country to target perps covertly, and nail them to the cross, and blow the whole topic of political control technology wide open in media, and in the halls of government… globally. And yes, that means yet another million dollars are needed. So add zeros to your donation 🙂
The manual’s instructions can generally be applied to any similar products, if one simply reads between the lines, and compares the differences between meters usefully. This is true even if talking about the $20K flavor, though the capabilities will expand greatly as meter sophistication (and price) increases. Just keep in mind that an expensive and more sophisticated meter will likely require some IEEE technical expertise, such as I actually have. I even have some background in microwave technology, and signal processing as employed by the intelligence community (selling and installing such technology, as well as general security and alarm equipment).
The greatest improvement high-end gear offers will be in the range of frequencies (bands) which can be analyzed, but there are many other benefits to better units, as well. For instance, the ability log to memory the readings as you go, plug them into a computer for even more signal analysis (big step up in usefulness), and improved sensitivity in range and angle of reading. A low cost meter reads rather broadly, say 30-40 degrees of arc, perhaps more, where my meter reads as little as 3-6 degrees of arc. Most low cost meters don’t even specify, and the ‘funnel’ nature of a broad angle contributes to misinterpretations of reading importance or meaning. Narrow is good, but you can compensate by taking care and multiple readings from multiple angles (triangulate).
Finally, we need to talk about what constitutes a dangerous signal reading on a meter. These devices display information in a wide variety of formats and scales which leave a non technical person with no understanding of what a high reading actually means. It only matters and is useful defensively if and when the reading exceeds safe levels. Different kinds of signals might be deemed dangerous at a lower level than the kinds of signal. For example, pulsed microwave is the most dangerous of all, and can be so at quite low strength. This is normally the main threat a TI faces, but most low cost meters cannot distinguish between them, or measure them correctly. This is not something commonly mentioned in their specifications, and you need talk to their engineers to inquire, to be sure the meter can deal with it correctly.
As far as safe levels, there are many levels established by many agencies of many countries for many purposes. What is deemed safe in one view or situation, may not be save in another view or situation. The nice thing about the expensive meter I use, is that it knows all these limits and indicates when one or more are exceeded. With a low end meter, you need to compare your reading to the various standards. Learn more about such standards, here.
Why am I Being Targeted? A Valuable Question for TIs
Being targeted is all about unanswered, yet critical and deeply troubling questions, psychological torture being at least half the intent of targeting. The foremost question is usually ‘Why?’ or ‘Why me?’ There only three answers which matter, and they are not impossible to discern, and knowing can improve one’s ability to resist.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2016, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting. What you will learn reading this post: • there are three primary reasons why TIs are targeted; • knowing which it is can result in better defensive/offensive strategies; • it is possible to discern the difference in many cases; • there used to be a fourth kind, but what it really is will surprise you. xThe way it is
 There were three or four possibilities, and the best answer which could be offered up front was simply to cite those reasons, a generic answer which lead to no peace of mind, and which usually lead to even more difficult to answer questions. And yet, to get to the bottom of things and mount a viable defensive/offensive strategy, such questions needed to be answered; you cannot fight a problem you do not understand.
There were three or four possibilities, and the best answer which could be offered up front was simply to cite those reasons, a generic answer which lead to no peace of mind, and which usually lead to even more difficult to answer questions. And yet, to get to the bottom of things and mount a viable defensive/offensive strategy, such questions needed to be answered; you cannot fight a problem you do not understand.The Three Answers
I and others used to think in terms of a fourth factor, which at least seemed to be another category, but it is not, by and large. And yet, as we will see, it remains telling and useful. Let’s start with the big three, first.
them at a personal level. But the bulk of joyriding would seem to be experiments upon the perps.
 Many perps are themselves TIs, either actual mind control victims or persons (typically sociopaths or psychopaths) who are put into experiments to see how THEY react in a perp situation based on THEIR psychological profile and the specific circumstances of the TI-to-perp interaction/response cycle. In fact, the TI is almost superfluous to the equation, once their suitability has been determined (their profile), and considered a consumable and expendable item in the project — though controls exist to prevent such harms as might result in Police investigations which might defy cover up arrangements.
Many perps are themselves TIs, either actual mind control victims or persons (typically sociopaths or psychopaths) who are put into experiments to see how THEY react in a perp situation based on THEIR psychological profile and the specific circumstances of the TI-to-perp interaction/response cycle. In fact, the TI is almost superfluous to the equation, once their suitability has been determined (their profile), and considered a consumable and expendable item in the project — though controls exist to prevent such harms as might result in Police investigations which might defy cover up arrangements.Knowing the difference can alter TI tactics
About Death Threats
Who’s Killing the Bilderbergers?
Some 17 years ago, the Unified Conspiracy Theory was formulated. It was so accurate — it was able to predict in 1999 the 2001 downing of the WTC by jetliners and resulting Middle East Oil Wars, and other major news events. Now it can be seen at work in my newest book on the Bilderbergers — where fact and fiction collide… fatally.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2016, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or link to original posting. Upate Feb. 20, 2017 Paranoia Publishing is set to start shipping hard cover copies of this book as early as first week of March. Amazon will carry it right away. ebook copies available direct from author now at half price ($6 – will return to normal price once hard copy is available) via paypal orders to proparanoidgroup at gmail com.What led to this book? The definitive International conspiracy.
After ten years of research into crimes of the New World Order, I began to theorize that the bulk of America’s dark bumps in the night were not simply random crimes by assorted forces for varied agenda, but completely orchestrated as a single, logical, step-wise plan toward a single, yet visible goal. It resulting in the Unified Conspiracy Theory, and it was reasoned that if one knew the goal, and the steps thus far taken, such a plan was predictable, and as a theory, the ultimate test would be to do just that.
The first three predictions made with the UCT were so scary, that I had to take actions, do something… anything I could think of, to attempt to thwart them. The first was, that some kind of terror event would bring down the WTC with jetliners, and result in a series of Middle East Oil Wars. So, in the Fall of 1999, knowing no authorities would bother to respond usefully, or quickly, I published a quickly written screenplay featuring such a plot, and put it online with explanative warnings, hoping against hope it might force any such plan to be aborted. No such luck, of course, even though Oliver Stone’s people took a look at the script in search of a project. They thought it an impossible ‘false flag’ scenario.

The second UCT prediction was an assassination attempt on 1992 Independent Presidential Candidate H. Ross Perot, or his family, in order to force him out of the Primary run against Clinton/Bush. I took no chances, and this time, notified the Secret Service of my concerns, expecting they would ask me for details. I used my backchannel contact, someone I had worked with before on several Treasury matters. Some several weeks later, Perot did back out of the election, even though the very night he did so, he had won enough votes to be guaranteed a place on the General Ballot. A few weeks after that, my SS contact confirmed that an attempt had been made just before the Primary, against his family; mailed Anthrax. That has its own telling ‘false flag’ backstory.
The third was that there would be at least two more major false flag attacks to follow, specifically naming the type of attacks, and the cities. One of them was my home town, which I had predicted would suffer a bio-terror attack, and I even identified the means of delivery and rogue CIA Fronts to be used. But by the time frame where that might become a more current concern, I had finished my book set, Fatal Rebirth, which spelled these things out quite clearly, again hoping it might spoil any such plan. I also took steps to notify the City.
Again, no useful results, but fortunately, knowing such details enabled me to personally thwart that attack, or at least postpone it. It is featured on this Blog’s home page. But I was definitely able to thwart second, different terror attack in the same time frame, likely a Plan B to the former. It was called Gas Station Tasking when announced by President Bush; the use of private planes to dive bomb the area’s largest gas station while a tanker truck was offloading gasoline, at the busiest time of the street traffic day. This is also detailed on the home page.
This could easily have taken out two gas stations, four restaurants, two banks, two two hotels, and potentially, two major shopping complexes, and the traffic on the busiest intersection in the County, plus a major Interstate and two State highways. Identified, were two of FBI’s Top Ten Most Wanted Terrorists, and others, including the Christmas Tree Bombers. They were getting help from an FBI Agent known to me, and so, as it was a false flag operation, FBI, CIA, FAA, DHS, in response to my going public, never asked for my evidence, which included fingerprints, video, multiple eye witness confirmations, and more. The cover up was started before the President even heard about it. See home page.
Why UTC matters to this new book
Other UTC predictions have since come to pass, as well. The reason this is all mentioned here, at all, is because the UTC does not just affect America, it relates perfectly to World affairs, as well. And in this world, we have various Round Table Groups of Globalists who push for a One-World Government, which is to say, elements of the modern-day Illuminati. Such groups as the Tri-Lateral Commission, the Council on Foreign Relations, and the Grandaddy of them all, the Bilderbergers, and many more (even United Nations, World Bank, et. al), all tend to be cut from the same New World Order mold.

This image relates to one of two strings of real World International murders footnoted in Who’s Killing The Bilderbergers, as cited in this book. From http://humansarefree.com/2016/06/mainstream-media-finally-admits-mass.html
Which in turn is to say, largely fascist, all-too often satanic, and decidedly power elitists seeking to rule the World through manipulation and control of (everything), and willing to do so at any cost, by any means. Not to go overboard, it is important to note that, with the exception of the Bilderbergers, most Round Table Groups, like FreeMasonry, attempt to draw in newbie membership who are completely innocent Sheep. This gives surface viability and credibility of these groups to mainstream in ways which allow them to mask the darker roles they play in seeking the Globalist rule, while also giving fresh students to draw into their world, especially the more successful up and comers. There is a backstory there, as well, as I have first hand knowledge, x 2 telling examples, having been such an up and coming business man.
Ergo, this new book is designed to do much the same thing as Fatal Rebirth; to warn you just what these people are doing, and why… and why you should be mad as hell about it and doing something to stop them. Only, my new book is global in scope, where Fatal Rebirth concerned itself only with America. And, while Fatal Rebirth began unfolding in 1947, Who’s Killing the Bilderbergers is a current-day affair. As such, it is perhaps more urgent, that you read it, and soon — because the future is revealed to be bleaker than the Dark Ages and time of the Inquisition, for those not forewarned and forearmed.
The plot thickens
I describe this book as ‘an International Novel of Novel International Affairs.’ A grand murder mystery across multiple Continents, trying to resolve mysterious death after death of prominent Globalist leaders. Are they simply random deaths by happenstance, or murders by elaborate design? Officially, they are not due foul play, and yet… each one has many unanswerable questions clouding that view. Just as troubling, their deaths seem to be tied to various strange conspiracy theories, while at the same time tied to various Globalist agenda, either narrative affording motive for murder. And, of course, it is soon enough discovered that they all turn out to be Bilderbergers.

Each Bilderberger tends to be an Officer or Board Member of multiple corporations, and has sway over yet others through major stock holder positions, or contractual agreements. Of course, many of these companies, in turn, control other companies, sometimes, long lists. Now, imagine what this Cloud Map would look like if we knew the actual identity of ALL Bilderbergers, and not just this handful. Then add CFR, Trilateral Commission, Club of Rome, Council on Foreign Relations, and on, and on; the Round Table Globalists; the modern-day illuminati.
By the time the truth of the deaths starts to be uncovered, the UTC will have started to reveal itself in action. In like manner to UTC’s ability to be predictive, readers will be propelled quickly into the future, headlong into the one final prediction which is the ultimate form of fatal rebirth… for us all. That particular prediction WILLmost certainly come to pass; it has, after all, been foretold by many authors well before my time. Among them, Satanist and high Mason, Adam Weishaupt; it is the entire purpose of and predictive goal of the Illuminati Plan, as he formulated it in 1776, when the group started their journey toward a New World Order (he first coined that term).
As this book reveals, just when it comes to pass, is largely up to you. You, are what you’ve been waiting for. They hope you don’t know that, and remain Sheeple.
An important detail
And, along the way to that story-ending element, readers will also encounter countless real-World conspiracies laid at the feet of Bilderbergers, all done in ways which let the individual decide for his or herself, which, if any, may seem fanciful, and which are more likely true. There is much documentation within the main body, plus more than 150 footnotes (an average of one every page turn), to help that process along. Some of those footnotes are illustrated graphically. The Climax and Ending will then show you the progressional nature of the Globalist plan as it unfolds toward the very last step in the plan, the point of no return for Mankind. These conspiracies back up the UTC usefully, and in fact, understanding them helps refine the UTC more usefully; one tends to validate the other, in both directions.
Smart Meters, Stray Voltage, and Targeted Individuals
There is a little known and underreported TI targeting method and symptom based on Stray Voltage, which is usually marked by a dramatic prevalence of ‘static discharges’ when touching things. But there are other symptoms, and happily, tests and cures.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2016, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or link to original posting. What you will learn reading this post: • What stray voltage is and why it can be a threat, especially for TIs; • The symptoms and risks of stray voltage (and targeting); • The possibility of yet another Smart Meter conspiracy; • How to detect and eliminate Stray Voltage.Stray Voltage?
 Stray voltage is the technical term given by the power and electronic industries to a situation where an electrical charge is present in the ground, itself. It can also be present in a structure, such as your home or workplace. It tends to be far more likely to be present at the ground-floor level than upper floors, and is commonly found present at insignificant levels almost anywhere electricity is used. It can even be found in places where there is no AC power nearby present, at all, if there is Quartz bearing rock in the substrate. Concentrations of Ferrous rocks and ground water near the surface can impact, as well.
Stray voltage is the technical term given by the power and electronic industries to a situation where an electrical charge is present in the ground, itself. It can also be present in a structure, such as your home or workplace. It tends to be far more likely to be present at the ground-floor level than upper floors, and is commonly found present at insignificant levels almost anywhere electricity is used. It can even be found in places where there is no AC power nearby present, at all, if there is Quartz bearing rock in the substrate. Concentrations of Ferrous rocks and ground water near the surface can impact, as well.
In structures, the type of structure materials and design can impact prevalence, as can furnishings and the layout of property. And though considered rather rare as an actual problem, for some reason, it is normally thought of or understood as being significantly more problematic in rural farms (especially noted in dairy farms) more than in bedroom communities, though it can be found even in downtown high rise areas. It seems to impact Cows in many observable ways, to include reduced milk production, troubled births, general health and premature deaths.
The power industry takes great care to prevent stray voltage levels from being detectible or able to impact living things, including you and me, but things can go wrong. When that happens, and depending on how strong it ends up being, it can be quite detectible, and generally, unpleasant, if not harmful or even dangerous. Some forms are capable of outright electrocution, such as created by downed high-tension power lines. While this post uses the term Smart Meters in the title, it is less about that, except that a possible conspiracy may exist between Smart Meters and stray voltage, as outlined below.
There are many reasons stray voltage might be present at problematic levels. I see these as divisible into three threat levels and causes. The first may be relatively minor in threat level, caused by natural eventualities unrelated to targeting, and unlikely to escalate in nature. An example might be living near to high-tension lines running parallel to metal fencing on your property, where a kind of induction takes place causing the fence to produce an electrical current.
The second is also unrelated to targeting in causality, but may be far more serious, even dangerous, and quite likely to escalate — such as may due to electrical shorts or combinations of other unhappy electrical happenstances. The important thing to take away is that the bulk of stray voltage may have nothing to do with being targeted, but any presence which is detectible should be of great concern to anyone, and pinned down immediately.
The third? I have recently discovered a new possibility, thanks to a coincidentally… even accidentally discovered set of facts learned from one of my very first TI clients. I say coincidentally, because in considering the new information, it dovetailed very nicely with other client information which had otherwise led nowhere. As result, I am now quite confident that there can be deliberate targeting by artificially creating and controlling stray voltage for the purpose.
It can be used to establish a variety of selectable threat levels and targeting effects (symptoms), to include other forms of electronic targeting. This level is not officially recognized to exist by the power industry, though the potential for conspiratorial knowledge and participation in its use surely exists. One would be unwise to broach the possibility with power companies or other parties, unless part of a legal response effort, as mentioned herein. The good new is, that regardless of the three types, any serious threat levels can be dealt with, almost always.
To weaponize AC power in this way (there are other, previously known and frequently spoken of ways, such as found in my book, MC Realities), simply requires shunting of power to the earth at one or, as is more likely, multiple locations around the property. This would likely be done through a control mechanism to throttle the voltage diverted, even to an ‘off’ position, something akin to a remotely controlled dimmer light switch. Naturally, it will consume significant electricity, and that will turn out to be a blessing, as we shall see.
After reading this short introductory post, a TI would be well served to learn more about the topic, even if not thinking themselves impacted by stray voltage, currently. As the link to that information only addresses the first two reasons, the reader should indeed finish this post, first. After reading BOTH sources, then, and only then should they attempt to fit their circumstances into the dialog and consider the best course of action. Feel free to contact me if unsure, at proparanoidgroup gmail com.
Symptoms, regardless of cause
At natural ambient and other low levels of stray voltage there should like be no outward signs discernible. We only need worry about the phenomena if we do start to sense effects. We have all experienced the random static discharge of touching a door knob after walking across a carpet. While discounting such experiences as carpeting woes, they can also be due to stray voltage, which can certainly augment or simulate carpeting-caused static build up, as not all carpets generate the problem to the same degree, or even at all. When you get such discharges in the absence of carpeting, that is a typically a clear sign of stray voltage — though cold dry air can contribute, as well.
Note: normal static discharge is usually relatively high in voltage but low in amperage, quite akin to that associated with spark plugs in an engine; unpleasant to experience, but relatively harmless, more likely to cause injury from jerking away with violent contact with another object, than from the actual shock. They may generate a small visible flash of light, an actual spark jumping a few millimeters, at most. But stray voltage can produce far more varied and dramatic, even dangerous results. There have been instances of seeing discharges which travel inches or even feet, making zapping or popping noises, producing heat. The risk of fire and explosion cannot be ignored, where flammable fumes or pure Oxygen sources might be present. Obviously, the voltage levels in such cases are even higher, as may be the amperage and risk of electrocution.
 Serious levels of stray voltage can cause effects similar to other forms of electronic targeting, and may indeed be augmenting such targeting from other sources. In point of fact, especially for persons who also suffer electro-sensitivity, there is a small chance that some persons who see themselves as being a TI may in fact not be. Accidental, or even natural stray voltage might be causing enough symptoms of targeting, by itself, to erroneously presume targeting. This would be good news if the individual is not also experiencing non electronic targeting symptoms, such as organized stalking, or other forms of harassment.
Serious levels of stray voltage can cause effects similar to other forms of electronic targeting, and may indeed be augmenting such targeting from other sources. In point of fact, especially for persons who also suffer electro-sensitivity, there is a small chance that some persons who see themselves as being a TI may in fact not be. Accidental, or even natural stray voltage might be causing enough symptoms of targeting, by itself, to erroneously presume targeting. This would be good news if the individual is not also experiencing non electronic targeting symptoms, such as organized stalking, or other forms of harassment.
Electronic targeting symptoms are radiographic in nature (radio and electromagnetic), and therefore, stray voltage symptoms, would typically be some combination of any number of things which match those same symptoms. The range of symptoms is broad, from headaches, nausea, dizziness, mood swings, sleep problems, sensations of burning, tingling, vibrating, tinnitus or humming sounds, as well as more unpleasant physiological symptoms such as heart palpitations, chest pains, muscle and joint pains, fibromyalgia-like conditions, twitching or trembling, and so forth. Arguably, there are other symptoms, as well, but these are the more commonly reported ones, and the easiest to identify as being abnormal. That said, the caveat is valid: don’t presume a system does not have a medical explanation; always see a Doctor (without talking about targeting) to make sure you do not have a ‘simple’ health issue in need of treatment.
In fact, stray voltage can simulate or stimulate a variety of general health problems in humans and animals, alike. When doctor’s tests find no other explanation, stray voltage (or other electronic targeting) may be to blame. Some animals are more able to sense stray voltage and will naturally avoid areas where it exists in undesirable levels; they can be ‘Bird Dogs’ to the problem by strange behaviors or health issues. High levels of stray voltage can also cause plants to die, or may result in random discharges between objects otherwise insulated. By way of example, a visible mini-lightening flash between an automobile and the ground or nearby fence or garage door frame.
The interesting thing about stray voltage is that its effects may be amplified by humidity and moisture, or even temperature. Therefore, such effects might tend to be more noticeable if walking in the rain or while wet, as when exiting the shower. Serious stray voltage could make swimming pools and standing water dangerous. But even relatively harmless but noticeable levels of stray voltage can be dangerous, because whatever is causing them could be capable of sudden and unexpected increases to dangerous levels. Take no chances, and deal with it right away, if symptoms are present. See below.
Smart Meters and stray voltage; a possible new conspiracy

The cover story for the hazmat-like wardrobe used in Smart Meter installation is ‘arc flash’ protection, yet no such precautions are needed for ordinary meter installation. In the UK, the protection is even heavier duty than this; suitable for sci-fi spacemen.
A lot of people, including many TIs, feel that the entire power industry’s move to Smart Meters is a Big Brother and/or industry conspiracy. Like most good conspiracies, there are multiple theories involved, ranging from price gouging to spying to mind control, and more. But the big concern and commonality in many of these theories tends to include the very same health issues as found in stray voltage.
Yet when the industry itself, as well as third-party independent testing firms investigate, most such studies indicate smart meters are no more dangerous than your computer’s wifi connectivity. I’m quite unconvinced about their conclusions, but I also understand how conspiracies work, and how the intelligence community thinks — and specifically, how they think about and employ mind control tactics.
It dawns on me as result of the dichotomy between the reality of Smart Meter user experience and test results, that there may be a conspiratorial answer which explains the conflict. Once a Smart Meter is installed, perhaps Big Brother comes along and uses the Meter to establish stray voltage. That would account for the health effects and higher bills, and certainly still enable spying and mind control capabilities.
The simple fact is, the studies giving a clean bill of health to Smart Meters are only testing the meters and the air waves. They are not testing for stray voltage. So, if you have a Smart Meter and are experiencing Smart Meter woes, perhaps you ought to test for stray voltage. If you find it exists, you will undoubtedly be advised by a lawyer that you have an excellent actionable case against the power company.
Note: It has been discovered that the power industry, in order to address public distrust of smart meters, is instead apparently installing meters which look identical at a glance to the old mechanical meters, but which conceal a ‘trojan horse‘ Smart Meter under the skin. They are, however, supposed to be easy to spot. TAKE NO CHANCES, and check YOUR METER, today, even if an ‘opt out’ user. And, if told you were not getting a Smart Meter and discover a trojan horse, you once more have a reason to contact a lawyer, and the media.
Stray voltage as targeting weapon
Deliberately causing stray voltage as a harassment tool is not the only ‘advantage’ to perps. Because electricity can carry embedded RF signatures, it can cause an entire area, such as a home and its yard, to become a kind of transmitter of other forms of targeting signals, just as can house wiring. It can therefore become a kind of amplifier of such methods. But to employ it requires something which should ideally be relatively easy to detect, and defeat.
Simply shunting your existing AC power to ground, a deliberate ‘short,’ if you will, is NOT normally going to be done because the power bill would go up dramatically, and tip the victim off that something was amiss. Therefore, the perp would need a second electrical service on site, which means a separate meter head, which they then ‘weaponize’ for the purpose. In apartments, it might simply mean using a neighboring unit’s meter. In a home, it may mean a separate power line to a concealed meter somewhere on the property or just outside the property line. It may be an underground service, even if the property is otherwise serviced by an overhead feed.
In an apartment situation, all the meter heads for a group of units are mounted at the same location, and labeled as to address/unit. If suspicious, you can wait until a high consumption power period (i.e., using your stove to cook), and then go look at the meters. If you do this when you see signs no one is present at the suspect neighboring unit (not using their stove), but their power meter is drawing more power — you may have found proof of the method and the perp.
In the case of a single domicile, simply call the power company and ask if there is more than one meter assigned to the address, or if there is a meter or extra meter assigned to neighboring lots. If the answer is yes, ask if any extra meter is in use and being billed, or if you might be able to acquire the meter for your own use (to justify why you ask). Any extra meter may be proof of the method and, with some legal steps, lead to identifying a perp.
Proving stray voltage
 To confirm any such targeting, you will need to prove stray voltage is present, the same thing which should be done if symptoms are present and targeting is not involved. There are three ways to do this. One is to call the power company, which has a legal liability to insure stray voltage does not exist, in the same manner that natural gas providers must worry about gas leaks. Another is to call an electrician. Either of these methods can also result in identifying and curing the source cause of stray voltage. It will likely be up to you to document their findings, such as with video or witnesses — though they may be willing to provide written documentation where they bear no liability risk. Again, you probably should not mention targeting concerns to these people.
To confirm any such targeting, you will need to prove stray voltage is present, the same thing which should be done if symptoms are present and targeting is not involved. There are three ways to do this. One is to call the power company, which has a legal liability to insure stray voltage does not exist, in the same manner that natural gas providers must worry about gas leaks. Another is to call an electrician. Either of these methods can also result in identifying and curing the source cause of stray voltage. It will likely be up to you to document their findings, such as with video or witnesses — though they may be willing to provide written documentation where they bear no liability risk. Again, you probably should not mention targeting concerns to these people.
The third method is less useful in terms of evidence unless you are an electrical engineer or have similar credentials validating the quality of your findings; you can obtain test equipment and test the matter yourself, again documenting every step as you go. It is not quite as simple as the illustrated image, and should involve more than one kind of instrument. The procedures will vary depending on where you need to test, and what the location is like or contains in the way of objects and surfaces. The entire property should be assessed, and if done usefully, will ‘map out’ zones of impact from high to low. More information on the ‘how’ is available online, including that link you should read after finishing this post.
Regardless of which method used, where targeting is suspected, know that the power can be turned off remotely as soon as any perps involved discover testing is about to take place. This means you will want to covertly order any such tests, and ideally, try to find a way to avoid having whomever shows up to conduct the test show up in a marked truck, and having them quickly first test somewhere out of sight from any possible perp surveillance position. THAT is the hard part. Doing that yourself is much easier, of course.
Impact, conclusion
If you are a TI or suspect same, I urge all readers of this post to comment as to their findings or conclusions upon further investigation. In two and a half decades of contact with 12,000 TIs, I have only known of perhaps three or four cases where stray voltage was in any way evidenced. As result, it appears to be an entirely ‘unknown’ targeting method (assuming such was the case). I have only recently been made aware of the possibility that a power company can have two different meter heads assigned to a property under two different account names WITHOUT the property’s owner/renter’s awareness, even though BOTH are in use — by SOMEONE.
It can only serve the greater TI community to learn if this is more wide spread than thus far observed, especially given that it can be easily detected and defeated if and when in use. Ditto because of the advent of Smart Meters, in which case this new information may be a very useful weapon for use by activists against the power industry, and legal pressure (lawsuits) by user-victims. It is equally important because where targeting is not involved, education on topic may lead to resolving a potentially deadly stray voltage of less sinister origin, and address final cure to otherwise unresolvable health issues.
And, in closing, let me state it once more. Any instance of serious stray voltage, even if not related to targeting, likely represents an actionable legal issue; you should consult with a lawyer about suing the Power Company and/or whomever pays the bill on any secondary meter head causing the effect, or any otherwise weaponized meter head.
TI Defense: 30 Tips to Help Fight Back
If there is one thing I’ve learned after having contact with 12,000 Targeted Individuals over some 25 years, it is that without help, they have no good chance at properly dealing with their targeting. There are many reasons self help fails, and yet the solutions are not that complex.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2016, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or link to original posting.The TI dilemma
I have never met a long-term Targeted Individual (TI) who did not have the same generalized and massive array of problems. The easiest victims to help were those who had only recently become aware of targeting, as their problem list was much shorter, making defensive solutions easier to derive and implement. But for everyone else, the list of issues was, well, mind boggling. I would see it in the very first communication (typically email or letter). It would be as if a letter about life from Lil Abner’s (by Al Capp) character, Joe Btfsplk, who never had a good thing happen to him or anyone around him.

Note: I am no longer in a position to offer such personal helps. I do still offer a free Helps Kit by email which is useful to the TI in multiple ways, and I’ve written many how-to books on topic which are quite detailed and useful, to date still the only ones of their kind, as far as I am aware. I am still open to email contact at proparanoidgroup at gmail com, and can field simple generic questions, but I no longer engage in situational analysis and tactical advice, investigations, or direct intervention. This post is intended to help take up that slack.
That first contact would be pages long, typically, in story telling mode, and full of unhappy emotion, a hard thing to read; both in terms of eyestrain and emotional drain. Paragraph after paragraph of one problem or targeting issue after another. There would be a long list of events and suspect perps (perpetrators). It would commonly entail problems with their job, their family, their church or other membership, their neighbors, the cops, the legal system, the medical system, their financial situation, their computer security, and more, to include actual targeting symptoms impacting their health, and at times, the health of their pets and their plants.
The effects would be physiological, emotional, mental, and in some cases, impact physical objects. It must have been even harder for them to compose it, than for me to read it. Each such effect might entail a variety of individual symptoms and clues as to cause. Oddly enough, typically NON OF IT IS USEFUL in providing helps. Their valiant and painful plea for help ends up being little more than an exhaustive rant in terms of value in a practical investigative analysis. The ONLY way to tackle targeting usefully, either as a helper or as a victim, is to start completely over, which is why the Helps Kit was evolved; it started over in a way which simplifies, organizes, and quantifies useful information.
A Detective investigating a crime does not want to hear the long drawn out account of the victim up front. They start with a GENERIC description of the nature of the crime from the Cop on the scene (who did get that account from the victim), and then they INTERVIEW the victim with SPECIFIC simple questions aimed at nibbling away at facts in order to find the ones which represent CLUES. “What did you see? What was said?” and so forth, each question hopefully suggesting another. They then use the answers to solve the crime. A good model for helpers and TIs, alike. A flood of data drowns the truth, but point-by-point realizations build toward it.
There is another problem. While their described symptom or effect may perfectly match a known Political Control Technology (PCT) or method, it is also absolutely true that each and every example could also be due to a natural medical situation, or have a simple but yet as unknown social, or financial cause. Since authorities and professionals who are the natural ‘go to’ for help prefer not to believe in the Boogey Man, the assumption is always that a natural cause is to blame. A wise TI would do the same, seeking to eliminate any such possibility.
Failing the wisdom creates more problems for the TI, even when the go-to helper cannot find the natural cause or address it, because it is next easiest to blame the TI for the problem, even to the point of accusing them of being a paranoiac schizophrenic; the easy out. For the record, when working long term with a TI, I will in time discover the truth, and the truth is, purely imagined targeting among those reaching out to me has proven quite the exception. But some might be delusional, of course, but I’ve also learned that persons with mental issues are often selected for targeting in training projects, so that any serious mistake by trainees will be far less likely to draw interest of authorities, who will make the assumption the whole thing was imagined.
The bigger problem

Targeting: The covert Elephant in the Room which must be devoured if to well survive, but HOW?
As result of all these things, a TI is faced with so many problems, and so many clues, that they can literally find themselves immobilized by confusion, unable to reason it out, or even unable to cope. And yet, there is always one more problem, far more serious than the rest: they do not understand the truth of their targeting situation. I’ve never known a long term TI who did not have a false belief as to the nature, cause, purpose, source, and method of their targeting. This is by design, a primary goal of targeting; to create a false belief structure which makes it impossible to defend against, because defenses will be aimed at the wrong problem.
This further makes easier another primary goal, to make the victim seem crazy, either by their reactions being seen as paranoiac, or by telling others things deemed insanely impossible. But to underscore, the biggest problem is that their defenses will not meet the need, resulting in failure and frustration, a tool for their tormentors. So, finally, they come to me in a desperate state, not just in terms of needing help, but in terms of simply needing someone to listen to them and actually believe their story.
No one should presume a TI’s story to be imagined or fake, though it is true there are some who pretend for ulterior motives. In time, the truth will out. But because of their failure to truly understand the nature of their targeting, they might have been led to believe almost any untrue thing which cannot be seen as rational. For instance, one victim (who was schizophrenic, as well) believed they were beset by Alien vampires. In truth, the targeting was evolved against the person because they had discovered a firm involved in illegal dumping of biohazard materials, and to insure that her story was not believed by authorities, they led her to so believe. They relied on her schizophrenia to protect them from discovery both as perps inflicting mind control, but as criminals violating Federal law. The schizophrenia, itself, made that easier to accomplish.
How to eat an Elephant
The old saying is, one bite at a time. Here are the bites, a series of axiomatic advice points presented in a somewhat stepwise manner, the same things I would normally work through with every client. Remember, only you can decide any risks involved, and take the wisest course of actions based upon those perceived risks. This is merely a guideline of what has worked well in the past, and is generic in nature…
- Acknowledge your belief structure has been manipulated and you do not likely truly know the who, what, why, and how of things; you have been deliberately mislead. Following this guideline should help address that flaw, but only if you remain open to the possibility. Educate yourself about PCT and know your enemy, and always seek and eliminate any possible alternative explanations — but also keep in mind the pitfall cited at this post’s end;
- Be wary of professionals which we should otherwise rely upon, such as doctors, lawyers, dentists, and private investigators. Most will either walk away or take advantage of you on the assumption you are crazy, or worse, seek to have you evaluated by mental health professionals. The best strategy regarding that, is to seek an evaluation on your own: a written clean bill of mental health can be a wonderful defense if eventually accused of being delusional, even if by authorities. If you must find a professional, including a therapist, your best bet is to go to a city at least 50 miles away, and find a relatively recent graduate (i.e., a lawyer new to the Bar), of some minority race. They are likely to be hungrier for work, and more anxious to do a good job, and less likely to have had their morals corrupted over time by the industry. Avoid saying you are targeted, just tell them your concern and enough facts to get their interest. Answer their questions, but where a question requires an answer which gets into targeting details, give the details, and offer no presumption of cause, even if asked. Let THEM make that conclusion on their own, or not — it should not change how they perform for you;
- Cops, on the other hand, will either instantly so peg hole you, or worse, turn out to be in place assets working with the enemy against you. If you MUST do so (as in reporting a crime), or if you choose to become a TI activist or otherwise ‘go public’ (includes any Web presence), follow the advice found here;
- Start and maintain an event log. Use a voice activated (VOX) recorder kept on your person to make verbal notes describing questionable events, suspect persons, vehicles, etc. Leave it on to capture events directly, automatically. Transfer this at days end using headphones, to a computer spreadsheet or database file. It should include Time, Date, Location, Description, Details, and your emotional or intuitive thoughts at the time as to what it might mean. Compare new events of the day with older events, looking for patterns, frequent appearances of the same person, vehicle, etc. With respect to persons, give them a ‘code name’ based on their appearance or behavior until able to acquire their actual name. For vehicles, do get plate numbers, but since plates can be replaced or stolen, also note vehicle damage, stickers or decals, and the like. This will help you get closer to the truth of your targeting, and may be useful as evidence at some point;
- Remember that if you have a pattern in your life (such as going to work the same general time of day along a given route), so do others. Do not be concerned in such routines to see others around you repeatedly, because other people also have routines which may overlap with yours. DO be concerned if seeing the same person/vehicle at disparate locations and times when out of routine, and especially if also noted while in routine;
- Establish site security at home, and to the extent possible, work. My book, The Professional Paranoid will help, but in general, you need to insure no door, window, or opening can be accessed from the outside, even with a key, without breaking and entering. Perps don’t like to do that, because it leaves proof you are not imagining things. The only entrance that should be key accessible, should be via a pick proof deadbolt lock. Put one on your garage door, as well. If you can, install security lighting and a video monitoring system. Protect rooms and entrances or items with simple alarms, and employ and document any trip traps you set per the instructions in my book;
- Establish computer security AFTER site security. Backup all files, wipe the hard drive, reformat, reinstall OS, set new password, reinstall apps, restore files. Discard wireless keyboard. Disconnect from Internet. Buy cheap used iMac and set it up to be a local server, connect it to the Internet with Web sharing turned on, connect your main computer to it. Download a Web security monitoring utility to run continuously on the Mac, check it daily. Reset your router/modem to factory specs, install new password. Repeat this process and reset and all passwords regularly, do not use same PW for all. Consider to join the Free Will Society, a closed Facebook Group I maintain (application is via the Helps Kit mentioned in the Note near page top), or any of the many public TI Groups on FB (I am member of many);
- Improve personal security, starting with phone. NO CELL PHONE IS YOUR FRIEND. Keep it in a foil pouch, turned off when not in use. Where that is not practical, remove battery and install only to check for calls to make calls, or other use. If a smart phone, there are a number of apps I suggest you install. Mobile Justice from ACLU; an aircraft tracker that sees transponders; Spectrum Analyzer and/or EMF Detector; RSOE EDIS notifier; iTriage health advisor. You MUST disengage certain features. Cary a camera ready to go (not cell phone) and voice activated recorder to document events. More advice in my book, including land lines and general bug detection;
- While observing (3,4), avoid trying to deal with the sum total of the problem. It becomes a matter of ‘too many clues,’ per the introduction of this post. Instead, choose any ONE. Then review all others for any which seem related, aligned, supportive, or opposing, and set them aside for study as a subset. Analyze these, alone, formulate a means to prove or disprove each clue, and based on those results, validate, reject, or find the subset unresolvable, and move on to the next subset;
- You MUST presume any physiological symptoms are potentially actual health issues and seek a Doctor’s advice. When doing so, do NOT mention targeting, but it is OK to mention external symptoms (pets, plants, etc.) as might possibly be related. Pursue any suggested treatments until no treatment proves useful. ONLY THEN will you know the truth, and be closer to true understanding of your targeting, andy you may actually improve or cure actual health problems as well. Along these lines, anything you can do to impact your physical, mental, and psychological well being is to your good — become a health nut and try everything that claims a benefit, as everyone’s situation and physiology is different, but products seldom attempt claims of addressing targeting effects; you won’t know until you try it — but try only one new thing at a time, or you won’t know which is responsible for good outcome;
- Deal with Gangstalking. Very simple. Ignore it. It is only there to jerk your chain, and that only happens if you allow it to happen. You can choose not to be upset, worried, etc. Document it, yes, but laugh at it and them for wasting their time and money. This is simple in concept, and yet hard to do because of human nature. Stop, Think Act, practice, practice, practice;
- My book MC Realities offers a very good review of how to detect, identify, and deal with PCT. Once a better understanding is obtained from he previous steps, you can start to defend yourself more usefully with these trial and error methods, which should give you some good specific truths about your targeting. In general, we worry about implants, which can include voice to skull (V2S), Directed Energy Weapons (DEW) which cause physical harms, mood/sleep control; and other electronic tech which can also account for V2S. The precise defensive/offensive tactics will vary to type and specifics. Shielding is almost always the best defense, but there are so many factors that the easiest thing to do is to shield an entire room for a few hundred dollars, but other methods should be tried first, as that is where the targeting truths can be learned. Where there are problems still encountered, feel free to contact me;
- If your targeting involves pain inducement DEW, or you have actual medical conditions which cause pain, ask me for my Jedi Mind Trick, the best way to describe a method I have developed which allows one to mask pain with nothing more than the power of their mind. It is difficult to master and requires practice, but once mastered, it is easy to apply, and for some users, it can also turn your body into an EMF meter for advanced warnings of attacks, and has application to general problem solving, including the issue of true understanding of the targeting’s nature. I use it to eliminate pain from toothaches (a Molar who’s roots were growing through my gums, into my mouth, and into my cheek), burns, fibromyalgia, and even tinnitus, and I can use my hands to find power lines in walls, as well as microwave and EMF sources. Demonstrated it many times;
- Once defensive efforts are well in hand, there may be some significant offensive opportunities. These are outlined in my books. Should you think any are appropriate, feel free to run your ideas about implementation by me for fine tuning or other commentary;
- As a rule, a TI has no concrete knowledge of the reason why they are targeted. Exceptions tend to be incorrect, as earlier mentioned. Knowing the who and why us the key-most truth, as it can sometimes lead to establishing a blackmail insurance policy. This key can sometimes be discovered in memories. Go back in time in your mind to a point roughly six months to a year prior to first noticing your targeting. You would be looking for some odd or unusual event or thing overheard or seen. It might be an argument or a document or a conversation which, at the time, did not make much sense to you, but stood out as unusual in some way. Almost always, it is a work related memory, especially if your work had some relationship to government, intellectual property, high finance, or high profile legal matters; the sort of place where conspiracies and dark crimes might hatch, take place, or be evidenced. Should you find such a memory, contact me for general advice on how to verify its usefulness and take advantage of it;
- Where defense cannot be well achieved or maintained, relocation can typically buy several weeks to months of temporary relief. Often, simply going mobile can offer at least partial, if not full relief for a time, especially when not in your own vehicle, and leaving behind all personal possessions (new clothes, luggage, etc.) and taking no phone, NOT CALLING ANYONE, visiting online accounts, or purchasing anything on a card. For a more permanent solution, consider residency at Free Will Haven, a targeting-free self-sufficient and low-cost intentional community project of the Free Will Society, which is based on tiny homes living. I myself have been living quite comfortably in about 120 square feet (excessively tiny) for the last three years, and am quite content to do so, sacrificing little in the way of lifestyle, otherwise. Again, an application is contained within the Helps Kit mentioned in the Note near page top.
- Be prepared for local, regional, national, or even global social turmoil, be it disaster, civil unrest, martial law, real or false flag terrorism, revolution, race war, or political or financial upheaval. PCT has been being ramped up in terms of victim numbers (some estimates place the national number as high as 12,000,000) and individual intensity. It is my belief that the reason so many people are being targeted and the targeting is increasing, is we are heading to a crescendo designed to amplify any crisis turmoil in order to enable a shift in government form, all in the name of restoring national security and social order. Arrange to have a 90 day supply of food and emergency supplies and basic tools. Leverage your preparedness with a visit my special Facebook pages and review each post found there: the Post Apocalyptic Library of portable survival how-to knowledge; the Post Apocalyptic Local Area Defense Network, especially useful to TIs even without a crises event; and the FEMA, Martial Law, Revolution Database;
- Consider dropping off of the Grid; escape the Matrix (there is an actual matrix involved), perhaps even with a new identity. This is seldom possible while still being targeted, but the attempt, if done properly, can buy you significantly more targeting-free time before you are reacquired. This two-part post can help.
Additional advice
There are also some common mistakes that TIs make which can be avoided. Oddly enough, almost every TI has already made them, and yet, tends to continue making them, failing to see the risk they pose until till late. Here is a summary list, but remember, there are no hard and fast rules. There can always be an exception. If you think you have encountered one, contact me for review to see if I might not agree, or why not.
- NEVER seek help from authorities or ERTs due to targeting, itself. If an actual injury or crime is involved, such as vandalism, death threat, theft, etc., by all means report it, as having it on record can be useful evidence of targeting for possible use at some future point — but do not mention targeting concerns, and once more, follow the guidelines found here. If questions are asked as to why someone might undertake an action against you, you CAN mention that there have been strange things happening and you might choose one or two examples, if asked to cite them, but state you have no understanding as to why anyone would do so, and that you have no suspects (even if you do). The last thing you want is an investigation which concludes you are mental, which is where it almost always will end up going the moment you deviate. It may be wise to apply this rule to friends and family, and certainly to co workers, as you can end up destroying relationships with disclosure. The only exception should likely be limited to those living with you, and even then, you will pay a price. I lost a wife and a foster daughter to it, and possibly another daughter;
- NEVER react to targeting stimuli if you can avoid it. Train yourself to Stop, Think, and ACT, do not REACT. You, STOP yourself from reacting, THINK about what they are trying to cause you to do (i.e., get angry), and the ACT contrary to that in some random manner. This both negates the purpose of the targeting, and causes perps all manner of concern, either about the validity of the psychological profile they had prepared on you in order to determine the best targeting methodology, or the operational reliability or skill of any equipment or perps involved. This can at times lead to dramatic increases in targeting efforts, but if you continue the ploy, it will lead to them trying to ‘repair’ whatever problem they think is the cause. That typically results in a small rest period of no attacks. Eventually, it can destroy the effort entirely, especially if this method is applied by someone in early targeting, as it prevents them from advancing to other kinds of targeting, or they advance and abandon the failing method(s). This, and use of the Jedi Mind Trick, and numerous blackmail insurance policies (each time I created one for a client, it protected me, as well) is how I have managed to negate nearly three decades of attempted targeting and its consequences; I do not consider myself a TI, because I keep winning;
- NEVER be overly concerned about death threats, being followed, or about gang stalking events, it will simply make you wax paranoid, and be seen as such. The people who engage in PCT would simply kill you, not threaten you, if they wanted you dead. Unless a threat was quite specific and included a warning that you should do or not do something, ‘or else’ vividly described, it has no basis in any real threat. If you get a threat with such a basis, that basis must represent a clear and present danger to THEM, in order to be valid. Telling you to stop being an activist, or stop investigating why you are being targeted, does not count, unless perhaps, you have gotten to the point where you can CLEARLY identify and prove with legally useful smoking-gun caliber evidence the who, why, when, what and who of it. In such a case, you have the makings of a blackmail insurance policy which can not only counter the threat, but force capitulation and even remuneration for your troubles at their hands. That was how I ended my first targeting, and was offered $40,000 per my demand. It has become the model for all client help efforts ever since. Being followed or gang stalked is merely a jerk-your-chain tool that goes back to Stop, Think, Act. The only real danger is in giving into it. The only targeting which is a real threat is PCT based on electronics of one kind or another, chemical or biological assaults, physical abuses (i.e., rape, beating, accessing you while you sleep), and dirty tricks which impact finances, relationships, reputation, and the like;
- NEVER presume another TI, TI activist group or organization, or general Web resource to know what they are talking about regarding PCT or solutions, for the likelihood they have it right is very low. Take it with a grain of salt, and tuck it away for comparison to other resources. Books are a far better bet at getting at the straight dope. Older books will by now have a reputation establishing usefulness. Avoid newer books or other sources by anyone claiming to be an insider, ex intelligence operative, or other ‘expert,’ as they are likely providing disinformation to insure you continue to fight the wrong problems;
- NEVER hook up with another person, especially another TI. There are many reasons this is important advice, and I assure you that the risks you undertake with even a casual date or one night stand is significant. I see it play out again and again. Rare is the TI that can better their circumstance by not living alone, and a sexual adventure is far too easily a set up opportunity of one kind or another;
- NEVER pay money to anyone offering implant scans, ‘scientific’ testing, or new age solutions without EXTREME CARE; it is likely a scam, even if there are YouTubes or personal testimonies, the likelihood remains high. Research, research, research. Even if you actually did locate an implant by some method, the number of people able to have an implant removed can be counted on one hand; the medical industry will not cooperate. I have yet to see any positive results from testing services or new age approaches, but if you want to submit a chemical sample to an actual laboratory for chemical or spectrum analysis to find out what it is, that is worth the time and money;
- Avoid participating in poorly conceived TI activist efforts to outreach, or outreaching directly yourself. By poorly conceived, I mean an effort which does not heed the advice employed here. At best, such efforts defame and set back the TI movement and each person associated with it, labeling them as mental. Many of these efforts are designed and promoted by perps, and used as a kind of ‘evaluation survey,’ especially those asking you provide personal histories or statements. If legitimate, such statements will tend to seem crazy to anyone not already believing that targeting is real — adding another ‘crazy story’ to a stack of them will not change their minds.
Other facts to consider
The following may temper your views in seeking full understanding and formulating defenses. Simply keep them in mind when reasoning things through.
- Many perps are themselves victims of mind control, typically the worst kind, the Monarch/MK Ultra kind. They know not what they do, literally; they are programmable people based on multiple personalities which can be triggered at will. While some perps are psychopaths, these, are not, though they my be controlled to exhibit the same behavioral traits;
- You may be such a programmable person, yourself, and like them, not be aware. If such a person, and also targeted, you represent some form of ‘failure’ in the programming, and the targeting is designed to neutralize any damage you might cause to the program if you become fully aware of your true situation, which is a real possibility as you work through understanding and defensive efforts. The important and terrible truth is, that such a person will sabotage their own daily efforts in this regard, and make no progress whatsoever. Such a person will likely exhibit many additional symptoms as found in my book, MC Realities. Most notable among these is a question or belief they were targeted or abused as a child, or themselves have abuser thoughts or have so abused. Should you come to suspect you are a programmable, you should contact me for special advice too complex for this forum;
- All PCT is Satanic in nature, origin, and intent. Your enemy is as forecast: Powers and Principalities, and there is scientific proof available. Therefore, your best ally is religious faith, and the best faith for the purpose is Christianity, and the best Christian Church (because it is acknowledged to hold closest to God’s Word in the original Greek and Hebrew translations) is the Wisconsin Synod of the Lutheran Church. There is a whole chapter in my book, MC Realities, which explains exactly why this is true in both practical and Biblical terms;
- You will hear it said all the time, that TIs fear they are being murdered, or that they have been murdered. THERE HAS NEVER been such a case. Being a TI can certainly mean to be suffering in great pain, and it may certainly to some, at times feel like it has the potential to kill. But thus far, the only known deaths of TIs have been from suicides or accidents, or natural causes such as old age or disease, according to official records. While it is true that there are ways to fake such deaths and such ways are known by our enemies… and it is true that some potentially deadly illnesses such as cancer may be caused by targeting… death is NEVER the goal. They invest perhaps a quarter-million dollars a month on a full-time TI. There is no point in killing off such an investment. So the only deaths which bother me are the suicides, because that kills not just the person, but effectively the soul, as that is the only unforgivable sin; a sin against the Holy Ghost. If you give in to it, you are surrendering to your enemy, Satan, not just the perps. I am in communication with literally dozens of persons who have professed to have been being murdered as far back as 1992 or so, and they are STILL HERE, some of them still making the claim from time to time. Only two out of 12,000 are known to have died, one of old age and disease, and the other in a traffic incident;
- There is no place one can go where targeting is not likely to follow within weeks to months, save one or two foreign countries. The only one of these that has been verified by multiple TIs, is Ecuador, which to me does not make sense, but it seems to be true, with three such instances reported to me personally from TIs I had vetted as legitimate TIs.
Why Stand Alone in a Crisis? Join the P.A.L.A.D.I.N.s
What will happen if a natural disaster or social upheaval comes and government cannot, or will not be able to defend you, your home, or your community? When armed marauders or looters come, will you stand alone, or will you have your own local network of helpers: Paladins?
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
copyright © 2016, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or link to original posting. Reading this post you will learn… • there are disaster and upheaval threats not even government can always quickly address; • individuals cannot well defend against marauding gangs and other threats in a crisis; • Paladins (modern-day ‘Knights’) may be a simpler, easier, safer solution than Militia; • Paladins can be useful at any time for humanitarian missions of their own devise; • Paladin Units (unite) can protect each other, their communities, and beyond, as needed. What is a Paladin?
What is a Paladin?
“Paladin” is another word for Knight, a kind of soldier of good moral character who in times of Olde served his fellow knights, community, country, and God. P.A.L.A.D.I.N. members are similar, and yet different. They are somewhat modeled after the Paladins in the popular Fallout computer game series, but THIS IS NO GAME. Fallout takes place in a future post apocalyptic World where there is no government, and everyone is struggling to survive, which literally means at times, kill or be killed, perhaps even eaten by others. Several groups compete for control with lust for power as their agenda, but the Paladins were formed in an attempt to maintain order and protect against such threats — a bit like self-organized Police the people come to rely upon.
Almost no one is truly prepared for disaster or civil upheaval. When it strikes, the impact of the disaster is therefore nearly total. All one has to do is look back on Katrina, or any other major disaster or upheaval around the World where local governments were unable or unwilling to respond — to see the value in not having to stand alone in a crises. FEMA and other government ‘help’ in Katrina was less than ‘useless’ for an extended period of time, actually causing more harm than good in many cases. Local law enforcement was either unavailable or, at times, a serious threat to many a resident’s well being. Likewise for the National Guard.

Is this you? No go bag, emergency plan, store of supplies? No guns and ammo, survival skills? No hope, no future?
In such events, local governments at any level collapse and become non existent in domino fashion, while regional and national governments play political waiting games. The following is a quote from From Disaster to Lessons Learned: What Went Wrong in the Response to Hurricane Katrina?
The Dissolution of GovernmentAs noted earlier, disaster response in the U.S. is predicated on a system of “cascading failure,” in which successively higher levels of government are called in as lower levels are overwhelmed. However, the system requires some government to be in place. When the storm hit, local government in New Orleans, for all intents and purposes, ceased to exist. Both politicians and administrators had evacuated prior to landfall, and what little structure was in place was immediately rendered ineffective. The severity of the disaster also paralyzed state government and stunned federal government officials. A period of many hours passed before coherent calls for help began to travel up and down the system; even then, they were generally unfocused and nonspecific. Mayor Nagin’s media appeals for the federal government to “send everything” were heartfelt, but were so general they were difficult to act upon.
Meanwhile, at higher levels of government, a political showdown was brewing between the White House and Gov. Kathleen Blanco of Louisiana. Louisiana’s National Guard was heavily deployed to Iraq at the time of the storm, and the governor had activated pre-existing agreements with other states to “borrow” National Guard troops prior to landfall. These troops were quickly moved to the area, but the White House wanted to federalize the troops, while Gov. Blanco wanted to keep them under state control. The White House also disputed the timing of the governor’s request to release active-duty military troops into the area, although later evidence showed that the request had come much earlier than initial White House claims.
Even once on site, FEMA and National Guard, et. al., cannot be everywhere at once, and they cannot solve all the problems and threats people face. In some cases, policy or needs dictates result in harm to individual residents, mostly unintentional, but at times, intentional. In the end, almost everyone needs to fend for themselves for a protracted period of time, and that often means defending themselves from each other, or facing general extreme hardships or death, alone.
In Katrina, nearly 2,000 died, and many died at the hands of others (including authorities who opened fire on crowds trying to escape across a bridge). There were, in addition to looters and aggressive authorities, at least one known roving gang of vigilante Whites who had set about to kill Blacks they deemed looters, ‘loosely defined.’ The true number of murders is unknown; few records were kept given the mass casualties, but ‘bullet riddled corpses’ were not hard to find. Where there is no law, lawlessness ensues.
Bad things happen
Disasters are all too common, some worse than others. But imagine an outright siege caused by insurgents, racial violence of the sort this country has recently seen, or even military invasion such as foreseen in Operation Lion Dance; where Chinese flood into America via the Canamex rail system, hiding in container cars which can be parked on any rail siding in America from a laptop. Or perhaps it is simple revolution or civil war born of irreconcilable political differences. There are many such threats, none of which are especially likely, but all of which are specifically possible.
P.A.L.A.D.I.N. stands for Post Apocalyptic Local Area Defense Information Network; the core organization. Do not let the gloomy sounding name deter or fool you. While it certainly could be a possibility that doom and gloom awaits us on a regional, national, or global scale (it is after all forecast by virtually every religion and many experts in military, financial, and political circles), any simple disaster or localized upheaval can result in a crisis government is unable or unwilling to address quickly. It is even possible, some believe, that government might become the cause or actual threat themselves, such as in a military coup. But if having Paladins available to help you fend off a crises in a post apocalyptic tragedy, how much better then that they could be available in a lesser threat, such as a killer quake or storm?
Here are just a few such threats — do you have everything in place to survive? Will you, alone, be able to defend them from those who do not? Or will you be waiting for government to get around to attempting to rescue you, not as a soul in need of help, but a mere politically acceptable (expendable) statistic should they fail?
• Sudden Poll Shift — a sudden shift could melt the ice caps and cause serious globally felt quakes • Sudden Ice Age or Ice Cap Melt — choose your favorite scientist and worry with them • Super Volcano — doomsday shroud encircles the planet killing all crops, causing ice age • Super Earthquake — hundreds of thousands or even millions could be homeless and helpless • Asteroid Strike — we’ve already had nearly a half-dozen near misses in the last twenty years • EMP Attack — total loss of all things electric, throwing us into pre industrial age • Solar CME Flare — same as EMP attack, but potentially global in impact • Planet X — we know it’s coming soon, its effects upon Earth could be catastrophic • Nuclear or Bio Terrorism — could render an entire region helpless • Pandemic — we keep coming close to having one, it’s only a matter of time • Financial Collapse — what happens when money has no value or is unavailable? • Civil Insurrection — race war, revolution, response to Martial Law, gun seizure • Military Coup — a top U.S. General has forecast it possible • War or Nuclear War — no nation is immune from invasion or sneak attack • Alien Threat — leaders of several nations and scientists have said it possible • Prophetic End Times Tribulation — seven years a mix of the above, or worseThe P.A.L.A.D.I.N. concept is simple, and addresses an important question: is it better to stand alone trying to protect your home and family against armed marauders or other dangers seeking to take what you need to survive from you, even your very lives… or to be prepared? Prepare a go bag and survival supplies, by all means, but to become a Paladin is to pre establish a local mutual defense network which can protect you and yours, your fellow Paladins, your community, and by extension, your country and way of life. P.A.L.A.D.I.N. is a non militia solution that can effectively become functional equivalent of a small and focused militia — on demand. It does not suffer the overhead and commitment of a militia, nor the political tainting.
Paladins may also elect to engage in general humanitarian missions at any time, for any reason or cause; actively active activists. This includes the possibility of providing aid to stalking victims, the homeless, or anyone being unfairly treated by another group in some way which cannot be well addressed by local authorities. It can even mean choosing to side with civilians against authorities in a non violent protest; whatever the Unit deems appropriate. Were I a Paladin near to the tribal protests in the Dakotas over the oil pipelines, I would have urged my Unit to give on-site support, for instance.

Armor wearing Paladins standing guard in Fallout 4, by Bethesda Game Studios (fallout4.com)
Everyone should join!
Anyone who has much to loose if accosted by armed strangers in a crises should join. Stalking victims and other persons who have experienced unusual targeting should definitely become a Paladin. This will enable you to call upon other Paladins when threats return, and help to document, prosecute, or thwart such targeting. Activists should join Paladin, as it becomes a tool useful in a cause, where you can make good argument to fellow Paladins to engage with you — and enables protection should those opposed to your cause elect illegal harassment campaigns against you (target you). Minorities and others who are consistent victims of gang harassments should also join, as it provides yet one more ally and strengthens your ability to stand against aggression, especially in rioting. Ex military should definitely join as an alternative to a Militia, which often has a bad PR image due to a political or religious bent they may have assumed. All are welcome.
To be a Paladin does not require ownership of a gun, but it is ideal. To own a gun does not require good training or a military background, but it is ideal. Weaponry and combat skills are only important WTSHTF big time, and most gun owners do know how to handle themselves, and they also tend to own more than one weapon, which means that in a pinch, they can share, teach, and lead. The primary requirement is to be of good moral character and to care about your family, your community, and your country. The rest will take care of itself; unity is the key factor.
P.A.L.A.D.I.N. Units of 6 or more Paladins are formed in any given Zip Code once at least half of the members do have arms, and at least one of them has some military or leadership background suitable for acting as Commander. Such leaders are provided with tactical advice on formation and operation of their Unit, and given contact information for any adjacent Units. Paladins can then call upon each other to request aid, or to propose missions to aid others. There are provisions in the formation of Units which allows local Units to join up for improved functionality, and for like hookup with Units in other communities, should regional operations be necessary.
Membership is by default anonymous except between Unit members and adjacent Unit Commanders, but that does not mean members must remain secret. Indeed, public evangelism and recruitment is encouraged (promotional materials will be made available). There is no membership fee to join. However, once a Unit is formed, a small annual membership fee determined by the Unit can be assessed to help fund missions or enhance emergency response capabilities. There can be some small personal expense in order to facilitate Unit functionality, such as the purchase of a Walkie Talkie by each member.
Each Unit is autonomous and stands alone in responsibility; it is not a political body or under the command of a national head, such as myself, even as founder. Therefore, there is no legal liability or risk except for those actions the Unit itself elects to undertake. I am not bound by your actions, nor are yours dictated or bound by mine. You serve only your own Unit member’s best interests and mission goals for public good, and remain subject to all laws in the doing, each member insuring the next does nothing which threatens Unit integrity or viability.
There is no political leaning or bent, nothing which should alarm authorities. In fact, Units should consider making themselves available as volunteers to authorities as emergency helpers or, where law enforcement has such programs, reserve deputies. In such a case, each member is free to participate or abstain, which is generally true in all missions. Units should be prepared to submit to lawful military or law enforcement once order is restored in a crisis, and should maintain records of all actions for use by any needed law enforcement investigations after the fact. That serves both as protection for the Unit and members, as well as a means to prosecute evil doers who may have been confronted by the Unit. Everything is above board and transparent within the Unit, and as private or as public as the Unit itself elects.
TO JOIN: simply email your interest to join to proparanoidgroup at gmail com and provide your City, State, and Zip. This does not obligate you to anything. This will be used to update a database of members maintained anonymously at my Facebook page for the purpose. That page is organized in a way which allows determining if a Unit can yet be formed in a given Zip — your evangelism in recruiting other members is key to that eventuality.
Once a Unit can be formed, members are so advised and connected to one another for the purpose of determining if they should form, and if forming, deciding who will be their Commander. They are also provided with additional support advice on how best to proceed as a functioning unit. Once forming, individual members are then obligated only to commit to the goals established by the Unit for mutual self defense and whatever additional good they may do for community and beyond, in or out of crisis (missions.) Risk and investment are minimal. Rewards can include the possibility of continued life, liberty, and pursuit of happiness — in the face of dire circumstances bent on preventing same.
Other material to consider
 The Post Apocalyptic Library is an important collection of life-saving information commonly beyond the average person’s current knowledge base, and which will NOT BE AVAILABLE once disaster strikes. It is a series of links to critical information which can be learned online or downloaded and printed for placement in a go bag or emergency supplies for later use. It is advised that extra copies should be made in advance for handout to others.
The Post Apocalyptic Library is an important collection of life-saving information commonly beyond the average person’s current knowledge base, and which will NOT BE AVAILABLE once disaster strikes. It is a series of links to critical information which can be learned online or downloaded and printed for placement in a go bag or emergency supplies for later use. It is advised that extra copies should be made in advance for handout to others.
The FEMA, Martial Law, and Revolution Database is a collection of materials which seek to educate the public about individual risks and likelihood of events beyond their control, and/or give advice on how best to survive or react. It is an eye opening review of little known facts which may prove quite sobering. Don’t be yet another Sheeple caught totally unaware.

Dropping off the Grid: abandon the Control Matrix. This author has done so for the last three years, and though living a rather spartan life by comparison to what came before, the freedom is enhanced, and the quality of life (happiness) with it. Living simply has proven to be more satisfying — and should be much safer in the event of major troubles. Here is a snapshot of possibilities. I will soon be offering a Seminar or other promotional venue (i.e., video) on the topic.
An Intentional Community is one way to live off the Grid. Here is one example, a low-cost, self-sufficient community based on tiny homes, a project of the Free Will Society I founded to helped stalking victims: it is called Free Will Haven. It has a gofundme. Such a community is by default more or less the functional equivalent of Paladins.
Terrorist H. Michael Sweeney’s RAP Sheet
OK, it’s true. There are at least a half-dozen ways the government can ‘claim’ I’m a terrorist. YOU TOO, for that matter. But I have a Record of Arrest and Prosecution ‘sheet’ to illustrate one of the ways I am definitely a terrorist to someone, including people that think I’m merely a conspiracy theorist. I am not ‘mere,’ at anything I do…
by H. Michael Sweeney proparanoid.wordpress.com proparanoidpress.com proparanoid.net
copyright © 2016, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Please comment any such repost to original posting.
What makes you a terrorist when you live in a Police State?
Simple answer: anything you do. There have been so many Constituion trampling Acts of Congress and Executive Orders, all so vaguely worded as to allow the broadest of interpretations, that it is almost just that easy for someone in government to label YOU (and certainly me) a terrorist. That can have very unfortunate consequences, depending on who labels you, why, and what they do about it. You can end up on the no fly list, or some kind of watch list, or even be vanished forever by Men in Black whisking you off in a black van.
One such example is, that being a conspiracy theorist automatically makes you a terrorist according to FBI. That’s bluntly stated, but true, as an article at Public Intelligence illustrates: “A flyer from a series created by the FBI and Department of Justice to promote suspicious activity reporting states that espousing conspiracy theories or anti-US rhetoric should be considered a potential indicator of terrorist activity. ” The flyer, linked in the article, specifically includes 9-11 Truthers (that’s about 1/3 of the U.S. population).
OK; I’m a conspiracy theorist, or if you prefer, a Conspiracy Terrorist. But I am no ordinary ‘theorist,’ because I have a R.A.P. sheet… a Record of Arrests and Prosecutions. And here it is, below the FBI Fellon ID Card (which shows that not even FBI always gets the right man)… but be sure to read the summary text before you wonder why I’m still walking around freely.

R.A.P. Sheet, H.Michael Sweeney
1976 Wire Tapping, 2 counts, charges dropped for insufficient evidence
1980 Embezzling, charges dropped after resignation from company
1983 Counterfeiting, Drug Smuggling, sentenced
1984 Wire Tapping, charges dropped for insufficient evidence
1985 Shoplifting, 4 counts, sentenced
1987 Fraud, Embezzling (pretending to be a Pastor), Bad Checks, charges dropped after restitution
1988 Wire Fraud, 3 counts, sentenced
1988 Smuggling, 2 counts (bioweapons, diamonds), sentenced
1990 Espionage, Interception of Electronic Communications, charges dropped by NSA intervention
1991 Bank Robbery, 4 counts, sentenced
1991 Wire Tapping, 4 counts, cold case due to flight to avoid prosecution
1992 Fraud, 3 counts, Witness Tampering, 3 counts, Withholding Evidence, 2 counts, Murder,
cold case due to flight to avoid prosecution
1993 Breaking and Entering, 2 counts, Grand Theft, charges dropped after restitution
1994 Wire Tapping, cold case due to flight to avoid prosecution
1994 Attempted Murder, 12 counts, case turned over to Internal Affairs, and dropped
1996 Espionage, 3 counts, Violation of Civil Rights, cold case due to flight to avoid prosecution
1998 Wire Tapping, Stalking, cold case due to flight to avoid prosecution
1998 Grand Theft Auto, Operating Chop Shop, 3 counts, sentenced
1999 Possession of Controlled Substance with Intent to Sell, sentenced
2001 Bioterrorism, Attempted Assassination, investigation closed by DOJ intervention
2002 Terrorism, 4 counts, cold case due to flight to avoid prosecution
2004 Bioterrorism, case closed due to lack of evidence
2004 Cyberterrorism, Hacking (of CIA’s Web site), charges dropped in exchange for services rendered
2016 Armed Robbery, 2 counts, cold case due to flight to avoid prosecution
2016 Bank Robbery, cold case due to flight to avoid prosecution
Summary Judgement
By now, if you actually read the full list, you realize no one person could be guilty of all those crimes and still be walking free… and that there were crimes on the list immediately after incarceration, and no jail breaks to account for that. This is because these are not crimes that I committed, but crimes I have investigated and exposed, or helped expose and prosecute, often working with Police, FBI, SS, and CIA, sometimes working against rogue elements of those and other agencies, even spy agencies of other governments.
Left out of that list, are perhaps 200 Stalking, Wire Tapping, and Torture cases I’ve worked on as online consultant with victims of such affairs (I’ve had contact with 12,000 individuals in that kind of predicament). I left them out because it would have made the post unreadable, and that’s a shame… a disservice to the thousands of victims of this form of abuse of power and conspiratorial corruption of principalities and powers.
So I do not claim to be a mere terrorist, but to have stopped terrorism. But neither am I a mere conspiracy theorist, because many of the conspiracy theories I’ve investigated have put people in jail, or at least shut them down and forced them to run away. One Governor, possibly two, a National Guard General, an elected County Sheriff, two Police Chiefs, a Criminal Investigation Division Lt., a C.E.O. of an international software firm, and a host of lower law enforcement personnel have all vacated their posts (some being jailed) after I finished doing my thing. While I cannot claim every one of them retired or otherwise departed their posts because of me, as I was not allowed access to official internal documents, I’m fairly certain a good number of them grumbled my name under their breath on the way out the door.
All that said, I hope that you, dear reader, have come to understand that a conspiracy theorist is no different than any other standard investigative force of a more official nature. Except for two small things, we all try to fit the available evidence with the environ of facts to determine the truth. We both form hypothetical postulations as to suspect and motive, prove opportunity and method, and try each point of evidence against all others which might disprove the hypothesis (though as we see all too often, many criminal cases are happy to prosecute the innocent if they think they can make a strong enough case and hide the truth).
We both theorize up front. The first difference is that conspiracy theorists do not have the luxury of making an official determination, while the official investigators do. The second difference, and most important, is that we start with questions regarding failures in logic in the official findings and reports; we question government, which is not only the right, but the DUTY of every citizen, always. How else will you ever find a cover up? We know there have been all manner of cover ups exposed in media over the last few decades, and I remind you, you NEVER have a cover up UNLESS there is a conspiracy, because a cover up itself REQUIRES a conspiracy to execute it, and the affair being covered up is always so complex that it, too, MUST by default represent a conspiracy. Guaranteed.
OK, FBI, come and cuff me… unless I’m wearing a bomb like other terrorists,or have run off to Mexico to escape your ‘justice,’ in which case, just have a better day.
FCC to Kill Local Television as We Know It
Once more, we see the Federal Government usurping power in ways which both benefit the big corporations at the expense of personal freedoms and financial viability of citizens. This time, it’s the FCC, and not the BLM, and they want to eliminate any chance for you to watch local television without paying through the nose for it… and suffering de facto censorship.
by H. Michael Sweeney proparanoid.wordpress.com proparanoidpress.com proparanoid.net
copyright © 2016, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Please comment any such repost to original posting.
FTC to Kill Local Television as We Know It
Tuesday last, a little heralded announcement by the FCC once more revealed how controlled mainstream media is. They, more than anyone, perhaps, should have been screaming the news from the rooftops, and complaining about it, as it affects EVERY major and secondary television station in every market across the country. The ramifications are so broad and sweeping as to threaten the very social fabric which defines us as a nation. In summary, the threats are as follows:
- Eliminates all local television service as we know it today, virtually ELIMINATING ALL OVER THE AIR BROADCASTS. No more ‘free TV.’
- All licenses by FCC currently in place are cancelled, and ‘up for sale,’ they want to raise 60 billion dollars which will be unaccountable funds off the FCC budget. This means they can be spent on any black project without any accounting.
- Major stations (e.g., your local ABC/NBC/CBS/FOX affiliates) will be paid many millions from the sale, far more than the stations are actually worth; hush money not to protest, we must presume.
- Secondary stations, including repeater stations or small unaffiliated stations in deep rural markets, and even possibly PBS, will be paid NOTHING, a virtual THEFT, and possibly, a loss of all public broadcasting systems!
- All will be sold to Cable and Web content providers, forcing consumers to get any TV by paid subscription or on-demand purchase.
- Significantly eliminates local news coverage, limiting it to official sources only; the government’s preferred message, a form of censorship which effects de facto mind control.
- Stages the FCC for total control of Web content under the new ‘authority’ it declared for itself last year; easier to censor and dictate what you can learn if there is only ONE resource and it is controlled by government.
It follows the Fascist model: The plan is insidious beyond belief once fully understood. It is perhaps no coincidence whatsoever that it follows Obamacare. If one reviews history of the quiet takeover of nations by Fascists and other dictatorships, those ‘bloodless revolutions’ always start with the complete takeover by government of all health care, followed next by takeover of all media. What follows is usually great financial and social upheaval allowing significant draconian responses, to include something along the lines of Hitler’s Brownshirts and the SS, and a permanent war footing with an expanded military and military police state. But people never learn by the mistakes of history, and there is plenty of that…
It happened that way in Germany, Italy, and in South America, it happened again and again. In each and every case, the takeover steps were quietly initiated and never fully understood even by those involved in enacting the changes. In every case, they inflicted greater hardships socially and financially upon citizens than those woes they claimed would be addressed thereby. In each case, a central power figure emerged who responded with ‘law and order’ and bypassed, neutered, or altered the form of government to a Fascist regime.
Unfortunately, any and all of the current Presidential candidates, save one, could fit that bill in this author’s opinion. Trump appears to be a closet fascist, Cruz appears to be one of the same old gang of criminals who brought us to this point in the first place, Bernie is a closet Communist, and that awful woman is simply a criminal rapist of nations and peoples. But my opinions are unimportant. Even if whomever is elected is not set to be a fomenter of fascist revolution, the power elite who manipulate politics will simply assassinate them or blackmail them to assure the desired outcome.
Naturally, like most draconian moves by government, the official propaganda is worded exactly the opposite in tone to the reality. That’s why we get Bills that actually accomplish the reverse of their title, like ‘Affordable’ Health Care Act. Believe as we say we do, and ignore what we actually do.
Take a look at FCC’s official page, here.
Now, lest you think me simply another lunatic conspiracy theorist, I got my first wind of this plot, to include all points cited herein (save my opinion on SOME of the candidates), from a conservative call-in radio show where the station owner of a secondary market called in to shout a warning and explain exactly how it was rape and pillage of the television industry and the public in favor of Cable and Web bigwigs. I don’t make anything up; I don’t have the time nor inclination!
Related articles
- Big Brother FCC Plans Internet Tax/Controls What Happens in Homes (universal free press)
- FCC No Longer Just Big Brother, Now Big Parent (huff post)
- FCC Sparks Fears of Big Brother in News Room (fox nation)
Proof Eight: Shooting Lines Also Depict Cheops in 3-D Cutaway View
The Great Pyramid in Egypt is one of the Holy of Holies to Masons and some Satanic cults, and is specifically tied in mysticism to the End Times and historical catastrophic events. This one will scare you.
Are there any patterns in mass shootings?
by H. Michael Sweeney proparanoid.wordpress.com proparanoidpress.com proparanoid.net
copyright © 2014, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Please comment any such repost to original posting.
Is there any proof mass shootings are not random?
What you will learn reading this post of the posting series…
• that select shooting lines form a 3-D perspective view of Cheaps and transparent depiction of all inner passages; • that there are specific ties between Cheops and the goal of the New World Order; • that Cheops is a kind of key to understanding European Illuminati/Templar relationships to mass shootings.Are mass shootings by intelligent design?
Proof Eight: Shooting Lines Also Depict Cheops in 3-D Cutaway View
Is there a mass shooting conspiracy?
Mysteries of Cheops
In the prior post we saw ties between shooting event lines which formed Masonic and Satanic symbols, and a series of orange lines which led us to the Great Pyramid, Cheops, in Egypt. While those were quite remarkable and sufficiently consistent to defy any chance of random coincidence, what follows will dramatically make concrete the notion of intelligent design as well as the importance of Cheops to said design. And finally, we will see there is yet another way to look at Cheops’ roll in the Illuminati/Templar and mass shooting tie-ins, but this time, from the European point of view.
First, we need to understand a bit about Cheops and its importance in mysticism. There is so much which could be said that there are literally countless books on topic which could be entered as ‘evidence.’ Here, I will focus on less than five percent of such material topically, only able to skim the surface of them. Consider it merely to whet your appetite to learn more, for which some suggested links will be provided along the way.
One key aspect of Cheops is that it is rich with magic numbers. This seems to be true regardless of if using the original units of measure employed by ancient Egyptians, or modern day equivalents. Indeed, some of our current units of measure stem directly from the ancient Egyptian measuring system, a fact often laid at the feet of Freemasons and their predecessors, the Masons. While I won’t spend time expounding, many of the measurements of Cheops, both in original and modern increments, enjoy magic number properties, doing so in ways which, like those illustrated in the prior post, are mind boggling. Some serious mathematicians have found even more wondrous relationships to both the ancient and modern discoveries of Man well beyond any possible knowledge to Egyptians of old.
Perhaps the keymost aspect of Cheops which potentially makes it ideal for inclusion in mass shooting patterns is that it is only the Giza Pyramid which has a complex of inner passageways and rooms. Early mystics and even some studies of Cheops by persons with scientific credentials and methods, have proposed and illustrated a belief that the construction of Cheops was an enlightened project involving supernatural or mystical knowledge of the future; the internal passages and chambers thought to be a roadmap to End Times and key events along the way. That is represented by the image, below, from this interesting Web site. Others out there (with less useful images) have more detail with the most recent/current annotation being the year 2010, roughly the height of mass shootings. That marking is in the King’s Chamber, which implies ‘control and authority.’
Of specific interest to mass shooting research and the notion of Illuminati Masonic Warlocks being the architects, thereof, is the fact that shooting lines can be found which quite correctly depict a pyramid across thousands of miles of the United States. More than this, they quite usefully do so in 3-D rendition, even to the point of detailing the inner passageways found in Cheops. In fact, the depiction is so uncanny as to have key aspects ‘to scale’ with measurements which work math magic using modern increments of measure against the ancient’s units of measure; not just scale in size, but across the barriers of time in the expression of numbers in different languages and cultures. Take a look:
Do the pyramids really relate the entire history of the World from beginning to end?
Shootings depict Cheops
Left: perspective transparent view; Right: inner view of interior passages. Remarkably, it took only 9 shooting lines, and 14 shootings, to depict the pyramid and passages. However, 5 shootings stand alone (not on lines), meaning 9 are, giving us again the magical 99/18 result.
As you may recall from the prior proof the orange lines are lines which run from shootings directly to the Great Pyramid, Cheops, each exactly 500 miles apart as measured along a given line which is perpendicular to them all, and which itself runs through several shootings. The green line here, however, is at the distance of 10,000 miles from Cheops, which is one/fourth the distance around the World (the vertical diameter being 40,008 miles on average), and it too transverses several shootings and is perpendicular, but the distance at this point between lines is 505 miles. Each orang line originates dead center of Cheops and is separated by almost exactly 7.5 degrees of arc to achieve this feat. That is interesting for another reason; 360 degrees divides by 7.5 exactly 48 times, and 24,000 miles (the rough diameter of the Earth horizontally), divided by 48 indeed equals 500 miles.
Now there are some admitted problems in trying to depict a pyramid with any degree of accuracy in a 3-D perspective view, especially if with cutaway to reveal interior passages. Such a view does not simply allow us to measure a line and compare it to Cheops with good expectation of results. Perspective causes a measured horizontal to be less as it is depicted further away. A line transiting diagonally in one or more axis in 3-D space is even less useful unless one knew the precise angles for each axis both it and the original against which it was to be compared, were employing (and additionally, the depiction version is arbitrarily decided by the person rendering it, and impossible to discern without their sharing).
The depiction in this case seems slanted over America as if about to slide into the Caribbean. That is for a reason: it is faced (viewed) with the same face (view) as the actual Cheops is when following the orange lines, there — presuming in both cases one is looking from the center orange line towards it. That is to say, looking at Cheops in America from the center of the lines, would give you this same perspective view if standing in the center in Egypt. That cannot be coincidence. The problem with that, however, is that in Egypt, in relation to the Orange lines, one corner is clearly (looking down from Google Earth) nearer the observer’s position than another; there is no line which is not at an angle to the observer.
Note: I further feel it is an error to assume that modern-day Illuminati Warlocks have the skills and knowledge base, or event he interest in the crafts and mathematics of Masonry, which they left to the Adepts when Templer remnants infiltrated the Mason’s Guild and eventually took it over to form Freemasons. They are not likely going to go for precise renderings as much as symbolism; accurate to the point which can be managed simply, but no more, I believe.
Why do Masons, the Illuminati, and Satanists focus on Egypt and Cheops?
How much is a Royal Cubit, anyway?
It is, as result, impossible to establish a precise method or true consistency in relationships (i.e., to test for accuracy in scale) of measurements between Cheops and the American pyramid. The required data and accuracy required to plug into complex formula is beyond our ability to deduce. Ideally, a computer program modling in true 3-D space could be used to compute and confirm such comparisons… if we knew the angles employed by the architect of the American depiction.
But that does not mean we give up. We do the best we can with the tools at hand, and must come away at the very least acknowledging that in the 3-D layout, the mere visual similarities alone are sufficiently ‘coincidental’ to imply intelligent design, and in need of further study with better tools. But that does not mean we cannot ‘cheat,’ and then test to see if our cheat had any merit. After all, perhaps the architects employed a similar gambit. We wont’ know unless we try, ourselves. So…
By rotating the view as I have in the image above, we at least have the illusion that the base line is perpendicular to our viewing angle such that we are tempted to measure it anyway, and then see if there is any discerned relationship to Cheops which results in some kind of conversion factor. If we CAN find one, we can then apply that factor against other test lines and, in theory, if or factor was arrived at by other than coincidental happenstance, we should find the measurements work out correctly in the conversion. Guess what? We can, and it does!
Cheops on a side is 440 Royal Cubits, or 36524 Egyptian inches (a precise year’s worth of inches times 100), which works out to 230.4 m, or 756 feet. I will admit that finding a conversion factor took me some time. I made no headway at all until I realized that the orange lines were like rays of a projection lens in a theater, taking a small image and projecting it to be much larger at a distance. I reasoned there had to be something about analogy involved in the conversion factor. I also felt that any such conversion MUST involve the ancient increments in some conversion to the modern, rather than a modern to modern comparison. Turned out true.
As I discovered, if you divide 36524 by 440 you find that there are 83.009 Egyptian inches in a Royal Cubit. Funny. Both sum to 20. If you then multiply this times the total degrees of arc for the American depiction, which is three orange lines, or 22.5 degrees (±.03), you end up with 1867.7, which is exactly the measurement of the depicted base line… in Kilometers; ancient to modern, using the orange lines as calculator. So, now to test the accuracy and intent, vs. the notion of coincidence (pretty big coincidence, if that is all it is.)
Testing our factor: There are only a couple of other places where lines are similarly ‘perpendicular’ to our view (like the base line) by our peculiar method of so assessing for the purpose. Two of these are passageways to the King and Queens chambers, which just happen to have shootings (house icons employed for this use to match the drawings of the actual Cheops chambers) at the approprate locations to at least approximate the inner passages with an appropriate resemblance. But there is a problem with trying to test these with our conversion factor. It has to do with the Mississippi River.
Looking at the drawing of Cheops’ interior, you will note there is an irregular passageway leading down between the upward and the downward sloping passages. This is thought by some to be a water drain, as there are interior air vents which happen to align with prominent Constellation stars on select key celestial event dates, and that admits water. The lower passage in fact has a chamber with a deep pit which resembles a Well. In America, as it happens, the Mississipi River runs a course reasonably similar to that passageway and at the appropriate points in our depiction, given some small fudge factor.
Clearly, the Illuminati has no control over the course of the Mississipi, which changes slowly with time, and therefor, any depiction of the inner passageways must in some way accommodate those changes. My conclusion is, therefore, that such accommodation would necessarily mean a skewing of measurement accuracy in these passageways. Indeed, no line among them which is angled, nor the passages to the King/Queen chambers, quite works out, though some come closer to doing so than others.
But there is an entirely different story in play once we get past that drainage passageway, at the very bottom of the network. That whole portion is, by the way, beneath the ground level of Cheops by a goodly distance. In fact, the pit, which was filled with loose rocks as if a French Drain, once cleared, measures 60 feet deeper. Now, there are three points of interest with respect to testing our measures, and some landmark verifications we can also apply…
These are: the entrance passage to the Subterranean Chamber; an exit passage which is a dead end; and the pit. Applying our conversion faster, all three lines as depicted are of the correct length and are at the correct scale to the previously computed base line. But there was no shooting or key line to establish these lines (well, one line seems to do so), so we must seek some other verification that these are as intended by design. They do exist. Lets take a look:
The entrance passageway: The entrance passage determines the location of the Subterranean Chamber in the depiction, which we will verify separately. But it also has an unusual feature along its walkway, a kind of antichamber or alcove to one side, with no discernible purpose. On the map, at its correct location in the depiction, we find our old friend, Remington Firearms (the white arrow). That was, in fact, one reason I tested line placement at this site. Interesting then, that both this Proof and the prior Proof find their factories involved in shooting lines, baphomet lines, orange lines, and pyramid lines. That cannot be coincidence, and points to intelligent design, and intent — especially since the other Remington facility from the prior Proof is also present directly along another passageway, as seen in the first image of the depiction from above.
The exit passage and pit, on the otherhand, when extended the correct distance within ONE METER accuracy, end at… water wells, pumps, and tanks; which relate well to the purpose of the Subterranean level. That leaves the Chamber, itself. You will note a graphic image overlay veils in transparent fashion the intersect between the two measured passages and the pit. While there to represent the chamber, it is not really as ‘large’ as the chamber would be if to scale. At a particular location within the Chamber area it does cover, we find a nuclear power plant. This is interesting because much lore about Cheops includes references to end times, and equates the Subterranean Chamber to Hell, and the bottomless pit. One of hottest things we have on Earth is the interior of a thermonuclear power plant, and it burns both with heat, and invisible radiation; hell on Earth, should you care to experience it, with or without an accompanying China Syndrome ‘pit’. But there is an even more interesting verification, which is why the overlay:

It is hoped that it is not intended that this nuclear facility suffer a China Syndrome disaster such as seen at Fukushima, in order to render the ‘pit’ real on Earth in a hellish fashion.
The inset is the original artwork from which the overlay was obtained, a sketch of the what the actual Chamber looks like at Cheops, where it is described as seeming more like an underground quarry with lack of intent in what remains. The original is of very low resolution, I’m sorry to say. What I noticed about it that caused me to think to do the overlay, was the leftmost vertical protusion. I’m glad I did, because when I overlaid it, seeking to line it up with the cooling tower of the nuclear plant, I noticed something.
Actually, I noticed it while playing with the transparency level so I could see where I was positioning it. I truly wish I had video capture ability to show you the startling discovery, which, with a slight change in aspect ratio, was maximized; the darket portions of the overlay precisely match and seemingly define changes in terrain or map features. The effect is this: it gives the impression that the terrain to the South and near the power plaint has been cultivated to MATCH the overlay usefully. The best that I could hope to do to depict it here was to increase the contrast of the overlay, and alter the levels. There were originally only two discernable shades, black and gray (it is a B/W original image with some dithering in evidence). There are now four, and only the lightest of these is NOT defining a shape or darker area on the Map.
I apologize in realization that this is nowhere near as useful a description as the visible effect I’d rather show with video, but I assure you it is startling and implies, along with the wells and the Remington matter, that these lines are indeed intended to be here and at these dimensions, which in turn verifies the scale conversion factor discovered. Intention by design, in design.
What is the the relationship of Cheops and Mass shootings to Templars and the Illuminati?
The European point of view
 At right is an image looking from Cheops towards Europe, to reveal how it ties in with the Illuminati and Templars of old… not to mention any modern day Illuminati Warlocks operating there, today. Especially if their operations include casting magical designs in mass shooting in America to fast forward the formation of the North American Union and establishment of a one-World government under control of the Antichrist. Observe:
At right is an image looking from Cheops towards Europe, to reveal how it ties in with the Illuminati and Templars of old… not to mention any modern day Illuminati Warlocks operating there, today. Especially if their operations include casting magical designs in mass shooting in America to fast forward the formation of the North American Union and establishment of a one-World government under control of the Antichrist. Observe:
At the bottom we have our orange lines radiating outward at increments of 7.5 degrees of arc, where, in order to get to their designated array of shooting destinations in America, they must first pass through Europe. In Europe, we find one of these lines passes directly through the birthplace of Adam Weishaupt, Masonic founder of the ancient Illuminati (ironically, in 1776 — not truly ancient as most count it).
It is interesting to note that one can create in Europe, using only the birthplace of Weishaupt, and the orange lines, a baphomet which is correctly aligned Northward (the stray orange line), IF, and ONLY IF, running the North-line through the VATICAN IN ROME at the adjacent orange Cheops line. Then, IF, and ONLY IF, electing to use the Weishaupt’s birthplace as the center of said baphomet, will it then result as seen.
The significance of that is manifold. For one, it rests upon the remainder of the orange lines in precisely a mirrored orientation and in like relationships, in general, with the orange lines as does one of the baphomets in America. In other words, just as the depiction of Cheops in America was at the same viewing angle relationship as if looking at the real Cheops from an orange line, so it is, here, with the two baphomets.
Thus once more, the orange lines ‘project’ an image in useful scale with the same orientation to create a sister depiction in America. The difference is, THIS ONE, is properly aligned North for ceremonial use, and the one in America is flipped, so to speak… which allows IT, TOO, to be aligned with North IN AMERICA. How can that be by anything, but design?
Weishaupt’s baphomet, by the way, is at a point along the orange Cheops lines where, if used as a measuring point, they are exactly 333 Km apart, which is 207 miles (sums to 9), and 180 nautical (18), and since 18 = 99, that makes 3 threes and 3 9s, which is 999, or a code number for 666. And, of course, if electing to measure in both directions (the diameter of a circle about the birthplace between two adjacent orange lines), we also get 666.
Finally, we also see in the image the yellow icons for Templar castles and other properties, at least the ones we know about, and the red icons (and one balloon icon) which are Illuminati historical sites. We see also one green and one purple line coming from America, one a guideline from a baphomet depicted, there, and the other from a Masonic emblem, there… where both additionaly go directly to Cheops. The circle is complete; Cheops, European Illuminati and Masonic (Templar) histories (and arguably, current Warlock activities), and shootings in America and their resulting patters, all neatly tied together by six lines which impact all else. Coincidence?
What is the link between Masons, the Illuminati, Satanism, the New World Order, and Egyptology?
Go back to Introduction
Go back to Proof Seven: Shootings Form Multiple Lines to Cheops Exactly 500 Miles Apart
Go to Proof Nine: Shooting Sets Share ‘Magical’ Data Points Which Decode to Messages
Proof Seven: Shootings Form Multiple Lines to Cheops Exactly 500 Miles Apart
Extending select shooting lines finds them bisecting at the ancient Cheops Pyramid to establish a series of lines all of equal degrees of arc. But that just prepares us for a bigger bombshell.
Are there any patterns in mass shootings?
by H. Michael Sweeney proparanoid.wordpress.com proparanoidpress.com proparanoid.net
copyright © 2014, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Please comment any such repost to original posting.
Is there any proof mass shootings are not random?
What you will learn reading this post of the posting series…
• that select shooting lines can be extended to a single spot on the other side of the World; • that spot is the Great Pyramid, Cheops; • that the lines are exactly 500 miles apart at a given point and form the same angle of arc.Are mass shootings by intelligent design?
Proof Seven: Shootings Form Multiple Lines to Cheops Exactly 500 Miles Apart
Is there a mass shooting conspiracy?
The last proof resulted in some negative commentaries to group posts announcing its availability, all based on disbelief in the postulations advanced. This requires me to repeat myself: It does not matter what you or I believe, it only matters what the architects of mass shootings believe. Now, in this post, we start to examine the symbolism of Cheops and its ties to the shootings, which is also about what THEY believe. But first, I owe readers of Proof Six an explanation about the relevance of the ‘orange lines’ to select purple lines of the satanic baphomets and green lines of the Masonic emblems discussed as tying directly tie to Proof Seven in an unusual manner. So here we go, referencing the image below…
The orange lines are the multiple lines to Cheops this post is all about, of course, but those lines by and large pass through Europe using what is known as the Polar Route on their way to Egypt; the shortest, most direct route, despite the fact that in the movies they always depict planes flying East over the Atlantic to get to either Europe or the Middle East, or the other way ’round if going to the U.S. This is why, for instance, Iran Contra gun running used a stopover in Denmark and other Euro sites on their way to Iran, something which at first didn’t make sense to me when I learned of it.
The purple and green guidelines used in finding and plotting the baphomets and emblems also go to Europe, and end up doing something the bulk of the orange lines ALSO do: they just happen by ‘coincidence’ to pass through at least one, but more often, MULTIPLE ancient Illuminati and Knights Templar castles and other properties employed in their conspiratorial affairs, including some more modern facilities, and even Adam Weishaupt’s birthplace. He, of course, was the founder of the Illuminati, and a high Mason, and the Templars were the folks who evolved eventually to become the Freemasons we have today, as outlined in my book, MC Realities. There is one other line which does this, which is a red line created from a perfect isosceles triangle from Proof Three, which is the best example of ties to the modern Illuminati, as well as ancient, but also Cheops as it also directly intersects with the famous glass pyramid at the Louvre Museum in Paris.
There are other indications these lines and their relationships with Illuminati and Templars is tied to Cheops, in that some of the lines continue past Europe to the Middle East to find Templar sites, there, and two others, one each from a baphomet and an emblem, go directly to Cheops as if an orange line. It is interesting to note further, that these two are extremely close to the second orange line in from either side of the six orange lines; uniformity. Take a look: each white arrow indicates a line of interest which ties to the Templars or Illuminati. The ‘houses’ represent Templar locations (those icons refuse to float accurately over their respective sites at this viewing altitude), and the harder to see red dots are Illuminati, save Weishaupt’s birthplace, which is well marked. There are 18 lines in all, our magic number which equates to 666 in occult terms, only one of which (orange) does not find a Templar or Illuminati site, but we are talking about locations which in many cases have been lost through the centuries and, likely, it really does do so, but we simply have no such knowledge, today. The modern day Illuminati, however, WOULD know. The line certainly passes through territories where such properties are otherwise existent (not all sites are shown, only those which are intersected by lines).
Cheops I had previously been aware of the importance of Cheops to Masonic and Satanic histories, some more tenuous or doubtful than others, but all generally of a mutually supportive nature. If one reads the Masonic Bible, Morals and Dogma, it is clear that the leadership of the organization at the higher levels, is Satanic in its beliefs, practices, and tactical applications, and that all things of Ancient Egyptian lore play into their belief structures and lore. To Masons, especially, there is significance in the Pyramid, and thereby, also to Satanism.
Yet one can find other resources which state the Pyramid is outright tied to Satanism in one way or another, both inclusive and exclusive of Masonic ties, which came later in history. It is a Chicken or Egg question, or sorts, depending on the factoid being considered, but we need not answer those questions; our concerns are valid regardless of the answer. So when I noticed that some shooting lines seemed to angle off toward what I knew to be the ‘polar route’ to Egypt. I sought to verify, and was immediately proven correct. In the image above, find six orange lines which all meet precisely at the peak of Cheops a third-way around the World. They are all drawn at the same degree of angular separation (about 7.5 degrees).
At a given point in the map, in America, they are all exactly 500 miles apart, and as this image shows, they relate to shootings as they go. To date, only one (left most) has no useful shooting along its path to make the claim, but that does not mean there will not be in the future, and so, it is included. It may prove a means of predicting and even preventing a shooting. CHEOPS ALIGNMENTS x 6 There is no significance in the 500 number — at any given point, the lines are equidistant by some measure, I just chose a point where it produced a round number.
However, as research continued, I learned some things which would seem to make that a more important point. In the image below, this is revealed, and in the doing, we see also how the shootings themselves tie to the lines in important ways. More than this, the actual measurements once more reveal magical use of numbers in the occult manner. We should talk about accuracy. Given the great distance these lines must travel (35 million feet or more), the worst accuracy of these key lines is typically less than .05 degrees of arc (dependent upon Google Earth limitations as discussed early in this posting series), or some 15,000 feet at measure point. These work out to a maximum error of .007% and .0004%, respectively. I’m good enough with that to cite it here as proof of intent, given that the architects of mass shootings likely used the same tools, as I. There has, after all, already been revealed in prior Proofs several clues that such is likely the case.
Here we see some 440 plus mass shootings plotted along with the six orange lines from Cheops. The three green and three red lines are for measurement purposes, and require some dialog in order to appreciate the ‘craftmanship’ employed by the architects; a kind of confirmation this is no random outcome. The Meridianal (vertical) circumference of the Earth varies depending on where measured, but the average is 40,008 Km. This means that the point where the orange lines are furthest apart is some 10,000 Km distant from Cheops. This spot is found at the middle green line, and the measure there is essentially 2,525 miles.
This is confirmed in the red line between adjacent orange lines which measures 505 miles. The other two lines are the points where 500 miles between, is found, for 2,500 miles total separation, there. EACH OF THE THREE HAS AT LEAST THREE SHOOTINGS ALONG ITS PATH. These numbers prove interesting, and thus I also elected to measure the diagonal (vertical red) and ‘hight’ (red along the orange line’s path) of a given rectangle formed by these lines. The vertical line, which happens to be North corrected for magnetic declination, a trait seen time and again in the various alignments of Satanic and Masonic symbols in the prior Proof, measures 777, a magical triplet. The height measures 606 miles. More interesting numbers.
Take a look (numbers are rounded unless otherwise stated, and reflect allowances for measurement errors introduced by Google Earth as previously mentioned): Note: you may wish to review the sidebar post on Magic Numbers before continuing. Because… 500 Miles = a palindromic 434 nautical, which sums in pairs to 77; 777 is not only a magical triplet, but forms by summing in twos (1414) the inverse palindromes 141 and 414, which sum together to form the triplet 555, and equals 675 nautical, which sums to 18, and 1250.46 Km, which sums to 18 by threes; 505 and 606 are both palindromes, of course. And about 2525, divide it by 505, and it goes exactly 5 times. 505 + 606 = the double doublet 1111 (a quad) 500 x 505 = 252500, which sums to the doublet 77; 500 x 606 = 303000, a palindrome times 1,000; 505 x 606 = 306030, a palindrome times 10 which sums in threes to 99, which is a code number for 666 just as is 18; 306030 also = 492508 Km, which sums to form the inverse palindromes 151 and 515; and 606 x 777 = 470862 which is divisible by 18 2,159 times, and the grandaddy 666, 707 times.
So we end up with 505, 606, and 707 palindromes, and the triplets 555, 666, and 777. 505 squared = 255025, which sums by twos to the palindrome 757; 606 squared = 367236, which sums to the the triplet 999, a code number for 666 (upside down); it also divides by 18 to provide the palindrome 20402; 777 squared = 603729, which can produce 999 by summing by 3, 2, 1 digits consecutively, a bit unusual; We can’t easily find the area by simply multiplying 606 x the top or bottom, because they are different. We can do that with both and then average the result. This yields 303000, a palindrome times 1000, and 306030, a palindrome x 10. The total of the two sums to 609360, sums to the palindrome 6116, and which divided by two = 304680. So now we know the area, which is 1680 sq. miles more than the smaller of the two, and that much less than the larger, of course. 1680 = 2704 Km, which not only sums to 13, but is divisible by 13 208 times.
The orange lines in detail
In the last Proof, we found the orange lines tied usefully to the layout of the four baphomets and Masonic emblems. Here, lets relate them more directly to the actual shootings which were also part and parcel of those relationships. The first lines at image left does NOT actually line up with anything, YET. It is presumed they will eventually line up with a shooting and may be useful in prediction of same, as there are very few communities in its path with logical targets which fit with other predictive factors. But I will not state these as our paranoid government tends to make anyone predicting such violence based on ANY criteria as the only ‘terrorist’ or ‘suspect’ in question. They tend to lock down such locations and charge the person who gave the warning with criminal intent of one sort or another, or act harshly against them in some way. Apparently, ‘See Something, Say Something,’ is a trap, and considered a crime. I know that at least twice that I reported terrorist activities, they did nothing about the report other than to harass me and try to cost me my job.
The next line is perhaps the most dramatic in terms of accuracy and alignment. It bisects with extreme accuracy two shooting events, even a third within Google Earth dictated error limits. The third also has three shootings within accuracy limits, two of which almost meet doorway-to-doorway accuracy.That line also passes through the Denver International Airport and quite near to a man-made earthen Ziggurat (stepped) Pyramid thought by many conspiracy theorists to be a D.U.M.B. (Deep Underground Military Base). The site claims to be a landfill, albeit the highest and fastest growing of its kind by far, if true.
It is also true that in its current state, it only appears to be a Pyramid in three of the four sides, the fourth being the area where ‘fill’ is taking place at this time. The next line features the sloppiest, worst-case error with two shooting points in its path. The larger error does not dissuade me, because both are quite equally distant from the line on opposite sides of the line (the line cleanly centers between them). There is additionally a business, Pyramid Foods, almost directly on the line near the Bartlesville HS shooting plot of that line. The next line also sports two shootings, one of which is quite near Meridian, MS; Cheops is itself a similar distance from Meridian, Egypt (a neighborhood name also used in several business names, there). The final Cheops line merely intersects within 1,000 feet of a single shooting event. This is near King’s Highway, and Cheops is a King’s tomb. Thus all the lines currently aligned with shooting points, are several are also aligned with something having to do with a Pyramid. This yields yet more consistency, but feel free to presume it coincidence, if you must. What does Cheops have to do with mass shootings?
Why Pyramid?
Beyond the earlier comments about why Cheops is important to Masons and Satan worshipers, there are a few other things which should be mentioned. One has to do with the construction of the Pyramid, which many historians think drove the establishment of at least some of the ancient Egyptian’s measurement system. What is interesting about that, as casually mentioned earlier in this series, is that as history progressed, their system became in various ways the bases for both the English and Metric systems, as well as the system employed in America. It is alleged that Masons (Templars) were the driving force behind this, in part, to insure or play to the mysteries of magic numbers.
So do not be surprised then, if the next post, I tell you that there is not at least one measurement at Cheops which is duplicated in shooting lines here in America which depict the same part of a pyramid in a 3-D view, but using different increments and a different scale (think miles for inches, for example). I’m still working on verification of a list of suspect instances, but it certainly seems the case. This would NOT be possible if there was not some basic underlying ‘magic’ built into both measuring systems with respect to conversions. But the real thing of interest about Cheops, here, is its lore.
Many learned researchers have studied the Pyramids endlessly to formulate many different theories relating to its design, how it was constructed, what its purpose was, and so forth. Many of their findings are controversial, but few are invalidated by the work of others, but might remain rightly in the realm of speculation, or ‘lore.’ Among these are two which would logically be of interest to a Warlock or high Mason (sometimes, the same thing).
The first involves the inner passageways of Cheops. We know these are important to the architects of shootings because, as we will see in the next Proof, they are faithfully duplicated in the 3-D depiction of Cheops by use of shooting lines and shootings. The reason why would seem to be in the lore, which according to some, says that these passages are a kind of history of the World being depicted from creation to its destruction. They actually make a very good case for this, and my own conclusions would tend to agree there is something to the notion, at least symbolically, if not accurately to the year. The claim was, that each Egyptian inch represented one year of history, a thing which seems to be true at least for specific historical events used as benchmarks.
If, therefore, the need to seat the Antichrist in support of end time prophesies requires taking away guns in America to allow the formation of the North American Union, then our architects, being wise in the magic and lore of Cheops and the like, would most likely incorporate as much of that magic into their plans as they could manage. The second involves what is called Pyramid Power in a book by the same name written by Max Toth, which is as good a reference as any of like conent summarizing the lore of Cheops, including the inches for years theory. If even half of the claims within were true (and I have verified at least two of the main claims in my own experiments), that is one more reason a Warlock would wish to incorporate pyramids into any conspiracy aimed at seating the Antichrist. But again let me say, it does not matter what you or I believe about such lore, it only matters what THEY believe.
Go back to Introduction
Go back to Proof Six: Shootings Also Relate or Depict Masonic and Satanic symbols
Go to Proof Eight: Shooting Lines Also Depict Cheops in 3-D Cutaway View
Emergency Post: BLM vs. Bundy is an Ominous Danger
It is seen by government as a win-win ploy that raises the stakes to unimaginable levels. What we see on the surface has nothing to do with the sinister plot which it enables and portends. This is our last and only chance to save the country, or loose it to tyranny forever, and rush toward Earth’s final demise.
Will Bundy vs. BLM start Revolution 2.0?
By H. Michael Sweeney proparanoid.wordpress.com proparanoidpress.com proparanoid.net
copyright © 2014, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Please comment any such repost to original posting.
What is going on in Nevada with the BLM?
What you will learn reading this post…
• government’s actions against Bundy are mere window dressing — something more sinister is afoot; • the stakes are incredibly high, but hard to see — your very life and the fate of the World, in fact; • there is only one logical solution, and everyone plays a role. What can I do to help Bundy against the BLM?Why BLM vs. Bundy matters regardless of if his cause is just or he has no legal leg to stand on
UPDATE: Same day posted… Oh, so now we find out its really for the oil companies? What Corporate Police State? BLM sells 29 oil, gas leases in northeast Nevada End update.

Free Speech Zone meaningless when dogs and tasters are aimed directly at the people. From againstcronycapitalism.org (click)
Government made it matter, and with dark purpose. At one glance it is an effort to usurp power over people, and the States, as well as to empower corporate ranching over private ranchers. It is a form of unfair and excessive taxation without representation against a political enemy of financial convenience to friends of the White House. And, it is an opportunity to make yet one more National Police Force out of the BLM. But, thanks to controlled media/government PR, not everyone sees these points of view.
But even that view is incomplete and misses the mark, if we but look closer. It is a deliberate series of escalations by government over time to garner public attention among and inflame we select people (why it gets little due mainstream coverage — save that which slants as it did at Ruby Ridge and Waco). They know the Web will be awash in the circles of we Patriots, Constitutionalists, Activists, and others who oppose the tyranny and oppression our government has come to represent since 9-11. The Sheeple must not be unduly disturbed until it can have false flag impact of calculated value.
I talk a lot about the need for citizens to draw lines in the sand and be willing to become Minuitmen should such lines be crossed. Now comes government to draw it for us, I write here to tell you that you have no choice but accept the challenge, and act decisively. You may perish either way, but I’d rather perish attempting to control my life and future than to leave it to others less kindly inclined to favor me. If there is to be armed revolution, let it be on our terms, not theirs.
Why so conclude? Because if they work it right, the ‘standoff gone wrong’ is a perfect chance to justify taking guns. By forcing a showdown and a gunfight (what the snipers do best – there is no justification for government deploying snipers unless for this cause, AND to selectively inflame those who stand for Liberty and who remember Ruby Ridge). There are two possible ends, of course, though I think they will insure BOTH transpire.
Regardless, such a battle is win-win for government. The “poor defensless BLM armed only with tasers,’ if loosing large numbers will be seen by Sheeple as an outrage, and given that Militia were involved from multiple quarters, and other armed parties, Obama can order Martial Law with suspension of the Constitution. Especially if also employing agent provocateurs for local violence across the country, as was employed in the LA Riots, where National Guardsmen posed as rioters to prime the pump. This would likely result in orders for the military and Police to go door-t0-door. Who knows, Obama might even order the U.N. in as long-feared and first promoted as concept by Henry Kissinger. Or, he might simply order in the military; A-10s, attack choppers, a Stryker Battalion, and so forth.
They can then conveniently ‘quash armed rebels and terrorists,’ confiscate all guns, round up dissidents and politically incorrect opponents (like you and me — why they have been spying on us so earnestly), and hold a Con Con (they are already staging for it) to pass the Constitution of the NewStates of America, already written, which essentially enables the formation of the North American Union and surrender of US sovereignty to the U.N. in stages. All of this leads, of course, to a one-World Government (that Constitution has also already been written), and provides a single seat of power to enable the Antichrist’s coming to power.
Note: The NewStates Constitution is reprinted in my booklet, Fatal Rebirth, along with the World Constitution, complete with analysis line by line (NewStates) to show how draconian a document it really is. Rights become privileges which can be revoked at any time by any agency or party of government for any cause, even retroactively, and almost anyone in government can write law, and again, it can be retroactive. And if you think the two-party system and the FED/IRS is bad, wait until you see what follows. You can request a free copy of the ebook version of Vol I of Fatal Rebirth by email request to pppbooks at comcast net.THAT is what is at stake. Nothing less than EVERYTHING!
So we must be decisive: regardless of how we view Bundy’s cause or government’s viewpoint, regardless of if an armed and concerned citizen or a dumbed down Sheeple, we all have equal stake in this unfolding globalist tragedy. And, we can all play a role no matter our status, and regardless of if present in Nevada, or not. But about that decisive action…
Why is the BLM standoff against Bundy in Nevada taking place?
What we should prefer…
Should we stand up with arms in hand and enable, if not force, the ultimate showdown? I fear this is exactly what government wants, as already stated. But there is another, wiser choice.
By all means, men of arms should rally, but standing firm and waiting for the other side to blink or blunder is a fool’s plan, and it can only end in bloodshed. What must be done is that which can neuter Government’s ploy. And only one set of steps can do that:
a) anyone and everyone should file court actions against any and every agency, branch, and individual of government involved at every level of government. Any and every cause, grievance, or objection, as allowed by and based on State, County, and Federal Law, and the Constitution and Bill of Rights, should be employed. Bury them in legal actions, EACH OF WHICH includes request for either an Injunction or Stay Order. These actions should not all be done at once, but the flood should be continuous, so that new ones can replace those quickly disposed of. THIS BUYS TIME;
b) time is our friend — it generates awareness and understanding. It buys media attention and gives Sheeple a chance to better understand what is taking place. Just as the 99% movement could no longer be contained by a controlled media, so must this matter be brought into every home. Invite major networks, espcially foreign press, to specifically include RT, to set up broadcast facilities right on the Bundy Ranch, and bypassing the see nothing viewpoints established by government for controlling media in the manner done at WACO (NEVER AGAIN!). Install microwave and shortwave communication systems for the purpose. But also, LOCAL media is the key, as is the WWW; do not rely upon mainstream. Militia and other group ‘spokespersons’ in your community should approach their local news sources with proposed interviews to get the word out. IF EVERYONE UNDERSTANDS WHAT IS TRULY AT STAKE, AND TAKING PLACE, GOVERNMENT’S PLOT IS UNDERMINED AND THEY LOOSE THE SHEEPLE;
c) flood the theater with actors. There should be so many people there is not enough room in the minimal areas intended to contain them. OVERFLOW. The ‘1st Amendment’ area, itself an affront to the Constitution, and should be enlarged and enlarged again, forcing retreat or conflict which will make news favorable to our side. If you have access to a professional camera, start a ‘newspaper’ or ‘Radio station’ and flood the press area and make it overflow, as well. And Bundy’s ranch should become a city of tents, and include as many unarmed persons as possible who wield nothing but baseball bats or the proverbial pitchfork. THIS MAKES THE WHOLE AFFAIR MORE VISIBLE and LESS TENABLE TO GOVERNMENT’S GOALS;
d) involve the local Sheriff and State/County Officials. The Sheriff has effectively stated a hands-off non intervention policy. Fine. Perhaps he is a puppet put into place for the purpose, or co opted by any number of means available to government for rendering him neutral. But the flurry of legal actions should be intended to FORCE HIM to intervene on behalf of Bundy and supporters. If nothing else, he should have a presence on the Ranch to insure armed groups behave (public safety). The Governor and Legislators, and County Officials should called to DEMAND it. Perhaps even the National Guard should be called to stand by. A simple invite, if not enough, can be followed by a media blitz and public demand that such action is needed. Any politically motivated decision to remain neutral should be negated, thereby; a political suicide. INVOLVE THE SHERIFF, as WITNESS and PEACEKEEPER;
e) party! No alcohol or drugs, but good cheer, song and dance. Use loudspeakers. Mix well with speeches and ‘town hall’ dialogs. Use the platform (the nation will be watching) to air ALL GRIEVANCES with government, not just this ONE issue. Give voice to the rest of the 99% in a way that movement never was able to achieve on its own. SOROS WILL HAVE NO VOICE, this time;
e) prepare for Martial Law at home. That means emergency kits and plans (like the one government would not approve). It means weapons. If it is declared, you will have scant few hours to choose to fight, run, or to surrender to your fate at the hands of tyranny. If not taken away, you will need to survive for months without anything like normal civilization. No key resource, including electrical power or communication, can be assured, and will likely be withheld on purpose. Travel will be restricted and many will not be able to work, and there is no shopping, only rationing. BE READY TO BE SELF RELIANT, BE READY TO FIGHT IF THAT IS WHAT IT COMES DOWN TO;
f) if and when the shooting starts, DO NOT ENGAGE! Dead BLM or other Agents will be made into martyrs by mainstream. DO NOT GIVE THEM WHAT THEY WANT. Show restraint, and let the casualties be on your side. Keep putting out a continuous feed of information and video so that media and the WWW know what is going on. IF THERE ARE TO BE MARTYRS, LET THEM BE OUR OWN, and LET IT BE TELEVISED LIVE. If a full-scale armed revolt spontaneously errupts nation-wide, then by all means, defend yourself at the Ranch, and FOLLOW YOUR CONSIENCE AND DEFEND THE CONSTITUTION.
g) petition for redress. Redress of grievances is a key component of our Nation’s Constitutional form of government (this post makes clear, mid post). When it fails, we have no government, only tyranny. It seems today there is NO REDRESS POSSIBLE at the Federal level. ONLY THE STATES stand in the way of total Federal domination, which is part of what this whole affair is about; a means to increase Federal power over the States. But while all this is going on… and while we have media platforms established… we should be seeking redress through our State Legislators, making a series of calls for action to quickly pass laws which…
1) nullify all Federal gun laws, NDAA, NSA surveillance, and forbid Federal drone overflights except under warrant and oversight by State authorities;
2) eliminate Federal arrest and warrant power. If a Federal judge issues a warrant, or an Agency is moved to move against a party (like Bundy), they must instead go to the appropriate local Law Enforcement Agency and have them execute on their behalf. They may go along, but as observers, ONLY;
3) make clear a mandate that your State shall NOT approve a new Consitution if a Con Con is held, nor the removal or neutering by Amendment of the current Constitution, and any existing Federal Law which does so should be nullified;
4) add freely to this list anything which addresses abuse of power by the Federal government, such as militarization of Police, Obamacare, etc. This will be your one best chance to spark public dialog and debate, and to make certain that people, and especially State Legislators, realize THEY are the ones with the real power, and the duty to protect freedom and force the Constitution.
What is at stake in Nevada and the BLM standoff with Bundy?
Government has drawn a line in the sand
Let’s make sure they regret it. Force them to be the ones to cross it, and let them trip over their own power play. Now… go forth and spread the word.
Crime Series: Ten Unexpected Proofs ‘Random’ Mass Shootings are by Intelligent Design
Ten easy-to-grasp but remarkable proofs, both visible and hidden: Illuminati style mystical symbolism and related ancient magical mysteries, calling cards, bragging rights, and Warlock spells cast against America, and the World. Conventional clues, too.
Are there any patterns in mass shootings?
by H. Michael Sweeney proparanoid.wordpress.com proparanoidpress.com proparanoid.net
copyright © 2014, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Please comment any such repost to original posting.
Is there any proof mass shootings are not random?
What you will learn reading this multi-part posting series…
• there are 10 interlocking proofs that mass shootings are not random; • they include various kinds of patterns, visible and unseen, and even coded information; • that the pattern predicts itself, and understanding may therefore help stop the murder; • that the codes and clues seem to be like signatures identifying the architects.Are mass shootings by intelligent design?
Introduction: Ten Proofs ‘Random’ Mass Shootings by Intelligent Design
Is there a mass shooting conspiracy?
Note: This series is not yet ready for full presentation, but the most recent Fort Hood forces me to start releasing the material without delay. The reason for delay has had to do with an inability to provide high quality graphics suitable for proofs. This will be overcome, shortly, I hope.
One thing you need to know about me as an investigative writer or, as media and government would prefer you to think of me, a ‘conspiracy theorist,’ is this: whenever I decide to take a close look at a potential conspiracy or lesser matter, I do it right. If I cannot uncover something no one else has brought to light, I’m either not finished, or I’ve backed out concluding it beyond reach, or a dud. If you read my findings on a given research, you will undoubtedly learn something FACTUAL no one else had previously discovered or brought to light. And so…
In this matter, we find the shear volume of startling new information overshadows and renders original headlines and competing theories essentially meaningless — especially media’s version. It will make you angry. It will scare you. The question is, will it motivate you to do something about it? YOU are what you are waiting for, you know.
But in introduction, there is still one other point which must be made; it is in form of a problematic question. Can I get you, the reader, to override your current belief structures long enough to consider the unusual nature of the findings? This presentation will most assuredly fly in the face of what most people consider ‘traditional wisdom,’ but it also will explain why it is non-the-less valid. Can you handle the Truth, or will you wimp out to the comfort zone of current beliefs?
Area all mass shooters psycho?
On suspending belief structures

Dormer was not quite a ‘Mass Shooter’ incident, at least not at a single location/time. But the affair highlights the problem of accepting ‘random’ as the right word to apply to shootings when there are so many problems with the official story. CLICK to learn about why many people think him just another shooting patsy.
I began a ten-year research project for a book, Fatal Rebirth, in late 1989, which also begat a screenplay published on line in 1999 (The Electronic Apocalypse). In the book’s Introduction I urged the reader to suspend their belief structures briefly and read the material as if merely fiction for entertainment’s sake, because many of the concepts within were so new and unusual as to defy belief — likely seen as ‘far-fetched’ by most uninformed readers. I offered over 1,500 footnotes and a huge Appendix section to help them consider why I deemed them factual.
This blog post should be read in like manner, especially if you are content with government’s actions, are a politician, member of a government agency, military, or any part of the justice system, or Media. Especially if you are involved in a mass shooting incident as a professional or a victim seeking to know the truth. And even more so if you are gun owner, or even among what 2nd Amendment supporters refer to as a ‘gun grabber.’ I plead, therefore, that you suspend your belief structures briefly as if reading a political/horror-science fiction piece. That’s what it is, actually, minus the fiction component.
You will, like readers of Fatal Rebirth, I would hope, realize the truth by the time you reach the end. Or, at the very least, you will be entertained for all your reluctance to let the message sink in and take root.
If nothing else, even if you choose to doubt some of the more obscure subtopics (i.e., relating to mysticism) have any factual basis in REALITY, consider this: it matters NOT what YOU think, given they ARE taken as real by persons likely to be behind any such conspiracy (i.e., ‘Illuminati’ Satanists). You MUST also ask yourself, “Can the sheer magnitude of interlocking clues be ignored?” Because at every turn they defy the odds of coincidental probability, as illustrated by carefully crafted control study groups. If thinking logically, you MUST concur that intelligent design is revealed despite what you may think about the logic of the beliefs which lay behind it, or the unusual way in which the evidence was revealed.
Pending you conclusion, by all means feel free to think me mad if you must. Read just for fun, but please read it through to end before you render final judgment as to if madness or truth be present. A logical reader will be converted unless their mind is already so firmly made up that they do not wish to be confused by facts which destroy their belief structures. Judge not what ye know not, but that upon which ye are well informed and have considered fully, judge freely.
Your future and the future of your children could well be at stake, a statement applying to all mankind. Why do I say this? The book mentioned above, Fatal Rebirth, was based on trying to illustrate what I call the Unified Conspiracy Theory; the notion that all of America’s darkest bumps in the night for the last half of the prior Century, forward, were not random oddities by random people for random agenda, but carefully orchestrated by the same core group of people with but one goal for the World in mind.
I termed them Shadow, but they are also known by other names; the New World Order, the Illuminati, the Power Elite, Globalists, and among them, member names like CIA, Skull and Bones, Bilderbergers, Council on Foreign Relations, and many more of like nature. Their goal I termed End Game; the establishment of a One World government, a single seat of power in order to seat the Antichrist upon his throne and bring us to Armageddon.
The Unified Conspiracy Theory, once justified in research and taking shape in book form, led me to realize that their stepwise actions over fifty years of mysteries were indeed leading to one goal. Knowing the goal, I reasoned, it should be possible to forecast the next logical steps. So the book also included within its presentation several terrible event predictions expected to take place in our near future. Thus far, though I do not claim to have gotten all event details precisely correct, many terrible forecasts have already come to pass. Among these were:
a) an assassination attempt on Ross Perot or his family to cause him to drop out of the Presidential Race, a matter which indeed transpired using mailed Anthrax according to a Secret Service back channel contact;
b) the false flag downing of the World Trade Center by civilian passenger jets which;
c) resulted in a series of Middle East Oil Wars. Other predictions include two more terror plots which are part and parcel of this blog post. Those are…
d) a false flag nuclear attack on Charleston, S.C. and Portland Oregon (the later of which I have already thwarted, it seems – see middle of my home page), and more to the point…
e) MASS SHOOTINGS.
Note: you can get a free copy of Vol I of Fatal Rebirth (ebook) by email request to pppbooks at Comcast (net). You will be glad you did, as it will take you far deeper into the Rabbit Hole than Alice or Neo had ever gone. This pill is black, though trimmed in red, white, and blue.
So, if ready to suspend your belief structure, let us begin. Pretend there is, despite media’s recent attempt in the Cincia shooting to portray anyone who believes in the New World Order as mentally ill and anti-patriotic, that such a conspiracy is actually afoot. Also pretend, if you must, that Political Control Technology in the form of the Manchurian Candidate is real. There are real-life Jason Bournes out there, as my book, MC Realities, and other books on Political Control Technology illustrate more than adequately. Even the Smithsonian channel knows.
This will make the key postulations, testing methods, conclusions, and proofs of the core material easier to accept, especially as they will be offered in the manner of scientific discovery — exactly as I undertook them as investigative writer. You will, in fact, be able to retrace my work to double check it, if you wish — as long as you review the full series of posts and sidebars before you attempt it, lest you make a critical error. Please subscribe to my blog pages to insure you are notified as the remaining posts in the series are added.
Are mass shootings are by intelligent design?
The Investigation

Jason Bourne… though fictional, is based on real-World programmable assassins. Do you suppose CIA or anyone else would not find something useful to do with failures in such programs? Might they not make excellent disposable patsies? Image/film: http://www.imdb.com/title/tt0372183/
Some several months ago, insulted by media’s misreporting of Aurora and Sandy Hook and outright clues that a disinformation campaign was afoot, I began finding ample cause for concern. But how might one determine if other mass shootings were arranged as part of some kind of sick criminal conspiracy, one which might involve both real and faked shootings?
I started with several basic presumptions of truth, and then set about to see if the logical evidence such presumptions would require were indeed in place. The ‘illogical’ presumptions fostered by the Unified Conspiracy Theory requiring suspension of belief are as follows:
1) That Shadow and their Globalism requires destruction of America, and its Constitution in order to enable forming the North American Union, a matter which in turn requires that the Right to Bear Arms is first invalidated, and arms confiscated or gun owners otherwise neutralized in a manner similar to that of the Australia;
2) That the New World Order, the modern day Illuminati, if you will, would be well capable of undertaking a campaign of gun violence for such cause, but being an Illumined Power Elite lost to Satanic and Masonic mysticism, they would employ mystical constructs which would leave detectible footprints if knowing what to look for;
3) That the principle tool of such a plot would involve a small army of patsies, cut outs, and fall guys, principally from a category best known to the public as Manchurian Candidates. It may additionally involve a small army of blindly obedient members placed within our armed forces, the intelligence community, and law enforcement to aid more indirectly in supporting roles. This would include logistics, psyops, and cover up, or even command and control, generally unaware as to the truth or reason behind their orders. These are the same players frequently found playing key roles in the lives of mind control victims at large.
All three presumptions must be true to make a proper accusation, for they comprise the basic proofs of any crime: Motive, Opportunity, and Means. Normally, we think of opportunity as meaning access to the scene of the crime, typically proven by forensics such as fingerprints, or better yet, actual eye witnesses. In this case, they deliberately left their fingerprints, in a manner of speaking. In fact, the bulk of the proofs fall into this category, perhaps even naming individuals behind the plot. At the very least, we are indeed dealing with the Elite, those involved in principalities and powers.
Indeed: Two names have already surfaced by such clues, and both are billionaires. I also have a dozen other names of likely conspirators, but no names are released; these things are my Life Insurance Policy.
Sidebar Post: On Programmable People. This sidebar post addresses the notion of the possibility that at least some mass shooters are mind controlled patsies, and reconciles their coexistence with truly random shootings — those which are more naturally spontaneous crimes — which can collectively still both be component parts of the same intelligent design. This leads us to the finer details of how shooting event locations and dates lend importance to our consideration, and just how these things can additionally reveal intentional, yet concealed clues.
Here it should be mentioned, that many observers of the New World Order crowd favor the supposition that among their leadership we might find the modern-day Illuminati in spirit, if not in actual blood lineage, even though they may have since assumed a different family name. By way of example, in my research, I have had reason to conclude that the Rotheschild name was assumed; those assuming it being Knights Templar in hidding, their wealth derived from Templar treasure, and not truly Jewish by ancestry or faith, at all.
Many who favor the notion of a Modern-day Illuminati additionally believe, as do I, that there are at least two, and as many as four groups competing with each other within the movement to be the ones ‘honored’ to have one of their own selected to become the Antichrist. Much of what is discovered in this investigative series will point to this being true in one way, or inherently implied in another. It is, in fact, one very good reason to employ symbolisms and other clues which act as signatures of those so bidding for selection.
Such evidence was abundant, even easy to find, and I remain convinced that the trio of presumptions are sound enough to warrant seeking incontrovertible proofs. I sought such proofs both in quality and quantity sufficient to illustrate that ‘random’ was not the right word to describe mass shootings, but rather, ‘intelligent design,’ is.
The path of my continued investigation led to endless shocking discoveries, but there was a problem: to describe the methods and explain findings to the casual reader would, it seemed, require a tedious educational process and boring, repetitious citation of facts. It would be about as fun to read as a spreadsheet or database. Not good.
People want visual sound bites easily grasped. More so if Sheeple content with their Evening News and easily frightened off by words like ‘conspiracy theorist,’ and ‘New World Order,’ or similar. Worse, the investigation bogged because of the real life tragedies each shooting represented. Proper investigation meant exhaustive study of individual events, reviewing endless horrific detailed accounts and sad, brutal media imagery. It was taking an emotional and even physical toll upon my body and mind, and my spirit. Eventually, instead of plodding along 10-14 hours a day as at the start, I found myself barely able to work on it a few hours a week.
I played with several ideas on how to present the story NOW, without completion of the full study, for there is indeed already a mountain of proofs uncovered. But again, the complexities in presentation left me feeling it a hopeless task. Finally, I decided to break it down into about a dozen short compartmentalized components suitable for a series of blog posts. Frankly, I’m hoping it will spur someone to offer useful help; it will take funding and staffing to properly complete the study. Or better still, perhaps some Sheriff or other authority will assume the duty as result of shootings in their jurisdiction.
Follows is a synopsis of the Ten Proofs to be presented. There will additionally be, at appropriate points, companion posts detailing the scientific methods or other analytical procedures involved in select proofs where a doubting Thomas type may wish to challenge the validity of claims. I firmly believe that for my proofs to be accepted, they should be presented in a way such that ANYONE can duplicate my work and verify accuracy and conclusions.
This is a legitimate investigation despite its atypical and unorthodox methods and odd topics involved. NOTE: links will NOT WORK until the various posts involved have been posted. You may click on them to discover their current state. Again, subscription to this blog will notify you when new posts are added.
What are the ten proofs of a mass shooter conspiracy?
The Ten Proofs in review…
Proof One: Gun Grabbers Selectively Ignore Mass Shootings, Conceal Patterns;
Any time you find a cover up, you necessarily have a conspiracy to contend with. Gun grabbing groups, including government and biased or puppet media forces, should be using every opportunity to make their case for gun control, but act as if the bulk of gun violence never took place. Why do they employ selective blinders? There is a reason.Proof Two: Shootings Exist in Identical ‘Magical’ Categorical Clusters;
The Illuminati loves magical numbers, as they can translate into meaningful words or names, or leverage ‘spells’. Interesting then, that basic shooting statistics establish set after set in the most magical and potent number of all, one which decodes to ‘Satan.’ This alone reveals dramatic coincidences well beyond the possibility of random chance.Proof Three: Shootings Exist in Endless Sets of Three Forming Straight Lines;
The same Dispersal Pattern Studies method applied by government researchers to UFO sightings reveals Mass Shootings do something UFO sightings allegedly do not: form repetitive patterns with GPS accuracy, doorway-to-doorway-to-doorway.Proof Four: Straight Lines in Turn Form Complex and Perfect Shapes;
When it comes to symbolism, nothing outperforms a graphical shape. Better still when that shape itself has magical properties or relationships to other shapes, or its own hidden or obvious meaning.Proof Five: Shapes in Turn Form Complementary ‘Magical’ Clusters;
It defies odds that perfect shapes should cluster together in ways which share overlapping lines or corners, and be generally both aligned and mirrored in additional symbolism.Proof Six: Shootings Also Relate or Depict Masonic and Satanic symbols;
Select shootings define such symbols with precision. Masonic Symbols are rendered in 3-D. Satanic Symbols are positioned correctly for magical application by Warlock.Proof Seven: Shootings Form Multiple Lines to Cheops Exactly 500 Miles Apart;
Extending select shooting lines finds them bisecting at the ancient Cheops Pyramid to establish a series of lines all of equal degrees of arc. But that just prepares us for a bigger bombshell.Proof Eight: Shooting Lines Also Depict Cheops in 3-D Cutaway View;
The Great Pyramid in Egypt is one of the Holy of Holies to Masons and some satanic cults, and is specifically tied in mysticism to the End Times and historical catastrophic events. This one will scare you.Proof Nine: Shooting Sets Share ‘Magical’ Data Points Which Decode to Messages;
Shooting line sets share three or more identical magical numbers within their data points. These decode to tell us when and where the next shooting will be, name a shooter, or perfectly prophesy some specific outcome.Proof Ten: Individual Shootings Examined in Micro Duplicate the National Study Proofs
Two examples are offered; Aurora and Sandy Hook. They not only duplicate the ten proofs, but they mirror each other and one points to the other. Why are mass shootings on the rise?Are you ready of this? Buckle up!
So let us begin. I propose your best bet will be to SUBSCRIBE to my blog pages so that you are automatically notified as new posts are made to complete the series. Please link, share, tweet, etc., and by all mean vote your ranking at page top of each one, and comment with your questions, criticisms, or thoughts. How else will other know this is important?
Do bear in mind as you read, each offered proof individually seems to defy the odds or logic path required for truly random shooting events. Collectively, it is monumentally clear. Also bear in mind that I am human, and I, like any other, am prone to making mistakes. A ton of information had to be entered and copied from one location to another multiple times (multiple database and software applications). Therefore, either because of a mistake on my part, or perhaps because of a mistake in media or other accounts/records, any given individual data point in any given set of proofs may be found invalid.
By all means let me know if you find such a discrepancy, but please remember this: a single error in a single data point does not invalidate all other data points, and therefore, does not invalidate the conclusions or the suppositions, themselves. In order to dispute my findings, you will need to offer proofs that the method is flawed, the entire data set was in error, or analytical logic was faulty. More: such dispute must address and ultimately invalidate all ten proofs, or short of that, offer equally viable alternative explanations which fit the findings and afford a more innocent explanation.
Since each proof tends to defy all possible odds of random coincidence, and does so consistently, again and again, naysayers will have their work cut out for them. More so, because in many cases, control groups have been established to show truly random data points enjoy no such pattern. I have done my homework, and carefully so.
I will demand the same of naysayers.
Go to Proof One: Gun Grabbers Selectively Ignore Mass Shootings, Conceal Patterns
Go to Side Bar: On on Programmable People
How Social Network Trolls Target, Track, and Psychologically Profile You
How to spot and deal with Trolls, including a clever tool they use in any social media capable of posting images (VERY prevalent on Facebook), and quite insidious with far reaching implications. BEWARE: you betray yourself and your friends if you take things at face value.
What is a Web Troll?
by H. Michael Sweeney
copyright © 2014, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
How does being a web troll work?
UPDATE: Nov. 11, 2014 Perhaps as if to ‘test’ me as result of this article (or not), a Web troll began the process described herein to goad me argumentatively while also employing a good half dozen of the usual disinfo tactics in the 25 Rules of Disinformation (linked below). So I unfriended him and watched: that same day, ‘someone’ created a new FB account and almost immediately friended two of my friends, posted ONE activist post, and ONE peace post, then requested to friend me. Sure. OK. BUT I HAVE MY EYE ON YOU, because that’s how easy it is to get a new identity and hook back up to a target. Not that I care. Trolls are tasty.
Are you being targeted by online government trolls
How Social Network Trolls Target, Track, and Psychologically Profile You
Reading this post you will learn…
• That there are three basic kinds of trolls and subsequent ‘missions’ against targets like YOU; • That there are troll profiling and tracking tools or methods which can be recognized; • That there are ways to protect yourself without drawing more unwanted attention; • That the Troll represents a danger in that their ‘assessment’ can lead to escalation in your targeting. Is social media infiltrated by government trolls?Government and Commercial Trolls
Consider, for example, the friend ranking and layer’s of affiliation tracking tool. A graphic is created containing a simple textual message. It is graphical because there is no easy way to distinguish between two identical text messages, whereas, altering a single pixel’s color by 1 imperceptible shade of difference makes it unique, and allows thousands upon thousands of individually trackable versions. A Troll who has managed to friend a targeted person of interest then posts the textual graphic as if a sincere request. Examples will be shown.
These kinds of posts seem innocent enough and easily get spread as requested, allowing simple computerized search processes by FB’s intelligence community or marketing partners to see not only who is close to the target party, but at what layered level and loyalty or, if you prefer, like minded thinking. In point of fact, ANY image shared with a given political, philosophical, religious, or other belief or emotional message can be so tracked to perfectly define each such poster’s psychological profile, and rank their threat level to the paranoiac governmental powers that be. The same is true of marketing trolls seeking to learn about your product usage or demographic, etc.
The only safe share, then, we might presume, is textual or perhaps the sharing of a URL and it’s image, or an image we ourselves create and have perhaps included in our FB albums. Even with URL’s however, the possibility exists it is still being tracked, especially if a Troll operated resource such as Federal Jack, a known DHS sponsored Sorcha Faal disinformationa conduit targeting conspiracy theorists, activists, and other ‘potential terrorists.’ Their goal is to get you to ‘share’ their links, thereby spreading disinformation while psychologically cataloging YOU and any of your friends’ beliefs; all who click to learn more. They may need to have a troll assigned to them, after all, for being yet another ‘potential terrorist’ — a free thinker, patriot, constitutionalist, etc.
Worse, we have learned from our new Paul Revere of the coming Second American Revolution (Snowden), that NSA is not only monitoring FB activities big time but that Trolls from NSA, FBI, DHS, DOD, and even the FED, and other paranoid agencies, and even corporations who have a strong and growing list of people who think ill of them, like Monsanto and some banks — all regularly maintain false social media identities for entrapment and spying purposes. They even infiltrate online gaming. Snowden’s latest bombshell, according the foreign media analysts, indicates there were so many game Trolls that it was starting to change the character of online gaming, and special tools had to be developed so that Trolls would not end up targeting other Trolls and more easily remain inobvious. We are talking here, about games with chat or other communications capabilities within the game or as part of game support, especially when in a social network manner.
And it is clear that snooping is also rampant among commercial interests, which is certainly true in online gaming, which after all, is a commercial enterprise. FB is perhaps the biggest offender in this area.
How can you spot a social media troll?
Differentiating an innocent graphic from a potential spy tool…
There are several online graphical message generating services. FB themselves seems to be hooked up with one called your-ecards (.com). Another is someecards (.com). Anyone can use these to generate a simple textual graphic with or without use of stock illustration graphics (e.g., a man looking perplexed), typically in silhouette or line art form. They can then easily share it through their favorite social media(s) with a few additional clicks. These can always be recognized because the logo for the creating Web service is displayed at the bottom. An additional hallmark of such services is that the background is almost always colored, and there are scant few colors available. The default color or otherwise most popular seems to be pale blue, pale green, or yellow-orange.
So when you see a colored background, typically with larger or fancier text than a normal posting, you are clearly looking at a graphical text post. The next thing to look for is the logo. If you see a logo, it was likely a sincerely generated message by a genuine human resident of social media. However, if there is no such logo, the message may have been generated by a Troll using his own computerized tools to psychologically target you regarding a select individual hot button. Are you, for instance, a tax protester, pro gun, anti GMO, for or against a given politician or political topic, or simply, who is a good like-minded friend of yours as opposed to some stranger you’ve accepted on the Network. Such messages also tend to be minus any artwork — text only. There is one more defining clue to look for.
Because there may be multiple versions of the same message for targeting different individuals by multiple Trolls interested in gathering information about many someones, there is a need to tell one shared message copy from another, which is exactly why it needs to be a graphic. YOUR version must be physically different from MINE. The simple solution is to vary one or more pixels in a way easy for a software routine to detect, and then match to a targeted individual and their Troll/need. Given the countless millions of users on FB (and other social media) who might be deemed targets, it may mean that many, many dozens of pixels will need to be manipulated. My research shows that, indeed, most of the suspicious postings, in addition to missing the logos, have such visual manipulations. Examples:

This is an example of a Troll-generated chain letter designed to find out your religious views, and who among your friends is of like mind. Note the guilt factor in the last sentence, and no true traditional Christian message. Note also the dark aberration, a visual flaw above the numeral 9 of 97%.

This is an example of a Troll-generated chain letter designed to find out more about your true close friends, as opposed to casual Network contacts you don’t personally know. Again, note the visual flaws in the slightly darker ‘blur’ areas about the letters… you may need to zoom in. This phenomenon is common in such messages, creating a pool of pixels useful in manipulations.
So one needs to look for such abberations or flaws in the background, usually darkened pixels along the edge, most commonly gathered in clusters or strips. You have to ask yourself… if going to the trouble to create a custom graphic for a text message instead of simply typing it in, why would they: a) choose the ugly colors used by such as your-ecard if not trying to make you think it such; b) take the extra steps to strip away the logo if using such a service (the point being they did not); and c) end up creating an image with a flawed background (where did the aberration come from, if not deliberate)?
When these clues are present, you are staring at a Trollish spy tool. To then share it betrays and catalogs you and links you and your beliefs with any of your friends who do the same, and theirs, and so forth, on down the line. The proper thing to do is enter into the comments: “I suggest you delete this post because it fits the description of a Troll’s chain-letter spy tool to catalog, track, or psychologically profile and establish links between like-minded persons: learn more here: http://wp.me/p1GyKw-zi” That link goes to this blog post you are reading.
Then I suggest you share the post anyway with a similar message, “Share this to warn others about Troll spy tool chain-letters to catalog or psychologically profile and establish links between like-minded persons. To learn more about this tool, visit this link http://wp.me/p1GyKw-zi.”
Finally, look carefully at the original post. Most social media will have a means to indicate if it was itself being shared, or was a direct post. If direct, it’s YOUR Troll. If shared, the poster was gullible in sharing, and is not likely a Troll… but beware that that could be arranged for as a deceit — so watch to see if the poster repeats the ploy frequently. You might optionally go to the ‘cited source’ of the share and try to find the post on their wall if you want to try to see if they are the Troll, and on to the next if not, and so forth, posting or messaging those encountered along the way who are victims, if you can. But that can be a LOT of work.
Are social media trolls sociopaths or psychopaths?
More Direct Trolls; Psyops and Sociopaths
The real threat to activists and politically incorrect persons online, like myself, is government agents paid to do nothing but sit in front of a computer and pretend to be your social network friend, someone you don’t really know at all, of course. They don’t just post Trollish images, they comment, and even message you. Like the aforementioned tool, they seek to learn everything they can to psychologically profile you, as well as see who ‘likes’ your posts and what THEY comment. But they are also there to play mind games. You are officially a victim of psychological warfare, perhaps even by someone from within the U.S. military, or even the military of another country. They are quite often sociopaths, so chosen because those traits make them more efficient.
Here are some tips on how to spot and deal with this class of Troll, as well as the kind of Troll who is simply out to make trouble for a given collective of people who believe a certain way about a certain topic. You know the type, my favorite example being the warrior Atheist who deems it his life’s mission to ferret out believers in God and annoy them with endless barbs and zings as if they were evil and dangerous for daring to worship. These people will wax sociopathic, too, and even psychopathic, when given enough rope. UNFRIEND these kinds of Trolls.
Hint 1) Trolls work in packs or maintain multiple identities to be a self-contained pack. That way, if you delete one of them, others survive, and then they generate yet another new identity and friend request to maintain the pack. The advantage is that you can suffer a series of ‘In deference to your view, we all seem to believe the same (whatever)’ posts (i.e., you are an idiot on this matter). Sure. You might be an idiot. But at first, the pack is all positive and flattering to your own beliefs so you a) get used to seeing them, and b) start respecting their beliefs and presuming them the same as yours. That’s the worming in stage.
But when it is appropriate for profiling or attempting the role of agent provocateur or disinformationalist, they will all suddenly be believing in something more off the mark, and increasingly so, as often as not. But by now, you like them and their beliefs, and so, your reaction tends to be as they expect; they are pulling your chain, and observing your jerks, evaluating, and cataloging, attempting to modify your behavior through deceit — a form of mind control. Can you be controlled, or are you firmly centered in your beliefs? Are your notions your own, or being foisted upon you?
Hint 2) New Troll requests tend to be persons with scant history on the network, and very few posts, but posts akin to your own in substance. Note that Facebook asks you to suggest friends to them. NEVER do this unless someone you ACTUALLY KNOW in the real World. If you do it, you are giving them a list of new targets. Since I don’t fear and even enjoy playing with Trolls, I let anyone into my friend list, but that does not mean they get what they want from me. But you may be better off simply passing on marginally viable friend requests.
Hint 3) Try posting something deep and yet somehow provocative (in the eyes of the establishment) which requires a bit of reading and thought before drawing conclusions. Look for a pattern in response from the same suspect persons; a) almost instantaneous response in the manner of (Hint 1), and typically emotional rather than logical in nature. This is almost always short and designed to be inflammatory or provocative, a bit testy. This is followed by b) one or more secondary (pack) responses delayed rather a bit in time. These will be more in depth and thoughtful, and validate the former with logical argument, and may contain a link to give further credibility. Other brief pack replies may be sprinkled in for effect. Collectively, they are all in agreement regarding your idiocy (or whatever).
It is when the same people tend to respond in these patterns that you are very likely dealing with a Troll pack. You will find this is true regardless of what time of day or night you post. They never sleep because every psyops Troll is actually three people manning a keyboard around the clock. They can always respond quickly with the first response, but the careful response requires that they actually research and formulate the best supporting answer based on all they know about you and the topic, which they might need to first research, and likely, it involves a supervisor’s approval or must be compared against preset guidelines.
Hint 4) Thick skin, undaunted. There is nothing you can do to make these people not remain your friend, short of unfriending them, yourself. While they may match or even exceed your own expression of ire, they won’t go away no matter how you might choose to argue, or confront with insult. Indeed, they tend never to deal with insults directly, at all; they are irrelevant and serve no usefulness to their goal. A real person has an ego that must be defended, but they are just playing psychological games and feel superior regardless of what you say. But when you argue, watch out for the next hint, which is commonly employed in their responses.
This is also true of the sociopathic/psychopathic ‘cause’ trolls.
Hint 5) They tend to employ the 25 Rules of Disinformation. Easy to spot, easy to deal with, if you know what to look for. Be careful, though, because ordinary people sometimes use flawed presentation style or less-than-thoughtful posts which on the surface appear to fit one or more of the rules, when they are just being human. Watch for repeat performances, to know the difference. Give them rope.
Can trolls lead to real-world targeting?
Dangerous escalations; why we dare not ignore trolls
The real danger in online Trolls is this: their whole purpose in targeting you online can be to determine if you deserve real-World targeting, as well. With a few keystokes you can end up having your entire life put under a microscope; phone surveillance, tails, observation posts, bugs and cameras covertly placed in your home, mail intercepted and snooped, and so forth. Men in Black stuff. Its why I wrote The Professional Paranoid; a how-to book on detecting and dealing with this kind of targeting.
And, it can escalate further: electronic harassment, dirty tricks, political control technology (mind control) to make you look mentally ill to others, destroy personal relationships, wreck your income, and sabotage your life. For that, I wrote MC Realities, another how-to.
But it can also lead to the worst of all possible escalations; NDAA vanishing. If truly a pain in the neck to the government, a threat which needs to be dealt with more urgently… you can ‘legally’ (so they claim) kidnap you and make you vanish without any legal process. They can elect to torture you or give you over to some other country for ‘processing.’ Or, if they want, they can murder you and dispose of your body. This is how we know we are living in a tyrannical Police State, and why, then, government dare not tolerate free thinkers without Trolling them, and trampling on rights and freedoms at every turn, and why fear mongering is their number one justification. ‘Oooh… terrorists are everywhere! We need to TSA and NSA your ass for your own safety.’
What should I do if I encounter a social media troll?
What to do with a Troll
I personally do not mind their presence so much as some might. I enjoy providing them with disinformation, or provoking them to try to chase down a given pathway of dialogs only to suddenly drop the matter as if it never happened, or I don’t really care, or even was deliberately jerking their chain. I even kid them.
But most people would prefer to unfriend them, and there is NOTHING WRONG WITH THAT. Just know they will be right back with a new identity. It may be better to deal with the ones you know than to worry about finding the new ones you don’t yet know.
My favorite thing, however, is to educate them. I like posting factual material which challenges their personal beliefs that their job and their boss are operating on valid or just principles or beliefs, and purposes. I make them ashamed or feel guilt, whenever possible. It does not work with everyone, of course, but it is fun to try.
Are social media trolls dangerous?
Conclusion
Your privacy and personal safety could be at stake if you are in the hands of Trolls. The threat level is determined by how much our paranoid government fears people who fear government’s growing fascist police state/spying mentality, and dare to talk openly about it. The more vocal you are, or the more aligned with or closer in links to others of like mind, or the more active you are elsewhere on the Web, or the more followers you have, and even the kinds of searches you make (that, too, is being watched by government) and certainly, your own original postings… each of these things determine if you might become the victim of someone else’s Troll, or have a Troll assigned to you, and what kind of Troll.
And once your ‘threat level’ has been assessed, that could lead to escalations that you will not likely want to experience. If you get a sense that such escalations are already in place or happening, by all means read my books, because they will help you know for sure, help identify the players, and form defenses. You can also contact me personally for free and for-fee online consulting or direct intervention services.
It’s what I do when I’m not being a thorn in the side of tyranny… and attracting Trolls.
Gun Shops, Grocers, Other Retailers Key to Disaster Survival
When the stinkiest FEMA kind of stuff hits the fan, anyone who has a business dealing in key resources will find their valuable inventories and property at risk of sack and pillage by looters, or outright theft by government. There is a way to protect such assets while at the same time insuring better chances of survival of families.
How do I protect my business in a disaster?
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
What can gun shop owners do to protect against gun consfication?
The Threat to Business Property is significant in a disaster…
Korean shop owners (rooftop) defend shops during LA Riots to augment or supplant Law Enforcement (click for riot details)
In the prior part of this series we reviewed a wide variety of disaster situations that make emergency preparedness an ultra-important concern for families, reasons far more serious and far reaching than mere quakes, floods, or tornadoes. In the second part, we proposed a disaster preparedness plan much more comprehensive and truly useful than that advised by FEMA/DHS, albeit one government will never approve. Why? Because it’s closer to their own preparations and mimics their own capabilities, and removes you from dependence upon them. That means they cannot control you by being your only source for key survival items.
But the previous material addressed family needs from their perspective. And, there were certain aspects of such a plan which would prove difficult for many families without the help of an outside party. Then we have businesses to consider, who have their own unique concerns as to what happens in dire emergencies. Business owners or responsible managers of many kinds of retail and other business with select kinds of inventories or resources, should be every bit as concerned as a family, and looking for a disaster preparedness plan which specifically protects their valuable business assets, both real property and inventories.
There are several key reasons to consider this a critical concern: One, many disasters are deemed Acts of God and are therefore not included under insurance provisions unless, perhaps, paying extra premiums for specific policy riders such as a flood or tornado insurance. No insurance policy provides protection against acts of war, which includes revolution, military coups and similar political unrest, often even excluding protection against riot losses — regardless of the cause of the riot.
And beyond the worry of insurance protection, FEMA’s plan for your assets in an emergency will very likely include confiscation and take over of your property ‘for the good of the community.’ Similar concerns exist in any Martial Law situation. So if you have such a business, you should worry and wonder if there is not some way you can protect your assets from such total or near-total loss or take over. Never fear, the Professional Paranoid is here to help…
What will happen to gun shops in a FEMA declared emergency?
Partnering with Family Collectives
The prior posts in this series dealt with idea of forming multi-family unit collectives for improved emergency preparedness at the family level, as well as why such preparedness plans and kits should go well beyond minimal FEMA advice and prepare for long-term disasters, not just three day fire/quake/flood protection. This involved numerous considerations and plans in terms of organization and supplies, individual responsibilities and more. But for many such collectives as might be established, some items become difficult to come by or store due to cost or special attributes.
The bottom line is, in a serious emergency situation, looting and general criminal activity become a serious threat to any owner of a business handling inventories of critical resources which are also valuable to long-term disaster kits. Often just as important, many such inventories represent a storage problem for long-term home survival kits. Gun shops especially, and even food or fuel can be difficult to store in quantity suitable for a long-lived disaster. Many more items could be added to such a list, as a given collective of families will have their own unique set of limitations and issues to resolve. As result, even a motorcycle shop or car dealership, auto parts store, tire shop, or tool shop, may find themselves in the same position as a gun shop. In some communities, for example, boats will be a key product in need of protection and in demand as an emergency item. So there are many kinds of businesses who can take advantage of the ideas offered here.
My goal in this series of posts was to attempt to find a solution addressing both these concerns by partnering family collectives with such owners. And, the word owners could in some cases mean ‘managers,’ where owners are corporations or persons who do not themselves manage and/or live near enough to ‘take charge’ for the purpose. Such partnerships are simple: the owner joins or heads a family collective, either one they formed on their own (perhaps made up of employee families), or by joining with someone who approaches them with an acceptable offer.
In some cases, such as gun shop owners or owners of vey large facilities (e.g., super market,), they may wish to partner with multiple collectives. This is because in the event of worst-case long-term disaster scenarios, there may be a need for significant armed resistance against third parties, even to include unconstitutional seizure by Federal forces. By unconstitutional, I mean in the event of an attempt to overthrow the government by the military, or armed insurrection to restore the Republic against some other form of tyranny. We will know that horse when it rides into town; mass arrests or attempts to seize weapons door-to-door will be its hallmarks.
We all remember the LA Riots? Even though the National Guard was deployed, it was up to citizens to protect their own property. Neither soldier nor Police and Fire were of much help. Korean family-owned businesses gave us the model we need to consider following; they armed themselves to the teeth and took to the roofs of their stores and residences and fended off looters. Family units can band together in like fashion, and better yet if also joining with a one or more business owners in some mutually beneficial arrangement.
Gun shop owners, in particular, have a serious need. They become the highest-value target in town, and therefore, need many able-bodied people to bear arms — in sufficient number to become a significant deterrent to assault. This works well for the families involved, as well, providing them with low or no-cost access to weapons needed to protect their families and homes. The trick is to find ways to do it which do not amount to simply giving away inventory. Not a problem, given that provisional contractual agreements can be drawn up in advance.
How can we prevent government confiscation of our business assets in a declared emergency?
Making it work for all concerned
I propose that such partnerships might be best approached with a contractual agreement for mutual protection. The agreement should provision for both the possibility of taking possession of weapons and munitions immediately and only after a serious event transpires. It might provide for trade of ownership of weapons deployed once the crises is over for a minimum guarantee of service to the shop owner providing protection of the business property. Weapons can be deemed as ‘rented’ during the disaster with options to purchase afterwards, perhaps with rental applying to the price, or may be considered as ‘payment’ for protection helps rendered, or some mix, thereof. Such items, pre any event, need not be fully deployed to family possession, allowing for normal inventory turnover so that older inventory is sold off and replaced with new, and families don’t need to worry about storage.
Take a gun shop: Only if the family collective partner wishes to take possession (ownership) of weapons for storage at home up front (the suggested kit calls for one pistol minimum), need any money change hands. Once a serious emergency transpires, the families can be issued the additional firearms from shop inventory, and sign for them. They must keep them safe, and must use them on call or by schedule in protection of the store property. It would only take one person from each family unit at a time, given the quantity of family partnerships participating — to adequately defend the store. They ‘pay for what they use’ in the form of a rental/purchase option to be addressed after the emergency ends, perhaps involving payment terms (perhaps involving very small payments pre disaster). There are any number of creative solutions to make it mutually viable.
I am no lawyer, but in a civil emergency, many laws fall by the wayside as a matter of practicality. A gun permit process is not something you worry about when the government is shut down and lives are at stake. However, a wise shop owner might want to check with a lawyer and get some advice and deal with such concerns up front. There is no reason a single individual from each family collective could not undergo a permit process as part of the contingency preparation. What they do with the weapons in an emergency should at that point no longer matter to the shop owner, with reasonable agreements to avoid illegal uses in place. One might also want to address how to safely store key records in order to insure lists of gun holders are not compromised and lead to confiscations, anyway.
Other kinds of businesses? Consumables such as food from a grocery store which have dates of expiration would be lost, anyway, so any financial arrangement to distribute storables in an emergency with any level of appropriate financial reimbursement or property protection services of participants should, IMO, be eagerly embraced. For most shop owners, it converts a disaster where they face the potential loss of all inventory and significant property damage into a situation that more closely approximates the ultimate ‘sale’ where all inventory goes out the door to happy customers, AND the property is protected.
From the family side, a collective should easily be able to field 6-10 adults to defend as many different business sites simultaneously, while still retaining sufficient adults to protect the home base camp. Therefore, they have access to 6-10 different key survival items they might not otherwise be able to afford or store long term. It is a win-win situation for everyone but looters and would-be confiscators.
Upon event occurrence, family members ‘report for duty’ and are issued weapons, sending the appropriate portion back to the family for home defense and protection from confiscation by FEMA/Military. I propose an organized convoy is the only safe way, as otherwise, armed interlopers might dare to ambush a lone person or single vehicle. I further suggest that, if not already the case by natural instinct, a strict military-like organization and rules for command and engagement be established. Such a model should ideally trickle down to the family units as well, if a long-term event is involved.
Therefore, prior military service, especially in combat or involving combat training, is to be highly prized in any collective or partnership. Where such experience is found in a retired Officer (as opposed to an enlisted rank), so much the better. If there is additionally someone with prior intelligence or forward observer experience, or demolitions or military engineering background, better still. Likewise for any medical corps. or other medical background.
In closing, the business itself should have on hand sufficient stores of foods and other resources (as opined in the prior post) to sustain several months of a ‘stand off’ in defensive posture. A key factor will be the ability to communicate with partnering family units that they may be called in to provide force rotation, deliver emergency supplies, or outright tactical relief against assaulting forces. The prior posts cover communications alternatives in a total outage of all utilities.
How can I protect my business as well as my family in a disaster?
Related articles
- FEMA Preparing Military Police For Gun Confiscations and Martial Law (eutimes.net)
- The Use of Food As a Weapon Against American Citizens (republicbroadcasting.org)
Military Purge Underway? A Military Revolt Warning Sign
A sure sign that the government fears a military coup or the military itself is about to attempt one, is a purge. The government will purge those it fears unloyal, and/or the military purges itself of those unwilling to go along. Whoever best purges post haste, just might win. Either way, however, the people tend to loose to an errant government and/or would-be military dictator. It is, after all, how authoritarian Police States are born.
Is Obama conducting a purge of the military?
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
What causes a military purge to take place?
Reading this post you will learn:
- That history proves purges take place when governments fear their military is about to take over…
- Or when the military prepares for such takeover…
- And such tyranny grows from purges within political circles and the military to involve citizens…
- Everyone is challenged with loyalty oaths, untrue (or otherwise) accusations, tricky questions, or even torture…
- The wrong answer can mean death, prison, or ‘vanishing;’
- Evidence abounds that we have been in a pre-event purge for several years…
- That the purge is nearing the point of reaching open armed conflict;
- That the result of a purge is almost always a Police State, regardless of which side wins
Why is Obama conducting a military purge?
Updated Nov. 14 2013 Changes indicated in RED reflect latest termination and dim view of purge by Russia and China who see it as possible PRELUDE TO WAR.
Updated Dec. 10 2013 Section added and indicated in RED as relating possible ties to Global Research Web site going dark and decade old CIA plot to capture Soviet nuclear warheads.
History on Parade…

All authoritarians get rid of non supporting military men. Only in America does media not dare report it happening. (click: rarenewspapers.com)
History is rife with examples of political purges, both bloody and near bloodless, and unfortunately, both sides can end up playing the game. Sadly, we also see that most bloodless purges end up being bloody at one point or another; they push the other side into reactionary defensive acts. Worse, once one side or the other becomes dominant, the purge is extended from the national politik (government officials and military) to local politik (regional-to-city leadership and law enforcement), and from there, down to every day citizens; any such purge portends a intended shift in power to an actual or de facto authoritarian dictatorship.
The classic example would be found in the Russian Communist Revolution, which actually evolved as successive political leaders reshaped ‘the revolution’ to suit their own visions. But you find the same things generally true in the French Revolution, Mao’s Red China, or even in the American Civil War, where the Union employed the Ironclad Oath, and various Generals (see last paragraph in the link under ‘1862’) exercised internal ‘loyalty and fitness’ purges, ad hoc. One could easily be shot for a careless comment or answer.
Why would Obama conduct a purge?
A purge HERE?
There has, in fact, already been an attempted military coup in the United States. We are, or were, fortunate at the time, that the attempt failed before the purge which would have been required could get started. While most Sheeple have never heard of it because it was contained and not made public, most of the rest of us are aware of the Business Plot of 1932 which attempted to stage a fascist takeover in America by means of a military coup. Some of the biggest Industrialists of the day were involved, names which still today are iconic labels on everyday products, like Singer, and Dupont.
But thanks to one-tough and loyal Marine who tricked his would-be conspiratorial recruiters, the affair backfired. That’s a big ‘Hua!’ for Major General Smedley Butler. But a purge did follow, one which sought to eliminate the threat from the cadre of business leaders and their friends involved, including other military — along with an attempt to cover up the entire matter in order to maintain confidence in the nation’s internal and external affairs.
One thing remains clear: the general purge model is especially of concern when one is dealing with a bloody purge, because it does work its way down to citizens, Sheeple or otherwise. Especially otherwise. And so, I strongly urge that we must take a very close look at our current troubled situation and most recent history with respect to Presidents, politics, economy, international affairs, and the military. So, what’s going on, here in America, right NOW? Well, the answer to that won’t be found in mainstream media unless, perhaps, you are talking about press from abroad.
Now comes a new worry: The European Union Times is reporting the both the Russians and Chinese consider Obama an unstable, power-hungry madman and, with the latest firing (added below with RED) , have themselves taken unprecedented military responses towards possible military conflict with the U.S. and any of its Allies. Seemingly related, are two other news stories in one at the Web site regarding Chinese troops (and a spy ship) in Hawaii, and a simultaneous FEMA ‘simulation’ of cyber attack (Fire Sale) on US power and communications networks, itself timed to coincide with the largest Cannibalistic Corona Mass Ejection the World has ever recorded striking the earth and disrupting our magnetic field in a way which threatens disruptions similar to said cyber attacks . A grain of salt is due, here, as the EUT is, well… extremist in nature. Extreme ‘what’ remains in question… a bit like a super-market tabloid without aliens and pictures of personalities doing naughty things or being too fat on the beach.
Update Dec 10, in support of prior update…
Is the U.S. military conducting an internal purge?
Proof of a purge?
Many observers think its happening, including people who are far from being conspiracy theorists; media types, military professionals, and more. In simple terms, consider the following statistics and facts, none of which are in dispute, though almost all of which are veiled from Sheeple’s eyes by media and government. Mainstream employs careful wording and skips filling in the blanks with useful detail. But others mince no words.
And speaking of words, we must realize that when a bloodless purge is underway, there must simultaneously be ‘disinformation’ to cover up the fact. This means that excuses will be used to veil the truth, and this will be quietly accepted at first by both sides, often because, at least for the individuals involved, some form of blackmail or other threat is in place to insure their silent acceptance. For some, it may be some form of National Security agreement. For others, it may be a sexual indiscretion, or a criminal or financial matter which dictates cooperation lest it be made public.
So take what is often offered in ‘face value’ with a grain of salt. It is the fuller picture which is painted in the broader strokes which overpower individual words, or lack of words… and bear in mind that when there is a purge, one must also look at resignations as part of the ‘flow’ of things — especially if related to protests or potentially motivated as a self-defense move. Doubly so if in numbers.
Why is the U.S. Military conducting a purge?
Is Obama conducting a purge?
Many think so, and the preponderance of evidence cited would seem to support the notion. It is, after all, what prompted my own review (more detailed than theirs, naturally — that’s always my goal, at least). Consider these reviews, and the fact that many sources claim Obama’s differences with military leadership have to do with his asking them if they were willing to shoot Americans, presumably in a gun-grabbing operation of some kind:
Freedom Connector, Nov 16, 2012: What’s Behind Obama’s Military Purge? — by Bob Livingston, an ultra-conservative newsletter writer;
The Independent Journal Review, on June 28, 2013: Obama’s Purge; Military Officers Replaced Under the Commander-in-Chief — a situational analysis by Kyle Becker;
The Western Center for Journalism: Obama Escalates Military Purge — by the Editor
World Net Daily, The Examiner, The Guardian, and many others citing The Blaze, Oct. 23, 2013: Blaze Sources: Obama Purging Military Commanders — Sara Carter citing actual fired military commanders’ viewpoints.
There are many more, but you get the idea. From the outside, looking at the observable clues leaking out from the inside, and sometimes even from the mouths of those involved, the impression is a Presidential purge is under way. More: since the above, Sorento’s desire to attack Syria met with such resistance in military circles as to warrant an article (translated from an unstated German source), well worth a read: Historical Disgrace: The U.S. Military Mutiny Forced Obama to Retreat. Yet as already mentioned, other stories relate that the purge is because the Military is refusing to go along with plans to grab guns and shoot Americans who refuse to comply.
Why does a military purge predict a shift towards authoritarian dictatorship?
Flip side: is the military is purging itself of White Hats?
No one else on the Web seems to think so, but I’m wondering why not? When the stability of a country comes into question, forces within the military tend to start wondering if they need not do something drastic to change things, and eventually, a strongman General is able to recruit others of like mind to work out ‘contingencies.’ One of the first steps in preparing for possible enactment of such plans (a coup) is to evaluate the remaining Officer Corps, and get rid of loyalists.
Or, it may be a group of powerful business leaders who make the call, and who recruit members of the military for their cause, resulting in the same process, a ‘la The Business Plot of 1932, already mentioned.
You know something sinister and deeply troubling is going on when Veterans are being told they can’t fly the American Flag on public property, Officers, even Chaplains, are threatened with court marshal for having a Bible on their office desk or speaking about religion with others who are not already in the same faith, and telling them to resign if they have a problem with the policy. What? Oh, I forgot: the military and military policy is dominated, according to authors like Alex Constantine, by Satanists.
In point of fact, as Alex and others have pointed out, self-proclaimed Satanist General Michael Aquino, was a chief architect of the Revolution in Military Affairs, the policy which defines the next major new war type the military will face is ‘A People’s War,’ where the enemy is disgruntled patriots, Constitutionalists, and the poor and disenfranchised. Well, now, that’s just about everybody in the U.S. but the ten percenters at the top, and dumb Sheeple, is it not?
Now, while the first section paints a picture of a Presidential purge, I must remind you that both sides of a major power rift often purge, and that outwardly, the signs will typically tend to look the same. So now, let’s take a closer look at those purged and their circumstances, to see what we might decide for ourselves. After all, other Web sources speculate the reason for Obama’s purge is that he fears a military coup, a notion which alledgedly originates directly from the Russian Military and the Kremlin.
However, that story would seem to be related to another alleged Kremlin and GRU (a KGB-like Russian Spy group similar to CIA) claiming Obama had ordered the detonation of a nuclear bomb in or near Charleston as a false flag event and the military refused, prompting the firing of so many nuclear commanders. I find this fascinating, because in my book Fatal Rebirth, I predicted Charleston would be the target of a nuclear false flag attack AFTER the also predicted (in 1999) downing of the WTC by passenger jets and resulting in a series of Middle East oil wars.
Snopes.com, whom I do not entirely trust as a legitimate ‘debunker,’ does attempt to debunk the above story by attributing its true source to Sorcha Faal, a known professional disinformationalist who works for, among other people, DHS. So then, why would DHS promote this particular disinfo? That makes no more sense than the outlandish conspiracy claimed by the story. But if baseless, and not Russian sourced, why has RT (Russian Television in English) News not ALSO debunked it, and instead reported on it as factual?
So understanding if there is a purge, and who is undertaking it, and why, is going to be difficult. Really, you can’t tell your players (or their position on the team/role in the game) without a roster. So here it is, so you can decide for yourself…
What are the signs of a military or political purge?
Point Comparisons: Roster of 266 Vanquished Officers and Key Staff under Obama
This is an updated and more accurate compilation the found in lists elsewhere which cite 197 or fewer. More than 50 being offered in rich detail, here. These numbers represent a massive bloodletting not seen under any prior President in American history. There are so many you might be tempted not to read them, but in the reading, at least of their name and command position, you find some interesting, if not scary things, not to mention patterns. To be sure, some who were let go may have indeed been let go for non-purge and quite legitimate reasons, but the large numbers of higher rank Officers and the nature of the clumps of specialities/assignments/duties, especially, amplify reason for concern that more is afoot than ‘bad conduct’…
Fired Nov. 3rd, Colonel Eric Tilley, Commander of Japan’s largest U.S. base in Japan for ‘allegations of unstated misconduct.’
First Lieutenant Ehren Watada was the first Officer to refuse deployment to Iraq as an illegal war, was eventually allowed to resign. Now, if his view was unjustified in the eyes of military, why was there no court marshall? If justified, why did we go to war? It implies disparate viewpoints in military ranks, and between military leadership and the President;
Major Stefan F. Cook, US Army Reserve, refused to deploy because he did not believe Barry Sorento was a legally elected President, joining with two other officers according to Wikipedia (no Web source names them, but they are described as a retired Army Major General and Active Reserve USAF Lieutenant) in a law suit (Cook vs. Good – scan down). They did not win their suite, but neither did they have to serve, again meaning disparate viewpoints. Touche’;
Captain Connie Rhodes, US Army Physician filed a similar suit (just beneath prior link, same page);
Predator Drone Pilot Brandon Bryant resigns USAF over immorality of drone attacks on noncombatants, making five people who refused to serve and suffered no court marshall;
Colonel James H. Johnson III, Commander 173rd Airborn, fired and convicted of bigamy and fraud in expense accounting, apparently jumping out of the airplane and into the frying pan;
General Joseph Carter, Commander Camp Edwards and Adjutant General of the Massachusetts National Guard resigned even though a months investigation failed to produce evidence of a rape allegation;
Brig. General Jeffery A Sinclair, former Dep. Commander 82nd Airborn in Afghanistan, fired and facing possible Grand Jury review for criminal sexual indiscretions — sounding a bit like the CIA entrapment of Wikileaks mastermind, Julian Assange;
Army Major General Peter Fuller, Commander in Afghanistan (of unstated forces — which to me implies intelligence hanky-panky), let go in 2011;
Marine Major General C. M. M. Gurganus, Commander Regional Command Southwest and 1st Marine Expeditianary Force (also Afghanistan) was let go in 2013;
Marine Major General Gregg A. Sturdevant, Commander Aviation Wing at Camp Bastion, Afghanistan, and Director of Strategic Planning and Policy for US. Pacific Command, let go in 2013;
General David D. McKiernen, Commander of the Afghanistan Theater was let go at Obama’s orders after four months of arrival, for saying the campaign was less noble than was Iraq. That was 2009, making him the first four-star General released by a Commander-in-Chief since MacArthur by Truman. In 2010, Obama fired…
General Stanley McChyrstal, Commander of NATO International Security Assistance Force (IASF), Afghanistan, a matter linked to the death of reporter Michael Hastings. He was replaced by another soon-enough-to-be-fired General Petraeus, below. Seems like Obama liked no one involved in the Middle East, does it not?;
General David H. Petraeus, also left the Army as NATO IASF Commander as to be appointed by Obama as Director of Intelligence, CIA. He then resigned CIA over charges of an extramarital love triangle, but at the time there was the controversy about the CIA’s role in the handling of Benghazi intelligence and no-go rescue aftermath. And, stepping back once more, the man who replaced him at ISAF when he stepped up to CIA was…
Former General Michael T. Hayden, in like manner yet again, quit the USAF to be appointed by Bush II to be Director of NSA, and then, also like Petraeus, was fired over extra-marital sexual conduct (officially), and unofficially, over internal disagreements with Obama on intelligence policy and validity of evidence regarding alleged Syrian nerve gas attacks (shades of Bush and Weapons of Mass Destruction in Iraq);
Marine General John R. Allen, Commander of NATO International Security Assistance Force, Afghanistan, was investigated and removed for ‘inappropriate communications regarding Bengahzi’ (he countermanded White House orders not to attempt rescue of the besieged Embassy). The investigation continues without fruit, be he was also seemingly an injured party in the above Petraeus love triangle. You couldn’t make this stuff up as screenwriter of a Kardashian’s in Uniform special. Now, regarding Bengahzi…
General Carter Ham, Commander Africommand (counter terror operations) also relieved of command and arrested for attempting rescue despite orders from White House to stand down… and before him…
General William ‘Kip’ Ward, 1st Commander of the Africommand fired for ‘financial irregularities’ in expense accounts;
Rear Admiral Charles M. Gaouette, Commander of the Stennis Aircraft Carrier Strike Group relieved of command in the middle of Middle East deployment for unstated ‘inappropriate leadership judgement’ also thought Benghazi related. But not just him…
Capt. Owen Hornors, Commanding Officer of the Carrier Enterprise, no less, was let go for ‘making and showing to the crew raunchy cartoons.’ No patterns here, folks — move along, move along;
Rear Admiral Ron Horton, Commander of Western Pacific Logistics Group was also fired for knowing about and failing to put a stop to the Enterprise cartoon shows;
Brigadier General Bryon Roberts, Commander of Ft. Jackson (training facility) resigned over charges of an ‘altercation’ with a woman. He commanded the training of the Iraqi Security Forces slated to replace US Military, and served directly under the Joint Chiefs with distinction;
Vice Admiral Tim Guardina, U.S. Central Command, drops two ranks to Rear Admiral, and looses his 2nd in Command position in charge of nuclear weapons for allegedly using counterfeit casino chips (felony fraud). Now that would be easy to set up as a frame up… which begs the question, why no criminal charges or court marshall, if true — or a resignation? It’s called ‘leverage’ and keeping a close eye on a person in question by keeping them close at hand;
Four-Star General James Mattis, Commander of US Central Command, being fired for ‘Mad Dog’ warnings to the Obama adminstration on the dangers of proposed Middle East military actions in Syria. Very interesting if, as stated in the next item link, he was the one responsible for that firing, and perhaps more so, if it was his replacement who arranged it (at this point, I’ve not been able to isolate which might be closer to being true, if either);
USAF Major General Michael Carey, Commander 20th Air Force (that’s 3 Wings of ICBMs/450 warheads at three AF Bases) was let go in 2013, making the third man in charge of nuclear forces to be let go — unprecedented;
Army Major General Ralph Baker, Commander Joint Task Force Horn of Africa in Djibouti, Africa, let go in 2013 — anti piracy and counter terrorism support unit, also likely to know what really happened in ZeroDark Thirty;
Lt. Col. Matthew Dooley, 20 yr Vet Army Instructor for National Defense University and Joint Forces Staff College allegedly fired at Obama’s request for teaching a previously approved course called Perspectives of Islam and Islamic Radicalism (for which he had also previously been commended) because it was deemed ‘offensive’ to Muslim organizations who somehow managed to learn about it (but had not experienced it). On the other hand, the Army Vice Chairman of the Joint Chiefs, now head of US Central Command himself described it as “against our values,” and so, this appears more likely a military purge victim than an Obama victim, done in a way that blames Obama publicly. A nice two-edged blade being twisted;
Commodore of Logistics, Lt. Col. Allen B. West, Battalion Commander, 4th Infantry, 20 year vet forced to retire pensionless for coercing terror attack information from a prisoner in Afghanistan by discharging his weapon to get his attention. Now that’s odd, because Logistics has nothing to do with prisoners. However, Logistics is THE MOST KEY tactical element of ANY military action;
Marine Colonel Daren Margolin, Commander of Quantico’s Security Batallion — FBI’s and USMC training facilities also used in joint LEA/Military trainings even when disallowed by Posse Comitatus;
Marine Colonel James Christmas, Commander 22nd Marine Expiditionary Unit and Special-Purpose Marine Air-Ground Task Force Crisis Response Unit, let go in 2013;
In 2012, Six USAF Training Officers from Lackland AFB base were fired after being charged with rape and adultery;
In 2011, 25 Command Naval Officers below the rank of Admiral were let go (not already mentioned), including captains of nuclear missile warships and submarines;
Recall the TV show Last Resort, where an American sub commander staves off an unjust false-flag nuclear first-strike against Pakistan as part of a military-coup deception… by threatening D.C. with attack, instead?;
Also vanished in 2011, 12 senior enlisted Navel personnel in charge of key programs, facilities, and projects;
In 2012, an additional 28 Command Naval Officers below the rank of Admiral were let go, again including several captains of nuclear missile warships and submarines.
Also vanished in 2012; 15 senior enlisted Navel personnel in charge of key programs, facilities, and projects;
Meanwhile, still in 2012, 157 Career USAF Officers below the rank of General were forced to quit. Moreover, and potentially related, the USAF has resorted to offering nearly a quarter-million dollar bonus to fighter pilots to keep them from resigning after meeting their minimum obligation. Yet the 157 were ‘let go due to budget constraints’ according to the official story?
All the while this has been going on, and Obama’s proposed actions in Syria have not been sitting well with anyone but Sheeple on the citizen side, it turns out the military was not too crazy about the idea, either. Not just General Mattis and other officers already mentioned, but rank and file enlisted: a spontaneously created ‘photo-bomb’ campaign flooded the White House with individual refusals to serve in any military action ‘helping Al Qaeda’ fight the Syrian Christian government… appropriately went viral on facebook.
Does Obama fear a military coup?
Another kind of Roster: 92,600 Enlisted are being disbanded
Bloomberg is reporting, with the official line being budget cuts, that nearly 100,000 soldiers, sailors, and Marines are being let go starting the first of this month (several weeks ago, Oct.). The troubling element is that the bulk of these (67,000) are US Army. If gun grabbing operations took place, the brunt of such action would involve the Army. That fact, and the fact that the military has been using a Shoot Americans Questionnaire which would help them purge themselves of those unwilling to do so — if their actual plan, makes me wonder who is being forced out, and why?
And here’s another reason to wonder: If the Sorcha Faal story was done for DHS, and keeping in mind that DHS ordered enough ammo to kill everyone in North America several times over, the ONLY possible motive I can deduce for fostering Faalishness is to fuel a counter conspiracy to the real conspiracy. That is, if they were planning to shoot Americans over gun grabbing efforts, then why not create a counter story saying the Military was revolting because the President was going to grab guns and order them to shoot Americans to do it? It would be another two-edged sword blaming Obama. Watch the left hand so you don’t see what the right hand is doing.
I’m just saying. I really have no way of knowing any more than do you. But I do know how disinformation works, and that is definitely one way it is used. It’s how it got its name.
What does a purge of the U.S. Military mean?
The broad view: being caught in the middle
The stage has already been set for our consideration, and depending on who is doing the looking, lots of people are starting to see that a purge is taking place, almost all eyes focusing on the US Military and/or the Obama administration. Point of view dictates how they analyze the whys and wherefores, but they all agree that purge is the word.
Bloodless, thus far to be sure… but to remind… a bloodless purge tends to force the other side’s hand and can easily escalate to a bloody one, if not also outright armed conflagration. At some point, someone elects to do something to end the gutting of their power base, and that something is not usually gentle in nature.
That DHS has been buying up weapons, munitions, coffins, medicines, and other key items in quantities suitable for a twenty-five year war… and that FEMA has launched a massive ‘disaster’ preparedness advertising campaign, simply adds fuel to whatever may be the real cause of the mysterious smoke under consideration.
If you find this all a bit troubling, you may wish to do some more reading. One place I can suggest you start, is my own book set, Fatal Rebirth, which written in 1999, predicted the entire pickle we now see ourselves in, from the bringing down of the WTC by passenger jets to financial debacles to the purge, and much more.
A free ebook copy of Vol I can be obtained by email request to pppbooks at Comcast dot net. Given the violence purges tend to evoke, you may also wish to read my post (series) on emergency/disaster plans and resource kits to cover ANY threat, natural or man made. Who else but the Professional Paranoid would dare bribe you with a free book just to read a blog post? Email me!
Who is purging the military and why?
Related articles
- Obama’s Military Purge (canadafreepress.com)
- U.S. Military Could Depose Obama, So He’s Destroying It (calvinistview.com)
- Obama Firing of Military Reminiscent of Stalin’s Purge (vaticproject.blogspot.com)
On False Flag Zombie Attacks in July
When the CDC starts talking about zombie attacks, DHS buys more ammunition than God and calls out all Federal Agencies to prepare for (something) at 100% strength with two weeks notice… while a Zombie blockbuster movie scares our pants off… there might just be something to worry about.
When do Zombies act on behalf of National Security?
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
Federal zombies may be in our future
OK, this might be tongue in cheek. MIGHT BE.

Future Post Office Poster? From notrightinthehead.net, a collection of more than interesting Zombiesque material (click)
But it is completely factual (scary movie music rises). I just saw a couple of video blogs (streaming Web radio) where one of my kindred spirits (translation: conspiracy theorist, or on a good day, as we prefer it, investigative reporter) was interviewing someone claiming to be in the know: DHS, FBI, FEMA, and just about every other agency, military as well, have been ordered to bring all manpower, reserves, and resources, to 100% capacity by July 3, and to stand by for further instructions.
I’m not comforted by the fact that ALL the search engines can NO LONGER FIND THIS WARNING no matter what I type in (it would have helped if some of the words were not in use in gazillions of other vids, too). Thing is, two days ago, it was EASY to find using the same words. Who has the power to do that? No matter. I’m on the job. A few ones changed to zeros in government’s Internet won’t stop me.
Note: This kind of censorship and information manipulation is one reason I formed nnn.osp.org to create a 100% citizen-owned-and-operated wireless Internet alternative where there is no ISP (no monthly bill), no government or corporate censorship, spying, or control: YOU are the Web!In trying to solve that problem, I encountered something which revealed even more useful information than I was searching for. The CDC is apparently involved, too. We are talking about a terror drill involving a ‘fake’ outbreak of (something awful). Wince. Gee. What could that be? Well, I got to thinking. Recall the CDC warning about what to do if a zombie attack broke out?
Well, they claimed that was tongue in cheek, too. But I’m starting to wonder. Have you seen World War Z? Nothing seems far fetched after that! I mean… first CDC puts out the defense guide… then DHS buys enough ammunition to kill all the extras in WWZ (and every citizen in North America, with order quantities in Satanic numbers, no less)… not to mention enough coffins to take care of the half-eaten bodies… and now DHS, FEMA, FBI, the National Guard, (and CDC) are manning up for something very big.
And even if not Zombies… let us not forget that some guy named Kokesh (not related to David Koresh) is planning a ‘Million-man’ armed march on Washington, D. C. on July 4th. I mean… Damn! I don’t know what it means, but what I’ve more recently learned does not make me feel any better about, it all…
Why is terror drill set to coincide with Scout Jamboree?
Terror Drill Set for Scouting Jamboree
The orders for these agencies are to be at 100% by July 3rd, and then to stand by. Turns out, unless a cover story for a general Martial Law (you don’t suppose Kokesh is going to end up in a shootout with Feds, do you?) move to seize power by the New World Order, that there is to be a terror drill in Yellowstone during the Scout National Jamboree (July 15-24). But wait one minute; is it not true that at almost EVERY major terror event blamed on some turban wrapped, kidney machine toting, Koran spouting man with a beard… that there was simultaneously a terror drill of the same exact sort taking place at the same time?
Is that not the HALLMARK of a false flag operation? You create an exercise or drill on the same date in the same community for the same kinds of details (e.g., type of attack, type of target), and then, if the people really responsible (no turban, kidney machine, or Holy book) happen to get caught before they can pull it off, you say ‘It’s OK, they are with us, and everything is coolness.’ Where have we seen that used before?
A few places. The Sarin gas attacks in Japan. Sept. 11. The London Subway bombing. Bombing in Madrid. The Norway mass shooting. Even Aurora and Sandy Hook. Retired Army Intelligence Officer, Captain Eric May has said, “The easiest way to carry out a false flag attack is by setting up a military exercise that simulates the very attack you want to carry out.”
Are Zombies real after all?
Zombies on parade
Again, ‘tongue in cheek’ can only go so far to making one comfortable about the facts. Also while searching for the missing radio show links, I instead found some disturbing video — tons of it, in fact, which claim to evidence real Zombie attacks, including one faked ‘secret FBI briefing.’ But only one of these bothers me enough to deserve sharing, as it is a montage of real news stories that are quite shocking and, collectively, imply there are real people out there who are certainly acting like Zombies, and who are apparently quite hard to kill, too.
But that’s not the only disturbing thing about the video.
The second is found at the end of the long-winded (classified) reading of a (classified) Bill on the Senate Floor that (classified) seems to regard some kind of (classified) serious catastrophe, and what government is going to do about (classified.) At the very end, as if a causal afterthought of NO IMPORTANCE, the reader quotes, “and draft a NEW BILL OF RIGHTS.”
E X C U S E ME?
A new Bill of Rights? What’s wrong with the one we have such that once this (classified) happens, it is no longer useful? To me, the ONLY scenario where that makes sense is if the country has become an official Police State under perpetual Martial Law, the result of a military (classified.) Well, let me tell you if I see even a hint of that taking place, I’m going to (classified) and (classified) and all of (classified) had better double their (classified). Even if they claim it was the Onion Congress.
Well, that’s all I can think of to say about something that is so far fetched and based on ‘less than mainstream’ resources. So I’ll simply leave you with the original video which started the whole thing off. I did find it. But I warn you, it is not the sort of thing I would normally care very much about paying attention to now days, given the veritable flood of such ‘sky is falling’ reports on YouTube.
However, I also remind you, in my book set Fatal Rebirth, and resulting screen play published on the Internet in 1999, that the sky was going to fall in New York City, raining passenger jets upon the World Trade Center, and resulting in Middle East Wars. Some of us Chicken Little’s base our warnings on a bit more than conjecture. You can get a free ebook copy of Volume One, and see what else I’ve correctly predicted, and what things I’ve warned of which have yet to transpire.
It also behooves me to add, here, that as a specialist in privacy/security who helps targeted individuals and deals regularly with Political Control Technology… that I should mention that some estimates are that the government has created up to two million ‘sleeper’ agents using Manchurian Candidate mind control methodology. If true, we are talking about programmable people who can, with a simple text message or other signal, be launched off on almost any kind of mission with no recourse or understanding. Blindly obedient.
Such people can be made to believe any unreal circumstance, or believe themselves to be anything or anyone, and are often capable of exhibiting super-human traits (such as seeming to be bullet resistant). I’d hate to think about what would happen if a flood of such persons were unleashed thinking themselves Zombies. They soon enough would be, for all practical purposes. I’d not want to be in their warpath. World War Z, indeed.
Related articles
- False Flag Biological Attack Expected This Summer? (pakalertpress.com)
- National Scout Jamboree 2013 False Flag Insider Warning (thetruthseeker.co.uk)
- NEVADA GOVERNOR CANDIDATE Warns BOY SCOUT JAMBOREE MAY BE NEXT FALSE FLAG (secretsofthefed.com)
- May 21st Is Judgment Day So Begins the Zombie Apocalypse (wholesalecostumeclub.com)
- The Government’s Knowledge of the Zombie Apocalypse (costumediscounters.com)
- False Flag Insider Warning – National Scout Jamboree 2013 (oneworldchronicle.com)
- Mass Casualty Terror Drill Planned for July 2013 During Boy Scout Jamboree (2012thebigpicture.wordpress.com)
Revolt Against Mongressanto: GMO Crops Torched in America
Though a controlled media is suppressing the story, 40 tons of GMO crops were torched, prompting an FBI investigation. We The People do NOT WANT GMO, and if the Monsanto Congress does not watch their step, arson will become outright violence, and from there, even lead to revolution.
Why were sugar beets set on fire in Oregon?
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
Who is Oregonians for Food and Shelter?
Update June 22, 2013: Additional research reveals some interesting things about the who and why behind the $10K reward offered for the beet burners… at document end.
Are Monsanto and Syngenta GMO criminals?
What you will learn reading this post…
- People are taking the law into their own hands to kill GMO production[
- There is an apparent media blackout, even on the Web;
- The government is ramping up for what may end up being another WACO/Ruby Ridge standoff;
- We may be looking at the Boston Tea Party of 2012 just before the next American Revolution.
Who is the earth liberation front?
Rebirth of the early Earth Liberation Front?
I Can’t Believe I’m the FIRST and ONLY one to report this on the Web.
NOT ONE MEDIA OUTLET outside of local circles has dared to mention it, perhaps because government fears that if the public learns that other people are getting fighting mad (literally), they might join in, and become an actual revolution. It was only reported locally live on KXL Radio and echoed by the Oregonian, where the ONLY Web mention exists, hard to find because the headline wording is carefully avoids the most likely keywords for a search — took me rather a while to find it. Here’s the scoop — PASS IT ON!
40 Tons of GMO Sugar Beets were set ablaze in Eastern Oregon, yesterday. FORTY TONS — the entire acreage of two full fields of crops IN THE GROUND were set ablaze over a THREE NIGHT PERIOD OF TIME. That means ARSON. And I have to say I am cheering! The only way could feel better about it is if I had dared to do it myself — which to be clear, I would not: I don’t look good in prison orange, and would be too worried about possible loss of life if things went terribly wrong.
Evidence is that 6,500 plants were destroyed BY HAND, ONE PLANT AT A TIME. That, in turn, implies A LOT OF PEOPLE were involved: would you want to stick around once a fire was going and wait to be discovered? No, someone (many someones) probably wanted to move as quickly as possible. WE ARE TALKING ABOUT A MOVEMENT, a kind of ORGANIZED REVOLT — and this is exactly the kind of retribution I’ve warned was coming; when lawmakers and corporations refuse to honor the Constitution and instead engage in ‘legalized’ criminal acts such as enabled by the ‘Monsanto Protection Act.’
This is all shades of… well, the BOSTON TEA PARTY. Instead of throwing tea into the harbor to protest taxes, someone was throwing flames onto crops in the ground to protest New World Order shenanigans. We are a long ways from Boston, but more recently we have the Earth Liberation Front, a group which also had its roots in Oregon (I love my State and our people; we have core beliefs and fight for them). The ELF, in 2000, burned the offices of a GMO research project at the University of Michigan, a project funded by the Federal government and Monsanto at the time.
The ELF, or ‘Elves’ as they are sometimes called, is an ad-hoc group with its actual origins in the U.K. But forest mismanagement caused splinter cells to be established in Oregon, and subsequently, Michigan and elsewhere as new corporate wrongdoings became evident. Like the IRA, they have an official, public side, one not associated with criminal adventure, and instead focused on educating the public on the issues, such as the Gulf oil spill. They are a kind of militant Green Peace, perhaps.
But ELF cells normally come forward immediately to claim responsibility, because to them, its all about publicity to educate the public. Since there has been no statement, I’m deducing it is simply Oregon Farmers who have said, ‘Enough!’ Another clue that may be the case is that this comes on the heels (two weeks) of Japan’s rejection of the entire Oregon Wheat crop for the year (a tremendous financial blow because over 80% of Oregon Wheat is exported) because ONE report said ONE field was contaminated with at least ONE GMO plant.
The rightful fear is, because of pollination processes, once you introduce a GMO crop of a given variety ANYWHERE, the wind and insects will spread its genetic contamination to non GMO fields, and thereby ruin the ENTIRE INDUSTRY for a region. In fact, Oregon farmers have tendered a multi-billion dollar class action law suite against Monsanto, joining a long list of states doing so. Monsanto has experimented with GMO crops before they were approved in 16 states. They were supposedly all destroyed, but state after state is finding out the hard way, that Pandora’s box has been deliberately left open.
But while other governments in Europe and elsewhere are passing laws to ban GMO crops, and burning entire crops themselves, in America, our government is passing laws protecting Monsanto from legal repercussions, and therefore, it seems, farmers are forced to burn the crops, themselves. This means that where in other countries, citizens are being protected from corporate crimes, in America, citizens are forced to become ‘terrorists’ to survive. That’s how blatantly corrupt our corporate police state has become, I’m afraid.
Can GMO spark an armed revolution?
First Blow For the Revolution?
In this case, both fields belonged to the same Corporate Agricultural giant known for embracing GMO, though trying to do so quietly, another reason perhaps big media has kept the story from reaching the Internet. We are talking about Syngenta. Nowhere on their US Web site will you find mention of GMO, but that is exactly what the company is about. They have even lied publicly in writing on this issue with a public declaration. Yet their very corporate name shouts GMO.
But the FBI, and local media knows better (and now, you)… because apparently someone from the Syngenta operated farms mentioned the fact as a possible motive for the arson. This is a serious matter in many respects. It throws down the gauntlet and says, WE ARE MAD AS HELL AND ARE NOT GOING TO LET YOU GET AWAY WITH THIS BULLSHIT ANYMORE! But it also raises the stakes and put lives and property at risk, and if it goes wrong, could end up sparking an armed revolution.
Imagine the likely scenario: the FBI identifies a particular non GMO farmer as being participant and puts together a 100 man assault team to surround their homestead, land they’ve been farming for generations. What do you suppose would happen if they stood their ground? You would have another WACO standoff, another Ruby Ridge. Do you suppose that the other several dozen participants in the crop burning would stand by and let them pick them all off like that, one by one? I doubt it.
They would muster every rifle their families could carry, and call in farmers from adjacent counties, and likely be joined by some number of citizens from the local communities, and surround the FBI and other local authorities. They might even be joined by local Sheriffs, if not out of sympathetic understanding and general GMO angst, then in hopes of defusing the situation. I’m telling you, this can easily get out of hand.
And in a way, I’m hoping it does. Because I think WE NEED A DEFINITIVE EVENT to send a CLEAR MESSAGE and draw a line in the sand: NOT ONE INCH MORE — BACK OFF! It would rally the informed to action, stir the Sheeple to understanding, and FORCE THEM to take a side, lest they end up in a possible cross fire if shooting breaks out everywhere GMO crops and corporate properties exist, and their executives live.
Even though it could easily spark a full-scale revolution, I’m still for it. That threat is not lightweight, either — it is incredibly easy to start and carry out a successful revolution. I’d be tickled pink to live in America, once more, a country based on a social contract called the Constitution and Bill of Rights, where government was BY THE PEOPLE, FOR THE PEOPLE, of the people, and not a fascist police state in the making BY CORPORATIONS, FOR THE NEW WORLD ORDER.
GMO? Burn, baby, burn…
Mongressanto? You may just be next.
Who are Oregonians for Food and Shelter?
Update: The Who and Why of the $10,000 Reward
‘Oregonians’ for ‘Food and Shelter’ sounds like a charity that provides food and shelter, but that’s not right. Their Web site describes themselves in terms which, after thoughtful consideration, would leave you believing them a non profit NGO, a special interest group (SIG) of professionals seeking to educate their peers in the latest timber and agriculture technologies. Closer to the truth, is that they are a Political Action PAC, putting out their own Voter’s Guide, and involving themselves in political matters impacting timber and farming.
Their members are a who’s who of AG and Timber, but with a specific bent toward biotech… specific biotech. Their Boards and Chairs are well peppered with people from Monsanto, Syngenta, and other firms with a vested interest in GMO, and firms they do business with. In fact, there are even two firms represented who have had consensual dealings with Central Intelligence Agency fronts. One of these was harmless and related to fire-fighting, but the other (Portland General Electric) was tied to much darker matters, though I’m sure they were not quite aware of such details. But then, those same folks also went to bed with ENRON (also a CIA operation), didn’t they?
The OFS founder is one Terry L. Witt, who cites himself as a professional Manager of Non Profit Groups, as though you should go see him if you have one in need of management. Really? The Web site was founded in 1999. Within a few months, Terry was writing in support of Monsanto’s patent infringement suit against a farmer over GMO crop migration (contamination) such as faced by Oregon Wheat growers. It would not be the first time he would play hatchet man for GMO, additionally using op-ed in the Oregonian to disinform on behalf of (again) Monsanto.
Indeed, if you look at the one and only truly informational page at the Web site (despite the fact they list three topics to choose from – the other two have no links provided), the topic is… you guessed it; pro GMO. So what is the real agenda, again? But perhaps we should overlook this narrow view, because they do point out their Web site is still under construction. What?
Established in 1999, and still under construction? Could it be because the Web designer is (whois information) Troy, Terry’s son, operating out of their $700,000 home in Tigard? Hmmm. Troy has his own business (he is a photographer and ‘lead designer’ at a ‘design studio’), and his Web site is even more under construction: it consists ONLY of a logo (ergo, my use of quotes). There is not even a statement on being under construction since created in 2005. “Focused Marketing, Messaging, and Design,” the logo claims.
This could be the trait of (choose one):
a) someone not very good at what they do; b) a CIA front; c) a corporate front for money laundering (e.g., payments from Monsanto); d) a front or over billing a client (e.g., Monsanto); e) a clever ploy to distract conspiracy theorists and waste blog reader’s time; f) all of the above.I’m sorry, but I come away with the distance impression OFS is nothing but a surrogate for GMO interests, and thinly veneered, at that.
That’s the WHO and the WHY of the $10K reward.
Frankly, given these facts, I’d rather someone offer a $100K reward if they would all simply go away.
Related articles
- Monsanto Video Revolt: Global anti-GMO online rally launches – RT News (2012indyinfo.com)
- Monsanto Killing U.S. Agriculture (personalliberty.com)
- Monsanto Declares Defeat In European Market (fastcoexist.com)
- Belizean Activists: Illegal Planting of GMOs an Act of Biopiracy (foodfreedomgroup.com)
Flight 800: At Last! I’m no Longer a Conspiracy Theorist!
For nearly a decade I’ve been trying to get media and the public to examine some simple proofs of a conspiracy we call Flight 800 Friendly Fire; the downing of a jumbo jet killing 230 souls with a Navy missile fired in a war game exercise gone wrong. They only wanted to call me ‘just another conspiracy theorist.’
NOT ANY MORE.
Was flight 800 shot down by a navy missile?
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
NTSB admits Flight 800 shot down

DISINFORMATION!
Seven years is a long time in Sheeple years (1 year in Sheeple years = 40 years of apathetic stupidity) and most Sheeple don’t even remember what Flight 800 was about, and some readers here may be younger and simply have no clue, or wish a refresher. In simple terms, Flight 800 was Trans World Airlines 747 jet bound out of New York late evening on July 17, 1996. Twelve minutes later, the plane and all 230 on board were lost in a fiery crash into the sea just off of Long Island. No one knew why, but rumors quickly sprang up that it was shot down by a Navy missile. Even military witnesses said so.
Even faster, the Wag-the-Dog disinformation engine of the U.S. Navy, Department of Defense, CIA, FBI, and the rest of the Federal Government launched one of the biggest criminal conspiracies of all time to cover up the truth. From the very beginning, I quickly involved myself as investigative writer because I quickly spotted traits of disinformation at play, and because I was compelled by a very credible claim that friendly fire was to blame by a revered source.
Non other than Pierre Salinger, former Press Secretary for Presidents John Kennedy and Lyndon Johnson, and former ABC Newsman, said that he was calling a press conference to reveal information from a CIA informant confirming the fact. But he had been set up for a fall with one of the oldest tricks in the disinformation handbook (as result, I wrote the 25 Rules of Disinformation to expose such tricks — my most famous and most read work with over 25,000,000 downloads); he was to become a strawman sacrifice to quash the rumor and associate it with ‘an untrustworthy Internet.’ Hence, the Salinger Syndrome. It destroyed him, but he is a hero for it.
I won’t explain the details of that, here (there is plenty of detail at my Flight 800 pages), nor much else about Flight 800 or the three-year running battle with Federal agents I and other civilian investigators had to endure to simply seek the truth and justice. I will only say that they used every dirty trick to shut us up they could muster, including sending out whole teams of FBI agents to intimidate us in person, Naval Intelligence people to pump us to see what we knew (pretending to be ordinary citizens), and I even got death threats from a foreign agent. Surveillance? You bet, including multiple vehicle tails, various aircraft, high-speed chases, and literally having to walk around Federal and local operatives to get from one side of a public venue to another. They wanted us to know they were dogging us.
But the one OTHER thing they did universally was to discount us by calling us ‘conspiracy theorists,’ and then ignoring anything we had to say. When the NTSB report finally came out, I personally had a field day combing over it and pointing out the obvious lies. They had falsified evidence, concealed evidence, and manufactured evidence to prove it was an electrical short which exploded a fuel tank. But that was also clearly impossible as even their own report showed. For each such point I’ve just mentioned, I was easily able to offer three different proofs. See my Three Simple Proofs (look for the small image of the gold NTSB CD a ways down the page).
But I was merely a ‘conspiracy theorist,’ and so, they still ignored me. Not one local news director would air my material, and the Oregonian flat refused my editorials. Of course, every major Network at the time was owned (controlling interest) by a major military contractor making Navy missile parts. Never mind that the proof was easy to illustrate. I was a conspiracy theorist, and THAT, was that. “Don’t confuse us with the facts, our minds are made up for us.”
Fast Forward a little.
The report finished, only one thing remained. The head of FBI, who personally monitored material I posted to my Web site (I cannot tell you how I know this without someone at FBI getting into a lot of trouble), and the head of the NTSB investigation, all resigned their posts at the end of the affair (publishing of the report), literally walking out on a scheduled meeting with a waiting collective of fellow civilian investigators, family members, and other ‘conspiracy theorists’ who were refusing to buy magic fuel tank explosion as ‘fact.’ They could not bear to look them in the face and lie to them in person, it seems.
With their resignations, NO ONE had ANYONE they could officially speak with, no one who would listen to, much less answer questions or challenges regarding the lies and blatant evidence of same. This was true in the halls of government, and in the newsrooms. We were all once more easily dismissed; conspiracy theorists are political and social zeroes in government and media circles. That’s why government loves to label dissenters. Pick a label, any label… in a political storm.
Fast Forward a LOT.
TODAY! On the radio today I heard that several NTSB Investigators have come forward and publicly admitted that the official report was doctored, stating flatly it was impossible that the fuel tank was responsible, and that there was indeed (as I had not only been saying, but showing) evidence of missile fire; it was a massive cover up.
What this means to YOU.
It means that conspiracy theorists (the good ones, like me – if you will permit me to so claim) are merely investigators forced to wear a label. It also means that many conspiracies are REAL, and self evident by the conflicting information in the official stories, and the cover up efforts and disinformation which follow. A cover up is itself proof of a conspiracy. You cannot have a cover up unless there is something to cover up, and its existence proves not only the crime is real, but it cannot even be undertaken except by a conspiracy of multiple parties to effect cover up; two interlocking conspiracies in one.
The lesson is: QUESTION GOVERNMENT, they lie. QUESTION THE OFFICIAL LINE, it has holes. QUESTION MEDIA, they are bought.
I urge you to read about Flight 800 at my Web site. There, you will learn things no other investigator has revealed. I was the only one to discover and illustrate the actual fraud in the NTSB Report. I was the first one to identify the ship most likely to have fired the missile (and subsequently visited by a foreign Agent making a death threat on behalf of their country — which should tell you something about the accuracy of my claims).
It will show you how easy it is to pull the wool over a Sheep’s eyes, and make us all into Sheep. It will show you how easy it is to fake it, and to make the public believe an unreal thing. It will reveal how easy it is to have a controlled media. It should leave you with a much greater respect for Truthers, and for conspiracy theorists, in general.
But why should I care, you might well ask? After all, I’m no longer a conspiracy theorist now that my theory has been proven FACT, and the conspiracy proven REAL, right?
WRONG. As long as Mr. Sorento and his crew run government, or others of like mind succeed him, there will be fresh lies to expose, new crimes to investigate. In fact, I’m working on a backlog, because that man and his cronies, like all Globalist Presidents, has more dark plots and evil deeds to dare than one conspiracy theorist, alone, can keep up with. Pray for me!
Care to help me out in other ways? All it takes is to pay attention, ask questions when facts conflict, and challenge government and media when they don’t get it right. And challenge the guy standing next to you when they don’t get it, because Sheeple are a terrible thing to leave running around loose in a Wolve’s playpen. If you ask me, that’s just plain good citizenship.
Or is that yet simply one more way of saying ‘terrorist’ in D.C.? Move along, Citizen, nothing to see here. Move along.
Related articles
- Former investigators ‘break silence’ about NTSB cover-up of TWA Flight 800 crash (nydailynews.com)
- TWA Flight 800 Crash Not as Reported: Documentary (newser.com)
- Conspiracy Confirmed! TWA Flight 800 Whistleblowers Speak Out – NTSB Told Them To Lie (fromthetrenchesworldreport.com)
- Six NTSB Investigators Claim the Official TWA Flight 800 Crash Story Is a Lie (ajmacdonaldjr.wordpress.com)
FREE WILL: A TIs Greatest Asset, Oft Hardest to Employ
What you believe determines how you react under and are able to defend against targeting. That’s a key reason that targets are psychologically profiled before targeting even begins; the enemy needs to know what chains best to jerk. Turns out, there’s a simple way to jerk back.
Free will: a Tis greatest asset, oft hardest to employ
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.What can you do if you are a targeted individual?
What you will learn reading this in-depth post…
- That belief structures define us, establish our psychology, and our responses to stimuli;
- There are many ways targeting both takes advantage of and yet alters beliefs to weaken the will to resist;
- Will power equates to Free Will, the greatest gift of God to Man short of salvation through Christ and life, itself;
- The pitfalls of targeting psychology as it relates to Free Will, and;
- How to use Free Will to thwart targeting and run psyops on the perps.
Where do you get help if you are a targeted individual?
Challenge][ As author, lecturer, and consultant on personal privacy and security, and abuse of power, I invite the reader, especially if a Targeted Individual (TI), to make a comparison. Compare the nature and content of this post with the typical posts or emailed materials by other persons offering insight into targeting methods or technology, and/or defensive tactics. Then decide which closer resembles the reality of your experience, and which plays instead to the very fears and results ascribed herein to be unexpected weapons. You become what you believe: let’s take an in-depth and lengthy examination, and see…
Is the information offered insightful and helpful, or more likely to lead the victim deeper into the proverbial Rabbit Hole of dread. There is a difference between education and helpful advice through understanding (what a consultant or educator tries to provide), and the rhetoric and trivial dialogs of technospeak or psychobabble offered with questionable veracity, something closer to beliefs and opinions, or even mis- or disintormation than well-sourced facts — regardless of if offered with good intent, or ill.
Topic][ We are talking about TI’s, Targeted Individuals, of course; persons harassed endlessly by organized groups using Political Control Technology (PCT), which can mean any number of things from gang stalking to electronic weapons, and much, much more. PCT is military and intelligence community developed technology, so if one is targeted, the perpetrators (‘Perps’) are almost always from those quarters, or from parties with whom they interact, undertaken for political or criminal purposes.
We should be grateful, in a way, for PCT. Prior to advances in PCT made since WW II, when a person became a roadblock or threat to a political agenda or criminal plot, they were simply done away with; murdered, typically a ‘wet job’ assassination or, if time allowed, dealt ‘an accident,’ or what we call ‘heart attacked.’ PCT, however, allows a whole new way of dealing with ‘inconvenient’ person who are not quite an immediate threat, thus avoiding the pitfalls of murder investigations and unwanted publicity they entail, and dangerous questions they raise.
When the target is a person of wealth and power, or public influence, it is less likely to be used. PCT works best on those unable to afford exotic defenses which would render it near useless, if not completely pointless. Those in the public eye may be too well observed already to risk deployment of useful PCT methods without risking detection by third parties. PCT only works when no one believes it is being used except the target. So unless they can first financially destroy or socially discredit such persons, they may elect instead a good old fashioned murder. Ask Vince Foster, Ron Brown, or even Marilyn Monroe or Princess Di. People with high credulity working for them can’t answer hurtful questions once they are dead.
Perps often fear victims][ It is fear that such questions might be answered by the target which drives any consideration for either assassination or PCT. When someone is thus targeted, it can be said they actually fear the target, fear them enough to justify ‘self defense’ and pre-emptive action. Thus the TI may actually hold an ace up their sleeve and simply not know it.
Part of my job as consultant is to seek to see if that is the case, identify it, and wield it as offensive weapon. For such victims, PCT was elected as a preferred method not just because it seems safer, but because of the way it works; the goal of PCT is to render the target into a social, financial, and political zero. No one pays attention to a zero, it is nothing of value to them.
This targeting achieves by making the victim seem crazy; no one wants to believe in the Boogeyman, so when they start talking about being targeted, they are presumed paranoiac and/or schizophrenic, and discounted. Once they achieve this status, of course, neither will anyone believe any information they may offer which caused them to be feared in the first place, even if they have evidence which might otherwise raise eyebrows. But that does not mean the information has no power over perps, if realized and properly used.
Other reasons for targeting][ This is not the only reason for targeting, however. One cannot deploy technology without training users on the methods and devices involved, and that requires live, unwitting subjects. In like manner, one cannot develop devices and improve method without experimenting on human Guinea Pigs. This is all fact, and even found in the Congressional Record (Church and Rockefeller Commission Reports), but for some reason, we still can’t quite believe in the Boogeyman enough to consider the possibility that someone is telling the truth when they complain of targeting. Finally, one can also be targeted for joy riding (psychopathic pleasures) or vendetta — both forms essentially an abuse of power through access to the technology for personal reasons.
The reason one is targeted often defines the entire game, including best defense strategy. But that is beyond the scope of this post, and indeed, inappropriate — because every situation, though perhaps similar in generic description to another, will have sufficient variables in play such that strategies should be tailored to the individual circumstance. Environmental, social, and personal matters all come into play, and more.
Why won’t people believe it when someone says they are being targeted?
It gets tricky
Self as a weapon][ The first step in targeting is surveillance from afar and the development of a psychological profile, which is the definitive ‘self.’ The goal is to calculate the victim’s likelihood of being responsive to an array of attack options. It also seeks to uncover some key ‘theme’ for the attack psychology. For some it will be guilt, trying to make the person feel they are targeted because they are bad. Others might come to think the theme is to suicide, or to undertake a specific course of action. It can be almost anything, or it may be completely generic harassment without a theme, because we all different psychological makeups.
Now, while more than one assault method is available, only one will likely be brought to bear at a time, and fostered until it achieves a certain level of success. I call this a calibration phase. Additional targeting methods are brought on line in a sequence designed such that the success in the former better aids the progress of the next, which in turn ideally augments or reinforces the former. While that is not always the case, doing so is a high-value procedural goal; it is important to achieve as prompt a negative impact on the psyche and behavioral responses as possible, so that responses to attack will be seen as being due mental aberrations — rather than the actions of a Boogeyman.
Disbelief as a weapon][ Such disbelief as to true cause by onlookers is, thereby, almost guaranteed. Paranoiac responses (e.g., looking over one’s shoulder to see if being followed) are natural when one is targeted, but do not mean the target is actually paranoid. But they immediately seem paranoid to others, even as the process begins. Yet in time, they wax toward true paranoia, as fear and assault from general targeting starts them to questioning more and more events around them in fears they might be connected to targeting.
Soon enough, even innocent things are indeed so judged. It is this same mechanism which renders professional spies less than useful, in time, because they start to over react to their daily dread of discovery. Intelligence agents are, by retirement age, generally speaking, quite paranoid. But there is more such as this, to come. This is not mental illness as some count paranoia to be, but rote conditioning; paranoia by reflexive repetition.
Imagination as a weapon][ Part and parcel of MC is to make the victim believe in a false reality as to their circumstances. They seek to create a belief that the problems they face are beyond their ability to resist, and other than they really are. Clearly, any onset of paranoiac beliefs will play to this, and create opportunities to put the ploy into full play. Once achieved, when they fight back defensively, they fight the wrong problem with the wrong solution, further cementing the notion that resistance is futile when the effort fails.
This ploy is also used another way; to make them think the wrong people, or at least additional people, are involved, but who are not. Targets are goaded into lashing out, if not verbally, more dangerously, that they might get into trouble, and have key support relationships sabotaged, even face arrest or other legal entanglements — or ideally, be forced into mental evaluation and perhaps even institutionalized ‘for their own protection.’
Mistrust as a weapon][ On the flip side of this tactic, they often approach persons close to the victim and attempt to subvert them with lies hoping to induce actual participation. They may present credentials or badges of trust, and talk of child pornography or other criminal behaviors, even terrorism, and sow seeds of mistrust and ‘patriotism.’ Once a victim begins to experience such mistrust, they in turn, feeling betrayed, begin to mistrust others close to them. The net result is that they can never be sure who the players and helpers really are, again fostering whole new paranoiac fears.
Fear as a weapon][ The above fears are very effective. Yet some PCT is so fearsome, such as bioimplants, that even suspecting it is in use, heightens paranoia. There are many tricks which can cause victims to assume implants in place, or some other dread, when not true. However, this is more commonly the case with long-term victims who have already been well along the paranoiac response path, and have had their beliefs altered well away from the true nature of their enemy. The longer one is targeted, the closer to this state they tend to become.
At such a point, paranoia can naturally grow to the edge of schizophrenia in appearance, perhaps better described as the form of hypochondria in terms of ‘sensing’ symptoms (such as where the implants are thought to be placed, or whatever the dread may be). Fear and imagination, when combined in an unending onslaught, can manufacture new false realities of any construct.
Once that transpires, or where implants really are in use, it is almost impossible to work one’s way out. Doctors will refuse to inspect for implants, and X-rays won’t reveal them because they are set for tissue examination, and not dense matter. The latest generation of low-cost implants are indeed fearsome: they are far too easy to place without the user’s knowledge (thought to be an insect bite) while they sleep, are extremely small in many cases, and are designed to bond with and look like bits of flesh if uncovered with scalpal. It takes a good magnifier to see signs of man-made tech.
Who is responsible for political control technology?
Consequences of false beliefs:
To be a helper first of all and foremost requires no preconceptions of what is true or imagined by the target. For the very reasons described herein (false beliefs), alone. But also because even if truly schizophrenic, that does not mean the person is not ALSO targeted. In point of fact, the class of victim who is a test or training subject is often chosen exactly because they are already schizophrenic; there is no possible way for anyone to believe that they are targeted no matter how badly a trainee or test goes haywire. And paranoia, being natural, is actually closer to a proof of targeting than a reason for disbelief.
This is exactly why it is so hard to get good helps from the very people who should help (e.g., Cops, Lawyers, Doctors, Politicians), and why I do not prejudge based on ‘wild’ or implausible claims or implied clues that something is wrong with their facts. If, in the end, if the person is schizophrenic, I’ll eventually come to understand that, and deal with it. If they are ONLY schizophrenic, I’ll by then be in a better position to guide them to the proper psychiatric helps.
But also, if schizophrenic and actually targeted, the illness will not deter detection of that truth, nor prevent me from addressing it — though it makes it more difficult. And I will still try to help the victim obtain the helps for the chemical imbalance causing their aberration, as well. And that is all it is. It is not being crazy, and if it did not have such a scary sounding name, people would realize it is not that big of a deal to so suffer.
This approach is also critical because it means I can ignore (mostly) any obvious or even inobvious false beliefs held by the victim. They are inconsequential to the true nature of targeting unless I myself also rely on the false facts, but I do not, or at least try not to so rely. Ignorance in this case is bliss. However, at some point, any errors in belief structures must be repaired or, perhaps, tested. It may, for instance, be me who has false perception. A good test can teach whomever is wrong the true nature of things, provided their minds are not sealed to logic (that can be the case).
The logical path][ Were I able to go into a TI’s home and install pickproof locks and facilitate true site security, render their computer and phones secure and defeat surveillance devices, make various targeting method tests, set up defenses in response, and do the appropriate investigations and analyze victim history — I can make ALWAYS make progress. It may not be total victory, but if not, the resulting shift will see the targeting closer to an annoyance than a trauma.
I’m talking about all the things I advise my client Tis to do, of course, since I cannot do it for them at distance (while I do offer direct intervention, it is generally too costly for a TI to afford, as it usually involves securing other professional specialists or services, as well). This is what I do: play 20 questions, give assignments, some of which are tests to undertake, and figure it out as we go. Repeat as needed.
Rationalization as weapon][ But victims tend not to follow my advice even after agreeing, or fail to undertake steps correctly, or misconstrue the results, or even reject the advice or conclusions out of hand — all generally because their current belief structures (as to the nature of the beast) will not allow them to yield fully to my advice or to the possibility of another reality. Their minds are closed to logic, and they rationalize an excuse for the subconscious decision.
Strangely, this is often even true when the instruction is a test which would make that very determination. My best successes have only been possible when the victim was relatively new and had as of yet had no such strong false belief structures to struggle with. Long term victims tend to have a ‘been there, done that’ not-going-there again approach even though they haven’t, yet, really (at least not in the manner as prescribed).
And understand, I’m not saying I’m always right, by any means. I’m frequently wrong; since I am not there, I must rely on the information I’m given, but it comes from people who are not consistently capable of giving me the correct information— because it is all filtered through their belief structure born of targeting falsehoods. Even if I were on site, I myself might be misled by clues or symptoms, or miss something key, or simply make wrong conclusions. So imagine how much harder it is for the Victim, alone in a stressful environment.
Desperation as weapon][ It leads to desperation, and in that state, victims do things they ought not. They almost habitually (mix and match) ‘hook up’ with other Tis, seek sexual encounters with strangers; move into places indefensible, write to authorities in an inappropriate manner, spend serious money on foolish or fraudulent defenses, and more. They rationalize wrong choices via hope instead of choosing carefully with logic, and by that same rationalization, discount failures and thus end up repeating the same error, again.
Speaking to my introduction paragraph, they tend to believe at the drop of a hat most any technical or tactical explanation or offer for help (especially if a new or unusual method, and for too many, even if seeming nonsense) — especially if it in any way reinforces a false belief already held. And they tend to reveal too much information when in dialogs, further aiding perps in psychological profile and targeting fine tuning. These things they do in hopes it will somehow at last lead to something that does help.
The path unwanted][ All this further exaggerates their false beliefs, and then typically in the end they call those same people (with home they hooked up or from whom they obtained information or helps) Perps when things don’t work out as expected. Regardless, seldom will they toss out the newly acquired fears or beliefs about tech. There is such a desire to ‘understand’ the problem, that they consume and eagerly share information constantly, even if there are logical signposts that it is incorrect. Eyes are raised if anyone dares point out such flaws, and their honest appraisal becomes circumspect. Of course, sometimes, the objections are indeed false, perhaps from a perp.
Division as weapon][ Thus in the end, the victim community ends up bickering and fighting and being suspicious of one the other. Even though it is sometimes absolutely true one is a Perp (or just as bad in net result, a true schizophrenic believing themselves a victim), way too many thought to be, are not. For those wrongly accused, help is subsequently even harder to come by, as they tend to isolate themselves defensively. Victims end up torturing victims unwittingly in a mass self-reinforcement of victimization.
This is why I no longer participate in group dialogs, polls, petitions, etc.
And why was false advice given in the first place? When not because the giver was a perp, it is most likely a false belief structure which allowed the giver to sincerely think it would help, perhaps because they used it in their own targeting. But they failed to realize the perps took steps to make it seem like it helped. This takes us back to the opening statement: part and parcel of MC is to make the victim believe in a false reality as to their circumstances. They giveth and taketh away after it has led to more division in the TI community.
How sinister the weapons are][ But even when the advice or information is good, if filtered through false belief structures, it will not be useful to the victim as a rule, and for the reasons cited already. It matters not who is giving the advice; me or a TI, or some third party. False belief structures still get in the way, and perhaps, for some individuals, pride contributes; they do not wish to admit they’ve been wrong all along.
I can sometimes make decent progress with a long-term victim suffering false beliefs, but seldom as much progress as desired. Regardless, and this is almost always true for all clients, when even a small level of progress is made, the victim gains strength and the will to continue fighting. They become a Survivor, and are no long victim, and that alone is worthwhile. If I can get that far, there is hope that more progress can be made, and in time, it usually is, but every new gain tends to be hard earned… but with luck, at some point, there is an opportunity to suddenly break away altogether.
But you often dare not tell a victim they have false beliefs (as I attempt, here) or a key to truly understanding their problems, even once a survivor, because it will probably be rejected along with other advice. They have to somehow come to realize it on their own, and start from zero; that’s when good advice and helps can actually work. Even then, they must also have the will power remaining to force themselves to stop the bad practices which deter helps and neuter advice, as well as the bad habits born of desperation.
What is political control technology?
But then there is FREE WILL
Free Will, the Survivor’s weapon][ Exercise of Free Will, the gift of God which no other can take away unless freely given in submission, is the greatest weapon a TI has: only if they CHOOSE to allow an attack method to have emotional impact, will it be so. Street theater, V2S (voice to skull), and even pain generating tech becomes little more than a bad joke when one is able to simply decide it has NOTHING TO DO with their ATTITUDE and emotion, or their psychology and philosophical approach to daily life.
A Cancer victim in constant pain who CHOOSES to continue to live and enjoy life… such a person in such a state is a wondrous thing to behold, because we see they can be truly happy in life, accepting their fate and enjoying life even MORE than someone uninflected because of it. So why cannot a TI do the same? Only because they CHOOSE to suffer the very psychological effects the targeting pushes them reflexively into. But unlike cancer, there is a cure for that.
Never REACT][ Instead STOP, THINK, and consciously ACT; stop yourself from reacting, think what your reflexive instincts were telling you to do — and consider if that was not what was expected of you. With that in mind, then ACT contrary to it in some manner, doing so as if an actor in a play. In the beginning you will have to act like an actor, because it will not seem ‘normal,’ but in time, you will find that things get easier, and eventually, reflexive, such that targeting no longer has any control, not even to force you to stop, think and act. THAT will be true freedom; the day you no longer automatically respond as predicted by your profile — because you have created a whole new profile, one which is targeting resistant, and one they cannot understand or deal with.
To me, the real beauty of this method is that it is mind control in reverse; the perps become confused, and are rendered victims of your psychological warfare upon them. The accuracy of their psychological profile is diluted and eventually becomes useless and meaningless. The lack of progress and success causes underlings to get in trouble with superiors on up the line. People get ‘fired’ and replaced.
They even start replacing equipment, thinking it defective. And from that fact comes a warning: expect attacks to intensify, either as punative response, or in experimentation to see what’s wrong. But they will not want them to get so intense that they damage tissue or leave other physical evidence, so if you start getting microwave burns, for instance, go to a Doctor and get it documented, and photograph them for evidence, and as always, update your log of targeting events with great detail. They will back off if this starts to happen, almost always. If they do not, let me know. I have thoughts on that, too.
Related articles
- Gang Stalking – We targets are alone. (neverending1.wordpress.com)
Does God Ever Approve of Deposing Tyrannical Governments by Force?
When peaceful change does not correct a tyrannical government, what remains is armed revolution — or — docile subjugation. History shows revolutions are slow to come, but when they do, swift to take hold. Yet, there is an important difference between being able to say ‘this government is tyrannical…’ as opposed to ‘This government is Godless…’
Does God ever approve of deposing tyrannical governments?
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.Does God approve of revolution?
Reading this post you will learn:
- Citizens of any nation may believe there is reason for armed revolt
- That the Antichrist cannot come to power until there is a massive Global revolt
- That God commands we not revolt against authority
- But that there may be some forms of government where revolt is not revolt, but just punishment in the eyes of God
Who is really in charge? Who SHOULD be in charge?

Iranian Revolution: Governments fall when people unite.
In a prior post we sought by means of two polls, to determine who the real authority and source of power is in America, currently, compared to who is the RIGHTFUL source of authority. If you have not read that post, this post will likely be more valuable to you if you first at least review the Poll, and hopefully, employ it. Now, while the answers are specific to the United States, the question posed in THIS blog post, remain valid for any country under any form of government, even if Islamic.
The reason it applies globally, and as many of my posts point out, we are in a life and death battle with the New World Order, then we are up against powers and principalities who seek to seat the Antichrist. Even if not so, if we feel our government tyrannical and evil, we may be predisposed to considering armed revolt if we see no peaceful choices working.
But also as pointed out, if we resist properly, we can delay the unpleasant and totally fatal End Times that go along with that scenario. That means a Righteous (right-use-ness) fight to assert our right to God’s gift of free will as opposed to an evil (vile-use) motivation.
Scripture clearly tells us that we are to submit to authorities, even if they are oppressive, the example given being Caesar; the Roman Empire, eventually headed by an ungodly man who thought he was a God, and which literally enslaved most of the known World at the time. There are several verses which we should consider to see if there is perhaps any exception or justification for rebellion:
Hebrews 13:17 and Romans 13:1-7 are the primary establishing commands we seek to question, saying, “Obey them that have the rule over you, and submit yourselves: for they watch for your souls, as they that must give account, that they may do it with joy, and not with grief: for that [is] unprofitable for you.” “Let every soul be subject unto the higher powers. For there is no power but of God: the powers that be are ordained of God.”
1 Peter 2:13-14 echoes, “Submit yourselves to every ordinance of man for the Lord’s sake: whether it be to the king, as supreme; Or unto governors, as unto them that are sent by him for the punishment of evildoers, and for the praise of them that do well.”
Thus if we are faithful to God, it seems we must presume even tyrants were given authority over men with God’s blessing for some reason known only to him, and that their authority serves Him in such hidden cause. Yet it also sounds like it is based on the assumption that there is at least some degree of responsibility to protect and care for the nation, to specifically include spiritual care for their souls. And it is true, that even Caesar allowed the captive Jews to worship their own God. How odd was that, when such as he would soon claim to be a God?
So two questions come to mind which may alter the equation, and deserve further consideration.
One: What if the authorities actively seek to destroy God by advancing the Antichrist?
That is, after all, the primary premise which is in play up front and which drives the new World Order movement at its inner-most core. It is one thing to revolt because of tyranny and loss of freedoms, which is certainly a motivation in any revolt. But it is another to do so because the authorities seek to destroy men, destroy their spirituality and lead them to sin, and destroy God. What does scripture say about that?
An answer may exist in the complex story of Nabal and Abigail. Overly simplified, perhaps, for the sake of focus to topic and the limited space of a blog, Nabal was a powerful man of self-assumed authority at a local level who, when some of David’s people came under his power, was harsh with them, and took actions which were a threat to even David’s life by denial of food, offering instead great insult. Nabal worshiped Belial, a name for Satan.
David responds by gathering 400 men in arms to confront and deal with Nabal in reprisal. But one of David’s men warned Abigail, Nabal’s wife, explaining the problem. 1 Samual 25:17 is his conclusion and of interest to answering our question. “Now therefore know and consider what thou wilt do; for evil is determined against our master, and against all his household: for he [is such] a son of Belial, that [a man] cannot speak to him.”
Is that not how powerless we feel in the face of the NWO and their ceaseless crimes against us, plots all against God? Do they listen to our reasonable pleas?
But rather than justifying David’s intended battle, which we might deem rebellion, Abigail intercedes with great wisdom on behalf of and in acting authority of Nabal’s houshold. She brought food to David, and pleaded that there be no battle. David agreed, and Abigail returned to Nabal saying nothing. In the days that followed, Nabal died, God’s judgement upon him.
The story would seem to have no true relevance if that were the end of examination, for there is no Abigail likely to intercede on our behalf within the construct of the NWO (if one exists, please email me, and let’s fix this!). But there is one more passage which does apply. David, as God’s servant in the passage, thanks Abigail for stopping him from attacking Nabal, an act he himself describes as, in afterthought, evil (unrighteous). In part…
1 Samual 25:39 “And when David heard that Nabal was dead, he said, Blessed be the Lord, that hath pleaded the cause of my reproach from the hand of Nabal, and hath kept his servant from evil: for the Lord hath returned the wickedness of Nabal upon his own head.” In other words, had David attacked, it would have been wrong. He indeed should have left the matter to God, who in the end did take care of it.
On this, then, we see the Bible remains adamant that we not ‘fall away,’ the term for rebellion, even when authority is clearly Satanic and seeks to harm us. And yet, I still wonder… there is the one other question…
Two: What if WE are the authority, and it is our servants that we need take to task by force of arms?
 This is one reason why the poll was offered in the prior post. One may find there is a distinct difference between a government based on divine right as addressed by the above Bible admonishments to submission, and government based on a social contract; the Constitution and Bill of Rights. If, in the polls, We the People or the Constitution/Bill of Rights were seen as the ultimate authority, and especially if the poll also showed that the darkness of the New World Order was the true current power, then divine right would no longer seem a valid component.We would not be rebelling against authority, for we are that authority.
This is one reason why the poll was offered in the prior post. One may find there is a distinct difference between a government based on divine right as addressed by the above Bible admonishments to submission, and government based on a social contract; the Constitution and Bill of Rights. If, in the polls, We the People or the Constitution/Bill of Rights were seen as the ultimate authority, and especially if the poll also showed that the darkness of the New World Order was the true current power, then divine right would no longer seem a valid component.We would not be rebelling against authority, for we are that authority.
We would instead be rebuking those assigned the task of executing authority on our behalf, our public servants. Restated, if We the People deemed to grant the power of governmental authority to those in Congress, the White House, the military, and so forth… by means of a document we (our Forefathers, anyway) penned and signed as their charter of such powers, then they serve us at our pleasure, and should they err and refuse correction, we ought be justified in using force to end the matter, per Thomas Jefferson’s beliefs and intent; the whole reason for the 2nd Amendment right to bear arms of like capability as the military.
Biblically, that would be a Master-servant relationship, and we would still be in compliance with God’s Word to punish our errant servants. A master does not fall away from a servant in rebuking, punishing, or even killing him for just cause, nor does he do an evil thing in the eyes of God. Indeed, it is the servant that falls away in violating the will of the master, and punishment of any kind may be in order according to circumstance.
Luke 12:47 “And that servant, which knew his lord’s will, and prepared not himself, neither did according to his will, shall be beaten with many stripes.”
And one more thing…
If the poll would seem to insufficiently justify the above reasoning, or you otherwise find it unacceptable, the Bible does specify one, and only one other just reason to fall away and not obey authority. That singular reason is when authority commands something which is contrary to God’s commands. You are to obey God, and not man, in such a case.
Acts 5:27-29 (and similar in Acts 4:19) makes clear: “And when they had brought them, they set them before the council: and the high priest asked them, Saying, Did not we straitly command you that ye should not teach in this name? and, behold, ye have filled Jerusalem with your doctrine, and intend to bring this man’s blood upon us. Then Peter and the other apostles answered and said, We ought to obey God rather than men.”
Therefore, we must seek and define just cause for rebellion; such deeds or laws or deciets which prevent or thwart obedience to God. How can we judge if this be the case, or no? Start with what God has commanded, and compare. Look to the Ten Commandments, and we only find two which may qualify.
One: Thou shalt have no other Gods before me. Unless and until we are commanded to worship some other God, this is no justification. If the one-World religion is forced upon us, we might justly revolt, but that is something not expected until after the falling away and the one-World government is established. It is yet for a future time.
Six: Thou shalt not kill. Now we start to wonder if this is not a basis. Wars fostered by deceit to steal resources and confound the God of Abraham by putting Satanic sects in power (Hashemites – see prior post) would seem to be commanding our soldiers to kill for unjust cause. Depopulation efforts such as Chemtrails, Agenda 21 and Codex Alimentarius, and GMO crops is asking us to submit to being killed, and if we do not submit, to aid in the killing of our own children.
Indeed, the laws have already been written to enable and essentially require that we unknowingly allow the State to guide our unwed teens to kill their children by abortion. The 1.4 billion rounds of munitions ordered by DHS likewise seems destined to be used against us. Must we submit ourselves and our families unto death?
Suppose they do at last come for the guns? To do so is the final step in their revolt against our authority. Once they have the guns, they become the Master, and we become the servents; slaves, really. From that moment forward we are forced to serve Satan’s desires of any and all manner without recourse, and no longer have any means to resist. The Antichrist can come to power, and it is End Game.
Does God intend we should serve Satan without a fight, or is that a sin. There are more than a dozen verses on this but the one with the strongest and simplest clarity perhaps is Matthew 4:10 “Then saith Jesus unto him, Get thee hence, Satan: for it is written, thou shalt worship the Lord thy God, and him only shalt thou serve.”
Only Him shalt thou serve.
Him only.
HIM!
And how do we do that? Do we grab our guns and start shooting? It is, after all, relatively easy to start a revolution. I hope not, unless perhaps it is in defense of the guns, that final signpost, that final straw… or perhaps if some cold, hard proof of genocide or like atrocity toward depopulation. But then, we each draw our own lines in the sand, and choose how to resist. I’m thinking there needs to be a way to fight back which does not require violence, one which can be applied more safely, and immediately… by anyone… today. This moment.
There is.
It’s available to us all, and has been all along.
It’s called the 1st Amendment; free speech, and when combined with an even more powerful tool, God’s gift of Free Will, it is all powerful. Become activist and use these weapons, or the entire Constitution and Bill of Right have no meaning for you, and perhaps the Word of God as well, for you may end up being doomed and unable to obey it when it is found to be, for you, too late. You can always just opt out of the system… and drop off their control Matrix (take the Red Pill).
The Mark of the Beast, or death may be your only choice, then — or armed revolt. But if you ever end up deciding the time is ripe for such revolt, I pray you do so in agreement with God’s view of your actions as being righteous (right-use-ness). That is one reason for having two polls to compare one to the other: if we be the rightful authority, than it is not revolt, at all, but due punishment, and not just our right, but our obligation in the eyes of the God.
Related articles
- Devotions: I Samuel 25 (spiritualgym.wordpress.com)
A Poll: Who Is the Real Authority and Power in America?
I really don’t think we can answer that so easily. Is it Mr. Sorento and his Executive Orders? Congress and their unconstitutional laws they don’t even read? Bankers and the FED? The Military and Arms Industry? The Individual States? The United Nations and their Treaties? The Council on Foreign Relations? The Illuminati, the New World Order? Or… is it We, the People and the Constitution?
Update: May 14, 2013 Preliminary results indicate 75% of us think the rightful power in America should be We the People and the Constitution/BIll of Rights — but only 6% of us think that we actually achieve that ideal. More than 70% think the real power currently in force have nothing to do with government, at all. IS THAT RIGHT? I hope not, and thankfully, the sampling is fairly small (only 21 votes). WE NEED MORE VOTES to truly get a handle. TELL YOUR FRIENDS TO TAKE THE POLL! by H.Michael Sweeney Copyright © 2013, all right reserved. Because this involves a Poll, it makes sense not to allow normal reblog. Permission hereby granted to reproduce this blog in full with respect to commentary, including this paragraph, but WITHOUT the pole, itself, using instead links to this blog at the appropriate point. All other links and text must remain in tact. A Poll: Who Is the Real Authority and Power in America?What you will learn reading this post and answering a Poll…
- That there are many possible answers to the question;
- That each is supported by useful argument;
- That each is arguably false by countering logic;
- That God has given us signposts that we might choose wisely;
Who is our true Master in America?
I’ll start by saying I’ve been the fool, as I think have we all. Nothing anymore is black and white, it seems, though most of us operate as if it were. That’s how we make mistakes. The visible things on the surface of matters which guide our opinions and actions are more and more subverted with falsehoods and concealments, and manipulation, and yet like the Ostrich, we prefer to believe what is apparent without question. Look where it has led us:
Never before in history has there been so much talk about the end of the World… about global revolution, wars, and rumors of wars… about religious beliefs and disbeliefs, and bitter differences between them. Or about the New World Order, which can only serve to seat the Antichrist and lead to Armageddon… about powers and principalities, plots and conspiracies.
Count me guilty of all such talk. It’s on my mind almost every day, if not the forefront, then nagging at me in the background. There are simply too many news events where things simply do not add up to equal the facts offered in the telling. Things are rapidly becoming Biblic in scope, things forecast in that very book. The signs are everywhere, even as also forecast. I cannot help but consider, and write. I think we all need to consider, lest we blunder into oblivion. Of course, that may just be me being paranoid, again.
Is it mere paranoia as some say, even hope? Or is it a growing shared consciousness coming to the surface? Or is it simply proper attention to signposts and the very Word of God?
When have we had so many signs in the heavens? So many serious earthquakes and mega disasters? Dieoffs of large numbers of people and animals? So many people in unrest simultaneously? So many wars and rumors of wars? So many sightings of strange creatures, UFOs, odd visions and even noises of no tangeble explanations? So many rare events in and from the stars? When has the Earth been so polluted and ecologically threatened? NEVER. All these things have been forecast.
Ought we not heed them? Moreover, when has there been such a fascination in our entertainment with the occult, witchcraft and satanic things, zombies, monsters, and other dark things including end-of-the World scenarios? Are we being conditioned to accept the Antichrist’s rise to power, that we may yield to the Mark of the Beast more easily?
When in history have there been such vast schemes forced on the masses by a handful of powerful people with questionable agenda? I speak of Agenda 21, the sustainability movement which would deny you the right to own property, have a car, choose where you live, and work, and if you can have children. I speak of Codex Alimentarius which makes natural herbals and vitamins illegal, and forces you to rely on big pharma drugs, and to be subject to inoculations. I speak of the plan to establish a one-world religion which melds everything from Shamen to Buda to Christ and Mohamed and even Satan. I speak of HARRP and mapping the brain so that mind control weapons can regulate thought and mood on demand, and of chemtrails, GMO, and Seed Vaults and race specific pathogens (gene-guided bioweapons) which enable depopulation. There is more such as this which could be added.
The answer as to who is the true authority in charge is a serious question not easily answered, but one which is critical to trying to answer and deal with the rest. In the end, there is probably no useful concensus given multiple ways it can be thought of, born of differing perspectives, and that is why a Poll is being offered. But it is critical that we know, because we are at a crossroads in history which will determine the fate of the World, though most of us are asleep to the matter.
If we are truly at such crossroads, the Bible warns that before the Antichrist can come to power, there must be a ‘falling away,’ a revolt. 2 Thessalonians 2:3 “Let no man deceive you by any means: for that day shall not come, except there come a falling away first, and that man of sin be revealed, the son of perdition;” In the text of King James, ‘falling away’ means ‘rebellion,’ and the day spoken of is the End Days, the ‘son of perdition’ the Antichrist; the rise to power of Satan.
It does not say who wins, and indeed, it may not matter, because the Antichrist could rise from either side of such a battle. But as I’ve said in my prior posts, I believe that if sufficient numbers of people are found to be righteous (right-use-ness) as opposed to evil (vile-use) in application of Free Will, God will let the World continue. I believe Armageddon comes by the dictates of our own actions, that there is no set time for it as Men consider time. And if that is the case, I’d rather have more time than less.
How about you?
Who is the real authority and power in America?
Who truly rules us, right here in America?
Is it Mr. Sorento? The presidency, regardless of who sits. But I refuse to use the other name this man claims, for he is indeed a man of questionable legal authority to hold the Office of the President. If he is legal ruler, why did the military allow troops to decline assignment to combat if stating they did not believe him their lawful Commander in Chief? There is a significant chance he will be proven a fraud in court by some accounts. If a fraud, his Executive Orders and Bills signed into law are null and void. But the real question is, is any President the true power?
Is it Congress? All they do is propose and submit laws to the President. They don’t actually tell us what to do in any direct way. Worse, they don’t even read the laws they vote upon, and never seem to question that massive bills thousands of pages long are ready for their consideration within days of most ‘needs,’ things otherwise unexpected. The Patriot Act was written well before 9-11, for instance. The body is widely viewed as corrupt and acting against the best interests of the country and those who elected them.
Is it the Military? They are supposed to answer to the President, and civilian authority. Yet they have threatened Martial Law, suspension of the Constitution, and a military form of government. They now presume the right under NDAA to murder, vanish, and torture any American without due process. They raid our cities in mock drills. Their documents indicate they intend to shoot Americans demonstrators who protest (they already did so at Kent State), if confronted. Others define a new form of warfare most likely to be faced in the future as ‘Peoples War,’ where the enemy is a group of ‘Ex military, Constitutionalists, patriots, religious extremists, the poor and disenfranchised.’
They have approved a plan (the blueprint of terrorism we now face) called Operation Northwoods, which we find duplicated almost to the letter in terrorism: it was to blow up American ships in harbor (the USS Cole), blow up American buildings (US Embassy Bombings, WTC Bombing), assassinate Americans on our streets (DC Sniper), shoot down remote-control airliners thought full of Americans (9-11 attack), and blame it on (in the plot, Cuba, but it can be used as a tool against any group or nation with the right operatives) in order to justify a war. All of this is detailed in Fatal Rebirth, right down to the circuit boards employed. Want a free ebook copy of Volume One?
Is it the Supreme Court and Court System? They are only called into play as a kind of last resort, and only indirectly tell us what to do on select things which come before them. And yet, they are supposed to be the final, ultimate authority in the scheme of checks and balances which define the construct of our government.
Is it the States, and States’ Rights? The Federal Government is limited in what it can do to force compliance at State level. International treaties cannot be signed and entered into without ratification by the States. It is by agreed upon Union of the States which formed and empowered what we call the Federal Government, for the purpose of doing their bidding for the collective good.
Only by coercing State compliance voluntarily with Federal funding programs are most Federal mandates found sufficiently ‘convenient’ at the State level. But if it is the State, then the question of the Military comes back to haunt us, because there is hardly a standing Army as such; the bulk of the Military outside of the DOD is in the form of National Guards (Army and Air Force units), which are State militia. The Navy, Marines, and Coastguard are the exceptions.
Is it the County Sheriffs and local law enforcement? If there were large-scale civil unrest, and/or a move by the Federal government to enforce gun controls deemed unconstitutional, who is the true local authority over you, when so many Sheriffs have unified themselves to tell Sorento they would not enforce such laws and would even arrest Federal agents if they attempted to do so. So important is this issue, that we now learn that in response, Sorento is asking to form a whole new Federal law enforcement agency (itself thought unconstitutional – a National Police) to arrest Sheriffs who take such a stance. Who will side with whom, against whom, when push comes to shove?
Deputize me, and Barry will find out. And know this: it will take only One Governor to order his National Guard into D.C., and one Constitutionally loyal General to arrest and detain anyone guilty of treason as result of such forced confrontations.
Is it FEMA and/or DHS? A state of Emergency was declared because of Sept. 11 attacks. It has not been lifted. The FEMA Charter under law gives them absolute authority over almost everything in such declared emergencies, including the Military. If you read the list of what they control and can do, you would say Hitler would have envied their absolute power. Yet we see no visible signs this is being exercised… unless you are observant. Their vehicles can be seen driving our streets, and Police-like uniforms are being worn here, and there, with FEMA patches. They are too quiet, methinks…
Much the same can be said of DHS, which was created by the Anser Institute, a shadowy military-intelligence think tank. It was formed exactly two years prior to Sept. 11 attacks, almost simultaneous to the Project for a New Amrican Century’s war plans for a series of domino wars in the Middle East to gain control of natural resources, and give power to puppet governments run by what they called in their PowerPoints, Hashemites. The Hashemites are an ancient Satanic sect predating Allah that involved opiates in their religious ceremonies, and are brethren to the Assassins, of like construct. Their historical trails will lead you to the Knights Templars, to Rosecrucians, witches and warlocks, to Masons/Freemaonry, and to the Illuminati. DHS has ordered 1.4 billion rounds of ammunition and is doing all manner of things dark and sinister which cause many people to think them planning a war with American citizens.
Is it a Secret Shadow Government? Unseen string pullers. I call it Shadow in my book set Fatal Rebirth. Some call it Illuminati, perhaps in the form of the so-called Round Table Groups (evolved from Knights Templar meetings), like the Bilderbergers, Council on Foreign Relations, and even Rhodes Scholars. Some say it is the high Freemasons, Skull and Bones, and the like. Others think it the Jewish Cabal (bankers, mostly, primarily due the Rothschildes influence, but I maintain they were Knight Templars who assumed Jewish identities to avoid persecution by the Pope). Such forces do exist and make themselves felt, and all those elements cited can be seen as a collective. But do they actually rule, or are we grasping at paranoiac straws? Do they really control all power in order to seek the New World Order, and to seat the Antichrist, as first suggested?
Is it the FED and Banksters? Wallstreet & Culprits, Inc. This rightly belongs in the Shadow category, but it is such a singular force in American life that it deserves to be listed separately. What one giveth, the other oft takes away, resulting in yo-yo financial forces which define our economy in ways which in turn define our politics and national policies. Attempts at to police them tend to be negated with ease by these institutions, who repeatedly bring us to the brink of fiscal doom and then propel themselves forward with profits galore, often out of thin air. But seldom do we gain or recover our losses from wealth redistribution to their favor.
Is it the Corporations? Big Pharma? The Oil Companies? Military contractors? The Board Rooms of legally defined living entities seem to hold sway over Congress and even the President. Monsanto writes laws which give it a blank check, submitted to Congress by their pocket Congressman, and Monsanto backed PACS contribute to other Congressmen to insure passage. Then the President not only signs the Bill into law (deliberate lower case, I refuse to believe his signature lawful), and appoints Monsanto kingpins to guide the FDA to ‘oversee’ Monsanto. We see the same thing in Big Pharma, in the Oil Industry, and in the Defense Sector. The fix is in. The public trough is for sale to the highest bidder; it should be renamed corporate trough, because the Public cannot access it — we just pay for it.
The Constitution and Bill of Rights? This is the very charter which defines the organization, operation, limits and authority of all branches of our government. Without it, there is no authority of the President, Congress, or the Supreme Court. And yet, it does not actually rule us, as such. And most certainly, it seems to be loosing its power as both Congress and the President continually issue laws and executive orders deemed to violate and negate it. This is why so many people deem our leaders to be outlaws, and why Sheriffs are starting to say ‘NO!’ It’s why many people are buying guns, and talking about Revolution being a real possibility.
It’s the primary reason I write, in fact.
We the People? We are, after all, the ones who authored and empowered the Charter. It has no power except that which we gave it by our signature (Founding Fathers), which means neither does the President, Congress, etc. have power but that which the charter affords. We are supposed to be the ones who control government, giving it limited powers to manage our nation for us. Government is supposed to be a tool which works for us, not the reverse. They are supposed to fear our anger should they err, we are not supposed to fear our government, which is more and more our sad state.
Who really rules, as opposed to who is the rightful ruler?
The Poll, in two parts
So please use the Poll so we can see if there is consensus as to who is the RIGHTFUL ruler, vs. who truly rules at the moment. There are, therefore, two parts: who is the PROPER final authority in the power structure; and who do you think really controls us, currently? These two answers will define much of what follows; our fates, and as I fear most likely so, our judgment by God, and, more to the point, how soon it comes to pass. Will that be two o’s or three (SOOON!)?
Please use both polls; you may vote for any THREE choices in each (e.g., the three branches of the Federal government, the three most conspiratorial choice, etc.). The closing comments show why it is important to answer both polls, and will lead to the first of two analysis posts which logically result.
And here’s why it’s critical we know the answer to BOTH polls, as we will explore further in parts II, and III… if there is a dichotomy in the two Polls’ results… where the current power resides not in the hands of the rightful authority, then should not that be rectified? If, for example, the rightful authority is We, the People or even the Constitution, and we find any other in power instead… then ought we not be seeking in earnest to change that?
And more to the point, if we see there is no peaceful way to effect such change, there is a more key question we must ask (part II):
Does God EVER approve of deposing tyrannical governments by force?”
Part III will be a specific analysis of Poll results once sufficient votes are cast.
Related articles
- One in four Americans fear Barack Obama is antichrist (metro.co.uk)
- Poll: 1 of 5 Republicans Believe Obama is the Antichrist (atlantablackstar.com)
How to War With the New World Order (Checklist)
No matter how simple the weapons and tactics of war, you need a checklist; an action plan which is your method to the madness which is war.
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
How to drop out of society
Continuation of prior post: a checklist on how to drop out

Exit the system, stage left
In the prior segment we introduced the notion of going to War with the New World Order by defining the problem, the underlying mechanics and principles involved, and getting a good look at our enemy. If you have not read that, and especially if you are skeptical that such a War MUST be waged, please read it now. We closed with Step Two of how to take the War to our Globalist enemy: Drop out of the System. That, in turn, opens up a series of possible tactics from which one might choose to employ, offered here as if a checklist for customizing your battle plan.
To repeat an important consideration, don’t expect to jump in with both feet, but rather, ease into those things which seem easiest to accomplish, and then expand upon them as opportunity and ability allows, and in like manner, move into other areas. Unless one simply happens to have the needed resources and capabilities in place, it is not likely even possible to undertake all of the ideas simultaneously: Some of them you simply might not care for, or accept as viable or workable with respect to their goals or your personal circumstances. Don’t feel you need to follow these suggestions any more than you need to ‘play their game.’ After all, it is about free will choice; God’s greatest gift to Man short of life itself.
And that’s exactly what we are trying to stop the New World Order from ending. Free Will.
What do I do to drop out of the system?
The Checklist
❑ Don’t buy into the system: Don’t rely upon credit of any form. Debt is control, a thing admitted through history by bankers themselves. They sell credit to you with the promise of instant gratification and convenience, and even ‘perks,’ but the price is not mere interest, but firm control which locks you into their system. Once there, they own you and are assured you will not easily revolt. The banks and lending institutions, and the retail creditors, oil companies all… all rely upon credit to trap you into a Debtor Control System some call the Matrix, or the Grid.
Then there is the endless electronic transaction trail it generates which is of great interest to TIAO (Total Information Awareness Office — since renamed Terrorist IAO to make us think we are not the true targets of interest) to track your every movement. TIA is designed to eventually detect and record any and all forms of social transactions where information, money, or property changes hands, and even to calculate psychological profiles and future actions based on that information.
If enough people stopped using credit religiously, the banks would falter and interest rates would be less artificial and manipulative. The shockwaves would have a negative, inflationary impact on the economy, especially for MIIM corporations, because the dollar would falter against foreign competitors, seeking its true value (0).
Since the bulk of the National Debt is held in the form of Bonds owned almost entirely by the wealthy elite who make up the NWO, their financial power base is eaten away from within by the very stuff they covet most, which dwindles in value and usefulness. While a bad economy also has a negative impact on personal situations, it also hastens the general public’s realization that MIIM’s system serves them more than us, and will lead to more converts over time, and lead to victory and the chance to rebuild anew. That is the long term effect.
In the short term, forgoing credit and relying instead on alternatives herein not only saves you interest (money), but allows you the freedom to choose what you will pay with. In essence, it makes it easier for you to survive a bad economy by relying instead on an underground economy, ignoring fake Federal IOUs in favor of the truest currency of all; value given for value received, in a transaction where each transactional party dictates what is of value, and its worth.
For instance, there are barter institutions which allow you to trade goods and services for other goods and services — no money or little money needs be involved at all. They act as a kind of ‘bank’ trading ‘credits’ used in such barters for a small percentage of the transaction — much less than would be the interest in a credit-purchase situation. But of course, you can also effect barter with individuals directly, often providing increased flexibility in coming to an agreement.
Be careful, however, when using services, because there are tax issues which generally force such services to report at least select transactions, and that may be undesirable. The System is trying to make barter unworkable, even illegal. But in an underground economy, such concerns are no different than highway speed limit signs when hurry, you must. You can simply offer to trade directly with those you personally do commerce with most often. Offer to trade excess items or items you make, or services, for whatever you want. There are people who live completely by this method, not even paying rent with cash or credit, though such is rare. I could tell of wonderful outcomes with barter, personally.
Somewhere, if you ask around with persistence, you will find someone who is willing to trade, and in such a case, you mutually agree upon values and no one, not even Uncle Sam, gets a cut in the ideal circumstances. Enter Craigslist, and the like. Of course, there will be things you cannot easily barter for, many of them essential, such as certain foods, rent, and utilities. We will address such needs elsewhere.
❑ Don’t fund the NWO brand names: Determine what companies belong to MIIM, and boycott their goods and services, and do not buy their stocks. That means some hard decisions. If the company is a military contractor, or a multinational, or owned or controlled by one (a subsidiary), it is a company you should avoid doing business with and one worthy of constant public condemnation in activist style. Also, avoid purchases of any precious gems or metals, since the great bulk of the mines are owned by the NWO — else why to think they push these commodities so hard by selling fear and uncertainty?
Unfortunately, this means doing without certain goods altogether, such as new cars and appliances as technology advances. It IS OK to buy used, if it is not going to be financed. I drive a six year-old car and use a six-year old computer — and they work great. I am not so far behind the technology curve as to ‘hurt.’ I might spend more on repairs but have no monthly payments and the original cost was well below new — so it costs considerably less to give up a little prestige or performance, or whiz-bang feature. Doing so means the system is not profiting by my presence — I am not participating. You can amplify upon this by growing your own food (to be illegal under Agenda 21 and Codex Alimentarius), making your own clothes, and similar self reliance.
❑ Don’t buy the advertising: Boycott the newspapers, magazines, and media outlets owned by MIIM. Obviously, you will need to keep up with the news, somehow, despite the fact that you know you cannot fully trust any such source for complete honesty. I suggest TV can stay, or perhaps radio, but NEVER select ONE news source (channel, station, commentator).
But whenever you hear an ad for a product on ANY mainstream source, or see one in a magazine you happen to read despite your strategy (e.g., waiting rooms), take a moment to write a letter, even if a form letter, to the advertiser(s). Do not use Email for the purpose, for only a written letter will have impact — and then, only if it is business-like and polite. Don’t wax as politically indignant as might I; “Dear Fascist: Regarding your sinful and shamless partnership with XYZ Media in their evil plot to…”
Better idea: tell them you do not trust the media source which aired their ad and believe it biased, because it is owned by (insert the appropriate military contractor or megacorps, here), and thus, you refuse to buy their products because they are paying for disinformation to be disseminated. If enough people did this religiously, advertisers would be more careful, and Media would falter, its income stream hampered and profitability down. It might even wax honest.
❑ Don’t be tracked by purchases: Demand retailers destroy or remove RFID chips on products you buy, and protest their use. Most will have no clue, so educate them at the register, perhaps forcing a call to a Manager… simultaneously educating those waiting in line (no angry rants — just calm explanations and politeness). In the end you will likely need to destroy them yourself (microwave oven for tiny ones, scissors, shredder or burning for larger ones).
Items where removal and destruction is not possible should be kept in a foil pouch when not in use (this includes some state drivers licenses, passports, and other chipped items). Pull clothing tags and similar, and destroy them, shred purchase documents unless you are desperate to be allowed a return or warranty remedy in event of a defective item, in which cass.. Simple discarding may not be sufficient for such items if you think you are being sought or surveilled; trash is not your friend, it is a data mine. Don’t pay by debit card unless it is prepaid and not tied to you by name (one reason many places don’t accept prepaid). Cash is King of safety, though it labels you a convenient ‘terrorist,’ in FBI retailer snitch programs (one reason we need to kill the System; its insane paranoia creates that which it fears in self-fulfilling cycles).
❑ Don’t work for the system; Do not allow yourself to be employed by a member of MIIM or one of their subsidiaries unless willing to use that employment to their disadvantage. An example would be seeking to find and expose information damaging to the company, especially if exposing wrongdoing. I, for instance, took a job working at Shell Oil, where I uncovered a terror plot, by chance. More likely, it would simply be better to take a job with a smaller firm, one more likely to itself be a struggling competitor to the larger MIIM players in its field.
Help them to succeed, remembering that a small firm is more nimble and creative, and can often fare quite well compared to a megacorps, which relies mostly on boardroom antics and bookkeeping tricks to advance its position. If enough people did this, MIIM firms would not know which employees they could trust and it would likely force them to be more honest and less conspiratorial for fear of being exposed. And, they would need pay more to attract better people, driving the wage base upwards for all workers, instead of conspiring to beat it downward.
❑ Avoid the paper trails: Avoid seeking permits and licenses where at all practical. Consider doing so under an alias, and using bogus addresses. An illegal extreme might be completely false ID, or multiple IDs, which I’d not advise as wise unless there was a shooting war. Remember that an alias is legal, as long as it still ties to your true identity. It is where and when you allow a given tie (i.e., your correct phone number) to be used or established that will help limit the usefulness of the paper trail.
If unsure, check with a lawyer. If enough people did this, the tracking systems would bog down in duplicated efforts and be confused by the alternatives, increasing your true freedom; paper trails that go nowhere. You literally route paper trails to alternate addresses or phone numbers. These can be real-World addresses/numbers where you have access and discovery regarding any attempt to use them (by the system), or PO boxes or similar mail drops (i.e., blind drops, double blind drops).
Examples might be relative’s addresses, or unused mail boxes such as where an apartment complex of 44 units has 45 mailboxes (slap a number on it), and so forth. Keep your real world address only for those things which you wish to receive mail for — and I don’t mean bills. They should go to one of the alternates. Have many such alternates, and establish a list of parameters as to the type of material you allow to be sent there. This is how to deal with utilities in a way that reduces trails. There is a difference between a physical address where the service is delivered, and a billing address.
Another very valuable tool is a lawyer or bookkeeping service, or any professional service that is willing to hold mail for you. Another tool is to swap addresses with trusted friends, or to take select mail at work, if you have access to it in a way that is not obtrusive or invasive to your employer. This is an even better way to deal with utilities: send the bills to your lawyer for collection. You can establish a trust and put the bills in that name, or pay directly through a lawyer. There are similar arrangements possible through financial management services available through banks and elsewhere, though they keep records and report to government. Think outside the box, and get some expert advice about alternatives.
❑ Avoid communications traps: Avoid using mainstream communications channels. Use disposable prepaid cell phones you replace frequently, donating old units to groups who give them to battered women and others who need a way to dial 911 without having a monthly bill for the privelege of safety. Read this about cell phone privacy and security issues. Create and employ a steady stream of free Webmail accounts and abandon older ones as you go, keeping perhaps three active at any given time, and using alternatives for varied purposes. I use one for Real-World contact in key transactions (let’s call it the ‘official’ number), one for my most important confidants, and one for things between. Consider mail box services, blind drops, etc., if needing secure and neutral mail delivery, such as described in my book, The Professional Paranoid.
❑ Don’t fall into the insurance trap: Avoid insurance whenever possible, to the extent your strategy allows. This advice can be very bad advice for some people, so be sure to examine the option carefully before you decide. I only suggest some alternative logic paths may increase the choices available to you, which are these…
Insurance is a bet between you and the insurance company and like all good casinos, the odds are stacked in their favor. The bet is this: They bet you and others like you will face problems which requires insurance pay outs which are collectively less than the monthly premiums paid by you and others like you. In the meantime, they invest your payments in stocks and other business deals and earn interest or dividends on your money while waiting to pay out any claims.
You, in turn, are betting that you will benefit by having a problem which exceeds your personal ability to cover the expense yourself. Who cares? Only those who fear the odds should care. The insurance company knows they will win, or they would not make the bet. If enough people did not take that bet, the cost of insurance would rise (because of fewer participants increase their risk to profit ratio) to the point that the system would fail; only the rich could afford it, and they don’t need it.
Take medical insurance. If you don’t have it, hospitals must still accept you and treat you. So you end up owing them a big fortune? Even a three day stay can cost between 12 and 100 thousand dollars! The insurance wouldn’t have covered it all, anyway, and you would still end up owing them a small fortune. If you are reading this, likely, you could no more easily pay back a small fortune than a big one. So let the debt stand, as either way, they would have no means to collect it if you have dropped out of the system.
Regardless, the hospitals (the big ones owned by MIIM) will write off the debt or work with you to cover it. There is also bankruptcy as an option, if they press you, as discussed later. I’ve used that one, myself, and while it had its down side, it had many benefits. Yet in the final analysis, if you don’t pay, and have no assets which can be attached, and don’t care about your credit rating… let them go fish! Bankruptcy is not needed, just toss the bills into the trash, and don’t talk to them on the phone.
Likewise with home or renter’s insurance. If you don’t have it, the worst case scenario is that you are homeless and without your possessions. All the insurance company would do for you, after an endless battle of paperwork and legal moves designed to avoid paying, is help offset some of your expense. With insurance with the same firm for nearly fourty years, I had some $40,000 in computers stolen, and never saw a dime, for instance. But gee, they were quick to pay off a $1,600 repair bill… and increase my premiums to compensate. Good neighbor?
In the meantime, you would still be depending on charity and the mercy of relatives or friends. You can go that route all the way and fare just as well in the end, avoid the legal hassles, and the insurance payments. Sure, for many of you that’s probably untenable advice. But tell me, what are the odds of a total casualty loss? If truly concerned, stuff that money away in your own investment methods against such a need; self insure. Some states have Self Insure laws which make it easier to do that effectively and safely, a bit like being Bonded.
Auto insurance is another problem. In many states, you cannot get a license or buy a car without it. So, perhaps you should not own a car, or have a license. If you choose to drive without and get caught without a license or insurance, the vehicle will probably be impounded or even permanently confiscated depending on local law, so the risk may be great. Or, you could just drive a junker and abandon it to the system in such a case.
But if your identification does not well track to you (per the earlier suggestions), you may care little about the fines and courtroom proceedings demanded by traffic tickets and fines which result. If your car was a $200 beater, as suggested, you may consider it expendable and cheaper to have lost it than paying the insurance and tickets over time.
On the other hand, remember that part of auto insurance is liability, and you probably don’t want to wind up being responsible for another citizen’s financial woes because you did not have insurance. Of course, one can buy just liability insurance and minimally be in the system. But if you are in a ‘no fault’ state, the other fellow’s insurance would cover it, and if he was uninsured, like you, then that was by his choice, making you de facto partners in suffering.
Doing without a car altogether may be the best bet — relying instead on public transportation. In fact, overloading public transportation will tax the system greatly and hasten good results, because it is inordinately expensive infrastructure which never quite pays its own way. Convenience isn’t everything. A Monthly Pass, $40. Watching the transportation system go bankrupt, Priceless. Moreso because they CAN’T shut it down, but will instead ‘bail it out,’ and that will cause more people to join with you, in the end.
❑ Don’t feed the system: Avoid paying taxes where possible, always vote taxes down if given a chance (unless something you just can’t resist supporting), and always demand more services which require tax funding. If enough people did this, the system would be forced to raise taxes to cover the need against the will of the people; more and more citizens will come to realize the system is not working, or not working to meet their needs. The movement grows.
There are many ways to avoid paying taxes, and most all of them are legal, though they represent a significant exposure to harassment and punitive response. It only takes courage to use them. I won’t waste the reader’s time with the details, because there is a wealth of material on the Web about the tax protest movement. Here are a few to get you started, including some eye openers which addresses the tax protest movement in historical and practical terms, as well as religious — many of them (those critical of ‘schemes to avoid taxes’) being created by the system to protect the system (use a grain of salt). On the flip side, some advice is just plain wrong, even fraudulent or criminal (take care).
http://www.ehow.com/how_5666700_avoid-paying-taxes.html
http://www.bizfilings.com/toolkit/sbg/tax-info/fed-taxes/tax-avoidance-and-tax-evasion.aspx
One can simply decide they are not going to pay taxes, and opt out of the IRS’ system. This is fraught with danger despite claims in some quarters that there are legal ways to do so, per several of the links found in the pages cited above, so I’m not suggesting it is a great idea for everyone. One could further rely on multiple IDs and poor tracking to addresses, and frequent change of jobs (if we had a better job market), declaring tax exempt status each time. You get to keep more of your pay until such time as you feel you are being closed in upon by the system demanding you comply or account for yourself, and then move on, and reinvent yourself once more.
Taken to the extreme, one could obtain false ID under the Social Security number of a deceased person. This would be illegal, and is not being advised — but CIA agents do this all the time, even multiple times for a given assignment. At some point, if a shooting revolution begins, this would be a more logical step, one we should all consider for personal safety. But by then there may be a National ID and chipping in place, rendering it an unworkable alternative. Preemptive moves may be wisest of all.
But if you can seek income from self employment or be legally considered a ‘contractor,’ you become responsible for your own taxation, and that offers opportunities to deal with taxes in a more useful manner. But it would take a book to discuss all of the many strategies involved in a good tax game plan. The Web links provided mention more than I’ve covered, here, including such books. And, of course, it is always true that you should seek every legal deduction or tool you can to simply reduce the taxes actually owed. You shouldn’t need to be a disenfranchised activist to see the value.
❑ Know what the system knows and help them unlearn it: Make a list of every business and governmental agency that likely has information on you. Contact each of them and ask for a complete hard copy of what they hold on you. Invoke FOIA if you must with agencies, and rely upon various consumer laws for the business sources. Force them to expend the hundreds of hours (in many cases) and other resources it takes to comply. If enough people did this often enough, their cost of doing business would skyrocket.
Take the care and time to review information carefully, and fight to have errors corrected. Demand that businesses do not share information about you with others (specifically forbid them to sell your name or information to others). If possible, ask to be expunged entirely from their electronic records. Many laws or corporate policies require them to comply, unless you are talking about data on contractual or financial obligations, or other legal histories of like importance.
❑ Don’t bank with the system: Avoid checkbooks and savings accounts. If possible, arrange to sign over your paycheck to a relative who does bank and have them cash you out. Of course, you can also go to the check cashing services, but they will demand ID and charge a hefty fee. The less paperwork, the better, but if dealing with a relative, have a written understanding between you so that the IRS won’t claim all your money is income they have not paid taxes upon.
The best arrangement would be an employer or work situation where cash payrolls were involved, ideally with no reporting to the IRS. Illegal migrant workers are often paid under the table and don’t get taxed, and thus working for less than ‘minimum wage’ may mean you still have almost the same spending power as if getting the minimum. So, perhaps joining them is better than fighting them for service jobs. That would truly take you off the grid.
❑ Consider Bankruptcy as a tool and a weapon: Do not fear bankruptcy, but do not blindly embrace it, either. Study and know the full ramifications of a bankruptcy as it would play in your specific circumstances, before deciding on its use. For many people, it is a valuable tool for exiting the system. Not only does it allow a fairly clean exit, but it can do harm to the system in the process where the creditors are of the MIIM variety.
I know of some people who deliberately build up large debt with MIIM institutions and firms, and then go bankrupt. Even though they may have hundreds of thousands of dollars in such debts, this is actually only a minor inconvenience and a drop in the bucket to most MIIM players. Still, I suppose, if enough people used this approach, immoral though I rank it, it could add up rather quickly. It is a dirty war forced upon us, and thus such immorality is not mine to judge, but yours and God’s.
Just know that while bankruptcy provides certain protections and allows the complete elimination of commercial and private debt, it does not protect against taxes and may not prevent repossession of some goods. The exception can be one’s home, car, and tools, but laws vary from state to state and even case to case — and the government is trying to make it so hard, it is almost impossible. A lawyer should likely be involved, and that is yet another expense to consider. Even a simple bankruptcy will mean many hundreds of dollars out of pocket up front.
❑ Don’t Educate Within The System: Take your kids out of public school and put them into private school or home school programs. The quality of education will rise (as will the cost, because you will still be paying taxes for schools unless you have dropped off the property tax roles). The moral teachings and principles of leadership and responsibility will once more be included as part of education. If you remain in the system, don’t be shocked when you learn your underage daughter has an abortion without your knowledge, or if your kids start being put on Prozac or similar psychotropic drugs without your consent. They will certainly be dumbed down politically, and have no useful grasp of history for preservation of America’s true heritage and core beliefs.
This ends the overt or outward steps one can take to drop out of the System. There are many other good ideas out there. I’ve tried to focus on the mainmost effective steps to start you thinking outside the box. In the next section, we will look at COVERT steps you can take, thinks not outward in nature, things which will increase your defensive posture should things turn nasty, even to include a shooting war. They remain none-the-less critical to your ability to well live off the grid, in or out of a shooting war, as they leverage your personal abilities by allying with others of like interest.
That will be Step Three, the final step: Establish and underground network
❑ Network and establish an underground: There is already a large network of ‘underground’ players which you may choose to rely upon. For a more trusting relationship, it is easier to start your own. Find like-minded people in your area and establish relationships based on keeping to as many of the below advised procedures as can be achieved. You will find that you can help one another in immeasurable ways.
One of the most valuable may prove to be bartering amongst networked peers, and learning from one another what works and what does not, or how best to apply a given tactic. My wisdom is miniscule compared to someone who is in your exact situation and who has already tried and discarded, or tried and refined a tactic. Make their experience work for you.
One place to look for established networks is public access television and radio, and underground newspapers. You can also find allies through bulletin boards at local colleges and places frequented by modern society’s ‘les miserables,’ such as head shops, book stores, music stores, secondhand stores, and so forth. Political rallies, especially for more Constitutional issues or controversies, is also a good place. While it is preferred that your network be closely aligned politically, remember thaty the enemy of your enemy is your friend, even if they be an Anarchist or Communist at heart.
Start up conversations and be friendly. Find common bonds (music, books, news topics) and get started just like any other attempt to make new friends. Then pose a question or offer a sentence which suggests you are dropping out of the system for political cause, and state your concerns. If they don’t know what you mean, educate them. If they do know, or after hearing your explanation, you will know almost immediately if they are kindred spirits. Develop such relationships with appropriate caution and reasonable paranoia towards possible betrayal. With a little time and patience, you will find some real gems. Discard the losers, and attempt to rehabilitate fence sitters.
Another way to network is to directly use Public Access radio and television resources, or the underground presses, yourself. You can (for free) learn to use broadcast equipment and create and present your own public access programs, or simply be a guest or participant in someone else’s show. Such shows are a wealth of information relevant to a broad array of social injustice and crimes or other victimization, and how to fight back. You will find allies, and you will make converts. In short, you will become an activist if not one already. That is what the system fears most — someone that pricks them, and they can’t reach out and correctively scratch back.
❑ Establish a Personal Network: Within the broader network, set up your own, smaller core underground support group using methodology similar to that used by the intelligence community when setting up an organization or project. This raises several sub topics, to include information as well as personnel issues. First, figure out who is the primary authority for the group (group leader). It need not be you if you don’t have a head for leadership or a desire for the tremendous responsibility it can represent.
Compartmentalization is a key intelligence community tool, and it would serve organizers to read up on that methodology, as well as other methods intelligence spooks employ. A hint of these methodologies is offered in these general guidelines or ‘talking points.’ As you seek to establish your group, these should indeed be discussed among you as issues to be addressed and decided upon.
Terms like covert, secret, and sensitive as used herein could be misconstrued to imply the purpose of such a group is clandestine or illegal in nature. That need not be true, but could be so, to a degree, yet still not be dark in purpose. For instance, you may wish to barter or trade services or goods privately in deference to what the system would prefer or considers legal. You will need a network of people with like interests in order to do this at will, safely. You will want to protect that network from discovery or the system will move to squash it (and you).
Of course, if a shooting war erupts, you will then have everything in place to escalate to darker needs as you see appropriate in defense of your family, country, and the Constitution. Everything will be illegal, then, but the true criminals are the ones judging it so. A network can easily be adapted for true intelligence gathering and black ops against any usurper of power, or formed into underground combat units, were that to become your collective wish. That is the real reason they won’t like the existence of networks. Here are some basic covert network guidelines:
❑ Categorize information: Identify material as being either sensitive (controlled) or public, (uncontrolled) and determine who has both a right to know (authority), and need to know (required to do their job/assignment) for access to controlled information.
Establish a formal means for controlling (restricting) and tracking (recording) both access and the ability to make copies. Never give both access and the ability to copy unless the copies and the process that generates them are also controlled and tracked. You need to be able to reconstruct any possible leak of sensitive information based on who accessed it, when, and how. Eject from your group any violators of protocols, even if accidental or seemingly innocent. The Network’s integrity is more important than risking it further to an uncertain loyalty.
❑ Safeguard information: Where possible, insert dummy information into sensitive information as a further tool for tracking leaks. Dummy information should be ‘detectible’ in terms of identifying the nature of the leak and ‘neutral’ in terms of impact on those accessing it (it should not cause them to alter their legitimate use of the information). It should be unique to a given or limited person or group of persons in terms of access, to better identify the leak source; a given person knows a given thing no one else knows, something which seems important and rightfully sensitive, but which is not, and something which would be easy to detect if leaked (cause visible actions as result). Establish ways to test such loyalties and detect any betrayal.
❑ Control access to information: Organizational members (family, fellow dropouts, and trusted friends or coworkers who support you in any way) should be categorized as protected or visible in terms of identities and operations. Protected individuals will be given and referred to only by code names, and only their operators or handlers (i.e., group leader) will know who they are and how to contact them. A protected person may assume a cover as a visible person, or may prefer to be seen as completely unaffiliated with the group. A good example would be a liaison with another group. A visible person might be a spokesperson, or a Lawyer, etc.
❑ Likewise with operations: Things you plan to do should be categorized as sensitive (covert) or open (overt) in nature. Only team leaders assigned a given operation will know all details. Even the assigning authority (team leader) might not need to know all details, though they will need to know those required to accomplish the goal and the general plan, that they might pick the best team members, and properly monitor the outcome or status of the effort.
Team members (operatives) may or may not need not know precise plans, timetables, operatives, lead-in event details, actual objectives, and so forth. Individual operatives will know only their individual assignments, restrictions or other parameters, and goal, but not have an understanding of the nature of the project or the identities of others involved unless part of the same interim goal.
❑ Form network alliances: The primary authority (group leader) will likely wish to establish special relationships as part of an ‘intelligence’ network for seeking out and sharing of critical information useful to the needs of the group. This should likely include counterparts in similar groups located elsewhere, where such trades of information can be mutually useful. But it might include ‘insiders’ positioned within non underground businesses, agencies, or groups able to provide useful information, persons considered friendly to your cause for whatever reason.
The usual formal first-contact means is a simple presentation of needs/interests and possibly the exchange of bona fides (proof of identity, purpose, and sincerity of beliefs based on prior accomplishments). It is better to rely upon gradual building of trust and bonds. Don’t show all your cards up front; it can backfire and get you into trouble, or scare them away.
You will want to establish simple tests of fidelity for the alliance partners, too, and conduct these with a subtle degree of covert manipulation, being careful to insure you can demonstrate, if caught, any deceit was not intended to be harmful to the other side and was necessary for your satisfaction of their integrity. Restated, give them something which seems like it could be used against you but which would backfire if they do (a trip wire, of sorts), and yet, which you can explain as such should they detect the deceit.
❑ Protect alliances: This creates a network of networks and amplifies the power base and resources for each group. It is acceptable to define limits of operation, mutual goals, etc., each group is willing or interested in working on. It would be dangerous to assume anything about another group, as there can be ‘guilt by association’ complications if something they do causes too much attention. Likewise, whatever you do can cause problems for others, so be sincere and honest when presenting your beliefs and intents, or you may find yourself cast to the wolves by an angry cadre. In essence, you live or die as a group by what you say as well as what you do, so live up to your own stated expectations, and hold everyone accountable for failures so there are no mysteries as to why they failed.
❑ Establish a Recon Team: The primary authority should find persons with skills and real-World resources, contacts, etc., suitable to establish conduits of reliable covert collection of information (intelligence gathering) about key strategic matters relating to persons or groups deemed a threat or activism target of the group. All group members should participate to the extent possible in overtly safe ways, but some individuals would excel in covert application, and their assignment to duties in this regard should not be known to the group. Special skills such as investigative or research skills, photography, locksmithing, communications technology, and computers are good starting points for considering who to assign.
This function is critical in a shooting war, but even if just trying to survive as an underground community, there will be threats which will require attention, and activism toward preferred reforms will need to continue in ways which do not threaten group integrity of operation. To fail to have such team in place as an underground group could be a significant risk if matters evolved to a shooting war.
Additionally, omnipresence in the greater community is desired with respect to information access. Therefore, project leaders and even group members may be asked to separately recruit ‘operatives’ who will contribute to the project or goals of the group without necessarily having allegiance to it, or even be aware of its existence. This is ‘recruitment’ which may involve any of the inducement methods used by the intelligence community itself, provided such methods have been approved by the group leader (some might be seen as illegal or immoral, such as bribes or blackmail). Not everyone will be good at recruitment, but those who are become good candidates for inclusion in the Recon Team.
❑ Establish a security team: The primary authority will also wish to establish a small team of persons who covertly address internal security — counterintelligence. They should be active in various projects as if ordinary team members, but would additional focus on internal security matters (watching for security leaks, infiltrators, etc.) Only the most trusted of persons should be members of this group, but all members should share the responsibility of watching for and reporting signs of security threats, external and internal.
❑ Use a consistent model: Each project leader will wish to mirror the organization of the group in small scale with respect to networking policies and layout, but bona fides will not be an issue, nor will they need their own security team, but rather, one individual would be assigned internal security matters. They will likewise wish to mirror the group leader with respect to operatives who will report directly to the project leader, only.
❑ Be discrete with all communications: Communications between various covert components must be established such that contact, sharing of instructions, information, and reporting, can be undertaken without anyone within or outside of the group being the wiser. The use of code names, code words or phrases, and flag actions (i.e., placing an object in a certain place or position), covert meetings, blind drops, and so forth, will be called for in almost every instance.
❑ Delegate where possible: These operational guidelines create a certain project management overhead which should be delegated downward so that a higher level is not overly involved in the operational details of a lower level. Upward/downward reports or downward group- or team-wide presentations keep leaders and group members informed as appropriate. The group leader should not worry about how the project leader communicates with his operatives, etc. Everyone with a special skill should seek to clone themselves by training a possible replacement so that the loss of any person’s would not seriously harm the group’s operational integrity, and delegate tasks to trainees to test their abilities and grow their confidence.
❑ Weapons of war: Early in the formation of the group, a consensus should be sought regarding definition of what weapons of war are deemed acceptable or required to meet group goals and maintain operational integrity. It is presumed and hoped that such weapons will be limited to the same weapons as used by any activist outside of an underground group (words, public protest, etc.). But given that Homeland Security has placed bid requests for 1.4 billion rounds of ammunition for use outside of the military, it seems clear that someone intends or expects there to be a shooting war, soon.
Therefore, a ‘policy’ should be calculated to everyone’s satisfaction regarding actual weapons and munitions which may be needed if a shooting war erupts, be they intended for self defense or for offensive operations against forces of oppression, be it on an individual or group basis. Considerations should include: a) access — will there money available to purchase, will there be a market in tact which can sell? If not, get them while you still can and stockpile for future need — you won’t want to wait until your only option is a criminal black market under Martial Law; b) choice — is there someone in the group who knows what weapons are good for what uses? If not, assign someone to find out; c) training — is anyone able to shoot a weapon or even comfortable doing so? If not, they should take courses while they still can; d) storage — where will they be kept until needed, stowed by individuals or the group? A secure place safe from deliberate detection efforts will be required.
Thus ends our review on how to drop out of the system and form your own underground. These are fairly basic in nature, and yet may simply be too much for most readers to contemplate. But sooner or later, the way MIIM is heading, we are all going to have to make a tough choice: do we stay within the system and be controlled by it, or do we break away from the system and seek its destruction, or at least be ready to do so at some strategic point before it is too late to do so?
Our survival as free-will individuals and citizens, and as a free nation, will likely depend on that decision. Better to make the decision sooner, than later. Better to do it methodically and with good principles of operation than by spontaneous guesswork. When MIIM makes its final moves, the warning may be mere hours before they start going door-to-door and results in shooting, and it will be too late for decisions, much less planning, then.
Do I hear someone knocking at your door? Better check your political watch and peek out the window before you open it.
Related articles
- 20 Key Ways to Defeat The New World Order (thedailysheeple.com)
- New polls on N.W.O beliefs and need for Revolution are in! Truth is rising in the light! (notesonthenwo.wordpress.com)
How to War with the New World Order (a Primer)
If you are no fan of the notion of a fascist, satanic World government ruling a depopulated World with all the power of the Antichrist, you may want to know there is one simple weapon we hold that the NWO fears we will discover and use, one more dangerous than guns.
How to War with the New World Order (a Primer)
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.How to war with the New World Order
Any enemy can be defeated if you know their weaknesses

Masonic mural at Denver International Airport depicts future of New World Order
Follows is an abbreviated collection of excerpts and updates from my book, The Professional Paranoid Defensive Field Guide, which includes many more such tactical advices, many being useful in any kind of war the New World Order force upon us, even a shooting war. But this post addresses a war that we can more safely bring to them, one non violent, perhaps forestalling the need for guns altogether by stopping the NWO cold.
Regardless, it also undoubtedly gets me listed officially as a ‘financial terrorist’ with evil Men in Black (or Army green, Police blue). Who cares? We are all treated as terrorists anyway, pending a moment of convenient political gain for actual ‘attention’ to our particular branding. Screw them and their paranoiac need to so label free thinkers, of whom Thomas Jefferson says government should rightly fear (for cause of making them BEHAVE RIGHTLY).
They can NDAA-vanish me at anytime, if they dare — just as they can any of YOU. That’s the whole point, isn’t it? If one man is not free because government violates its own Constitutional Law, then no one can rightly claim to be free. And so, given Homeland Security has placed bid requests for 1.4 billion rounds of ammunition for use outside of the military, the threat of an outlaw government seeking or expecting a shooting war with Constitutionalists forces me to write. If they so expect, so must we.
I must write, if for no other reason than personal self defense, which depends in turn upon the successful defense of others, give such advice. It is the collective WE, The People, who must survive, not mere individuals. Governments can come and go, can fail and be reconstituted, overnight if need be. But if freedom dies and We the People become a historical footnote, transformed into mere chattle as manageable individuals for feeding the profit grist mill of a corporate state (that’s fascism, by the way), something precious and extremely difficult to replace is lost for a long, long time.
The advice of which I speak consists of three simple steps, each with multiple topical elements, options, or ways to grasp and effect them. This post details Steps One of three. Collectively, they would allow us to be effective in the effort, and better assure individual and collective safety even if armed conflict is forced upon us.
And there are other resources online, some of which I have linked as you read. There is, for instance, fightthenwo.org, numerous sites promoting an effort called ‘global noncompliance’, and illuminati-news.com, where one finds an article somewhat like my own. Just type in the appropriate search terms to amplify your knowledge base, and your options, and to cement your confidence if daring to stand against the machine as do I.
You and I are not alone, given the broad range of topics which stir people to activisim in causes with which you should become familiar, for it makes of such persons a thing called allies. You need not agree with them all, but we all should stand together, for all such activists become targets of the NWO. I’m talking about things like Agenda 21, Canamex Highway, gun bans, Codex Alimentarius, Digital Angel, TIAO Dataveillance, RFID, NDAA, the FED, Political Control Technology, Chemtrails, Animal Rights, Occupy, Anonymous, and on and on and on.
Often, we should consider allying with both sides, perhaps one more than another if so moved — but ever mindful that the enemy loves to divide and conquer by fueling our disdain for one side over another. Fighting amongst ourselves means we don’t even see the real enemy. All these groups, save moments of manipulation, should be ally and enemy to the Globalist agenda, and not enemy, mine. To steal from another anti-NWO group’s slogan… which I essentially endorse, and again for which the operative word elected is WE…
“We are Anonymous. We are Legion. We do not forgive. We do not forget. Expect us.”
What can we learn from Anonymous? The most obvious lesson is that invisibility equates to an invulnerability to retaliation. Sure, they have losses, but the group is getting stronger and gaining in popularity in pop culture and elsewhere, and doing some real good as it goes, as some count good (no movement pleases all its supporters all the time). But by and large, their integrity as a working force against evil is unchecked because of their anonymity. They are off the Grid, beyond the Matrix (though hiding within and manipulating it), they have gone Underground.
That is were we must be to be both safe and effective in battle; underground.
So begins our review on how to drop out of the system and form your own underground — which is also to say, how to more covertly and safely defend your country from enemies foreign and domestic. These are fairly basic ideas, and yet may simply be too much for most readers to contemplate actually undertaking, at least wholesale (easing in may indeed be easier). But sooner or later, the way MIIM is heading with insane abandon, we are all going to be forced to make a tough choice: do we stay within the system and be controlled by it with no recourse, or do we break away from the system and seek its destruction through violent confrontation, or at least prepare for that eventuality? I think dropping out is a better, safer choice, one which also serves as preparation for a possible violent day; it covers all bases.
Our survival as free-will individuals and citizens, and as a free nation, will likely depend on our decision. Better to make the decision sooner, than later. Better to do it methodically under a plan and with good principles of operation than by forced into spontaneous guesswork on the fly by sudden, unexpected perils. When MIIM makes its final moves, the warning may be mere hours before they start going door-to-door and shooting erupts, and politically incorrect persons are vanished. It will be too late for decisions, much less planning, then.
What can be done to stop the New World Order?
Step 1: Understand the Problem, Know Thy Enemy

A few hundred people control the NWO
One must realize that the New World Order movement, with its roots going back to the Satanic Illuminati in, perhaps not so coincidentally, 1776, was a centuries-long plan to form a one-World government that their might be one World leader; the Antichrist. Believe it or not, we are dealing with powers and principalities, a relentless and seemingly unstoppable force which never sleeps, has countless minions of dark allies and dupes like forces to work with them unknowingly, and employs clever deceits and sinister plots to lubricate its machinations. Most of the battle is invisible, as often is also the outcome; we can loose significant ground and not even be aware until much later — the price of forgetting or pretending there is no Satan or Hell… or even a God, for too many of us.
It is not the United States Federal Government, or the United Nations, or the initialed Agencies or Department of Defense, or local law enforcement that we face. It is not globalist corporate giants, the FED and Jewish or international bankers, or the Military-Industrial Complex or the oil companies who are our enemies, nor their boards of directors, foundations, religious and charity fronts, or their political action groups. It is not the modern-day leadership of Illuminati philosophies inherent in the Power Elite round table groups such as the Bilderbergers, Club of Rome, Council on Foreign Relations, Tri Lateral Commission, Rhodes Scholar disciples, or even the infamous Skull and Bones/Thule Societies and their counterparts, or even the Freemasons from which sprang the Satanic Illuminati. Neither is it CIA, FBI, NSA, DHS, DEA, ATF, ONI, DIA, or any of the endless initialed investigative and enforcement agencies.
No. It is instead all these entities combined, and much, much more, who make up the face of our enemy. To define or limit the enemy to any one group or several, short of the whole, will miss the mark, and fail. It matters not if they participate knowingly in support of Illuminati goals, or by coincidentally by coincidentally aligned or secretly guided agenda. They are the collective wall of hardened, massive stones which lay between being free in all pursuit of life, and being a slave dead to God. Those stones form the Pyramid upon which sits the All-Seeing Eye, which is the symbolism of the very Antichrist and End Times; the ‘eye’ of Lucifer taking up the key-most position (where one should instead find a stone referred to as the frustrum), thereby frustrating the placement of the capstone, the return of Christ.
The question then arises, what chance does the individual (YOU, me, all of us who prefer FREEDOM and LIFE to slavery and death) against such a vast array of forces? What chance would we have to make a difference in what essentially appears on the surface to be prophecy being fulfilled, day by day, regarding a predestined final-day battle between God and Satan? Who are we that dare intercede in such contests between Titans of Biblic proportions, and what could we possibly hope to contribute of any value or impact in a battle of such scale; that which leads to and includes the showdown at Armageddon?
The answer is, in my humble opinion, EVERYTHING.
It is not simply God vs. the Devil. It is God and the good sought and achieved by Man through God’s gift of free will vs. Satan and the evil done by Man by subversion of free will. It is about righteousness (right-use-ness) vs. evil (vile-ness), both effected by our own individual choices. I believe that to the extent that there remains sufficient good will and righteousness in Man in his time on Earth, the date of Armageddon, and those things which lead to it, are delayed. Scripture refers to this as Grace.
This whole notion is reflected manifold in scripture, for those willing to heed a rather short Bible lesson, which is an all important part of Step 1 — to fully understand the stakes involved and the true unseen mechanisms which guide outcome…
Jerimiah 5:1 regarding God’s Judgement upon Jerusalem for failing to honor God and his Commandments says “Go up and down the streets of Jerusalem, look around and consider, search through her squares. If you can find but one person who deals honestly and seeks the truth, I will forgive this city.”
Genesis 18:26 regarding Abraham’s prayers beseeching God not to destroy Sodom, God says in respose, “If I find fifty righteous people in the city of Sodom, I will spare the all the place for their sakes.” Abraham negotiates the number down to 10, an important number spiritually.
Romans 2:4 tells us why the forbearance of Grace is offered (though all-too often sadly betrayed by Man’s delight in sin) with “Or do you show contempt for the riches of his kindness, forbearance and patience, not realizing that God’s kindness is intended to lead you to repentance?”
2 Peter 3:9 is more to the point with dialog on the coming of Judgement Day, and Christ’s return. “The Lord is not slow in keeping his promise, as some understand slowness. Instead he is patient with you, not wanting anyone to perish, but everyone to come to repentance.” Being patient, he gives us time (a period of Grace) in which to work toward salvation. What we do with that time is our own choice.
But if we make no effort on behalf of good in the face of evil, no matter how overwhelming it may seem, then we deserve the fruits of evil, as spelled out in Ecclesiastes 9:3 “This is the evil in everything that happens under the sun: the same destiny overtakes all. The hearts of people, moreover, are full of evil and there is madness in their hearts while they live, and afterward they join the dead.” More such as this can be found.
So let us also heed God’s advice and enter into battle. Ephesians 6:13 tells us how: “Therefore put on the full armor of God, so that when the day of evil comes, you may be able to stand your ground, and after you have done everything, to stand.” Much more is also available on this topic, as well. But hey – this video says it in an extremely beautiful way.
The number 10 in the Bible (and elsewhere), for instance, represents fullness, full measure, fulfillment. Thus, as long as Good can be seen sufficiently ‘full,’ as in ‘full of Grace,’ which is God’s forgiveness and forbearance, there is no reason for Judgement Day to come to pass. Should Man drop below a rating of ’10,’ Judgement is enabled and will come to pass. Thus, I argue; it is all up to you and me, to decide that moment — perhaps why ‘No man knoweth the hour,’ of that day, for we cannot take self measure.
The Bible offers more and better advice, than this feeble attempt at presentation. I simply offer how you might apply it using specific strategems. Let us consider:
Short of armed revolution, and in the absence of any seeming control over our government through the traditional election processes, the alleged system of checks and balances and for obtaining redress in the courts… as illustrated by the failure of Congress and the Courts to ever address crimes of the White House, or to curb the military or intelligence communities when they go awry… and surely their failure to quash NDAA, the Patriot Act, the outrageous acts of TSA, ICE, and all such madness — is the option to undertake another kind of war with the NWO; a guerrilla war fought on our terms, not theirs. I speak of an offensive war, one which effects a defensive posture, as well.
It may be time we take the battle to them, and use their own System to ensnare them.
Let’s face it. The enemy, as it otherwise stands, holds all the cards: We must use their money, follow their laws and suffer under their court judgements (for most of us, relying upon their lawyers appointed on our behalf — unless we are wealthy, in which case, we are more likely part of the problem), are subjected to controls by their police and military, must depend on our news from sources their Military-Industrial-Intelligence-Media complex (MIIM) controls, send our kids to schools in an educational system they manipulate, and use their insurance to visit their Doctors, hospitals, and take their drugs, etc. All the way we foot the bill for these things which define our limitations, and profit their machine.
At every turn, they hold control over our lives: we cannot get a job without identifying ourselves using their number. We cannot keep that job without giving them a huge portion of our wages as taxes, which they then frequently use against us, along with other monies they manage to extort, steal, or siphon from us through societal forces of their design. We cannot well protest our lot because they own the media by which we would have our say, and we use an Internet rife with their control, censorship, and eavesdropping (there is a better Web alternative in works, however — take a look).
We cannot ‘vote the scoundrels out’ because they control the voting process and the choices we are to be given. Ergo, Dog and Poney shows replete with hanging chads or worse, and if not that, assassination of candidates or death threats against them or their loved ones. In short, the terms ‘Republic’ and ‘Democratic Process’ have become a sham, as no matter who we vote for, the same old policies are continued toward NWO domination.
As bad, ‘redress’ is a word no longer in the American political lexicon; the System is rigged at every turn to defy it except in the most well-funded of battles, it costing millions for instance to employ media to advantage, or prosecute a case through the Courts, and the Internet is so controlled by cyberwarrior tactics that most organizational efforts there are easily derailed through infiltration and sabotage. And now they want to take the guns, which if allowed to come to pass, will mean all doors for redress can be permanently shut tight against us.
No thank you. Gunfire before gun grabbing, for me.
But the purpose of this post is to avoid the need for that eventuality. We must realize who MIIM is, and deal with them accordingly. MIIM’s arrayed forces and allies are by and large fascists and racists, and even Satanists, or some combination thereof. They tend to be psychopaths and sociopaths who wield immense wealth and power in all areas of societal and governmental structures. Their collective is hundreds of years old, and thus, they have had ample time to calculate and think ahead, to plan for every contingency, and tend to easily defeat a defense before we can think to undertake it.
But there is good news in all this.
Despite their position of dominance, it happens that there is one thing all principalities and powers fear, something which we possess… something they fear we will discover as the weakness or flaw in their plan. And it is such a simple thing, and defines Step Two. The beauty of it is, that implementing it now not only weakens their hand and strengthens ours, but if at some point the war becomes a shooting war, we will stand a much better chance of being able to either run and hide or to stand and fight. Either way, it will be harder for them to find and manipulate and destroy individuals, and thereby, the whole.
You can do neither if they collect you, first, or already control you outright in their System, what some call the Matrix. The solution? That’s the next post…
What scares the New World Order?
Step Two: Drop out of the System:
To explain that first requires that we understand what the System is. The System is two infrastructural parts; the commercial side and the government side. The commercial side sells itself to you every day. Advertising for products and services creates desire. Desire leads to purchase. Purchase yields profits against cost, and is a two-edged sword used against you. Part of the cost is payroll, which is used to pay you less than you are actually worth. They reap the GNP at your expense; you provide both the labor and the capital which drives their machine, so whatever they pay you, they get back by the resale of your fruits (you effectively work for free by giving them back their own money in exchange for very little of true value).
All along the way, taxes are levied to fund the other part of the System. They win-win, you loose-loose, but you get (something) they’ve convince you that you can’t live without, despite the fact that the World did just fine without it since the beginning of time. Everything from better deoderant to cars that talk, from perfect pills to pornographic movies through your cable company. And let us not forget GMO produce and foods so processed and full of additives that ants no longer eat anything in our kitchens but raw suger. As Dr. Phil has said, “If it wasn’t food 100 years ago, it probably isn’t food, today.”
Lucky you to have it so good, at long last. Whatever happened to happiness; the contentment that comes from simply living and enjoying nature and the company of others, and the fruits of our own labor? Who decided that these things had to be purchased in newly constituted forms, and that we should have no other choices? And, I might add, who can believe anything they tell you about what is good for you when every few years a new study reverses a previous finding, and perfect pills result in class action law suits for the harm they do?
Oh, but the System cares not for trivial details as these, because we are so dumbed down we don’t see the problem, and buy the next new thing.
Meanwhile, the government part of the system tracks and manipulates our participation in the first part in many ways. Your social security number, as mentioned, plays a major role. Your credit rating and banking numbers further track your every move financially, and government’s FINCEN (Financial Crimes Enforcement Network) and the Total Information Awareness Office (Department of Defense) are both gearing up to access every transaction from birth to death for every citizen. As the Bible has predicted, you already can hardly buy or sell without a number of some sort, a de facto Mark of the Beast by some accounts. But that yolk has not yet come to pass in its bitter fullness (Digital Angel awaits you).
The money itself also has tracking systems built into the bills (the little embedded strip you can see holding the bills up to the light can be sensed by special equipment), and FINCEN will be able to track cash as easily as credit once it is fully established and retail systems have evolved to accommodate the technology, called RFID (Radio Frequency Identification Device).
The Military AND the commercial side are partnering to establish wholesale use of RFID technology which will allow transactional tracking at points of sale to include a complete and total understanding of each and every product you purchase, effectively giving it a unique serial number. It can tell how and when you acquired it, whatever it is, right down to razor blades (already chipped). In fact, retailers have actually used cameras to track shoppers as they move through the store by zeroing in on select RFID chips in products in their cart, or already owned and in their possession (e.g., lipstick tube). You are the sum of your RFID, and once cataloged, you can be tracked anywhere.
As you read this, cash registers, inventory control systems, and security systems (doorway monitors, cameras, traffic monitors) are being designed and built which can scan RFID at a distance. Millions of credit cards, mailing labels, ID cards and driver’s licenses, and even cell phones have already been chipped with RFID, and some things, like select cell phones and cars, include GPS tracking. Security cameras and roadside or sidewalk monitors are being upgraded to track them. Unless you go naked in the World, or make your own clothes and use no manufactured objects, you can be tracked by RFID, because everything manufactured and sold will eventually have chips embedded.
We register with government for everything. We register to be born and to die. We register for school, to vote, to get driver’s licenses, to fish or hunt, to buy or rent a car or home, to have a phone or utility services, or to save a little extra money when we shop or to use credit, and so forth. At every turn we are giving out information about ourselves which is fed into computers, computers with back doors and inherent ‘links’ or leaks between databases to serve marketing and or government purposes. Hence Dataveillance.
How else do you suppose that you get so much junk mail with your name on it? One CIA front (two fronts, actually, one here and one in Europe), as I document in my book, the Professional Paranoid Defensive Field Guide offer to sell information on 98% of American adults. The other two percent have already dropped out of the system. Why should government intelligence agencies be in the business of spying on you and then selling your little ones and zeros for a profit? Do something about it, and drop out. Let them sell just zeros, if they can.
If you elect to remain in the System, if and when they want to reach out and get you for some reason, they will know right where you are, that very moment. Their data will let them profile you psychologically and predict your actions (as described in the Department of Defense’s original RFP White Paper for the TIAO). Don’t answer that knock at the door… you don’t want what they are selling. And you won’t be able to run at that point, because they can freeze all your financial assets, and in some cases, can remotely disable your car, and in all cases, turn resources such as your cell phone against you. It will be too late, then.
Proactive and preemptive tactics are what you need.
To preempt, disengage yourself from the system. When someone drops out of the system, the overhead of the system is actually increased to a degree, but the funding thereof is reduced. This causes subtle instability within the system which impacts the remainder of those still within the system. By deliberately weakening the system in this way, the New World Order is forced to become less transparent, and more domineering, more visible to those who have not yet seen that particular light. It compounds like interest as more and more people figure out they should exit.
Thus, more persons will exit, recruiting others as they go; the cycle will continue to the point where the system must either fail, or seek to seize absolute control sooner than it otherwise intended, before they are ready to do so with full confidence of victory. A shift in balance of power is achieved, the stronger side left unstable and off balance, giving the weaker side a chance to make significant gains with smaller efforts. The domino effect, slow motion though it will seem, at first.
Dropping out is fairly easy — just stop playing the game. Take actions which reduce your exposure to their ever evolving control matrix, and which free you up for further actions at reduced risk. Risk tends to lessen with time as you get better at living off the grid. Most of these things are very easy to do, and have little true risk, but may represent major inconveniences or social roadblocks up front.
You may likely face serious decisions about how you execute such a plan, and to what extent you are willing to go to make it happen. Fortunately, it need not be an overnight matter, which means you can ease into it over several months time, perhaps a few years (presuming we have that much time remaining). Just know that for every cost you are willing to bear up front, the benefits to which it leads tend to be far more valuable in the final analysis. The more steps you manage to accomplish, the easier are the remaining steps.
This ends the introduction to Step Two. What follows in the next segment are a series of suggested guidelines or action options to actually be effective doing it. Some of them you simply might not care for, or accept as viable or workable with respect to their goals or your personal circumstances. Don’t feel you need to follow these suggestions any more than you need to ‘play their game.’ After all, it is about free will choice; God’s greatest gift to Man short of life itself.
And that’s exactly what we are trying to stop the New World Order from ending: Free Will.
What are the tools of the New World Order?
Next up: How to War With the New World Order (Drop Out Checklist)
Related articles
- Is ARMED REVOLUTION COMING to USA? (americanholocaustcoming.blogspot.com)
- 84 Million Americans Aware Of NWO/Illuminati (planet.infowars.com)
Globalism’s Self-Serving Cycles of Terrorism
A reality check for citizens in every nation, democratic, communist, totalitarian, or religiously governed (e.g., Islamic); terrorism is not waged between governments or ideologies as outwardly advertised, but a covert weapon for political control used by Globalists against all peoples, especially the very members of terror groups duped into participation. More to the point, it is waged by powers and principalities, against God and Man, and serves Satan.
Globalism’s Deliberate Self-Fulfilling Cycles of Paranoiac ‘Terror Threats’
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
What you will learn reading this post…
- Terrorism is a sham, a weapon of political control technology;
- Terrorism never benefits terrorists in any real way, given the backlash;
- Terrorism is never approached as a problem to actually be solved because it serves the ‘target’ government’s interests as long as it exists;
- Terrorism is about control of the masses through fears designed to sponsor a willingness to subjugate ourselves to the New World Order;
- Therein is the real secret; the NWO is Satan’s Illuminati plan to seat the Antichrist, terrorism being a mere tool.
Who benefits from terrorism?
Reality Check Time for citizens of all nations

Image: Agence France-Presse Getty Images; India Ink blog post on lessons learned on terrorism in India (click)
Rewind the clock and review the last few decades or so — the time frame of the alleged ‘War against Terrorism.’ If you consider cause and effect relationships with much care, you quickly see that there would be no terrorism of true consequence except for government’s need to both instill fear in you as a form of Political Control Technology (behavior and thought control through deciet), and as a generator of ‘fuel’ for that very mechanism.
Look more closely, however, and we find even the governments are not the true benefactors. That would be Globalists, which put in other terms, is the modern-day Illuminati; the New World Order movement for a one-World government. This is governments run by the power elite, also called Fascism in some circles. Such rule is required if the Antichrist is ever to come to power. That is what I hope to illustrate in this post, along with some other eye openers of like nature:
Case Study; Control Group
But before we do that, we should first establish and consider, in the method of good scientific study, a ‘control group.’ We can then hold up the control group for comparison to the ‘terror group’ of events we will consider to make our final findings. Any differences should be for us valuable clues. For this purpose, let’s use something entirely unrelated which, like terrorism, represents a deadly threat to lives and the wellbeing of any nation; traffic accidents. Rewind the last decade or two in your mind and replay as you consider…
At regional and local levels, mostly, and to somewhat lesser degree at national levels, the high death toll and financial cost to the nation inherent in traffic crashes, including GNP impact, typically sparks ongoing efforts to improve highway and auto safety. This consists of an endless series of changes in rules, laws, and regulations, as well as advertising campaigns to educate drivers.
Specific examples over the years would include improving crash safety standards for auto makers, improved highway lighting, signage, and general design considerations, mandating seat belt use, ‘Don’t drink and drive,’ and other safety ad campaigns, tougher traffic laws and fines, more enforcement, and so forth.
In replay of that history, can you uncover recollection of ANY instance where a given governmentally sponsored approach significantly resulted in an INCREASE of traffic accidents or fatalities? I think not. The point is, in this control group review, we see that a problem which is seriously addressed for its own sake tends to evolve improvements, rather than degradation, over time. Restated, a legitimate problem genuinely and sincerely addressed in this way can always be made better by a cure, or an ineffective cure can be discarded in favor of a renewed attempt.
We must also ask, for reasons which should become apparent, who benefits thereby? The answer is, essentially, everyone. Drivers live longer and suffer less as a class, costs of accidents go down, though costs of ownership of vehicles tends to increase somewhat due to more expense in manufacturing and, for some, higher fines or fees associated with use of their vehicles, and taxes for improvements in highways. Most of us are content with these offsetting costs, and do not complain too much. The nation’s quality of life and GNP are enhanced.
More to the point, there are no significant losses of freedom or increases in political control by government, though new laws addressing safety issues may impose changes in procedures and provide for penalties; no one is unduly oppressed or repressed thereby, and basic rights remain unscathed.
Hmm… that seems to fit rather well with Titus 2:7 “In all things shewing thyself a pattern of good works: in doctrine shewing uncorruptness, gravity, sincerity.”
The Comparison Group; Terrorism

Osama bin Bushadine
Rewinding and replaying the same period of time, but this time looking at Terrorism, let us compare to the Control Group. One difference we see almost immediately is that virtually all of the effort to combat ‘the problem’ stems from national government responses, rather than regional and local levels. They, alone, by and large, have defined the problem and ‘solutions offered.’ That, alone, might be a significant clue; a small handful of Men, all of like nature and purpose within the power elite, control all aspects related to the issue.
Indeed, no one else’s opinions are even allowed to hold sway, regardless of their quality of logic or popularity among the People. In almost every case we find, in reverse to the Control Group, that their actions have stimulated, rather than abated, the problem of terrorism. Indeed, if we go back far enough, we find that the problem did not even exist except for the causality of their actions. To make the point, let us look at several ‘models’ of terrorism. Start with the European model:
Go back to the time prior to the European Community, and you find that terrorism essentially was non existent in the early years of Post War Europe. But it came to be, based on the nature of groups formed to foment terrorism, because of ‘Cold War tensions,’ if we believe the political rhetoric of the day. Based on the rest of this presentation, I’m thinking you will rightly conclude that assumption a sham, and the true cause lay elsewhere: false flag psychological operations. And should you not naturally so conclude, we will see there is proof it is so.
In point of fact, the processes which will be described, next (in the American model), apply to quite well to the European model. Terror attacks in Europe enabled the same exact processes, and in Europe, I assert, directly helped and led to the formation of the European Community, itself, a key Globalist early goal. Remember that notion as we near the end of looking at the American model, which will bring the point home in unexpected ways, and fully relate the Globalist aspect.
I only thought to bring up European model because it underscores and echoes in reenforcement the discoveries we will find in the American model. Any nation which has in the past or currently experiences terrorism should find these same factors in play, as well; they are portable concepts useful in any governmental environment. But in all cases, they serve only one special interest group, a group present in every governmental environment; Globalists. Allow me to make the case…
In America, terrorism was not even in the American lexicon until CIA began funding, training, and arming radical Muslims as part of their meddling in the affairs of Islamic nations rich with natural resources. Such meddling is a sure-fire way to generate resentment and hatred given their religious beliefs, beliefs which impact political actions in ways perhaps uncommon elsewhere.
I remember, in fact, one of the early newspaper articles (and later, others) on topic having to actually DEFINE the basic terminologies of terrorism in order to write about terror events. The point is, however, that we can lay terrorism at the feet of CIA and American foreign policy (on the one hand closest to our observation), and, as we will see, on Globalism, on the other, less visible hand.
If I were willing to make this blog longer than you would wish it in reading time, I could detail that for you to a level which showed CIA and the Department of Defense, often in alliance with military contractors and Globalist firms, actually imported most terrorists we have heard about acting on US soil (and elsewhere), often aiding in their visitation, training, and financing up to the moment of their terror acts, and even in their escape and any subsequent reentry into country. This I do in my four volume bookset, Fatal Rebirth, with over 1,500 footnotes of factual evidence. Want a free ebook of volume one?
So we see right away that the very problem was created by government. In defense, or rather concealment of the fuller truth, they claimed it unintended, even coincidental or unavoidable, and most of us believed them. But the footnotes I speak of show otherwise, especially in terms of lesser known ‘smoking gun’ events. One test of the sincerity of the claim is the question, does government move to ‘address’ this new terrorism problem as they did in our Control Group? Well, sort of…
The very first effort in response of note was the Patriot Act, a major assault on Constitutionally guaranteed liberties which, they promised, would be repealed as soon as they got a handle on the problem. Tyrannical governments which have evolved throughout history have always got their start with that very argument in justification of repressive actions, creating for themselves that slippery slope of no return. So many times have they had the chance to repeal the Patriot Act and instead elected to extend it, if not add to it, that I’ve lost count. Full grease ahead, downard, Ho!
Virtually all Congressional and White House actions aimed at combating terrorism have followed this self-same pattern: repressive responses which reduce Liberty in exchange for alleged security, a formula known to leave the people with neither, and which instead leads to a totalitarian police state. That’s how the Communist revolution in Russia led to something Karl Marx never intended for his movement. That’s how South American dictators grew their power. That’s how Hitler came to be, and so forth. But it is not how you combat terrorism, for it has not abated, though one may argue there is a current lull. So again, I ask, who profits?
To be sure, not the terrorists, who are guaranteed to generate a backlash against their own homelands. Examine all of history, and it is rare to find an example of the use of terror which resulted in good outcome for the nation from whence attacks originated, and on whose behalf their acts were supposedly committed. Their people suffered, typically through military response, worse casualties and consequence, than did the nation targeted with terrorism. It is a loose-loose situation for terrorists. There is but one exception, to be noted shortly.
Indeed, it is instead the nations targeted by terrorism who benefit. Not the citizens thereof, who bear the brunt of attacks at a personal level, but the men and political forces in power. Terrorism, in fact, gives power to the national government and its leaders, big time. Always; Hitler the perfect example. In international terrorism, the real loosers are the citizens of both nations, and more importantly, all religions who worsiph the God of Abraham; the Jewish, Christian, and Islamic faiths for whom terrorism is a great tool for Globalist (Satanic Illuminati) divide and conquer tactics.
But it is a double whammy for citizens of the target nation, because they not only suffer the casualties of attacks, but the loss of freedoms and rights usurped by a government become more tyrannical. Such benefits are why false flag terrorism is often the tool of one’s own government. Hitler used it, and many Americans are convinced George Bush used it in Sept. 11, and so forth. Fatal Rebirth offers much evidence in support of that belief. Such powers and principalities go out of their way to foment or fake terror acts, even if they have to supply and fund the ‘leadership’ of the terrorists and grow them into a local power — the only terrorists to benefit being those paid and empowered at leadership levels.
Proof, in Fatal Rebirth, shows the number two man of al Quaeda, in fact, to be a double or triple agent working for CIA and the Department of Defense. That’s right, the man who not only planned, but helped execute the attacks on American Embassies, the USS Cole, and the bombing of the World Trade Center, the man who managed to put bin Laden into power and unify other terror groups under his command… was one of our own. And if that were not enough, he held a job with a major defense contractor when not employed by the United States Army.
Is terrorism false flag?
Terror culture growth in a petri dish
The macro illustrates further. Government actions to combat terror actually stimulate it, rather than fighting it. Every action in the Middle East has tended to angrify Muslims even more, making it easier for them to recruit combatants to use against us. Middle East policy continues to be based on previous failures, with no learning curve in evidence. Even those things we would outwardly see as ‘good acts,’ were often deliberate betrayals.
For example, an American company providing schoolbooks for use in the Middle East for very young children used pictures of bombs, grenades, and guns for counting exercises… early enough that by the time CIA was training Osama bin Laden, those children were old enough to be recruited into al Quaeda. Now, once we have invaded and seized control of Afghanistan, the same publisher is providing books with butterflies and Poppy blooms. So now, instead of growing terrorists, Afghanistani youth will grow up thinking it perfectly normal to grow and sell the crops used to make Heroine, those fields guarded by American soldiers as you read.
We continually arm radical groups for use against their own local regimes we conveniently deem ‘repressive’ after decades of working with them as allies and arming them to the teeth in many cases. And then wonder why the radicals soon enough turn those weapons on us, irrespective of if a new regime was put in place, or not. Moreover, any new regime is more dangerous than the old, outwardly, though I maintain it is an intended consequence. This is indeed on purpose of our terror and foreign policies, as reflected by the fact that we keep repeating these mistakes as if oblivious to their cause and effect relationships. There is proof.
Fatal Rebirth, recounts a specific PowerPoint presentation at the Pentagon by Defense Policy Board kingpin, Richard Perle, part of the PNAC (Project for a New American Century) plans to take control of the Middle East, and by capture of the bulk of remaining Oil repositories therein, to control the World. It is all based on concepts espoused by the Council on Foreign Relations and other Globalists, and Zionist interests via a partnership with a joint US-Israeli think tank. It laid out a multi-year, multi-war/revolution plan for takeover of the major Middle East nations in domino fashion, specifically with the intent of giving control over to radicals, specific persons controlled by or partnering with Globalists. Every war in the Middle East, including the more current revolts, was in the Power Point, with more such to come.
For example, Fatal Rebirth shows you that the top two people now running the Afghani government were both former CIA employees who also did work for the Oil Industry, and both were directly involved in trying to get the Taliban to grant oil and gas pipeline rights to American oil companies. Do you honestly think citizens at large in Afghanistan would benefit by and approve of covert CIA/oil industry control of their nation in the guise of a new democracy? This is what I mean when I say outwardly, new regimes may seem less than friendly, but secretly, they remain Globalist puppets to perpetuate control mechanisms there, as well as elsewhere.
Make no mistake. This is not an American plot so much as an international plot by Globalists, the modern Illuminati.
This is also revealed in the referenced PowerPoint, where even darker aspects tie directly to Mysticism, Satanism, and Illuminati principles, matters requiring too much detail to explain in this venue. But I will add that Perle himself has his own CIA front-like operation which works directly with Arms smugglers for the purpose. Stability in the Middle East is NOT a goal, and never was. Such political machinations foster a kind of hidden control of the Middle East through secret alliances with terrorist leadership in exchange for quid-pro quo cooperation (attacks). There is no usefulness for political control plots found in peace and stability.
This covert alliance betrays the very reasons rank and file membership of terror groups join, as well as the greater citizenry and governments of their homelands, not to mention putting at risk the long-term welfare of religious doctrine which often guides their nation and political movements. If the people joining terror groups fully understood this, they would behead their leaders as traitors, and rethink their strategies in realization that terrorism is political control weapon being used against their own people as well is those of the target nation(s). Only the Globalists and their proxies in the involved governments and terror groups, can possibly win.
It deserves restating of who benefits, and how: in funding, arming, and aiding in terror attacks against the U.S. and other nations where Globalism runs rampant, the target nation governmentals (and the Globalist movement) gain two things, and the leaders of terror groups gain prestige and power over their own people for their ‘successes,’ and loyalty and devotion in anger evolving out of backlash-sponsored ‘failures.’ The two things the Globalist proxies gain are an empowerment to further restrict freedoms and wax oppressive through legislative response to terror event ‘successes,’ and validating police state mentality by offering minimal proofs of effectiveness at the few terror attack-sponsord ‘failures.’ Perfect quid-quo pro.
So we see that regardless of if a terror even is effective, or fails, there is win-win for the Globalist and their terrorist cohorts, but only loose-loose for citizens and terror participants, who are mere pawns in a grand deceit.
Ergo, in our comparison, Luke 6:43-44 seem quite appropriate; “For a good tree bringeth not forth corrupt fruit; neither doth a corrupt tree bring forth good fruit. For every tree is known by its own fruit. Figs aren’t gathered from thornbushes, or grapes picked from a bramble bush.”
A need to shift gears: homegrown terror
A kind of proof that such terror is artificially generated and outcome is controlled lays in the fact that if it were NOT so, the focus would remain on the foreign sponsored terrorism, and changes or experimentation in solutions would evolve to some eventual gaining of ground. But, if one is intending a Police State, one realizes that eventually, there will be internal resistance and insurrection forces to be dealt with at some point — given that the only solutions applied are repressive to freedom in nature. There is only so far one can go in oppressive reduction of personal freedoms without sparking resistance.
What is domestic state sponsored terrorism?
The answer? Raise the stakes and ‘broaden the war.’
Therefore, almost immediately on the heels of the Truther movement, we here in America started to hear about homegrown terrorism, a thing which caused most of us to respond with ‘???’ And from this has evolved a whole new series of staged events to justify the next waves of repressive acts and moves which, like those for Islamic terror, actually tend to foment and generate the very terrorism they would pretend to combat.
These also served to empower the TSA and other repressive acts designed to train us to be obedient to Police State social controls (and the basest of personal insults and groping to which we dare not protest.) This additionally causes us to realize we need to fear and respect our government, despite the fact that our whole form of government is based on the notion that they should fear displeasure of We, the People. Once we have it upside down in our head, it is easier for them to advance with less meaningful resistance.
But then, they had yet to meet the 99%.
But the general strategy creats self-fulfilling harbingers. To worry about and act to ‘prevent’ or ‘combat’ terrorism will eventually spawn it. At some point, you no longer need false flag or even entrapment provocateurs. Fascists want and need internal civil unrest in order to justify further tightening of their power grip, and the unraveling of and discarding of the Constitution (esp. 2nd Amendment) that they may evolve into a truly Globalist entity. Specifically, in America, as I frequently detail in other posts, the establishment of the NAU; the North American Union. An exact replay of Europe, and why that model was briefly examined.
We see signs this is so by the fact that there are separate non terror-related actions which are preparing for acceptance of Globalist programs which can only function if there is a new Constitution under an NAU construct. Agenda 21, Codex Alimentarius, the CANAMEX Highway, United Nations Small Arms Treaty and other U.N. sponsored mandates such as Biospheres, all clue us in to this fact. Our Constitution and, more directly, the Second Amendment make these things almost impossible under our present form of government. They need Martial Law, suspension of the Constitution, seizure of firearms, and a new Constitution with more leeway.
They are easing us into the mentality of Globalist control by selling us on grandiose benefits which seem lofty, but which are truly unworkable and intended to conceal the truth: total control is not freedom, but slavery, and a one World government sponsored by the New World Order is nothing but a mechanism to seat the Antichrist as World Leader — the whole point of the Satanic Illuminati plan to create the NWO in the first place.
So they push for gun control legislation guaranteed to make more militant the mindset of gun owners. Then we conveniently have a wave of gun violence worthy of sparking demands for gun control, a matter deeply tied psychotropic drugs evolved out of CIA mind control research. I don’t even own a gun and yet they make me want to stockpile weapons and ammunition to protect the Second Amendment from panic-driven, unthinking gun grabbers and their Globalist sponsors.
I can only imagine that militia members are waxing paranoid and actively planning for and training for combat with government or United Nations forces. Eventually, someone from such a group will undertake an act of violence to ‘strike a blow for freedom,’ but it will most likely be a false flag event intended to justify efforts to enact gun confiscation. It will, in point of fact, be labeled as ‘terrorism.’ No right thinking group of gun owners would effect a first strike policy, knowing this would be the result, though a paranoidal schizophrenic individual, may, with entrapment encouragements.
They passed the NDAA and the DOD embarked on reckless and provocative mock raids of American cities in violation of Posse Commitatus to make us fear government to levels that may spark shooting of federal agents, soldiers, or cops in perceived self defense, as examined in an earlier post. Again, if some truly paranoid person does not eventually do so, I fear a false flag series of events will be staged. It is absolutely critical that government be able to vilify gun owners if the NAU is to come to pass, lest there be a full-scale armed revolt.
They passed the Monsanto Protection Act, which protects Monsanto from liability and enables their forcing of dangerous genetically modified crops into the food chain (to include meat supplies since corn and soy are fed to animals as well as to humans). This will most surely make militant a number of the millions of farmers who have sued Monsanto, and tens of millions more who realize GMO foods KILL livestock, cause birth defects or sterility, and even cause hair to grow through the digestive tract from tongue to intestines.
Eventually, again as I have posted earlier in full review, someone will get the idea in their head to act out in a violently against Monsanto, perhaps an arson or a bombing, or worse. When you take away the right of redress through the courts, you guarantee revolt in some violent form. False flag efforts will hardly be needed, IMO, but entrapment encouragements will likely be involved. Fascists NEED such violence to come to power, and once more, they will call it ‘terrorism:’
We must have terror and internal chaos if we are to have a New World Order. In fact, it would seem it is forecast by God to follow a period of great upheaval. 2 Thessalonians 2:3 “Let no man deceive you by any means: for that day shall not come, except there come a falling away first, and that man of sin be revealed, the son of perdition;” In the text of King James, ‘falling away’ means ‘rebellion,’ and the day spoken of is the End Days, the ‘son of perdition’ the Antichrist. Be not deceived by your leaders.
How is terrorism a tool for political control?
Findings
In summary, we see the pattern is complete in all instances, following the path of cause and effect which is opposite the model of the Control Group. There is no effort to combat terror, but instead, to generate it. It is a political control technology, a kind of mind control; it generates fear to enable tighter security control at the expense of liberty, generates resentment to foment new terror threats and, thereby, to repeat the cycle even well after any foreign threats might be abated through takeover of their governments (per the PowerPoint).
There is a great falling away taking place in the Muslim World, as they war amongst themselves for radical supremecy. In the non Muslim World, where radical Islam conducts terror strikes, populations loose freedoms which will steadily lead them toward having no other choice but armed revolt. My prior blogs are full of this warning, and show how perilously close it may be right here, in America. But this is a World-wide phenomenon, as the Occupy movement has shown. We are ripe. We have been deceived by a cyclic strategy which brings us ever closer to boil over.
Such cyclic strategy worked in the Middle East flavor, it worked in the European flavor, and the South American flavor, and it will work in the homegrown flavor (if we allow it). Dumbed-down Sheeple comply with little true objection in the false belief it is perfectly logical to so evolve, not realizing, like the frog in pot of water on the stove, that the political control temperature will soon be fatal and leave them with no way to escape a terrible unwanted and unforeseen fate; rule by a totalitarian police state, and even the Antichrist. Got 666? Almost.
In Fatal rebirth, the cover of the first volume expresses it all this way: Terrorism creates Nationalism (obedience and loyalty to government — who’s political leaders benefit from terrorism); Nationalism fosters Capitalism (most notably, the Military-Industrial-Intelligence-Media Complex — who profit from terrorism); Capitalism empowers Globalism — the power elite of the round table groups, the modern Illuminati (who benefit and profit from terrorism); Globalism therefore requires Terrorism — funding it directly, and through their control mechanisms within capitalism, nationalism. In effect, it is nothing more than a cyclic machine, an engine to power control mechanisms, and made up of control mechanisms, cyclic in nature.
I call it the Armageddon Machine. I also call it treason, though that is just the outer shell at the national level. If a shooting war erupts (armed revolt), the shooting should not stop until that machine is destroyed. It will not be a revolution simply to restore the Constitution and reestablish freedom, but to delay or prevent the end of the World as we know it. The modern Illuminati, the Globalists of the World, will be the true enemy, not just some handful of govermentals and their obedient armies. It will be a war with powers and principalities, the truest source and form of terror imaginable.
They exist not just here in our own country, but in other countries, from whence they manipulate and participate in events, here. We will likely have to take that war to them, as well. Any such revolution will need to be enlarged to an internationally scope, or we will never be able to start anew with hope of long success. Emptying Freedom’s lifeboat of Illuminati water has little effect if the satanic hole from which it springs forth is not also plugged.
This is true in every nation. Fascism, the outward manifestation of Globalism, exists in every government to one degree or another. The more affluent and powerful the nation, the more it controls the nation in subversively covert or openly overt ways. It matters not if the country is socialist, communist, democratic, or religiously governed (e.g., Islamic); fascist-globalist mechanisms guide it toward Illuminati goals. As the Occupy movement has illustrated, there is hardly a nation where the people are not starting to awaken to these facts.
The next revolution will undoubtedly spread to be global — especially if it originate in the one nation thought to be ‘most’ free. As America goes, so goes Canada, and Mexico. As America and Canado goes, so goes Britain. As Mexico goes, so goes Central and South America. As Britain goes, so goes the European Community. As they go, so goes the entirety of the former Soviet Bloc. And from there it is only logical that Middle East and Asiatic, and the rest, join in.
Is the war on terrorism fake?
Epilog…
That possibility moves me to employ something from the Prolog of Fatal Rebirth as Epilog, here. Because all men seeking freedom in such a battle will become John Gault in that day. If not, or if John Gault falters and fails, the Antichrist will come to power; we suffer End Game. But if Gault prevails, as in the fictional character’s role in Atlas Shrugged (Ayn Rand), the World will come to a screeching halt on its current course to Hell, and get a second chance, a reprieve, and an extension to our lease on the Planet, though at great cost. From Fatal Rebirth:
Truth cannot live on a diet of secrets, withering within a web of entangled lies. Freedom cannot live on a diet of lies, in the end surrendering to the veil of their oppression. The human spirit cannot live on a diet of oppression, being subservient against the will to that unchecked evil. God, as truth incarnate, will not long let stand a world devoted to such evils. Therefore, let us have the truth and freedom our spirits require… or let us die seeking these things, for without them, we shall surely and justly perish in an evil world.
And yet, in final note for this post, I am also moved to write… as the Bible text indicates, that to so revolt may play directly into their hands. The answer is found in the nature and outcome of any such revolt, especially if Global. The key, I am convinced, is where the revolt starts, when and why, and how it concludes. That, however, will be another blog post. Here, I will simply say this: God has our back, either way — provided we make no foolish mistakes and act without right-use-ness of Free Will (righteousness). Subscribe to learn more.
Related articles
- Non-Muslims Carried Out More than 90% of All Terrorist Attacks on U.S. Soil ! Jewish & ‘Latino’ Extremists Carried Out Even More Attacks Than Muslims! (socioecohistory.wordpress.com)
- The FBI’s Fake Terror Plots – Judge Napolitano (therebel.org)
- N. Korea EMP Attack Next False Flag per Wag-The-Dog Evidence (proparanoid.wordpress.com)
Dear Government: I will not Comply w Internet Tax Bill; Go Fish!
Sometimes a citizen has to think Boston Tea Party. My time has come. Neither will I be forced into indentured servitude as involuntary tax collector, nor will I allow government to tax the sweat of my brow creating the goods I sell. There is more I will not, as well.
by H. Michael Sweeney
copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
The Senate passed the Marketplace Fairness Bill (Internet Tax)

from Facebook post by The Anti-Media
Just say no!
This is in point of fact sweetheart legislation to benefit Amazon.com and select other firms, though they claim instead that it will benefit local retailers who ‘suffer’ because people can buy goods for less at times on the Web. So what is this, really, a tax on savings? Where do they get the nerve to steal from us yet one more time? And how do they get the nerve to call Federal Price fixing against select businesses the ‘Marketplace Fairness Act.’
If you really want to level the playing field among sellers, pass a law eliminating sales tax that States might join with Alaska, Delaware, Montana, New Hampshire, and Oregon, who have no sales tax. Take Oregon, for instance, where voters must approve any tax, and pay only income tax; NO SALES TAX. Sales tax, especially when citizens have no say over it’s levy, or no, is legalized highway robbery by the taxing authority.
If the Bill passes the House the way the it is currently written, a Web marketer would henceforth be required to collect sales tax for all federal, regional, and local taxing authorities where the purchaser resides. This creates a nightmare of calculations which can only be met by using complex point-of-sale software, software which Amazon.com has already written according to radio commentator and former newsman, Lars Larson. Amazon is the only Web firm pushing for this law, the only Web company with the nerve to charge a 2.9% service fee on tax collection, payable by the third party seller who sells through Amazon.
That’s just one reason I don’t sell anything through Amazon, who has a bad habit of running rough shod over smaller businesses. That is exactly what the tax being forced upon its lesser Web competitors will be doing.
My findings are somewhat different than Larson’s, however. The service fee is correct, but Amazon uses third-party software solutions from a company called Vertex, which is currently the new name for (by acquisition) the old Arthur Anderson Accounting firm… you know… the CIA’s preferred accounting hijinks firm to conceal money laundering from illegal arms sales, drug sales, and terrorist payoffs. See 2002 on the firm’s timeline.
The government says they will give the software away, but do you suppose Amazon (or Vertex) will give it to them, for free? And what about firms like PayPal, where Web transactions are already complicated, and where Amazon/Vertex software will not likely fit nor be well adapted? Important, because a lot of Web marketers work out of simple Web sites which rely exclusively on PayPal for payment transactions, and have no site processing capabilities, even if handed the software, having no means of implementation short of paying someone to re-engineer their Web site.
The Supreme Court has already ruled that you cannot force a business without a physical presence in a State to collect tax for products or services paid for from persons within that State. But Congress is being asked (by Governors of Sales Tax States, naturally) to write such a law, anyway. That’s highwaymen writing laws to make highway robbery legal without even having to visit themselves upon highway travelers. Automatic holdups.
I refuse, thank you
And that notion brings us to the bottom line. Take me. I sell books. Books I wrote and self publish. This is the sweat of my brow and I will not have anyone charge a tax on one when I sell it. Nor will I do the job of tax collectors without being paid for the trouble, and certainly will not pay someone else for the trouble ‘on my behalf.’
You cannot force someone to do a job for free, that is called slavery. So instead of the highwaymen at least confronting the travelers and demanding taxes under threat of punishment, themselves, they instead intend to force others to do so on their behalf, and or to pay a third party (i.e., Amazon/Vertex) for the privelege; this is clearly indentured servitude, and forced contractual agreements with no say so in the terms, thereof.
Hmm… sounds a lot like Obamacare, doesn’t it. Funny, that was called a tax bill, too, once the Supreme Court told them forced contractual obligations were unconstitutional. Making it a tax made it legal, somehow.
Bottom line: If you want me to collect and pay such taxes, use someone’s software or services, or see me pay a sales tax on anything I purchase from another State via the Internet, then bring your guns that you can stand over me at every transaction. Bring lots of bullets, too; say all 1.4 billion of them, because I, and perhaps many others, will probably be forcing you to duck for cover in the effort.
Else go to Hell.
O.K. I’m calmer, now, having got that out of my system. And sure, the law only applies to businesses doing over $1M annually, and that is not (yet), me. But if anyone wishes to place an order for $1M or more in books, I WILL NOT TAX the sale, nor pay such a tax upon demand. That’s my promise… and THERE IS a harbor close enough for me to dump… well… in the absence of any bales of tea… the taxman who cometh. I’d even throw in a Congressman or two for good measure, except I can’t throw them any farther than I trust them.
Related articles
- ERA Opposes Internet Sales Tax Bill (prweb.com)
- US Senate Approves Internet Sales Tax (slog.thestranger.com)
N. Korea EMP Attack Next False Flag per Wag-The-Dog Evidence
If a military coupe planner needed an excuse for Martial Law in a hurry, what better way than to EMP the country and blame N. Korea? Such an attack from N. K. is impossible, and yet Sheeple wallow in the wag-the-dog Sheep Dip in a daze.
North Korea EMP Attack Next False Flag per Wag-The-Dog Evidence
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.How will North Korea attack America?
What you will learn reading this post…
- A review of signs that a false flag EMP nuclear detonation in our atmosphere will be staged;
- A review of what such an event enables and sponsors of value to the NWO traitors;
- What you can do to preempt and deal with consequences if it happens;
- How you can help prevent it from happening.
Is an EMP attack against America possible?
Why I write and you should read…
On April 3rd someone advised me that Google showed there were almost 200,000 Web sites claiming doom and gloom in the form of a North Korean EMP attack on the U.S. While many of these were the usual conspiracy theory resources (some with good reputations, some questionable, and some known disinfo organs such as federaljack.com.), unlike many conspiracy matters, there were also some mainstream news sorces carrying the story.
That, alone, made me sit up, but two days later, it had jumped to over 309,000, and is now nearly 900,000 (Korea + EMP attack.)
Even many mainstream outlets (e.g., Newsmax, Investors Business Daily, Washington Times) normally quite conservative were forecasting the darkest of all possible outcomes, some claiming up to 9 out of 10 Americans would die as result. I smelled, as did the person sending me the information, a big federal disinformation rat. Ever hear of Wag-The-Dog? Remember WMD in Iraq? That was really WTD.
If not, go rent or otherwise watch the Dustin Hofman, Robert De Niro movie with the same name, Wag The Dog. It will give you a hilarious review of EXACTLY what it is, and how it works, in a tongue-in-cheek presentation of real-World disinformation tactics employed by the Military-Industrial-Intelligence-Media complex. It’s all about manipulating people so they won’t question government crimes.
This EMP attack story is particularly disconcerting because it smacks of portending a false flag attack by our own government for reasons explained herein. Shades of the hit TV series Revolution, in fact, where there is sudden loss of power and political chaos results, almost as if the TV show was to prep us for what is to come that we might be easier to subdue in appreciation to military ‘rescue.’
What is an EMP attack?
What is an EMP attack?
When a nuclear bomb is set off, huge bursts of radiation of all manner are released in an unstoppable flood. Everything from heat and light to atomic radiation. Normally such bombs are used for their physical destruction capability, eviscerating a core area and causing blast and fire damage over a much broader area, and radioactively poisoning and rendering unsafe an even greater area. But there is another, more tactical use.
It is widely known but little spoken of, untill late (wag-the-dog tactic: foster massive dialogs in support of false story point), that if such a device is detonated high in the atmosphere over an enemy territory, the sudden burst of gamma rays creates a massive electromagnetic pulse (EMP.) So massive, in fact, that it destroys or interferes with most anything electronic. Motors, generators, and many digital and non digital components are, in fact, destroyed if in operation at the time, and some items will be harmed even if not in use, unless sufficiently shielded. The entire power grid would, in fact, fail and be extremely difficult to repair for a long, long time.
The result in such an attack on a modern society is total and instantaneous transportation into the Stone Age (more correctly, perhaps, the 18th Century, the agricultural age). But given that modern societies have no infrastructures in place which rely upon 18th Century technology, it might as well be the Stone Age. The ONLY defense against EMP attacks is to destroy the warhead in flight to destination, one of the reasons America has stubbornly tried to develop anti-ballistic missile systems since the time of Reagan and, truth be known, before.
But I note that wag-the-dog disinformation tends not to mention this factuality. Better if we think we are defenseless, where the only benefit to such a belief exists if one intends a false flag event.
Note: most of what is written from this point forward is covered, along with other related topics, in great detail in my four volume book set, Fatal Rebirth, including copies of the Constitutions mentioned below, with analysis. Want a free ebook of volume one? The book literally predicted 9-11 and resulting Middle East wars, and much, much more. It also predicted false flag attacks would be used to justify the Martial Law and subsequent events discussed herein, and what can be done about it.
What is a false flag event?
The nature of False Flag attacks
When a country wishes to start a war or enact some terribly repressive changes in political/governmental paradigms, it is historically common to stage a fake attack by some designated group or country as fall-guy. The people become enraged and demand retaliation, enabling a war, and wax super-patriotic and tolerant of any losses of freedoms or dramatic shifts in the structure of government to ‘better assure victory.’ Wag-the-dog rhetoric is required well before the event to paint the would-be source of the attack as a very dangerous opponent, vile and full of unchecked hatred — but the real purpose is to build fear and hatred of the ‘enemy.’
Internationally, the country employing false flag is seen as innocent victim, and may bash away at their new enemy freely, perhaps even recruiting ally nations. In some cases, even the people in the target country think their own country guilty as charged, which can foster an underground or more overt revolt which further helps assure victory. Only their leaders know the truth, but who will believe their claims?
Not very many beyond the most loyal, not many that count. Wag-the-dog efforts must, therefore, include ‘evidences’ after the fact, but one clue is that such evidences may seem just a little too convenient and quick to be located — such as the old reliable and oft used ‘found wallet’ belonging to the terrorits. Sheeple really are stupid to fall for that time and again. It has been used about six times, now.
All that is required is to stage a single, large-scale or politically sensitive event (e.g., assassination), or several smaller events which can be tied together at the desired time, all ‘evidence’ pointing to the same (false) source, also a job for the wag-the-dog folks. Hitler used the Reichstag Fire, burning of the beloved national library and many rare books, which was blamed on the Communists to justify changes in governmental structure which altered Germany from a Republic to a one-man show controlled by the fascist Nazi party. It launched the World down the path to WWII.
How can you spot false flag events?
Detecting false flag operations

Robert Dinero as spooky government disinformationalist Brean in Wag the Dog; “Why do people go to war?” “The War of the future will be nuclear terrorism… and there ain’t no war but ours.”
The Truther movement can offer a great deal of evidence that Sept. 11 was such an operation, and in fact, as I will offer in another post (and detail in Fatal Rebirth), most, if not all, terrorism against America and elsewhere, is demonstrably false flag in nature. All that is needed to establish or illustrate a false flag event is to use one’s brain in review of the basic facts, which, of course, Sheeple don’t know how to do because they’ve been dumbed down by psyops TV programming technology, rich with wag-the-dog. False flags look like this:
a) there is an abundance of early, pre-event wag-the-dog negative media coverage painting the bad guys as evil and out of control, building them up as a huge threat — perhaps even a specific threat;
(e.g. pre 9-11, Osama bin Laden was not exactly a household word, not even amongst the many radical Muslim terror groups, but he had an excellent PR firm, called CIA, who was fond of trotting out videos of him making threats, and listing him as prime suspect in prior attacks — while a CIA station chief pays him a visit in a Saudi hospital.)
b) the event takes place and immediate evidence is produced;
(e.g., within mere hours of 9-11, a terrorist’s wallet was found ‘laying in the street amid debris’, and other evidence sufficient to allow President Bush to provide the full names of all 19 alleged participants.)
c) the official story and available facts conflict, often in spades;
(e.g. 9-11 hijack flight passengers used cell phones to call relatives; cell phones did not work in flight in those days)
d) it contains nonsensical or illogical, impossible facts, or ‘magic bullet’ explanations;
(e.g. the nose of the South Tower plane passes completely through the building in tact, but nothing larger than a shard is found of it on the ground — no plane blown up by missile, by bomb, or fuel tank explosion has ever had the nose section destroyed so utterly, large sections of it should have been found.)
e) there are signs of a cover up regarding evidence: vanishing, altering, or manufacturing of evidence;
(e.g. Flight 993 cratered into a field, again with only shards remaining, and yet the crater is shown by earlier satellite images to have existed as a geographic feature well before 9-11. No FAA investigations looking at serial numbers of parts, either.)
f) there is a wag-the-dog disinformation effort evident; a cover up;
(e.g., American media refused to report what international media had already reported: that the date of the Afghan invasion was set, and allies arranged for prior to the 9-11 event, and that the Defense Policy Board had presented a PowerPoint presentation at DOD which, in fact, laid out a series of domino wars and revolutions in the Middle East to put radical Muslims into power as puppet governments — the Hashemites. It also failed to tell you that the top two men in the new Afghani government are ex CIA/DOD employees who also worked with Chevron Oil with Condaleeza Rice trying to get the Taliban to agree to an oil/gas pipeline deal pre 9-11. This is meticulously detailed in Fatal Rebirth, which has over 1,500 footnotes.)
g) there is an attempt to discredit anyone who questions the official story, and offer lame excuses for conflicting facts;
(e.g., Truthers are constantly ridiculed and labeled in casual remarks by media and governmentals as mere ‘conspiracy theorists,’ called traitors, insane, and even terrorists — more wag-the-dog disinfo. In ‘debunking’ various Truther claims, almost every one of the 25 Rules of Disinformation have been employed.)
h) an official investigative body (i.e., special ‘independent’ prosecutor, Grand Jury, panel, commission) is established to ‘find the truth, no matter where it leads,’ but they selectively examine evidence, alter, vanish, or falsify evidence, and are generally made up of people who benefit;
(e.g., the 9-11 “Independent Commission” was entirely, save one, made up of Bush cronies, each of which had previously bailed him out or were in his debt. Some had ties to the very institutions and technologies used in the attacks. And as Truthers easily point out, their efforts were white wash in nature with respect to manipulating, hiding evidence. All but two of the 12 had intelligence community ties. See table of cronyism toward bottom of this Noilwar! page.)
i) there is evidence of prior knowledge and/or media complicity.
(e.g., the Pentagon was making plans for emergency response in event of aircraft crashing into the Pentagon — photo of models planes and firetrucks and Pentagon with military brass in Fatal Rebirth… – or – BBC news in a live report announced that Building 7 of the WTC collapsed while it was still standing in the background… and then it collapsed on air, later, causing the Reporter to ad, “Oh, there it goes, now.” Google removes the vid, and BBC claims they lost the footage.)
Collectively, even individually, such wag-the-dog tactics are nothing more than a cover up. Whenever a cover up is in play, it is proof of a conspiracy, because if for no other reason, than to effect a cover up REQUIRES a conspiracy of players. Further, as there is no reason for a cover up unless there is an original criminal act, that, too, is part of the conspiracy.
Why would happen in an EMP attack?
What is the value in an EMP attack to Globalists here, and abroad?
As I have written of in many prior posts, there is an existing intent, in response to a perceived cause, to declare Martial Law and suspend the Constitution, and establish a new military government. This is out of the mouth of one of the nation’s top military leaders. You can bet that door-to-door searches and seizure of guns will follow, as was done in Katrina.
We next start to see mainstream media actually cover the fact that the military is practicing raids on American cities, in some cases with helicopter gattling guns blazing, and troops repelling, doors being blown off of buildings. They have never covered such events this way, before, indirectly indicating it is wag-the-dog psyops, again prepping citizens for future events. But of late, the quantity and intensity of such violations of Posse Comitatus has skyrocketed to include many major cities, indicating something big is on the horizon.
There is further the general intent by Globalists to establish a new Constitution for the NewStates of America, and the World Constitution, both documents already written (and both reproduced and analyzed in Fatal Rebirth), which makes rights more like a privileges, and provides an endless array of reasons, methods, and governmental authorities who can rescind them at any time, even retroactively, for individuals, groups, or all citizens.
Moreover, it enables the formation of the North American Union, and makes easier the acceptance of U.N. Treaties without ‘violation’ of ‘national sovereignty’ or the (new) Constitution. End Game ensues; the one-World government is formed (the World Constitution is ratified (already ratified in some countries), and the Antichrist can be seated.
Can you predict a false flag attack?
What are the signs EMP false flag may be afoot?
To answer this, we go back to our signs from above. I suspect that CIA types have infiltrated the N. Korean government to act as agent provocateurs assigned to stir up the young leader to his current state of rhetoric and provocative acts. The true likelihood of them launching an attack is nill, as indicated, below. But for a false flag event to enjoy any plausibility, there must be a seed basis for blaming another party.
a) there is an abundance of early wag-the-dog negative media coverage painting the bad guys as evil and out of control, building them up as a huge threat — perhaps even a specific threat;
(N. K. stories started weeks ago, and then suddenly the web was awash with EMP stories, both mainstream and Web.)
b) the event takes place;
c) the official story and available facts conflict, often in spades;
(Such conflicts are already known: an EMP attack requires an intercontinental ballistic missile and a large hydrogen bomb, both technologies at much lower states of development in N. Korea than required for the job — according to an insider analysts who should know — but who cannot say so publicly because it would blow his security clearance.)
d) it contains nonsensical or illogical, impossible facts, or ‘magic bullet’ explanations;
(This would only become apparent after the event, explanations forced to address any major holes in the official story — they might claim it was a high-altitude weather ballon-delivered device that escaped detection.)
e) there are signs of a cover up regarding evidence: vanishing, altering, or manufacturing of evidence;
(also post event)
f) there is a wag-the-dog disinformation effort evident;
(We have a taste: there are currently nearly 900 thousand Web articles forecasting EMP attack on the U.S. by N. Korea, some of which are mainstream, but most of which stem from a select few sources associated with government disinfo sources such as Sorcha Faal, who is often used by DHS and State Department. These, in turn, are replicated and virally spread as if trustworthy, typically enlisting the aid of those conspiracy theorists prone to not well checking sources or examining the basic facts; fear mongering.)
g) there is an attempt to discredit anyone who questions the official story;
(Currently, there is hardly anyone in this category to discredit. I knew of only know seven of us when writing this, who consider EMP a false flag scenario. But we are ahead of the curve: this is normally a post event phenomenon, and until and unless naysayers abound or have a major following and are widely believed, there is no reason to bother labeling us insane, etc. Worse, an EMP event negates the need as there will be no media/Web platform for dissenting views and swaying anyone in the first place.)
h) An official investigation;
(Also a post event item, and again in this case, no need, as there is no way to get the ‘report’ out to anyone.)
i) prior knowledge.
(also post event.)
I will add one more thing, also from my reluctant resource. Any such actual detonation of a device will leave a fingerprint. Nuclear devices put out radiation signatures which can identify the maker of the device. In like manner, it is impossible to launch a missile from that part of the World without it being detected, and tracked. Indeed, a false flag missile would be detected. Many countries around the globe have the technical ability to monitor these fingerprints.
However, ONLY those in power (and their agents who run the equipment employed) in those countries are the ones who would know the truth. You would think it represents a de facto attack on their country to one degree or another, given the release of radiation. Regardless, given that most such countries are Globalist controlled (e.g., the European Community) or otherwise U.S. allies, even to include Russia — you cannot depend on their honesty.
They will likely say ‘Yup, N. Korea did it!’ Others, like China, may say ‘Not possible! It was a U.S. device.’ The number and nature of opposing nations will determine the degree of plausible deniability at home and abroad. A few dissenting nations known to be less than friendly toward America will be dismissed easily. But if any neutral (watch South America) countries concur, then you will see a magic bullet explantion offered to counter; scientific mumbo jumbo to discredit or counter such claims. But here, no one will hear any of those arguments, so who cares what others are saying?
How to prepare for EMP attack?
What can you do to preempt, or prepare?
Preempting such a false flag event is easy: just spread the word. Share this post, replicate it, make it viral, and so forth. Kick Sheeple in the butt and wake them up, teach them to use their brain, and make disciple activist of them if you can. If we can get 200,000 posts revealing it a false flag out there, they are less likely to feel safe in fostering it.
Preparation is easy enough, but tactically difficult in many cases, and costly. There are several areas of concern, most of which can be usefully addressed with some effort and or money, but some defy good solution for many of us:
There will be total loss of electrical power, and it will be long-term. A good portable gasoline-driven generator will become worth its weight in Gold. But because gas stations will not be able to pump gas until they can establish their own generators, you will also need a goodly supply. Because it is not particularly safe to store a lot of gasoline in the garage, an Oil furnace tank becomes the better solution. The generator should be stored in a well shielded location, or covered with a metallic ‘blanket,’ or grounded mesh. You should have spare fuses and circuit breakers for every such item in your home.
There will be serious interruptions in the flow of food, water, and all goods. Even when goods can be found, most key items will be seized by FEMA. The price will be sky high an anything you can find as it will all revert to black markets, though FEMA and authorities will eventually use deadly force to attempt remedy. The first interruption could last for many months. So a good Emergency Kit of critical items and supplies is very valuable. The ability to quickly become self reliant (e.g., like a farmer) may make a significant difference in the ability to long survive. Rainwater collection may be appropriate, and despite alarmist concerns about radiation levels, it will remain safe. Regardless, plan on distilling all water prior to consumption, because water can only be stored for so long before things tend to start growing in the containers.
Transportation will be almost non existent. Any vehicle in operation at the time of the attack, and many newer (computerized) vehicles not in operation may no longer run, requiring replacement of many components before they will run (generators, alternators, various computer components, sensors, controls, switches, etc.) So now you know what spare parts to stockpile in a heavily shielded storage. Those few that do run will quickly become highly sought targets for theft. Vehicle security will take on a whole new definition and importance.
No single existing security scheme will seem adequate, and one may need to be willing to run over or shoot people trying to hijack you when traveling. Having at least one vehicle at all times not in operation, and of older technology with lots of spare parts in hand. Don’t forget windshield wiper and heater fan motors, and multiple sets of spare tires, as well, because tires will become targets for disabling a working vehicle. Have bicycles, scooters, and other alternatives available, too — but travel only in the case of dire need, or be prepared to defend yourself in the effort.
Computers, radio gear, and other digital systems not shielded from EMP are at significant risk. Those in operation will surely die, those not in operation and not well shielded may die. Walkie talkies, short wave radios, and computers, digital cameras, infrared goggles, and other critical devices should be placed in an Emergency Kit and the kit should be well shielded. A Farady cage (e.g., chicken coup wire mesh, or better), with a grounding wire, is best, but even just wrapping in aluminum foil may be sufficient, especially if stored beneath layers of buildig structure, such as in a basement. Of course, a TON of rechargeable batteries are in order with rechargers for use with the gas generator.
There will be rampant criminality: those caught without preparation will not see relief from FEMA or the Military early enough to prevent a ‘survival of the fittest’ mentality from taking over. If you have food, water, a generator, or a working vehicle, YOU BECOME A TARGET. You will need to be well armed and have security provisions in place against assaults on your home or your person when you travel. It will be in the best interests of the military to let things go crazy… to let people use up their ammunition and grow desperate for survival goods so that when they do come to help, we will be willing to cooperate in any way they demand, including forfeiture of our guns and other properties, accepting a new Constitution, and so forth.
No immediate help, not even from the military. Even if they wanted to help, they will be quite preoccupied in a war with N. Korea, and likely, Red China. We will hear only rumors, of course, because radio, TV, and the WWW will be none existent. That’s why helping to establish Web Walker, now NNN OSP (the Nodular Netizen Network Open Source Project — a 100% citizen-owned and operated wireless network which is operable even in disaster) may be of great value. NNN will also be useful against Web 2.0. When Internet services are reestablished (outside of Web Walker), they will be VERY government friendly; no politically correct sites will be found, only government approved information and globalist firms, and all Web data will be transparent and readable by the intelligence agencies at will. Support NNN OSP!
This is a bleak picture. Ask yourself, if FEMA was really there to prevent disaster and help in times of disaster, would there not be some such advice as this coming from them? No. The Globalists need a catalyst to propel them into power. It is not in their best interests to protect you from such chaos, or warn you of the risks and protections you can effect yourself.
They need to destroy the country if they are to advance to the next stage… and to insure you are without guns when they do — or at least out of ammunition. I hope you noticed there is a shortage of ammunition right now, in part because DHS has ordered 1.4 billion rounds in Satanic quantities for (?).
Related articles
- FBI Created 17 False Flag Terrorist Attacks (adask.wordpress.com)
- The Art of Catching Government False Flags in Real Time (activistpost.com)
I’ve Defrauded and Deluded Myself, I Am Not Me, But I AM
We go through life thinking we know who we are and why we do what we do, but like Actors who start believing they are the sum of their Press Clippings and the heroic characters they play, we are frauds. It took a simple but powerful video to teach me the truth, something I once knew, but lost sight of.
I once was lost, but now am found.
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.What you will learn reading this post…
- I’m a fool, and have been offering knowledge as if expert and wise, when in fact, I fall short;
- While my advice and opinions are based on truth and logic, I should have offered a better, more useful message;
- That message does not betray my beliefs and life experiences, but instead, explains them, and gives them meaning;
- That it should be the same for you as it was for me, if you will but open your heart and consider it;
Whre can I get help when no one believes my story?
A note of apology: a technical glitch with wordpress refuses to let me format the document correctly, making it a little difficult to separate paragraphs. No matter what I do, it displays as intended in preview mode, but not in actual URL access. I regret any inconvenience.

Introspection: the most valuable tool an investigative author could possibly have (examine yourself, first). From heartofaleaer blog (click)
I’m talking about me, H. Michael Sweeney, aka the Professional Paranoid, activist author, and consultant on privacy/security, and abuse of power topics. People come to me for help all the time, and I’ve started to believe in the value of my advice as much as they hope it to be of value in their desperation. Well, my advice may be good some of the time (more often than not, I have always thought, based on feedback), but even so, I’ve not quite been offering the best advice, in the best possible way.
This self examination also translates to my abuse of power issues of which I so frequently write, as everything I tend to blog about is so much in parallel to the basic aspects of things now clearly revealed to me because of simple but powerful video, that I’m hoping those who read my blog posts as activists, will see that parallel as well. It’s not just about me, its about everything in the World and how we deal with it. Let me explain by first going back in time. Some of you who have read my material before may know some of this, but as Paul Harvey used to say, its time “For the rest of the story…”
The Revelation
Monsanto Protection Act Lights Fuse of Armed Insurrection
Self Defense is the right of all Men regardless of any Law. When an illegal law deems to both make redress and self defense illegal, many will see it as time for a revolution. The Monsanto are coming. To Arms! To Arms! by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included. Will Monsanto GMO spark a revolution?
Reading this post and its links, you will learn…
• Things so terrible that I will not bullet list them, lest you flee this page in fear of dark things; • Things which may mean life or death to you, your family, and America as you know it; • Things which, in the best of outcomes will undoubtedly mean thousands of lives taken by violence and/or a biowar intending depopulation. Why does Monsanto have its own Police Force?Many of us ‘prepers’ and ‘conspiracy buffs’ have warned for some time that government wants a showdown with YOU in their gunsights. Now we start to see proof there is a price to be paid for failing to heed, for those not prepared to face what apathy and inaction leads us all toward at speed. Got Bushmaster? No? Gave it up to Feinstan, Bloomberg, Sorento, et. al? Better put your affairs in order, then.
This latest tyrannical atrocity, The Farmer Assurance Provision Act of 2013, also dubbed the Monsanto Protection Act to reflect fascist provisions burried deep within it, is one line in the sand many will not likely let be crossed without a gunfight, or similar violence. Understand this: a fuse has been lit, and while the length of its burn is not known, the bang at the end could very well turn into a repeat of 1776.
Frankly, I don’t know whether to pray it does, or does not; it’s THAT SERIOUS a line in the sand, to me.
But it is not my opinion which matters as much as does YOURS. But do you even have one? If you do not, or don’t even know of and understand the nature of the threat from GMO corn, soy, and other bioengineered seed programs, and matters closely related, you will be happy to know Mother nature has a special place for you. It is called survival of the fittest, and destruction of the weakest, you being the latter in the equation; those who die from eating genocidal foods, a very real possibility in almost any proper review of facts.
We are talking about crops genetically modified to have built-in pesticide powers based on Monsanto’s Roundup, a known poisonous substance, and other ‘properties’ which make it even more dangerous. The Act gives Monsanto the power of life and death decisions with zero responsibility (impunity), and takes away the ONE THING which is designed by our Forefathers to PREVENT armed revolution; the means of the People to seek redress of grievances with government through the courts.
OK, then, if that’s how they want it… get ready to ‘pass the ammunition,’ instead.
Because why? Because there is so much resistance to labeling such foods at every turn, and because they are used to feed animals you eat in other foods, there is no way currently to avoid eating them, or know if you are or are not, save perhaps eating only organic produce. Even then, contamination is not impossible. The only solution left would be to stop Monsanto and friends DEAD in their tracks, and unfortunately, it appears they wish for force matters such that the only option available for us to do so may be to seek it in literal terms.
We would rather it be figurative. But if YOU otherwise make no collective effort to stop them peacefully, you will deserve your fate for being a dumbed-downed mind-controlled Sheeple. Your apathy and non participation will be causal to any escalation toward violence forced on those unable to make headway peacefully. Their failure will be because of your lack of support.
If you don’t get that, stop reading this until you’ve visited Oz to find some brain matter to replace the straw in your head. It’s all over the Internet, and from many, many viable sources (even the disinformation deliberately put out as a straw man tactic is based on ‘kernels’ of fearsome truth — and efforts to debunk this particular ‘conspiracy theory’ themselves lack credibility and tend to follow the 25 Rules of Disinformation, such as employing straw men, vanishing evidence, and so forth).
Is self defense justified if GMO threatens the lives of you and your family?
Things to know for your survival:
- What Farmers have to say of their general concerns;
- What Organic Farmers say about GMO contaminating non GMO crops, 270,000 sue Monanto;
- Why 5 million famers are suing Monsanto over GMO for monopolistic practices;
- Why 17,000 Famers in India committed suicide over GMO (due those practices);
- How Monsanto in turn sues farmers when crops are contaminated with GMO, claiming ‘patent infringement;’
- What Monsanto is doing to establish a private police force to use against farmers;
- Why Monsanto spent $4.2 Million to defeat a GM food labeling law in just ONE State;
- What Lawyers have to say about why the legislation to protect Monsanto from lawsuits is needed;
- What Third-World nations have to say about GMO as a threat to their national security;
- What Huff Post has to say about GMO causing infertility and infant mortality;
- What UK news is saying about GMO causing cancers and birth defects;
- German Law Suite for GMO corn killing 65 Cows, causing infertility in others;
- About White House interference through Justice Department to prevent Monsanto investigation;
- On Sorento’s incestuous appointment of Monsanto Chief to Senior Advisor to the FDA, the only agency with authority over Monsanto;
- On Supreme Court Justice Clarence Thomas’ rise to absolute power after four years as Monsanto attorney;
- On Monsanto Employees in Congress and elsewhere in government;
- On Monsanto Protection Act introduced by Monsanto pocket Congressman, worded by Monsanto advisors;
- What Monsanto says internally about liability;
- Peaceful Protest Groups like OccupyMonsanto are undoubtedly now or soon to be labeled ‘terrorists.’
- OccupyMonsanto leadership is arrested at the White House though there on legitimate business and behaving according to protocol;
GMO is tied to the Doomsday Vault, Agenda 21, Codex Alimentarius, depopulation
Doomsday Vault, Agenda 21, Codex Alimentarius, = depopulation
If the above still does not convince you, ask yourself why GMO crop makers, Bill Gates, and Rockefeller have funded, along with Bilderberger leaders, a ‘Doomsday Seed Vault’ protected by the highest of security on a private Island in frozen wastelands owned by a Bilderberger. There, non GMO seeds are being stored for some future use, accessible ONLY by the Globalist Elite — while at the same time we see from the above that these same people are taking steps to insure non GMO seed cannot even be purchased, much less used, without violating law. We are talking about billionaires who have private chefs, often having them travel with them on trips, and NEVER eat anything we eat, except on a rare lark.
Part of that story requires us to add to this complex mix of topics some equally scary things outside of, but tangent to GMO: Agenda 21 and Codex Alimentarius, for instance, and the concept of depopulation, long a known goal of Globalists to reduce us to a half million souls. Consider all these things collectively, and you realize that violence may be the only recourse, sooner or later, unless we can unify and find a quick way to avoid it. But the fuse, having been lit, makes sooner more urgent, and later less tenable.
Now, Sorento and Congress show their true colors as traitors to all Americans and the American way of life… even life itself, in fact, the hallmark of Satanic thinking in the Illuminati Plan to create a one-World government that they might seat the Antichrist. It’s O.K. if you don’t want to subscribe to that ‘theory,’ but I’ve written books with over 1,500 footnotes to make that very case.
But it is just a Congressional Bill we are talking about, and, after all, Congressmen will simply excuse themselves, saying they ‘didn’t read the Bill’ before they voted it. Sorry, but if things erupt with violence (and to a lesser degree if it does not), they will still be held accountable if they voted for it, as will the Great Pretender who signed it. Consider the full measure of risk they undertake by their crime against humanity, which is also treasonous. There can be no greater penalty than those common in such crimes, especially if during a war (revolution).
And for the matter, therein (Sorento’s signature) lies the problem for Monsanto. Even if Monsanto is not razed to the ground by angry citizens… even if their poisonous ‘product,’ which is nothing more than a tool designed to give them a global monopoly on farming and to depopulate the World with a soft kill is not destroyed in grain stores and warehouses before it is planted… even if they survive attacks against them and their evil seed… the Act does not afford the protection they presume by its signing into ‘law’. It is a fictional belief… not Law at all, but a fictional ‘law’ which is at best temporarily useful while government pretends it legitimate.
Any Bill signed by Mr. Sorento under a false identity will eventually be ruled null and void as will be all ‘law’ of the last four plus years of his charade; his pretense cannot long last, even if it requires a number of years after his final term in office expires to force the Courts to admit it. He has no power, and neither does anything he signs. There has been zero Law enacted since he took Office. He, and all who helped in the charade will be jailed or worse, and of no power whatsoever to help Monsanto (Oh, happy day!)
There will be no protections if the ‘law’ thought affording them was found illegal. Nor if collusion between Monsanto and politicians writing the Bill, and the White House are established as criminal in nature (as is already seeming to be the case in the links above). Even if the Courts were so foolish as to overlook such reasons for nullification, perhaps due to bribes or threats, or the influence of Clarence Thomas, the court of Public Opinion and a little thing called self defense will still afford a final ruling which will be enforced.
Can self defense ever be peaceful?
PEOPLE HAVE THE RIGHT TO DEFEND THEMSELVES FROM HARM
This ACT, I fear, is the final spark which has at last lit a fuse which cannot easily be put out; a fuse leading to armed insurrection. I’ve tried to warn government and citizens in my earlier posts that every time politicians elect a criminal or unconstitutional choice, they put a gun to their own heads in a game of Russian Roulette, a game which decides if armed revolt breaks out.
Given the levels of frustration that I feel in this matter, I can only imagine how famers feel, and picture them raiding grain stores and destroying Monsanto product wholesale, if not marching on Monsanto properties with guns and torches to level them and drag corporate bosses into the streets. I fear hanging in effigy may not be seen sufficient. Hopefully I am wrong, and mere alarmist. But if I thought it would actually end the matter usefully, I’d be tempted myself. But would it be useful, really?
I wonder. I wonder because I also fear this is exactly the situation intended by Globalist leaders who seem to control our government. I fear it why DHS has placed bid requests for 1.4 billion rounds of munitions, including 9 million sniper rounds, none of it for normal military operations. In fact, I fear it related to a long list of other curious purchases and moves by government over the last few years, especially those since Sorento took office.
They collectively point to an intent to light such a fuse, I fear. Such pointers include, for instance, a steady stream of military mock raids on American cities with armed helicopters discharging gattling guns, soldiers repelling from or landed from the choppers to blow the doors off of buildings and engage in combat with ‘resistance,’ of some imagined sort.
Who will stop GMO crops from killing you or your family?
WE ARE THAT RESISTANCE
Confrontation is exactly what I and many others have feared all along was intended at some point in the future, and now, with the Act — it seems absolutely unavoidable and on the near horizon. Now that they see they cannot arrange to ban guns which approximate military grade, thereby effecting a de facto gun seizure, indications are now that they are going to instead foment a wave of violence in the heartlands and cities to justify labeling gun owners as a threat to national security, and come after them by force.
I even worry they may even foment that violence themselves and blame it on us (false flag operations) to justify their heavy hand to passive onlookers, the Sheeple at large. For this Act will undoubtedly result in such outrage and frustration as to move those most concerned to violence, even if it takes some entrapment or priming of the pump of anger and concern. If not shooting, then arson or bombing, from which must eventually evolve shooting by on side or the other. The fuse has been lit.
While there are only a few million rural persons who’s livelihoods still depend on farming success, almost all are quite well armed. There are tens of millions more who truly understand GMA enough to side with Farmers, a large number of them also armed, and some number of them are surely angry enough to say, “Pass the ammunition!”
But even if only 1% of farmers dared take a militant stand and resist with forceful action to protect their way of life, and the lives of all us… to save us from domination and ruination by Monsanto and a truly insane and clearly fascist government (defined, in part, as a government which makes oppressive laws to the benefit of corporate profits and the power elite to the detriment of the citizens)… even 1/tenth that number is more than enough people to start a full-scale armed revolution (statistically proven through history).
The mechanics of revolution, as I have pointed out in above linked post, clearly require only two things: a handful of angry people willing to do something which cannot be ignored by government, something which is seen to strike a blow for freedom; and a government willing to use a heavy hand to quash them for their trouble. In every instance, instead of quashing them, they make martyrs and fuel the anger in those previously asleep in their inaction. As result, those who survived the start of matters are joined by many millions more, and a full-scale revolution is born. “Pass the ammunition!”
This time, I fear government has indeed gone to far, and I urge everyone who is angered and moved to action to please stop, think, and act responsibly. Do not react carelessly out of emotion. Violence on your part is likely expected, and desired. Do not give in. Instead, organize and resist in every legal way you can muster (there are ways to do that). As part of the protest, I beg you make clear, as this post attempts to warn, that escalation will be the consequence of inaction by government and the criminal corporations.
They must be shown we will not let them continue to consider humans as mere objects they may move about on a financial and political chessboards, and knock off the board as pawns to suffer death or a life of misery or servitude. We will not idly stand by and let them win the game in which only they, Globalists all, deem to be onlyplayers with any chance at winning. We pawns must become our own self-guided army, and change the rule of the game so that we… we mere avatars of their avarice, are the ones who win.
How can GMO crops be stopped?
WE DARE NOT LET THE GAME CONTINUE AS IS
The fuse is lit. Who will help extinguish it by right action? Who will fan it to burn faster? Only YOU can decide. YOU are what you’ve been waiting for. Either way, I’m looking forward to ruining their game. But I can do nothing without YOU, be it words or bullets that eventually do the talking.
Enough talking. It’s all made me hungry. Let’s get something to eat…
On second thought, I’m not so sure there’s anything good to eat any more. Perhaps I’ll just share this post with some friends, instead, and start a dialog about what we might be able to do change that little problem.
What can we do to stop Monsanto madness?\\\\\\\\\\\
Related articles
- Monsanto Required (Nutrition Optional) (factgammon.wordpress.com)
- Top 10 excuses for Obama signing the Monsanto Protection Act (thedailysheeple.com)
- Monsanto = GMO? ~ Oh HELL No! (conservativeread.com)
Don’t Ban Guns, Ban Magic Bullets
Whenever you get a magic bullet explanation, you know there is a cover up. A cover up is proof of a conspiracy; a hidden agenda or dark plot. Why is that so hard for most of us to grasp that we accept without question the claim that it is, instead, mere conspiracy theory?
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included. What is a magic bullet explanation? What you will learn reading this post: • Magic Bullet explanations are commonly used as a cover up tool; • Such explanations do not always involve bullets, but use the same methodology; • To make explanations stick, it is necessary for media or government to label any who question as ‘conspiracy theorists;’ • Magic bullets, when unquestioned and excused by labeling, are themselves proof a conspiracy exists; • There are many dark bumps-in-the-night in our recent history which so illustrate (several included).Despite the fact that there is a dramatic and continual reduction in gun violence in America over many decades… part of the national experience involves an increase in traumatic mass shootings which are seemingly random and without cause… and we have media to point out every shooting event as though it somehow relates directly to the mass shooting madness, presumably in hopes we will say, ‘Please, won’t someone take our guns away?’
If everything were as it is presented on the surface, I might not be so upset with those who so conclude. The idiocy of a Piers Morgan and others suffering from Feinsteinian mental incapacitation would seem tolerable and understandable. But is everything as it is presented on the surface? Cleary it is not, if you pay the least bit of attention and are not dumbed down by TV Psyops News technology. I speak of magic bullets being used in the guns they want to ban, and similar use of failed logic in ‘factual presentations’.
I’m talking about JFK assassination quality explanations and related tactics employed in cover ups, even beyond shooting events.
Where do we get the expression, “magic bullet”?
What is a Magic Bullet?
The first Magic Bullet, the definitive illustration, arose out of the conspiracy to conceal the truth behind the murder of President, John Kennedy. In review, the Warren Commission investigating the matter had a big problem in two parts. The first was, the number of shots fired in a narrow interval of time from an obsolete bolt-action rifle in poor repair could not possibly account for the number of wounds of the two men the shots struck — unless there were two or more shooters… or unless there was some magic involved. FBI’s best sharpshooters could not duplicate the number of shots and hits fired in the space of time allotted and came nowhere close to the magical performance alleged of the designated patsy, Lee Harvy Oswald.
The second problem was that they dare not rule a conspiracy of multiple shooters.
In fact, Supreme Court Justice, Earl Warren had privately been both warned and threatened by President Lyndon Johnson that it MUST be ruled a ‘lone gunman,’ because there was a significant fear that the truth would require the U.S. go to war with either Cuba and/or Russia, as there was anecdotal (staged) evidence pointing in those directions. Too, there were early conspiracy theories evolving putting the blame on, variously, the Department of Defense, the CIA, and the Mob. But the later (Mob) included ties yet again to the former (CIA and elements of Defense), and so there could certainly be no conspiracy allowed if one were to skillfully avoid detection of skeletons in the national closet.
In the end, the conspiracy theorists would be proven right, of course — but even today, no one in media or government will so admit. It HAS been proven by sworn courtroom testimony of CIA agents involved (Marita Lorenz, E. Howard Hunt; Hunt vs. Liberty Lobby), and more recently, a Mob shooter involved , and additional evidences over time, all of which has been addressed in earlier blog posts and most of which was covered in detail in my book set, Fatal Rebirth. The Warren Commission had Marita’s testimony, but chose to ignore it.
The solution to prevent any such discovery was, like the problem, in two main parts, plus a third supplemental component. The first was a lie, and the second was to seal the records to conceal the lie. The lie was in the form of a bullet which defied multiple laws of physics and over 100 years of ballistics forensic science. It was first dubbed the ‘Magic Bullet,’ by New Orleans District Attorney, Jim Garrison in the trial for murder of JFK of CIA operative, Clay Bertrand Shaw… who indeed also had significant ties to the military and the Mob, not to mention an international assassination ring using both military and CIA resources (what Lyndon Johnson later called ‘Murder Inc.’), to include persons involved in the Dallas shooting.

From Jim Garrison’s trial of Clay Shaw
The Magic Bullet did the impossible: it inflicted two non-fatal wounds in Kennedy (entrance/exit), and four wounds in Texas Governor, John Connally, hardly any two of which lay in a straight path with a former point of origin. It traversed through 15 layers of clothing as well as the knot in the President’s tie (say, another 8 dense layers), 7 layers of skin, 15 inches of body tissue, destroyed 4 inches of a rib bone, shattered a radius bone, and came to rest in the Governor’s thigh, whereupon it elected to fall out onto his stretcher so it could be discovered at Parkland Hospital.
There it was found in near pristine condition with no signs whatsoever of having struck anything other than, say, a swimming pool filled with Jello. Such a bullet, copper jacketed, should have not only been significantly deformed by impact with the bodies, but also, shattered or splintered by the bones. But this was indeed a bullet with magical properties…
To have done as claimed, the bullet would have had to changed directions in mid air multiple times, and, according to Garrison, paused briefly in flight if to match the wound reactions in Conally seen in the Zapruder film. You can see why Garrison called it a magic bullet. So problematic was the conclusion, that the Warren Commission arranged for (bought) the testimony of a physics professor that all of the above was possible through a series of incredulous existential explanations using scientific theory (techno-babble). The cover up was begun, and much of America knew it, but could do nothing about it.
And if that were not bad enough… to make the Magic Bullet theory stick, Walter Cronkite, ex military intelligence turned CBS news anchor, thought to be acting under CIA’s Operation Mockingbird (media infiltration and manipulation), effected the supplemental component and coined the term: ‘Conspiracy Theorist.’ This he used skillfully to make anyone who dared question the Warren Commission’s findings seem ‘crazy,’ and ‘unpatriotic.’ That tactic (labeling) is one of the 25 Rules of disinformation, and dovetails nicely with the Official Formula for Conspiracy Coverups. It was so successful that it is still used, today, and in Spades.
Who uses magic bullet explanations, and why?
More Magic Bullets…
Not all magic bullet explanations are directly tied to shooting bullets, though some, as used in Sandy Hook and Aurora, do — as we see, below. They can instead be any key evidencial matter which simply does not make sense, but which is fully embraced and remains unquestioned by government and media, as if nothing were amiss. So let us go down the Rabbit Hole of our more immediate history and find some more magic bullets.
Oklahoma City domestic state sponsored (false flag) home-grown terrorist bombing: there are many magic bullet explanations we might discuss regarding the devastating blast at the Murrah Building that took 168 lives, including 19 young children at a day care facility on site. The most glaring is the nature of the bomb, itself. The official explanation is the use of a traditional home-made ANSFO (oil and fertilizer) explosive. The problem with that explanation is that the blast damage was such that ANSFO was impossible, a matter which forced FBI to continually upgrade the estimated size of (number of containers) the explosives used until they were forced to stop because they would exceed the capacity of the truck used.
The real problem was that the forensic evidence did not quite properly match ANSFO with respect to explosive residue, and, in point of fact, included pointers to a new type of explosive developed at a CIA proprietary which had earlier reported the equipment used to make the devices as having been ‘stolen.’ Additionally, the specific damage to the structure and nearby objects were unique and in opposition to the nature of the relatively low pressure blast waves associated with ANSFO, but sympathetic to the high pressure blast waves created by the CIA device, called METC, which produced forces of nuclear blast caliber on a small scale using an incredibly small bomb construct.
This is fully documented at my Web site, which, unfortunately, the IRS has effectively shut down as I can no longer afford to operate Web sites pending payment of an unexpected tax claim arising out of loosing our home in the Mortgage crunch (contributions via paypal using proparanoid at century link net would help get me back online). But I was not alone in this realization.
Brigadere General, Ben Partin, Ret, was the military’s foremost authority on explosives, and he essentially said much the same thing, and so, while I can’t link to my own Web site, you can hear him explain it in his own words, here. I’d rather you go to my Web site because it additionally contains condemning evidence that the bomb factory, complete with the appropriate Ryder truck used to deliver and detonate the bomb, had been photographed from the air by a hang glider pilot. He appears to have been shot down for the effort… at a secret facility constructed by the National Guard and protected on the roads by Marines with machine gun-mounted jeeps and in the surrounding woods by Men in Black — identically dressed in suits, sunglasses, and sporting shoulder-holstered weapons. You know… your typical National Guard facility built in a STATE PARK, complete with a cover story they were ‘testing Humvees’.
True to the above magic bullet explanation in multiple parts, even Partin was labeled a mere ‘conspiracy theorist,’ despite his credentials — or media failed to tell you he even existed. However, both he and I, among others, were invited by Willis Carto, former Editor of The Spotlight, a defunct Washington, D.C. newspaper — to participate in a round table review of OKC and Flight 800. That event, which I was unable to attend, also failed to make the news despite Carto’s best efforts to insure it.
Robert Kennedy’s murder by CIA’s Thane Ceasar and patsy Sirhan Sirhan: OK, just because a CIA mind control shrink was murdered after bragging to a prostitute that he programmed Sirhan… and because the woman in the Polka Dot dress that shouted ‘We killed Kennedy!’ in glee was seen with Sirhan, earlier… and because the cop in command on the radio that day told the cop that overheard the woman not to investigate because ‘We don’t want any conspiracy theories,’ was himself ex CIA… or because the man that ordered all RFK murder evidence relating to bullets fired destroyed was ex CIA, too…
That does not mean CIA had anything to do with RFK’s death, unless you are a wild conspiracy theorist. But there were some actual magic bullets to deal with, like the ones found in the woodwork destroyed as evidence, which exceeded the number of bullets in Sirhan’s gun… and the fact that the only shots which hit RFK were from immediately behind and fired upward (Sirhan was an appreciable distance in front of Kennedy). These bullets sound pretty magical, to me.
Thane Ceasar, an armed security guard on loan from a CIA proprietary was the person standing immediately behind Robert, that day, but of course, Police never thought to check his gun, lest THEY become conspiracy theorists. Amen.
The Vince Foster murder suicide: A key staff member of the Bill Clinton Whitehouse, Vince Foster, was found dead in a park at a precise location known in some circles for frequent use by spys in clandestine meets (e.g., a KGB meet with CIA). There was a conspiracy coverup at the time suspected (first revealed in The Spotlight) in the Clinton Administration, a matter in which Foster was a key player, and there were expectations he might spill the beans. No chance of that.
Instead, the official story is that he used an antique gun to shoot himself in the mouth at the park. Only problem was, it was indeed a magic bullet; in addition to the gun being inoperable, there was magically an absence of a pool of blood and splatterings at the scene, where his body was neatly laid out completely prone as if falling backward while remaining perfectly rigid. There were also no powder burns, another magical property. Charges of conspiracy theorists would abound at the slightest questioning of these inconsistencies.
Flight 800 friendly fire shoot down fuel tank explosion: Again, the best evidence I would normally point you to exists at my own Web site, where I reveal use the actual information from the official NTSB Crash Report to prove the NTSB altered, concealed, and manufactured evidence in support of the their conclusion that frayed wiring caused the center wing fuel tank to explode, killing 230 persons. Again, there are many magic bullets, but the primary fuel tank explanation is the most glaring — never mind many confirming eye witness reports (including military observers), radar tracks, and other proofs that a missile fired from a warship participating in war games brought down the plane.
There were many magic bullet issues with the fuel tank, the most glaring of which was the absence of soot on the appropriate surfaces of the fuel tank components, sooting which instead existed on surfaces inconsistent with the explanation (sooting on the outside, but not the inside where the explosion was claimed to have initiated). In like manner, the sequence of destruction described did not account for select (ignored) damages, specifically including two holes in the fuselage which were claimed not to exist, but which are visible in photographs if knowing where to look — which if taken as an entrance and exit point for a non exploding (war game) missile, would perfectly account for the sequence of destruction, both cited and ignored. Thirdly, the flight recorder data itself clearly reflected the effects of the missile strike and was sympathetic to the fuller destruction sequence, but was ignored and simply dismissed as ‘faulty data’ by NTSB.
But we who opposed the official story were mere conspiracy theorists, right? Never mind I have some experience in crash investigations while in the USAF, even reporting to Congress as part of a Weapon Systems Acceptance and Evaluation Team where crashes were reviewed and analyzed. Having credentials just means you are extra crazy to disbelieve the official line, it seems.
The Aurora theater false flag shooting team lone gunman event: once more, there are many magic bullets. Here, I’ve already outlined 25 key questions, thankfully NOT at my Web site, but in blog form. Most of these, or at least in combinations, represent magic bullet issues. So many questions, in fact, it took three blog posts to review them all, the last perhaps being key-most. Just a few to pique your interest in summary:
I’m a damn conspiracy theorist, that’s how!
Sandy Hook false flag lone shooter event: I would hope by now it would not be required to point out that you can’t claim there were only four pistols found inside the school plus a rifle locked in the trunk and then claim the rifle was used to shoot everyone. But it is equally important to question how it would be possible for nearly every bullet to find its mark and to stay inside the bodies of a child as claimed if it was indeed the rifle that was used. Never mind that the Police audio transcripts would seem to describe someone taking an AR-15 out of inventory (“shorting” is the word they use), perhaps that it could be claimed to have been ‘found.’
Surely don’t disbelieve or question the ever changing stories about kids and a bus driver who escaped the shooting by walking past a Fire Station where they could have both taken true safe shelter and reported the shooting to first responders immediately, and instead walked another two blocks to sit on the grass and await discovery by a strange little man with a Masonic emblem cut into the lawn in his back yard. There is more you might ought ignore, but to pay attention and object would make you, too, a conspiracy therorist.
The election of foreign-born CIA operative Barry Sorento President Obama: I really have to laugh if you don’t already know this one, and won’t even waste my time explaining another crazy conspiracy theory to you. Just go watch that new TV series, The Bible, instead, and you will feel better almost immediately… at least by the time you get to the scene where Christ is tempted by the Devil. LOL.
Sept. 11 false flag precision-crafted terror attack by a man living in a cave: Ditto.
Why are magic bullet explanations used?
Guns or magic bullets?
So, in conclusion, I’d prefer we don’t ban guns, but instead pray we ban magic bullet explanations, and banish news sources that never quite seem to notice their existence or address them, but are quick to label anyone who does. Use your brain, pay attention, and avoid accepting on faith the content of dumbing down TV news shows and, especially, spin-control talking-head commentaries; those sources with mottos like ‘fair and balanced,’ and ‘spin-free zone’ are clear warning signs.
Think for yourself. Question government, question media, question inconsistencies, and be vocal about it, loud and frequently. And simply don’t give a damn if someone calls you a conspiracy theorist for your trouble; you can’t confuse them with the facts, their mind has already been made up for them.
Me, I take the label as a badge of honor. I rather imagine Diogenese would be proud of all who quest for truth over lies. Got lamp?
Does mainstream media tell the truth?
Related articles
- Psyops TV: How They Dumb You Down to Set You Up (proparanoid.wordpress.com)
- Official Formula for Conspiracy Coverups (proparanoid.wordpress.com)
Psyops TV: How They Dumb You Down to Set You Up
You are being indoctrinated and conditioned to accept the Orwellian nightmare. Cancel that. You have been, and here is how.
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.How can you spot psyops on television? Easy. Just turn it on!
Update: April 20, 2013 Made correction to heading numbering, and to add this commentary based on media coverage of the Boston Marathon bombing:
Hillary Clinton’s worries about loosing the information war to the Internet were most clearly mandated in the Sandy Hook matter when manipulated media was never more obvious. They made so many mistakes in presenting ‘facts’ that it is no wonder that conspiracy theories were popping up faster than for JFK’s murder.
Then came the Boston attack by two Brothers, and it is suddenly a 180 degree shift, almost as if CBS, the only network I was able to observe (but perhaps others) had actually read this blog page and fixed everything I’ve cited, as well as repaired the flawed methods employed in Sandy Hook for getting out the official falsehoods. No more conflicting facts, replaced instead on continual source checking and self correction, and plenty of differentiation between solid sources and conjecture.
They also dumped the psyops special viewing effects described herein, making it very possible for the most dumbed down of us to follow along and not get confused. It was 1950’s quality newscasts, all over again, but in living color. If all of media would follow this model, and do their job to question questionable government reports, there would be no reason for we conspiracy theorists (their term for questioning contradictions in what we are told) to worry the likes of Clinton.
This does not, of course, prove there was no false flag event involved, or a broader conspiracy yet to be uncovered, but the point is, there is no set of conflicting statements to fuel speculation of any such conspiracy. I don’t see conspiracy being the case, though there are some things which bother me about the affair which I’ll save for another blog well after the dust has settled.
I’d like to offer three cheers to all of law enforcement at all levels for a hard-won effort, and to media for doing their job the way they are supposed to, per the best tenants of Journalism. Keep it up, and you can put people like me out of business, and me happier for it! End of update.
Was the Boston Marathon bombing false flag?
What you will learn reading this blog:
• Documented CIA and similar covert media psyops programs have been run on us as far back as 1914, and likely, before;
• Media disinfo and conditioning is a form of Political Control Technology, a polite term for mind control;
• TV programming is designed to make us fearful enough to accept military rule and violation of Constitutional rights;
• TV news employs psyops science in visual presentation as a key tool for dumbing down;
• TV ‘entertainment’ is often a dumbing down tool and/or conditions us for dark things to come;
• One small group controls and insures that school textbooks jump-start young people toward the dumbed-down state.
Can TV be used in mind control? Yes!

In 1968 you got a simple, direct presentation of news. Still images in the background, moving images filled the screen replacing the reporter. Simple, informative.
In defense of Television executives, media moguls, and producers everywhere, they have largely been duped into cooperating in TV psyops unknowingly… well, yes there are quite a few very eager to go along, too. After all, Fascists exist in every industry sector, especially when the New World Order crowd deems media control a priority; one of the key steps in the Illuminait’s original 1776 plan to establish a New World Order (they coined the phrase); a long-term plan to establish a one-World government that they might seat the Antichrist.
But here and now in contemporary times, the tools of psyops are all powerful, and the Illuminati would seem well and alive in the Globalist ’round table’ enclaves such as the Council on Foreign Relations, the Bilderbergers, the Skull and Bones, Rhodes Scholarships, and on and on. But we are talking here about their operatives, not their leadership; the ones who effect psyops in support of such agenda.
That means we are talking about CIA, military, and military-industrial-complex infiltration and manipulation of media, which is why in my books on abuse of power by and crimes of the New World Order, I call it the Military Industrial Intelligence Media Complex (MIIM). We start this examination by going back a little bit in time, as what has come before has been in building block fashion…
Does the military industrial complex use psyops to make us want a war? Yes!
Stage 1: Operation Mockingbird
Actually, stage 1 predated Mockingbird, and yet was its archetype. It took place pre WWI, when the Powder Interests (arms industry, predecessors to the military industrial complex) bought control of 26 newspapers to change public opinion about entering into the war.
Note of whimpering: I would normally send you to a link at my own Web site with the full Congressional Record proof of the matter, but the IRS has effectively shut down my income producing sites leaving me to live on about $530 a month after paying them $150 against some $6,000 of the National Debt seemingly engineered for the purpose. So the link illustrating the matter will take you elsewhere. Any contributions via PayPal using proparanoid at century link net would help put me back online. End of whimpering, for now.America was, at the time, quite Pacifist in view, until the bought media began reporting in unison the lie that German soldiers were regularly raping and then cutting off the breasts of Belgium women, especially Nuns. That, and like reported crimes never happened, at least not as claimed, though you still find citations that it did based on the original reports even today. Post war research verifies NO SUCH CLAIMS.
There was one oft cited incident as ‘proof’ of such. The victim was not a Nun, as reported by a Belgian soldier’s commentaries published in a book by the American Defense Society in 1918. That group was formed in 1915 with ex military, arms merchants, and others and was quite militant, led by non other than Theodore Roosevelt, who had lost the 1912 election against Pacifist Wilson. This was AFTER media reports about the atrocities and seems an attempt to ‘prove’ the matter after the fact. They hardly needed bother, as anyone who questioned such reports was decried as un-American, unpatriotic, and a Socialist traitor. ADS believed in enforcing Sedition policies (criticizing or questioning government was treated as a crime).
Such tactics changed our mood as a nation. So when they also illegally secreted munitions aboard the cargo holds of the Luxury Liner RMS Lucitania, and then let the Germans know about it… the Germans did the predictable thing and sank the ship, sparking enough outrage that we finally went to war. Now, while we are wanting to talk TV, here, and a bit perhaps about the film industry, closely related — what they learned in 1917 would apply once TV had gotten its foothold in the American landscape.
The National Security Act of 1947 saw the birth of CIA, Department of Defence, the National Security Council, and all resulting sins, including mind control projects. The lesser known story, as revealed in my book set, Fatal Rebirth, is that the Act was sponsored by the evolving Powder Industry, as well. In fact, they threatened to establish a civilian operated equivalent of CIA if Truman did not move Congress to do so.
As it happens, a relative on my Wife’s side was right in the middle of that, serving both directly in the Truman White House as State Department liaison, and later, a like role for the Secretary of Defense. I had access to a trunk load of his papers going back to WWI, where he was Army Intelligence. ‘Uncle’ George Bernard Nobel was also a Rhodes Scholar who later helped establish Pacific Rim Globalist round table groups while professor at Reed College, to whom we donated his papers — save the WWII code books disguised as Masonic lodge codebooks (a different one every 90 days), which I retained.
One of the earliest projects undertaken by CIA, of course, was to attack United States citizenry with the same exact covert war tools it would later apply against other countries they wanted to topple: disinformation through media infiltration and control. Called Operation Mockingbird, CIA put thousands of agents to work in all forms of news media, and bribed or intimidated, blackmailed, or misled legitimate reporters, producers, and moguls to cooperate. Don’t take my word for it, it, too, is in the Congressional Record.
It continues today in many ways, though Mockingbird was ‘discontinued,’ after it was revealed in the 1970s through Congressional investigation… after nearly 30 years of disinformation damage. One early example of particular note close to my heart was the coining of the phrase ‘conspiracy theorist’ by ex Army intelligence officer, Walter Cronkite. This was used to discredit and quell the many questions arising in the public’s mind over ties between JFK’s murder and CIA and the military, and the Mob partnership behind the plot, as eventually proven in courtroom testimony by ex CIA Agents involved (Hunt vs. Liberty Lobby).
Another close to my heart was the deliberate and methodical placement of jokes in comedy shows regarding tin foil hats (continues today there, and on the Web), implying anyone/anything relating to the possibility of mind control was ‘loony.’ In truth, the joke were sparked because a particular man in NYC entered a Police Precinct wearing a tin foil hat claiming he was being mind controlled by CIA experiments.
Totally ignored and shoved out the door with suggestions he see a shrink, his body was later found… minus tin foil hat, where there were dozens of electrodes implanted in his brain. This made the newspapers, and within weeks TV sitcoms began having jokes about tin foil hats here, there, and everywhere. There is no Web link regarding that unfortunate victim’s news accounts now that my sites are shut down, but I have also documented it in my book, MC Realities.
Here is another look at Mockingbird by one of America’s last true investigative journalists, Carl Bernstien, of Watergate fame. But the important part is that television played an important role in early Mockingbird, a role which would eventually prove key to getting Bush and Nixon into the White House, the start of the Bush Dynasty. That, and CIA ‘adapted’ software used to ‘count’ votes in America (the book Votescam, by James and Kenneth Collier, is a good place to review, the very first chapter).
How does TV dumb us down?
Stage 2: Indoctrination to set you up

50s & 60s TV: Broderick Crawford’s Highway Patrol, and The Man From U.N.C.L.E. featuring Robert Vaughn and David McCallum of NCIS fame as Soviet born Illya Kuryakin
Coincidental with Mockingbird was infiltration of Hollywood and TV programming with propaganda which continues at a heightened pace, today. I’m talking about the early use of documentary-style portrayals of real-world, and later, fictional events involving ‘white hat’ Agencies. The first of note was I Led Three Lives, a dramatization of the true-life story of an advertising executive who was actually a covert undercover FBI double agent within the Communist Party, where he was involved in aiding and yet subverting plots to overthrow the United States. It taught us to fear the Reds all over again after McCarthyism. Then came FBI, staring Efram Zimbalist, Jr., which overtly went after the Communists as well as bank robbers, kidnappers, and other nasties — in an America where the only car maker was apparently Ford, as the streets were filled with the sponsor’s product; an early product placement strategy where even the bad guys drove them.
The purpose of these shows was: a) to make you glad we had such agencies by; b) portraying evil everywhere, and c) always getting the best of the bad guys by being good guys, upright, moral, and always operating legally. It worked. I loved those shows as a kid, as did my parents. As consequence, a whole generation of young grew up wanting to join the FBI, CIA, Police, and so forth. CIA had shows like Robert Culp/Bill Cosby (in a serious role!) in I Spy and Patrick McGoohan as Secret Agent, not to mention The Man From U.N.C.L.E. (a secret United Nations version of CIA that taught us to trust the U.N. to watch out for us) and interest in law enforcement was fueled by endless Cop shows, of which there were so many over the years as to be pointless in naming, except perhaps for Jack Webb’s Dragnet, and Broderick Crawford’s Highway Patrol, two of the earliest successes.
Fast forward to recent times, and they’ve refined the tactic to condition us to military dominion. But also with a mental switch being thrown… as they now want us to think that its OK for the good guys to not be so legally upright. You know… ‘the ends justifies the means’ thinking (a Fascist’s motto). It started with shows like JAG (Judge Advocate General), where the military justice and investigation system was quite well presented that we should think it as good as civilian justice, coincidentally more or less synchronous with A Few Good Men, a major motion picture equivalent with Jack Nicholson and Tom Cruise. Well, they at least obeyed military law and procedure, but the next wave was a bit more ‘loose’ about it, spin offs from JAG, mostly.
That would be NCIS and a flood of sister/spinoff/parent shows where you are guaranteed in each and every episode to see someone’s privacy illegally invaded at the touch of a computer or other act (but it is OK, it is the military/government, after all, and they would certainly watch out for us innocent folks who have nothing to hide, right? Besides, the bad guys don’t deserve the same treatment as we would want for ourselves, do they?) Rights should be contingent upon government’s judgment, we are to believe, and they seem pretty free to make instant judgements in these shows… “Already done, Boss,” as McGee (Sean Murry) says so frequently in NCIS.
Note: Indeed this is exactly what the Constitution of the NewStates of America spells out. The document is intended to replace the current Constitution after Martial Law and military rule, according to former Naval Intelligence Officer, William Cooper, who discovered the document had been prepared at a cost of $25 million by a NWO think tank. In Fatal Rebirth, the entire document is analyzed verse by verse to reveal that there are no guaranteed rights. All are conditional, and all are subject to retroactive cancellation, and more than one authority may so decree. Anyone may be ruled an enemy of the State at any time for any reason.Such shows also tend to have advanced alien-caliber technological capabilities which work instantaneously to provide, in the nick of time for both the plot and the next commercial break, the critical evidence. This aspect is also present in many of the crime fighting counterparts such as Numbers (where they in each show attempt to present, but I have yet to see, a scientifically correct presentation of their questionable methodology), Profiler (gets us used to the idea that profiling, normally a negative term, is a bit like pre-crime thought police, and a good thing — we need more cops on our streets, and a few more in our heads), CSI, and so forth, proving to us Citizens that we ought be good and fully obedient, because like Santa, the cops and the Federales can always find out who’s’ naughty and nice, no matter what. Obey, or they will get you.
The truth is, though you may yet still doubt it, you are being set up for military control. More on that notion in the summary. And yet, it is a double whammy, because everything the TV moguls have learned about how TV can be used to manipulate you for the purposes outlined, can also be applied in marketing to boost advertiser sales. So while you are being dumbed down and set up, you are also being convinced you need (everything). So don’t just obey, but also, order yours today, and be sure to borrow heavily to do it! Remember, debt is the ultimate form of non violent control, and the last thing you want is to force them to resort to violence (which is inevitable, anyway, because they have to get the guns, you know – another reason for needing to stage an event worthy of Martial Law).
Does news deliberately dumb us down? Absolutely!
Stage 3: News Manipulation to dumb you down
We will talk about a number of things here, and a bit later, we will look at some specific technical methods employed. This section sets the stage. I’d send you to my Web site for the 25 Rules of Disinformation, all of which are easy to see illustrated in news in general. But I can’t (still whimpering and hoping for your kind contribution), so here is one of the many dozens of sites which have reproduced it, my most popular piece ever, with many tens of millions of downloads. You will find that each ploy is used on you every day, either directly by media, or by those they are interviewing without doing their job of asking hard questions when things don’t make sense as result of the ploy(s) elected.
So when they tell us there were four pistols ONLY found in Sandy Hook, and the Rifle was locked in the car, but all the kids were shot with a Bushmaster, and moreover, virtually every round fired by the 3,000 foot per second high powered bullets not only hit a target (almost no misses), but also stayed in the bodies… we tend to accept it as ‘factual.’ No wonder there are so many conspiracy theories afoot about that, and other news stories of our time. And this is proof of dumbing down, because more than half the people are NOT questioning the ‘facts,’ all effectively turned into Ozzian Scarecrows in search of a brain; straw-stuffed Sheeple.
Used to be, Newsmen listened to what sources were telling them, reported that, and when finding inconsistencies, pursued them until they had an answer, and told us that, too, wether it was a good or bad answer. They also used ‘redactions’ or other correction notices to update us when things became clearer. Now you get the official line, and on to the next story before you think something was amiss. Heaven forbid we should dare ask about the man behind the curtain.
Got a war? Imbed the journalists with psyops media warriors to insure news cameras see only what they are supposed to see, and report what is allowed to be reported (patriotic pro war). Those not willing to be embedded, get shot up by helicopter gunships and tanks just to make sure they might ought prefer to be embedded. And yet, there is even disinfo and psyops taking place in such friendly fire incidents…
Who is most often central to those reports? Reuters, an original CIA Operation Mockingbird front which was (at one time, at) owned outright by CIA, though you won’t find that in a Google Search (you used to be able to do so). It is listed in my books, and of course, at my sites (whimper). My favorite photograph (also at my Web site) is a news crew in Africa interviewing some Nigerians about terrorist activities in the region, and the guy holding the sound boom has a T-shirt which reads, “NOT CIA.” Really?
Which brings us to some more dumbing down/setting up. Remember that series of ‘bin Laden’ videos we kept seeing after 9-11 ‘obtained’ with messages for the World? If you are not afraid of terrorists, you won’t put up with oppressive Constitutionally neutering laws and atrocities by TSA, unconstitutional border checks 60 miles inland on highways not even going to the Border, and military gunships letting go with their Gattlings near your kid’s school. Internationally (but not in America), experts on bin Laden, on the Arabic language, and in governments far and wide were stating publicly on THEIR news that the videos were fake (eventually admitted to by CIA), not bin Laden, but a look-alike, and not saying what was claimed, at all.
Keep in mind every news outlet in America of any clout ALWAYS keeps tabs on what other nation’s media are talking about. That’s one way they learn about newsworthy events around the World, and about how other nation’s see events in America, which is often an element of the ongoing story, here. So it isn’t just experts in America they were deliberately ignoring, they were also pretending no one else in the World was talking about it. Deliberate psyops by concealment. That’s willful malfeasance, and as such disinformation has effectively cost American lives, makes them complicit in murder,should anyone wish to file a lawsuit.
But, thanks to the Internet, we eventually as a collective consciousness began to realize the tapes were phony, and we also began picking up on stories which revealed that the Iraqi troops bayonetting of babies in Kuwaiti hospitals in order to steal their incubators was, like the Belgium women’s breast story… an official CIA hoax. Now here is where we see yet another manipulation of media, this time the Internet. As recent as two years ago (last time I did it, anyway), you could find mainstream coverage on the Web of the revelation that this was a lie fostered by a Public Relations firm that is listed as a CIA front. Not now. Now you can only find blogger, Youtube, my closed Web site, and foreign media reports. One of the Rules of Disinformation is, after all, ‘If you don’t print it (or hide it, later), it didn’t happen.’
It was roughly in this time frame, in my opinion, that America began to realize that we hardly EVER got the truth from Washington, or for the matter, the Washington Post, New York Times, Time Magazine, CNN, MSNBC, ABC, et. al. The led to…
What is the information war? Disinformation at its finest.
Stage 4: The Information War
The information war was officially on between the Internet via outspoken activists, investigative writers, and indeed, conspiracy theorists who sought only the truth, and the MIIM complex and their minions of control, mainstream media. This was recently officially acknowledged in a recent remark to Congress by Hillary Clinton as Head of the U.S. State Department, obliquely referencing the Internet in and among a larger collective of ‘alternative media’:
“We are in an information war and we are loosing that war.”
Of course, you only got the sanitized version from the Washington Post and other mainstream outlets. They would have you believe she was only worried about foreign news networks such as Al Jazeera, and RT (Russian Television) News. Both of these outlets offer English speaking versions and are enjoying American viewing attention at up to 100 times greater than failing american media giants. And where are they getting all the attention? Not via TV sets, but the Internet, a little detail omitted in the telling of her story by those media giants.
But who can blame us for wanting to hear what other countries say when we find out our own country is lying to us? And I mean BIG TIME. Did you know the Pentagon knew the date of the Afghan invasion and was sending Colin Powel and top US Generals around to our allies to arrange for multinational support well before Sept. 11 attacks? What? You thought we only went to war when there was a just cause? Would it help you to know that Australian, Indian, UK, and Russian news sources were talking about this before Sept. 11 and wondering how we were going to justify war with a backward non technological country rich with oil, gas, and illegal drug growing operations?
Clearly, someone in the military knew in advance there was going to be a ‘Big Wedding’ (al Qaeda’s alleged codename for 9-11) event, and was sending out guest invitations. But American media dare not report that fact before the event, or you would realize 9-11 was an inside job. Truthers exist everywhere, as result of the endless conflicting facts, but are belittled by media in self defense; if they admitted the truth, they would be confessing complicity to a conspiracy to mass murder.
And yet they continue to loose ground, making it an urgent matter for the Globalsist to more quickly move toward Martial Law, because THAT will also enable…
Stage 5: Internet 3.0, the Kill Switch, and political censorship
Congress has repeatedly attempted to redefine the Internet towards political censorship, a matter which deserves its own blog, and indeed, many good articles already abound. Take a look at SOPA, PIPA, and CISPA, for instance (Congressional Bill nicknames). But if there is a Martial Law, the Web will be shut down, as will be phones, mail service, and radio/TV as we know it. The only communications allowed will be government to you, and mostly unpleasant in nature. Moreover, it will be illegal to criticize government publicly.
Eventually, services will be restored, but at that point, you will not be able to rely upon the Web for ANYTHING short of government and corporate approved content. A total Police State will have been achieved, and we will be dealing with the NewStates of America, which will move to form (as enabled by the new Constitution) the North American Union in support of the march to a one-World government, and the Antichrist’s End Game.
Fortunately, we are not there, yet. But they are preparing us for that day, conditioning us daily in our TV news feeds. And to help us get the right message, they use clever visual tricks to go with the information they want us to come away with (and minus that they are unwilling to reveal). That brings us to the most interesting section, in my view…
How does TV dumb us down?
The psyops science behind TV News
A seldom noticed tool for dumbing down is right in front of your eyes when watching modern network (and to a degree, local) news programs. It is the methodology (psyops science) of visual presentation. Compare today’s methods as we examine them to the image at page top from a 1968 newscast. Which one is likely to better insure your attention is focused on the words you hear and the key photos or moving images representing the actual news topic under discussion? The answer MUST be, the old way. A mind’s attention divided against itself by distractions cannot be whole in thought. It’s how accidents happen in the real World. It’s how dumbing down happens in the news world.
First Example: CNN; the sample images are divided into zones for discussion purposes. I have additionally outlined areas in red which represent special effects being applied in unique ways with respect to transparency. When things are transparent, and especially when the background is indiscernible, it allow the subconscious mind to be confused; something solid seems real and factual, that which is nebulous is less real or concrete, and more implied than factual.
Zone 1, a and b parts — is showing a moving graphical pattern promoting the news program, which in this case really is not a news program at all, but a news spin mechanism to take a select news story and make sure you get the official slant in a way that interfaces well with the greater Globalist agenda (i.e., gun control is good, OWS and Internet activists are bad, etc.). You literally see it in her eyes; ‘You have to believe me!’ There is no synchronicity in the movement of the background pattern between the zones, giving your mind a kind of subconscious mental puzzle to resolve… is it the same pattern, or isn’t it?
Zone 2 is also in two parts. The official CNN Logo (b) is animated over a separately animated background (a), to create a mental 3-D puzzle of sorts. An element of the puzzle is that the background is nebulous and hard to grasp, with just enough detail to imply there should be something there recognizable, and yet, just as you think you understand what it is, it is not. There is actually a 3rd unmarked zone I failed to note at first… the blackened rectangle at the lower-right corner. It also contains the same CNN image machinations, but the color has been removed, creating yet another puzzle for the subconscious to resolve.
Zone 3 in two parts — is yet another play on the name of the show, with things in motion. The name scrolls to the left in (a), competing with and drawing your eye away from any other text which appears, and then vanishing with transparency into part (b), which is where they want your attention to go (nothingness). So when the text changes and your eye darts to it (distracts you from the spoken word or other video present), you are additionally distracted subconsciously by the scrolling text adjacent; two tiers of distraction, one distracting you from the other.
Zone 4 in four parts — four different text sections, each able to change for various reasons, which may be synchronous as with a complete change of presentation topic, or asynchronous within a presentation to provide additional timed distractions. The worse offenders would be those texts which scroll endlessly. Your eyes dart back and forth endlessly, unless one thing seems more important momentarily. Regardless, you mind has been divided repeatedly.
What you are left with in most such shows, is no fewer than a half dozen moving images and as many textual elements, all competing for attention to subtly make it less likely that you will remember much more than the most basic of details — such that most Americans STILL TODAY, (of those who favor TV as their news source) are not even aware of the conflicting facts about guns at Sandy Hook, much less any of the other controversies. They simply were unable to absorb the needed level of detail to say “Wait a minute. Yesterday you said one thing, and now you are saying another?” Naturally, they also don’t realize they’ve been fed yet another magic bullet story (several, actually).
Second Example: Univision; every network, indeed, every show, has to have a different ‘skin’ to make it visually identifiable. So a second example gives us a look at other ways to do the same thing within such skin changes. Here we see Zone 1 — a giant moving graphic element in four parts of the screen, all of which employs color cycling to further divide the parts. Color cycling is a psychotic technique which relaxes and subdues the conscious mind. Within it words are alive with motion, another layer of distraction. It is pervasive but cleverly segmented by other elements such that it is as if four separate, but synchronous sections, each competing for attention subconsciously.
Zone 2 in two parts — the primary (a) is the Reporter or first talking head. Multiple talking heads with their own window is a popular skin construct, one which especially becomes a great distractionary tool when you allow each person to speak over the other in heated manner which never seems to let but one side make their point fully… but the viewer, conditioned over time to side with the presenter’s viewpoint, simply sees ‘them winning the argument,’ and not them manipulating the flow of dialog. Else how do you explain ANY popularity for the likes of Torry turned ‘American Pontificator’ Piers Morgan, and the countless talking heads of like ilk?
Part (b) — is supplemental text information for labeling window content, and can change to other information for distractionary purposes. The question is, why is it important to tell us it is the Studio when we know that? Or to name the party just introduced or the newsperson we are used to seeing? We already know these things; they are simply there as a decisive distractionary tool. Every time they change, our eyes and attention are tempted to be diverted.
Zone 3 — in two parts is the second window for alternate video or added talking heads. This reduced viewing area will LIMIT the detail we are allowed in the news presentation. They might allow us the luxury of full screen video for things where they want us to absorb something (i.e., the full scope of violence by protestors), or elect the minimal viewing window when they’d rather we not so easily see something (i.e., police violence). Sure, sometimes it does not matter, and sometimes there may be no deliberate intent inherent in such changes. But the tool is there if they need it.
Zone 4 — is a replay of CNN’s, with an additional 5th part. There is no intrinsic difference in strategy or use. Again we find special effects using transparency along with motion (red outlined area near lower right corner). In this case, text is scrolling which is not quite readable without great effort, the same text (I think) as used in the main background (Zone 1), but scrolling the opposite direction. How distracting is that? It has to be intentional.
Worse, if there is any actual verbal content in all that scrolling background text, it is being absorbed by the subconscious. There is therefore the potential for subliminal programming, an early CIA developed mind control trick — but I do not know it is present, nor can I make such a determination as I do not read Spanish, and the original image is not clear enough to support translation efforts. I would defer to anyone with more direct specific analysis.
So, tell me again, Hillary, Piers, et.al, about Sandy Hook, 9-11, and why you don’t believe there is a conspiracy afoot somewhere in those engineered tragedies, and other controversies which flood the evil Internet? Oh… because people believe what you tell them to believe. I should have known better, since the public all went to school using text books approved by a handful of people in Texas appointed by George Bush to globalist standards… and most other States will not approve books unless the Texas group has first approved them.
Yes, I’m talking about the same people that insured text books sent to Afghani schools a decade before September 11 used pictures of bombs and guns and grenades for counting exercises… just in time to create a generation of terrorists… and then replaced them with pictures of wholesome things once we invaded. How could anyone believe anything else than the official message, given the running start on dumbing down such programming gives them? But you know, that’s yet another news story that’s vanished from the Web, of late, so why do I waste my time arguing with you?
Its the people who think for themselves I’m really concerned with reaching.
Who is winning the information war? YOU — if you pay attention!
Related articles
- The disaster of manufactured consent in the Matrix (usahitman.com)
- Illuminati Mind Control & the Report from Iron Mountain (fromthetrenchesworldreport.com)
Open Letter to United Nations by Red Chinese National
Open Letter of Complaint to the United Nations, by Xin Zhong Qing
Received by H. Michael Sweeney direct via email March 18, 2013
PLEASE REPOST. NO COPYRIGHT NOTICE.
Notes indicated red by H. Michael Sweeney. As you read, unless you are already familiar with political control technology, you will be moved to dismiss the complaint as the rantings of a mentally disturbed individual. While it is certainly possible that is the case, it is also not only possible, but highly probable that the descriptions are true accounts as the victim is best able to relate in conversational English. Please consider such translation issues as well as the following facts before you make any such decision:
1) As testimony to the State of Massachusetts Legislature on a Bill to limit use of electronic weapons reveals, there is NO symptom of schizophrenia (imaginary persecution or other unreal events, realities) which cannot be induced electronically; 2) Therefore, most victims of political control technology seldom have a correct understanding of the exact nature and cause of their targeting, and indeed, specific effort is typically undertaken to insure their beliefs are incorrect (you cannot fight a problem if you fight the wrong cause); 3) As one who has worked with hundreds of such victims around the World, I see select clues within the dialog which align with many similar charges from others within Red China, as well as other countries, including America. I am specifically comparing to cases where, after working with the individuals for a considerable time, tests and defensive strategies verified that targeting was real — though generally different than the victim’s original perceptions and understanding. 4) You will note that many of his prior letters were enjoined by other signers, up to 77 persons. 5) Yesterday, I got four hits to my wordpress pages from Red China (rare). One of the pages hit regarded how easy it is to start a revolution, which featured the 1989 failed Tiananmen Sqaure incident. Another features how to outreach as a targeted individual, my also my main page on political control technology, and another was my contact page. I now believe these were Xin’s visitations. Xin Zhong Qing is a fairly common name in China. There is even a Container Vessel operated by the Red Chinese Army of that name.Letter begins:
United Nations Commission on Human Rights:

Xin Zhong Qing from his social media page, Red China
My name is xin zhong Qing, Is the Chinese Jiangsu province Nanjing city an ordinary law-abiding civilians. Here, I on you accuse China Security Department “secret agencies ” in a group of spies criminals, they abuse “monitoring” privilege, make high-tech “brain control” technique, remote control my body and spirit, the implementation of more than 40 years, The days and nights of continuous uninterrupted secret torture persecution.
In the Chinese Cultural Revolution ” of 1971 , in the 20th century , I was framed for “5.16 counter- revolutionaries “, were subjected to cruel political persecution. This group of ” secretagencies ” in the secret criminals, in order to force me to, admit that they are “5.16 counter-revolutionaries”. At the same time, in order to stop me openly accused Justice voice, they use high-tech ” brain control ” technology means frenzied , day and night, 24 -hour continuous remote control of my body , the implementation of an extremely cruel persecution and assassination plot secretly tormented.
They are a group of secret agents Alcatraz. To me implemented secretly tormented persecution means extremely brutal, shameless, comparable to the German Hitler fascist concentration camp Gestapo and Japan 731 units of bacteria devil evil, their Monstrous evil, just pale into insignificance by comparison!
They control my body, every minute non-stop manufacturing my body, appear all sorts of pain; itching; extreme cold; heat; numb; vertigo; tremble; Extremely uncomfortable; incontinent, frequent cough vomit nasal bleeding paste the nose, as well as the infamous “sexual torture” and other pain. For over 40 years time, wherever I go where, this secret pain never stopped, and I can’t sleep, normal study, work and life, day and night in very suffering pain, like a living dead!
Their Monstrous evil, not only a violation of China’s constitution and laws to “respect and ensure human rights” provisions, also completely violated the Charter of the United Nations and the “Declaration of human rights” and other relevant safeguard basic human life, survival rights provisions.
Therefore, I had to the Communist Party of China and Chinese government post a lot of complaint letters:
• In the December 3, 2007 issued a “President Hu Jintao to collective letter”(the 77 victim joint);
• In May 5, 2008 issued a “Chinese” secret organization “open letter”.(the 43 victim joint);
• In September 7, 2008 issued a “ An Announcement to the Whole World by Chinese Victims”.(the 65 victim joint);
• In March 6, 2009 issued a “Accountability Mr. Geng Huichang, one of the leaders of the national security sector”. (the 76 victim joint);
• In March 15, 2010 issued a “China’s civilian population, in fact, no protection of human rights! ”
• In August 16, 2010 issued a ” Ten Questions “Politics and Law Committee of the CPC Central Committee , Zhou Yongkang, secretary ;
• In January 1, 2011 issued a “To the CPC Politburo Standing Committee member of the open letter to all”;
• In April 5, 2011 issue “urged China’s security sector, Geng huichang and others pleaded guilty to the letter!”;
• In July 15, 2011 issued a “Geng Huichang, is China’s brain control criminal gang black Protectionumbrella!”;
• In February 24, 2012 issue”Notice to all Chinese compatriots Book”;
• In August 4, 2012 issued a ” Accountability Zhou Yongkang, Politics and Law Committee of the CPC Central Committee! ‘”And so on
However , I have sent the Many letter of complaint, not only did not get any reply. On the contrary, the arrogance of this gang of secret agent criminals more arrogant , more intensified secret remote control of my physical and mental torture persecution . I am still in the” shouting days days should not ; shouting ground ground should not” suffered torment pain life..
Now, I tell you — the UN Human Rights Commission issued this complaint letter, urging you under the Charter of the United Nations and the “Declaration of human rights” and other relevant human rights documents, To as a member of the United Nations of China National Security Department “secret organization” this group of Spy against human criminals are a Monstrous evil, Must be a serious investigation , and the findings made public . At the same time , Will referred the case to the United Nations Criminal Court, Will this group of secret Spy criminal prosecution, for crimes against humanity!
The following annex, is my day and night, in more than 40 years of uninterrupted suffered this group of secret Spy criminal on my body remote suffering persecution, daily live record fact evidence excerpts (January 1, 2012 — November 30, 2012) :
Yours lofty salute!
China’s Jiangsu Province , Nanjing “mindcontrol”victims :
ZhongQing Xin
February 28, 2013
Sender: Nanjing victims ZhongQing Xin(screen name Red Master)
Address: Nanjing Xiaguan District # 94-14 Tung Cheng, a village
Tel: 13776686557
Email: njxzq_88@163.com; xdj805187@sina.com;
623962269 @ qq. Com
blog:
Note by H. Michael Sweeney: the first link appears to be being blocked in Red China. Attempts to reply by email also fail.
http://www.mmmca.com/blog_u16348/index.html?skin=painteddesert;
http://user.s6.qzone.qq.com/623962269/main;
致联合国的公开控诉信
联合国人权委员会:

Emblem of Communist Party of China defined in the Party’s Constitution (2002), Article 51. (Photo credit: Wikipedia)
我叫忻中庆,是中国江苏省南京市一个普通守法平民。我在这里向你们控诉中国安全部门“秘密机构”中的一伙特工罪犯,他们滥用手中的“监控”特权,使有高科技“脑控”技术手段,遥控我的身体和精神,实施长达四十多年之久,昼夜不停的秘密折磨迫害。
在上个世纪1971年的中国“文化大革命”中,我被莫须有地诬陷为“5。16分子”,遭到了残酷的政治迫害。这伙“秘密机构”中的特工罪犯,为了迫使我就范,承认自己是“5。16分子”。同时,为了捂住我进行公开揭露控诉抗争的正义声音,丧心病狂地使用高科技“ 脑控” 技术手段,昼夜24小时不停地遥控我身体,对我实施令人发指的秘密折磨迫害和阴谋暗害。
他们是一伙秘密特务恶魔。对我实施秘密折磨迫害的手段极其残忍、无耻,堪比德国希特勒法西斯集中营的盖世太保和日本731细菌部队魔鬼的罪恶,是有过之而无不及!
他们遥控我的身体,分秒不停的制造我体内各个部位,出现各种剧痛;奇痒;极冷;极热;麻木;眩晕;颤抖;极度难受;大小便失禁,鼻腔内频频咳吐出血糊状鼻涕,以及无耻的“性折磨”等痛苦。在长达四十多年之久的时间中,不管我去住何处何地,这种秘密折磨痛苦从没有停止过,致使我根本无法正常学习、睡眠、工作和生活,日夜在无比煎熬痛苦中,犹如一个活着的死人!
他们的罪恶,不仅完全违反了中国宪法和法律“尊重和保障人权”的规定,也完全违反了联合国宪章和“人权宣言”等有关维护人类基本生活、生存权利的规定。
为此,我曾向中共及中国政府书写并投寄了大量的控诉信。如:在2007年12月3日发出了《致胡锦涛主席的集体控诉信》(77位受害者联名);在2008年5月5日,发出了《致中国“秘密机构”头头的公开信》(43位受害者联名);在2008年9月7日发出了《中国受害者告全世界人民书》(65位受害者联名);在2009年3月6日发出了《问责国家安全部门领导之一耿惠昌!》的控告书(76位受害者联名);在2010年3月15日发出了《中国平民百姓,实际上根本没人权保障!》——中国“脑控”受害者的“公民人权黄(网)皮书”;在2010年8月16日发出了《“十问”中共中央“政法委”书记周永康》;在2011年1月1日发出了《致中共中央政治局全体常委的公开信》;在2011年4月5日发了了《敦促中国安全部门耿惠昌等认罪书》;在2011年7月15日,发出了《耿惠昌,是中国“脑控”犯罪团伙的黑保护伞!》;在2012年2月24日发出了《告全体中国同胞书》;在2012年8月4日发出了《责问周永康!》等。
然而,我发出的这些控诉信不仅没有得到任何回音。相反,这伙秘密特工罪犯的气焰更加嚣张,对我的身体和精神的秘密遥控折磨迫害更加变本加厉。我依然在“呼天天不应,呼地地不灵”的煎熬中痛苦生活。
现在,我向你们——联合国人权委员会发出这封控诉信,强烈要求你们根据联合国宪章和《人权宣言》等有关维护人权的文件规定,对作为联合国成员国的中国国家安全部门内“秘密机构“中的这伙特工罪犯的反人类滔天罪行,进行认真调查,并将调查结果公布于众。同时,将此案移交联合国刑事法院,对这伙秘密特工罪犯,进行反人类罪公诉!
下面的附件,是我在四十多年中,日夜不间断遭受这伙秘密特工罪犯对我身体遥控折磨迫害,每天进行实况纪录的事实罪证部分摘录:(2012年1月1日——2012年11月30日)
顺致崇高敬礼!
中国江苏省南京市受害者:忻中庆
Fiction of Future Fact? 23 Families Jailed, Loose Their Homes in Weekend Raid
Is it mere fiction (from book, Fatal Rebirth), or your future reality? Don’t be so sure you know the answer, because smaller scale events like it have already happened.
What will happen if martial law is declared?
by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included.
Actual MJTF suburban raid. The crime? Selling unpasturized milk through a Farm Coop, an Agenda 21 crime established as result of United Nations and Globalist mandates through Bush/Clinton/Obama admins.
From Fatal Rebirth, by this author; proparanoidpress: a fictional account of crimes of the New World Order from 1947 into the future, with over 1,500 footnotes so you may decide how much of it really is fiction, vs. reality in play. Based on the Unified Conspiracy Theory developed in a ten-year research for the book, it has correctly predicted political assassination efforts to effect control of the US election process, the downing of the WTC by passenger jets and resulting Middle East oil wars, and more. It also led to the author’s direct intervention in and prevention of one, and possibly two terror attacks on Portland, Oregon.
A FREE copy of the ebook (Vol. I of four volumes) is available for the asking. For more information, special pricing, go here. Why are Bloods and Crips Gang members being given Police badges?23 Families Jailed, Loose Their Homes in Weekend Raids
A local news clipping (a sub chapter in Fatal Rebirth, Vol. III)
Police struck another blow against continued political and social unrest this weekend when they arrested 31 adults and took another 58 men, women, and children into protective custody in a series of surprise predawn raids ordered by Homeland Security. The actions were part of a continuing series of such raids across the nation undertaken in increasing numbers under authority of blanket bench warrants issued by the new FEMA Court System, a concept adapted from and empowered by provisions of the Patriot Acts and subsequent legislations.
The Multi Jurisdictional Task Force (MJTF) raids regularly involve elements of the National Guard, State, County, and local Police, and special Community Active in Policing Services (CAPS) deputized citizens as well as the usual Federal advisors, undercover operatives, and observers from DHS, FEMA, FINCEN, FBI, DEA, DIA, BATF, IRS, CIA, and numerous unidentified agencies.
Each Agency representative determines if arrestees were in violation of pertinent Federal laws or if there is any reason to suspect militia or terrorists activity or support. This time, the blanket bench warrants were served on the Corbin neighborhood where some 600 homes were searched Saturday and Sunday after roadblocks cordoned the area. There was little formal resistance from most law-abiding citizens, many of whom were given temporary shelter from the cold in the several motor homes set up for preliminary resident interviews. Coffee and hot chocolate was served by representatives of the Red Cross, who also provided blankets to those insisting on watching their homes being searched from the sidewalks.
However, gunfire punctuated several intense confrontations between agents and a few persons believed to be criminals or underground members of or sympathizers with the Constitutional Army of Repatriotization (CAR). However, these resulted in only minor casualties on both sides, and the Cobra gunship helicopters and heavy-machine-gun-mounted vehicles were not called into play as have been reported the case several times earlier this week in Detroit.
The statistics locally to date since declaration of Martial Law three weeks ago now stands at least 115 dead and 321 hospitalized, 7 of those injuries and two deaths being CAPS members and one DEA officer injured. At least 1,890 persons have been detained for questioning or actually arrested. The majority of deaths and detentions of non Islamics are attributed to armed resistors, presumably militia or criminal elements or supporters, or discoveries of significant contraband. Readers are reminded that possession of antigovernment literature is grounds for detention and questioning about loyalties and activities. The bulk of detainees are, however, apparently of Middle East origin, though no precise numbers are available.
Agencies conducting the raid were looking for weapons not already turned in during the amnesty period earlier this year, as well as illicit drugs, hoarding of food and fuels, proper travel documents and proof of citizenship, extremist and cultist materials, pornography and other contraband. Most of those taken into custody were taken immediately by helicopter to unspecified out-of-state Federal facilities for interrogation and possible ongoing detention.
Under recent revisions in the law in support of Martial Law, any charges resulting from the raids will be submitted to the temporary FEMA/FINCEN Court system operated under the US Army’s Judge Advocate system (military tribunal) for summary convictions instead of wasting time and money with the traditional drawn-out trial processes. If ruled guilty, their homes, vehicles, and personal properties will become the property of the State under forfeiture laws, with some of the goods to be distributed to the CAPS program managers for community enhancement. Most trials are in absentia with the defendants participating only by affidavit.
Elsewhere, Stevie Wilson, former member of the Bloods gang and acting spokesperson for the CAPS program described the raid as “rewarding in many ways,” and thanked the Police for giving them greater latitude in conducting searches… “It’s a lot easier for us to find contraband now that we don’t have all the procedural red tape that forced the Cops to oversee our every action directly.” Police discounted the usual charges made by those arrested that the former gang members had planted evidence and were only interested in confiscating goods they themselves would get to keep… “These charges are easy to make, but hard to prove. They can’t get out of it that easily.” offered an unnamed law enforcement official who, like many of the special agents, needed to protect his identity by wearing a black Ninja-style hood.
In a related matter, Mrs. Ira Johnson, wife of well-known newscaster Dave Johnson, has formed a new organization of housewives whose purpose is to help the progress of the searches proceed as smoothly as possible. The organization, called WELCOME, will urge all housewives to make their homes as easy to search as possible by using as much table space and floor space beneath tables and adjacent to furniture as may be possible to array items from within drawers and boxes, especially breakables, important papers, and valuables, to prevent damage and reduce cleanup afterwards. These steps, as well as placing the empty drawers on edge against the wall will dramatically speed search process. The organization also advises wives to urge their husbands to destroy objectionable and illegal materials in advance of searches for the sake and safety of the whole family, and to avoid embarrassing questions. See related story on page 6, Objectionable Materials List Broadened to Include Many Men’s Magazines. Raids will continue unannounced for several months until all areas have been searched at least once according to a FINCEN press release. At that time a special panel will convene to determine if further searches or other measures may be necessary.
Related articles
- SWAT: Is America Coming Under Martial Law? (jonathanturley.org)
- ACLU Launches Nationwide Police Militarization Investigation (jhaines6.wordpress.com)
- Department of Homeland Security Raids Gun Collector Who Didn’t Violate the Law (thedailysheeple.com)
1776 2.0 Cometh: What Price Treason, and Who Pays?
Gun Control Laws and other Constitutional/Bill of Rights erosions by government are TREASON. Ultimately, YOU decide who is going to pay, and how.
1776 2.0 Cometh by H. Michael Sweeney copyright © 2013, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this paragraph, are included. Compare 1776 to 2012 and tell me where you liveWhat is the price of treason, and who pays?
Historically, the price of Treason can be unbearably high. If caught and convicted, the price can be as high as death, typically by hanging or by firing squad. In time of war, especially, and if that war be a revolution to throw off a tyranny born of such treason, the death penalty is more oft employed. Therefore, only a fool undertakes treason lightly; those who accept such risk must have great personal gains as their motive, else why the gamble?
But the cost is also high if such tyranny is not overthrown. If one is subservient to it without protest, or resistance is beaten down by it, the cost is loss of all Freedom, and often, again… the loss of life itself. For when government gives unto itself absolute power, it is corrupted absolutely, and free to deem any person at will as unworthy of life simply because they are seen as an inconvenience to whatever drives their tyrannical agenda. Yes. An example is called for:
Today, the person acting as President, through the NDAA Act, has, in conspiracy with those who voted for the Bill, usurped the power to take life and liberty with just a word; the tyrannical power of a 12th century King. When any one man establishes by manipulative means the power of life and death over fellow men in deference to all existing law, it is a crime. Treason.
Alex Jones was right, gun control means 1776 all over again
A line in the sand: when is 1776, 2.0?
 SOON, thanks to the push for gun control, when each of us must decide if we are subservient and wiling to be the ones to pay the price by giving up our rights as well as the means to insure them… or if we will instead assert our rights and throw off the yoke of fascist rule of the New World Order by defending our guns in resolute defiance BY RULE OF LAW; the Constitution’s Second Amendment. That’s what it is there, for — it is not there for Duck hunting rights. It is that we might always have available Minutemen, and all who are able ought serve.
SOON, thanks to the push for gun control, when each of us must decide if we are subservient and wiling to be the ones to pay the price by giving up our rights as well as the means to insure them… or if we will instead assert our rights and throw off the yoke of fascist rule of the New World Order by defending our guns in resolute defiance BY RULE OF LAW; the Constitution’s Second Amendment. That’s what it is there, for — it is not there for Duck hunting rights. It is that we might always have available Minutemen, and all who are able ought serve.
Heed my words, for I have been warning of this moment in time for more than ten years, starting with my bookset, Fatal Rebirth.
Note: Fatal Rebirth predicted Sept. 11 events in sponsorship of Middle East wars for oil. It predicted assassination plots against Ross Perot to kill the third party movement (indeed, mailed anthrax attack on his family would cause him to withdraw from the election the very night he would have won a place on the ballot and legitimized a third Populist political party). It predicted many things, including a series of mass shootings to enable gun control legislation. It also predicted the next wave of terror attacks, including likely locations and methods, as false flag ruse to declare Martial Law, suspend the Constitution, and go door-to-door to collect ‘contraband’ and discover ‘terrorists’ (after our guns, mostly). But it also predicted how to resist and overcome such tactics, with specific advice to the Militia and others wishing to resist. You can get a free copy of volume I ebook by email to pppress at century link net.I’ve written many posts about the coming moment, too, best described as that critical moment when each of us must decide if a line in the sand has been crossed which cannot be tolerated. Some of these posts are listed below, others are linked within this text. In one, I put it this way: government plays Russian Roulette and puts a gun to their head every time they undertake an oppressive or unconstitutional act, and pulls the trigger at its signing into law.
Eventually, they will go too far, and it will be yet another shot heard around the World; 1776, once more. It is, after all, how revolutions are started. An attempt to seize and restrict gun ownership is that line in the sand which must not be crossed, even at risk of escalation to armed rebellion. It guarantees not just one shot, but many, many, many more immediately thereafter. Only a fool would fail to realize that if any such revolution comes, those who are deemed as traitors will find it was as if there was a de facto bounty upon their head.
And from the very beginning, at the time the Constitution was penned, and the Amendments thereof brought into being, Thomas Jefferson and his patriot fellows warned this would be so: “The beauty of the second amendment is that it will not be needed until they try to take it.”
That Jeffersonian comment underscores the reason for its existence, which has NOTHING to do with the right to hunt or protect us from criminals, but everything to do with being able to protect us from government run amok. Our government runs AMOK, NOW, and has for some time. Shame on YOU for allowing it to go this far! Shame on me and you if we do not at last toe that line in the sand, standing firmly, side by side.
Are mass shootings simply false flag operations to take guns?
Let us be clear: what defines treason?

Treason defined on the fly by Mobs: Fascist Government Leaders (including Police officials) hung by the mobs when Mussolini was overthrown
Those in power define the answer, the wording of law not withstanding. I am likely now, or soon to be, like all dissenters, activists, and Constitutionalists, gun owners, and the like, as a single class targeted by a fascist coupe marching toward their New World Order, to be declared guilty of treason for daring to write these words. That’s the way Fascism works, and why no one is safe when it rules. But should 1776 revisit, and the People and Constitution win, WE will be the ones who define Treason. Here is my view of what that definition should be:
a) It is treason to swear an oath to uphold the Constitution while at the same time being a member of a New World Order institution which has their own oath to give up sovereignty in favor of a unified World government (which, ultimately, enables seating of the Antichrist). Therefore, a long list of governmentals are de facto traitors by virtue of lying when they gave their oath of office — while being members of the Tri-Lateral Commission, the Bilderbergers, the Council on Foreign Relations, Skull and Bones, or being a Rhodes Scholar, or similar.
These groups all require agreement to such contrary oaths or with stated globalist agenda, all of which is nothing less than rewording which conforms with the Illuminati formula for World domination, for which it was they who coined the term, New World Order. It is, today, very hard to find a Congressmen or other governmental who is not such a traitor, and the remainder look upon such groups as if wiser than their own ability to think for themselves, even to the point of accepting and acting upon their Globalist ‘reports’ as if Congressional findings. Treason.
b) It is treason to knowingly propose and vote for, and sign a Bill into law which is unconstitutional, or any Bill you have NOT READ and debated properly. Any act to subvert the Constitution, be it willful or by negligence, justifies the charge of treason, and let the defendant prove otherwise. Given that all such persons are educated in the law as a rule, one may safely presume there are no fools unaware of the significance, and the due seriousness with which their duties under their oaths of Office require of them to be diligent.
They undertook such acts at their own peril, and in full awareness of the responsibility to take care. So be it, when it comes time to answer for it. The list of such Bills is long, and many shall be held accountable. In fact, I can only think of two or three Congressionals who may be completely innocent, but there may, hopefully, be others. If not, perhaps the time for revolution is now.
c) To the point, here and now, today: ALL governmentals who support gun control laws which take away the right of the citizen to own military grade weapons are guilty of Treason. The Dick Act of 1902 made clear that the UNREGULATED MILITIA (that’s ANY citizen with a gun who stands to serve) shall NOT be denied the right to have military grade weapons. And yet, Congress has subverted this law time and again, by clever rewording of definitions, and the trickery of ‘dual oaths’ of service.
Therefore, all prior gun control laws which so inhibit access, or which create registration lists, are de facto null and void, and treasonous. Any attempt to collect weapons against the wishes of owners constitutes theft of private property on the one hand, and an attempted coupe on the other (treason), as does any attempt to prohibit or limit access, or to ‘register,’ anything with a Federal agency.
Personally, I want my own SAM and Apache gunship, thank you. I want all gun control laws repealed. The only law which I would approve is that to purchase a weapon, you would need be an adult of sound mind, and with no criminal record, to be determined by a blanket background check where the purpose of application was unstated, but authorized by the person being checked, as all background checks should be. I only registration process should be to register guns, not owners: a registration process managed by the States which collects sample slugs from fired guns from sellers (the Registrars) for forensic comparisons in criminal matters. The State would not know who owned the gun, but if used in a crime, could obtain a warrant to get that information from the seller of the weapon. I further want colleges to offer firearms safety training courses as an alternative to ROTC, and as part of ROTC. I want every State to have at least one citizen militia not subject to State control, and I want the State to provide them with access to military training facilities and expertise. I want every citizen who is qualified to own to be able to open carry or conceal carry. In short, I want to reduce the likelihood of criminal use of guns by means of practical and immediate (real and clearly visible) deterrence. There are clearly other topics to be decided by law, such as matters of keeping guns away from unsupervised access by children, but I’m not taking up more space, here and now to totally define my views. If you want full details of how such a law could work, please request it directly and it will be made available by email.d) All governmentals who supported NDAA are guilty of treason as well, for that law not only strips away whole sections of the Constitution, it even defeats the Magna Carta and gives the President the power of a 12th Century King to put citizens to death by mere say so (or torture or imprison them indefinitely without trial or evidence). Is that why DHS ordered 9,000,000 sniper rounds not for military use? That’s about how many dissidents there are in this country with a loud voice, such as myself, if I may be so bold.
e) All governmentals who support the DOD sending National Guard troops to war overseas without an Act of War and Congressional declaration of War are guilty of Treason. The Dick Act, again clearly denies the President or anyone else the power to order National Guard to active duty in any other fashion. They are NOT part of the regular Army subject to DOD. We have been fools to not be aware and hold both our STATE and Federal representatives accountable under the law their wiser forefathers set for them to follow.
f) All governmentals who support the endless spying and abuse of privacy of citizens at large in the name of fighting terrorism are guilty of treason, as are those involved in seeking the development and deployment of Political Control Technology (PCT) in like guise. Not only do they, and the 30,000 drones they want to put into our skies erode Constitutional rights and safeguards long cherished under the law, they make such protections meaningless. The very nature of PCT reveals their lust for totalitarian control.
Worse, they these things are a sham: they are not there because government fears a few thousand terrorists, but because government fears 360 million citizens, which is its RIGHTFUL state; the government is there to serve us at our pleasure, and be vanquished at our displeasure, not there to rule us at theirs, and subject to suffering their displeasure. Treason.
g) Any governmental who writes a law is also subject to the law, and thus any who violate the law and evade punishment by virtue of their power of office are guilty of treason. A government which violates its own law, as ours is so often guilty of doing, has no right to demand we obey their laws, doubly so when oppressive and unconstitutional. And doubly again when the person signing them into law cannot even prove citizenship to the simplest of standards. Such people make of The Law, something less, ‘the law,’ a mockery of no value whatsoever. I refuse to obey the law, but accept and follow only the Law of the Land (The Constitution)!
And let us not forget their oft cited caveat: we have recourse through the courts if we think a law unconstitutional. What recourse is that, really? When it can take a decade to work a suit through to the Supreme Court and cost millions of dollars, there is no recourse of practical meaning. When they can write new unconstitutional laws of like purpose ten times faster than we can negate an old one, there is is no recourse which excuses their writing them, and act of pure lust for power. Treason.
h) Media should never be allowed to be under control of the military-industrial-intelligence complex. It is so much under control, today, that I term it the Military-Industrial-Intelligence-Media (MIIM) Complex. When CIA puts thousands of operatives into media… when the top three TV networks are owned by military contractors (during the Flight 800 time frame, they were)… when a newspaper publishes the names of all gun owners and deliberately places their family, homes and the guns in danger… when ‘unafraid’ and ‘fair and balanced’ means ‘the truth is whatever government and globalists say happened, facts be damned,’ then those involved are guilty of Treason.
This list could be (should be) longer, but this is a blog and people don’t like them to be too long. So if they come for the guns and shooting breaks out, heaven help virtually any governmental captured, should the Constitutionalists and Patriots win out over ‘the law.’ So. Congress, and Mr. Obama, usurper King… spin the cylinder, put the gun to your head, and pull the trigger by signing that Bill. Let’s see who pays, and what the price shall be.
You know where I live, and many more like me. You have lists of gun owners through previously written gun laws which should never have been allowed. But every citizen knows where all of you are, too. You don’t have enough Men in Black to get the 9 million activists before the rest of us come after you in numbers you can’t stop. You certainly don’t have enough to go after all 300,000,000 guns we possess… or is that why DHS also ordered 4.2 billion rounds or regular bullets?
What will you do when they come to your door to search for guns?
Who controls gun rights?
It is not lawmakers in Washington, D.C., who write illegal (unconstitutional laws) on purpose. They control only their own fascist rhetoric. The framers of the Constitution, and that document, are the ONLY authority we need obey. Even if you do not own a gun, the weapon Washington fears is in your hands; they fear a united WE, the PEOPLE.
Ergo; to lawmakers and other power usurpers and their minions of enforcers who disobey their oaths of office: I dare you to try to take that weapon from our hands. Bring on 1776 2.0, if you must. Clint said it best. “Do you feel lucky, Punk?”
Well, do you, Punk?
Note: the current proposed (Fascist Feinstein) gun law (clear analysis, here), will essentially force gun owners to give up the bulk of all pistols, rifles, and shotguns in a manner not unlike already undertaken in Australia. Those efforts resulted in a huge spike in gun violence as criminals were given a blank check knowing no citizen was protected by the likes of Mr. Smith and Wesson. We lost what? Well under 100 lives this last year to gun violence of the type the legislation claims to be defeating? Australia lost 93,000 lives to gun violence after confiscation, and their population is a mere fraction of our own. Yeah. Gun control works. It works for fascists and criminals (same thing, different levels of prowess and evil goals). Do not obey illegal laws. Challenge authority. Stand on your rights.Related articles by me
- On Being Prepared for Martial Law or Revolution
- Portending Martial Law: Three Facts That Put You at Risk
- Raw Numbers Prove DHS Gearing Up For Martial Law, Revolution, or Chinese Invasion
- Compare 1776 to 2012 and Tell Me Where You THINK You Live…
- Statistics Prove Gun Control is No Solution; Gun Violence is a Political Ruse
- Mind-Controlled Mass Shootings Don’t Change My Mind
Related articles by others
- Petition to charge Sen. Feinstein with treason soars past White House threshold (rawstory.com)
- Gun control: The right to commit treason (richarddawkins.net)
- Gilberton Police Chief: Disarming Americans is Treason (sgtreport.com)
- No, ma’am (ireport.cnn.com) INCLUDES CNN’s inappropriate anti-gun commentary effort to defeat the impact of this Marine’s letter.
Collateral Damage: A Web Experiment in Which You Judge and Impact Social Policy
Should a line be drawn? When the claimed benefit is thought to outweigh concern for deaths of innocents, what is the difference between a nuclear strike against a city and using a drone or a car bomb to kill everyone in a car where only one person was the target?
By H. Michael Sweeney, copyright © 2013, all rights reserved, proparanoid.wordpress.com Permission to duplicate online hereby granted provided it is reproduced in full with all links and text colors in tact and unaltered, including this notice.When is collateral damage acceptable?
Is collateral damage ever acceptable?
With Obama ordering 30,000 Drones into American skies, and the military regularly conducting raids against American cities, and Police shooting at anyone on two feet to get one Cop Killer in California… we should perhaps come to a clear and concise understanding of what constitutes acceptable collateral damage, if anything at all. Perhaps “Thou shalt not kill,” is all we need to know. But…
If you could save 100 lives by killing one innocent person, would you elect their execution? If the only way you could prevent a Sept. 11 style attack threatening thousands was by shooting down a hijacked jetliner, would you so elect? Would you order someone sniped because of a significant chance they were about to kill the President, with no way to prevent it otherwise, but also no way to know for certain if they were the right person because all you had was circumstantial evidence? Where do you, personally, draw the line?
We hear those two words more and more in our news, even when there is no actual war going on. Drone diplomacy and policing has turned the taking of life into a video game, where decisions about who lives and dies is frequently being decided by a stranger in a darkened room half-way around the World. Murder is still murder, is it not? Or is it? What madness is this, that anyone ever has the authority for reasons of political expediency to decide life-or-death fate of innocent persons? Or is it silliness to even dare ask?
If a murderer deliberately sets out to kill you, or any person sets into motion events which accidentally kill you, that’s God’s domain to decide. His Will be done. But if your government or another wants to kill you simply to insure that someone else dies, or to insure some important political outcome for which you are not involved with or perhaps even aware of, who decides if the reason is good enough? I doubt they ask God before they sign off on the act. But what if YOU were the one to decide?
The answer is not simple, of course. For instance, for each unintended casualty, the blowback can be quite damaging and unexpected. Each becomes a martyred victim of US Imperialism (or something similar, depending on the target, of course) and literally strengthens the enemy. Governments and media in all nations involved, including our own, tend to roast (the President, or whomever) over a slow fire; it weakens relations with allies and foes alike internationally, and erodes political integrity at home. Collateral Damage can end up being to a tactical mission and the politics and politicians behind the mission the same as a total crash and burn, the burn often worse than the evil being attacked in the first place.
Is it OK to kill an innocent person if it will save the lives of many other people?
Where would you draw the line?
The answer may indeed be yours to decide — by means of the simple poll herein, which you are invited to use, which may very well give us a public concensus which can be used to help shape public policy by agencies, and the military, and those who empower them and wield them as political tools. Results of the poll may spark more officious study or even be cited directly in activist and legislative quarters. But only if you participate will it have such value. Answers are anonymous, and not traceable to individuals.
Lets look at a few examples in history which will give you practice for the Poll.
Deliberately sinking a passenger liner: During WWI the passenger steamship RMS Lusitania was headed for England from New York with nearly 2,000 souls on board. Two people decided its fate, but ultimately, one was responsible, correctly predicting the other’s response to their provocation.
A torpedo was fired by a U-Boat, sinking the luxury liner, a horrific event which turned the tide of public and Congressional opinion in the United States and brought America into the war; nearly 10% of the 1,198 persons who died were Americans, many of them prominent. Who was really to blame?
It was not the U-Boat Captain, because the German High Command had already given the order that the Lusitania, if sighted, was to be considered a combatant because intelligence had revealed it was carrying munitions for England acquired from America, a violation of international law. This decision weighed 2,000 against the loss of life such munitions would inflict upon the German Army to the detriment of their war effort. But their decision it is not the one you are asked to judge.
Some other, unknown person, an American, also made a decision. Not just to illegally put munitions on a passenger ship without informing the steamship company, who would have objected and refused. No, that was by far a more innocent decision. The real decision that we are asking you to judge is this: that person also decided to deliberately allow the Germans to learn of the munition shipment specifically in hopes that they would dare sink the Liner, because that person, and their counsel, wanted the United States to go to war for political expedience.
Would you deem the Lusitania’s passengers as acceptible collateral damage for such a ‘noble political aim’ as rescuing Europe from domination by Germany, the argument they relied upon in their decision? Would it help to know that among those counseling for the move were shareholders and Board Members in the Powder Industry, makers of weapons and munitions?
This later aspect, the Powder Industry, highlights the importance of questioning such decisions. Often the decision makers have ulterior motives which are not part of the official consideration, or justification. The Military-Industrial-Intelligence-Media Complex, and the New World Order crowd (often one and the same people), are more often than not the decision makers. So choose wisely, your answers.
Dropping the Atomic Bomb: In WWII we decided to use the Atom bomb to try to force Japan to surrender. While the US Government was unwilling to cite the true facts and figures used in their decision, the argument to bomb was simple: using the bomb could speed the end of the war and save more lives on both sides than would be lost by dropping the bomb. Just like the Germans and the Lusitania.
President Truman rightly saw no difference in terms of moral choice between Atomics and fire bombing, already authorized in the bombing of Dresden, a like horrific act of war against civilian populations. Of course, we were also regularly firebombing Japan, a nation where homes were literally made of paper, burning to death up to 100,000 civilians in a single city. Indeed, we might should be arguing the bombing of any city by any kind of bomb should undergo the same scrutiny. But we need to focus on a singular incident.
In excusing the use of Atomic weapons, the military claimed they had at the time estimated it would save 500,000 to 1,000,000 lives of US military, and 1.7 to 4 million Japanese by avoiding invasion. We now know that the actual estimates were far less than the propoganda those larger numbers represent, numbers which continue to be used even today.
In like manner, the number of deaths predicted for the Japanese were minimized beyond reality. It was argued that by dropping warning leaflets ahead of the attack, citizens could be evacuated and limit their losses to mere tens of thousands, refusing the advice that such leaflets would be ignored as a scare tactic, which was indeed the case. Very few people fled the cities as result; most who could flee had already done so when non atomic bombing started taking its toll.
In all, more than a quarter million Japanese perished because of the two bombs dropped (it originally being argued a single bomb would do the job). The actual number of American lives estimated to have been saved from invasion was 60-190,000, and perhaps twice that number of Japanese. So let us presume the estimated loss by bombing was only 50,000 Japanese, and that it would save up to 200,000 combatants on each side by conventional invasion (50K vs. 400K). What would your decision be?
When the actual loss of life was later known, how would you feel? I think I would feel like confessing and suicide. Indeed, our first Secretary of Defense, James Forestall, who was one of the decision makers, may have taken that path, or he may have been assassinated for threatening to do so. He, or someone, put a cord around his neck before his body left the second story room via a window… in a government detention facility with barred windows, where he was being kept against his will after walking off the job without explanation.
Lets reduce the scale a bit — are Janitors acceptable collateral damage? Based on a real-World decision to bomb Lybia in retaliation for terrorist attacks backed by the Lybian government… dialog in the screenplay The American President (title role played by Michael Douglas) detailed what is thought to have been part of the actual decision making process by Presidents Reagan and, later, GW Bush… though in fact, the terrorism itself was seen by many as reprisal for attempts to kill Muammar Gaddafi already undertaken by America. I doubt the dialog took place in real life, but let’s use it, anyway…
The President (Shepard) is having a late-night emergency dialog with military and staff about the decision to order a B-1 Bomber attack in a ‘retaliation’ scenario. He is under intense political pressure by the other Party in a hotly contested bid for reelection against a man named Rumson (a ‘Defense Hawk’ rather a lot like Donald Rumsfeld), Shepard’s lack of military experience and seeming timidity in the face of affronts by other nations and terrorism being used against him. Keep in mind, that a large building would not have a single janitor, but a team of many, as well as the likelihood of citizens at large being on the streets nearby:
A.J.
Robin, as soon as our planes have cleared Libyan airspace, you can call the press…
LEWIS
General Rork says around O-Eight Hundred.
ROBIN
Sir, what do you think about a national address?
SHEPHERD
The last thing I want to do is put the Lybians center stage.
KODAK
I think it’s a great idea, sir. You know Rumson’s gonna be talking about your lack of military service.
SHEPHERD
This isn’t about Rumson. What I did tonight was not about political gain.
KODAK
But it can be, sir. What you did tonight was very presidential.
SHEPHERD
Leon, somewhere in Libya right now there’s a janitor working the night shift at the Libyan Intelligence Headquarters. He’s going about his job ’cause he has no idea that in about an hour he’s gonna die in a massive explosion. He’s just going about his job ’cause he has no idea that an hour ago I gave an order to have him killed. You just saw me do the least presidential thing I do.
So what would your verdict be? Would the international strategic political value of such an attack justify the collateral damage of a few janitors? On the assumption you genuinely feared the opposition would take America into an unwise war for the benefit of the military-industrial complex if they won the election, would the political gains at the voting booth change your answer?
Final example: Drone attack. It happens more than we hear about in media. I highly urge you to watch the Matt Damon/George Clooney film, Syriana (sorry for the multiple film references, but such things are part of media’s overall impact on our belief structures, and often the best ways of illustrating visually a gritty reality otherwise limited to mere words). Syriana is an insightful look at the intrigues of Middle East politics and oil-industry machinations rarely gained from the headlines. It also shows you exactly how a Drone attack is carried out in terms of command and control. But you need not see the film, or read the non fiction book it was based upon, See No Evil, by Robert Baer.
The question is, a CIA informant has provided fast-breaking intelligence that a known terrorist has, by unusual circumstances, been spotted hitchhiking and picked up by a car now driving along a deserted roadway in the desert. Presume there is a terror plot in works that will take perhaps hundreds of lives if you do not find a way to stop him. But it is also known that the other occupants, the driver, a woman and a child, do not know who their passenger is. Do you order a Drone to strike, or do you pass for a better opportunity, which are few and far between?
These are hard questions our leaders face all-too often. They do what they think is right for you, perhaps at times for political gain or for corporate profits, but always doing so in your name regardless of reason. So let’s take the poll, and see what you think should or should not be done in your name.
Poll on collateral damage
The Polls
Poll assumptions: Assume you are Commander in Chief or some other person for whom the decision is yours and yours alone. You’ve already asked advice, but it was 50-50 in weight results, and of no help, or there is no one to ask. The answers are incremental in nature, and as it is multiple choice, you only get one answer — each prior answer is considered inclusive in subsequent answers.
You should take the poll before finishing this article, because the remainder of the article might change your answers in the first section. Part of the experiment is to gauge just that: did additional considerations change your answer, as covered later.
But remember: how you answer about the value of the lives of others may impact how government thinks about the value of your life, or a loved one. A casual answer could be costly, considering the 30,000 Drones, military raids on American Cities, and trigger happy Cops in many American cities.
Now that you’ve taken the first section. Lets ask the question in two more case studies. Bear in mind this time, however, how you’ve already answered on the Poll. That means you will need to weigh your answer to the following questions based on decisions you’ve already made. Its about body count, and justification. The context will be different, but it should not change your answers if your logic remains true to form.
The first regarding the Death Penalty for capital crime. We know for a fact that some percentage of persons sent to Death Row turn out to be innocent, in the end. Shockingly, there are at least 39 instances where there was overwhelming evidence of innocence but the stay of execution was refused out of fear it would cause turmoil or harm to the general function of the courts and penal system. For example, a single incident might force the verdict in hundreds of cases to be thrown out and require new trials. Is that acceptable collateral damage, or should the death penalty simply be abolished and the system be forced to clean up its own mistakes?
Take that same reasoning, now, and apply it to NDAA, the National Defense Authorization Act, which gives the President and Military the power and authority to assassinate any American merely suspected of being involved in terrorism (or simply kidnap and vanish and/or torture them). No due process. No trial. Is there any difference in the likelihood of collateral damage being present in such an act as there is in the Death Penalty scenario? That, too, is being done in your name.
Is it acceptable collateral damage to execute a death row prisoner who is really innocent?
The second is more complex. It will require you to suspend your current belief structure and to take on the mindset of someone quite different than you (hopefully). If you were of a political mindset that truly believed that the only good future course for the World was a one-World government… and understood that the only way such a government could exist was if, among other things, the United States, Mexico, and Canada formed the North American Union… and that the only way to establish that was to stage a military coup and suspend the Constitution that it could be replaced with a new Constitution which enables the NAU. Consider further that you believe (correctly), that the 2nd Amendment makes the outcome of such a coup highly unpredictable.
Note: the Constitution of the NewStates of America has already been written, as reproduced with analysis as such a document in my bookset, Fatal Rebirth. Please see special offer on free copy of Volume I by email.
If you believed the above to be true, and you believed that if there a one-World government was not established, dire consequences such as World-wide famine and wars over shortages of oil and food would result costing billions of lives (the kinds of arguments sometimes used to recruit for Globalists agenda)… and given HOW YOU RESPONDED TO THE POLL, could you justify in your mind a given number of innocent lives to help insure repeal of the 2nd Amendment?
Would you be willing, for instance, to authorize staging mass shootings to heat up the gun control debate, knowing that eventually, it would force a confrontation with gun owners and result in Martial Law, etc.? Would it be better to kill a few hundred people to save billions, or not? Would it matter if whole bunches of them were school kids, or wouldn’t it make it better for the purpose? Regardless of your own personal answer, look at the Poll results to see how others voted.
If just ONE person voted in the first section in a manner which implies they might also decide in favor of collateral damage in this matter, then does that change how you view of conspiracy theories regarding Comumbine, Aurora, Sandy Hook, and the many other mass shootings where such charges have been levied by critics? Does it change your previous opinion as to the likelihood or possibility that such a conspiracy might exist?
Is a false flag event ever excused as acceptable collateral damage?
How can collateral damage be anything but murder?
Summary commentary
Just asking? Just saying? No. It’s more important than curiosity, or what I believe is true. As a nation, we make public policy and law, in part, by virtue of battles between varied agenda and beliefs present in our collective body of decision makers, and prior policy and law.
Leaders make collateral damage decisions based on the limitations of law and public policy, and their willingness to violate either. But also, any willingness to violate the law or policy is, in part, determined by public outcry and expression of citizen beliefs. God save us were the no such thing as an activist, conspiracy theorist, honest and diligent reporters, or letters to the Editor and to Congressmen.
Unfortunately, where a conspiracy exists by those with an agenda, it is easy to manipulate emotions to impact that public expression. The purpose in asking these questions, was to help you reevaluate the mechanisms and basis for your viewpoints, and to stir you to express any changes in opinion or beliefs which result, or to at least be more open to considering the arguments of others that such change is warranted.
If you do not understand the reality of decisions made in your name, your opinion about them is incorrect, and the decisions are not being made correctly to your true wishes. You are de facto victim even if you are completely unaware, and by your ignorance, others suffer more seriously, including paying the ultimate price.
Those who have full understanding also know that conspiracy theories only exist when reported facts do not make sense. Conspiracies are hard to prove without proper investigation, which is all ‘conspiracy theorists’ seek to sponsor when they propose their alternative explanations or explore the evidence publicly. If enough people say “Yeah… what about that, Mr. Congressman? I want an honest investigation with no white wash,” truth stands a chance. Conspiracies cannot otherwise prove themselves except by two means, one rare, and the other all-too common, but completely ignored.
They rarely are proven by confession or smoking gun evidence, because theorists do not have the authority or means to acquire them, as a rule. But whenever there is any evidence of a cover up, or disinformation tactics used against the theories, that alone proves there is a conspiracy afoot. So when media and government responds to theories by name calling or lies instead of explaining away the charges with useful facts… you know there is fire beneath the smoke.
Please question government, always, lest you be fooled again. All governments lie, and all-too often, for reasons just as questionable as collateral damage, which is almost always part and parcel of any conspiracy. They do so in your name, and only you can prevent that deception, that collateral damage. Your mind is yours to control, not theirs to manipulate with lies, just as your life is yours to live, and not theirs to dispose of as collateral damage for political gain.
Neither is there any difference between your life or that of a loved one, and the life of some nameless person in another nation on the other side of the planet. If they deem any individual acceptable collateral damage, then every individual can be so deemed just as easily, regardless of nationality or political beliefs. If you have rights, all have rights, or non have rights. There is no insurance for you, alone, but that which you make true for all by voicing your mind.
There is no difference, so use your mind, think for yourself, and voice your opinions loudly, lest you loose your life, or someone else does in your stead… and in your name.
Related articles
- Kirsten Powers Tears Into Conservative On Fox After He Dismisses Concerns Over Innocents Killed By Drones (mediaite.com)
- France hides “collateral damage” caused by its airstrikes in Mali (willyloman.wordpress.com)
- COLLATERAL DAMAGE: US Has Killed 100s Of Afghan Children Since 2008 (secretsofthefed.com)
- Thinking Our Anger (c4ss.org)
12 Frightening New Questions Illuminate the Dorner Urban Legend
Just when you think you’ve heard everything about a major news event which suffers questions pointing to a conspiracy, someone figures out or finds something others have missed, or failed to see in the same light. I like being that person. By H. Michael Sweeney, copyright © 2013, all rights reserved, proparanoid.wordpress.com Permission to duplicate online hereby granted provided it is reproduced in full with all links and text colors in tact and unaltered, including this notice. 12 new questions/veiwpoints addressed in this blog: • About the validity of physical evidence deliberately left at a murder scene; • About the validity of the ‘mental torture’ call to Randal Quan; • About the death of innocent bystanders; • About using a hotel on a Navy base; • About the million dollar reward? • About footprints in the snow, and the death of the one man with the answer; • About the ‘chance find’ by a citizen and a news crew of a James Bond-style assassin’s weapon; • Several questions about the Death of Chris Dorner.
Why Chris Dorner was murdered and framed
Questions?
 The Web is awash with questions and commentaries doubtful of the Dorner shooting, my own included. In my earlier posts, I’ve already addressed some of the same questions, and yet, have also come up with some new ones, or new insights upon existing questions. They are presented here in hopes they will help further illuminate the matter toward a better grasp of the truth — which sounds more and more like Dorner being set up as a distraction or cover up for something larger, something with Federal fingerprints.
The Web is awash with questions and commentaries doubtful of the Dorner shooting, my own included. In my earlier posts, I’ve already addressed some of the same questions, and yet, have also come up with some new ones, or new insights upon existing questions. They are presented here in hopes they will help further illuminate the matter toward a better grasp of the truth — which sounds more and more like Dorner being set up as a distraction or cover up for something larger, something with Federal fingerprints.
The first post: Dorners ‘Manifesto’: Manufacturing a D.B. Cooper-ish Urban Legend?, analyzed Dorner’s alleged ‘Manifesto’ and showed a long list of reasons it appears fraudulent, whole sections of it written by someone else, thereby validating concerns that Dorner was a patsy and a conspiracy was in play.
The second post: Dorner, the Urban Legend: Implications Behind a Fraudulent Manifesto, took a much closer look at the crime than most online treatments have employed. It provides deep-background information which suggests Dorner might have been a mere playing card in a high-stakes military or CIA project, possibly pre staging for a Martial Law sponsored coup. Ergo, the Ace of Spades graphic.
If you have not read these earlier posts, and are not comfortable with accepting the above descriptives of their content as viable concepts or factually accurate, please read them before reading this piece, or it will waste your time, as your basis of understanding will be in the absence of key information. Also be sure to review the excellent and revealing ‘related articles’ at the bottom of this page — especially the video interview relating Chris Dorner’s contacting alternative media and essentially confirming many of the points I’ve been making in my posts.
Was Chris Dorner a pawn in a Federal Plot?
Questions which point the way to understanding, even without answers
 1) Dorner’s gear found at the first murder scene: Why would Dorner choose to leave Police equipment traceable to him at the scene, when said equipment would be valuable to ongoing operations if intending a killing spree? Curiously, there is video evidence that he did this. Someone who looked like Dorner, at least at distance in the poor quality view, in a vehicle which was apparently his (no definitive statement on that in reports, for some reason), is caught on a security camera dumping the items, including his badge and police uniform. Why would Dorner do this in front of a visible security camera in broad daylight? The murder took place at night time (see the news video report, toward end). There would have been cops already swarming the area, making it a high-risk adventure.
1) Dorner’s gear found at the first murder scene: Why would Dorner choose to leave Police equipment traceable to him at the scene, when said equipment would be valuable to ongoing operations if intending a killing spree? Curiously, there is video evidence that he did this. Someone who looked like Dorner, at least at distance in the poor quality view, in a vehicle which was apparently his (no definitive statement on that in reports, for some reason), is caught on a security camera dumping the items, including his badge and police uniform. Why would Dorner do this in front of a visible security camera in broad daylight? The murder took place at night time (see the news video report, toward end). There would have been cops already swarming the area, making it a high-risk adventure.
Why would Dorner even leave the gear at all? It would be valuable in any further covert applications if he was intent on continuing the alleged killing spree. It can’t be to deliberately ‘prove’ to Police it was him responsible: the call to Quan, a mere fingerprint, or a call to Police would have served as well and would be far safer. But it does make sense if someone was trying to frame him, sending someone who looks like him enough to pass for him, especially if borrowing his car to do it.
2) The alleged call to Quan by Dorner: If Randall Quan represented Dorner at the review hearings which resulted in Dorner’s dismissal, why is it only described in media references as a call from someone ‘claiming to be Dorner?’ Other qualifiers like ‘may have,’ ‘allegedly,’ etc., were almost always used. Would he not know Dorner’s voice?
Bear in mind that where a caller deliberately makes rude and insulting, emotional jabs at one’s psyche, the resulting change in mental state (anger, mostly) will deter one’s perceptions and judgement of such things. To me, it sounds like Quan was enough of a professional that he at least recognized the possibility of the voice not being Dorner’s, and must surely have couched his statements accordingly, else why did LAPD statements and media originally do so?
3) The death of innocent bystanders: If killing Monica was because she was family, as claimed by the manifesto, why kill her companion? Dorner should not have known he had proposed to Monica only days earlier, and Dorner has been repeatedly cited as taking care not to harm innocent persons. Likewise for the trainee with Crain. Why harm those men? Might it be because both men could have seen who the real killer was, a risk addressed by a killer who could not afford anyone saying it was not Dorner?
Kieth Lawrence, killed with Monica, can be seen wearing what appears to be a Police uniform in some online photos, but he was not a Cop. He (article) had been a security guard at a Universtity, and had undergone trainings with Ventura County Sheriffs and Oxnard Police, but should have been seen by Dorner as purely a — he was NOT wearing his guard uniform at the time of the shooting, and thus was unarmed. Many accounts say there is evidence (?) Dorner stalked them both for some time, so surely he would have known Lawrence was not with any LEA, certainly not LAPD.
It is also interesting that both were shot multiple times. In fact, so many that reloads would have been required, or for gun grabber’s edification, a high-capacity magazine was used — or — unless there were two shooters.
5) A hotel stay on a military base: Why did Dorner go the Naval Base at Point Loma (San Diego — see timeline)? It was confirmed that he had been in a hotel ON BASE and the base went into lock down when someone reported seeing him. Could it have been an attempt to meet someone who might provide him with evidence he was being framed, or something useful as a blackmail insurance policy to force (someone high up) to call off the dogs?
6) The million dollar reward: Why (and how) was a $1M reward arranged for so quickly, and who really managed that hat trick, when normally, $20K is the most anyone ever sees pinned to their name, and only after much time has transpired since the manhunt began? Only bin Laden and associates have, to my knowledge, enjoyed that level of value on a wanted poster, and so quickly. This article seems to have a convenient but implausible answer (just above second video); a collective of leaders from the area including businessmen ‘came together.’ Really? When does that ever happen, elsewhere?
7) Footprints in the snow, and the death of the only man who knew to track them: How convenient is it that the final standoff comes to pass because two officers ‘track him’ to the cabin… and one of them is fatally shot to death — a super-cop sent on Dorner’s chase like a bounty hunter? The other was wounded. Jerimiah MacKay, killed at the cabin, was a 15 year veteran of the San Bernadino’s Sheriff Dept. His specialty was going after stolen cars. He was on Dorner’s case from the outset, but fared not better than any other Cop. But in less than four hours after a truck was reported stolen by someone matching Dorner’s description, he and his partner were tracking footprints in the snow to the Cabin. Excuse me, but how did they know to track these particular footprints?
They had NOT found the stolen truck, so how and why did the presume these to be his footprints, or even know they existed, and where? NO ONE had ever seen Dorner alive near the cabin, nor any other person who might have been responsible for the footprints they choose to follow, nor, for the matter, whoever really fired the shots that felled them. Next came an swarm of lawmen and choppers, and the Cabin was set afire. Restating the question more pointedly, how did the dead Sheriff know to follow the footprints, unless there was some foreknowledge; a conspiracy afoot requiring Dorner’s body to be found cindarised? Now that he is dead, we may never know how he knew how to find those footprints, and why he knew to follow them.
8) The finding of a murder weapon by a citizen and news crew: A man reportedly found a crashed car (not the truck allegedly stolen by Dorner just prior to his being cornered) near the cabin, and nearby laying in the open in the snow at the roadway’s edge, a Walther P22 pistol with silencer and flashlight (a James-Bond style, professional assassin’s weapon). Coincidentally, a news crew happened along just then, as well? And they thought seeing a man standing at the side of the road was obviously newsworthy enough to investigate and interview?
This is three days after the Police the Cabin was fired and Police had swarmed into the area, and the day after concluding their investigation in the area, opening roadblocks to the public. Anyone see red flags here? If not Dorner’s truck, who’s car was it, and who’s gun? If Dorner had somehow stolen a car after stealing the truck, why has it not been reported? The car renews interest in and underscores the question about how MacKay choose to follow footprints, and where they originated, not just where they led. It is also raises the possibility that whomever killed MacKay was not Dorner, but a professional assigned the task.
9) The death of Chris Dorner: Was Dorner dead already, killed at some point well before the cabin event? It would be easy to have staged the events leading to the fiery conclusion, especially if one man knew to follow the footprints to the Cabin preprepared with Dorner’s body and rigged with squibs to simulate gunfire. It would only take a sniper to eliminate that man, the one possible person who might know the truth or unknowingly expose it if allowed to live, perhaps the only one outside of any inner conspiracy circle within LAPD or CIA/military camps.
10) The tale of four sets of ID, three wallets: How did the wallet survive the fire, and how many wallets and ID sets did Chris Dorner own? There had already been multiple reports of his wallet and ID being found, and yet they also find it, in tact, with readable plastic ID, in the ashes of a building where nothing else survived the flames. Add in the discarding of his badge as yet another form of ID. I DO NOT BUY IT.
That is specifically one of the oldest tricks in the intelligence community’s playbook for framing someone or making it seem that a body is someone it is not. Yes, it can also be used to misdirect authorities as to your true presence or whereabouts, but you only need employ that gambit generally once, and even then, only when making a major tactical move (like an escape, or an assault). Four times? Not synchronous with either escape or subsequent assault? And so close together in some cases, essentially wasting valuable ID resources?
11) The body of Chris Dorner: Is Dorner even dead, at all? If it were not for the phony ID find, I might not be moved to ask. But it implies official deceit. So, is he alive and vanished by virtue of NDAA style actions by our acting President or a unilateral military decision, or has he managed to pull off his own escape plan? I doubt the later, but even the Coroner’s report of dental matches, or DNA match will not be proof enough to answer the question; given the weight of material pointing to conspiracy, a fraudulent Coroner’s report is simple to arrange if CIA is involved, and easy enough for lesser groups.
12) The fire and ‘suicide’: Why did, per police radio traffic, LEA deploy multiple fire-starting ‘burners,’ incendiary tear gas canisters, if not intending to start a fire? Why did they turn away fire trucks with a decision to wait until all four corner’s had caved in once learning there was a basement? In almost every use of this kind of device, a fire erupts if it lands on or against anything flammable. Using multiple burners insures a fire. Was it to make sure the only way to ID Dorner’s body was dental records, the easiest of all to tamper with when officially faking someone’s death? Was it to insure that Dorner never had a day in court where he could expose crimes by LAPD or others well beyond those already known?
Bonus Question asked by others re Media complicity: Why did media volunteer to black out the Dorner event already underway? Choppers in the air pulled away at Police request issued thru FAA (suspicious and completely unprecedented in its own right), because Police claimed ‘news coverage might tip Dorner off.’ Excuse me, but the gun battle had already ensued, and the cabin was already surrounded. Police positions were not clearly revealed by aerial video because of dense trees about the cabin and the distance and angles involved. So what was the threat, again? If Dorner didn’t already know he was surrounded after engaging in a gun battle, he was not likely to be watching TV to find out.
And how do you get a TV signal way out there to the Cabin, in an isolated valley, when the cabin had no TV aerial visible, and the nearest broadcast station carrying feeds were in LA, 67 miles away on the other side of mountains forming the valley? What was the real reason Police wanted no one to see document they were doing? Why did media comply, knowing their signal was of no value that far away? Why did FAA aid in that cover up?
Why was an assassin’s pistol found by civilians near the cabin after Police finished investigation?
Summary
All these question and nagging discrepencies are the stuff which makes for an Urban Legend. Remember, an urban legend is always based on some kernel of truth, and yet is almost never truly what it seems on the surface. People tend to believe the legend, and fail to ask the right questions even if choosing to look closely. Dark lies need to be exposed and examined carefully in the light.
In looking closely, ALL of the above questions imply their own answer: a conspiracy, lies, and intelligence community tricks being employed. Whether those tricks are by CIA, military, or LEA application is something only the answers to the questions will reveal. But you (in bothering to read this), I, and other ‘conspiracy theorists’ seem to be the only ones asking questions. Given the obvious nature of many of them, that is its own clue something is wrong, something quite related to the bonus question. Anyone not seeing that, is not paying attention.
Turn on the damn flashlight!
How did Police find Chris Dorner?
Related articles
- Truthing Chris Dorner- Playing the skeptic (therealmcteag.com) An alternative and thoughtful viewpoint addressing Dorner’s cult status
- Chris Dorner Speaks on Before Its News (video interview beforeitsnews.com) More proof Dorner’s Manifesto not written by him, Chirs Dorner claims he is framed, and clues he was getting help from Anonymous.
1.4 Billion Ammo Orders Use Satanic Magic Numbers
When satanic leadership of the NWO undertakes a plot, you can bet there are satanic magic numbers in use, somewhere. Sometimes the obvious is right in front of our eyes, if we but just look askant.

Homeland Security (patch) Police (helmet)? Why does DHS want Mine Resistant Behemoths like this in your city?
Why did DHS order 1.4 billion rounds of ammo? Satan made them do it!
Updated March 6, 2013, and errata: A previous update of this same date was in error as it implied DHS had ordered 2,717 MRAPs. Claims do abound on the Web that DHS’ has also placed a recent Order for 2717 MRAP (Mine Resistant Armor Protection) Light-Armored, Gun Ported Vehicles also uniquely satanic. However, the order was actually via U.S. Navy conduits and are intended to be manned by the U.S. Marines, presumably in overseas operations — but of course, deployment can actually be ANYWHERE.
Regardless, the smoke comes from fire theory is fueled by the fact that DHS does use the same vehicles (image) and has their own Police Force (ICE ERO — Immigrations Customs Enforcement Emergency Response Operations). If you go to ice.gov Web site you indeed find them crowing about numerous ICE ERO arrests in civilian police matters unrelated to either Customs or Immigrations. Ask yourself then, why does DHS want these vehicles and Police (soldiers by any other name) otherwise illegal under Posse Comitatus in YOUR city? Updated analysis marked via RED text.
Is DHS a Satanic branch of the US government?
By H. Michael Sweeney, copyright © 2013, all rights reserved, proparanoid.wordpress.com Permission to duplicate online hereby granted provided it is reproduced in full with all links and text colors in tact and unaltered, including this notice. Did Satan make DHS order 1.4 billion rounds of ammunition? Does DHS have its own Police force?What you will learn reading this blog:
• That all numbers have meaning, sometimes spiritual, even satanic… and magical; • That the magic numbers are easy to find and translate, by way of example; • That the DHS munitions orders are rife with satanic numbers and meaning; • That that meaning implies they will be used against citizens and destroy the America we know in favor of the North American Union.What does the DHS munition order have to do with the North American Union?
One indicator that the DHS 1.4 gigamunition orders are intended for pure evil use may be the actual quantities ordered, themselves. When the Satanic leadership of the NWO makes plans, they use every Satanic leverage they can muster to insure success. Magic numbers are almost always present one way or another. We got a taste of that on Sept. 11, 2001, and other black days in history where the date itself forms magic numbers. Yeah, yeah —mere coincidence, right? Don’t be so sure; read on.
What is a Satanic Magic Number, you may ask?
To answer that, we need to go back to ancient times and consider the dead languages, such as the Greek, Hebrew, and Latin. In those times, each letter of the alphabet had a numerical weight or value associated with it. The best known by most of us are termed Roman Numerals, but all these languages used such a system. Thereby, a given word, phrase, passage, or text document could have a numerical value by simply adding them up. That’s one reason the name of the Antichrist can be given as a number.
Also prevalent in those days was the occult practice of Numerology, the belief that each number carried with it a social and religious meaning or importance, a functional word/phrase equivalent. Numerology as pertaining to religious use was largely associated with cults and early Satanic religions, but also, even Biblic texts rely upon numeric valuations. Typically, the ‘meaning’ of a given number remained constant between the dark (Satanic) and light (Biblic) uses, with minor changes to suit emphasis or application.
By such a scheme, it is possible for a number series to be converted to a sentence-like translation or summary of its meaning. We will be doing a little of that, later on. In reverse fashion, one practiced in numerology can devise a number to have such a translated meaning. In addition, there are certain number properties which are thought to hold magical abilities which amplify the power or intensity of any such meanings. Doublets, triplets, and so forth, perfect increment/decrements (e.g. 1234), squares or other root products, and palindromes, those numbers which are the same forwards and backwards, and even prime numbers divisible only by 1 and themselves, are examples.
Note: If you find this interesting, you may also want to learn about the Gematria Calculator, which translates numbers to words and vice versa. The link also provides additional background details to the above presentation.
What is the history of magic or satanic numbers?
Machinations for illumination
The means of manipulation to relate magical translations has some flexibility. The number sequence 123456789 can be looked at for the purpose as a single 9 digit number, or three three digit numbers, or it can be broken into pairs with the odd man out at either end, or in the middle. When in the middle, groupings both left and right of it may incorporate it for ‘double duty.’ Groupings can then be summed to obtain other numbers to be employed for translation purposes. Thus our example number in groupings of threes would become 6 15 24 as a result.
Sum results can also be summed yet again. The most common form of summing, however, is summing in strict pairs, which is a bit different. Summing our example result 61524 (not in pairs) would produce 45, the actual sum of the three numbers, but in pairs, it produces yet a new three digit number, 666, the most powerful of all Satanic numbers for obvious reasons: 6 is treated as if a pair, 15 sums to 6, 24 sums to 6. The other way to sum is to simply sum them all as individual digits, which yields 18, another code-like way to express 666 (3 x 6 = 18).
A thing to do, especially with larger numbers, is to review their table of divisors; all possible combinations of division the number supports. The quantity of divisors can be examined, as well. The only useful divisors would be those found magical themselves, and especially so for the more important Satanic numbers, 13, 18, and 666, or multiples thereof, or numbers which yield them by the above machinations. Indeed, there are many means which can be applied, but regardless of the method, the interesting fact is that the odds of being able to discover a magical meaning to any given number of some size (e.g. 5 or more digits) is relatively small, despite it being easy to find magical numbers by the described means. Restated, it is easy to find magic numbers, but not easy to find magical meaning; more is needed to impart meaning and actual power.
Only a few specific numbers in a given range (e.g. 10100 – 10200) would have much going on in terms of useful magical impact. 10100 can be argued a magic number, for instance, because it has the doublet 00 and the palindrome 101, and is based on the the number 1 which has a significant meaning in its own right (primal force). But that is not enough — and yet is tantalizing enough that we ought look more closely.
Indeed, if employing the divisors method, we find it divisible by the doublets 1010, 2525, and 5050, and the additional palindromes 101, 202, 404, and 505. If we cared to do so, we would learn these numbers have meaning of their own. Thus it turns out to be a magical number, but yet, it is not Satanic (the meanings are good, not evil), and therefore of no value to our search — unless we encountered an ammunition order in that quantity, in which case we might deduce it for a good cause. We do not, and should not find it, in that those seeking good are admonished in the Bible against using numerology, and thus it should be only by coincidence or divine providence that they would have elected a good number.
Who uses magic or satanic numbers?
Not just any old number will do
The important thing is, finding a Satanic number is not common enough that one can argue ‘any number can be shown Satanic.’ In our sequence above, one does not encounter a number with the potential for even a mild Satanic interpretation until 101124, which is able to produce the number 18 in machinations several different ways. Even so, it is not sufficiently dark to be used for justification, because it does not enjoy any of the other requirements:
It must afford an actual translation which imparts a meaning, and/or, alternately, enjoy a symmetry or consistency as if a ‘theme,’ and/or, alternately, offers a myriad of such finds employing a wide variety of magical numbers; it should tend to be somewhat obvious and clear cut in nature. If it does not hit you over the head, it’s probably not intended to have magical meaning… unless, perhaps, it is part of a set of other magical numbers where one might deem to look for a theme within the entire set. That complexity, fortunately, is not required with the ammo order, as each number appears to express itself, alone, and as a whole, the entire order’s theme is also consistent with any individual number’s meaning.
Indicators are indeed everything. In numerology, select numbers were deemed to represent good, and others, evil or occult, meanings which could be used to reference conceptual constructs, events, outcomes, traits, or even objects or persons, etc. You can learn about any (usually limited to two digits) number by typing into your search engine, ‘what is the meaning of x,’ substituting your target number for ‘x.’ Some references will focus on positive spiritual uses, some on general Numerology meaning, and a few will focus on occult uses. However, even the spiritual and less blatantly dark Numerology definitions will paint a useful picture in most cases. Try several resources.
One must not discount the opposition, either. If truly seeking translation, one must expect to find a mix of good and bad magic numbers. For example, if the message were intended to be something along the lines of ‘Satan destroys god’s plan for man,’ it might look something like 18 (Satan) 11 (destroys) 27 (salvation) 181127. That number contains a palindrome 181, which sums to 99 in pairs (using the middle number in an odd digit count with each number to its left and right), which again sums to 18, and the last four sum to 11 yet again collectively. The first four sum to 13 (sin), the mechanism by which Satan destroys salvation. The theme is present and expressed several ways. So if I was an evil Mason designing a Temple or other building of mystical import, I might make sure to employ that number and others like it in the dimensions (e.g., expressed in millimeters, it equals 594 feet, where 594 sums to 18, 94 sums to 13).
How are magic numbers used in the real World?
Real World example
Indeed, we find precedence. There is in India one the tallest buildings on the sub continent which is of that height, called Planet Godrej. Godrej is an Indian personal name which translates/relates to the occult Zoroaster metaphysical faith, also known as Zarathrustra, an ancient Persian occult faith (oldest on Earth) of mythological importance to the ancient Egyptians, and therefore, to Masons. The name is historically associated with wealthy business families worshiping Zoroaster. Remember Ghostbusters, the movie? The evil from the other side in the film was based on Zoroasterism.
Thus Planet Godrej might be intended, by its designers, both by its name and its dimensions, to represent diversion of Man from Salvation by means of sinful business efforts, planet wide. What is the building actually used for? It is a luxury apartment complex catering to wealthy business leaders in the heart of Mumbai (Bombay), each replete with servants quarters. It is located in an entertainment district which includes gambling. There are only two other buildings of the same height in the World cited on the Web: a similar residential building for business leaders in London, the Vauxhall Tower, and one of the five Suntec towers in Singapore. Vauxhall is a name derived from the Russian pleasure gardens of the Tsars, a place of diversions from mere amusements to outright sinful sexual excesses for business and political leaders in Russia. The Suntec towers are part of Suntec City, a complex of business office and convention spaces, residential, and entertainment facilities. See any themes, here? I don’t make this stuff up, you know.
What numbers are satanic?
Meet our magic numbers
Here are the numbers we will focus upon for our purposes, today; those numbers most used to represent Satanic dialog/themes, or to clarify them — in the simplest and briefest of summaries. Note there is some translation taking place in the larger numbers employing the smaller number’s meanings, so you see how translation can take place with consistency. Those few in bold are the true Satanic numbers of power.
3 Fullness 5 Balance, the power and limit of man to control 6 Illumination, enlightenment, legend, man 7 Mystery, esoteric or scholarly magic, associated with Saturn, a name for Satan, might be a curse 9 Visitation, spirit 10 Law, obedience 11 Imperfection, disorder/chaos, that which precedes destruction 13 Rebellion, depravity, sin 16 Material power, incarnation 15 Three dimensions (reality), new direction, blinding temptation (Satan) 17 Victory, Son of Man (Christ), liberation 18 Oppression, bondage, slavery = 3 (fullness) x 6 (legend/man/illumination)= 6+6+6 = 666 21 Distress = 3 (fullness) x 7 (mystery, magic – a curse) 29 Departure, cast out = 3 (fullness) x 13 (sin) 30 Rulership, dominion = 3 (fullness) x 10 (law, obedience) 31 Offspring, branch 33 A sign, warning, predictor = 3 (fullness) x 11 (that which precedes destruction) 36 Adversary, enemy = 2 (division, double) x 18 (oppression, 666) 39 Infirmity, death = 3 (fullness) x 13 (sin) — the wages thereof 360 Encircle, trap, capture = 10 (obedience) x 36 (enemy) 666 Satan’s nameNow to the analysis of DHS ammo orders with the above in mind. To follow along and be comfortable with my findings, you may wish to open another window or tab to a divisors calculator, and to activate your desktop calculator. The divisors calculator additionally gives you the sum of divisors, often of value in the analysis. Because there are so many numbers which might be analyzed, I will simplify the presentation by focusing on the first number (which happened to seem to be the least magical on first look), the largest single order item, and the final total. You will then be well versed in how to check any of the other numbers on your own. Since it can be confusing to describe mathematical things verbally, I have also attempted to employ color coding to help you more easily see what is being referenced.
How do you find magic or satanic numbers?
The first item: .223 Assault Rifle ammuntion, yr 1 35635000 rounds
Sum of divisors: 83504520
1 2 4 5 8 10 20 25 40 50 100 125 200 250 500 625 1000 1250 2500 5000 7127 14254 28508 35635 57016 71270 142540 178175 285080 356350 712700 890875 1425400 1781750 3563500 4454375 7127000 8908750 17800 35635000
Bold = palindrome Red = 13 sum Green = 16 sum Blue = 17 sum
At first I did not see too much going on with this number other than it was an unusual palindrome, 35635, and that the divisors contained three of those as well as three 17817 series (e.g., 178175). But the sum of divisors (83504520) proved interesting, too, when run through the divisor calculator: its 13th divisor is 18. It’s 57th divisor is 360 (entrap), 57 summing to 13, as well. Then, looking at the last three digits of the 178175 series, we find they summed to 13, also.
If this was all there was, I still would not have bothered going any further in my hunt, concluding there was insufficient magic present. A weak theme of 13 with a hint of 18 in play was not exactly ‘saying’ much. The hypothesis would have been found inadequately proven, and this article would not be warranted.
However, when one checks in groups of three or four digits, one quickly discovers that a large number of divisors, including half of those with 13 present by summations, almost always summed to either 16 or 17 either as a whole, or as a balance of digits in the case of those with 13 present. In total, there are six each 16 and 17 summations, three of the 16 conjoined with a 13. Thus the ‘theme’ would seem to be 16 (incarnation) of 13 (sin) is greater than or opposes 17 (salvation). In this case, it can be made greater because the conjoined instances are all palindromes, although, the odd number remaining 5 (balance), implies a balance of power is being contested.
Now, going back and looking at the original number 35635 again, we can see that 35 is 5 (balance, limit and power of man) x 7 (having to do with magic and Satan). This is another way of saying the same thing (balance of power in conflict). Further, that converts it to 57675, which can be summed in triplets to form the doublet 1818. Again, very powerful and weighted to Satan’s advantage against Man and Man’s salvation. With the same general theme being found expressed three different ways, I elected to write the article; the numbers said something after all.
DHS orders ammunition in quantities based on Satanic numbers.
The largest order: .223 Assault ammo, yr 3 728582000 rounds
728582000 728582000 728582000 728582000 728582000
Sum of divisors: 1761716112 1761716112 1761716112 1761716112 1761716112 1761716112
1 2 4 5 8 10 16 20 25 40 50 80 100 125 200 250 400 500 1000 2000 364291 728582 1457164 1821455 2914328 3642910 5828656 7285820 9107275 14571640 18214550 29143280 36429100 45536375 72858200 91072750 145716400 182145500 364291000 728582000
Bold = palindrome Red = 13 sum Blue = 17 sum Purple = 18 sum Pink = 15 sum Teal = 10 sum
Again we see palindromes richly present. The order quantity itself contains 858, which by sums translates to doublet 13, very powerful. The larger palindrome, 28582 likewise summed provides doublet 15 (temptation in spades). The sum of divisors is even more palindromic, containing 17617 as well as 171 and 161. That provides for one 13 in the former, and if summing the later together, provides 17, plus the outright 17 in one of them (171), and 17 by summing of the other (16+1). Then we also find a single number with two palindromes: 5828656, its first two numbers summing to 13, second and third to 10, the last three to 17, the first three to 15: 5828656 5828656 5828656
We find 13 is also present by summing in four divisors, each an ‘island’ without conjoining. However, 17 seems to be everywhere, in each instance conjoined with 18, 15, or 10, and in like manner, 18 is abundantly conjoined with not only 17 as just mentioned, but also 10. Indeed, the order quantity palindrome also contains two each of not just 13, but two each also of both 15 and 10. That’s a pretty potent palindrome.
In checking the divisors of the sum of divisors, as in our first year order, we find the number 13 pops up, this time rather than in the form of being the 13th divisor, it is divisible by 13 directly, which goes 135516624 times. That not only starts with 13, but contains two adjacent 13s by summing: 1355 16624, as well as containing 15 and 18 (135516624) by sums, or outright 666 if summing just the last pair, and 17 two ways by dropping either 1 in the first sequence. You also get 666 summing the 51 ahead of the 66, and of course, 55 gives you 10. All the key numbers are present in the one number, which is multiplied 13 times to amplify its dark power.
In almost identical manner, the palindrome 45536375 from the original divisors does the same, in overlapping combinations: 45536375 (17 15), 45536375 (17), and 45536375 (10), and 13 in the 553. Only 18 is missing in this one. Now go back to the actual order number, and you see it happen similarly, yet again: 13, 15, 17 and 10 are all there. From all these we deduce a consistent (three-way depiction) of a theme dialogs: 18 (slavery, Satan) vs. 17 (Son of Man) = ‘conflict’ or ‘battle;’ and 17 (Son of Man) vs. 15 (change of direction, blinding temptation); and 10 (obedience) through 18 (slavery, Satan). These same themes have been repeated four times in this one order item!
Combining these, and we get the picture of a battle of some sort on an epic scale. Considering that we find 13, 18, 17 are the only ones which also stand alone (rebellion, liberation, slavery), it appears that is the nature of the conflict is to be a rebellion to decide between liberty or slavery.
DHS orders ammunition in quantities based on Satanic numbers.
Grand total of all munitions: 1405175654 rounds
1405175654 1405175654 1405175654 1405175654 1405175654
Sum of divisors: 2108519640
1 2 2819 5638 249233 498466 702587827 1405175654
Bold = palindrome Red = 13 sum Blue = 17 sum Purple = 18 sum
Because the number becomes considerably more finite when it does not have a lot of zeros, we get very few divisors, and thus it becomes ‘harder’ to find magical numbers since there are fewer to consider. However, they are present. The quantity itself contains both 18 and 13 two different ways, and we do have one palindrome, and 17 exists outright, only mentioned because it will be omnipresent elsewhere.
The first two four digit divisors if summed in pairs, produce palindromes: 1010, and 1111, respectively. The next two divisors both contain a summed 13 (49), and the later of these can also produce 18. The next divisor produces a 13 in addition to a palindrome. We also find that most of the divisors contain 17 by summing: 5638, 249233, 498466, and 7025877827.
But we are not done. If we also compute divisors for the sum of divisors, we find some more interesting things not common to similar efforts with the other numbers. We find a wealth of palindromes. In fact, more than 20% of them have palindromes, including a 5 digit 67976, which makes for a doublet 13 by summation. There are numerous doublets, many numbers containing multiple doublets, including 4040 (40 is the number of death and rebirth, or destruction and renewal).
That number, 14954040 also contains both 13 and 18 in sums sharing the 495. There are even very rare triplets, including 666 itself — twice! The other triplets, 333, and 999, additionally contain 13 in their construct. Like the original number, 13s and 18s also abound in many different ways. The overall theme for the entire order, then, is 13 (sin) amplifying the power of 18 (Satan) against 17 (Son of Man).
Who in DHS wants to overthrow the US by force in favor of the North American Union?
Update: 2717 MRAP vehicle order
Sum of divisors: 3360. 8 divisors:
1 11 13 19 143 209 247 2717
Bold = palindrome Red = 13 sum Blue = 11 sum Purple = 18 (666)
A palindrom (717) starts this off, which sums in pairs using a shared middle number to the doublet 88, and we have a doublet 33 in sum of divisors. Both Doublets are divisible by 11 a number of times (3, 8) which sum again to 11. Still, not that much to crow about until we look at the divisors, of which there are very few, and yet which provide a wealth of results in EVERY divisor of note. The order is divisible by 13 209 times which sums to 11, and divisible by 11 247 times which sums to 13. It is divisible by 19 143 times which combine in sums to 18 (666). So, just look up 11 and 13 to get the ‘theme,’ and amplify that by 18.
Why did DHS order 2717 MRAP vehicles?
Summary
Therefore we see the simple outer theme, inwardly, concealed if you wish, expresses an overall theme akin to Armegeddon, or the Great Flood, to be visited upon America. But also, you see… if the NWO has is to its way and be able to establish a one-World government, the true purpose thereof is to seat the Antichrist, and lead us to the final End Times, actual Armegeddon.
But to get there will require something called the North American Union, abandoning the independence of Mexico, Canada, and the US altogether. But the greatest roadblock to that is the United States and our massive gun ownership which binds us like an insurance policy to our sovereignty and Constitutional integrity. Unless they can find a way to cancel out that insurance policy, they cannot have their way. The North American Union cannot come to pass without something drastic happening.
The numbers suggest they may at least think they have found a way to solve that. A bloody way. In fact, the sum of divisors of the grand total is equal to (270 x 13) + (3165945 x 666). Various sources cite the number of guns in private hands in America is 270 million. 3,165,945? That’s just about the size of the US Military and Police forces, combined, depending on who’s numbers you use. But that’s just me and some numbers talking.
How can the North American Union come to pass?
What do you think?
Support the second amendment if you hate the North American union!
Related articles
- Raw Numbers Prove DHS Gearing up for Revolution, Martial Law, or Chinese Invasion (proparanoid.wordpress.com)
- The Numerology of the Holy Name of Jesus Christ (world-mysteries.com)
- The Magic of Numbers (mapelba.wordpress.com)
- Whats Your Digits? : The study of Numerology (distnction.org)
Dorner, the Urban Legend: Implications Behind a Fraudulent Manifesto
What would it really mean if Dorner did not write the Manifesto claimed for him? Like many bumps-in-the-night mysteries in our national consciousness… the answer may lead to CIA and the Military.
By H. Michael Sweeney, copyright © 2013, all rights reserved, proparanoid.wordpress.com Permission to duplicate online hereby granted provided it is reproduced in full with all links and text colors in tact and unaltered, including this notice. The image is specifically excluded from permissions to duplicate: see text with image. Dorner, the Urban Legend: Implications Behind a Fraudulent ManifestoWhat you will learn reading this blog:
• That there are more, darker possibilities than the obvious bad Cop framing a good Cop; • that possibilities include direct ties to Rodney King and Operation Verdict in support of Martial Law for a military coup; • that CIA has infiltrated LAPD (and most major LEA) for their own criminal needs and may be at the heart of Dorner’s fate; • that there are many clues most of us have missed which foster TEN new questions which help understanding; Did CIA or Military frame and murder Dorner? What is the truth about Chris Dorner?
This original artwork is trademarked and copyrighted and may not be reproduced in any form dissociated from this blog in full or in part without express permission: I especially do not want some bad cops turning the left-half into some kind of racist T-shirt. If someone wants to make the WHOLE thing into a T-shirt, we can talk.
In my prior blog post in this series, I showed more than a dozen reasons to question if Dorner’s Manifesto were his manifesto, at all. While portions were surely written by him, it also seems clear that because of different writing styles and the very construction employed, as well as external evidences relating to the security of Dorner’s Computer activity — the sections which paint Dorner as a mad killer were by someone else. I’m not the first to suggest it, but perhaps the first to fully dissect and expose. Without those additions, all you have is a laundry list of LAPD wrongdoing and an open letter to LAPD pleading for resolution by a perfectly good Cop.
If we agree that there is reason to question the authorship of the condemning portions of the document… then we have to wonder what else about the greater Dorner matter is real?
There had to be a motive, and a pretty powerful one, at that, to warrant setting Dorner up for murder and feeding us lies. So much of Dorner’s laundry list of LPD sins ultimately translate into or directly relate to racial prejudice. Dorner cites everything from racial slurs to violence, specifically mentioning the Rodney King beating/video to show how systemic it has been. But this cannot be the motive, in my opinion.
Racist Cop complaints are, within LAPD, a small-potatoes issue representing little ‘threat’ sufficient to motivate the fraud and murders involved. LAPD, even as Dorner points out, has a long history of such prejudice and covering ups. When leadership habitually protects those who step out of line in this regard, there is no threat worthy of the death penalty in yet one more accusation, even if by a fellow Officer. We are moved to think it has to be something else. Or does it?
Was Dorner a CIA or DOD patsy?
In the game of Hearts, playing the Spades can steal the whole deck
In the game of political power and control, it is our Hearts and minds which are at stake via psychological manipulation of the masses. The closer you look past the thin and faulty veneer of the Dorner story, the more the clues we find which lead us not just to bad Cops in LAPD, but also, unfortunately, to the CIA and Department of Defense and very dark things that threaten to impact us all. So hang on… this is a far bumpier ride than the manhunt we see on the surface.
As I document in my bookset, Fatal Rebirth (new special low price offer in place, by the way), the 1992 Rodney King beating Dorner was careful to cite — had led to CIA reconnaissance overflights of major US Cities to perform low-level, high-resolution aerial photomapping of black neighborhoods for something called Project Verdict. Verdict was preparation for the declaration of Martial Law if rioting broke out nation-wide when the trial of the 4 LAPD Officers involved was concluded with an expected white-wash verdict of ‘innocent’. So concluded, it was.
And based on a lot of indicators, it was planned that way from the start; a plot to overthrow the Constitution.
But it failed, though LA indeed became a battle ground like never seen in any American City, requiring the National Guard AND US Marines to restore order. 53 died, more than 2,000 were injured, and nearly 4,000 fires leveled whole neighborhoods and cinderized over 1,000 businesses. Had other cities followed suit, the whole deck of cards would likely now be under military control, exactly as forecast by our highest ranking military in the event of nation-wide martial.
Now know this: in the time frame of the beating, trial, and aftermath, King was reportedly described by various officials predisposed to rude thoughts as the ‘King of Spades.’ Also active World-wide at the time was Operation Gladio (still in play, today, it seems), a US/NATO clandestine effort to topple Communist Bloc nations which further evolved to include a series of false flag terror events targeting Americans and NATO citizens to justify repressive draconian responses. Was Verdict part of Gladio? No way to know, but it sure fits the mold.
Fortunately, Verdict was thwarted. But I have to ask: was it intended from the start to foster a military coup? POTUS in ’92 was an old CIA man, George Herbert Walker Bush, a man tied to many of the darkest of bumps in the night America has ever known, from JFK to Watergate, and beyond. An excellent review exists in book by Pete Brewton, The Mafia, The CIA, and Goerge Bush, intro here. Gladio was under his watch as CIA Director, and while in the Oval Office.
1992 was a hotly contested election year, and conspiracy rumor mills of the day were warning that a military coupe was in the making to insure Bush held office; under Martial Law, the election could be cancelled. Rodney King may have been the key to such a plan. Absurd? Perhaps, but let’s consider it for a moment, anyway:
Bush was running for second term against Clinton and billionaire H. Ross Perot. Clinton had his own CIA ties, as did Hillary, but I won’t bore you with the details, here — but when I was saying the same publicly, I got hate email laced with expletives directly from the Oval Office. I was at the time researching my four-volume bookset, Fatal Rebirth, documenting crimes of the New World Order from 1947 forward.
As result of my investigation, it became clear to me that H. Ross Perot was a dangerous threat to the two-party system of power control via Dog and Pony Shows of pretended and superfluous political differences. Given Perot’s growing popularity, I feared they would take him out. He was last Century’s ‘Ron Paul,’ without the benefit of a congressional title.
I warned the Secret Service, who did nothing but put ME under surveillance for five years. Meanwhile, Anthrax was mailed to Perot’s family (the same thing used to silence one of Bill Clinton’s State Police-assigned body guards when he was Governor of Arkansas, to silence him from testifying about Clinton’s ties to CIA drug running in Iran-Contra, a George Bush sanctioned operation.) The Perot attack was confirmed to me by my own back-channel Secret Service Agent contact. It forced him to quit the race the night of the Colorado Primary, which he won even after quitting. Had he not quit, it would have given him enough electoral votes to have a place on the main Nov. election ballot.
But the NWO does not want you to have true freedom of choice. So you only get to vote for the two candidates they offer you, both of whom they own outright. If you knew the full story of how Ron Paul was prevented from being on the ballot, you would understand. Even with two candidates, the election is rigged so that it does not matter much how you vote, though wild-card antics like Chad counting can upset the equation without angering Eurobosses. Here’s how, and why it relates:
In those days, I had already interviewed a man claiming a flight crewman of CIA’s Evergreen Airline had confessed details of a secret flight: Bill Clinton, George Bush, and others (not Perot) were flown to Europe to meet with Bilderbergers to decide who would be our next President, Clinton being the answer. The plane landed and taxied to the end of the runway, where other Bilderberger planes already sat waiting.
Everyone got onto the same plane for their meet after deciding who would be the new President, and then departed in reverse manner, never officially entering the country. While we cannot confirm if this is a true event, it would give Bush a motive for circumventing by directly usurping power through martial law to end the election process. But to declare it would require some kind of internal upheaval on a national scale. Could such be engineered, and yet not seem manufactured to anyone, especially the Bilderbergers?
Are the Rodney King and Dorner matters linked to a Martial Law plot?
Playing the rest of the black cards
The race card trick: beating King and getting video taped was the first step. King was the perfect choice: he not only had the same last name as Martin Luther, but when clean shaven, he looked much like the much missed, martyred man. Beat King with video documentation, and you get instant renewed martyrdom, and kindle angst anew nation-wide in the black and white populace alike. But good quality video at night in those days was not as easy as it is, today.
The high-tech (for the day) Sony camera used had just been purchased and was taken right out of the box for the first time that night in response to the beating, it was claimed. I say claimed, because right out of the box, the battery would have been useless. The person filming was a Canadian-born contractor who had been raised in Argentina. You know, that country where the Nazi’s went after WWII, and where George Bush has bought huge tracts of land, and a fun place known to be a CIA playground in South America.
The second was to make sure the verdict in the trial was ‘not guilty.’ That was arranged by: a) having the first judge removed from the case as ‘biased,’ and b) the new judge assigned changing the venue to an all-White, well-to-do community resulting in a jury of 10 Whites and one Hispanic. But how do you make sure the violence level upon such verdict is sufficient enough to warrant calling in the National Guard? Simple — step c) have the National Guard foment violence to prime the pump. False flag stuff. Military stuff. CIA stuff. Any sign of that in LA at the time?
Well, as Dorner himself also mentions, we had for Chief of Police in LA at the time one Daryl F. Gates, clearly a New World Order Police State mentality kind of guy. He virtually invented SWAT teams and Police intelligence operations involved in wholesale spying on civilians. He also pioneered ‘sweeps’ of up to 1,000 officers at a time to arrest and detain everyone of a given class (e.g., 25,000 black and Hispanic youths, known or suspected gang members) simply for the harassment value, and to keep them off the streets for the convenience of city public relations, such as employed during the 1984 Olympic games.
The spying operation did favors directly for CIA fronts, while other police operations, including drug enforcement programs ‘invented’ by Gates (CRASH) made themselves useful to sanctioned CIA drug running in LA County. Ask ex LAPD Officer Michael Ruppert, who has been trying to blow the whistle on CIA drug operations in America ever since he was approached by CIA for the purpose of recruitment while on the Force. Ruppert thinks Gates was a CIA Case Officer, a CIA in place asset.
We should mention Gate’s role in the CIA mind-control assassination plot against RFK, where Gates ordered key evidence destroyed because ‘it was taking up too much room, and an ex-CIA Cop in the Command Center under Gates, ordered Cops not to go after the Man and his associate, the Woman in the polka dot dress seen earlier with Sirhan, and later seen running away gleefully saying “We did it! We shot Kennedy!” At the time, he said, “We don’t want them to get anything started on a big conspiracy.”
So then, was there any false flag ‘stuff’ of the sort going on in the LA Riots? In Fatal Rebirth, I detail some little known facts which national media censored, but which was revealed in local news reports. Things like someone parking an unlocked railroad box car full of guns on a siding near the LA Watts black community, and even helicopters dropping guns like they were beaded necklaces at Mardi Gras; like staging a violent attack on whites by blacks and videotaping it for news use… the participants other than victims later identified as National Guard in civies; like four black men caught by Police driving around town with a car full of guns and Molotov Cocktails, later released to a National Guard Major who claimed they were his Men. Here is a bit of a taste; guns appearing out of nowhere, a first-hand account.
Is Dorner intended to spark race riots to allow Martial Law?
To triumph, play the trump Ace
So one question which arises is, was Dorner to become the ‘Ace of Spades’ (the basis of my artwork) in some delayed completion of the Martial Law scenario by the military? Is some future revelation planned which will show him to have been framed and then murdered by LAPD, a tactic seeking to rekindle the 1992 hatreds all over again?
Keep in mind that in preceding months, there have been, and continue to be, a rash of massive live-fire (blanks) military Special Ops raid training exercises conducted in downtown Houston, LA, Minneapolis, Boston, Miami, and elsewhere (YouTube is rife with videos). Not once did city officials get advance warning, causing panicked civilians, some of whom took up arms just in case they would need defend themselves from (someone).
And, also in the weeks prior, the US Army leveled the 43 Acre Sepluveda Basin Wild Life Preserve (home to 250 species of birds) belonging to Los Angeles City WITHOUT NOTIFYING ANYONE. And as I write this, reports continue to come in of whole trains, as well as convoys of trucks carrying military vehicles along I-40 to Los Angeles. Someone is getting ready for something centered around LA.
But in truth, I rank its being tied to Dorner as being lower in likelihood than Chinese invasion or other, more useful martial law scenarios such as pandemics, nuclear or bioterrorism, etc. It might even be easier to stage an alien invasion, given that DARPA has developed huge stealth (radar absorbing, visually hard to see, soundless) UFO-like craft which have been test flown and sparked UFO flaps, already. So why go to the trouble of trying again something which didn’t work well in 1992?
A little more likely: something redacted from Dorner’s list of LAPD sins
If we presume that the Dorner’s material was altered, it is reasonable to presume something was removed. Something so dangerous if made public, that it was worth killing for, and framing Dorner to silence him. Imagine for a moment, that the people ‘killed by Dorner’ were people who also knew too much or who were considered weak links in a conspiracy. Or, some of them, perhaps even all, may have simply been targets of convenience because they were mentioned in Dorner’s complaints against LAPD.
Monica Quan was the daughter of LAPD Capt. Randal Quan, ret., who represented Dorner unsuccessfully (and poorly, according to the Manifesto) in hearings which resulted in Dorner’s termination from LAPD. Both Monica and her fiancé, were found shot dead in their car parked at their shared condo address. What if someone feared that Randal Quan might have shared some secret with her? Might that have resulted in targeting her, and the boyfriend in case she had in turn shared it with him?
Within minutes of the shooting by some accounts, the ‘manifesto’ was posted on Facebook, though not discovered for many hours. Open and shut case, right? But think about it. If you were going to launch a killing spree against cops… how much advance notice and tactical warning would you give them? Dorner’s alleged post included excruciating details of the threat and methods he would employ. And then, there was silence for four days, giving Police ample time to put investigative resources in motion, and putting Dorner at risk of capture. How logical was that, tactically, if how it really went down? It makes no sense.
On the fourth day, a gun battle ensued when two LAPD claim they spotted Dorner near the home of someone named in the post as likely target. One of the two Cops was grazed, but their suspect escaped. But how likely is it that it really was Dorner, given that a total of seven people known not to be Dorner were shot at by spooked Cops thinking them to be? We are talking about Cops opening fire without warning and shooting people clearly not Dorner — in the back in some cases. Dorner is a huge black man. So why shoot two Hispanic women, a slightly built white male, and a young surfer dude? Clearly, they had no real clue what Dorner looked like, then. So I must ask, did they really know it was him in that first gun battle?
Then, that same day, a SWAT Team Officer, Michael Crain, also a bad Cop according to Dorner, was shot dead, and a trainee with him critically wounded while they waited at a stoplight — attacked by someone who ran up to the car on foot. A bit curious to me that everyone killed by ‘Dorner’ died in the front seat of their car… which means someone was waiting for them at exactly the right place and time for a quick hit and run operation.
That requires exceedingly good intelligence and access to very detailed and current internal Police information in the case of Crain. I don’t believe Dorner, an ex Cop, would have that level of needed information available. Do you? It may be helpful to know that one of the favorite assassination points for CIA hits is while the target is in transit by car. Funny thing is, though, it takes CIA-style tricks to insure that a target will stop at the one stop light you deem most useful for the hit. That means more than one person is involved. Are we to believe Dorner pulled the feat off single-handedly, or would an internal conspiracy be more probable?
And who is Crain? An ex-Marine. Dorner is ex Navy, thanks to his problems with LAPD. But while he was still a Cop and in the Naval Reserves, both would likely have been ‘in the loop’ with respect to any illegal or paralegal joint military-police drills of the type mentioned above. And, therefore, we may presume both might have known something about an illegal future operation, or some dark matter associated with one already conducted. So how far fetched would it be for one to be killed to silence them and the other to be blamed for it, and to modify Dorner’s texts for the purpose?
It’s almost guaranteed to work, especially if the first killing is scheduled at a time when Dorner would have no alibi he could prove, such as being home, alone. Imagine being Dorner: you hear on the radio of the Quan shooting, and realize… ‘My FB page mentions the elder Quan in a bad light. That may make me a suspect. I’d better review my wording.’ So you try to do just that and discover you are locked out of your own account, and you recall your Credit Union account was hacked by an LAPD Officer once, already. So you just go to the page and find your list of complaints has suddenly become a confession (manifesto). You have no choice but to run, knowing Cops kill Cop killers almost always, no questions asked.
Especially run when you hear news reports that: a) some of your personal Police equipment was been found in a trash bin near the murder scene; and b) someone claiming to be you called Randall Quan to mentally torture him over Monica’s murder. And, thereby, unfolds the story we have been fed in media. But as we’ve seen, there has to be more at work here than that.
If the Dorner manifesto is a fraud, what can be believe about the official story?
Next up: 12 Frightening New Questions Illuminate the Dorner Urban Legend
Will America survive Chris Dorner?
Related articles
- Dorners ‘Manifesto’: Manufacturing a D.B. Cooper-ish Urban Legend? (proparanoid.wordpress.com)
- 5 ways the Rodney King beating and LA riots changed america (CNN Editorial)
- How not to quell riots: Los Angeles-1992 (faroutliers.blogspot.com)
Dorners ‘Manifesto’: Manufacturing a D.B. Cooper-ish Urban Legend?
What would it mean if the Dorner ‘Manifesto’ was not written by him? What if he were deliberately being made into an urban legend to cover up crimes by the real authors, including Dorner’s murder before the Cabin assault even took place?
By H. Michael Sweeney, copyright © 2013, all rights reserved, proparanoid.wordpress.com Permission to duplicate online hereby granted provided it is reproduced in full with all links and text colors in tact and unaltered, including this notice.What you will learn reading this post:
• There are many clues which make it doubtful that Dorner is the sole author, such as… • there are three distinctly different writing styles, typically standing out as if additions after the fact inconsistent with and reversing the intent of material clearly Dorner’s; • there are past tense and third-person references to Dorner as if already dead, and implied future tense when relating to the murders Dorner allegedly committed; • there are clever tricks designed to paint Dorner ‘mad’ which not even a crazy person would be fool enough to write.Was Dorner framed? Who wrote Dorner’s manifesto? Was dormer killed and his body put in the cabin?

They claim they found Dorner’s wallet and readable ID here? Sure. But that’s OK, because they also found it at the Mexican border. Sure. At least that’s what they told media to tell us when it was expedient. Image: redicecreations.com (click) – about two wallets.
I must say that when I first heard reports about the Dorner incident, each update simply seemed more and more… unbelievable. Increasingly, the possibility grew in my mind that it was a set up. I mean, you have a good, moral cop fighting a just cause against corrupt, brutal, and racist cops harming citizens, and then he’s suddenly a crazed killer destroying the very foundation of his case by brutally murdering a minority citizen… not to mention cops? And everyone signs off. Please.
That’s just as believable as conveniently finding known terrorist’s wallets with their real identities, not alias’ commonly used as a cover, among the ashes in attacks where the largest thing otherwise remaining was a mote of ash. They’ve pulled that one on us three times that I know of, including Sept. 11 attacks. No false flag here… move along, move along.
But wait! They’ve found Dormer’s wallet repleat with readable plastic ID, where? The ashes of the burned-to-the-foundation cabin? AND, they found them at the Mexican border just hours earlier? No conspiracy here… move along, move along.
The only way I could justify the actions claimed of Dorner in my mind was if it were yet another ‘mass shooting’ event sparked by psychotropic SSRI drugs of the likes of Prozac, Paxil, Zoloft, and others. These killer-makers all have murder and other violence as unpredictable side effects, and have been found to be in use by virtually all mass shooters. Ban guns? No thank you, but please, ban SSRIs and zany brain Witch Doctors who keep inventing new reasons to prescribe them like candy. Check out the facts and how SSRIs have bearing on the matter.
Sure. If Dorner was suffering depression, stress, and daily anxiety that he might be shot dead by dirty cops for ‘crossing the Blue Line,’ he might have been prescribed SSRIs for cause. But I doubt it. Because consistently co-present with the violent side effects is a lack of reason, logic, motive, or even an understanding of why they undertook violent acts, or even clear recall of them. Dorner, in his ‘manifesto,’ not only remembers, but screams a reason, motive, and understanding — flawed thinking though it be. But then, there are problems with the validity of that document… I don’t think he is the sole author.
Was Dorner framed? Who wrote Dorner’s manifesto? Was dormer killed and his body put in the cabin?
A manifesto which is not a Manifesto
Trotted out was the alleged Manifesto, which is in this case is really nothing more than a dumb-you-down term used much the same way the Davidian ranch at Waco and Randy Weaver’s log cabin were variously called an ‘enclave,’ a ‘fortress,’ or a ‘compound,’ all implying military defensive planning in their design. Propaganda BS. Reading Dorner’s work (uncensored version), you find there is no Manifesto present, at all.
No. Instead, it seems like five distinctly different texts in three differing styles as if by three different persons, and for four different purposes, not counting some political sandbagging and blindsiding thrown in for good measure. If you take away the things which seem added, all you have remaining is a plea for LAPD to do the right thing about a laundry list of wrongdoing.
1) The main body, which accounts for the bulk of the 18 page document is a detailed review of crimes and abuse of power of LAPD Officers, leadership, and events relating to Dorner’s whistleblowing and the resulting harassment and cover up — an event log. There is reason, calm, logic, and moral dignity present, and cohesive writing style. Clearly, it is the Dorner who fits the profile of a good cop and who is in control of himself. No Manifesto, it is merely a point-by-point, blow-by-blow accounting of his experiences trying to be that good Cop.
2) The introduction paragraph, on the other hand, is something else: a ‘confession’ of the murders and what sounds like an attempt to ‘excuse’ them by virtue of righteous indignation forcing acts of extreme violence as a “Last Resort,” which is indeed the title line. But were these things added later by someone else?
Particularly problematic is the writing style of this large paragraph. It is like the 9-11 cell phone calls from hijacked planes where callers spoke in ways no one ever does, revealing the calls were staged: “Hi, this is Mark Phillips, your son.” Would not a Mom know her own son, and their family’s last name? Interesting, especially since cell phones in those days did not work at altitude.
In the ‘manifesto,’ we read what seems like someone else trying to make you think them Dorner. Why would you write about yourself the way others describe you when you are not around, and generally only at your funeral service or on a death bed — in past tense?
Example a): “…completely out of character for the man you KNEW who always wore a smile wherever he WAS seen.”
Even if one actually believed that’s how people saw them, would they not more likely in such a case say; “… out of character for someone who always tries to wear a smile…” or “known for always wearing a smile…”?
Example b): “I know most of you who personally know me are in disbelief to hear from media reports that I am SUSPECTED of committing such horrendous murders…”
Why not simply say “…disbelief that I murdered anyone…”? And why even bring up media at all, especially via the expression, ‘media reports’? If I were going to say it at all, I’d simply say ‘on the news,’ but it is entirely superfluous given its assumed they had to know by one means or another… unless one is writing in knowledge that there WILL BE breaking news, and that writer is used to describing news as ‘media reports.’ That is exactly the way Cops and others who must at times cite news sources, including myself, would be used to saying it. Its use implies a different writer, one with foreknowledge of future events. Sure, Dorner is also a Cop, so he might write it that way, too, except that…
In like manner, the choice of the word ‘suspected.’ If you know you did it and are taking credit there on the spot, why use that word at all.
If written instead by another Cop framing Dorner, that Cop would be so used to referring to third-parties as suspects, and expressing ‘facts’ in certain ways, that it could have easily crept into typed text without notice. Someone writing about their own actions is not so moved. These are not the only instances, and more to the point, they only exist in select parts of the text, nowhere in what appears to be the main body (next three items) clearly written by Dorner.
3) In the middle of the main body, the accusations against LAPD, we find a curious out-of-place section, a very large paragraph, of zero relevance asking journalists to review his school years (he lists towns he lived in) to show he was never a bully or got into fights. And yet, the same paragraph describes an incident with him throwing the first and only punch and getting punished, and about continually earning more such punishments thereafter. Excuse me? It is as if someone wanted journalists to deduce the opposite of what the paragraph claims to want, and deem him not only violent minded, but mentally incompetent and unable to distinguish between the two states of being. It had to have been ADDED to get there in the middle, given a lack of context to prior or following material.
4) The passage is one of only two sections, which use profanity. It is also the one place where he derides Christianity and claims not to be a Christian, though elsewhere he presents his morals in very Christian terms. Now, I’ve read many documents similar in nature where the author was non Christian, and they made negative comments at every opportunity, not at just one point.. So I must ask:
Could this section have been inserted, and ‘addressed’ to journalists because, a few paragraphs later, Dorner also asks in the main body that journalists review a particular set of events and specific records which validate his LAPD accusations? By sounding completely bonkers and self contradictory in the first request, the second request would likely be ignored as well. This is essentially the whole de facto effect (and purpose?) of the entire ‘manifesto.’ It screams ‘ignore anything I say or complain about, because I do the opposite of what I say and am worse than those I complain about.’
Funny thing is… the nature of sociopathic and psychopathic behavior specifically includes the ability to well hide it, rather than to reveal it unknowingly — which requires them to be immune from doxastic self deception (i.e., saying you do not get into fights, then citing fights, and not sensing the paradox). Someone deliberately created that paradoxical paragraph.
5) From that point forward, it seems as if almost every paragraph of the remaining main body text has at least one sentence, or even a whole paragraph (added?) which tends to convert it from a rational, non threatening letter into a reprehensible, irrational threat. You literally feel the tone change between what came before, and the additions. I get the distinct impression someone started by adding the final section (described next) at the bottom of the document, and then worked their way up paragraph by paragraph, editing for an I-am-a-mad-man-so-kill-me-quick effect, and stopped with the middle insert we just reviewed. Save original passages, most are tacked onto the end, because that’s the easiest thing to do, and they are often very simple, short one liners — but an original writer would tend to include such key elements throughout the dialog and thoughtfully so.
Example a) I have exhausted all available means at obtaining my name back. I have attempted all legal court efforts within appeals at the Superior Courts and California Appellate courts. This is my last resort. The LAPD has suppressed the truth and it has now lead to deadly consequences. The LAPD’s actions have cost me my law enforcement career that began on 2/7/05 and ended on 1/2/09. They cost me my Naval career which started on 4/02 and ends on 2/13. I had a TS/SCI clearance(Top Secret Sensitive Compartmentalized Information clearance) up until shortly after my termination with LAPD. This is the highest clearance a service member can attain other than a Yankee White TS/SCI which is only granted for those working with and around the President/Vice President of the United States. I lost my position as a Commanding Officer of a Naval Security Forces reserve unit at NAS Fallon because of the LAPD. I’ve lost a relationship with my mother and sister because of the LAPD. I’ve lost a relationship with close friends because of the LAPD. In essence, I’ve lost everything because the LAPD took my name and new I was INNOCENT!!! Capt Phil Tingirides, Justin Eisenberg, Martella, Randy Quan, and Sgt. Anderson all new I was innocent but decided to terminate me so they could continue Ofcr. Teresa Evans career. I know about the meeting between all of you where Evans attorney, Rico, confessed that she kicked Christopher Gettler (excessive force). Your day has come.
Example b) Chief Beck, this is when you need to have that come to Jesus talk with Sgt. Teresa Evans and everyone else who was involved in the conspiracy to have me terminated for doing the right thing. you also need to speak with her attorney, Rico, and his conversation with the BOR members and her confession of guilt in kicking Mr. Gettler. I’ll be waiting for a PUBLIC response at a press conference. When the truth comes out, the killing stops.
Example c): Those Hispanic officers who victimize their own ethnicity because they are new immigrants to this country and are unaware of their civil rights. You call them wetbacks to their face and demean them in front of fellow officers of different ethnicities so that you will receive some sort of acceptance from your colleagues. I’m not impressed. Most likely, your parents or grandparents were immigrants at one time, but you have forgotten that. You are a high value target.
6) The next, closing section is a long list of ranting which, along with a concentration of profanity, is a bit of a grab bag. It is unusual in that it has countless little paragraphs aimed at a wide variety of public figures in a bouncy mixture of complaints and praise which render the writer a loon. Also in the section is a kind of long train wreck of a letter to LAPD, with dire warnings of impending violence towards other cops and their families. Much of the letter portion, if one again discounted sentences and portions which might have been added to flip meaning, may indeed have been written by a sane Dorner, a genuine plea to do the right thing, with additions again subverting them into threats. That is not how threatening people write. The nastiness is pervasive, not tacked on neatly. Sans such additions, it is no longer a train wreck, nor rambling.
7) These added things tend to be in the same style otherwise questioned in the opening examples, but with more Angst and vileness.
Example (not a typo by me) regarding killing cops; It was against everything I’ve ever was.
Wait a minute. There is a difference between me writing about me; “It was against everything I’ve ever been,” or about someone else; “It was against everything he ever was.” Those are the only two possible original sentences. Either there was a super-nova brain fart, or a partial correction was made to the later sentence. Let me explain.
Imagine someone other the Dorner subliminally mixing thought states from first to third person as well as from relating life experience of the living to past experiences before one’s death. So ingrained as natural to repetitive writing about third parties (in Police reports?), perhaps, that only a partial editing correction (‘he’ to ‘I’ve) was made, the writer still not catching the tell-tale ‘was.’ Either or both reasons for the error make it someone other than Dorner doing the writing, and further implies Dorner already dead, or sure knowledge he was to be, soon.
8) Nothing in the document would convince you Dorner was crazy as much as does the letter component. When I say rambling, I mean a completely different visible style of sentence structure (or lack thereof), with gross errors not common to the main body. Among them, are incomplete or nonsense sentences, such as the very last one, “We need to hold ou” What? The Cops were at the door and he had to stop mid-sentence and fetch some beers? And yet, again, these sentences/passages are mixed in as if additions to existent, logical, well written material. Take them away, and it suddenly seems normal.
9) And what about depression? He ‘admits’ suffering from it in the letter part. Funny thing about that is, it always seems officials in questionable deaths of the politically incorrect find a way to say ‘We had indications he was depressed…’ when they ‘suicide.’ Perhaps, but that still only accounts for the murders if he was on psychotropics, for which nothing else matches the symptoms, and still leaves the document flawed in its present construct.
10) But also in the section is a very long rambling bit which seems to be there only to serve gun grabber needs, and given that Dorner is (allegedly) now one of the ‘mass shooters’ of late, we can expect it to be one more log on the fire in that debate. How convenient.
But, uh… what should we expect, given that the section also praises the likes of both Clintons and Sr. Bush, as well as CIA’s (or Mossad’s) journalists of choice (links reveal), Walter Cronkite (Who wrote this? WC retired when Dorner was three years old!), Peter + Jennings, Anderson Cooper, and Wolf Blitzer, et. al? A Globalist’s Cop who likes a controlled media — who owns all manner of firearms, which he lists, and yet wishes were banned, and which are on Feinstein’s list, too? Please. No propaganda here, move along…
Was Dorner framed? Who wrote Dorner’s manifesto? Was dormer killed and his body put in the cabin?
Conclusion
Given the dichotomy and logic and style flipping content overall, one might choose to toss off the concerns I’ve stated and to instead presume it at simple face value as the work of a lunatic. Heaven knows media is accepting it, so why shouldn’t we? We will actually answer that question, in another blog in this series.
For me, because there is no hint of a specific or consistent lunacy… because nothing in the document as it sits should make any sense even to a deluded writer… because of the clues of alternate author additions cited… we might do well to question authenticity. If NOT authentic, then there is a conspiracy, and nothing we’ve heard about any event related to the matter can be trusted to be true. So, presuming there is a motive to decieve, is there anything suggesting means and opportunity, for someone to make such changes to Dorner’s words? Lets ask a couple of key questions which address that:
1) Where did the ‘manifesto’ come from? Answer, from a Facebook page the LA Times describes as “believed to be Dorner’s.” Huh? Three problems with that:
a) wishy-washy ‘believed to be,’ makes me wonder all the more about authenticity. I have doubts, because…
b) anyone can get a Facebook account in any name they want not already taken, and…
c) anyone who has ever had a FB account should know how easy they are to be hijacked, hacked, or accessed and manipulated by unauthorized users via password cracking. Ergo, next question…
2) How secure were Dorner’s computers and access to his Web accounts? Answer, from his own documentation of LAPD targeting for being a whistleblower; Thaniya Sungruenyos, an LAPD Officer had hacked his Los Angeles Police Federal Credit Union account from her home address, per the IP address provided by the Financial institution. LAPD ignored the evidence and covered up the event, according to Dorner.
Interesting what you can learn, when you question the official line and look more closely. Seen anyone in media following suit? No? Well, that leaves just you and me conspiracy theorists, I guess. But then, there are other people who wonder, too. Check out the last two related articles about Dorner, one of them a Police Chief.
What is the truth about Chris Dorner?
Next up: Dorner, the Urban Legend: Implications Behind a Fraudulent Manifesto
Is Dorner really dead?
Related articles
- LAPD’s indefensible Dorner pursuit (salon.com)
- Some Minorities Sympathize With Cop Killer’s Frustration, But Disavow Murder Spree (huffingtonpost.com)
- Police in California are so scared they are shooting at anyone they see in blue Nissan truck (dailypaul.com)
- My Friend, Chris Dorner (buzzfeed.com)
- Police chief recalls ‘the Chris Dorner that I knew’ (usnews.nbcnews.com)
Confirmed: Interview on Mass Shootings: Absolute Patterns Prove NWO Conspiracy
Join me on an interview on Urban Warzone in a new timeslot: Thursday, the 31st of January at 1:PM EST to be startled with answers to troubling questions about the images herein.
Note: Cyrus has confirmed the new time slot IS indeed 1PM EST. He has simply not been able to yet update his Update Jan 29: Reconfirmed and posted actual time/date. Announcing that a special image will be added to this page while on air, and removed afterwards. That image will be used to explain how the remaining graphics herein were arrived at, as well as highlight the differences between relationships between parties in the ‘official’ media/government version of a mass shooting (Aurora) and the result of private investigations in multiple states by myself and assisting field investigators. You can’t imagine how revealing it is until you see it for yourself. But its complexity goes beyond the ability to well explain in the blog and thus it will be subsequently removed. Your ONLY chance to see it is to join us LIVE, though you will be able to listen to the verbal dialog later once Cyrus posts it – sans image.That’s the day after this post: we will explain how the following graphics came to be and how they prove that mass shootings are part of a long-term plan to establish the NWO. Tune in and participate live, and have this blog post open.
Reading this post you will learn…
• That virtually all mass shootings are not random events, but part of an elaborate plan with multiple patterns only possible by intelligent design; • That these patterns manifest in many ways, including the ability to generate complex graphical images of mystical and satanic symbols on maps; • That individual key shootings (i.e., Aurora, Sandy Hook), have additional patterns of their own, all playing to a larger North American pattern of like construct; • That patterns can be so accurate as to predict likely future shooting events.This matter is too complex for a mere blog. Therefore, I will be going on air to explain more usefully, referring to the images in this blog for purposes of illustration of key points. Please review the images below and read the questions posed for each, questions which I will attempt to answer on air. Then join in the discovery, live, at Urban Warzone.
I will also be preparing a PowerPoint which I want to make into a video. Listen to the show to learn how you can not only get a free copy when it is finished, but also, a free copy of my book, Fatal Rebirth, which predicted this eventuality in the first place more than ten years ago. It also happened to predict Sept. 11 attacks, and much more.
As you review, keep in mind that random events do NOT form geometric patterns. Official Pattern Dispersal Studies by the militaries of many governments around the World investigating UFO sightings have proven that. Not one single instance reported of finding even three points in a perfectly straight line, much less forming right angles or shapes. Yet in analysis of mass shootings hundreds of miles apart, it is possible to find many in a line (and many lines form very complex 3-D shapes), and in some cases (where information details allow), accuracy to within 25 feet, and with doorway-t0-doorway accuracy.
The first question is (but among the last, perhaps, to be answered), why is it that all such plots ONLY work with such accuracy when doorways or driveway entrances are used in the plots? That alone implies intelligent design, does it not? Read on…
How is it possible that these ‘quadrant’ lines were discovered by patterns associated with just five shooting events, and yet, confirmed by many dozens more such events? How do they relate to the Illuminati NWO movement, and what additional discoveries can they reveal?
How is it possible that investigation of facts surrounding the Aurora Shooting led to an ability to locate and plot this graphic? How does it relate to Masonic Mysticism and why is it not pointing North? How is it that six more real-world roses in the Denver Area have intricate relationships to the shooting, as well (blue, purple, red, yellow lines)?

Image Three: Some more traditional Masonic symbols created from data points associated with the Aurora shooting
How are these (and other) Masonic symbols revealed by information drawn from the Aurora shooting? How can random events possibly generate such patterns unless by intelligent design? What process was used to discover them? Who is behind it?

Image Four: Perhaps the most meaningful of Masonic Emblems, these point toward a future terror event well beyond 911 scale
How does it happen that two large real-world structures would be discovered to relate to these famous Masonic emblems and point to a future terror attack? How are they interlocked, and how might their intentional existence and relationships verified in other ways? How does it relate to and predict terrorism? How is the terror event tied to mass shootings?

Image Five: Baphomet (one name of the symbol, and one name for Satan); an upside-down 5-pointed star
What is the significance of being able to plot this symbol from shooting data points? Why is it not perfectly upside down (normally to be aligned to North in ceremonies)? What are the significances of its structural elements in black magic?

Image Six: Sandy Hook is no different than Aurora with respect to finding symbols, and yet, it is quite different
WHow is it possible to get symbolism out of Sandy Hook when there were far fewer data points (actually, answer is found in the next set of images, and by the text labels in this image)? Why is the Pentagram tipped the other way?

Image Eight: The Dark Knight Rises Gotham City Map compared to real map of Sandy Hook has many shape alignments
Why are there so many curious matches between the movie showing a fictitious Sandy Hook when James Holmes opened fire and the real-world Sandy Hook? Why bother to have such elaborate symbolism in a conspiracy in the first place — why not just worry about event planning, alone?
Note: the name matches in blue and red texts do NOT represent any reason to presume any conspiratorial relationship between persons or businesses, but merely represent someone using them as landmarks for their ‘secret’ machinations. Also, the three features at the school are not ‘front’ and ‘rear,’ but at the sides. The Shed happens to belong to the Masonic Lodge. The small dot at the school is not actually ‘in the real world’ as such: it is a cement pad in the shadow of a tree which, in Google Earth, provided the visual of a round black shape presumed to exist (we must assume) by the planners. Or, it relates to something intended in the shooting plan for which we yet have any details, or which failed to take place as planned (e.g., where Lanza was supposed to die).Why does Gene Rosen have a Masonic Emblem hidden amongst ‘random’ mowing patterns in what is effectively his back yard (though ownership has not been established)? Why does his story change so many times? Why would a bunch of kids and (one version) a bus driver go PAST the Fire House to get to his house when CLEARLY, there would have been BETTER SAFE HAVEN and some hope of getting help found at the Fire House?
How did plotting the location of all ‘random’ mass shootings enable discovery and plotting of this Baphomet? Why is it slightly imperfect?
Note: The distances involved do impact accuracy because of idiosyncrasies in Google Earth plotting tools. The smaller the distances, the more accurate you can be (to a point); Sandy Hook was accurate to within 20 feet or so, Aurora (much larger scale) to within 50 feet or so. Despite the vastly larger scale, here, accuracy is less than Google Earth would allow, with several tens of miles in error where perhaps hundreds of feet should be the maximum error. There is a very interesting probable reason.
Statistics Prove Gun Control No Solution; a Political Ruse
Statistics prove gun control is no solution; gun violence is a political ruse.
Taking away guns does not stop psychiatric care-sponsored killings: pseudo science and drug industry profits are the real killer
by H. Michael Sweeney, copyright © 2012, all rights reserved. Permissions to duplicate in full with all links and credits in tact hereby granted, provided they point to proparanoid.wordpress.com and include this notice. Was Sandy Hook Shooting a multiple shooter conspiracy? Updated 4/10/13: Proof media and government don’t want you to know the truth and employ disinfo tactics instead, re ‘gun control.’ Changes and pointers to related material indicated with RED TEXT.Reading this post you will learn
1) Statistics show the worst shooters are victims of mind altering drugs given under ‘psychiatric care’ with poor or no supervision; 2) They also show that when denied access to guns, people find more gruesome means to kill, even in mass murder; 3) That such drugs have a history tied to CIA mind control research in a class I call mind control enabling psychotropics; 5) That the ONLY winner in gun control is tyranny. Who is lying about the guns used in Sandy Hook, and why?
Official portrait of George H. W. Bush, former President of the United States of America. (Photo credit: Wikipedia)
Update: The mass murder attempt in Texas yesterday employing a knife and response by media proves a couple of key points regarding the validity and reasons behind gun control efforts. Additionally, Mr. Sorento, Presidential pretender, is blindsiding Congress and the public when he gives speeches on gun control.
1) There are a rash of ‘copy me’ mainstream news articles using the same exact text/images/headline claiming that mass knife attacks are RARE according to experts. Other media have at least reworded the same message, but remain parroting an official line. This is blatantly false as the statistics show, below, marked now in Red. This blog has cited more than 20 examples of mass murders or attempts using weapons other than guns, specifically to point out that taking away guns does not stop murderers.
2) Other articles and news sources (TV/Radio) are trying to spin the knife attacks in support of gun control by offhand remarks such as ‘If he had used a gun, there would have been more deaths.” Perhaps so, but who is to say his intent was to actually kill — else he would have chosen a weapon with a longer blade. More to the point, if students had been allowed to conceal carry, HE would have been dead with reduced bloodshed of innocents.
3) Sorento gives his speeches before a 100% manufactured crowd of supporters with absolutely no opposing viewpoints allowed, This gives the illusion that NO ONE in their right mind could possibly disagree. This is result of his illegal quashing of 1st Amendment Rights by signing the so-called Federal Buildings and Grounds Restrictive Act. This Law allows Police to eject, even arrest anyone who protests on government property or anywhere near events where government officials are appearing publicly. This is nothing less than subtle disinfo blind siding. End update.
Arguing to take away guns ‘that have no use to a hunter’ is to ignore the fact that the 2nd Amendment has nothing to do with hunting, and everything to do with insuring government does not abuse their power over the people. It is intended to be a form of checks and balances to tyranny, and nothing less.
We clearly need it now more than ever, given the rapid loss of freedoms to government’s paranoiac response to ‘terrorism,’ a crime of questionable attribute, at best, and one which kills fewer Americans than results from wrongful deaths at the hands of law enforcement.
My idea of gun legislation, therefore, is to give me the right to pack a government provided SAM missile launcher and Apache helicopter, not merely some bolt-action rifle I pay for at my own expense — in part because pistols and single shot rifles do little to deter soldiers able to pick you off from a distance with their sniper rifles… and DHS is spending billions to stockpile enough ammunition to kill everyone in North America, including some 9 million rounds of sniper bullets. I have to ask why, and fear the answer is the T-word.
Why does the government want to take your guns away? Martial Law is why.
Lets be clear
No one wants to take away from the legitimate concerns of victims of senseless murders of innocents as underscored so horribly in the recent rash of mass shootings. It is right to be angry and to grieve with introspective analysis and to seek a solution to prevent such heinous acts as so painfully evident in the massacre of children and adults in Connecticut. And all Americans and people elsewhere in the World are victims, too… we all are forced to suffer some lesser anguish in our compassion for those who lost family members and friends in these events.
But please, do not become yet another kind of victim by taking the bait and blaming guns, not even a particular kind of gun, especially when inconsistencies and the very nature of official statements of evidence suggest either a conspiracy of shooters is being foisted upon us as yet another ‘crazed lone gunman,’ or lies are offered in a conspiracy within government to force gun control upon us… or both.
How, for instance, in Sandy Hook, is it possible for the Coroner to cite to media with law enforcement at his side that everyone was killed by a rifle, when State and local Police had already stated that only handguns were found in the school with the shooter’s body (first, two, then four pistols), and the only rifle found was in the shooter’s locked trunk?
There are other questions, but not as many as found in Aurora’s theater shooting. These kind of nagging ‘conspiracy theory’ questions for which the public deserves to have answers are always ignored, of course, because, ‘they are merely conspiracy theorists’ doing the asking… even when persons of credentials ask. Thus the truth, including the real cause of ‘gun violence,’ is never explained.
Why are there so many ties between Sandy Hook and Aurora?
Right in front of our eyes all along
And yet, the real cause has been right before your eyes the whole time, but deliberately veiled by corporate and government forces allied for varied agenda. I first wrote about the problem in my book, Fatal Rebirth (a four volume look at crimes of the New World Order which predicted Sept. 11 attacks, an assassination attempt which took place, and mass shootings of the kind we face, now, and so much more). I also wrote about it in my books on Political Control Technology, such as MC Realities.
A ten-year research effort for these books, as well as personal family experiences, made it all-too-clear. It is subsequently verified by statistics and other information you can easily verify for yourself: the real culprit is a thirst for power and control, both financial and political. Their weapon is disinformation, and chemicals. As such, then, it is imperative that we look both at mass shooting events as well as political assassination events; both being used to effect political change against the natural will of the people and course of governments. It is, after all, yet another form of mind control for the masses: change the mood and the will of the people with lies.
Are mass shootings sponsored by the CIA or military?
Start with the Congressional Record
If you are closed-minded about the possibility of mind control and see it as mere tin-foil hat nonsense, then you are already a victim of CIA’s Operation Mockingbird, and should skip this section because you will not wish to be confused by the facts. It might even be harmful to your psyche to learn you have been manipulated by a form of mind control called disinformation, aka propaganda. Mockingbird put thousands of CIA agents directly into media at all levels from management to reporters and anchor persons… to make sure you got all the news that’s fit to distort.
The Church and Rockefeller Commission findings of the 1970s regarding CIA mind control research further revealed all manner of inhumane MC research and non consensual testing on unwitting human subjects. It is clear that among even worse atrocities, CIA was keen to develop drugs that could control a person’s mind to the point that they would do anything commanded, even to kill themselves or others; the Manchurian Candidate, or ‘programmable person.’
There is much more I could write on this topic, but I do not wish to cause readers not open to the notion to stop reading, for there are more important things yet to discuss. I suggest Alex Constantine’s book, Psychic Dictatorship in the USA, for those wanting the gory details, and my book, MC Realities, to learn about the development of psychotropic mind altering drugs (mind control enabling drugs) by Eli Lilly under ex CIA director George Herbert Walker Bush and Dan Quayle as company executives… the very drugs we are about to see quite tied to the type of gun violence of which this article speaks.
When media controls what you think, you are a victim of mind control
Gun violence: Look at the Statistics
The first mass shooting of note in America was the Texas Tower sniper murder of 13 at the University of Texas, Austin, in 1966. From that time forward there have been countless incidents, so many, in fact, that media hardly thinks to look at the big picture, all-too preoccupied with the gory details of the most recent events. Convenient for them and government, perhaps…
…as it does not serve hidden agenda if you compare today with yesterday and learn that there is a pattern of significant relevance which is clearly being withheld from you. You make your decisions based on the colored view of blood-red tinted glasses fitted with blinders of ‘current news.’ There is a reason I call it the Military-Industrial-Intelligence-Media Complex. What makes you think ‘free press’ has anything to do with American media, a media largely controlled by less than a dozen people, exactly as the Congressional Record cited to be all that was needed to control the press. The statistics will reveal it all…
SSRI medication was developed by CIA as a mind control enabling drug
What mass shootings and assassination events have in common:
It is so rare to find otherwise, that I dare say every such shooting has many, if not all, of the same key ingredients in place: a) prior psychiatric care involving the use of prescribed mind-altering drugs (pscyhotropics, generally of the SSRI variety — Selective Serotonin Reuptake Inhibitors such as Prozac, Zoloft, Paxil, and dozens of others); b) a triggering event based on emotional stress or trauma or the curtailing of or failure in treatment processes, such as failing to take medication or overdosing; and in all-too-many cases, c) the otherwise ‘coincidental’ peripheral presence in their lives of military, CIA, or other persons, firms, or organizations associated in some way with mind control technology.
Note: there is another kind of triggering event for the Machurian Candidate style of programmed shooter, the kind of person used as a disposable patsy, because they tend not to be very effective as actual killers. The best example is, perhaps, Sirhan Sirhan, who emptied his gun at Robert Kennedy but hit him, not, according to modern forensic review: Kennedy was shot from behind, and upward. Such persons are programmed in advance to do a specific thing upon hearing or reading a select unusual triggering phrase.
Such phrases are offered once to cause them to pay attention (throws a mental switch). It is then subsequently repeated twice close together to cause them to carry out the instructions (initiates a command sequence). Interesting, then, that in Sandy Hook, that a particular Web set published the following phrase three times, once as title, and twice in the text: “Sandy Hook Lingerie Party Massacre.”
This was published on the same day as the Aurora shooting, in which the film, The Dark Knight Rises, shows a map of the villain’s attack plans with Sandy Hook (a district of Gotham City renamed to Sandy Hook for the film, for some unknown reason) as the place next to be struck. And yet, it is strange things like this which get us conspiracy theorists labeled as ‘nuts’ by media that you might be more comfortable in ignoring us, instead of thinking for yourself. How comfortable are you, right now?
The rush to gun control serves the NWO agenda for a one World government
SSRI drugs cause violent thoughts and deeds as side effects
SSRI drugs are killers, both by suicide and by murderous acts committed by those taking them. There is a remarkable summary of this phenomenon at ssristories.com, a Web site which just a few years ago listed perhaps only 50 or 60 examples, but today cites about 5,000 cases which illustrate the problem. The link sorts them by the general nature of the case, but you can sort by date or location, or any other heading.
A quick review reveals some startling examples, which I shall first outline in terms of the dangerous aspects of the drug class and its propensity for sponsoring unchecked violence in patients, and then more specifically relate to mass murders and assassinations, gun violence ahead of other forms of murder.
Why do ‘scientists’ and ‘doctors’ of excellent educational qualifications fail to realize, in light of these known side effects: every physical person has a unique physiology, DNA, and dietary makeup, and thus, it is impossible to predict the results of a given infusion of chemicals into a body where, especially in the brain, the EXISTING balance of chemical makeup is not prepared to suffer alterations with kindly result. Why then, do they persist on guessing at initial dosage levels, and then upping the ante when results are not deemed adequate, until side effects make it clear the med will not help, and then switch them to another med, and start all over again? It is witchcraft-level insanity, and it is guaranteed to have negative outcome.
It is NOT science, nor is it MEDICINE.
It is important to realize even this massive list is only a tip of the iceberg. It ONLY represents reports by family members, doctors, organizations, and other select researchers who were examining and reporting purely from the medical viewpoint. Further, as many of the reports are voluntary contributions, it represents only reports from people who happened to learn of the Web site’s existence and who were moved to report, and, moreover, is limited to reports from people who came to realize the relationship of events to the drug. For this reason, you will not find mentions of assassinations of note, such as my research indicates should be included (name ANY assassination attempt in modern American history, and you will likely find it true).
Among the reports (and a couple of details from my own research) we find court rulings and law enforcement investigative findings which frequently place the blame squarely on the drugs, and not the violent person, in some cases causing the courts not to elect punishment — even for capital crimes involving death. Here is your summary of drug induced violence:
Suicides are very convenient in a conspiracy
Let’s talk suicides:
1) Over 250 reports involve suicides only, and many times that number include suicide as aftermath to other violence, such as arson, murder, and so forth. Suicide is almost the norm after such drug-caused violence;
2) One attorney reports he has had a total of 73 calls about suicides from just one specific SSRI;
3) Indiana county study shows 41% of all suicides involved SSRIs
4) Wisconsin study shows 54% of teen suicides involved SSRIs
5) Sweden study shows 52% of women suicides involved SSRIs
6) Report shows US military suffers 18 suicides a day, 40% on SSRIs
7) Multiple reports of suicide pacts where all participants were on SSRIs
8) Another 200 questionable deaths listed which may have been suicides.
9) EVERY SSRI lists suicidal thoughts as a side effect
10) Suicide attempts often involve the most painful and horrific, and least effective means, such as blow torch, grinders, etc., or the most illogical, such as trying to jump out of an airliner, or stripping naked and wandering off into a winter wilderness. Suicide by Cop is quite popular, as are head-on and other fatal car crashes, for which statistics are likely quite under reported.
Manchurian candidate murderers are always ruled as acting alone
Let’s talk murders:
1) Over 1,200 reports of murder attempts, about one fourth of them followed by suicide or attempts;
2) Within one week of returning home, nearly a dozen soldiers on SSRIs killed their wives;
3) Methods vary widely: when guns were not available, almost any means might be employed, including additional reports under other categories, such as vehicular homicide, arson, and so forth (roughly another 100 cases). Details follow.
Conspiracy must exist if there is a cover up in place
Of interest (or no interest, really) to TSA and FAA:
1) Nearly two dozen incidents involving violence on an airplane or at an airport;
2) Individual reports of eleven private plane crashes killing 24 people blamed on SSRIs;
3) Airline Industry study reveals 100 crash pilots using SSRIs;
4) At least one hijacking was initiated by an SSRI user.
No one goes ‘crazy’ without some triggering event – contrived or coincidental
How about kidnapping and hostage taking?
1) About twenty instances linked to SSRIs;
2) Seven instances involve schools and students as victims.
When you hear ‘lone shooter,’ think ‘conspiracy cover up.’
How about arson and bombing?
1) 80 arson events, three involving schools, two events where school administrators on SSRI set fires at home;
2) 35 bombing instances, two involving schools.
CIA lies to put their own men in post of Chief, Spokesperson, and head of Internal Affairs
Other Killing Sprees?
1) Remember the rash of US Postal Worker rage shootings? Most were SSRI;
2) About two dozen instances of fast food chains, trains and busses, churches, banks and other offices, and even a country club and a nursing home;
3) More than 30 incidents at schools, about 1/3rd of which were SSRI, including virtually every event which made national or international news;
Gun control is a codeword for police state control
And when there is no gun available?
1) One 17 year old holds 20 children and teacher hostage at point of a sword. So if you take all the guns, better get all the swords, too;
2) A Mother attacks her son with a sword. See what I mean?
3) School day care center looses two children and an adult to a knife attack. After all, knives are just short swords, right? So, if you are going to take away larger gun clips, but not small, then we presume you would take swords, but no knives. What did you gain?
4) A woman laughs as she uses her car to chase down three kids at an elementary school. Alright, so now no one can own a car, right?
5) Man attacks 11 kids and 3 teachers with a machete. See what I mean?
6) Numerous fires started with intent to kill people in apartments, stores, offices, and schools. Starting to get the idea?
7) The johnstonsarchieve.net Web site lists these additional incidents (scroll to events with ‘criminal’ cited instead or ‘terrorism’) with no known tie to SSRI drugs, but are cited here because the killers had no guns:
-
- Bath Michigan man uses dynamite to kill 40 children, himself, and the School Superintendant over inability to pay school taxes causing foreclosure of his farm. So if you take all the guns, better also take all the materials used to make explosives;
- Poe Elementary playground attacked by man with bomb in suitcase killing himself, his son, the Principal, a custodian, two other students, and injuring 17 other children. See what I mean?
- 63 students and adults were burned to death by an angry student at a school dance in Goteborg, Sweden (gun control in Sweden is strict). So if you take all the guns, better take all the gasoline and matches;
- 67 teen students died from an arson attack on the dorm at Kyanguli Secondary School in Machakos, Kenya, injuring 19 others. See what I mean?
- The Elementary School of Ikeda, Japan, lost 8 students and another 13, including two teachers, were injured by a man with a kitchen knife (there is total gun control in Japan);
- 72 kindergarten students and teachers at Zhanjiang City, China, became dangerously ill from rat poison put in their salt by a competing school operator (there is total gun control in China). So now there can be no household poisons?
- That same year, 2002, two men upset with contract provisions with Number One High School in Changed, China, put rat poison in breakfast food making 195 children and teachers seriously ill. See what I mean?
- Two years later, Number Two High School in Ruzhou, China, suffers an attack by a man who kills 8 and injures 4 students with a knife while they sleep in three separate dormitories;
- And yet the next year, a man who had lost his job, again in Zhanjiang, attacks several Nansoon Middle School students with a kitchen knife, injuring 8;
- In Jikari High School, Yamaguchi, Japan, a student threw a homemade bomb made from nails and emptied firecrackers into a classroom, injuring 58 students and the teacher. Might as well do away with the 4th of July celebration, anyway, since you are getting rid of the Constitution and Bill of Rights;
- In 2010, a man killed three students, and a teacher, and injured 20 other children and staff at the kindergarten of Zibo, China, once more with a knife;
- Another machete attack took place in the 5th grade class of the Talisayan Elementary School, Xamboanga City, Philippines, killing one student, a teacher, and a grandfather of a student, and injuring 4 more students and two teachers (gun control in the Philippines is near total);
- If you wish more examples, there are thirty more at the bottom of this wikipedia link on list of rampage killers, including at least two alleged deliberate crashing of passenger jets. So let’s put TSA and the FAA out of work and ban aircraft. After all, you do want to protect people from violence, right? That really IS your motive for taking away guns, RIGHT? Sorry… I didn’t hear your answer.
If you do not own a gun, you do not own your government
And what about when other citizens nearby ALSO have guns…
…the guns they want to take away from you and me? The news of such events that does not make endless headlines because it does little to support gun control wishes of those who seek total control over an unarmed public? A mention the day it happens is as good as it gets, as a rule. Thanks for much of this compilation by gunwatch.blogspot.com:
1) A 1995 mass murder for drug effort was spoiled in Muskegon, MI, when the store owner, despite being shot four times in the back, managed to use his own gun to scare off druggies who had planned to kill everyone in his store;
2) A 1997 high school shooting in Pearl, Miss., was halted by the school’s vice principal after he retrieved a pistol he kept in his truck;
3) A 1998 school dance for Parker Middle School (Edinboro, PA) shooting saw one teacher killed, and anther teacher and two students wounded before a man living next door forced the shooter to surrender by getting the drop on him with his shotgun;
4) A 1999 gun shop owner with concealed pistol shot a gunman to the ground who had brought 100 rounds of ammo with him to ‘go out in a blaze of glory’ at, of all places, a shooting range in California (a guarantee he would get his wish);
5) A 2002 shooting at Appalachian School of Law in Grundy, Va., came to an abrupt conclusion after three had been killed and three more wounded —when two students, unbeknownst one to the other, ran to their cars to retrieve firearms and confront the shooter with threat of crossfire;
6) A 2005 shooting which started at the Smith County Courthouse in Tyler, TX, and involved high-speed pursuit, was ended because of the intervention of Mark Allen Wilson, who had a legal concealed carry weapon. This one did not end as well as the others cited, herein, as Wilson was himself killed by the shooter, who was wearing a bullet-proof vest. However, the exchange of fire allowed Police who had been kept at bay to end the matter with fatal shots of their own. This was after the shooter had already killed his ex-wife and wounded his own son, and wounded three lawmen in the melee;
7) A 2007 gunman attempting to kill parishioners of the New Life Church in Colorado Springs was only able to kill two before being shot by an armed retired Policeman who had changed his mind about going to church that day because of a previous like attack on a church in Ogden the prior week;
8) A 2007 mall shooter in Utah, after killing five and wounding four, was shot dead by an armed off-duty police officer;
9) A 2008 shooting in an Israeli School (the Mercaz HaRav massacre) was ended by shots from a student and off-duty policeman using personal weapons, who entered the school with such intent after hearing shots which killed 7 teens and one teacher, and wounded ten other students;
10) A 2008 Winnemucca tavern shooting was ended after two deaths when the shooter, while reloading, was shot dead by a patron with a concealed carry permit;
11) A 2009 workplace shooting in Houston, Texas, was halted by two coworkers who carried concealed handguns;
12) A 2009 College Park party was interrupted by two gunmen who counted ten guests and then counted bullets to insure they had enough. After separating the Men and Women one of them started to rape one of the women, but was ‘coitus interruptus’ by shots from her boyfriend, who killed one and drove off the other gunman;
13) A 2009 restaurant robbery attempt by two gunmen Anniston, AL, was thwarted when one of them threatened the life of a patron who was hiding, only to be shot dead by the customer, who had also prepared his concealed pistol for possible use. A few shots were then exchanged with the second gunman, who was critically wounded;
14) That same year, a convenience store in Richmond, VA, was robbed at gunpoint, the clerk being shot and wounded, and other patrons being shot at before the robber was shot dead by a patron with concealed carry permit.
15) A 2010 Mills, N.Y., shooting incident where the gunman, an angry customer, intended to kill six employees (he had a ‘death list’ of their names) of a cell phone store was, after opening fire on his first victim, himself shot dead by an armed off duty policeman with concealed weapon.
16) A 2012 RV park shooting incident in Early, Texas, was ended by a resident with his pistol as the gunman, after killing two people and their dogs, then held Police at bay with his scope equipped rifle;
17) A 2012 church shooting in Aurora, Colo., was stopped by a member of the congregation carrying a gun.
I leave you with two things, the first being: In Australia, where total gun control has been enacted (confiscation to establish an almost completely unarmed public), in 2011 there were STILL 94,000 shootings that took 29,000 lives… with not one civilian able to defend themselves. In America, the one spot where gun violence is rated worst, oddly enough, is the District of Columbia. Let’s compare:
There, the 2011 death rate by firearms was 12 deaths per 100,000 population, and that’s in a country where gun ownership is 89 guns per 100 adults. Compare that to Australia where it is now roughly 6 guns per 100 (est. by using UK provided figures), where deaths are 131 per 100,000. Does that sound like gun control works as proponents claim?
To get that information in media, of course, I had to go to England, because the American press won’t tell you the truth about such things. They got their information from FBI, which any US paper or news network could just as easily have done… but actual investigative reporting would not help government take away your gun, would it?
The second is this: Out of 10,650 murders by gunmen in Virginia, only 4 were by persons who had legally registered with concealed carry permits. Criminals don’t need or seek permits, of course. These four deaths by legitimate ‘gun toters’ would seem somewhat balanced by the fact that there are about as many instances, the most recent being the Clackamas Mall shooting… where persons with concealed weapons elected NOT to use their gun to shoot at gunmen engaged in murder because they did not feel they could safely do so without risking hitting innocent persons in the line of fire, or return fire hitting such persons behind them. That is part and parcel of good gun handling safety training, which all firearms owners should be required to have: my idea of a ‘gun control law’ that might actually work some good.
But personally, I’d rather have open carry… I’d even be moved to wear a six gun and cowboy hat if the 1875 Colt .45 hadn’t been stolen from my family some years back (when I did wear it in public on occasion). Open carry is a silent and untold deterrent to gun violence. In Cuba, there is no standing army, because every capable citizen serves in the Defense Force (like the National Guard), and is issued an AK-47, side arms (many people pack), and even grenades. Result: LOW CRIME, and very few murders by these weapons. The same is true in Switzerland (different weapons, of course), so it has nothing to do with Communism, that it works.
Statistically, in the Old Wild West where wearing a gun was the norm, gun violence was also relatively low… (e.g., the murder rate per capita in Abilene was lower than any modern US city, today). There have probably been more shooting victims in TV and movie westerns than in real life in the old West. When almost everyone has a gun, politeness rules; even when confronting someone in an unpleasant situation, it was done with carefully chosen words.
“SIR, I believe that Ace up your sleeve proves you are a card cheat — and the pot is therefore mine, unless you wish to object?” Given the choice, most villains would back down unless the odds were significantly in their favor… which gun control laws will surely provide them, one 2nd Amendment-eroding law at a time.
Related articles
- MK-ULTRA Links To The Sandy Hook Assault (minddefensecoach.wordpress.com)
- Guns Save Lives (personalliberty.com)
- America: Ban False Flags, Not Guns (disquietreservations.blogspot.com)
- Gun sales up, gun violence drops (wtvr.com)
- Gun control? We need medication control! (hangthebankers.com)
SPQR, PAX Amerikana: the Failing Roman Empire of the NWO
And why they must keep you afraid of (something) and distract you from the simple truth.
by H. Michael Sweeney permission to reproduce granted if in full and with all links and credits in tact, and linking back to proparanoid.wordpress.comSPQR, PAX Amerikana: the Failing Roman Empire of the NWO
At a root level, the United States governmental model is not that much different than that of the Roman Empire — especially today. Yes, I will be found to be generalizing in ways which take some liberties to make the point, but would hope the reader is intelligent enough to understand the reasoning for cause. Compare and consider:
• Both were/are based upon a Senate form of government (in Rome, they said ‘SPQR,’ which stands for Senätus Populusque Römänus — the Senate and People of Rome) headed by a supreme, all-powerful dictator with the ability to make his own laws regardless of basis in legality. We call them Executive Orders, they called them edicts from the Emperor who, in the declining years of the Empire, thought himself God. Hmm… you don’t suppose Obama… ?
• Both were/are expansionist in nature based on superior military prowess applied in an endless series of wars to ‘insure peace.’ In Rome, they said ‘Pax Romana,’ which translates as ‘Roman Peace.’ For the Romans, conquest was early on territorial in nature and garnered slaves to build and maintain the Empire and establish a comfortable standard of living for citizens. For the U.S., early conquest was territorial in nature and garnered resources to do the same — over 140 military campaigns between 1776 and 1900, and more to come. Sure. Some were and would be righteous and just, but many were and would be contrived and questionable.
• In Rome, they declared neighboring peoples as ‘warlike’ and ‘barbarians’ to justify conflicts to subdue them. In America we declared the Indians and others in the same way, and even took land Canada had claimed by threat of war (54-40 or Fight!).
But it is the declining years where the similarities are more useful to the purpose of this missive, because America is clearly in decline, too. Let’s therefore go more slowly…
• Rome’s military was a fearsome beast which cost a lot to maintain, and which could easily overthrow the government if given a reason. For that cause, it was important to insure they were kept busy and constantly rewarded. In America, the same is true. In point of fact, there was an early New World Order sponsored (the same powerful Fascist business elite as drive the NWO movement, today) attempt at a military Coup in 1934 which was thwarted largely by one man, Major General Smedley Buttler, USMC. More recently, four-star General Tommy Franks has stated that the next major terror event would result in a military form of government.
• Rome sponsored wars (‘Let loose the dogs of war!’) and allowed soldiers the reward of ‘Cry havoc!,’ a policy which let soldiers rape and pillage the conquered and keep a share in the spoils of war. In the U.S., the Military-Industrial-Intelligence-Media complex is rewarded by huge profits in the manufacture and sale of armaments and arms technology. The high ranking soldiers, themselves, reap their fortunes by taking seats on the Boards of Directors once they retire ‘with honors.’ Unlike the Roman military where one served until no longer able, most soldiers of today are short-term liabilities replaced every four years or so. Therefore, they reap no reward but that of medals for their valor, and perhaps a skill useful in seeking employment.
• In both cases, the taxes upon the people had/has become a great burden and the standard of living began to slip (brother, ain’t that the truth), and because money was harder to come by, less was spent in maintaining other important governmental responsibilities, the quality and operation of societal infrastructure began to decay, including the physical aspects made of stone, wood, and metal. That’s one reason why aspects of America’s transportation (bridges, mostly), water and sewer, and rail systems are in many cases on the verge of total collapse.
• In both cases, the people began to express dissatisfactions with high taxes and poor upkeep of civilization itself, and related woes, including the wars and the price of the military. Distraction was needed to keep the people happy. In Rome, they built coliseums and offered up gory gladiatorial massacres and theatrical entertainments. In America, they employed film and television technology to offer up unlimited access to pornography and artistic entertainments, and Grid Iron and other sports to replace bloodlust contests.
• And, in both cases, these distractions were not considered enough. The government saw that they needed to find a way to make the people see some outside threat as a greater threat than concerns over a failing governmental system. The only way power could be maintained was to instill a great fear, one so great as to justify a tighter Police State grip on the people. In Rome, it was the Huns of Germanic culture, and the Cicilian and Turkish Pirates of the Mediterranean. In truth, it was largely a non threat; the Huns couldn’t cross the the rivers and mountains which protected Rome, but the people weren’t told that.
In America, it has been a long list of like things… longer than you know (refer to this list of military actions which is from whence the counts are derived, herein):
a) In the 40’s and 50’s it was the Red Scare of McCarthyism and the Bomb which drove Nazi-style inquisitions and empowered Hoover and the FBI to become perhaps ten times as powerful as it had been before, and fostered the creation of CIA, the Department of Defense, the National Security Council, and the birth of mind control projects. We had WWII and Korea, and 24 other military actions. Television took root to keep us distracted with the likes of Lucile Ball, Bob Hope, Howdy Doody, the Mickey Mouse Club, and other mindless offerings (which I dearly miss).
b) In the 60’s and 70’s it was the Domino Theory and the Bomb (especially the Cuban Missile Crises), and ‘campus radicals’ which allowed the Military Industrial Complex to mushroom via Vietnam and 18 other military actions, plus a phony Drug War to allow CIA to profiteer, while at home the FBI and CIA ran COINTEL and COINTELPRO operations and gave us Watergate. We also learned about CIA’s infiltration and control of media via Operation Mockingbird, and how perversely they had sought after and employed mind control research. The Free Sex and drug culture kept many distracted, while the film industry began pumping out pornography to keep the less liberated distracted, and Television sold us consumerism for like cause on a scale no one would have thought possible. “Buy today, be happy (hold up box of soap next to smiling face)!”
c) In the 80’s and 90’s it was the ‘Evil Empire’ and off-shore and distant Dictators we had to fear, countered with an endless series of some 60 spats and more exotic entanglements like Iran Contra, Marcos, and Panama. The NSA made ECHELON a household word and we learned about FISA (actually a 1978 Act) secret courts that rubber stamped warrants to make political spying effectively legal — and trading of illegal political spy files by Police departments, CIA, and the Anti Defamation League/B’nai B’rith/Mossad (note: I was a victim of this!). It also brought us HAARP, the project born by a proposal ‘to control a billion minds’ by a Presidential Science advisor. Pornography escalated to video markets and strip bars are so commonplace that only live sex shows seem the unusual. But they’ve also learned they can distract us with news stories about celebrity sins such as skater knee whacking, football player knife slashing, and Royal weddings and the death of a Princess.
d) And that brings us to current history, where the idea of an endless war which can never be won was fostered; the terrorism ploy. Now this they are milking for all its worth. Police and Federal Agents are indoctrinated to the point of paranoia seeing ordinary acts as signs of terrorist behavior: you cannot take a photograph, pay for something with cash, write a school report or possess a bumper sticker which mentions Ron Paul, or cite the Constitution without being suspect of terrorism. You cannot go to the Airport (and soon, to a sporting event, theater, or public building) without being sexually molested by TSA. No remnant of the Constitution remains in tact, save perhaps the 2nd Amendment, which hangs on just enough to prevent total take over — the whole REASON it exists in the first place. And now pornography comes in over cable television, and live sex shows are becoming commonplace, and for the less prurient, reality television and the spread of lotteries and gaming casinos.
None of this makes real sense. Why should you fear a terrorist when excessive Police violence injures and kills more citizens in any given year than do terrorists in their best year (9-11 attack)? It is a bill of goods used to control you and keep you docile in order that the Military-Industrial-Intelligence-Media Complex can continue on its New World Order agenda, reaping in huge profits as they usurp more and more political control over you. They want us to fear terrorists. I say, let’s show them a form of terrorism they SHOULD fear; a free people who control their own government, as the Founding Fathers intended.
Unless you believe in and support PAX Amerikana, SPQR-style (are a Fascist), just say NO! Boycott the system at every level (be a financial terrorist): avoid banks, don’t use credit, buy used instead of new, repair instead of replace, refuse and resist GMO foods and grow your own, rely upon barter and cottage industry. Actually, there is an endless list of concerns similar to GMO. It would behoove you to learn about and resist conspiratorial NWO agenda projects like Codex Alimentarius, Agenda 21, Carbon Tax/Carbon Credits/Carbon Currency, United Nations Biospheres (and an endless array of other UN mandates), and the Canamex Highway and the North American Union via the Security and Prosperity Partnership.
Disobey government (be a political terrorist): insist on your Constitutional rights (for many of you, you must first LEARN what your rights actually are, especially with respect to dealings with Police and investigative agencies, and the court system) and go out of your way (be an activist) to do so; video Police (even if… especially if they pass a law against); employ civil disobedience and support Occupy and similar movements; write everybody in power and speak your mind; vote for no one who is not a Constitutionalist, a Libertarian, or an Independent (kill the Democratic and Republican Party Dog and Pony Show); write every media outlet to express your views and flood them with complaints over bias reporting, and write their advertisers threatening or actually seeking to boycott.
Please deem to review the 24 Planks post which attempts to highlight the changes needed in America to restore it to the strong and free country it once was. If you agree (or disagree) with any one of them, SO COMMENT on the page, tweet, share, reblog, and rate. THAT POWER is a right you should AT ALL TIMES exercise when you see something you like or dislike anywhere along these lines. How else will those who spy on us and those who (pretend to) serve us have good meter of our pulse and realize they had better back off a notch or two? If you do not express yourself, you have not learned the one simply truth: YOU are the one you’ve been waiting for to change what is wrong. Get busy, because they have an endless supply of Obamas and Romneys to take us further down that SPQR path to destruction.
Compare 1776 to 2012, and see where you really live, and decide if you are willing to accept that, or not.
Related articles
- The Fall of the American Republic? (reflectionandchoice.wordpress.com)
- America and Rome: Legends of the Fall (reflectionandchoice.wordpress.com)
- Rome’s 9/11 (reflectionandchoice.wordpress.com)
What of Early, of Late?
How vastly different life turns out for one friend compared the next… and yet how much so alike as to be frightening
Copyright (c) 1996 by H. Michael Sweeney — All Rights Reserved Permission to reproduce for non profit use granted provided it is reproduced in full and links back to proparanoid.wordpress.com. This article was written for the Oregonian, but the Editor notified me that they no longer wanted my Op-Ed submissions because they generated too many responses critical of government. So I added the Oregonian stings and published it instead in my book set, Fatal Rebirth.
posse comitatus act posse comitatus group gun control
From the local news: A Portland man was arrested today for shooting two State Troopers in the back after being stopped for a traffic infraction. Neither officer was seriously wounded, thanks to bullet proof vests. Arrested at the scene on charges of attempted murder was Phil Early, of Portland, Oregon…
As it happens with many news stories, there is more to the story than meets the eye. Sometimes, there is a story behind the story.
I knew Phil Early in a more innocent time. I knew him as well as anyone, both teenagers attending Jefferson High School. He was a very different person then, certainly exhibiting no characteristic that might lead to his shooting a female State Trooper and young man wearing a State Trooper uniform* in the back. His worst offenses in those school days were being suspended for playing hooky.
Having lost track of Phil after I went into the military, and having often thought about him over the years and the many good experiences we had shared together, I must wonder what could have brought him to this unlikely end. Having heard that he had joined the Army and was killed in Vietnam, it is a shame that it took this tragic news event to reveal the error in that information and open the possibility of our meeting again. Perhaps, under the right circumstances, I might even have made a difference in his fate. This haunts me.
posse comitatus act posse comitatus group gun control
But that is not all that haunts
Despite the outwardly heinous act and the many negative stories of Phil in the local media, there still seems much good about Phil in tact from when I knew him. He still is a caring and giving person, according to those who knew and worked with him in his last days as a free man. It is said that he helped anyone who asked and gave of himself freely, without judgment. I even understand that he had fallen victim to con artists who took advantage of his giving nature, but he had not let their greed dim his caring for or trusting of other strangers in need.
This was the Phil I knew, who would volunteer to loan his best blazer to a casual acquaintance (I had known him all of fifteen minutes when he offered it to me), or a Phil who would give his last two bucks for gas to a stranger stuck in front of the local grocery store. And that memory does not tally with the news reports of a man who supposedly, by association with Posse comitatus, has a hatred for other races. The stranger he had helped to buy gas in the early 60’s was a black man. In those times, equality was a mere dream in Martin Luther’s sermons, but already reality in Phil’s heart.
And speaking of Posse comitatus, I try not to automatically think harshly at the sounding of the name. It was the Posse comitatus Act of 1864 which protects citizens from abusive application of military against civilians in police actions, unless under martial law. This, perhaps, is why the current group by that same name does not recognize the State Police as a duly authorized Police agency.
Rather, they feel that any armed force under direct authority of State rule, regardless of the name it uses, regardless of the document of law or charter which empowers it, and regardless of its stated mission or rules of procedure, is nothing more than a state militia — a military body. As such, just like the National Guard, it is seen as a military unit subject to the Posse comitatus Act.
It was originally reported that Phil, like many Posse members, had an arsenal of weapons and ammunition. The Posse apparently believes, like many groups, that it is up to the citizens to protect themselves from the possibility of a military overthrow of the government — a thinking which, in exercise, requires a well armed and well trained civilian population. I now understand that Phil’s arsenal has turned out to be closer to the number of guns owned by the average farming family in Kansas. The description of many of these weapons apparently better matches that of “collector items” than of “arsenal.” This is closer to the Phil I remember, who liked to collect a variety of many like things, as would please his eye. In blazer’s for instance, he had nearly a dozen. He had many fewer guns.
There is one disturbing thought, however. As different as our lives must have been, and as different as our current situations seem, there is much about Phil’s late history that matches my own life. I, too, have grown suspicious of many in law enforcement, and have had my share of confrontations with them, including multiple attempts on my life by assassination.
Phil’s negative experiences might be deemed politically shaped by Posse comitatus. Mine have been as a result of investigating illegal activities of those within law enforcement — coincidentally involving illegal application of National Guard and other Federal agencies by or within police — the very thing feared by Posse comitatus.
posse comitatus act posse comitatus group gun control
The nature of fate?
In realizing this commonality, I ask what might bring us so tenuously close in our thinking and experiences, despite the many years and miles between us? I go back to the innocent times, and a possible answer seems apparent. It was the time of Camelot. We, the youth of the nation, had a man in the White House we could love and look up to, regardless of any political realities perceived by our elders. And then, he was gone, taken away in violence under questionable circumstances.
I remember well the weighty discussions with my peers at the time, including Phil, of course. Even then, the theories were abundant. As more was learned, the doubts grew about the lone gunman theory. Perhaps this dashed our innocence and planted a seed of mistrust of an armed government and its secret minions of intelligencia – a mistrust which ultimately led us each along separate but similar paths, once we parted ways at the end of high school.
Now of course, there are more facts pointing to CIA assassination than to Oswald. Despite CIA Operative testimony under oath in court that CIA was directly involved in the murder and a cover up, which necessarily and demonstrably began before the murder, media still chooses to label anyone who questions such things as “conspiracy buffs” — despite the fact that major media was present in the court at the time to hear that critical testimony.
That the CIA-Operative witness had, within weeks of the assassination, come forward to FBI with the same material, and later, also testified to the Warren Commission — and all ignored the truth, does not make us “conspiracy buffs” feel any better about media or government. Apparently media prefers to continue to publish fiction as fact rather than admitting they were blinded to the truth from day one. Perhaps government simply finds cover up the only acceptable way of life.
Come to think of it, local media and government did the same with local murders undertaken by Portland Police. Despite abundant witnesses to the contrary, media blithely published verbatim as fact, Police accounts of the shooting of a young man named Shaw — an event which I have researched to conclusions contrary to their version of the story, as documented elsewhere. There was a similar conspiracy of silence with respect to the 104th and Liebe Street Raid.
There, National Guard, including a helicopter and an Armored Personnel Carrier (APC), was illegally used in an alleged drug raid, but this author has discovered was more likely connected to the murder of Shaw. Local TV station KATU was the only station covering the raid, a matter itself perhaps telling since their former anchorman was also a former Police Commissioner and current City Councilman. Civic-minded KATU edited in new questions to field interviews of the neighbors of Liebe Street, in effect reversing their answers to make them sound supportive of Police actions, instead of condemning… everyone on Liebe Street was outraged at Police, the Guard, and KATU, but media would not air their grievances, nor would any government agency.
Surely, this angered the Posse. It angered many people, especially because of the abuse of power exhibited by Police. That summer saw Portland host the Guns and Hoses Olympics, where police and firemen from around the nation came to visit. With competitions in sniper shooting and police dog attacks, there was also likely an effort to show off Portland as a modern and well-equipped Police Department. Perhaps, but some would point to statistics to show it one of the more deadly departments, with the best way to die of gunfire by Police was to call 911 and threaten to kill yourself. They usually finished the job that those less dedicated to the deed could not. Perhaps it was such things, both old and new, that drove Phil’s anger.
Perhaps there are many from my generation who cannot let go of our misgivings and outrage from such things as the murder and cover up of our President by our own government agents. Perhaps there are many who, at least secretly within, believe in their heart that that terrible act in Dallas was the first of many dark chapters — chapters sufficiently dark to suggest a fearsome future at the hands of their authors.
That we see and deal with seemingly endless supply of similar Federal abuses and lesser version on a more local scale, does not help. Some of our generation are moved to action, while others prefer the safety of quiet contemplation. For those of us moved to act, some choose the pen, as have I, and some of us choose the gun, as apparently did Phil. Phil himself deeply regrets his actions, which he says were driven by the dominating and abusive attitude of the officer. Something, he says, just snapped within him.
posse comitatus act posse comitatus group gun control
How do we judge such matters?
I cannot condone what Phil as apparently done. I can, perhaps, understand its root cause. Society must condemn his actions. In friendship, however, I am moved to point out that this is not a simple case of gun violence, as many in media have promoted with gusto. Indeed, there is no such thing. Gun violence is not a living thing which happens of its own volition. Gun violence is the result of a given set of life experiences and circumstances. In fact, those things would conspire to vent violent action even in the absence of a gun — such as stabbings or other assaults.
Those that believe the guns are the evil root should therefore also seek to take away all the knives, baseball bats, pillows with which to smother, stockings and ties with which to strangle, etc. Each case of gun violence deserves some degree of calm analysis towards possible prevention of future shootings — not a knee jerk call for seizure of arms. In analysis of Phil’s case, I suggest his actions were driven by something which those very actions themselves could not possibly well serve.
Could Phil have thought through the emotions that drove the instant, and looked beyond in some considered philosophical light, he might have come to the same conclusion. I would suggest to Phil that his enemy was not present when he opened fire. It was not present in the persons he shot, except perhaps by some misapplication of mere symbolism. They were most likely doing a tough job in a just cause. Nor was his enemy their leaders or those that worked to create agencies so troublesome to the Posse.
No, not these things, but far less tangible things. An unhappy history with no suitable answers of blame. A docile public apathy with unconscionable surrender of power to an increasingly errant and abusive government. A growing frustration with no means of proper release. A gradual loss of freedoms to a New World Order. A reasonable fear allowed unreasonable control.
Looking back, and talking to others, I wonder: how many of my generation have traveled so perilously close to Phil’s path? How many more of us are near the line he has crossed? Too many, I fear. A legacy, perhaps, of Dallas? A signpost, perhaps, of our future path?
~~~
posse comitatus act posse comitatus group gun control
* The second person shot was, of all things, an Explorer Scout.
Under some extremely inappropriate reasoning, the State of Oregon and the Boy Scouts of America have decided that it is appropriate to dress Explorer Scouts in full State Police uniforms, sans weapons, and put them on the streets and in patrol cars — on the front line against crime, unarmed, untrained, and often, unsupervised.
This deserves another article of its own, as yet another example of the growing Police State in Portland, Oregon. Here, in Portland, highway workers, Explorer Scouts, firemen, private security firms, the National Guard, and even gang members, have all been inducted into the general law enforcement umbrella in one way or the other. One has to ask, why?
I only wish that Phil had thought to ask such questions first, and not have shot, at all.
Related articles
- New Effort To Curtail Posse Comitatus After Colorado Massacre (mountainrepublic.net)
I AM Brandon Raub; the meaning and relevance thereof
Lessons we have ignored from fallen Empires, both in real history, and in popular literature
by H. Michael Sweeney Permission to duplicate granted provided reproduced in full with all links in tact with credit to the author and proparanoid.wordpress.comgovernment out of control, a fascist Police State
As it happens, there is a Facebook Group named I AM Brandon Raub. I have joined this group and the commentary there has prompted this article. Please consider this an invite to join, as well. In specific, this post is in response to the analogy made in the Group that we should all say “I AM Brandon Raub!” in the manner of “I am Spartacus!” So lets examine that, and other reasonings:
government out of control, a fascist Police State
Who is Brandon Raub?

Brandon Raub, USMC, Ret., a Patriot detained as ‘Mentally Ill Terrorist’
Brandon, a highly decorated U.S. Marine, is the first to make national news of about 20 ex military persons targeted by the Federal government in their paranoia that We, The People, might choose to replace our government with one that obeys its own laws. That is to say, restore it to a fully Constitutional behavior. Currently, the Federal Government is outlaw not only to the Constitution and Bill of Rights, but in violation of the Magna Carta and many International conventions on behaviors relating to human rights, both in war and in peace. Don’t take my word for it as blogger, even mainstream knows it true.
On Aug. 16th, 2012, a small army of Gestapo Police, Secret Service, and FBI Agents knocked on Brandon’s door and took him into custody. Central to his arrest was Brandon’s Facebook posts, which I assure you, are far less critical of government than my own, and far less suggestive of dire future alternatives. I talk openly of the threat of revolution, Martial Law, and a Police State, where Brandon was more reserved, and says nothing but that which is patriotic and based in truth.
The difference is, Brandon is a recent retired Marine with significant combat skills, and I am not. Not just Brandon and the 20 others, but tens or even hundreds of thousands of recent veterans of Iraq, Afghanistan, and other deployments. You see, our paranoid government officially thinks ex military are going to become a fountainhead of domestic terrorist activities.
Actually, I think they are probably right to fear patriots, and have been trying to warn all concerned: where the actions of government are illegal and in violation of the Constitution, those with the training and skill to defend the Constitution and sworn to so defend it, ARE LIKELY to do so, if pressed to a point of last resort. The government has only two paths: forge ahead on their course toward a Fascist Police State and press the issue to an explosive tumult, or recant and find salvation in the Law of the Land, and restore Liberty to the ‘Land of the Free,’ a land falling well short of living up to the title.
In summary, and as proof of the problem, the following facts of the matter shall serve:
government out of control, a fascist Police State
a) Brandon was NOT arrested for what he said. He was arrested for ‘resisting arrest,’ but video of the event shows no such resistance. You cannot arrest someone for resisting arrest unless you first arrests them for some other charge. He was not given Miranda rights. He was arrested by local Police, and not Federal agencies. There was no other charge filed;
b) A County Judge dismissed the case stating the Petition for his Detention contained NO FACTS – NO REASON FOR HIM TO BE HELD. The Judge stated this was a violation of his civil liberties;
c) Federal agents still insist his posts are ‘terrorist in nature.’ Read his post, here, and you will see that all patriots are terrorists under government’s defective logic;
Note: Here is a remarkable video interview with Brandon by attorney and author, John Whitehead of the Rutherford Institute, so you can hear Brandon’s words, directly. Within it is the key section of the video of his arrest.
d) Regardless, Brandon was ordered placed in a Federal psychiatric ward for 30 days (but has been released short of that). Concerns were that he would be rendered a mental vegetable by chemical and shock therapies intended to neutralize him permanently, or at the very least become officially labeled as ‘mental’. The government believes that if you dare criticize government, you are mentally ill. That’s the same argument made (last paragraph in this link) in Iron Curtain countries to eliminate ‘intellectuals’ who opposed Soviet iron-fist rule. What does that tell you?
e) Family lawyers have been joined by legal council from The Rutherford Institute in seeking his release, pointing out that the legal document used in his rendition is problematic; that Civil Commitment Statutes are being used to silence individuals engaged in lawful expression of Free Speech. But the current outlaw government clearly has no concerns about Constitutional Rights.
government out of control, a fascist Police State
Say “I AM Brandon Raub!” in the manner of “I am Spartacus!”

Starz Docudrams Spartacus
Spartacus, a Roman Gladiator slave, led a revolt of Gladiators and formed an army of other slaves set free by force in the very heartland of the Roman Empire. In the end, as depicted in the popular film, Spartacus, the revolt was suppressed, and the survivors questioned to find Spartacus to be singled out for special punishment.
Spartacus stood up in arrogant defiance, but for naught. One by one, man after man with him stood in his stead and proclaimed as well, “I am Spartacus!” Their love and loyalty for their leader and their cause (Freedom) drove them, and so thwarted the Roman attempt. Well, “I am Brandon Raub in the manner of ‘I am Spartacus’.” I am as guilty as he of ‘terrorism’ for demanding a just government under the Law. I am as guilty as Spartacus for wanting freedom. What say you?
government out of control, a fascist Police State
Say “I AM Brandon Raub!” it in the manner of “I am John Gault!”
Ayn Rand‘s classic Novel (now a two-part film), Atlas Shrugged, shows the classic struggle between the forces of Socialism and Capitalism in their most simplistic and idealistic forms. Ayn had escaped living under USSR’s Socialist government to the U.S., where she found Socialism creeping into government, and wanted to warn us that ‘value given for value received,’ and ‘a man’s sweat and intellect are his own property’ should be preferred to ‘you didn’t build that’ and ‘those that have should give to the have nots.’
In her massive book, a work which profoundly influenced and changed the lives of many readers (including myself), a fictional plot element was the question found scribbled on walls and posted everywhere at large, “Who is John Gault?” There was no one by that name, in truth, but there was a man who lived the role, and the answer to the question was, he was the man “Who will stop the engine of the World;” to end the madness and restore sanity. In the end, those who understood and sought to right the wrongs joined with him in attempting to do so, each of them earning the right to say, “I am John Gault.” Well, “I am Brandon Raub in the manner of ‘I am John Gault’.” I want to stop the engine of errant government. What say you?
government out of control, a fascist Police State
Say “I am Brandon Raub!” in the manner of “I am a Jew!”
History is rife with examples of martyrdom for faith in the face of oppressive governments. Choose any faith you wish. I choose to focus on the Jews of pre WWII Germany, to make the point most evident in The Diary of Anne Frank. That point is best summed up in the oft quoted wisdom from Martin Niemöller, author of Gestapo Defied and, more subsequently made popular by Milton Mayer in his analysis of what went wrong in Germany, They Thought They Were Free. That book, by the way, with substitution of America for Germany, and various political figures and nomenclatures here in America for those of the Third Reich, could just as easily apply to our country, today. Are you so blind as to think otherwise? Read it if you doubt me, and know that I am not alone in the thought. But this is the quote which makes clear my point:
government out of control, a fascist Police State
First they came for the communists, and I did not speak out—
freedom of speech because I was not a communist;
Then they came for the socialists, and I did not speak out—
freedom of speech because I was not a socialist;
Then they came for the trade unionists, and I did not speak out—
freedom of speech because I was not a trade unionist;
Then they came for the Jews, and I did not speak out—
freedom of speech because I was not a Jew;
Then they came for me—
freedom of speech and there was no one left to speak out for me.
Had people spoke out… in unison… Hitler’s power would have been rendered futile, and his evil would have been exposed for all to see. But we all feel we are but an Ant against a man. But no Man could survive or attempt to war with ants if every ant swarmed as one body to defend their home and their right to exist. Well, I say “I AM Brandon Raub in the manner of ‘I am a Jew’!” I stand with my fellow men of good cause to defend their right to be and do as they deem best for them, as I would deem for myself. As if one of their own I lend my voice in unified SHOUT! What say you?
government out of control, a fascist Police State
I am Brandon Raub in the manner of “I am a TI Survivor.”
A TI is a Targeted Individual, which is to say, someone targeted by Political Control Technology (mind control). That can mean any combination of centuries-old methods such as gas lighting, dogging, and street theater (generally described as organized stalking), to modern methods such as Mob Flashing, Web stalking, and high-tech surveillance. Add to the mix bioimplants and electronic weapons which can simulate every known symptom of Schizophrenia, and you have the ultimate tool for rendering a victim a social, political, and financial zero guaranteed to be ignored by (everyone). This is particularly useful when the person is a whistle blower or otherwise knows something which could expose government corruption or evil deeds.
A TI survivor is someone who not only refuses to succumb to these tactics, tools developed and perfected, and employed by the intelligence community and military, and their corporate and other partners, but someone who stands firm and chooses to fight back as best as they can. I have the honor of saying I have stood with and helped TI survivors to survive for several decades, now. I know of no one more courageous.
Aside: Please consider to join and support the Free Will Society, because as such technologies are perfected, they become useful against anyone who dares to speak out or resist an errant government.
Now Brandon Raub is also a TI Survivor, and will likely be subject to more exotic forms of such targeting as time goes on. Well, I say I am Brandon Raub in the manner of “I am a TI Survivor!” I refuse to let government get away with mental torture and to use ‘mental illness’ as a political weapon by ‘creating it’ where it does not naturally exist. What say you?
government out of control, a fascist Police State
Who are you, really?
Who do you want to be? A victim of tyranny left standing alone, or a defender of self and of truths profound standing with others of like mind?
Who have you been waiting for? John Gault? YOU are what you’ve been waiting for. You ARE John Gault!
Do you need a Sparticus to lead your resistance? Or does Sparticus need you? Brandon Raub is your Sparticus, and he needs you! You ARE Spartacus!
Do you need to see a whole class of people targeted before you say anything? Then you are too asleep to the facts; they have already come for religious Davidians in Waco, the trade unions are decimated, the far left and the far right, and even the liberals, the Tea Party, and Ron Paul supporters… and now the ex military. All have been conveniently equated as terrorists for the purpose, and subjected to political targeting and harassment by Federal agents. You ARE of Faith!
Do you need to wait until your very mind is under attack? Again, too late. You are under constant attack through disinformation, dumbing down, and wag-the-dog media manipulation (propaganda is mind control). Worse, Command Solo flies your skies, and other technologies which parallel its capabilities bombard our cities with who-knows-what control signals. When you choose to accept sound bites in lieu of researching for yourself, or, to flip the tables, when you choose to accept some blogger’s commentary (yes, including mine) or some other Web source as valid without checking credibility (e.g., useful verifying links), then you are already a victim of mind control. Recognize the truth: You ARE a TI survivor!
And therefore say I; if you are any of these things, then You ARE also Brandon Raub!
government out of control, a fascist Police State
What say you?
Related articles
- I AM BRANDON RAUB (and so are you) (resourcemagonline.com)
- Why is Ex-Marine Brandon J. Raub Being Held in a Psych Ward and What Does It Say About Today’s America? (reason.com)
- John Whitehead Interviews Detained Marine Vet Brandon Raub (dprogram.net)
- HOT: Statement from Brandon Raub’s Attorneys (economicpolicyjournal.com)
25 Questions No One Has Asked About Aurora Shooting (pt. 2)
You can always spot a conspiracy at work… was james holmes a patsy by DOD or CIA? whenever you see evidence of a cover up in play
Our review continues from PART I, by H. Michael Sweeney, Copyright © 2012 all rights reserved. No reproduction permissions will be granted for the first 90 days. Links only, please.In review: This in-depth series of posts will reveal startling new investigative issues for the first time, anywhere. The detail required to make concise arguments on a long list of critical elements forces it to be offered in installments. You may wish to subscribe to be sure you do not miss one along the way. Doing so, you will discover:
- Three motives for making James Holmes a Patsy with Fascism as benefactor, and two possible motives for targeting Century Theaters
- Easy link access to the key-most videos and images for each critical point of evidence presented in a logical, easy to follow order.
- Reasoning there were at least three additional helpers involved in a professional black operation backed up by even more supporting players
- Introduction of an actual political REASON for targeting The Dark Knight Rises (TDKR), a reason which fits one of the proposed motives
- 25 key questions missed by almost everyone, the answer to any one of which could easily provide reasonable doubt that it was a lone gunman event
- A walk-through narrative portraying an alternate scenario which fits all conflicting facts into a workable reality.
James Holmes was a patsy Part Two
James Holmes was a patsy
If you missed part one, click here
QUESTION 8: Who warned people not to use the EXIT in theater 8, and why? Tim McGrath mentions it, and I’ve seen but lost track of one other witness who confirmed the same point. Tim says the people in 8 were panicking and trying to leave. Toward the end of the clip he states someone entered the theater from the Lobby area and warned everyone not to go outside because the shooter was outside. Excuse me? How would they know this? If there was, WHO was it, because according to this witness, shooting was still going on in theater 9? Could this be misinterpretation or misunderstanding? I’d be open to the suggest except that it also happened in theater 10…
QUESTION 9: Who warned people not to use the EXIT in theater 10, and why? At 2:50 AM Channel 9 coverage has a witness from (by deduction) theater 10 who describes events while the shooting was going on in theater 9. We really need to pin down if it was theater 10, so here is the deductive logic thread: Someone came into the theater from the left entrance, and warned them not to go outside, again while shooting was still taking place. Theater 9 would be to the left of theater 10, and theater 7 would be the left of theater 8. It would not be logical to presume someone further away from events (nearer to theater 7) to either be criminally involved or otherwise inclined or able to perceive a need for a warning. Any such person would need be closer, so it had to be theater 10. So again, who and why… would someone issue a warning without basis for such knowledge?
QUESTION 10: Why were bullets going through the walls into both theater 8 and 10? A look at the theater diagram from the Denver Post reveals that it would be logical for some rounds to pass through into 8, but there are only two ways it could have happened in theater 10. Either there was a second shooter unseen because people were attempting to hide or flee with their backs to the screen, or James deliberately turned his weapon on the wall. It is also possible any second shooter went behind the screen to appear in the dark on the far side, making them hard to see, but only if they used a silencer to completely suppress flash. This would create a distinctive sound witnesses did not report, as far as we know. Only in a cross fire situation should bullets logically enter 10, as shooting the wall is illogical. Why would James waste rounds to shoot the wall, especially since his shooting spree was ended prematurely when his gun jammed? Has anyone counted the bullet holes and compared to the half-empty magazine?
QUESTION 11: Who wore the second gas mask and used the second rifle found behind the theater? We have multiple Police statements which confirm James was found in his car and had with him in his car, a gas mask, and three guns: an AR-15 rifle, a Remington 870 shotgun, and a Glock handgun, with a second handgun and the high-capacity drum canister for the AR-15 discarded inside the theater.
Yet we have photographic evidence, Police radio traffic (18 minutes in), and additional statements to the press which prove a second mask and weapon were found lying on the ground behind the theater. The gun was at the threshold of the EXIT door, and the gas mask was found all the way at the end of the building, some 150 feet away from the EXIT and Jame’s car, where ‘the shooter’ is first reported being seen. The gas mask is part of a whole other series of questions which are the most troubling, of all. So why did James bring but not use two rifles, and two gas masks? And why does that weapon show a standard magazine (the light gray forward appendage). We were led to believe he quit shooting because his drum magazine jammed (which he left inside). Curious, as I would have thought the gun would be sans clip of any kind.
QUESTION 12: Why did the shooter not shoot the first and most logical victim? Jennifer Seeger clearly describes on ABC, a rifle being the first gun used to shoot into the air, and then it was leveled at her, but the shooter paused and did not shoot. She dropped to the ground and he instead opened fire on the crowd behind her. The clues to the answer as to why may lay in the next few questions.
QUESTION 13: Why does one witness says the first gun used was a rifle, and another a shotgun? We know he had both a Remington 870 shotgun and an AR-15 rifle with him. Both witnesses state the gun used was aimed directly at them, and both were within a couple of yard’s distance of the shooter and near to each other, and both took cover quickly. There are several other questions regarding these accounts, but the bottom line is that there is both a visual difference in the appearance of such weapons, and a stark difference between them their sound when fired. It is inconceivable that one can misidentify a shotgun as a rifle some mere feet away, especially once fired. Does the 870 shown at right look like a rifle, to you? Does the rifle look like a shotgun?
We have already examined Jenifer Seegar’s account. Here is the shotgun account by witness, Pierce O’Farrell, in a Channel 9 report, In point of fact, he was immediately shot at and wounded by shotgun, twice — once before being able to gain cover, and the second while he lay low. All witnesses seem quite believable taken on their own, but I find a shooting victim with medical treatment confirming their story more credible than someone unscathed. Why two distinctly different accounts? Again, other questions may hold the answers…
QUESTION 14: Why did several witnesses stick around for more than a day and well into the night and even the next day after the shooting to be interviewed endlessly by local and national media, to include multiple appearances on a given media outlet? I raise this question because they both tended to use the same individualized phrases and hand gestures over and over, and both emphasize a lone gunman. In some cases, the cameras seem rather far back to insure we see the gestures. In fact, one of them goes overboard in his efforts, consistently waxing emotional to the point of tears. More to the point, the conflicting facts cited above play into the matter, and may be why more than one ‘conspiracy theorist’ has suggested these are paid actors intending to Wag-the-Dog.
Here is the man, Chris Ramos, on CNN. This is him on ABC. The others are Jenifer Seegar and her friend from the ‘rifle’ account just spoken of. She is seen here on ABC, and here on CNN. Her companion who frequently appears with her but who hardly speaks, becomes a kind of ‘silent confirmation’ to cement the reality of her statements. If these habitual appearances are not a Wag-the-Dog plot element, I’d like to know what they really are? Seegar’s not being shot and not knowing which weapon first was used suggests she was not actually present — but if that’s true, then the only way she could have known about the first shot being in the air would be if she was a participant with prior knowledge of the plan. There are yet other clues of Wag-the-Dog forces in play, as seen next.
QUESTION 15: How did CNN’s Wolf Blitzer manage to so quickly have available a slick 3-D computer-rendered, fully touch-screen interactive replay of the crime, and why was it altered between airings? His show, some 12 hours after the shooting, but only a few hours after witness accounts and Police statements useful for the purpose were known, provided the most comprehensive report yet available, and put EVERYTHING from the OFFICIAL STORY into clear context. Find it here, the third video down in the group of smaller videos toward page bottom. How did they mange to have this super sophisticated technology ready to go so quickly, unless prepared in advance?
I am additionally concerned because subsequent use of the same presentation in a later program is altered. The first presentation shows only James’ entry via the EXIT and the aftermath (e.g., the kicking in the door first impression). The second shows someone going to the EXIT from within the theater to the EXIT door, depicting them LEAVING, which NO WITNESS HAS DESCRIBED, followed shortly by the shooter’s entrance (as if not expecting someone would end up recounting the man opening the door, and thus it does NOT show him returning from the door, but vanishing). Witnesses specifically describe the man from inside as NOT leaving the theater by the EXIT and a significant delay before the shooter arrives.
You see the altered version here at one minute into the CNN video. This change took place after challenges to the ‘kick the door’ claims were taking hold on the Web, perhaps best exemplified by Alex Jones’ special report to that end earlier in the day. Yet the witness reports about the man opening the door (and NOT leaving) were known to media before even the first airing. Why was it not included in the first place if not Wag-the-Dog? Why was it subsequently altered to an INCORRECT depiction, later? Yet one more possible clue follows…
Was Aurora shooting a DOD or CIA operation?
The next installment asks these important questions:
James Holmes • How did CBS News know to describe ‘buckets of ammunition’ before anyone had seen inside Jame’s apartment? James Holmes • Why did the shoot try to get into theater 10 after leaving 9 when his gun was jammed? James Holmes • Why was James so calm when arrested when the official reason is impossible? James Holmes • Why did James allegedly mail his attack plan to arrive well before the attack? James Holmes • Why did his Psychiatrist call Police when it was not delivered to insure they found it anyway? James Holmes • Why was almost everyone in James’ life connected directly or indirectly with Mind Control technology? James Holmes • And more… PLEASE: Comment (page bottom, or contact me), Rate (at page top), Share/Tweet this article. Visit my Reader Forum to promote your own cause or URL.Related articles
- Mind-Controlled Mass Shootings Don’t Change My Mind (proparanoid.wordpress.com)
- Lion Dance (a screenplay): How China Invades the U.S. via the Canamex Highway (proparanoid.wordpress.com)
- Six Dumb Arguments We’re Hearing About the Aurora Shooting [America’s Screaming Conscience] (gawker.com)
Why Targeted Individuals should not hook up with other TIs
And why they do, anyway, and almost always regret it
Definition: Hook up: reside under the same roof for more than a week.
Copyright © 2012, all rights reserved. by H. Michael Sweeney, author of MC Realities: Understanding, Detecting,and Defeating Mind Control and Electronic Weapons of Political Control Technology. Permission to duplicate on-line hereby granted provide it is reproduced in full with all links in tact, and links back to proparanoid.wordpress.commind control psychotropic weapons DEW voice to skull
The first thing to understand is who we are talking about; Targeted Individuals. The term is military in origin but is used by the intelligence community and law enforcement. That’s apt, because even though the kind of TIs I’m talking about are not a bona fide target of these groups for some justifiable cause (not terrorists, not criminals, not enemy spies), the technology and methods used in their targeting were developed by the military and intelligence communities, and corporate and collegiate partners.
More critically, the attacks they suffer as result by electronic weapons, gas lighting, street theater, dirty tricks, and psychological warfare, and so on, are more often than not at the hands of those self-same developers, as well as members of law enforcement. Not officially of course. There is no such thing as the boogeyman. Ask any Judge, Psychiatrist, Congressman, or Lawman. They seem content to overlook the fact that the whole of the Political Control Technology employed is applied primarily for the purpose of making the victim seem to be a Paranoidal Schizophrenic.
They certainly overlook the mountain of official government documents and other evidence that every symptom of Schizophrenia can be simulated by such technology.
Enough on that. Well, not really, but to get more, read my book, MC Realities, which is the only self-defense book on topic on the market I’m aware of. What we really want to talk about is the tendency of TIs to want to hook up with other TIs for what they hope will provide a means of mutual support and protection. By ‘hook up,’ of course, I mean close interpersonal relationships which include sharing of housing, with or without romantic intentions.
Well, yes and no to that notion. While there is some useful psychological support value in having someone of kindred spirit to share in burdens born of like difficulties, as a rule (there are exceptions), I have long advised against it in the strongest of terms.
mind control psychotropic weapons DEW voice to skull
Here’s why; what I see as the risks involved.
1) It decreases security rather than increasing it, as it can result in each TI gaining as new enemies those involved in the targeting of the other TI(s). But that is not the worst of it, because where that happens, it becomes such a tangle that if someone like myself comes along to try and resolve the issue, there are suddenly too many clues to sift through to determine anything truly useful in defense or offense — a matter which is tough enough to resolve with just one set of attackers.
2) It almost always turns out that one of the TIs is accused of being a perp (perpetrator) disguised as a TI in order to get closer in and do more damage. More likely all will end up accusing each other, even where no one is guilty. It is the nature of the natural paranoia generated by being targeted which fosters such fears, and any such fears, when unfounded, always grow until some bit of circumstance seems to tender hard evidence when it may simply be coincidence. But it is also true that many times, one or more of the parties actually are perps.
3) Any defensive strategies tend to become doubly complex and twice as difficult to mange to good end, which means each TI is neutered somewhat in the effort. There can also develop bickering over the best approach which further hampers such efforts.
mind control psychotropic weapons DEW voice to skull
There are reasons why my advice is ignored, and of course, only a small percentage of TI’s even get to hear my advice. For every TI we hear about, there are many, many more who are afraid to tell anyone out of fear of being termed mentally ill. Too — I’m not exactly a household name, so not all the ones who do come forward know I even exist. But here are the reasons my advice is ignored by those who do get to hear it:
a) They are so emotionally victimized that the temptation to find and leverage some small hope for kindred support and understanding overrides logic. In like manner, they are so depressed by the constant lack of privacy and security that the hope of increased security from a helpmate also overrides logic.
b) They foresee a possible savings of money through shared expenses, money being something all TIs tend to have too little of thanks to the targeting, which commonly involves financial dirty tricks such as repeat sabotage of vehicles, cancelling insurance policies, and worse, including getting them fired with rumor mongering.
c) They often feel they have ‘been around the block’ as a TI long enough to spot a perp and have some confidence they are insulated from risk. Wrong. Almost always.
mind control psychotropic weapons DEW voice to skull
A Simple but Tragic Case Example:
A TI client who had suspended my services for a time elected to hook up with another TI. The basis was that they were both ‘on the run’ in hopes of evading targeting, or so it seemed. My client was already mobile because of a need to travel in work duties (a respected person of useful credentials in their chosen field, as it happens). The other TI claimed to have been forced to vacate a Safe House provided by FFCHS (Freedom From Covert Harassment and Surveillance), claiming it unsafe there, and of poor sanitary condition. That was far from the true reason, but there was no means to check it out, and the client did not even attempt it, presuming in error anyone coming through FFCHS must be a legitimate victim.
So it was concluded of mutual benefit that they might travel together and share expenses, defenses, and information about their individual targeting. The first few days went well enough, but before a week had transpired, it ended in disaster. The short version is that it appears the refugee from FFCHS was not only a perp, but a sadistic psychopathic criminal of another sort: he produced a gun, made threats, and later raped his companion multiple times, and then ran off owing money. This took place immediately after I was invited to meet with them, it perhaps being my presence which spooked the perp into flight. Perhaps not.
But he had also gotten access to her email and sent out email in her name, presumably to sabotage relationships, and there was an incident which seems to have been aimed at thwarting me from providing helps, perhaps intended to scare me away (a third-party companion player showed up at our agreed upon meeting place, and their car was later in the day found in my personal parking spot where I live). It did not frighten me (read my books and you will see I’m quite foolish about things which should perhaps frighten me).
But it did not help my being involved, either, as the refugee also tried to convince my client that she should no longer have anything to do with me. After it was made clear our relationship would continue, it was that same night that it all went sour — as described above.
mind control psychotropic weapons DEW voice to skull
Summary lessons learned (hopefully)
Regardless of good intentions and hope, the risks of hooking up for mutual advantage is generally a risky affair. I only know of one instance where it worked out long term, and there were unusual circumstances which included additional third-party, non victim helps. These acted like a checks and balances to help get them over the rough spots. And to repeat, I’m talking about the natural growth of suspicion of each other which transpires even when one of them is not a perp.
By all means, collaborate and share information on-line. Even meet in groups, large or small, to share information and give emotional support. But please try to avoid commitments to share living space and all that goes along with being targeted. It is a trap no matter how it plays out, one which leaves both sides feeling betrayed, hurt, and more frustrated than before, or one side victimized yet again to the same end.
PLEASE: Comment (page bottom, or contact me), Rate (at page top), Share/Tweet this article. Visit my Reader Forum to promote your own cause or URL.
mind control psychotropic weapons DEW voice to skull
•••••
I would also like readers to know about the Free Will Society to Aid Targeted Individuals, organized on Facebook as a Group. Please give it a visit. If it helps, also please know that I offer a free Helps Kit, sample newsletter on Political Control Technology, and free 30 days on-line consulting to Tis. Contact me.
Web Walker: How to Bypass Internet Surveillance or Even a Total Web Shut Down
A simple solution: establish a Web Walker, your own Internet emulation to totally bypass the existing system — and its snoops
By H. Michael Sweeney, Copyright REMOVED. Permissions to duplicate granted provided it is reproduced in full with all links in tact, and referenced to the original article here at proparanoid.wordpress.com. Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web Shut Down Updated Nov 26, 2012: Removed copyright and some text changes which do not impact conceptually, other than it is in preparation for creating an Open Source project to make a real operational Web Walker network available World wide. Additions introduced with RED TEXT. Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web Shut Down This is a serious discussion of modest technical complexity which will take about fifteen minutes to read. If you bore easily with technospeak and are just curious, don’t bother yourself. Read this short, fun piece, instead, as it has more entertainment value. And then come back when you are more serious about preserving your freedoms in the face of the NWO.The FBI, CIA, DIA, DHS, NSA, and dozens of other agencies including the Federal Reserve spy on internet users, and it is going to get much worse, SOON — perhaps to include martial law and suspension of the Constitution in the major next terrorism wave.
For example, CISPA and other legislation continues to threaten to remake the Internet into a completely transparent spying mechanism, or worse, it seems logical to expect government to shut these systems down altogether in a Martial Law or other declared emergency, or if there is a 99% Occupy on Steroids event, or worse. Since the attacks of Sept. 11, the government has created more than 260 new Agencies, the bulk of which are geared up for or in support of spying on you and me, what we do, say, and think. King George-style Sedition laws cannot be far behind, and have already been proposed by some Congressionals, though defeated if actually reaching the Floor. Currently, offering this advice is legal, but you can bet government snoops don’t want you to know about it.
Survival in the future, more than ever, will depend on access to key information, and when government actions shut down or seek to have unlimited access and control of communications… you don’t want to be just another person without a clue while serious risks to your safety unfold nearer and nearer to you; if they shut down the Web, you can bet TV, phones, and radio will also be curtailed except for ‘official’ propaganda. And when it comes back on line, it will be a totally new Internet in terms of the threat of surveillance. Read this review of what to expect under Martial Law and you will better understand the concern. I WILL NOT GO PEACFULLY INTO THAT DARK NIGHT, for it is born of pure evil, that yet more evil may be undertaken, and I am not willing to live within an evil construct with no way out. How say you?
Hillary Clinton: “We are loosing the (dis)information war (with our citizens, thanks to alternative media outlets).”
These Hitlerite Police State tactics are being undertaken by a paranoid government in the name of combating terrorism, but the simple truth is, they do not fear terrorists, but the actual truth itself, and those who seek and share it. Terrorism is an invented enemy of political-control convenience that does less harm than unrighteous violence dished out by out-of-control Police. As clue this is true, very few of the hundreds of Federal Agencies and new weapon/surveillance systems/laws are aimed directly at Terrorists. No, the focus is ALL on citizens.
What better way to combat truth and free exchange of ideas and information than through the Internet, and by it, back doors into our computers, phones, and game systems by that same digital interface? You can no longer depend on the Military-Industrial-Intelligence-Media Complex to maintain such systems, provide you with protections of your privacy, or even uninterrupted access. Its time to become your own Island of communications safety. Become a Web Walker ‘Node’ (WW node). Not just because of privacy concerns, but also in case the government moves to shut down or replace the Web with a snoop friendly version… or even a natural disaster which disables whole portions of the current WWW.
There’s nothing particularly novel about the idea (but by all means, feel free to credit me with accolades). It is not patentable, but even if it were, I would freely put it in the public domain. Also feel free to come up with better solutions; I claim no superior skills or knowledge which cannot be surpassed by the likes of an Anonymous hacker or a software or hardware engineer, or every day super geek. It is merely a nuts and bolts solution to insuring privacy and continuity in the face of an overbearing Big Brother mentality.
To effect solution which protects privacy, truth, and unbroken access requires three things. Some hardware you probably do not already have, but may easily obtain; some like-minded people willing to work with you within a defined geographical boundary; and a willingness to take a little more trouble with your communications than you may be currently used to dealing with, though much of that can be addressed by those who know how to create automated scripting. Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web Shut Down
Web Walker Equipment:
Most of us employ a router in our home to service more than one computer, game system, or a laptop that roams throughout the house and perhaps even the yard, etc. A typical router can service four or five such devices to a distance of a couple of hundred feet. When the signal goes through walls and furnishings, the maximum distance drops notably, but some of us may have purchased booster antenna systems to compensate the signal loss. What we need to do is think bigger, and more powerful, and to establish cooperative communications ‘nodes’ to extend range beyond our individual capabilities.
As it happens, Apple Computer has our back; visit the Apple Store for more information and technical description. Their Airport Extreme router is reasonably priced (can be purchased refurbished from Apple for as little as $130, and new for about $120 more — I’ve bought used ones for as low as $50). Take care not to confuse with the Airport Express, a lesser unit.
The Extreme does not care if you are using a Macintosh or a PC, a game system, a smart phone, or anything else you might want to hook up to it, including Apple TV, a shared printer, or a hard drive for automated backup for all connected users. Unlike most systems which operate in just one frequency (2.4 Ghz), it also uses 5 GHz, where there is less signal clutter in the radio environment. That improves both range and prevents data errors that slow things down.
But what makes it especially useful is its power and capacity, and it offers a built-in range extending feature. As it sits, it can handle up to five times the data throughput of most routers, and does so for twice the distance of the best of them (802.11a/b/g standards), and is less subject to interference from other RF sources. As an example of range, I’ve enjoyed a useful signal at nearly 500 feet away, in my car, with several homes and lots of trees and power poles between us. Best of all for our purposes, it can accommodate up to 50 users simultaneously.
And, like Macintosh computers, it has superlative security features to prevent unauthorized access, which will be critical. It is indeed extendable with the ability to add up to four ‘bridges’ (more routers) in daisy-chain fashion (or a radial layout) to essentially quadruple what is already an impressive operating envelope, or to resolve difficult signal penetration issues within a building. Bridges become range extension nodes in your WW network; a Bridge Node (B node) to allow roughly 50 more users. Lesser Apple routers also could be used, or perhaps competing units, but with reduced performance/capacity. Here is a YouTube video on setting up wireless bridging.
Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web
Booster antenna systemsWhen you couple any node to a booster antenna, you can enjoy phenomenal range. Apple has designed these units with an internal, concealed omnidirectional (all directions) antenna and provides software that controls the gain and other aspects which can improve nominal performance. Some Extremes feature a jack for adding an Apple made booster antenna, but it is also possible to modify any model using instructions found here, and a $20 adapting cable that works with any standard booster system. By itself, the unit has a 20 db rating, though apparently offering better performance than competitor units with similar ratings. Were you to double or triple that with a booster, you theoretically double or triple the distance. Only the surrounding or intervening environment dictates resulting performance (e.g., trees, structures, hills).
Boosters come in two flavors: omnidirectional to boost coverage area around you in all directions, and directional, to extend range through an arc of about 15-30 degrees in a given direction. I am told you can actually use both omnidirectional and directional boosters simultaneously with a simple signal splitter. They are available for both indoor and outdoor placement (outdoor increases reach), but an outdoor unit can be concealed inside and aimed through a window or attic vent, which is highly suggested to avoid visual detection by Men in Black.
Because networks can be ‘named’ and selected by name for use, you can have any number of WW nodes, each with or without bridge nodes, each with or without their own booster for a given directional or omnidirectional need. Any one of these can be simultaneously connected to an existing ISP for ‘normal’ use, or can be operated as de facto Web Walker ‘ISP’ in a closed network, and easily be reconfigured (plug and play, or in this case, plug and share) at will.
Directional systems usually rely upon what is called a Yagi antenna design, which may or may not be enclosed in a can or tube, or small triangular housing. Where the signals going into or coming from a Yagi are additionally passed through an amplifier, phenomenal range can be achieved, though if building your own ‘black box’ solution, you must be aware of FCC guidelines and limitations on signal strength. But by way of example, an amplified Yagi system can be so powerful and precise that it is best used on a tripod with a rifle scope to center it on target destinations miles away. That is how the WW can be made to reach users well into the countryside, where line-of-sight access is available. By such a method, it would even be possible to link nearby communities in daisy-chain fashion.
Booster systems start in the 9 db range but you can find them up to 49 db, which can mean up to 1,500 feet between bridges, give or take. That’s well over a mile in total distance if employing four bridges, and about 3 million square feet of user coverage. Claims of distances for Yagi systems of up to 4,800 feet are out there, but don’t get sucked in by anyone who sells a product specifying distance — it’s a disreputable tactic that usually involves a sham. Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web Shut Down
 Like-minded people to connect with:
Like-minded people to connect with:
That’s the whole point, right? Such a system is not intended to replace the Internet for everyone who is currently subscribed to an ISP. That would cause bandwidth issues beyond the current state of the art’s ability to inexpensively cope. It is to allow people of common need and support to stay in truly confidential touch and securely share critical information which would otherwise be deprived of them, or obtained from them surreptitiously without permission. So you pick and choose friends, family, coworkers, compatriots, and patriots whom you think best meet your needs. That does not mean you cannot also have others join the network to enhance functionality. Here’s how you reach them…
First, map out the locations of people who should be logical participants and who are interested in joining your WW. Some may already be ‘in range.’ For those further away, consider directional antenna or bridge solutions, or a combination. For bridges used to fill in the distance gaps with useful signals, seek out the most logical locations for placement of bridges, and see if you know someone there, or could make friends with someone in the area. Explain your goals and see where the dialog goes. Hopefully you would find them kindred Constitutionalists or Activists at heart, or otherwise willing to house your bridge unit and keep it powered up in exchange for benefits, and perhaps join your WW node or even contribute toward costs.
But bridges merely render you and up to 50 other persons within range into a relatively small private local-area WW network, and may still fall short of enough range to reach intended persons at greater distance. But there is even more we can do. Because each individual node operator/user can have multiple named routers and select which is in use, any user can establish their own WW node and serve as a relay station from one such node to another… and if needed, to another, and another, ad nauseum.
By this means, a whole city can be encompassed. Multiple routes or paths from point A to D via B and C are also advised so that system integrity is maintained if a node is lost. There are additional security-related route redundancy considerations discussed shortly.
I’d suggest an ideal WW operator’s site would look like this: three Web Walkers with directional boosters just for distance in three differing directions, and one omnidirectional for those around you, perhaps a system you make available to all neighbors who apply, over time (a move considered a security risk, at best). I think of it as being triads of node triads in a pattern which blossoms outward like some kind of Dandelion seed puff covering the whole of its core being. But there are many environmental reasons an actual geometric pattern is not likely to result.
And at the end of those routes, that is where you want your most loyal of kindred spirits, because they should do the same, and likewise at the end of their otherwise completely separate routes. Keep in mind, too, that a bridge operator can likewise add additional units and establish their own WW node while remaining a bridge element in yours. It is completely free form to need for each individual node operator/user. Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web Shut Down
Changes in how you communicate:
Each WW node operator/user would be key to facilitating communications beyond their own node’s connected users (other nodes). Everyone on their own node (also true of B nodes), which functions with the ease of a local network, would become a peer-to-peer communicant party with others on that node; it is a local Intranet. They would be able to easily send information and files to anyone else in that same network, or even make portions of their computer files directly available to select or even all other communicants, with or without password requirements. That is, in fact, how they could mount a personal Web site for access by others, essentially serving as their own Web host system. Nothing new in that.

Google Earth Image: An excellent resource for planning WW layouts as it can show terrain and building heights to the planners advantage.
Martial law, Police State, revolution, natural disaster, Internet shut down, CISP, PIPA
Add some Intranet email software clients or peer-to-peer clients and you get some ease of communications which would seem rather normalized to the way one uses the Web, currently. But as for Web Walker-based user Web sites, the actual Internet would be out of bounds, or should be, to prevent assault from spyware or worms designed to discover and track Web Walker activity.
One simple solution is to buy a used Macintosh, which is generally impervious to externalized attacks of this sort, and which would be safer for use on any compromised Internet government might control. Go ahead and mount Windows and your PC software on it so it behaves like a PC if that’s what you are more comfortable with. In a way, a Mac is often more ‘PC compatible’ than many PCs, anyway. Protect Web Walker best by complete dissociation from the WWW by use of a dedicated router for the actual Internet. You can easily bounce back and forth between WW and WWW sources with a few mouse clicks, and copy and past may prove useful.
But where an elaborate WW node (e.g., multiple routers in multiple directions) is employed, the potential exists to relay information (email or Web site data) between any two adjacent WW locations. And there is no end of relays possible. All that is required is a localized addressing scheme, which is easy to come by because each server has a name, and each user an intranet IP address unique to the router. So whomever is the central-most party of a Triad (the designer, if you will), would determine the name of the WW router for addressing purposes, and track THAT node’s user IPs. So to send data or request data to/ from an outside Web Walker, would only require that you knew the address; IPnumber@router name. Thus whenever a new router (node) is to be added to the greater WW network, a proposed router name should be submitted to the network to allow people to indicate if it was perhaps already in use at their end.
As in the real Internet, you should never share addresses, as that could compromise user privacy expectations. That means no one knows exactly where on the greater WW network a given user is located. So to send a request for a ‘Web page’ on the WW network, or an email, one uses email (I suggest using PGP – Pretty Good Privacy encryption because it employs a sender/recipient decryption key scheme so that only the recipient can access) to send to the WW node operator. When the operator gets it, he compares the address to those listed on his own node(s), and sends it on if the recipient is one of his ‘flock.’ This could be automated with minimal software.
Otherwise, he switches his computer over to each of the other WW nodes which link to other, distant WW nodes, and forwards the file (also subject to automation). In this way the message goes everywhere until it finds the right operator, and is forwarded to the specific recipient. If a Web page request, the recipient sends an email back containing the Web markup language code for the file, along with all embedded images, videos, etc. This may require an email client which has no file size limitation, such as a virtual private network email client, which is a good choice, anyway, for management of email by a node operator.
The flaw in this plan is that the designer would need to spend a considerable amount of time looking at data flows and switching routers and forwarding as needed from one node to another. That could prove a severe issue in a major City environment well connected to large numbers of individuals. Therefore, two additional bits of advice are offered. Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web Shut Down
1) to some degree, restrict membership to those persons of value to the localized network. That means people who truly are kindred spirits, or who have useful resources or skills, such as weapons, food, or whatever is appropriate for assuring mutual survival. This is not our Children’s Internet;
2) Users should limit communications to serious needs, only. You don’t go ‘surfing,’ and you don’t send spam, or watch movies, porn, play games, etc.
3) Employ scripting, utility software, or write custom software to handle as much of the work load as possible. Macintosh has system-level scripting built in, as do many kinds of Web utilities, and Linux/Unix systems are also quite flexible in this respect.Web Walker: How to Bypass Internet Surveillance or Defeat a Total Web Shut Down
Men in Black
Naturally, the government will not like this idea very much. Who knows? They may label me a terrorist any moment for having published this idea. Welcome to do so if they want a bit of bad publicity. I’m sure I’m already on their list, anyway. But their concern means that you would likely want to hide your units and shield your rooms to prevent so many strong signals from screaming, ‘Here I am!’ Better they should see only one signal at a time, if possible, and not easily ascertain its point of origin. Ask me about Primus Pick Proof Locks for your home, if truly worried about Men in Black snoops.
Again, it would be wise to establish multiple routes between critical or important users or resources in case one route is compromised or suffers technical failure. Any two adjacent WW Node operators would know each other and would become aware of any such loss of service (again, to play safe, shut down any signal to it) and investigate carefully before deciding what to do about it (e.g., replace the route, help repair, etc.)
Unless they specifically passed a law or edict against, even if discovered, you should not likely be in too great a danger except from confiscation of equipment and questioning. Likely, the files on your computer would be a greater risk of getting you into trouble if they felt like pressing a given matter. Spare equipment, secret locations, and escape tunnels may be called for in the worst of times.
And should revolution come, I have heard it said regarding one such revolution, “It was the best of times, and the worst of times…” But in such a case, being able to communicate can make a bad time the best possible.
Update: Due to popular response and interest, I’m going to attempt to launch an Open Source Project to make Web Walker real. The first order of business will be to come up with a new name: at the time of first posting just a few months back, there was only one Web Walker out there, a Web authoring service, and one product (a one word trade name). Now, however, there are nearly a half dozen Web Walkers of all manner since then, for some reason. Why, if I was paranoid, I’d think it on purpose~ 🙂 Ideas anyone?
Click the FOLLOW button at very page top to learn more about the Open Source Project, or better yet, especially if wanting to learn about the may options or ways in which you can participate, use the CONTACT link at page top to express your interest. There will be more posts on the Project, to include many enhancements such as an inherent mechanism to simulate social networking and search engines free of advertising, spying mechanisms, and useless distracting fluff. THANK YOU for taking the time to learn about Web Walker!
PLEASE: Comment (page bottom, or contact me), Rate (at page top), Share/Tweet this article. Visit my Reader Forum to promote your own cause or URL, even if unrelated to this article.
Related articles
- Would you give the government remote control over your router? (arstechnica.com)
- Ron, Rand Paul: Get Government Away From Internet (personalliberty.com)
25 Questions No One Has Asked About Aurora Shooting
Answering them reveals there was no lone gunman
A careful in-depth review by an author who specializes in crimes of the NWO and Intelligence Community, to include MC, by H. Michael Sweeney, Copyright © 2012 all rights reserved. No reproduction permissions will be granted for the first 90 days. Links only, please.This in-depth article will reveal dozens of startling new investigative issues for the first time, anywhere. The detail required to make concise arguments on a long list of critical elements forces it to be offered in installments. You may wish to subscribe to be sure you do not miss one along the way. Doing so, you will discover:
- Three motives for making James Holmes a Patsy with Fascism as benefactor, and a possible motive for targeting Century Theaters
- Easy link access to the key-most videos and images for each critical point of evidence presented in a logical, easy to follow order.
- Reasoning there were at least three additional helpers involved in a professional black operation backed up by even more supporting players
- Introduction of an actual political REASON for targeting The Dark Knight Rises (TDKR), a reason which supports one of the proposed motives for choosing James Holmes as Patsy
- 25 key questions missed by almost everyone, the answer to any one of which could easily provide reasonable doubt that it was a lone gunman event, or that James even pulled a trigger
- A walk-through narrative portraying an alternate scenario which fits all conflicting facts into a workable reality.
James Holmes was a patsy Part One
James Holmes was a patsy
Introduction: my credentials and methods
The reader, if to have confidence in my commentary, should know my credentials. I write this as an author of seven books (proparanoidpress.com) generally upon topics which relate directly in any analysis of the matters in Aurora. That includes the topic of Political Control Technology (PCT — mind control), which mainstream media and government still refuses to acknowledge as a real and valid topic. This they do despite the blatantly available facts which abound, even to include evidence uncovered by Congressional Investigation. My full bio is available here.
But before we get into the meat of these matters, I want you to please stop and see this one video which is by far the most emotional and heart tugging (in a good way) of witness accounts: Jamie Rohre, telling how he and his family were under fire, and the frantic events and steps taken while worrying about his infants and their Mother from whom he had become separated. They were apparently not married, but the interview reveals that once reunited in the hospital, he immediately proposed, and she accepted. WORTH A WATCH. Good can overcome tragedy when you let it.
James Holmes was a patsy
Motives and Political Hay vs. Justice
I would hope my feeble efforts would raise serious questions for not just citizens, but also in the minds of officials; questions which a moral person should rightly feel in clear need of answering if justice is to be served. Questions which might lead any legal defense team working for James to a useful defense proving him innocent. Unfortunately, I have no reason to believe that is the goal of either the Court or the Police in this matter, and suspect any defense will be guaranteed to be marginal, at best. As common in all prior mass shooting events, assassination plots, and terrorist events, political hay is more important than a statue of a blindfolded lady, or her set of scales.
Motive 1: The most popular motive talked about the Web is the most obvious; the ‘trade your rights for security’ myth, a key step in order to allow a tighter Police State grip on the people. The hay in mass shootings and assassination plots is gun control, which is the key-most step on the way toward a Police State, and the only way it could long survive or even come to power in America. The proof of these remarks is perhaps easiest to illustrate by the ‘coincidence’ that in every shooting or terror event, Congress just happens to have in hand legislation ready for quick approval (but not reading or due debate) which provides a good deal of such hay for their New World Order horses.
In Aurora, it would be found in three forms, the first of which was, rather than a new law, a need to discuss the United Nations Treaty on Small Arms. Constitutionalists and gun owners fear the Treaty would force the 2nd Amendment to be repealed and guns to be confiscated, the approval of which was scheduled to be determined in a matter of mere days after the shooting. Fortunately, the effort failed and the treaty was not signed, but that does not end the matter; the U.N. has simply rescheduled for reconsideration to give them time to attempt to make the treaty more appealing (the US was not the only country to refuse it), and a new a sales pitch (more mass shootings, perhaps, such as the Temple shooting in Wisconsin?). I have already screamed my warning thoughts on the gun-grab topic in a series of posts cited at the end of this post. For the best overview of the treaty with both sides of view, visit the Judge Ben C. Green Law Library.
Motive 2: Less commonly discussed, but also logical; the Web is flush with stories stating James’ Father is a whistle blower set to testify in a Federal matter which would, if found damaging, be a potential motive for using as Patsy, his son. His father developed software used to monitor banking transactions for fraud, and it is said that his program detected and can prove where the trillion dollar losses really went — as criminal profits. Imagine trading a finding of mental incapacitation instead of a death sentence in exchange for favorable testimony. As result, his Father is said to have been scheduled to appear as a witness in a Federal Court as a whistleblower. At this point I would be remiss if not admitting the factual value as a motive is based on early speculation, as there has been no useful verification of any such court appearance. It would take considerable study of his Father’s situation to find facts before I accept it as factual, but it is sufficient a red flag as to deserve such study. Read about that, here.
Even more interesting, as a related mater, is that TDKR plot line is rather a strong parallel to the financial crimes under consideration. It may be EXACTLY THE REASON why James, and why TDKR. There is an excellent review of the film with that view in mind, here, with some useful background info on the software in question. Later, we will see there is also a potential reason why Century Theaters.
Motive 3: Also a matter to be determined more concretely, the third potential motive remains quite consistent with my findings in case after case when working with targeted individuals. I’m talking about victims of PCT, which is what I fear James Holmes is based on the wealth of clues in the greater picture. Such persons are always targeted for a reason. Almost always, that reason is FEAR of what the individual knows about some covert and illegal or immoral government Agency’s doings.
James Holmes, like so many of my clients, worked in projects associated with such an Agency; in his case, DARPA, the Defense Advance Research Project Agency. The work, in fact, specifically dealt with matters relating to Political Control Technology, though that is certainly not how they choose to describe it publicly. Learn more about his work, here.
What I find particularly interesting is that, in Jame’s case, the location where this work was undertaken was only two main intersections away from the shooting, essentially on the same Street. Just as interesting, is that he lived just ten minutes by foot away from work, only a couple of blocks from the theater, also just off of that same street, again. We will find some significance in that, later.
Being a PCT victim or even a threat to the entire PCT program would not in and of itself be a motive to set up an elaborate ploy to have them put away for life. There would be simpler solutions. However, if considered such a threat, it would make them a more logical candidate for Patsy among other candidates for a project which was slated regardless of if it was to be James, or not. Better to kill two birds with one stone than two stones.
With these motives and curiosities in mind, let’s tear into the conflicts inherent within the official story:
James Holmes was a patsy
What we told and can see raises serious questions
“Conspiracy theories” happen when there are obvious questions ignored by officials in government and media (Elephants in the room), where presented facts do not jive one with another. This is always the first hallmark of a cover up in a major story. I should make clear to the reader: there is NEVER a cover up UNLESS there is a CONSPIRACY. A cover up REQUIRES it, in fact, or it becomes impossible to arrange — especially when the “the only person of interest” is behind bars and cannot so arrange. Now, because media has not asked ANY of the questions herein, we must assume such a cover up has begun. Failure to question is a tell-tale hallmark which soon enough results in charges of ‘conspiracy theorists’ when challenged.
So let’s take a look at some of the questions I find most troubling, and address them. I’m not talking about external matters such as reports that FBI pulled a terror warning regarding theater attacks being a possibility. I’m talking about shooting details, doing so because I’m anxious to be called conspiracy theorist one more time, because I love pointing out that’s just a labeling game to avoid discussing issues. So, after I ask all the questions, I’ll present the ONLY plausible scenario which answers all the questions without contradictions, a replay of the crime as a false flag event involving multiple participants.
QUESTION 1: Why did a Judge, within mere hours of the shooting, order all records sealed in this matter as ‘contrary to public interests?’ What facts had been uncovered that early in the investigation which prompted such a concern? It would not be until well into the next day that facts even started to usefully unfold for such an important consideration. I’d like to know who moved for such a ruling, and the reasoning behind their request (stated reasons do not always equate to actual motive). Could it have been a call from Washington D.C., which sparked it?
QUESTION 2: Why was there a training exercise based on the same exact scenario underway at the same time, less than ten minutes away? The Denver Post reports such an exercise indeed took place at the Parker Medical Institute. A common theme in ‘terrorist’ events thought to be a false flag operation, is the holding of a training exercise for exactly the same type event at the same general place and time. This was certainly the case for Sept. 11 and the Subway/Bus bombing in London, for instance, and I seem to recall it being so with the Saran gas attacks in Japan.
QUESTION 3: Why did media first talk about the “lone shooter” effecting his crime by “kicking in the EXIT door?” Like all patsy shooting events, the initial stories given to and relayed by media without question create the all-important ‘first and lasting impression’ in the minds of the public. It would be impossible for anyone to kick in a fire door designed to open outward. In like manner, with the confusion clearly in place, no one could know with confidence at the outset that there was only one shooter, even if true.
No witness could rightly so claim. No Cop would be so foolish as to make such a statement. I would hope no reporter would invent it. But several early news accounts, including one aired on FOX Radio (play the second audio file on the linked page) a single witness identified (in print) only as ‘Pam,’ said exactly that. Why, unless a ‘planted’ statement for Wag-the-Dog* media manipulation? The first known airing was actually from NBC affiliate, Channel 9, on the scene. From their unthinking quote of ‘Pam’, news people everywhere simply repeated the line, just as mindlessly, and as if fact. Isn’t that a great way to get an initial mental image out into the public?
Was Aurora shooting a DOD or CIA operation?
James Holmes * An expression whereby news is manipulated by Men in Black to make people think things are much different than they really are, James Holmes popularized and hilariously illustrated in the Book and film of the same name starring Dustin Hoffman, Robert De Niro,QUESTION 4: Why did ABC News deliberately take James’ Mother’s quote out of context to indicate ‘they had the right person’ in arresting James? She has officially protested through legal counsel that that statement was in confirmation to HER identity upon first contact by phone. Again, media twists words and thereby assures ‘first and lasting impressions,’ a known Wag-the-Dog tactic.
QUESTION 5: Who lobbed gas canisters into the Lobby? At 3:29AM, as part of an interview with Police Chief Dan Oates after capture of James Holmes at the rear of the theater complex, a Channel 9 report reveals a lone gunman entered the lobby and discharged a gas canister and THEN went on the shooting spree. As we will soon see, there are other reasons to believe someone was in the Lobby doing just that. In fact, multiple someones. Did the man in the Lobby have orange hair? No one is telling, no one is asking. Why?
We might reasonably assume the above report an error, an assumption. But in a Web radio interview with witness Tim McGrath who was in theater 8 adjacent to the theater 9 where the shooting took place, we learn that while the shooting took place, there were FLASHES seen with the loud pops described as coming from behind, which would be the lobby/hallway area. It would, after all, be impossible to see any visual signs of activity in the adjacent theater where the shooting took place. So there really was additional activity in the lobby area such as flash bang smoke grenades, as confirmed by the other reports. Moreover, the Police dispatch audio tape appears to reference the front door (Lobby entrance) as being ‘blown out,’ at about 3:50 into the audio.
These events could in no way be undertaken by James Holmes, as he would need to take the time to exit the lobby after throwing canisters and make his way all the way around the building to the back, change clothes, arm himself, and then enter via the EXIT… in time for them to go off in the Lobby and be seen and heard while he is shooting. It makes no sense. How is this possible without at least one accomplice?
QUESTION 6: Who opened the EXIT in theater 9 for James? We now have multiple witnesses who saw someone within the theater open the EXIT door something like 20 minutes before it was used by the shooter. Without stating it in so many words, it is clear Police think it Holmes who opened the door, and then exited the theater through the Lobby to go around to the back where he prepared himself and then used that door.
But there is an oddity, here, because the man opening the door is not described by any witness as having blazing orange hair. Why not? It was not seen on the shooter, either, because of his head covering. Why wear the hair if not intending to show it? We will come back to this question. But we also have to ask, by what logic or reasoning would James not simply take the EXIT directly to his car and then return? Why return into the theater/lobby area, at all, unless it be a different person with yet another assignment to be fulfilled who did so?
QUESTION 7: How did the shooter gain entrance to REAR EXIT of the building at the time of the shooting? We know how he gained entrance to the theater through the EXIT door but that doorway led only to a short hallway serving theater 10 and 9 together, to yet another secure fire door opening to the lot where James’ car was parked. How did that door get opened for James? No one on the Web has addressed this question before me, and I think I know the answer.
Was Aurora shooting a DOD or CIA operation?
The next installment asks these questions:
James Holmes • Who warned people not to use the EXIT doors advising the shooter was outside, and why? James Holmes • Why did the shooter waste bullets shooting at a blank wall causing bullets to enter theater 10? James Holmes • Who wore the second gas mask and used the second rifle found at the scene? James Holmes • Why did the shooter not shoot the most logical victim? James Holmes • Why did that victim describe the first weapon used was a Rifle, when another says shotgun – who was indeed shot by a shotgun? James Holmes • And more… PLEASE: Comment (page bottom, or contact me), Rate (at page top), Share/Tweet this article. Visit my Reader Forum to promote your own cause or URL.Related articles
- Mind-Controlled Mass Shootings Don’t Change My Mind (proparanoid.wordpress.com)
- Lion Dance (a screenplay): How China Invades the U.S. via the Canamex Highway (proparanoid.wordpress.com)
- Six Dumb Arguments We’re Hearing About the Aurora Shooting [America’s Screaming Conscience] (gawker.com)
Informed Citizen of the Web… or Just Another Web Walleroo?
Try this short and fun test to see how dumbed down you might be…
Who knows? You might even be (gasp!) a Sheeple!
by H. Michael Sweeney Copyright © 2012, all rights reserved, Permission to duplicate in unaltered entirety with links in tact hereby given but please advise with URL via Comment or contact to proparanoid at century link net.Definitions:
A Walleroo is a kind of kangaroo.
A Web Walleroo is someone who hops around a lot on the Internet but doesn’t do much besides leave an occasional footprint of their passing through the digital landscape. They hop in and hop out with the briefest of glimpses and seldom stick around to actually absorb messages intended for them. Even when they do, they tend to do nothing useful with the information, being quick to gather visual fluff and short ‘textual or video sound bites,’ but sloth to consider actual substance and knowledge that might challenge their dumbed down state of mind. Got to hop on to the next visual bite!
Why the test? Because I note that while I may post advice to 6,000 ‘friends’ in groups of alleged mutual interests on important topics, less than 5% tend to take note and check out the material offered, and of those (say 300), less than 2% will bother to like, share, repost, rate (page top), or retweet. So I was wondering… is my writing style that bad (mostly get 5 stars when they do rate it) or do I just have nothing useful to say… or am I simply friends to a lot of Web Walleroos.
You can help me answer that by taking the test (or simply tell me you think my messages are just no good). I can deal with rejection very well, thank you. I think…
So take the test: Don’t worry if a given answer seems low or high, as they are used in calculations in unexpected ways. Everyone has some level of interest in ‘fluff’ matters of personal interest and some level of interest in more serious matters. This test attempts to quantify and measure one’s degree of interest in these two areas, and thereby to indicate their standing as either (Web citizen) Netizen or Walleroo.
You also needn’t worry if the answer seems unflattering to your sensibilities, because you can easily change your score by simply becoming more involved with the things that truly matter in life. Remember Aesop’s fable about the Ant and the Grasshopper.
Moreover, like all such tests derived by people too smart for their own britches (that would be me), it is not ‘scientific,’ and assumes much not in true evidence. It may therefore not truly reflect your actual status any more than a Political Poll really reflects who is actually going to win an election.
Straws. We are all grasping for straws. But that’s what makes it fun, isn’t it? To see if we can actually catch a straw and find it the right one? Give it a go…
Test questions (pencil and pad in hand), First section:
If you don’t regularly watch TV at all, skip this section (good for you).
How many times a week to you watch a network news show> Jot the number down, and again a ways to the right of it to make a second column with the same number.
How many times a week to you watch a talking head news/political commentary show? Jot it down, then multiply by 2 and jot that down in the second column.
How many times a week to you watch a reality TV shows? Jot it, then multiply your answer by 3 in the next column.
How many times a week to you watch a celebrity gossip/entertainment/talent show? Jot and multiply by 4.
How many times a week to you watch a sitcom or late night host show? Jot and multiply by 5. Underline these answers and add the columns up and write down the answers.
Now, think hard about the years just prior to Sept. 11 attacks and look at the total number of times for all shows. Ask yourself if you think as you look at each category if you likely watched notably more television then, than today, about the same (+ or – 10%), or notably less?
If less, double the second column total and jot it down just beneath it. If the same, do nothing, we will use the number directly. If less, divide the multiplied number in half and jot that down (approximate whole number is fine).
This is your ‘TV Media Impact‘ Score, which reflects how much of a chance your opinions, attitudes, and ACTIONS are altered by television.
New section: draw a line
How many Web Social Networks do you belong to or blogs, groups or causes do you regularly visit on line? Jot it down
Beneath this, jot down the total number of times you log into or visit them each week in total. You may wish to use margin space to jot down each one and add them up if you can’t do it in your head.
Multiply the two numbers and jot it down in the second column.
What is a typical number of times you like, share, comment, or rate someone else’s post or blog in a week – ONLY those posts which are NOT about personal matters but are actually about causes and topical matters of a more serious nature externally impacting your life, the country, or the World. Jot it down in the second column.
What is the typical number of times you like, share, comment, or rate where the topics are more of personal interests of less serious nature than the above. Put it in the second column and underline for a subtraction.
Subtract the second from the first. If less than zero, use zero.
This is your “Social Media Impact score.”
New Section: draw a line
Now subtract Social Media from TV Media and jot it down as a single, middle column. If less than zero, use a minus sign and keep going. You can probably do the rest of it in your head from here on.
subtract one for each real-world (e.g., Greenpeace, Republican Party, Garden Club, Exercise Club membership) or Web cause to which you belong and made a cash contribution or pay a membership fee, or have to go somewhere to participate.
Subtract one more for each such group to which you have attended at least three meetings in a year, and subtract five more for each instance which required overnight travel.
Subtract five for each attendance at a protest rally or public forum/debate, and five more for overnight travel, and 10 more if you participated as speaker or open dialog with a speaker, and 10 more again if you had an unpleasant confrontation with Police or other participants as result (stern words or worse).
Subtract 25 for each Web site or blog page, Cause, or Group you personally created and manage on the Web which has to do with the serious type of matters.
Circle this last result, which your final score for determining your status: Netizen vs. Web Walleroo. Lower is better as you may by now have guessed…
Scoring Section
0-5 You are a concerned and aware citizen.
The closer to zero, the more active and informed you are compared to others on the Web, and the more potent you are as activist both on the Web and in real life (they amplify your power in one with the other). you’ve probably Read at least one book each by Ayn Rand, George Orwell, Adios Huxley, and Hunter S. Thompson. You’ve read the Constitution and Bill of Rights and something by Thomas Jefferson SINCE school days, know at least two Constitutional Amendments for which you can correctly identify their number and purpose, and you know what Posse Comitatus refers to.
Now, if a negative number, you are a subversive radical
Yes, just like me, and as result you are probably being watched by one or more government agencies! Better read my book, The Professional Paranoid: How to Fight Back When Investigated, Surveilled, Stalked or Targeted by Any Individual, Group, or Agency. You tend to be a Truther and think the FED, Congress, the IRS, the UN, the Bilderbergers, the National Debt, and Terrorism are just forms of phony baloney. You have pet conspiracies you follow and probably believe in UFOs and mind control. GOOD FOR YOU! Right on all counts!
The larger the negative number, the more lists you are on with government, and the more likely you are to end up targeted by a Drone for surveillance, liable to actions sanctioned under the NDAA, have a FEMA Camp bed with your name on it, or likely to enjoy targeting with Political Control Technology (e.g., voices in your head, microwave assaults, street theater and gang stalking, etc.) You should use FOIA with all of the initialed Agencies of government to see how many files there are opened on you and what they are willing to tell you is in them. The more redactions you see, the more of a terrorist you are considered to be, and the more sophisticated resources they are throwing at you in order to keep tabs on you. In other words, THEY FEAR YOU! You are being a PATRIOT who questions government!
5-10 You are wishy washy on controversial matters, not terribly concerned that all the bad things out there can have too much impact on your life, but probably enjoy watching it all unfold, a form of entertainment. You join groups but don’t participate and probably don’t contribute. You sometimes shrug your shoulders and may catch yourself saying any of the following. ‘That may be true, but we can’t do anything about it.’ ‘As long as it isn’t me, I’m not sticking my nose where it don’t belong.’ ‘They probably know what’s best.’ ‘If you have nothing to hide, it shouldn’t matter.’ When you do choose to participate, it may be a contrarian remark or criticism, an attempt to change the subject.
10-25. You are a Walleroo! You should become more proactive in your beliefs, and perhaps should be taking a very close look at just what you do believe, and why. Challenge your beliefs to pass hard tests as proposed by those who believe contrary, and the truth may just set you free. This can alter (adjust) your priorities to be more in line with your true needs, which you’ve likely been hiding from yourself. You may even be that Ostrich with its head in the sand as the Lion approaches, hoping that if you can’t see the evil, it will not see you — like the Ravenous Blugblatter Beast of Traal, which is described in the Hitchiker’s Guide to the Universe this way…
The Ravenous Bugblatter Beast is so mind-bogglingly stupid that it thinks that if you can’t see it, it can’t see you. Therefore, the best defense against a Bugblatter Beast is to wrap a towel around your head.
More than 25? You are not only a Walleroo, but a Sheeple! You are probably perfectly content to buy whatever media and government hands you as Gospel, and tend not to care too much about scandals where they are caught lying to you, stealing your tax money, having sex with under age moist cigars, and the like. You are an adamant consumer of products and likely a staunch Republican or Democrat who accepts party line as the only line because that’s what your parents did.
As long as you can continue to enjoy your small World of pleasures you have defined for yourself (like the Grasshopper who preferred to play his fiddle than worry about things to come), you remain content. You have a towel wrapped around your head at all times, and will not even know what hit you when evil finds you. Now, hop off happily to the next bit of fluff, if I haven’t already lost you somewhere around the definitions – because if you are still reading this, I doubt we are talking about you, at all!
******
If you enjoyed this in any way, shape or form, I KNOW you will enjoy my companion post on calculating how much money the Federal Reserve has cost you personally. Its a bit more complex, but far more interesting and shocking in results.
Related articles
- Dissent Without Permission: Will Protest Permits & Free Speech Zones Halt Or Hasten Rebellion? (corporategreedchronicles.com)
- Political Parties are Like Entertainment for the Compliant Sheeple (libertarianreview.us)
Updated: Confidential Conversations that Never Happened…
A parody of real-life mechanisms in conspiracy cleanup (coverup contingencies)
by H. Michael Sweeney permission to duplicate granted provided reproduced in full and all links remain in tact, with credit given to the author and proparanoid.wordpress.com as source.James holmes is a patsy in a false flag operation
Update Aug. 29, 2012: As result of the popularity of my multi-part post on the Aurora shooting which is the most exhaustive review of facts to date, and because of the revelations the investigation involved in the effort have afforded, this post is woefully inadequate and no longer reflects the true concerns. Therefore, this update is actually a major rewrite to make it more in harmony with the true facts, rather than the early conjecture available on the Web at the time of its first writing. Additions or changes heralded in red. Any original material remains in tact, but in strike-through text, as I do not wish anyone to feel the material may have been censored for any other cause. Article begins:
Whenever the official story starts to have cracks in it, the cleaners go to work in Wag-the-Dog fashion, and power is applied to the weakest pressure points to make things ‘better for all concerned.’ As one CIA operative (one of the clean-cut train hobos at Dallas in ’63 set to cause a ruckus if the Grassy Knoll escape plan looked like it might be compromised) told me, “History is what we say it is, and it will not be changed by you or anyone else.”
Er… OK. But don’t fault me for trying the truth now and then, and forgive me with any liberties I take in the absence of good solid news reports full of details and hard facts… a matter which always makes me wonder what we are really dealing with…
 James holmes a mind-controlled patsy?
Come the terror at night,
or by day,
the citizens Plight is,
or it may,
be which one is right,
by what they say,
who is guilty of the fright,
and how shall we repay?
I wrote that with Aurora in mind, but it applies to a long American history of dark bumps in the dark, does it not?
James holmes is a patsy in a false flag operation
James holmes a mind-controlled patsy?
Come the terror at night,
or by day,
the citizens Plight is,
or it may,
be which one is right,
by what they say,
who is guilty of the fright,
and how shall we repay?
I wrote that with Aurora in mind, but it applies to a long American history of dark bumps in the dark, does it not?
James holmes is a patsy in a false flag operation
Added section: Ring: The receiver is lifted, but no greeting is offered, the Executive seated at the expansive desk in a plush office recognizing the calling number.
Voice on line: “The script will be ready on July 20. Adjust your plans accordingly.” The line went dead and the Executive hung up, and then dialed a number of his own.
Executive: “I’m green lighting Drum Roll. Production can begin at once, with a shooting date set for July 20. Make sure the cast and props are ready by then, and there are no problems in the storyboarding and rehearsals.” And then he hangs up.
Note: Double speak is the intelligence community perfected ‘art’ of speaking in the open about something by couching key matters in allegory or parable form. In the above example, we see how someone in the motion picture industry might talk about a film production… that was really something else… Drum Roll being the role played by the drum magazine in the shooting. Storyboarding means contingency planning, and rehearsals means that everyone knows the plan forwards and backwards. The script refers to the scheduled date of the theater shooting exercise which ‘just happened’ to be being held the same day of the shooting some ten minutes away off the same Freeway access as enjoyed by the Century theater. Interesting because high-risk intel ops such as would be true of a false flag operation, tend to employ a similar ‘drill’ for a like event on the same day and in the same city. This provides a cover operation so that if an operative is compromised, they will not be arrested and the plot can be aborted without exposure of the truth. End of added section.
James holmes is a patsy in a false flag operation
Ring: “Hello? News reporter here.”
Recognized voice: “The word’s going out to all our newsies… be sure to point out he had over $20,000 in high-tech equipment, and have another story by someone else suggest there is reason to believe there were Islamic ties, and be sure to play up the gun violence angle. And be sure not to mention he worked on that DARPA* project to develop super soldiers. That U.N. Treaty must be signed!”
News reporter: “But the shooting just happened. There’s been no time for an investigation, yet. What’s our source?”
Recognized voice: “Don’t worry about that. Just say ‘sources close to the investigation,’ and people won’t be smart enough to know any better… except for the ‘conspiracy buffs’ which you already know how to deal with.”
News reporter: “Right. By simply calling them that and ridiculing them for it. Got to hand it to Walter Cronkite for making that work so well in the JFK thing.”
*D.A.R.P.A. Defense Advanced Research Project Agency
Note: Walter was ex Army intel, and would have been a logical go-to person as part of CIA’s Operation Mockingbird which infiltrated news media with, by various estimates, over 1,000 operatives from CIA or on their payroll under the table. Since JFK, no conspiracy investigation has made good headway because media keeps trotting this excuse to ignore the valid questions of civilian investigators and investigative authors, or Engineers, Pilots, and other professionals who come forward with challenges to the official explanations. As one well known Comedian like to say, “I don’t get no respect, you know?”
James holmes is a patsy in a false flag operation
Ring: “Hello, Police Public Spokesperson.”
Recognized voice: “You have to stop talking about the possibility of the shooter having help. He’s a lone nut, nothing more.”
Police Public Spokesperson: “But people are trying to figure out how he got he got the larger weapons into the theater and all that gear. We already have one witness who’s been quoted as seeing someone open the Emergency Exit for him.”
Recognized voice: “Don’t worry about him. We have that covered. And don’t worry about what people think. We tell them what to think. Just do as I say.”
Police Public Spokesperson: “O.K. If you say so. Has everyone else in the loop here been so advised, or do I need to have an excuse to pass along?”
Recognized voice: “The key people are our people. We have it all covered, just like L.A. with the RFK matter.”
Note: In Robert Kennedy’s assassination, the Radio Dispatcher who controlled what Cops did that day and the Chief of Police were ex CIA. No wonder cops did not pursue the Woman in the Polka Dot dress, and the L.A.P.D. destroyed all the evidence which indicated more shots were fired than contained in Sirhan Sirhan’s gun, and did not protest that the fatal wounds came from the other side of his body where Thane Ceaser, a security staffer to a CIA involved military contractor had been walking directly behind Robert at the time of the shooting.
James holmes is a patsy in a false flag operation
Door shuts behind the lone interrorgator (spelling on purpose), and he takes a seat before the exhausted man at the desk. Interrorgator: “You told our people at the theater that you saw someone open the Exit Door for the shooter a second smoke grenade thrown from the opposite direction?”
Eyewitness: “Yes. I couldn’t see who because it was silhouettes against the movie screen might have thrown it.”
Interrorgator: “That’s impossible. We know the shooter was a lone gunman, and had no help. We have lots of people lined up who are going to be saying they saw it differently.”
Eyewitness: “I know what I saw. I was not more than ten feet away, and he crossed in it flew right in front of me.”
Interrorgator: “That’s not what you saw. The confusion and fear of the shooting has simply confused your memory. All you saw was someone getting up to take a leak or buy some popcorn. He never opened the door was some action on the theater screen from the movie… your mind has simply played a trick on you and filled in the blanks.”
Eyewitness: “No. I’m certain.”
Interrorgator: “Listen, kid. I’m going to lay it on the line for you.” Grabs him by the collar and jerks him halfway across the table. “I’m telling you, and you’d better listen up real careful like, you didn’t see that, you were confused. If you tell anyone you saw that, something bad might happen to you. There are a lot of people upset about this, and some of them have tempers and are looking for someone to go after. They don’t think very clearly, and I’m trying to keep you from getting seriously hurt… or your family for the matter. Do I make myself clear?”
Eyewitness: “You’re threatening me? With those people watching behind the mirror with cameras?”
Interrorgator: “You’re Goddamn right I’m threatening you.” Slaps face. “I sent those people on break and killed the camera, but in five more minutes, I’m going to call them back and we are going to be asking you the same question I started with, and you had better damn well tell me you were confused, or you and yours have NO F***ING FUTURE.” Shoves him back into his seat. “Do we agree on that, or not? Because if not, I can’t protect you!”
Eyewitness: “O.K. O.K. You win. I’m confused. I didn’t see anything except someone going to get popcorn.”
Note: Something almost identical to this happened to witnesses at JFK, RFK, and MLK, as well as the Flight 80o shoot down. Witnesses are often ‘told what they saw’ and told they were ‘confused by events,’ to allow investigators to later say their initial statements were not useful because of duress under stress impacting their memory.
James holmes is a patsy in a false flag operation
Ring: “Hello, Fire Department.”
Police Department: “We need you to take a Ladder Truck over to the shooter’s place and look in the window for us.”
Fire Department: “Why? We’ve never done anything like that before. What’s going on?”
Police Department: “We just want to make sure its not booby trapped. You need to tell us if it is so you we can send the Bomb Squad out.”
Fire Department: “Did the shooter say something to make you think there’s a bomb?”
Police Department: “Uh… sure. Yea. Something like that.”
Fire Department: “Well why not just send the bomb squad.”
Police Department: “Well, uh… I’m just doing what I’m told. I think they want high visibility with the press. Uh… you know… to make everyone look good. You will look good. We will look good… on TV… our small community will look good on national TV.”
Fire Department: “Whatever you say, Chief.”
Note: At a disadvantage with no concrete facts, there may have been a legitimate reason for asking the Fire Department to participate. Yet they did eventually send the Bomb Squad in and the first thing done was to use robots. Did the robots go in the window? Not that I’ve seen on video. No, they went in the front door. How do we know this? Because we have video of the bomb squad breaking out a portion of the window which would have needed to be removed if using the window for insertion of robots… doing so from the inside after the robots had finished. So why would there not have been a booby trap on the door blowing the robot away? That’s the FIRST thing I’d booby trap if of a mind to booby trap anything.
James holmes is a patsy in a false flag operation
Ring: “Bomb squad.”
Familiar Voice: “Be sure to blow a lot of stuff up at the practice demolition site afterwards.”
Bomb squad: “Why not just use the portable unit we always take with us? There’s nothing here large enough to require the demolition site.”
Familiar Voice: “TV coverage. Want to look good on TV, don’t you? Besides, the order comes from the top.”
Bomb squad: “Fine. We can have the rookies get in some practice at the same time.”
Note: The portable units (Mobile Explosion Containment Units) can contain significant blasts, but are not necessarily used for on-site demolition of bombs. They would perhaps prefer to instead transport explosives to a demolition site, as the units provide increased safety for such transport. However, some devices might be judged unsafe for transport, and should perhaps be destroyed at the crime scene. WHEN MULTIPLE DEVICES are found, there are several interesting possibilities which drove my inclusion of this portion of the dialogs.
a) The devices were too large to detonate on site. But we know that is not the case because we saw them on TV and they were small explosions (keep in mind that they use explosive devices to explode the bombs, so whatever blast you see is necessarily larger than the bomb by itself would have been.) Further, had this been the case, they should have likely been too large for collective transport, exceeding the safe operating limits of the mobile unit. But they were not shown making multiple trips to accommodate multiple bombs, so we again know this was not the case.
b) Despite the number of devices, their cumulative potential for damage is collectively within the ability of the chamber’s ability to safely transport through populated streets. IN SUCH A CASE, the bombs would normally be disposed of at the bomb squad’s facilities as a SINGLE BLAST. But we saw video on the news of multiple blasts in close proximity. This CONFIRMS they were not big blasts individually, and should have been done as a single blast. Why not? I can think of only one reason: Publicity stunt.
James holmes is a patsy in a false flag operation
Added section: Ring: “Executive speaking.”
Voice on line: “There’s been a problem with that special script for Drum Roll. It hasn’t been received by the Publicist.”
Executive: “Well where the hell is it, then?”
Voice: “We think it might be lost in the mail room for some reason.”
Executive: “Well get the… ah, you know… the ‘Director of Security’… to go search for it, then. That’s an important matter useful to Advertising and Promoting Drum Roll to the viewing public.”
Voice: “How do I do that? What do I tell them is the reason?”
Executive: Pauses. “I don’t know. It’s your job to solve problems like this.” Pauses again. “But try this; tell the Publicist to call the Director and complain about a suspicious package… and use that to get Security involved. Use your imagination.” Slams the receiver with a curse.
Note: Director of Security is their contact in the Police Dept. The Publicist is the Psychologist, or someone acting on her behalf. For some strange reason, the Psychologist indeed contacted Police about a strange package which showed up on her desk with no name on it, which turned out to be nothing but a text book being returned by a student. The explanation was concern, after the news about the bombs in James’ apartment, that it might be a bomb from James — in which case I wonder how James managed to put it on her desk while he was under arrest. For an even stranger reason, Police then searched the entire mail room to find the ‘script’ James allegedly mailed explaining in detail his plan to shoot up the theater. Strangest of all is that it was sent 8 days prior to the shooting. End of added section.
Next dialog, and the last, most telling of all…
Interrogator: “O.K., James. You want to tell us why you did it?”
James: “Did what? Why I am under arrest?”
Note: Jame’s reaction after the shooting is no different than Sirhan Sirhan (RFK), Jack Ruby (Oswald), David Chapman (John Lennon), Arthur Bremer (George Wallace), Squeaky Fromme (Reagan), and John Hinkley (Reagan), and others: No attempt to escape, in many cases going limp or calmly waiting nearby for arrest. Many of them have no recollection of the event, or have a single line of ‘political’ thought on it which they repeat, or start to explain and then just at the critical moment, change the subject.
These are all known methods of dissociation symptomatic of programmed Manchurian Candidates who are incapable of ‘confessing’ the truth, as they genuinely are not aware of it. In this case, we know he simply waited in his car and put up no resistance. What we don’t really know is if he has told the Police anything at all, but must presume not, or it would have been all over the news in some form or another.
So I’m taking the liberty and risk to assume, here. Please forgive any Ass made out of You and Me thereby. If I’m way off base, I’d be just as happy with the thought you may have gotten some entrainment value from it… because if I’m not off base, we are all going to end up mad enough to bring down the government and lynch some people.
James holmes is a patsy in a false flag operation
Please rate this article at page top, tweet/share, and comment. All comments welcome, good or bad.
Related articles
- Official Formula For Conspiracy Coverups (proparanoid.wordpress.com)
USAF Command Solo: Airborne Mind Control for the Masses
Not even the aircrew knows what they are telling you to think
by H. Michael Sweeney
Note: in preparation of this article, which updates and corrects some prior material I’ve posted in the past, I had intended to copy material already posted at my proparanoid.net Website, only to discover it appears to have been hacked (my host service stopped using Macintosh, it seems). The entire article relating to Command Solo has vanished, links and all. I wonder who would have a motive for excising only Command Solo information? No matter, it is also in my book, M.C. Realities: Understanding, Detecting, and Defeating Electronic Weapons and Methodologies of Political Control Technology.
A plane like no other, an admitted weapon against free-will thought
It’s a specially modified Hercules C-130 called Command Solo, and the U.S.A.F. currently operates a fleet of 7 of them (predecessors, Coronet Solo, entered service as early as 1978). They are based out of the 193rd Special Operations Wing stationed at what used to be Olmstead AFB, now part of the Harrisburg International Airport at Middletown, PA. Costing up to $110M each, they are the ultimate tool in government’s arsenal of Political Control Technology (PCT) used to subvert God’s gift of self determination. Official USAF info, here. Notice my photo is better than theirs.
Assigned to the Air National Guard, they frequently fly training missions over U.S. Soil, and no one who might feel a twinge of guilt, not even the aircrew, knows what messages they beam down to the ground. It’s all a super sophisticated programmed system with nothing but indicators and meters to show how things are operating. See inset picture.
Officially, it ‘intercepts and blocks existing broadcasts and replaces them with whatever information is deemed necessary to achieve mission goals,’ and operates in the ‘AM, FM, and UHF/VHF TV bands employing medium and high frequency, very high frequency, and ultra high frequency.’ The problem with these statements is that they avoid discussing yet two other capabilities, one being subliminal message embedding, and the other being the use of low frequency and extra low frequency, ELF. This is the darker potential of Command Solo:
All such psyops methodology is based on principles of mind control developed by CIA and the DOD, and even research by NASA, many of the same technologies used selectively on Targeted Individuals by operatives on the ground to make them seem Schizophrenic, though victims of that level of mind control also ‘enjoy’ other special PCT treatments as well, to include low-tech methods such as organized stalking, sometimes called dogging, or street theater.
It is not simply conspiracy theory or conjecture. The Air Force has admitted Command Solo’s use of such tech with startling results in sanctioned operations abroad, and further admits they are allowed to use it here in America in certain circumstances. But the problem is, there is no way to police or monitor its use, detect it in use, nor know what the content may be.
How it works

I used official USAF images for annotating as seen. Subsequently, they have been removed from USAF sites, all remaining images with less useful clarity or detail. My image was also deleted from search engine results after being among the first to show in a search.
Overt messaging: The least offensive possible use, whereby simple and direct propaganda is broadcast. The plane can even fly low altitude missions of this type and use loudspeakers capable of overcoming the plane’s engine noise by use of sound canceling technology. But this does not bother me in the least.
Subliminal messaging: The aircraft flies at altitude, loitering in large circles for endless hours, perhaps even employing in-flight refueling to increase time on station. There it picks up citizen broadcast radio and TV signals, and replaces or rebroadcasts them at amplified levels. It can work on select, whole groups, or even all locally available signals. How nice of them to provide improved reception quality for those listeners and viewers lucky enough to be below.
But there is a price to pay for the audience. The broadcast signals contain a few added elements of information embedded within the audio tracks. It is not known to be the case, but it is also presumed additional subliminals could be contained within the video. Subliminals are simple, brief, and repeated messages in a form not consciously discernible by the listener/viewer, but which, by repetition, are perceived and communicated subconsciously.
To my knowledge, the first known use that made the news about visual subliminals was in the motion picture industry when one frame in 24 (one frame every second) would have superimposed upon the image a single word, such as ‘popcorn,’ usually just before the intermission. This could also be achieved by the use of a second projector with all black film save the ‘word’ frames where the word was clear and transmitted white light in superimposition.
Alfred Hitchcock had the word ‘fear’ added directly to the film Psycho just before the scary parts. That was the use which became public, and revealed the fuller use to the public’s dismay, and soon enough sparked laws prohibiting its use altogether. We must suppose such laws are adhered to, as there is no easy way to know, for sure. All TV and film is candidate for suspect, and only frame-by-frame review would prove anything useful.
In audio subliminal messaging, a method known as ‘back tracking’ or ‘back masking’ gets a lot of attention in media, today… where the sound played backwards has a ‘secret message’, usually dark or evil. In some cases, the audio content may mirror the same information both forwards and backwards, such as is claimed for the famous ‘That’s one small step for man…’ moon-walk line, which backwards, says, ‘Man will space walk.’
The subconscious mind is said to ‘hear’ these messages quite well, but the phenomenon tends to happen naturally without engineering. While it is possible to engineer it, and many songs employ it for special effect, in my opinion, employing it for mind control purposes is less useful and less practical than employing a much more common method.
The simpler and earlier known method is to simply embed the message directly into the audio at inaudible levels and at frequencies or pitches sympathetic to the existing audio such that it seems part of the intended content. This method allows complex messages to be absorbed, and is well known as a means of teaching topical information or improving mental performance or even physiological attributes of people while awake or sleep. As long as the user of such content is informed of the existence and nature of subliminals, it is legal. Command Solo employs this later technology, but of course, there is no content warning.
EEG entrainment: There is currently no hard proof Command Solo employs EEG entrainment, though photographs (see image) of the plane reveal design elements which indicate the needed transmitters are installed. I’ve had the example photograph with annotations on line for nearly two decades and to date no one has protested the allegations with technical proofs or basis (or at all, for the matter, save possibly the protest inherent in the hacking thereof, which strangely left the image in tact — through removal of the image would have more quickly revealed the hack had taken place.)
The brain operates at extremely low frequencies (ELF) below 15 cycles per second (15 Hz). EEG (ElectroEncephaloGram) readings at multiple locations on the skull can be used to monitor brain activity by capturing these signals and converting them to printed readouts of squiggly lines for medical review. However, a given type of thought or mood, or even general physiological state (e.g. headaches, nausea, pain) will result in specifically unique EEG patterns as a collective. The EEG squigglies are indeed a de facto brain wave frequency map of such states.
Where such a frequency map is rebroadcast by traditional radio in the same frequencies but at stronger levels than the brain itself generates, the brain will adopt them as its own. This is called entrainment. Command Solo employs what I claim are special ELF transmitters to broadcast such frequency maps to a broad area to impact the thoughts of people below. Like the subliminals, this is presumed to impact anyone within several hundreds, perhaps thousands of square miles, though it must fade in potency as distance from the plane increases.
Therefore, by broadcasting subliminals such as ‘I should surrender if I get the chance…’ along with EEG states of mind such as ‘fear’ and ‘nausea,’ it is possible to perform quite a mind f*** of anyone unfortunate enough to be in the plane’s range of operation.
Follows is are excerpts from an article by Judy Wall, who was publisher of Resonance, a newsletter for members of MENSA (the high-IQ society) who specifically are involved in bioelectromagnetics study or research; a scientific paper. She also wrote investigative material for the magazine, Nexus, an international magazine covering technology as well as social phenomenon and their impact on mental and physical health. From Issue 7, volume 5 of Nexus, we find:
According to the (USAF provided) fact sheet: Missions are flown at maximum altitudes possible to ensure optimum propagation patterns… A typical mission consists of a single ship orbit which is offset from the desired target audience. The targets may be either military or civilian personnel…
In a phone call to the USAF Special Operations Command Public Affairs Office, I questioned the legitimacy of using these subliminal broadcasts against civilian populations. I was told that it was all perfectly legal, having been approved by the U.S. Congress (!) …the Air National Guard of the individual states in the U.S. can also operate Commando Solo aircraft, should the Governor of a state request assistance. That means the PsyOps mind control technology can be directed against U.S. citizens.
…On July 21, 1994, the US Department of Defense proposed that non lethal weapons be used not only against declared enemies, but against anyone engaged in activities that the DOD opposed. That could include almost anybody and anything. Note that the mind control technology is classified under non lethal weapons.
USAF General John Jumper ‘predicts that the military will have the tools to make potential enemies see, hear, and believe things that do not exist’ and that ‘The same idea was contained in a 15 volume study by the USAF Scientific Advisory Board, issued in 1996, on how to maintain US air and space superiority on the battlefields of the 21st century.’
Wall went on to report confirmation that Command Solo was employed in Iraq and specifically to sway Bosnian elections. The U.S.A.F. admitted to her that Command Solo played a significant role in getting Iraqi troops to surrender en mass, even sometimes to model airplanes (UAV – Unmanned Ariel Vehicles), and to sway elections in Bosnia to insure a Coalition approved leader was installed for the purpose of maintaining political control and stability of the region.
Additional thoughts (mine, not theirs)
This technology was first deployed in 1978. What happened in 1978? The World’s first mind control cult mass suicide: 909 persons at Johnstown, a CIA established cult started called The People’s Temple, led by Jim Jones. The cult, located in Guyana, was frequently overflown at surveillance distances by C-130 aircraft.
The significantly upgraded (EEG) version was introduced in 1980. What happened in 1980? Iranians stormed the Russian Embassy in Teheran; 63 religious Zealots seize the Grand Mosque in Mecca and are beheaded; Bani Sadr, the most pro American of candidates is elected as President of the new government in Iran (this is at the time Iran held 6 American hostages); unarmed farmers storm, occupy, and burn the Spanish Embassy in Guatamala, a key event to Democracy being established a few years later.
These events prove nothing concretely, but themes appear with a frequency to cause one to wonder, ‘what if?’
A logical question arises:
How do we know what information is contained in Command Solo when over U.S. soil? The answer is, we don’t. The aircrews do not, either. Nor does Congress, or perhaps even those who should know at the Pentagon. Perhaps only the preparer of the preprogrammed digital tapes used to modify and retransmit knows, and it is conceivable even that person does not know, likely ordering it by a code number which does not reveal content. It may simply be marked ‘Training Use Only.’ But somewhere, someone knows, and they won’t be talking about it honestly if it contains messages to sway our political opinions and social viewpoints, or our votes and other key actions.
Now, does that sound like a democracy in action, or more like a military police state growing its power? You know my answer, best summed up by the wish that the right to bear arms might ought to include Stinger missiles. I’d like to see these aircraft permanently grounded, along with the 30,000 Global Hawk drones they want to fly over U.S. soil to ‘protect us from terrorists.’
WE are the terrorists, because our ability to think for ourselves is threat to the security of the 1% who seek total control; we strike terror into their hearts every time someone like me makes public the truth, and someone like you chooses to read, share, like, and rate (page top) that message. We know this fear to be true for many reasons, as cited in my other posts on related topics.
That’s why its called PCT in the first place, an abomination before God in defiance and subversion of His gift of Free Will and self determination we were promised by the Constitution as ‘the pursuit of happiness.’ Where, exactly, do you live, again?
Buy now, be happy. Trust government, vote for X, and be safe. Spend money, be happy. Believe TV news, fear terrorism. Borrow money, be happy. Fear terrorism, Vote for X, and be safe. Watch TV, be happy. Ban guns, be safe. Buy now, be happy. Trust government, vote for X, and be safe. Spend money, be happy. Believe TV news, fear terrorism. Borrow money, be happy. Fear terrorism, Vote for X, and be safe. Watch TV, be happy. Ban guns, be safe.
Related articles
- Real Scientific Evidence for Subliminal Messaging: A Rising Tide (whatispsychology.biz)
- Timeline of Masonic/Illuminati/Mind Control Evolutions (proparanoid.wordpress.com)
- Can subliminal messages in movies be used to manipulate you? Like in FIGHT CLUB? (businessinsider.com)
Updated: Mind-Controlled Mass Shootings Don’t Change My Mind
The NWO can’t have my gun until I first get rid of the bullets
Update March 7 2013: Did the FBI undertake a covert ops to check out my gun collection (see image below, which I’ve posted both here and at my Facebook pages). Today and a few days ago, five individuals claiming to be insurance company employees entered a) my apartment; b) my daughter’s apartment; c) her husband’s father’s and brother’s apartment… claiming to do an insurance evaluation for the Landlord. They seemed to be focused on wanting to find and check out the water heater…
And so they looked in my bedroom (my office)… and then the closet… my (other) daughter’s bedroom and then the closet… the kitchen/dining area… the living room… and the master bedroom… and then the closet (where they FOUND the water heater)… and then continued looking for it in the other bathroom, the deck, and the deck closet… and then the attic storage area. It was OK, though, because they asked permission before opening any door, just like a law enforcement Officer would do when they had no warrant.
Having found the water heater behind a wall of stored items in the closet, all they could see of it was that it existed, as evidenced by about 12 square inches of tank wall and a couple of water pipes. I’m sure that was all they needed to answer their important insurance questions, because they didn’t ask anything about it, take pictures of it, or move anything to get a closer look. Yep. Insurance work is getting easier all the time thanks to the marvels of digital photography…
which, while they did not use it on the water heater, it being so important to them, and all, they did use it take pictures of other important things, mostly with deft hand-movements that concealed the camera from view. When I said something about the deck rotting after catching one of them using the camera, he even took a picture of the deck! Very important to water heater evaluations, yes?
Now would be a good time to mention that the woman looked very much like a known FBI agent from the Portland Office. Only the last time I saw her was when I was targeted by FBI for writing about Flight 800 friendly fire shoot down. I got visits from ONI, as well, and even one MI-6 chap who issued a death threat, and indeed over the next couple of months there were attempts on my life (not by him, but by local LEA, one of whom had been driving a car with license plates blocked out of Langley with DVM).
But I might be wrong. Might not be her. Kind of hard to tell because she had PUT ON SO MUCH WEIGHT! Any more and she would have a hard time passing the physical requirements. Kind of weird seeing someone who used to have a waist line now shaped more like a kite, and thinking them FBI. Kind of makes you loose confidence in government’s management capabilities, does it not?
Now is also a good time to mention that one of the men was seen wearing an old T-shirt from a known local CIA front… the one with all the technical toys hanging on his tool belt, and a clipboard. Anyone with the old T-shirt (the new ones are different) is usually an EX employee turned private contractor for hire. That front’s specialty is covert surveillance and eavesdropping. So if they left anything here, they had better real quick find a way to come and collect it before I can find it (I CAN VERY LIKELY find it), and end up filing a law suit, or at the very least go public with documentation of it.
The kicker? The image is NOT even mine, though I wish it was. It is a random image pulled from the Web for whom no original owner is evident (probably their wish). But FBI would rather do the knee-jerk, fear-based, jump-to-conclusion elaborate covert ops thing than bother to do a little research. Obama does not have enough money to pay for (anything we citizens need) but can spend $20,000 to convince the Landlord to go along with a phony insurance inspection ploy instead of $2 for a Google search? LMAO.
End of update – though I’d like you to know there are a series of companion posts which happen to also be my most popular posts (use My Posts menu item and select Top Ten).
Is FBI targeting people who have gun collections?
by H. Michael Sweeney
I may not speak for all gun owners, but i’m betting my sentiments are not at all isolated nor inconsequential. Look up the word consequence, to fully understand my meaning.
I hope the bluntness and inflammatory nature of my remarks are not lost on anyone. I deeply regret any need to write this, and in such tone, in the face of the unimaginable grief and wounds to the heart and soul of those who lost loved ones in Aurora. And though I’m sure they will not appreciate my remarks in the least, I cannot remain silent: I am incensed by the tragedy, doubly so because I see the darkness which surely drove it, and thrice so because it just happened to be within minutes of what is believed by many to be the intended new Capitol of the NewStates of America, also of that same darkness.
The shock value is for the Sheeple who need to listen up for a change and actually notice what’s happening around them outside of the sound bites they are fed daily. The NWO cares not for 71, 7,100, or 71,000,000 of us, if our loss will further their cause. We are but mere pawns who are allowed to pay for our own victimization that they may remain the 1% in power.
It’s also a warning to the governments of the World, including the United Nations and United States, that gun owners are the last people who give a damn about false flag terrorism as impacting our decisions on gun ownership. So if you want our guns, get yours, and come and try to get ours, if you can. A piece of paper, no matter whos’ signature is on it, or what flowery, tear jerking, politically correct words appear above it, will be of zero meaning to most of us, because we know why you want the guns, which brings us to the last reason for my blunt words.
Because it’s also battle cry for the rest of us, because we are so fed up with the BS that you spew forth so endlessly as if yours was the only side of the coin. We suffer from what I call too many Fascists Syndrome. You folks in power can have your Police State, but a piece of paper won’t get our guns, FIRST. You will have to take your chances after the fact, and we will see what happens when you try to go for it. You will have to get the answer to the age old question you’ve been afraid to openly ask, the hard way. And that question is…
Will we resist you, or won’t we?

Your actions dictate the form of debate: the power of words, or of bullets.
Either way, Citizens remain ready to open dialog. (wall photo – click)
You have feared the answer for decades, ever since the military Coupe your elders failed to make good on in 1933. The fear of what the answer might be to that question is all that has slowed you down, isn’t it? YOU, by the way, define the answer to that question, yourself. You define it by your actions. You would have no fear and not even need ask the question in that ‘kinder and gentler government’ you promised a few years ago, but woe unto you for the kind of government you are intent upon building, today. You risk much with every step closer to goal you take.
The Camel has a weight limit, and even we know not the final straw
What do I know that I should dare confront you so firmly? Because for decades I have researched you, and have written seven books about you. In particular, I’ve studied your preoccupation with Political Control Technology, that evil originally called mind control. There is one aspect of that, the Manchurian Candidate being a suitable (though technically incorrect) descriptor; a programmable killer, or agent, one capable of executing any foul instruction and being unable to later recall the deed, much less the instructions. MPD/DID through RSA torture is the proper term, along with hypnosis and chemical catalysts. Psychological magic mixed with Satanic methods of ancient times.
Words that should scare even you: Aritchoke, MK-Ultra, Often, Chikwit, NAOMI, and on and on. Patsies and real killers created by assembly line, rendered sleepers into society for activation on need, and often targeted with other forms of PCT to make them seem conveniently crazy should you need to call them into play. Am I crazy to say these things, or too close to the truth for you to dare even acknowledge I said them?
That is modus operandi, is it not? Ignore accusations as it tends to make people think there is nothing to them, and make the accuser go away once they get tired? Sorry, it’s been twenty years and I’m still talking, still accusing, and I am in no way alone. As result of our persistence, more and more Sheeple wake up each day, especially among the programmed sleepers. Fear us, for we are Legion! And guess what? We don’t even fear you enough to be anonymous about it.
Down to cases: to be specific, I accuse…
…that virtually every mass shooting incident has been a programmed shooter since the Texas Tower sniper felled 48 people, killing 16, in over an hour and a half of terror in 1966. And, as if some CIA operation gone wrong, media just magically stopped talking about it and kind of swept it under the carpet. Examine as many of this kind of incident as you wish, and please, by all means, lets include assassination attempts.
It is almost impossible to find an exception where the shooter was not under psychiatric care, commonly involving hypnosis and or drugs associated with CIA mind control research. At times, actual ties to CIA MC scientists or similar clues are found. Can you say, ‘Catcher in the Rye?’ How about Dr. William J. Bryan. Ring a bell? Manchurian, indeed!
It is almost impossible to find such an event where, if the shooter was captured alive, they were able to recall the incident. Why? Because of complete dissociation and honest lack of memory of the event, a known CIA methodology associated with mind control of the type in question.
It is ludicrous to the point of absurdity that any Sheeple remain unaware of the consistent ‘coincidence’ that Congress always seems to have legislation in hand ready to vote upon which ‘protects us’ from just such events as quickly as they happen, and quickly ‘strengthening gun laws.’ Gee, I have not noticed much improvement.
It was by this means that you have gotten us to register our weapons, which is something we should never have done, because now you know who and where we are, for that day when you come to collect our bullets. And you know, things still have not improved much with that law, have they?
It was by this means that you banned whole categories of weapons which would make any such effort more difficult for you, because you might end up collecting the bullets too quickly for your taste. And still no improvement in sight. Imagine that.
It was by this means that you made the good name of the NRA, of which I am not a member, and do not represent or speak for, but whom I respect, to seem to many Sheeple some dark kind of conspiracy, when in fact, it is YOU who conspire, and you who deceives. Still no improvement. Do you really think these laws through when you write them? Ever heard of logic?
And, it was by this means that you used even greater terrors to establish whole new agencies to spy upon us and to assault us with little dirty tricks in hopes of guiding us to the Sheeple category, but — SURPRISE! You instead created more of us and made us more adamant than ever. As I said, it is YOU that determines your fate, your actions which dictate the answer to your rightly asked question.
So, especially those of you in Congress, please keep that age-old question in mind when it comes time to consider outrageous gun or ammo taxes, and especially the U.N. sponsored international gun grab that gives up some more national sovereignty to the New World Order at the expense of the Constitution. Set the stage for a one World government and leader… who is that, again? The Antichrist? You really think we will allow that, do you?
Remember theses questions, and remember this: you can fool some of the people all of the time (the Sheeple), but you can’t fool the rest of us at any time, because Fascists are to us a known entity, and we do not listen to anything they say, except to hold it against them at their tribunal!
But what am I saying? I don’t even own a gun. But I assure you that I will, and millions more with me, if you force the matter to a head. Act wisely, for no one can easily stop what you might unleash through unbridled arrogance and lust for power.
Your move.
In the Rearview Mirror: When You Think You’re Followed
How to know, what to do about it
by H. Michael Sweeney
This is an updated summary review of information (not excerpted) from my book, The Professional Paranoid: How to Fight Back When Investigated, Stalked, Targeted, or Harassed by Any Agency, Organization, or Individual (available in ebook, CDR, and hard copy)
This post is a companion to a post on cell phone security made just hours earlier. Unless you want me to repeat that introduction, you should quick like a bunny hop over to and read it, first, as it sets the stage. I’ll wait right here…
Good. Now that we are on the same page, it seems pretty clear that if a person is being monitored in their phone calls, then there is a good chance they are under what’s called a full surveillance net. That means that in addition to your phones, everything from your mail and computer communications, and your travels away from home, not to mention everything you do in your home, including sex, are likely being monitored.
Only a Police State is paranoid enough to watch people like that… and perhaps voyeurs. One could argue then, I suppose, that sexually repressed people tend to be the ones who apply for and take these kinds of jobs with the intelligence agencies. Take a look at CIA spooks David Ferrie and Clay Shaw of JFK assassination fame, for instance. That may be why TSA has so many perverts groping people. I don’t know. Sorry, couldn’t resist.
Methods of being followed
Watch the Will Smith/Gene Hackman movie, Enemy of the State, and you quickly learn there are all kinds of ways: satellite surveillance, tracking devices, helicopters, cars, on foot, and even by microphone relay and telephone calls (where we left off). Now, with all that sophistication comes an associated cost factor, which tends to favor use of low tech except for the greatest of national security risks or fears. So you, as mere ‘suspect’ in some government imagined conspiracy to blow up your underware because you think for yourself and talk openly in an attempt to get others to use their minds, are more likely to be followed by car or tracking device than the more exotic means available.
Funny thing about tracking devices, though, is there is almost always a car following that signal. You won’t see it, but it’s almost certainly there. The purpose of the device CAN be simply to make and keep a record of your travels for later consideration, but usually, they prefer to be close enough at hand so that once you stop at a location, they can show up and see WHY you stopped… since the satellite isn’t going to be watching for them. So for my purposes, it’s the same as being followed by car.
The only difference is, you won’t see them in the rearview, but like the folks you do find there repeatedly, you will see them at destination if you are alert and can find a good observation post you can use with some useful patience. I’ve even found them there waiting for me. That was a fun story, just part of a five year running war with the paranoids, but I’ll save it for another time, perhaps. But other than them showing up like that, we need another way to know for sure.
How to detect being followed
First, how NOT too, would be more in order. Don’t keep looking for it, and don’t assume a car you see with great frequency is a bad guy. You are by and large a creature of habit taking the same routes to get to any given repeat location at roughly repeat times of day. So is everyone else. So I don’t get nervous because a certain rusty Chevy is within a few cars of me several times a week. Actually, I don’t get nervous even if I do think them following me, because I don’t want it known that I know. So I don’t spend all my time looking up at the mirror. If you insist on that, get a rearview camera ‘so you don’t back up over some kids,’ and glance at that furiously.
Just be aware of cars around you all the time, with NORMAL use of mirrors and glances out windows. Don’t be looking like you are on the lookout. Trust your instincts, and if you ‘feel’ like you are being followed, you may just be. At such times, or when you THINK perhaps a given car is just a little too familiar (or a driver), find something about the vehicle or driver you can identify later, and make a mental note, or a verbal note to a VOX (voice activated) pocket recorder, or a written note to a memo pad, or even a photograph. Note time, place, and descriptor.
The descriptor is going to be whatever thing is easy to recall. It might be a dent or rust spot, an odd paint job, a bumper sticker, or, where nothing else works, the license plate. Now there is a trick to remembering plates (more correctly, making them memorable) that I like to use when part of the sequence is alphabetic. RTU 035 is the plate of a vehicle associated with a CIA operative (more correctly, a retired Marine Forward Observer hired to ‘observe’ me by CIA). I glanced at that plate and forever now can recall it by my memory trick.
Simply make up some nonsense acronym out of the alpha portion and repeat it to yourself a few times while looking at the vehicle, not the plate – you want to associate the plate with the color, make, model, etc., not some rectangular piece of metal that might be replaced at some point. So in my example, I said ‘Rat-Tailed U-boat 035, Rat-Tailed U-boat 035, Rat-Tailed U-boat 035.’ Done deal. Next vehicle, please.
You can do the same with drivers. I enjoyed making up names for them, too: Pug Face (looked like a boxer who didn’t retire soon enough); The Professor (very dignified); The Liddy Man (wore a Liddy mustache and similar hair line; The Cuban (you get the idea). You will often see these people in multiple vehicles over time. It really gets interesting when you see the same groups of people in the same cars others of the group had earlier driven. And above all else, the most important clue… when you see the same people or cars at differing parts of town on the same day… especially if in those groups. Been there, done that.
But I did also employ both audio and paper, and photographs, as situations allowed or required (such as when there is not a lot of time and the situation is fluid). At days end, I would compile these all into a database, and once a week, for those repeat offenders (that’s the important clue), I’d go down to the Department of Motor Vehicles and run the plates to see who owned them.
Can’t do that any more here in Oregon, they made it illegal. Most states won’t allow it unless you are law enforcement. No problem. Lots of friends and relatives in law enforcement. Don’t have any? Make it happen, but you need to become GOOD friends because to help, they risk getting into trouble. It’s very helpful if you are both politically incorrect, at least privately (cops don’t get very vocal about that in public, it tends to cause unemployment).
Benefits and reasons for detection
There are some serious reasons beyond merely confirming suspicions. Example: Amazing thing about the DMV reports was, for me, that more than half the plates were reported either as stolen, non existent, or blocked by law enforcement. Actually, they didn’t tell me the later part, they just said non existent. But all I had to do was lean a bit and read it for myself on their CRT screen. Point is, such reports give you a clue as to who is involved. If you don’t get a lot of stolen/non existing plates, then you are probably dealing with private investigators, corporate goons, or some kind of group of idiot citizens thinking themselves above the law. Else, its government of some kind.
In my book I go into a lot more depth with some intermediate steps designed to better identify your players, and to give yourself tactical advantages. In fact, overall, its one of the larger sections of the book, and its followed by whole sections on offensive and defensive actions that fit into any knowledge gained about who is involved. That’s because, when you know who, you know why, and when you know all that, you know their limitations and what to expect from them when you do X. You start to control events forcing them to react to you instead of you being a mere bug under an unseen microscope subject to their manipulations.
And, it talks about their manipulations, and how to deal with them. They will attempt manipulations, mostly to see your reactions as part of establishing a psychological profile (another reason for cameras in the bedroom, I suppose). So one trick I talk a lot about, is ACT, don’t REACT. Learn to control responses: consider if the situation might be observed and a reaction expected or hoped for, and then decide if you want to confuse their profile by acting differently, or not. Then ACT in the decided upon manner, forcing them to react to YOU (incorrectly react, at that).
The other tactic I discuss at length worth mentioning, here, is that sometimes it is valuable to deliberately blow their tail by letting them know you know they are there, and who they are. They have to report that to their superior and they and/or their vehicle need to be replaced. Very embarrassing and a great chuckle to be had by all. It should cause escalation of methods used to follow you to levels harder to detect, at least by the time you’ve blown two or three tails in a row. Ideally, you do not want to escalate to that point where you can no longer detect the next level, so you would stop using this ploy when you felt that point was near (for most people, that’s going to be the first level, so this will be a moot dialog).
But for others, it has great advantage, because the book tells you how to use that information to better determine just who is following you. For example, at one point I was able to determine it included bounty hunters working with Clackamas County Corrections, and was able to thereby identify the Corrections Officers involved, as well as eventually find the high Sheriff himself (some decades back, of course — the current Sheriff is not a known CIA in-place asset) was involved.
I happened to catch him unaware on video following me on foot near where I worked, and that allowed me to identify him from a coincidentally convenient interview conducted on TV that very week. Subsequently, I openly took pictures of him when he drove past me in a car with Federal plates (neat trick for a County guy, eh?). Never had much trouble with HIM after blowing his invisibility, and in point of fact, after filing a complaint, he ‘retired’ from his elected post. The bounty hunters relocated, too.
The escalation which followed (that was the purpose, recall)? They advanced to use of trucks and vehicles belonging to and driven by employees of an electrical contractor which was later identified as a CIA front operating under 17 names in four States. So that told me my problem was NOT with the Sheriff’s department, but a much bigger fish. The whole story came out well in the end, as I was able to gain enough proofs to force them to stop bothering me, and even to pay me for damages.
Those proofs included not just my own problems with them, but documenting their spying on local government and high tech industry here in the Silicon Forest… letting themselves in wee hours of the morning past high security locks, using flashlights, and presumably, collecting and replacing recorded tapes. It’s all in my book, as well as another book, Fatal Rebirth, which better explains their growing paranoia since 1947 and on into the future. Ever heard of the Unified Conspiracy Theory? Check it out.
Then you will know why I make them so paranoid. Seriously, though; email me if you are having these kinds of issue: proparanoid at century link net.
Your Cell Phone is a Government Agent Spying on You
How to prevent gross violations of your privacy by the Police State
by H. Michael Sweeney
Updated 6/17: two changes in red
Note: This is a complex topic and thus is a lengthy post of a somewhat technical nature, and though it is based on knowledge of the U.S. communications network, most things found here generally apply World Wide. Given the complexity, it will not be useful to undertake reading it unless you have time to devote free of distraction, as it is too important for hit-and-miss reading. It is an updated summary review of information (not excerpted) from my book, The Professional Paranoid: How to Fight Back When Investigated, Stalked, Targeted, or Harassed by Any Agency, Organization, or Individual (available in ebook, CDR, and hard copy)
I’ll start with an inflammatory statement, which I’m fond of doing if it criticizes our errant government. We live in a Corporate Police State. This, I’m arbitrarily defining for the purpose of this article, is a form of government which partners with corporations against the clients of both. As Citizen, you are client to Government (you pay them taxes, they sell you societal infrastructure), and in this case, you are also client to your cell phone service provider. No client should be ever stand for being abused by those with whom they do business; they should stop doing business with them, or find ways to fight back and neutralize the abuse.
The Police State part arises whenever you have a government which applies surveillance and perhaps targeting with Political Control Technology (PCT) of citizens over political issues due to government’s paranoia; they fear the power of individual free thinkers who dare to have and express opinions contrary to their own. And, frankly, they should fear it, because the more Police State-like a government waxes, the more such persons they create, and the more likely such persons will become active in working to replace government. As other posts on my blog site reveal, when governments defeat traditional forms of redress, that could mean outright armed rebellion, if they persist and grow worse over time. Governments get what they create for themselves.
What has your government earned for themselves from you? Acceptance of abuse or defiance and protest against it? Your answer then defines you as being either a common dumb and obedient Sheeple or being someone who is more aware and thus deemed politically incorrect, and therefore liable to being spied upon by government through your cell phone. Here’s how they do it, how to detect it (when possible), and what to do about it.
Threat One: Listening in
A cell phone can be listened in upon by several means with varying degrees of usefulness, and in ways which almost make irrelevant any dialog about warrants, roving, blanket, or otherwise. Dialog on warrants would justify is own blog because as a topic, it is its own area of political spying abuse. So there will only be brief references, here.
While the information below talks about detection methods, most are not detectible usefully. At best, you may need to rely on situational evidence, such as people seeming to know things only possible by having overheard a conversation, or habitually ‘coincidentally’ showing up while you travel. It is all about being alert to your situation and surroundings. That is the price of politically incorrect (in a Police State). Here are the means:
a) If covert access to your phone was possible, it could have been cloned. Not all phones can be easily cloned, and some older phones may resist altogether, depending on who is doing the cloning (their sophistication). That means any use of the phone will be ‘duplicated’ on another phone somewhere as if the user thereof were inside your own head. This cannot be detected by you (assuming the user has set to mute) and, while the phone company could detect it in real time, they don’t try. It cannot be detected after the fact. Anyone using the tech would not likely rely upon a warrant, but it is possible that one could be involved. The technology to clone is hobby grade and above and thus almost anyone can construct the means to clone most phones.
b) Some cell phones have an undocumented diagnostics mode accessed by a keystroke sequence which lets the user hear all cell phone calls going on near to the tower at the moment, in random rotation. Since the number of users at a given instant could be just a handful, that often allows sensitive information to be gleaned, especially if one recognizes a voice. These codes are generally available on the Web, so anyone can use them, and no warrant is required. There is no means to detect its use.
c) The NSA (National Security Agency) worked with the phone industry to develop the modern digital telephone system which includes cellular technology as well as land-line phones. This has become a de facto World standard. The design incorporates command codes sent at ultra high-speed along the network mixed in amongst other call signal data. Phones generally cannot detect these codes (with some exception), but they do respond to them, and that is how they can be manipulated. The range of capabilities (and thus, the threat level) is broad:
1) Calls can be remotely listened to by NSA by computerized systems looking for keywords, in which case the call is escalated (see next). This cannot be detected and NSA routinely listens into almost all call traffic regardless of who the caller or recipient might be. This is under the umbrella of Operation Echelon, one of the earliest paranoiac efforts of the Cold War era intelligence community. Its been going on for decades.
2) Calls can be rerouted to a secondary location for recording and live listen-in capability. This allows thoughtful analysis of call content. This feature can be ‘preset’ so that all calls to or from a given number are recorded, which is exactly how they would choose to target the politically incorrect or a criminal suspect. A warrant is required by the phone company to set it up but anyone who knows the codes can bypass asking the phone company to do it. Virtually the entire military-industrial-intelligence complex knows the codes, and therefore, so do many individuals. It requires special black boxes anyone could build from scratch.
There is a subtle way to detect this form of eavesdropping on inbound calls, but it requires happenstance or deliberate query. If anyone mentions that it took a long time for you to answer the phone but at your end it only rang a few times, the call was rerouted and the caller heard extra rings while the secondary phone system took time to answer, initiate the recording process, and then pass the call along to you. This does not tell you if it is you or the caller who’s the target of the listen in, but you can query on outbound calls as to how many rings they heard at their end, and if calling several numbers at random with consistent results, you have your answer.
Another clue (very rare) can be when a call seems not to hang up and you continue to hear what is going on at the other end. That is a malfunction at the recording site which causes the call not to be released, and the line is held open. It is usually true that the other phone in the conversation was a land line. This brings us to the next threat:
3) The microphone of the phone can be turned on without the need of a phone call being placed or answered. The phone is then a ‘bug’ you carry with you. This can be detected in many cases by paying attention to battery consumption. If your battery life on a charge is normally many hours to days even with general use of the phone, but suddenly it dies or nears death within significantly fewer hours with the same level or less usage, it is being listened in, upon. This happens to me whenever I’ve announced I’m leaving the house, especially if to meet someone. Funny that the battery which normally lasts 2-3 days will crap out in six hours with a fresh charge, but return to the normal performance the following day.
4) I’ll mention as an additional capability less commonly employed is the ability to spoof a destination or point of origin call. You could dial, for instance, the Police to call for help, and someone else could intercept the call and pretend to be Police and sending help. Very useful when their own people are breaking into your home to cause you harm. The reverse is also possible, a call could come in from someone you know but be someone pretending to be calling from that number for some strategic value.
5) The original design did not anticipate the introduction of cameras into the system, but it is widely believed that it has been modified and may therefore allow the camera of the phone to be remotely activated with no means of detection. This has (since the original post) been verified as easy to achieve on all phones other than iPhones, and even iPhones are susceptible to more sophisticated conversions for the purpose.
There is no way to detect these spoofs at the time unless there is a flaw in their verbal dialog which triggers your suspicion and you are able to quickly devise a test question. This function generally relies upon black boxes, again, but are of hobby grade. I’ve received such a call as part of a break-in incident, the proof of it in the after-the-fact means of detecting the spoof, which is that such calls do not show up on the phone bill. That also means, of course, you have no proof for any legal recourse.
d) A more exotic use of the system as a dirty trick is that such systems can play tricks on you with respect to radio shows, where you are a guest speaker. These are often detectible as there will be a call to you just prior to (turns it on), and just after the show (turns it off) which entails an obnoxious squeal of digital codes which are similar to a Fax tone, yet clearly NOT a fax tone. I’ve been hit with this three times, and in each instance the effect was different, as was the tone set employed.
The first time was when I was one of the top three on-line civilian investigators (as media and government would prefer, ‘conspiracy theorist’) who was revealing new information never before known that served as proof of a missile bringing down Flight 800. I was guesting on Coast to Coast with George Noorey. The moment I announced I had this new information and began to speak of it, the show was sabotaged in the entire region of New York and Long Island where Flight 800 went down. It was a hot topic there moreso than elsewhere, because there were so many eye witnesses, not to mention investigators which we would presume government would prefer did not hear something that might redirect their investigation. The sabotage was truly clever; listeners in that area stopped hearing Art Bell’s show, and instead got an old recorded Art Linkletter show, ‘Kids Say the Darndest Things’, as confirmed to me by listeners afterward. As soon as the topic changed back off of Flight 800, the got Art Bell again.
On another show hosted by the late Michael Corbin, the effect was different. Callers were complaining that they could hear the host, but not me. The Engineer confirmed everything was correct, and the prior guest had been heard just fine with no changes in the set up, as was true of the next guest. More interestingly, my voice also did not record and so the show could not be offered on-line via download. An effective censorship. A similar third instance rendered the entire audio dead to listeners. The digital system is very powerful, it seems, especially when other digital equipment such as found at radio stations, is involved.
Threat Two: tracking you by cell phone
Your cell phone is constantly saying to the phone network, more or less, ‘Here I am, anything for me?’ Each cell phone tower nearby relays it to the phone company to find out. If anyone wanted to know your location, all they need do is figure out which tower(s) have your signal. This is supposed to require a warrant, or permission of the phone account owner (i.e., a parent trying to find a child), depending on company policy and service features (some do not allow owner access). But as the ACLU informs us, they often freely give this information out to law enforcement without a warrant. You see TV show cops and the folks at NCIS get at it all the time, as media is trying to train you to think it’s a good thing that should be allowed.
The above is true for all cell phones regardless of age or features, and provides an accuracy of varying usefulness dependant upon the number of towers and other factors. It can be as broad as a 4-6 mile radius, or as narrow as a few hundred feet when circumstances are right. The new GPS equipped phones will rat on you automatically to within about 50-200 feet in most cases. No way to detect any of this, of course, and a phone call does not need to be in progress. It merely needs to be turned on.
Threat Three: EEG functions
Cell phones are based on low wattage microwave signals in a relatively high frequency bands in the range of hundreds of Megaherz (millions of cycles per second) to several Gigaherz (billions). The human brain operates at ELF frequencies below 15 Herz (15 cyles). The difference does not deter those intending the need from using the phone in unique ways against their target.
A cell phone, like any other phone, can be used with voice-stress analysis to detect lies almost as usefully as if an EEG monitor were attached to the user’s head for the purpose. Anyone can buy the gear needed for a few hundred bucks, which lights up when you lie. They can be as small as and made to look like an ordinary deluxe ball-point pen, but are more commonly larger as size tends to relate to accuracy.
But a worst threat exists for Targeted Individuals (TI’s). These are persons who are commonly assaulted daily by a wide-range of Political Control Technology (PCT) in order to render them social, financial, and political zeros, usually by trying to make them seem delusional Schizophrenics. It is a form of mental, and in some cases, actual painful physical torture, as many forms of electronic weapons can be involved. The cell phone can easily become such a weapon.
In addition to all the other potential cell-phone abuses, which will be in constant use on the typical TI, they must worry about EEG manipulation. Signal processing methods used by the kinds of sophisticated agencies or firms (most commonly the intelligence community, military, and their corporat contractors) who employ PCT, can allow a cell phone’s signal to be embedded with a modulated signal in the same range as the brain’s own EEG.
When the phone is placed to the ear, it is close enough that the weak microwave signal with the embedded ELF signal, is still stronger than the normal EEG signal put out by the brain. When the brain is subjected to any signal simulating a given EEG signal that is stronger than its own, it adopts the external signal as its own. This is called ‘entrainment,’ and it is instantaneous.
This technology allows mood manipulation as well as manipulation of select physiological sensations such as feeling fatigued and in need of sleep, nausea, and headaches. Generally, such signals are mixed and alternate between extremes to emotionally and physically exhaust the victim, making them irritable and less than fully functional.
This threat is not normally detectible except by extremely expensive and sophisticated signal analysis by experts using costly special equipment. However, one very alert to how they feel before, during, and after use of a cell phone may detect or have a sense that this kind of abuse is being used against them. The threat also applies to cordless land-line phones, by the way.
Now, while the method is quite workable when the phone is at the ear, it can have a gradual, lessened effect if a few feet away. It is thought, by the way, that the use of an earpiece does not deter the method because the earpiece is also communicating with the phone at Gigaherz levels (Bluetooth).
Note: Another way Targeted Individuals are threatened by cell phones is Mob Flash. The victim’s picture and suggested things to do (called Street Theater) or say if they see them (usually described as a harmless joke associated with a birthday or similar) are sent to everyone in the same cell phone tower’s range. When you see people looking at a cell phone and then doing the same sort of thing, that evidences the practice. I suggest you have fun with them at their own expense and formulate an unexpected nonsense response. Booga booga!
Threat Four: the Software Mod threat
All of the above threats to one degree or another, including remotely activating its camera, can also come from yet another source; software mods to your phone. Even very old cell phones with seemingly no programability can be modded. It can be achieved by covert access to your phone, or by a phone call to the phone using a black box (which tend to show very odd phone numbers as the calling source), or even by a virus attached to a text message. Most phones do, after all, use Microsoft OS, which is quite prone to virus catching.
The obvious exception is iPhone, which wile not susceptible to such virus attacks, can still be modded by the other means. Regardless of the phone, unless a technician, you cannot detect the mod’s presence, and even technicians have doubtful capabilities. The only safe solution is to periodically have your carrier wipe your phone’s memory and download your approved apps and phone lists, etc., fresh.
Threat defenses
For all but the Mod threat, above, simply deny them their signals, and limit the phone’s usefulness as a weapon against you. Most people use the phone for relatively infrequent inbound or outbound calls. Anyone who uses it more frequently should also read up on the threat of cancer, which is so significant, that I refuse to put one to my head, and use speaker phone, only, unless absolute privacy is required, in which case I defer the call to another time and place, if possible. Frankly, the cellular industry is headed toward that time when class action lawsuits threaten to bankrupt them, as happened in the Asbestos and Tobacco industries. It’s exactly that bad.
Therefore, the simple solution is to turn the phone off when not in use. Power it up once in a while to see if you missed a call, and call them back. Your threat of tracking is limited to quite narrow windows of opportunity and tells them at best where you are the time of the call, which does not tell them how you got there or where you will be going next. Some newer phones ignore the power switch for tracking purposes, and it is thought they also allow listen in even when turned off.
This feature is not documented so we can’t say a specific phone is or is not a threat, but you should presume it so if built after 2005, and instead of turning it off, remove the battery. One indicator it may be an issue is if the phone stays lit up briefly after full completion of the power down (where it normally would not), or briefly lights up for no reason at all when not in use (someone has polled the phone with some sort of signal).
There are some who say that phones after 2009 also ignore battery removal. I have no confirmation, but you can also avoid power off and battery removal, as well as this added potential worry by simply placing the phone in a foil wrapper, even if just an empty foil-lined potato chip bag. And, by the way, put your credit cards in there to prevent people from using black boxes to steal your credit by cloning your card’s smart card chip. I use a foil lined oversized phone case to keep everything, including cash, and do not even own a wallet.
Deterring a listen-in threat is a different matter. Obviously, if you are using the phone, it is at risk. If you have a reason to suspect listen-in, it is likely because of a specific topic of sensitivity. Simply arrange in advance with persons with whom you likely need to speak openly about such topics to employ a simple code in conversations. A simple key word or phrase might mean ‘watch what you say,’ and then additional keywords might be translated as key sensitive elements of conversation. For example, you might agree that a given person’s name will simply be ‘Mr. Smith’ when, in fact, its not.
But don’t forget that there are two kinds of things one can say over the phone: things which are true, and things which are not. Thus if you suspect or know your phone is being used against you, try to avoid letting on that you so believe. That will give you the luxury of providing deliberate disinformation to any listening in. I’ll leave the usefulness of that up to your imagination, and suggest only that the person on the phone with you should likely have a means of knowing when you are using the ploy. Again, a keyword or phrase might help.
Where defense against listen-in seems impractical, simply avoid talking in specifics altogether, or offer to call them back later when you can do so from a phone thought more secure, such as a pay phone. Of course, the problem there, is, that government may be looking for your voiceprint with NSA’s help, so that any call you make is listened into. But land lines and topics like that will have to wait for another post… or you could get my book.
Seriously – email me if you have these kinds of issue: proparanoidgroup at gmail com.
Next post in this series: In the Rearview Mirror: When You Think You’re Followed
The NWO’s Dirtiest Secrets and How They Saved the World
All the King’s Horses and all the King’s Men, couldn’t put them into power again. Long live the NWO.
A modern fairytale with a chance at becoming true…
by H. Michael Sweeney
Permissions to reproduce granted provided credits and links remain in tact, and cite this blog as original source.
The revolution called ‘NOW!’
When the Sheeple finally started to wake up and realize the false flag terror campaign that had by then cost nearly a billion souls to perish, the surge of angry humanity was more than the militaries of North America, Europe, Asia, and elsewhere, could contain. As the deaths were largely from the pandemics of race-specific pathogens targeting Asians, blacks, and Hispanics abroad, the ‘fear factor’ in America and Europe proved not to be strong enough to suppress the truth about who was really responsible.
“NOW!” they chanted, at every confrontation. “NOW” read their flags of many colors as found in their respective national flags. They didn’t have to say what it meant. Everyone understood, and it struck fear in the minds of those in power, and gave strength to those opposing them. NOW was indeed the time for their action, as well as the basis of their urgent need, the source of their power, and the effect they would have by it. NOW was the movement, and it was the goal, and yet it may as well have been an acronym, as some insisted; ‘No Ordered World.’
In Europe, it was the Bilderbergers, and in the United States, the Council on Foreign Relations, and related groups of the so-called Round Tables and the think tanks, and the globalist foundations. It was they who were ruthlessly targeted by angry citizens who held them accountable in general for the rise of Fascism which drove the engines of the march toward a One-World Corporate State government controlled by the banks. Naturally, the minions such groups controlled to do their bidding by various means, such high persons as found in the military, intelligence communities, and governmental seats of power, were also declared enemies of humanity. The Boards of many corporations of the Military-Industrial-Intelligence-Media Complex were also on their list of enemies. After all, these were the only ones capable of engineering the false flag operations, of willfully concealing the truth, and the ones giving and obeying orders which drove vicious oppression.
The final straw and Agenda 21
The clues, or perhaps better described as the mistake… that thing which triggered this ‘understanding,’ it seems, was the move to form the North American Union and a World Currency based on the Central Bank model able to print what was claimed to be a replacement for fiat currency. This was oft referred to on the street as the Carbon Credits System, and these steps were deemed lines in the sand that, now being crossed, sparked a tide of revolt.
Somehow, the people realized it was still just another fiat currency printed at will, and not only represented more financial slavery through debt, but also, that it mainly served the interests of corporations, especially those in energy and finance, above all else. Coupled with the notion that sustainability should drive all political decisions, and discovery that the power-elite, pushing Agenda 21, believed that people were ‘not a sustainable product’ and thus had to be forced to sacrifice lifestyle and ownership of property, and be relocated to cubicle living near factories and farms ‘as the only way to usefully fit them into the new Carbon model’… caused international revolt on a scale not thought possible even by those who had long hoped for it to happen.
Bang, bang, too late, bang, bang, seals your fate
Militaries and Police the World over were overwhelmed, in part because huge portions of their ranks joined with the people. In some nations, the Air Force turned against the Army when the Army continued to fight the people. In others, the heads of militaries elected to resign, and in still others, to seize control of government, only to then be ousted by the people who wanted non of that nonsense, either. They sought only rule by the people of the people, and not to the benefit of persons, powers, or principalities.
Yet remarkably, most of the violence remained one sided. Despite their anger, most civil unrest was aimed at destroying the infrastructure of the power elite and going after individuals, and not directed at people in uniform who stood staunchly in the way with smoking weapons. Select individuals known to be chief among Globalists did not always fare well at the hands of crowds who managed to corner them, but by and large, Ghandi would have been proud that, despite the fact that citizens often had more guns, whole confrontations were resolved with gunfire originating almost exclusively from governmental forces.
Those in uniform, it seemed, did not understand the power of martyrdom or the true cost of tyrannical behavior. But then, they were the same people who did not understand their Oath of office, or they would have changed sides early on. They were the dumbest of Sheeple, of all, and did not have enough bullets to bridge their lack of understanding.
The truth that finally set men free
When it was over, vast stores of Globalist documents in print and digital form were acquired and pieced together to reveal that the people had entirely underestimated the depth of depravity and deceits, and the breadth of injustice and treachery, that the NWO had secretly undertaken. It was found to be, as many had claimed, a centuries old plot with an international tangle of conspiratorial Webs unimaginable. Among the many plots, one above all else was deemed the most insidious, more so than even the pandemics and false flag operations which had taken so many lives. It was the development of technologies to control men’s minds, and deprive them of God’s gift of Free Will; Political Control Technology.
The array of such technology was immense. Beyond the ability to imagine for most people, it encompassed almost every aspect of the functioning of the brain, from motor control and matters of the subconscious, to thought, reason and logic of the conscious mind, to simple mood and emotions, and much, much more. By the time this had been made public, and the magnitude of its use was revealed, some 400,000 key Globalists and their henchmen were in custody, and much of the technology itself. Thus, an international tribunal was being called for to weed out the true Globalists from those merely guilty of greed without understanding and perhaps duped or blackmailed into participation. Someone came up with an idea on how to best deal with the guilty.
They would construct a large ‘city’ on a preserve set aside in the middle of the Amazon’s deforested area (a practice quickly ended by the revolution) to serve as a prison for those who were convicted of crimes against humanity. It would be constructed in the manner of ancient pre Bronz civilizations without any modern facilities available, and only those tools and supplies needed to farm the land. For all practical purposes, inhabitants would be living in a single megalopolis circa 3,000 B.C., effectively in the Stone Age, sans great predatory beasts, that they might remake their small little World as they saw fit… from scratch.
That would be the façade, but concealed deep within all the stone and clay walls and the bare ground, hidden beneath steel plates to prevent discovery and access, would be the very mechanisms of political control these people had developed, to include surveillance. This would be used to cause them to suffer reduced mental effectiveness in ways similar to that endured by victims of the technology at their own hands. However, limitations would be put in place lest it be deemed inhumane punishment, because like any other technology, it could easily be abused. The difference was, that the Globalist designed it for such abuse, not realizing that it could also be used to prevent them from growing in power with less harshness in application.
Because almost all such Globalists had been of what were defined as ‘bloodline families’ for many generations, some going back for centuries in what was described as a Satanic plot to eventually seat the Antichrist, it was felt that they should be thrust together and allowed to live for generations amongst themselves. They would be free to wreck whatever havoc among themselves as might arise by so many ‘A type personalities’ being confined in one place and having only each other to victimize or overcome.
As they were almost exclusively Godless men who above all else hated the God of Abraham and those who worshiped Him, the Jews, Christians, and Muslims, the only literature they were to be provided, was the writings of those three faiths. Only if and when they were able to form a society which functioned free of conflict and competition for control through oppression, and forsake Satanic beliefs and fostered religious freedom, would there be any chance for leaving their prison, which was otherwise surrounded by significant security barriers.
The Illuminati lives
The name of the place was to be called Illumin, that those within its confines might rightly be called by the name they secretly coveted, the Illuminati. This was intended to be their Hell on Earth, the just reward for their crimes short of death. All the King’s Horses, and all the King’s Men, couldn’t put them into power again.
Note: While many elements of this pipe dream could certainly come to pass, and select of them are actually in works by the NWO, at best Men on Earth can only hope to deter that final Judgement Day which truly ends the war between Good and Evil. We cannot of our own volition earn such freedom as described here, as it would be in defiance of God’s plan, but that does not mean we must go like Sheeple to our doom. The Day of the Antichrist will come at is appointed time, but I believe Man is able to take part in the determination of when that time should be.
It is simply a matter of righteousness (right use ness) of power through God’s gifts of Grace and Free Will. At the moment, more and more power is being usurped to evil around the Globe. Grace is being subverted by temptations and deceits designed to keep us from thinking clearly and acting righteously. Free Will is under assault by Political Control Technology from disinformation to outright electronic manipulation of brain waves.
Very few people are daring to resist these forces or point them out, and far too many refuse to even see it when it is right under their noses, even in their heads daily. We need to change that if we don’t want the End Times upon us. The choice is YOURS to make, and no other’s. THAT is what Free Will is about more than anything else. And I believe that irrespective of the notion of forgiveness inherent within the principles of Grace, good use of Free Will is what helps us maintain any useful collective presence within His Grace. That is the key to how much time and how much freedom we might enjoy before End Times. It is so many grains of sand in an hour glass, and we determine the number thereof by our actions. The choice is your’s to make, and no other’s.
We are all John Gault. We are each that leader we’ve been waiting for. No one can save you but yourself, short of Judgement day.
This is why I write. I hope that is why you read and why you will share, “NOW!”
Related articles
- Citizen’s Viewpoint: We are ONE Person Away From Revolution (proparanoid.wordpress.com)
- Mass MindKontrol – Final NWO Assault (pakalertpress.com)
On Being Prepared for Martial Law or Revolution
What activists, militia, gun owners, and EVERYBODY ELSE should expect
by H. Michael Sweeney
Regardless of your beliefs of your political stand, Kevin Bacon had it right when he uttered the line in the film, JFK; ‘The Fascists are coming back…’ When they do, they won’t announce it beforehand, they will simply execute the End Game scenario as I wrote of in my book set, Fatal Rebirth. That book, if it helps with your giving me any credence, predicted the World Trade Center being brought down by jet liners and resulting in a series of Middle East oil wars… and several other unfortunate events including an assassination attempt on a Presidential candidate, ALL OF WHICH came to pass.
So I have just one word to those who do not believe Martial Law or Revolution are in their near future… ‘fool.’ Sure, I could be the fool. But I’d rather be a fool who is prepared for something which does not come to pass than the fool who was warned but choose to be unprepared when it did come to pass. With that in mind, here is my best advice on what to do to be prepared, with three different levels of preparadness for three kinds of people — from ordinary folk to the nastiest criminal and terrorist.
In the last post of this II part series, I outlined some significant warning signs that we are headed in this direction. If you agree the risk exists, the next step is to figure out which level of preparedness is right for you…
Level III candidates:
a) Is anyone in your family likely on a list? Anyone who is an Activist or outspoken politically on the Web, or in the real World, a Militia member, a registered gun owner, or who is a member of select ‘extremist’ political or religious groups (you probably have a good idea of who you are, and yes, that includes Constitutionalists, right wing, left wing, and wingless groups), is on a list.
b) If anyone in your family was ever given the treatment by any Federal Agency other than IRS (e.g., FBI, HSA, TSA, CIA,DOJ) for ANY reason, valid or not, you are on a list.
c) d) If you are currently a Targeted Individual, you are on a list.
d) If you the sort of person who, if shooting broke out tomorrow, would likely join in the fray against government, even if not thinking yourself on a list currently, should consider yourself level III or you may be neutralized before you can act.
e) If you are an illegal or in the United States on a Visa, and you would intend to stay, you may wish consider yourself a level III, because depending on where you are from, you may be in for harsh and harmful treatment.
f) If you are a criminal or a terrorist, you should consider yourself in this group. But you can please ignore me and get caught, please, because I’m not attempting to warn you to protect you, but to warn others they are going to be treated as if they were you, because government fears them more than you.
Level II candidates:
Everyone who is not Level III but who is also not employed by or associated with a government agency, military contractor, critical service sector (banks, fuels, transportation, utilities, etc.), or not independently wealthy persons of influence and power, be it corporate, political, or public image (famous people). This means the overwhelming bulk of us.
Level I candidates:
Everyone else; those who are so associated or wealthy; the 1% and people they love.
How you should prepare
Level I and above: You must presume an inability to travel, work, or access your finances. Banks will be closed. We are talking long term. You should prepare ‘Earthquake kits’ or similar of foods, emergency items, water, and cash in low denominations. Careful. FEMA will be in charge and will consider more than one week’s supply ‘hording,’ which is will be seen as a Federal offense which can result in detention and confiscation of personal property. Does your wife can fruits or vegetables? Better not have too many in the pantry.
Be prepared to have your home ransacked in a door-to-door search looking for illicit items, stolen goods, weapons, pornography, or horded stocks. You will be asked if you have such things and if you answer ‘no,’ but they find some, you will be detained. If you answer yes, be prepared to provide immediate access.
You will likely have advance warning of at least a half hour, during which you can put breakables in a safe place and perhaps pull drawers out and place them on tables so they won’t dump them on the floors to inspect the innards of the furnishings. UNLOCK everything if you don’t want locks smashed.
Be prepared for all medications in opened containers to be taken ‘for analysis,’ so you will want to have a supply of new-sealed medicines in reserve, at least a month’s supply. Some such things like insulin would not be an issue, but pills could be anything despite what the label says.
Any politically incorrect materials could subject you to detainment. They will likely want access to your computers and make a copy of hard drive contents. It will do you no good to erase questionable items unless you are quite expert in the field and have the correct software tools. Anything questionable found could result in detention and confiscation of the computer. It, or anything else taken will never be seen again.
If you have a dog or pet, put it n a cage lest it escape in terror or be shot as a presumed threat. Chaining is only going to be potentially useful if the radius does not encompass a walkway or access to a structure, but don’t count on it. There is additionally the risk of their own dogs seeking confrontation (even encouraged to do so) with yours. There will be dogs, so stand where they tell you to stand and do not make sudden moves.
In some cases those doing the searching will not be trained Police or military, but gang members or bounty hunters, or other persons who have been given cart blanch to do whatever they want, including theft of valuables. A a safe deposit box would be advised. If you have a wall safe, I’d not put anything truly valuable beyond personal documents there. You will be asked to open it, or risk having it blown open.
Stay tuned to the emergency radio and TV channels… the only thing which will be working. While you cannot trust everything you hear, there, it is best to obey any instructions tendered. Remain polite and obedient regardless of any personal affront you may experience. Be dressed when they come as they may choose not to let you dress or cover yourself if naked, especially if female. Lone females should invite a neighbor over for protection against risk of possible sexual abuse.
Level II and above: While level I persons will generally be afforded some degree of politeness and some hope of being given a chance to resolve issues which might arise (such as uncovering pornography not admitted to when asked), everyone on Level II is considered expendable, and in the way, a nuisance. You must be prepared to be even more tolerant and cooperative, as if a prisoner of war (close to the truth).
You should plan on hiding anything you do not wish to be taken, such as valuables, reserve supplies, or weapons, especially since you will be more likely to be searched by gang members or by unethical agents than Level I. See special tactical section on how to hide things. There will likely be ‘tests’ of your character and political thinking in the form of abusive behaviors and odd unnerving questions. There may be stress analysis lie detection in use based on audible response, so try to be truthful as best suits your needs.
Level III: You may wish to consider the prior advice for your family members, but any persons who fit the criteria to justify this Level should not stick around. See Tactical Advice section on Escape Plans. If the reason for such justification was terribly serious (e.g., being a known Anarchist or politically incorrect person such as myself), you should consider taking immediate family members with you, or at least having an alternate plan for their safe evacuation of the area. Make clear there will be no contact between you and them for a considerable length of time, and that when it does happen, it will be by unexpected means to which they should not react to at all with surprise. For example, they should not call out your name. They should not discuss it with other family members without care from surveillance. I suggest a copy of my book, The Professional Paranoid which offers a long list of specific issues such as this and appropriate strategies.
Special Tactical Issues:
Hiding things: You should not expect to be able to hide anything in your home safely. Not only might they employ dogs, but metal detectors, through-the-wall viewers, FLIR, IR, and Ground Radar systems. Merchandise of late is rife with RFID tags which send out what is effectively ‘here I am’ signals on radio request, and identifies the item. Anything buried at a depth of less than 80 feet is liable to detection, depending on its size, shape, and materials, and type of detection system and operator skill. Anything that absorbs and retains heat with a different coefficient than the items within which it is hidden will be more easily seen. So what can you do?
Depending on the nature of the item(s) there are some general strategies which can be useful. Small things like CDR discs or similar can sometimes be disguised or hidden in a way not likely to be seen electronically or visually, but I prefer to take no chances and instead hide things off the property and at distance. Items underwater and additionally concealed within an irregularly shaped bundle of various content tend to be invisible, so still waters can be useful. Indoors, there are often spaces in public buildings where one can hide small things and be assured not even the cleaning staff will encounter them, such as on top of overhead ducts, within vents, in the crevices of stairwells, etc. These would be low-traffic places such as emergency exits, back stairwells, etc.
Running: Establish your route and destination in advance, and consider variations for daytime vs. nighttime, as well as for circumstances. If there are troops on patrol and checkpoints, for instance, you need far more stealth options. False I.D. is illegal. Having found someone else’s I.D. and having it in your possession is only questionable. Using one or the other is one’s own discretion, be it real I.D. or something from your computer, but sometimes, walking right through the enemy’s door is better than trying to go around it. Of course, being proficient in a Martial Art is not a bad idea, either. Just remember that a Karate chop cannot outrun a hail of bullets. The best defensive martial arts courses money can buy today is Isreali Krav Maga. For extra money, they will sometimes teach you offensive tactics.
Once you have a route, especially if requiring days of travel, hide key supplies or items along the route in advance. Have more than one location for each so that if you cannot access one for a given reason, you have an alternative. As far as destinations go, the Book Set Fatal Rebirth has some very interesting ideas about how to modify and bolster structures to resist assault, as well as how to create perimeters of protection in layered form. Similar considerations on layered defense are covered in my first book, The Professional Paranoid. But the best modification is an emergency exit to a hidden remote point and yet another escape route prepared in advance.
Fighting, defensive or otherwise: If there is ever a revolution to restore government from a military coup or similar as so many of us fear is on the horizon (because, for the most part, that Congress is too blind to see the error of their ways in belief that the Constitution has no function despite their oaths to support and defend it), one must have a battle plan. What follows are just a few of the initial things which can be found in Fatal Rebirth, which goes well beyond this short article to include Rules of Engagement and an actual Battle Plan. Of course, that book was mere fiction, albeit one written for the ‘far out and unlikely propositions’ of ‘what if they took over the country and we had to take it back?’
I have a lot more to say about such things in Fatal Rebirth, all of it legal advice. But this forum does not allow it to be shared quite so freely without risk of prompting retaliation. I may already have said too much. So be it.
Please look out for each other, even those who refuse to understand, including where possible those who follow orders persecute you. Know your enemy and their weakness. It is their mind. Attack that and you win without bloodshed.
Related articles
- Military Viewpoint: We are Six People Away From Revolution (proparanoid.wordpress.com)
- Citizen’s Viewpoint: We are ONE Person Away From Revolution (proparanoid.wordpress.com)
- Will Obama impose martial law? (wnd.com)
- Compare 1776 to 2012 and Tell Me Where You Think You Live (proparanoid.wordpress.com)
- Pentagon Source Alludes to MARTIAL LAW Around July 1st 2012 (zionistoutrage.com)
- Are Feds Preparing for Martial Law? (godfatherpolitics.com)
- Dan Feidt: Military Prepares for Martial Law Takeover (VIDEO) (animalsclubfreedom.typepad.com)
- Will Obama Attempt To Declare Martial Law Before November Election? (pakalertpress.com)
- Media Beast To America: Bow Down To Military Police, Your New Lord And Savior (disquietreservations.blogspot.com)
Portending Martial Law: Three Facts That Put You at Risk
Warning signposts, mostly from local media, which mainstream media deems not to share
by H. Michael Sweeney
Call me a fool if you wish for thinking such is in our near future, but I’d rather be that fool than the one who disbelieves and is caught unprepared for serious consequences. My next post will be on how to deal with the consequences of Martial Law, but it will not be for the squeamish. The following information, save some more recent incidents, is documented in my book set Fatal Rebirth (over 1,500 footnotes). Most are also documented in greater detail in pages and pages of example after example in my book, The Professional Paranoid Defensive Field Guide. All stem from credible local news and agency resources and eye witnesses, myself included — serious matters all, despite a lack of mainstream coverage.
In addition to all of this, we have a report from theswash.com that the Council on Foreign Relations, which infects every part of government with members is proposing that the military take over Police duties in the United States. Now for the disturbing facts…
1) Fact set regarding surveillance:

DOD Image: RF-4CU Phantom
a) CIA, in Operation VERDICT, has over flown major U.S. Cities with low-altitude RF-4CU surveillance aircraft for LAMP (Low Altitude Photo Mapping) specifically related to Martial Law contingency planning. More current information reveals LAMP can include multiple imaging technologies such as visible light spectrum (photos), IR thermal, and ground penetrating radar. Overlays can therefore provide complete visual information as to locations and routes of critical power and communications, sewer and water, and service tunnels. LAMP also allows 3-D computerized modeling of an entire city. This means that a very detailed set of plans for establishing the best command and control locations, checkpoint roadblocks, observation and sniper rooftop positions, and cutoff points for communications, water, and power to any given neighborhood;
b) local National Guard are using city neighborhoods for training in the use of small (palm sized to dining table sized) UAV (Unmanned Aerial Vehicles) for surveillance, and passing along information to Police in some instances, a serious threat to privacy;
c) the Pentagon is ordering 30,000 Predator ‘Surveillance’ Drones capable of launching missile attacks for use in American skys, and these have already been used by one County Sheriff to illegally (Posse Comitatus) surveil a man deemed a suspect based on a personal vendetta (Color of Law violation of civil rights);
2) Fact set regarding ‘training exercises’ by National Guard units in various states:
a) in door-to-door searches of whole communities looking for ‘contraband’;
b) in highway and street checkpoint set up and vehicle searches, including stopping and unloading of buses and full identity checks;
c) in night-drops from helo into suburban neighborhoods for sudden control of same, informing citizens they were in a military reservation, and in other communities, broad daylight practice helo landing runs on shopping area parking lots and school yards by groups of helos full of soldiers;
d) in occupations of small towns by psyops teams who interrogated the residents as if foreign hostiles;
e) in providing ‘disaster relief’ (Andrew and Katrina) which turned out to be psyops teams evaluating civilian reaction to pervasive military control;
f) in storming hi-rise buildings, in at least one case a joint exercise between U.S. and Russian forces along side of local Police, and in another case, live ammunition was used, and lots of it, while on the ground, military psyops teams controlled the populace as if the event was not a drill, doing so in the guise of emergency medical care;
g) in beach landing assault of a beachfront community;
h) in assaults of entire neighborhoods with armored vehicles and soldiers entering by foot from all sides through yards and holding every citizen at gunpoint — a joint-Police operation in violation of Posse Comitatus and in direct violation of a Judges Order;
i) in night-time low-level attack helicopter runs between hi-rise buildings;
j) in one instance an Air National Guard jet straffed a school building at night with live ammunition, and in another, the vacated home of a politically incorrect individual was hit by a missile from a helo;
k) in surveillance by U.S. Navy helos over inland highways using ISAR Radar capable of tracking the movement of hundreds of vehicles simultaneously;
l) in psyops ‘practice’ flights of Command Solo aircraft capable of brainwave manipulation and known to be used to say elections in Bosnia by Air Force admition after the fact. Operators of these aircraft have no idea what content is being broadcast.
m) in military occupation of portions of larger parks and public lands, generally threatening civilians to vacate at gunpoint, often speaking foreign languages in addition to English. Related reports include sweeps of entire regions of forested lands by units who hassled civilians and used GPS to map locations of survivalist camps and hunting/fishing cabins.
Note: In almost all instances above, no advance warning and no on-site explanations were being offered, causing significant fear, confusion, and risk of armed conflict, except that in most cases, soldiers guns were allegedly not loaded (some lies caught regarding that). Many of these same kinds of trainings have also been held in mock U.S. cities set up at various military reservations, where bleachers at key points were set up so that officials might watch the action unfold. Some of these exercises included joint military and Police training which included use of lethal force in some cases (building assaults).
n) several respectable sources have indicated that the DOD has established plans that if Martial Law is declared, units from each State will be routed to an adjacent State (generally in tri-state rotation) so that troops will not face anyone thought to be family or friends.
3) Fact set regarding road signs:
a) in most communities of any size, and at key highway interchanges, one can find numerous highway signs and signs for public sites have been changed from the traditional green to a shade of Army brown;
b) many other signs have been affixed with curious reflective signs on reverse (seen only when going the other direction) with various codesl
c) highway departments cannot or will not explain either sign anomally.
d) analysis by many persons including myself reveals these are military codes and indicators;
b) brown sign locations represent ideal sites for military control points along key highways with large areas for staging of vehicles or encampments.
c) sign codes indicate exit points to nearby sites which would make excellent helo landing points, providing visual cues for ground traffic intending rendevouz.
4) Bonus fact set semi-related CIA infiltration of public sector:
a) CIA assets have opened a special training facility in California where bounty hunters, CIA and other intelligence agency members, military, and police are trained in clandestine entry, surveillance, and marshal activities (assault) of the kind not allowed by conventional warrants and law, but useful in a Martial Law situation. It is by invitation, only, that one may attend;
b) based on consistent discoveries (again, in Fatal Rebirth) most Major U.S. Cities would appear to have a Police Chief, Public Affairs Officer, and Internal Affairs Head (and sometimes SWAT head) who are CIA operatives (in-place assets), many of which who have taken the above cited training. A high percentage of Police Chiefs are promoted into place from the other three groups, allowing a perpetual supply of operatives to be arranged for’
Note: I have certainly seen exceptions, but in cities examined more closely, estimate a 90% consistency. Of course, this is one which cannot be proven except by circumstancial evidence — but why would there be so much like evidence consistently available? Almost all these people have military or intelligence community backgrounds, have taken that training or similar, and have a lifestyle indicative of extra income (two paychecks for the same job), and many are outright ex-CIA employees. In my community, over the last three decades, ex-CIA employees have also held other key jobs (e.g., Port Authority, City Council), and yet others have run for Mayor, Governor, Senator, etc. I suspect this is true in all States and major communities.
c) several major cities have adopted a CIA sponsored initiative to deputize bounty hunters and gang members for special community related situations unspecified, though door-to-door searches have been implied;
d) deputizing of highway workers, sanitation workers, postal workers, firemen, and similar has been variously proposed in communities or Federal interests over the last few decades, some proposals to include arming and arrest powers.
Part II of this series: On Being Prepared for Martial Law or Revolution
Its one thing to be warned, but advice on what to expect and what to do about it, is better yetRelated articles
- Compare 1776 to 2012 and Tell Me Where You Think You Live (proparanoid.wordpress.com)
- Military Viewpoint: We are Six People Away From Revolution (proparanoid.wordpress.com)
- Citizen’s Viewpoint: We are ONE Person Away From Revolution (proparanoid.wordpress.com)
- Dan Feidt: Military Prepares for Martial Law Takeover (VIDEO) (animalsclubfreedom.typepad.com)
- RightMarch: Obama Signs Martial Law Executive Orders (ConservativeActionAlerts.com)
Compare 1776 to 2013 and Tell Me Where You Think You Live
Congress and the President are pressing their luck just like King George.
Do you even know where you live? This review will help you figure it out. In 1776 the colonists were upset about quite a few serious matters, though the one the history books tend to focus on is taxation without representation. That was just the tip of the iceberg, of course, as any scholarly review would reveal. I’m not all that scholarly (though the information here comes largely from a ten-year research effort in the writing of my four-volume book set, Fatal Rebirth, which fully documents the more key claims herein). On that basis, here goes…
Power of King George vs. Individual Rights

King George III
In 1776 King George held the power of life-or-death warrant over citizens without a need for illustrating just cause. Because of the Magna Carta, there was at least the requirement for a trial, but near indefinite detention was possible by delay in setting a court date; a useful tool for dealing with dissidents.
In 2012, King Obama has unlimited powers of life-or-death warrant which have reversed even the Magna Carta, not to mention the Constitution and Bill of Rights, and without illustrating cause, he may order a citizen to be covertly vanished by Military with indefinite suspension, or have them assassinated, tortured, or turned over to foreign powers for same; the ultimate tool for dealing with dissidents, called vanishing.
Freedom of Speech
In 1776 Sedition laws forbad anyone from criticizing the Crown, leaving one subject to arrest for so doing. This included books, newspapers, and public forums in town squares, where it was common for people to stand on soap boxes or provided stages and speak to whatever crowd might gather. Soldiers were always nearby.
In 2012, King Obama enjoys control of Media as benefactor of CIA’s infiltration of Media in Operation Mockingbird as well as centralized ownership of Media outlets by the Military-Industial-Intelligence-Media complex (MIIM). There is a continuous concerted effort in Congress to neuter our ‘soap box’ called the Internet, and a recently passed Bill bans effective public gatherings for protest of government actions. It is virtually guaranteed that when you do attempt public speech you will be hassled over permits by Police, and be videoed by FBI if enough people show up, and be at risk of agent provocateur tactics and Police assault and arrest. While full control of media access tends to neuter free speech, actual Sedition Bills have non-the-less been openly discussed as ‘a need’ in Congress. That is coming, and could end up in book bans and book burnings.
High Cost of Goods and Taxation
In 1776 the East Indian Trading Company, a kind of corporate partnership between the Crown and the monopolistic firm, was almost the sole provider of transportation of goods to America. As result, the cost of goods were already burdened with excessively high shipping costs, upon which the Crown imposed high tariffs. Goods from America to Europe also had to endure these charges. Ergo, Boston Tea Party.
In 2012 King Obama in de facto corporate partnerships with monopolistic banks, insurance, medical care, and pharma industries to covertly levy the largest tax hikeseen in the history of the World. The cost of all goods and services if further raised by additional hidden taxes in the form of inflation from printing of trillions of dollars of money in yet another corporate partnership with the banking sector. This form of massive partnerships in another time was called Fascism, a descriptor of Nazism. We merely call it Socialism, today, a subset of Communism. Ergo, the
Tea Party.
Taxation Without Representation
In 1776 King George’s taxation upon the Colonies afforded no voice for American citizens in the King’s Court.
In 2012 there are only a small handful of Congressmen such as Rand and Ron Paul who have dared to vote according to their constituents wishes. All others are too preoccupied in their paranoiac fear of ‘terrorism’ to care what We The People think. Tell me then, who represents you in Congress? Really?
Freedom of Religion
In 1776 King George required that the Church of England was the only valid faith. This one fact caused a tidal wave of emigration to America, where it was hoped that one could worship as they would choose. In the colonies, however, attempting to exercise contrary faith anywhere but in your own home could result in court charges of both sedition and heresy against the Minister.
In 2012 King Obama is not quite there, yet. While the government has a history of persecuting and destroying (to include mass murder of Davidians) radical faiths, and there has been a consistent CIA and military backed effort to establish a ‘one-world’ religion which is more favorable to government needs, the worst Obama seems to be guilty of is favoring Islam, and false claims of Christianity to which he has repeatedly turned his back. His religious claims are, at best, as useful as his claim of citizenship.
Note: In my Book MC Realities I document the movement more closely than the overview shown here, which fails to mention the details (as are in my book) regarding the role of the D.O.D. (Army Psyops) and CIA (mind control) in forming such a religious organization, all of it undertaken, as it happens, at the U.S. Marine facilities at 29 Palms and The Presidio. And that’s exactly where it is unfolding, today, but now in ‘civilian’ operation by fronts established for the purpose, the military reservations ‘given’ to them for same. More interesting is the fact that key efforts in the project were managed by avowed Satanist (his religion a known fact at the Pentagon) Michael Aquino.Authority of Rule
In 1776 the claimed basis of Rule for King George in the Colonies was that he was first Christian Ruler to have caused the land to be settled, the authority given him by God to evangelize the heathen natives by the spread of Christianity. This was a charter given by the Church of England derived in turn from Rome. In order to legitimize colonies, the territories were to be purchased from the Indians in legal contract, and in turn, evangelism was to be undertaken. However, many colonies did not make such purchases, and the Church seldom undertook evangelism, and many Indian wars or massacres took place instead. The Crown did not obey its own charter or law, and thus had no legal claim of Rule other than by force of arms.
In 2012, the charter of power is the Constitution and the Bill of Rights, all of which King Obama has thrown out the window with the signing of a barrage of unconstitutional Acts. Moreover, since before Sept. 11 attacks, the United States government is continually guilty of violating its own laws, time and again. At best they band-aid the law with a new Executive Order or legislation after the fact, but often fail even to bother with that. The Federal Government therefore has no legal claim of Rule beyond the fact that the DOD on down to law enforcement still acts as if it does in complete ignorance of their Oaths of Office. In other words, by force of arms.
Right to Bear Arms, Troop Billiting
British foot soldier of the era
In 1776 King George billeted troops in the homes of Colonists without reimbursement for food and lodging expenses. While those living away from communities tended to be well armed, it was more common in communities to have an Armory where guns could be dispensed to residents in times of need against Indians, and then collected back afterwards. This was not gun control, as such, but practical logistics which tended to disarm many residents by convenience, since a musket cost a year’s wages.
In 2012, King Obama has no need to billet. Guns are required to be registered and it is clear that he intends to endorse the United Nations ban on guns and give up American Sovereignty in deference to a one-world government. This will require seizing of guns and the shooting of Americans who resist giving them up. This is one line in the sand which, if allowed to be crossed, will forever render all citizens subject to the whim of the King and those who control him (the New World Order). This IS TOTAL GUN CONTROL.
Military Occupation
In 1776, there were no Police in the Colonies, as such, but King George occupied communities through billeting and enforced the Crowns laws. Soldiers were everywhere.
In 2012, King Obama’s military is prepared to execute Martial Law (the means by which door-t0-door gun seizure would be facilitated) in guise of a Declared National Emergency (e.g., terrorism, pandemic). The Declared Emergency has already been issued, and thus we are only six persons away from Martial Law. Soldiers will be everywhere, and you will not be able to obtain food, water, power, gas, or travel or work except from or by the approval of Military.
Patriots Considered Traitors
In 1776, King George considered our Founding Fathers and those who followed them to be traitors and held them liable to the Death Penalty. Why? Because he feared loss of power and income to the Crown and East India Trading Company.
In 2012, King Obama, the Congress, and the Military and Intelligence apparat all consider those who support the Constitution, activists, patriots, and the poor and disenfranchised as enemies of the state, often outright calling them terrorists and targeting them as such with surveillance, dirty tricks, and violation of rights to include targeting with electronic weapons of Political Control Technology. These people would today consider the Founding Fathers traitors as well. Why? Because government fears loss of power and income to its corporate sponsors.
Now, with the above in mind, tell me… WHERE do you live?
One question sums it up, along with a sentence and factoid. Do you live in the United States of America, the nation established and protected by the Constitution and Bill of Rights, or in a covertly established (de facto) NewStates of America ruled by King Obama in tyranny not unlike that of King George? If you say the former, you are a huge fool, and if the later, doubly so for doing nothing about it. The Constitution of the NewStates of America has already been written for such fools as we.
Enjoy
Related articles
- Is America more exceptional today than in 1776? (salon.com)
- 24 Campaign Planks; H. Michael Sweeney for President of the United States? (proparanoid.wordpress.com)
- Do We Need and Should We Start a Second American Revolution? (godfatherpolitics.com)
Official Formula For Conspiracy Coverups
CU=(AC+P)x(LA+FB)x(4+D)x(FE-TE)^(GI)
by H. Michael Sweeney, from the Professional Paranoid Newsletter copyright©2002, all rights reserved — permissions by request onlyFor some time I’ve been playing with the idea of a book along the line of ‘Anatomy of The American Conspiracy’ or some such. The idea is to show that every one of our government’s best cover ups fit a very predictable pattern of events. I guess the idea is that if all these historical nightmares were simply random and natural evolutions of the nature claimed for them by media and government, there should be no ‘symmetry’ and no identical makeup. One event should not consistently look like another.
But what if there was actually a tried and true ‘formula’ in use by someone somewhere in an a CIA office with a door marked ‘CONSPIRACY COVERUP PLANNING’ (CONCUP)? What impact might that formula, if applied time and time again, have on the actual crimes involved? Would there be some kind of detectable ‘signature’ or pattern that clever observers could spot? You bet!
In such a book, I would take a few of our most famous conspiracies and conduct an autopsy looking for forensic clues that could be said to be similar in each event. From that, working backwards, perhaps, could be deduced the ‘formula’ itself. All of this, of course, being hypothetical, since we all
know that there is no such thing as a conspiracy — as media assures us, describing all who do not accept the official line as ‘conspiracy buffs’ and ‘conspiracy theorists.’ Never do they talk about the hard facts and logical questions raised by those ‘buffs,’ all of which are based on conflicting facts and holes in the stories being fed us. It’s tempting to become a ‘theorist.’
And no wonder, since no Federal Judge has ever found for a conspiracy. Why, even when the Christic Institute sued CIA and others over a long list of crimes uncovered by their exhaustive investigation… crimes which involved money laundering through select banks taken over by CIA for the purpose… the judge decided to throw the case out as frivolous, because there was ‘no evidence of a conspiracy’ beyond a few dozen cartons full of documentation and sworn affidavits. The Judge then slapped a $12M fine on the Institute, which was if someone knew how much money they had access to (as it was just out of reach.) This, of course, bankrupted the Institute and allowed CIA to seize all their assets in countersuit, including the hard earned evidence. Years later, of course, we found out that the judge happened to own a lot of stock in at least one of those banks… but of course, that was not a conspiracy, either. Obviously, it was just a ‘frivolous’ theory.
Well, as it happens, you CAN take almost any handful of conspiracies and dissect them as discussed, and guess what? There does just happen to be a long list of similarities. It also happens that the bulk of these similarities fit perfectly with the 25 Rules of Disinformation. Not exactly theory, the rules are used in college courses on Journalism, Psychology, and Political Science. Some progress is possible.
Taking JFK, Flight 800, and the Oklahoma City Bombing, for instance (others qualify, but these are useful to the newsletter), it can be shown that there are a number of ‘coincidental’ matters. From these clues, I have been so bold as to ‘theorize’ what the CONCUP formula might look like:
CU=(AC+P)x(LA+FB)x(4+D)x(FE-TE)^(GI)
This translates as: a successful CoverUp equals (Abundant Clues plus a Patsy) times (Linked Alternatives plus a Fall-Back Position) times the (FOURth estate plus Disinformationalists) times (False Evidence sold as truth minus True Evidence ignored, vanished, or altered) raised to the power of a government controlled investigation.
Some of these ‘variables’ need further definition. The Fourth Estate is a term used to describe Media, especially a controlled media, such as when CIA infiltrated U.S. media with 12,000 operatives to slant news in Operation Mockingbird. Linked alternatives refers to evidentiary trails which tend to lead ‘conspiracy theorists’ down a myriad set of paths which keep crossing each other or running directly one into another (a tangled Web resulting in ‘too many clues’ fabricated for the purpose).
In examining the basis for this deduction, one might be moved, if writing such a book, to cite specific examples. By way of illustration, I’ll offer a few such examples here — but point out each each example could fill a chapter if properly reviewed. Let’s face it. JFK, OKC, and Flight 800 are huge and complex conspiracies, according to ‘theorists.’
All three crimes (yes, Flight 800 was a crime) exhibit more abundant clues than we can shake a stick at. I insist that if given space to make the case, all three have a patsy – which in the case of Flight 800 is the Center Wing Tank. So much for (AC+P). (Disinformation Rule 12: Enigmas Have No Solutions; Rule 15: Fit the facts to alternate conclusions.)
All three have linked alternative paths for investigators to endlessly wander with no seeming apparent successful determinations (at least as far as are allowed to reach the public’s ears via media.) All three have a fall-back position established, a matter which again might take some explanation space. With JFK, it was either the ‘Communists’ (Solidarists, Cubans, or Kremlin, take your pick), a matter which was used to scare the Warren Commission into a desired finding for ‘lone assassin’ to avoid having to answer with a military strike against Russia. In Oklahoma and Flight 800, it would be International Terrorism. So much for (LA+FB.) Disinfo Rule 14: Demand Complete Solutions – Rule 11: Establish Fall Back Positions.
All three have enjoyed the helping hand of both the Fourth Estate and other non-news world Disinformationalists, a matter which hardly needs mentioning or proofs to anyone who has followed the ‘conspiracy theories’ as they developed. (FE+D.) Disinfo Rule 23: Create bigger distractions; Rule 24: Silence critics; Rule 15: Fit the facts to alternate conclusions; Rule 3: Create rumor mongers; Rule 4: Use a straw man.
There are definitely false and conflicting facts galore in all three cases. JFK’s magic bullet and the impossible shooting time/accuracy required. Flight 800’s exploding tank (where is the soot and the bulging, twisted metalwork?) and altered trajectory studies. OKC’s impossible home-made ANFO bomb and impossible mass destruction by that bomb. And all three have ignored true facts. JFK’s grassy knoll, missing brain, and CIA’s sworn courtroom confession by CIA agent Marita Lorenz. Flight 800’s vanished witnesses and missing FDR and CVR data and the silenced forensic investigation. OKC’s multiple bombs found on the third floor and seismic and audio recording evidence of two explosions. So we have our (FF-TF.) Disinfo Rule 20: False evidence; 22: Manufacture a new truth; Rule 13: Alice in Wonderland Logic; Rule 16: Vanish evidence and witnesses.
And government investigations, of course, are exactly the problem when government is the principle suspect being protected. No one in government seems to consider anything in the way of actual facts, ignores all challenges and questions about the claimed facts. JFK used the Warren Commission to white wash everything for us. We had FBI, mostly, and a rigged Grand Jury in OKC, and that’s according to a Juror. In Flight 800, we had US Navy, CIA and FBI, but mostly NTSB to dazzle us with doubtful logic proclaimed as truth. That is our (GI.) Disinfo Rule 8: Invoke authority; Rule 21: Call a Grand Jury, Special Prosecutor, or other empowered investigative body; Rule 1: Hear no evil, see no evil, speak no evil.
Of course, this is not such a book, so I don’t have the time or space to make a compelling case for these arguments. Nor do I have the space to describe the more elegant formula used as catalyst and bonding agents. There is a kind of nested trilogy of trilogies, you see, all having to do with disinformation.
One set is concerted disinfo attack aimed directly at the ‘conspiracy theorists’ through covert infiltration of the actual ‘conspiracy theorist’ group, usually to create a strawman or simply sabotage their progress; then there is disinfo through mainstream media designed to derail conspiracy gains that might catch the public’s imagination; and wild theories (more strawmen) promoted by bogus ‘theorists’ specifically to discredit all such ‘theorists.’ It would take a book to document the examples in JFK, OKC, and 800.
The Second Trilogy lies in evidence used by government, virtually all of which is flawed or tainted in some way by government’s handling — a matter completely intolerable in any normal criminal matter. Example: in Flight 800 FBI’s explosives residue tests were conducted after pressure washing the items; obvious evidence is ignored. Example: in JFK, Marita Lorenz’ testimony to the Church Committee on Assassinations, the FBI, and in court were completely ignored by everyone, including media; legal processes are subverted. Example: in OKC, two unexploded bombs found on the third floor were not presented to Grand Jury or at McVeigh’s trial — which would prove a broader conspiracy and implicate McVeigh as an obvious patsy — one who could not be allowed to die until the greater conspiracy was solved. This is why his death was so important — to cement government’s claims forever in media’s view, which was just why, in reverse, Oswald had to die at any cost, even if requiring the sacrifice of conspirator Ruby.
The third trilogy creates a coordinated disinfo machine consisting of a manipulated ‘Mockingbird’ media literally owned by the military-industrial complex (making it, in my own coined term, the Military-Industrial-Intelligence-Media complex, or MIIM); other-than news media ‘apologists’ (authors and prominent persons) who make cases for government’s arguments and criticize ‘theorists’; and a round of TV and film docudramas and ‘investigative reports’ designed to ‘portray the facts’ which just happen to match those provided by government press conferences and media, ignoring all else. Where this leaves us, of course, is at the doorstep of understanding. Gaining such an understanding may enable us to reexamine the events of our time more carefully.
It is your mind. Use it. Use it or lose it to their lies, a form of mind control.
Visual Roadmaps to Treason Expose Truth About Terrorism
It’s all about who benefits: Globalism needs Terrorism to prompt Patriotism to support Capitalism which drives Globalism
reproduced from book Fatal Rebirth, by H. Michael Sweeney though copyrighted, image reproduction OK if reproduced in full and notifying Author at pppbooks at century link net with resulting URl by H. Michael SweeneyNote: the relevance of relationships or even the identity of some names may seem lost to those who have not read Fatal Rebirth or otherwise studied such matters in depth. The book set (1,500 footnotes) clearly explains their presence in the graphics. Non the less, the bulk of names are known and should make sense to any individual who is half-way informed about news events of the last decade.
Image One: Satan’s Franchises, paths to seating the Antichrist
This is the engine of power and profit which drives the cooperation of greedy men. I draw special attention to Ali Mohammed, and Richard Perle with these links explaining their importance as puzzle pieces, pieces so important they combine to make almost all of the other elements in the pattern make perfect sense. This chart, by the way, can be drawn for almost any War in modern times. The name on the lines and intersects may change, but the franchises remain valid. It may further be useful to note that two of the players, Zalmay Khalilzad and Hamid Karzai were the CIA-backed, oil industry selected people we put in charge of Afghanistan, because most of us do not know who they are.
Image Two: Roadmap to Sept. 11 Treason
How can it be anything but an inside job when the terrorist both flight schools were CIA operations, and virtually every other resource used by the alleged terrorists was US military or military contractors? The map lets you follow the money (banking money, oil money, Saudi money, drug money, etc.) as well as key resources and allies from inception to destination in history. For example, the aircraft and staff of the Florida flight schools came from Caribe Air of Iran Contra fame, and were used by Jeb Bush as their own personal airline.
Testimony to Mass. State Legislature on Bill Restricting Electronic Weapons
Included list of 250 terms and technologies of Political Control Technology
Edited excerpt from book MC Realities: Understanding, Detecting, and Defeating Political Control Technologies
by H.Michael Sweeney, copyright©2006 proparanoidpress, all rights reserved reproduction by request and approval only, to pppbooks at century link netI write to the honorable legislative committees as a friend of the State and of all its citizens, volunteering the material contained herein as an expert witness on electronic weapons, electronic harassment and related technologies of political control. It is hoped that this material will be entered into the public record at your hearings and become useful in your final determinations…
Because of my knowledge on topic after a decade of helping victims of such technology, I must protest at the committee’s choice of language in the bill with respect to the first sentence… referencing control of these weapons only in the hands of the public by means of the phrase ‘no person’. This is to miss the entire purpose and intent of these weapons, and to fail to address the virtually sole possessor and users of the worst of the technology, which is government itself. The public does not need legislation to protect itself from itself, but from its own government. Language must specifically and clearly include government agencies and government personnel of all manner, Federal, State, and local…
In like manner, your definition of weapons is far too simple and narrow to avoid legal confusions. For example, the very same technology which is found in radar guns and FLIR can be used as a weapon of political control or harassment by mere abuse thereof. How will you protect against such abuses? How will anyone be able to determine by the wording of this Bill when the technology and application are legal and appropriate and when they are abusive and invasive?
The victim is not protected if the burden of proof rests on such simplistic language. The abuser, especially if governmentally authorized to access such technologies for normal uses, is not at risk where such loop holes exist. Your language must define and articulate to the complexities of the matter, which are illustrated by the technology reviewed in my (included) materials on topic. Merely adding ‘definitions’ section should address these concerns.
Finally, your legislation makes no provision for detection and enforcement. Can you imagine the local police arresting someone because a neighbor claims to have symptoms of attack? Without a means of detection, there can be no enforcement; all which remains is mere lip service, legislation not to protect the people from the weapons, but to protect the establishment from the people. The primary question is this: Is there anyone in our national or state governments who will stand up for the Constitution, support the Bill of Rights, live by the morally correct principles of humanity and of God, and resist the evil which stares you squarely in the face?
The challenge before your committee and, ultimately, for your entire legislative body, is not only formidable, but it is absolutely pivotal to determining the future of this nation…
Until one empowered sector of our own society, such as yourselves, makes an official protest and stand against this growing draconian onslaught, those things for which our nation stands come closer and closer to being silently crushed within a velvet totalitarian glove. Without such understanding… without laws to protect citizens from the dangers involved… and without any means of enforcing those laws… political control will be assured. The price for such control will be dear. It will be the surrender of that thing godly men call ‘free will’, and which the patriot calls ‘freedom and the pursuit of happiness.’
…May I propose three key concepts or points which should be a part of your deliberations?
1) The first is that any such legislation should be broadened to cover most, if not all non lethal weapons, not just electronic. The very same people who developed electronic weapons were responsible for the development of other non lethal weapons, and for the same unsavory reason: political control. All such weapons further have the same attendant risks to life and liberty and lend themselves to the same abuses and excessive draconian applications.
Perhaps just as important, a review of all such weapons makes the relationship between the weapon, the intended use, and the greater political control strategy which drove its development that much easier to grasp. In support of this notion, my report herein addresses the full spectrum of non lethal weapons, the greater portion of which are, perhaps surprisingly, the more hi-tech electronic variety.
2) The second point I would like to make is that your considerations and final findings must include and provide for public awareness. Only by educating the citizens of the realities of the existence and use of these technologies, can your efforts be well served. If the citizens do not understand the technology and the symptoms it generates, they cannot report the crime or well defend against it. In like manner, your law enforcement, the legal system, media, and the professional communities must also be educated, or the victims will have no place to turn without being labeled as insane.
Of even more value, such promotion and education will, more than any threat of punishments, deter actual use of the technology in the first place. All such technology is currently used in an extremely covert manner. The last thing an attacker using electronic weapons wants, is to be discovered. Such discovery puts not just the mission at risk, but also puts at risk the entire infrastructure of the non lethal weapons industry, and their leadership both in and out of government. Education will, in my opinion, prove to be your best weapon, in the end. But education in and of itself does not provide an adequate deterrence, because unless an attack can be proven, it is merely an accusation which, due to the sophisticated nature of the attack, can too easily be ignored by unconvinced authorities.
3) Therefore, the third and final point, perhaps the most important, is that if you are to have any true success in this matter, you must necessarily include funding for the exotic equipment required to detect and analyze the telltale electromagnetic fields, energy bursts, and radio frequency signatures which are the calling cards of these technologies. In fact, I remind you, it is precisely the output of these detectable indicators which makes this matter one of general concern to the population at large.
The leakage, overshoot, and reflection of these signals, energies, and fields created by these weapons have a great potential for harmful physical, mental and physiological effects on all citizens within a given radius of the intended principle target under attack. The collateral damage to these citizens is not now understood, nor can it be so understood until the actual weapons are captured and tested by independent laboratories. Even the most conservative estimates talk about dire health consequences associated with these weapons. If a particular cell phone can be found by scientists to cause a brain tumor, then what must we face when the signal strengths are many hundreds or even thousands of times stronger, and deliberately designed to cause physiological and mental effects?
If you fund the needed equipment, you will need to further fund appropriate training of technicians on how to use the equipment, as well as in general procedures and skills in the area of covert counterintelligence operations and general law enforcement procedures. This is exactly what will be required in order to be successful against those who use electronic weapons, and no less.
With the above in mind, I would propose the Bill provide for creation of a joint task force of specialists in the areas of law, communications, signal processing, electronics, bioethics, medicine, chemistry, psychology, counterintelligence, military, and law enforcement be created and managed by a carefully picked oversight body. In the absence of creating a new bureaucracy, I would suggest that such responsibility might best belong to any existing state environmental agency as opposed to general law enforcement.
One reason I say this, and it is intended as a general warning concerning the selection of specialist staffing as well, is that I can virtually guarantee that law enforcement of your state and major cities has already been infiltrated by members of the intelligence community, or would immediately so become upon passage of any such legislation. For this reason, the easiest way to assure failure of any mandate against electronic weapons is to simply hand responsibility for it over to law enforcement.
Keep in mind that the more exotic technologies are hardly used for their ultimate intended purposes at this time, but more typically used only in testing on unwitting guinea pigs, citizens at large, generally from among the underclasses, those persons least likely to be able to defend themselves or obtain the expensive helps required. Therefore, most victims are targeted not because of any actual political or intelligence value, but because of the value in learning how the technology works and how to best apply it without getting caught.
Now, regarding testimony from other parties, I might presume and certainly hope that many such victims will stand before you to offer testimony, and I beg of you not only to solicit for such witnesses, but to open your considerations to citizens beyond your state borders, that you may increase your chance at hearing the full truth.
Indeed, open your doors to Canadians, as well, for these weapons do not respect national borders, and are freely exported for testing and use abroad. And for every brave soul who dares stand before you in tortured fear of what will happen to them for their bravery, and an even greater fear of what will happen to them if they do not seek your help, there are likely tens of thousands of others on the continent which cannot or dare not testify. Regarding what they say, may I further advise of three additional points.
Regardless of how wild or bizarre may be the claims found in such testimony, there will be three absolute facts I can promise to be true regarding their claims:
1) among those testifying, you will hear persons who are:
a) legitimate victims of the technology and who are telling you the truth exactly as their ability to grasp and express it allows;
b) persons who are delusional and falsely believe they are victims, telling you of imagined things which have little or no basis in fact; and
c) intelligence community plants pretending to be victims in order to provide you with deliberate disinformation and, largely, to discredit the general value of all such testimony;
2) It will be impossible for you, short of elaborate investigation and expenditures of large sums of money, to make any useful determination of which category a given testimony falls within;
3) in light of the aforementioned difficulties, you should logically come away highly incredulous and doubting of the value of the entire collective of testimony, were it to stand alone.
This phenomenon (3) is a prime example of one of the chief purposes of political control technology, that of destroying the credibility of victims who dare tell others of their experiences. Think upon that, for a moment. Electronic weapons are designed to conceal their own use by making the victim seem incredulous. The testimony you hear will prove that it works exactly as intended. Do not discard the truth encircled by lies.
In light of these facts, I am moved to insure their testimony and my own presentation does not stand alone. I herein provide some meager proofs in the form of a technology review of some 250 terms and technologies of political control. A much more substantial body of such evidence is possible should it be required, which is why I have tried to include more valuable proofs in the form of references which are, by and large, easily obtained and verified.
This includes articles and scientific papers as well as actual patents on the technology itself. Patents are used only when other experts have already connected the technology to the claimed weapon. A reservoir of additional patents which could have been used, except for space and redundancy they represent, are included at report end. But understand that for reasons of national security, many more patents exist which were unavailable.
Also realize patent descriptions need not sound like weapons, partly as a natural result of the patent application process, and partly by design. Too, like many inventions intended for good, some patents having no apparent weapon’s application have been subverted to evil ends by someone who saw the potential…
In point of fact, the great bulk of evidential resources come from military documents, a matter which is deeply troubling to all right-thinking individuals because it paints a picture not of a military set on defending the United States from enemies who would threaten it, but a military which is the threat, itself… By the following materials, may you come to similar conclusions, and may you have the fortitude and resolve to do something about it, which is something we citizens cannot of our own accord achieve short of armed revolution. Please do not leave this the only remaining option for Americans, or that may be exactly what the next generations will need consider…
It was perhaps author Aldus Huxley, who first expressed concerns about political control technology, put into words within the fictional construct of Brave New World and Brave New World Revisited, Orwellian nightmares not unlike 1984. Based on 1958 technology, Huxley projected ahead a mere 40 years to describe exactly the kind of technology and social consequence which lays at the heart of our focus, here.
In point of fact, I hope to illustrate, we are well ahead of his projections. Welcome to the New World Order. Sheep, do not be alarmed at the slaughter of your fellow sheep. As it is for their own good, so will it be for you.
~ Sincerely, H. Michael Sweeney
 Unfortunately, as with all such legislation efforts at both State and Federal levels, the Bill was not passed, nor was it amended to make it more likely to pass. It was simply dropped. Too many powerful people, firms, and groups benefit from Political Control Technology to allow a mere Congressional representative the luxury of a morally correct vote or opinion. The Cogs of government work beneath and behind the visible mechanism of floor debate, and are turned by the steam of the Military-Industrial-Inteligence-Media Complex. What you and I think, need, or desire in the pursuit of freedom and happiness is irrelevant, as is anything as trivial as the Constitution and Bill of Rights.
Unfortunately, as with all such legislation efforts at both State and Federal levels, the Bill was not passed, nor was it amended to make it more likely to pass. It was simply dropped. Too many powerful people, firms, and groups benefit from Political Control Technology to allow a mere Congressional representative the luxury of a morally correct vote or opinion. The Cogs of government work beneath and behind the visible mechanism of floor debate, and are turned by the steam of the Military-Industrial-Inteligence-Media Complex. What you and I think, need, or desire in the pursuit of freedom and happiness is irrelevant, as is anything as trivial as the Constitution and Bill of Rights.
However, in 2004, a variation of the Bill WAS passed. It can be found here. A brief reading will find that not one of my suggestions was incorporated, and in fact, it specifically authorizes government to employ such weapons, the reverse of the need. All it does is makes it illegal for you and me. Like that was ever a threat. Yet the deem this legislation as an ‘Emergency Bill.’ Go figure.
Related articles
- Judy Wall (targetedindividualscanada.wordpress.com)
Timeline of Masonic/Illuminati/Mind Control Evolutions
From the Appendix of MC Realities: Understanding, Detecting, and Defeating Political Control Technologies
a book by H. Michael Sweeney – proparanoidpress.com
copyright©2006, all rights reserved This is an additionally annotated copy. Reproduction rights by request and approval, only
Sorry, there will be no links in the article, as it would take weeks to compile and make it harder to read (hundreds, closely spaced). Images are out, too, as visual formatting would be destroyed. Too bad, there are some really interesting ones.As a research guide, the following references do not always represent direct cause and effect relationships, but (unless otherwise indicated) at least visible relationships and ties. The expression ‘Masonic constructs’ means that various aspects of the organization or their procedures, especially secrecy, follow Masonic structure. When it says ‘formed by Masons,’ it means members, not the cult. A given citation in this list is not concrete proof, but merely a guidepost of where to look for such ties. However, inclusion is based on suitable ties being found by Author for the purpose to so conclude. In some instances, the basis is noted, but space limitations prohibit detail. Nothing contained herein is terribly hard to verify.
NOTE: You will see in review of this why so many people think that it is Jewish Bankers who rule the World, but they were never Jews, but Templars, in my considered opinion (the Rothchildes).
1118-1313 Knights Templar exposed to Assassins, Baphomet , Ritual Sexual/Satanic Abuse;
1313-1600 Pope Discovers Satanism, Disbands Templars, Rosicrucians becomes hiding Place;
1390 Stone Masons Guild (like a Union) socially prominent – NOT an evil group;
1717 Templars convince Stone Masons to accept them as Speculative Masons, establish Visible 33 Degrees – no masonry skills;
1776 Illuminati NWO effort founded by Adam Weishaupt, Satanist Mason;
Late 1700s Rothschilds become International financial banking giants: The Rothschilds (several spellings) were Jews, and they became the ‘basis’ of ‘Jewish Cabal’ accusations. However, my research leaves open the possibility that the y were actually Rosicrucians and former Knights Templar, who deliberately took on the identity of Rosicrucians and then Jews in order to escape detection and death. They became dominant world financiers in the manner of the Knights Templar by having family members establish banks in the capital cities of every European nation (as did Templars). Instead of shipping money from one bank to another and risking highwaymen robberies and international taxes and tariffs from multiple nations, they simply traded letters of credit. They were the first to invent ‘debt’ as capital, and in more modern times, it was the Rothchilds and the Rockefellers, et. al., who invented a similar approach to currency itself, resulting in the Federal Reserve System, which is owned by the bankers, not the government;
1769 -1815 Jacobian Society founded with Illuminati ties, will spur French Revolution, Congress of Vienna;
1825-1830 Unitarianism (Protestants), Mormonism (Masonic construct), Universalists (Masonic construct, first-step toward one-World religion) formed by Masons, League of the Just, a German-French Christian cult formed with simplistic Communist ideology;
1847-1860 Karl Marx develops early Communist dogma, while in influence of Cecile Rhodes and other Masons;
1864-1868 Civil War between the North and South: Rothschilds send Col. T.W. House to advise Lincoln, and dictates North war actions resulting in ‘powder profits’ in Europe and the U.S. while Southern General Albert Pike, Satanist, helps dictate South war actions resulting in ‘powder profits’ in Europe and U.S;
1867 Pike former KKK (Masonic construct), becomes head of Masons, writes Morals and Dogma, the ‘Masonic Bible’ which clearly spells out Satanic underpinnings, and parallels Illuminati plans to establish NWO in many ways, including the division and dilution of Christian Churches and sponsoring of Wars, especially between Muslim, Christian, and Jewish States. Masonry is a subversive group at highest levels;
1870 Pike establishes Illuminized Freemasons, incorporates higher than 33 Degrees, all secret and for dark works. Mason Cecil Rhodes is at Oxford, influenced by Rothschilds and Wartburgs — as inventor of Dynamite, the Civil War made him almost as rich; ‘powder profits.’ Rhodes uses his wealth to fund Rhodes Scholarship in pursuit of the same goals as the Illuminati (One World Government). In this same time frame, the Jehovah’s Witnesses are formed (Masonic constructs) and the Hermetic Order of Golden Dawn (Masonic, Satanic), and the Christian Scientists (Masonic);
1884-1911 EuroAmerican Alliances of Masonic and financial influence form: Rhodes, Rothshilds, Wartburgs, Rockefeller, Carnegie, DuPont, Loeb, Harriman, Bush, JP Morgan, etc. (oft called the RockRoth Alliance);
1913 Federal Reserve Established Foundations Established by RockRoth, American Press Bought by the ‘powder interests;’
1914-1917 WW I, ‘War to end war’ used as platform to promote NWO concepts: Col. E.M. House (Son of T.W. House) sent to advise President Wilson by Wartburg, Rothschilds, impacts war actions for ‘powder profits’ in Europe and U.S. At close of war, RockRoth moves: Council on Foreign Relations (CFR) Established, League of Nations established, Theosophical Society (Masonic cult) established to introduce New Age concepts, including marrying of religious beliefs into one-World religion;
1920-1921 It continues: World Union established, Lucis Trust (Satanic New Age) Pantheism, Humanism. Masons now headed by Alestair Crowley, Satanist. RockRoth interests found Tavistock Institute (U.K.) for ‘Pain studies,’ and ‘invent’ Eugenics; MPD/DID RSA (ritual satanic/sexual abuse methods of original Assassins learned by Knights Templar) mind control research is pursued;
1933 Roosevelt Assassination and U.S. Military Coup attempt by (many members of) RothRock (DuPont, Singer at point, Rockefeller insulated), Rothchild/Wartburg’s Central Bank prints so much money for Germany, inflation sets up need for War. Masonic Satanic Thule Society set up in Germany (Hitler a member) with ‘sister’ cult in U.S. – Skull and Bones. DuPont, JP Morgon, Warburg, Rothchilds help establish Kaiser Wilhelm Institute studies along same lines as Tavistock, under Dr. Mengele, plus Leibensborn Project to breed purebred Arians out of Wedlock. Program would evolve to become the sexual rewards program for exclusive use by SS Officers, who had to pass the strictest of tests for pure Germanic bloodlines. The Oxford Group founded the same year by the same general group of players, and Rhodes, asks Rockefeller to fund Alcoholics Anonymous, father to all twelve-step programs, which are a form of mind control and which provide access to secrets useful for blackmail when power players seek the help (one of the steps is usually to confide secrets, also present in Skull and Bones, et. al.);
1939-1945 WWII: RockRoth brings in E. M. House again. Harriman, Bush, others align with Axis and fund, do business with Nazi partners during war, later convicted of Trading with Enemy. Post war, United Nations Established by RockRoth, Operation Paperclip Imports Nazi Scientists including Mengele;
1947-1948 National Security Act urged by RockRoth threats to create the agencies with their own money if Government did not. CIA, DOD, NSA created, MJ12 Project (mind control), World Council of Churches, Church of Scientology founded (Masonic construct), Bilderbergers first meet, American Committee on a United Europe founded (ACUE), UFOs appear (MJ12, aka Majestic), Psychological Strategy Board (DOD psyops), Liberalization of Church Dogma. The many MK mind control projects following MJ12 spread out over the next two decades;
1950 L. Ron Hubbard gets going (fan of Crowley);
1959-1961 World Constitution & Parliament Association founded (WCPA) Masonic Satanic Ordo Templis Orientis reformed along with Order of Temple of Asarte, First Mass Shootings start taking place now as first-fruits of CIA mind control research – Manchurian Candidate programing, Unitarian Universalist Association formed (first marriage in one-World Religion process), Club of Rome (to establish European Community, ACUE partner);
1966 Church of Satan formed by Mason Anton LaVe, U.S. Army’s Psyops Michael Aquino is founding member;
1970s CIA establishes Cult Awareness Network (CAN), UFO Abductions reported in large numbers (suspected faked by Army to create MC victims through MPD/DID). Michael Aquino involved in pedophilia (McMartin Preschool) and DOD Satansim after doing psyops in Vietnam, works on Revolution in Military Affairs (RMA), Trilateral Commission founded, Operation Pique (radio frequency mind control) launched (precursor to many more, including HAARP);
1983-1988 Johnstown Massacre (CIA MC project) with CAN influence, EEG entrainment Radio Broadcast Same year, The Finders, The Franklin Coverup, Command Solo USAF air-mobile EEG platform, Provisional World Government established (WCPA) via ACUE, World Constitution Written, quietly submitted to individual nations for ratification;
1991-1992 European parliament Founded, Europe United, USSR Falls, EEG system GWEN Operational Same year, Taos/Oregon Hum start to be heard, False Memory Symptom Foundation (MFSM) Founded to deny MC exists… by ex CIA MC Scientists;
1993-1997 MC project Branch Davidians vs. BATF, CAN, US Army Deltas, CIA, Solar Temple Suicide Cult (CIA and BCCI scandal ties, derivative of Order of Rosey Cross — Rosicrucians… bringing us full circle). Shoot Americans Questionnaire, Interfaith Initiative launched – DOD via Michael Acquino at The Presido attempting to organize all religions into one CIA sponsored Church. HAARP goes on line, Heaven’s Gate Suicide Cult dies, RAATs Bioimplants developed by DOD (tested on Islamic students just in time for a rash of suicide Islamic bombers), Scientologists take over CAN (cute – a cult owns a professed cult fighting tool), Verachip ‘Mark of the Beast’ ID tracking implant authorized, RFID chips hit U.S. retail products, Total Information Awareness Office established;
Related articles
- Fundamentalists, the Illuminati, Freemasons, and the UN (leavingfundamentalism.wordpress.com)
- The Mystery Of Illuminati (mysteryworlds.wordpress.com)
- Meet the Ruling Faces of Evil (zengardner.com)
- Politics & NWO – Rothchilds and Rockefellers Merge Financial Empires NWO (disclose.tv)
- The Knights Templar today – who and where are they? (thetemplarknight.com)
- History of the Skull & Crossbones and Poison Symbol (mysafetysign.com)
Top 10 Reasons to Order Your Mass Murder Kit, Today
The Acme, Inc. Mass Murder Kit: Your ticket to a better tomorrow
a Farce in parallel to the Real World by H. Michael Sweeney.
There is only one link on this post. It goes straight to the heart of topic as proof of the farce we call ‘Terrorism.’
Acme Inc, a Subsidiary of New World Order, Ltd., and in partnership globally with numerous firms such as Central Intelligence, the Insurance and Logistics Agency, are now offering an easy-to-use Kit for mass murder. Now, with very little in the way of cost or obligation, almost anyone can become a mass murderer for fun and profit in support of their favorite cause. Financing and other aids available. When you order our kit, you will enjoy all the benefits with very little risk, since the purchaser will be fully protected from any downside!
• It’s Fun! After all, we all like to watch people fall down. Imagine how much fun it will be knowing it’s their last time!
• It’s Profitable! Your minimal investment in travel costs to meet covertly with our friendly yet paranoid sales staff will be handsomely rewarded with huge sums of money from sources like the World Bank, the IMF, and off-the-book black budgets. Why just one Middle East Client alone enjoyed two $500M payments, one just before, and one just after Sept. 11, 2001. And, he didn’t even order our best kit! His testimony follows.
• Full Confidentiality! Your agreement with us will enjoy National Security-level secrecy so that your identity and details of our contract will never be disclosed without your permission. We won’t even answer to Congressional Investigations! And just as importantly, our employees would rather die than betray your confidences. In fact, many have already met with ‘accidents’ to avoid such concerns!
• Free Publicity for your cause! Remember, there’s no such thing as bad publicity, and you will get plenty of it, to be sure. Even the smallest of test uses of one of our kits will reap huge headlines, because we have thousands of people we call Mockingbirds, who are positioned in Media so you feel like you have your own private Public Relations firm!
• Make New Friends! We can discretely arrange introductions to powerful and influential contacts like Bonesmen, Bilderbergers, Bankers (The Three B’s), and other Terrorists and Arms Dealers, and lots of individuals just as useful. They will love you and your work, too, as your power and influence grows with theirs in symbiotic relationships we help establish! Remember our motto: Globalism needs Terrorism to foment Patriotism to allow growth of Capitalism in order to drive Globalism.
• More Say with your Followers! Use our kit and, if deciding to ‘go public’ about aiding your cause, we guarantee your followers will not only look up to you in admiration and heed your words, but will grow in number as your popularity increases in leaps and bounds. In fact, if you do it right, you can become as powerful as any one of your peers… except the Pope and the Man Behind the Curtain. Naturally, we wouldn’t want to upstage the popular Antichrist or the real one, either.
• Culturally Enriching! The more you use the kit, the more you cause fruitful culture growth and evolution. Why just look at the changes in the societies of America and the World in the wake of Sept. 11. Imagine being able look into a mirror and to say with pride, “I did that!”
• Supports Green Policies! Improved sustainability and reduction of pollution caused by overcrowded population is achieved with each use of the kit. Depending on which kit you order, the aftermath may create large tracts of uninhabitable land which will be returned to Mother Nature for perhaps a hundred years.
• Many Models to Choose From! We offer all manner of kits so that there will be one just perfect for your needs. Our most popular and easiest to use is the Pyrotechnic Kit with a broad range of delivery options (e.g., plane, truck, covert placement); our flashiest and most exciting Kit is the new Atomics Kit, which includes free sunglasses and lead-lined gloves; but we also offer our new and most ambitious line of kits ever, the Bio Series, of which there are three to choose from. We have the standard model which impacts targets without recourse but fades out of its own volition with time and distance; the deluxe Race-Specific Pathogen model which targets only select ethnic populations with zero recourse; and the economy Viral model, which impacts everyone equally, but which can sometimes eventually be redoubted with vaccinations. Something for every need!
• Spiritually Uplifting! We know you, like us, are basically good Devil fearing Satan worshipers at heart, regardless of any requirement to profess otherwise. Certainly in spirit if not fact. Just know that each use of the kit is a kind of ceremonial event (a ‘sacrifice’) that not only fulfills prophesy, but brings the Antichrist one step closer to seating! After all, just like him, we all want to destroy all creation and life, even our own! We can help with that final, last step too, of course.
An Unsolicited Testimonial:
Hello terrorist posers! Get with the program at Acme and get serious! My name is Osama. You don’t need to know my last name in this public venue, do you? Ha, ha, ha… we all know who we are, don’t we? I want to tell you these guys at Acme know their stuff. I was not much more than a hired thug shooting at Soviets in Afghanistan for target practice when they approached me. Cost me nada to get started.
They provided everything, gave me the Royal treatment (Saudi Royal treatment), even better service than Acme’s most famous early customer, W. Coyote. But hey, that hairy looking Dude was narrow sighted and set small goals, not at all like you or me. Besides, his biggest problem was he didn’t realize ‘speed kills.’ Not Acme’s fault he failed time and again. I assure you, not that way for me!
I got a personal representative named Amriki from one of the Logistics partners called U.S. Army, and he handled the whole thing. He got me set up with followers, arranged for publicity by blowing up some American surplus war ship and some third-world (disposable) Embassies, and some parked cars in the basement of the World Trade Center. It all worked out so well we eventually decided to have a big wedding in New York! You probably saw it on TV. It was highly publicized and used a lot of remotely flown airplanes and stuff like that. I didn’t say that. Big oops. Ignore building 7, too, please. Really.
But the service did not stop there. No. When the publicity got so great that I could hardly stand it any more (my health was not very good, mind you), I took a long vacation and they ran the whole thing for me in my absence. Pina Coladas every night! And when I got tired and no longer wanted to be involved at all, and I realized I couldn’t possibly top myself anyway, they arranged for my terminating the contract (and everything else, really). I went out with such style that lots of people, even those in America who hated me, couldn’t believe it, and some even felt sorry for me and wanted a better funeral service for me than the bitter-sweet burial at sea we asked for.
I love these guys. You will too!
Citizen’s Viewpoint: We are ONE Person Away From Revolution
We all draw lines in the sand, knowing or not,
which if crossed, will see us engage in battle
by H. Michael Sweeney
I do not call for revolution. But I warn of it, and the why of it is quite obvious to me; too many of us, and in all walks of life, are openly using terms like Fascist, Police State, Dictator, Hitlerian, New World Order, and so forth. This should tell you the water is starting to boil. That governmentals fail to understand this mystifies me. Unattended, it will boil over, but so far, the only attention government is giving is to turn up the heat is to madly develop more Political Control Technology and Draconian measures as if believing they can absorb the spillage. So it behooves you, the reader, to consider just what lines in the sand might be important to you, as well as what your role would be in any such revolt. After all, you have three possible positions: stand for freedom; stand under the yoke; and attempt to remain neutral, each considered below.
This is the third in a series of blog posts about the likelihood of armed conflict in the United States to regain control of government and restore the Constitution. Other supportive articles have also been written before the need to write had been sensed, and have become more relevant thereby. The first post, What Does it Take to Start a Revolution discussed how scary it is that it takes so very few people to start a revolution, and how low the cost in life tends to be, and the role of government in its own demise. The second, Military Viewpoint: We are SIX People Away from Revolution, revealed that such a revolution may be forced upon us by the Military itself by seizure of government in a de facto military coup, likely involving a massive terror event, be it false flag or otherwise.
Note: The war on terror is about control; fear is license for control. That’s why false flag operations are repeatedly found through history to be an all-too-common principal means of empowerment to evil men. Ask Hitler, for instance, the archetype of today’s modern Fascist. Do not be so foolish as to think there are no such men in our military and in government. And, know they are Fascists, and tend to occupy all high places in time.
This post, though perhaps the most important of the series, concerns only one small aspect of topic. It reviews the ONLY matter which defines the individual’s role in any success of a revolution, and as important, the ability for them and their family to well survive it. In other words, your very life and the future of your nation rest on this one small thing: how will you know when the day comes, that day the military thinks is inevitable (as do I), and people start to pick up their guns and say, ENOUGH! And, what will you do about it? Fortunately, guns are not the only answer.
That moment of decision can be different for each one of us; the defining moment when government crosses a line in the sand we have premeditated or which we may not have foreseen, an event which pushes us to that state of no return. When that happens, the individual starts working in full measure for the downfall of tyranny and restoration of freedom. Some have already reached that point. Hence, the phenomenon called Anonymous. Thankfully, there has yet to be any shooting or other violence of consequence from any quarter, certainly not Anonymous, who carefully points out the folly of it.
That could change overnight. It only takes one lone, frustrated individual to make a mistake… though history proves it could also be the right thing if the right circumstance, reason, place, time, personages, result, and consequence. But I for one, would hate to try and second guess that much risk and any ability to control it to predictable outcome. I have no bravado for foolishness, and would discourage others from presuming for themselves such a fearful and dangerous confidence. Yet I hold my breath because, as singer Phil Collins has so well sung, ‘I feel it in the air…’
On remaining neutral when it hits the fan…
From government’s viewpoint, you are either for them or against them. Those who are neutral (pacified or fearful to move) will be viewed with great suspicion and dealt with accordingly. The likelihood of being able to remain neutral without joining in the revolt is slim, because being neutral will mean targeting of the sort likely to cross a critical unstated or belated line in the sand (e.g., detainment and questioning most unpleasant, confiscation of property, denial of employment, etc.). There is even less a chance that you would ever be allowed to join government’s side, as you would not be trusted. The longer one waits to decide, the more dangerous their position becomes… neutral could be the worst place to be of all.
On standing under the yoke
Unless in an active support role (e.g., a Policeman, vocally supportive public person, etc.), your only value to government is that you are not an opponent, but it does not mean you are not in the way. On the one hand, you are acceptable collateral damage if unfortunate enough to be standing in-between them and the opposition in a conflict. When they cannot visually discern which you are with ease, they presume you guilty by the association of presence. This is a very dangerous role to undertake, because on the other hand, if you stand with government in opposition to the Constitution and openly support tyranny, those in revolt may deem you a viable target for retribution.
This results in a kind or risk of being caught in the cross fire, despite intentions of seeking a presumed safer position. I would not want to be in this category unless so high on the food chain that I was well protected by armed men… presuming I was so faulty in my thinking.
But then, high-powered crosshairs tend to easily bypass and render moot such protections, a cold hard fact.
On opposing villainy
This is the more enviable position in any logical review, and is in my opinion why successful revolutions tend to succeed with minimal loss of life. You know where you stand and it is not under the yoke. You know who you trust and you have allies you can count on solidly. But, of course, you have a clear and present danger against which you must steel yourself. If one would read my book set, Fatal Rebirth, there is advice to such persons on how to better defend and more wisely prosecute a successful effort of survival and victory. But do bear in mind it was written as fiction some two decades ago (predicting 9-11 and resulting Middle East oil wars) and was talking about a revolution forced upon the people… a bit like we are starting to face today. This is what makes knowing about lines in the sand so important.
The other reason this stand is more logical, is that in full-out revolution, the forces of the other side tend to switch sides as time passes. Elements and whole units of Police, military, and their supporting or directing resources start to see the light, either because they are being educated by what they hear and see happening, or because they start to see who is going to win. They bring real hardware assets with them for use against those still opposing. I seriously doubt, for instance, that many in the U.S. Air Force will stand by and let the U.S. Army use helicopter gunships and tanks on protestors, as indicated as likely according to Army manuals on dealing with civil unrest here in America. Clearly, that’s a crossed line.
Lines in the sand
For some citizens, such lines have already been crossed, perhaps again and again, and they are already actively working to destroy the corrupt government or prepare for the day when the point of no return comes. This even includes secret organizations operating covertly within the branches of the Military, for instance. Government is rightly paranoid, for they have made themselves enemy to their own. They have forgotten the most basic principle of their charter (the Constitution and Bill of Rights), which is that they are supposed to be a government of the people, by the people, for the people. Instead, they see themselves as a government over the people, and continue to usurp more and more power without regard to the rules of the charter (law of the land). A government which no longer obeys its own law is an outlaw awaiting a day of reckoning, and deserves no mercy.
We should perhaps review lines already crossed, because they happen so quickly and generally so quietly that most are unaware of at least some of them. There are, in fact, so many that rather than attempting to list them, I will instead simply cite other posts which are their own lists, as found in the Related Articles at page bottom).
For most of us, however, while we may grumble that a given action or law already upon us was criminal or unjust, it did not cross a line we had set, and only served to heighten our awareness (which this blog series also attempts). We sense something is intrinsically wrong and are starting to wonder what we should do about it. We are Sheeple starting to wake up, but yet dazed and confused, by and large. We are frogs who. though quite concerned, are not yet quite ready to jump out of the water as it nears boiling. Only those who do can have a chance to survive the experience, sadly.
Those of us less confused have already awakened and defined lines in the sand. I first stirred in 1961, when as a high-school Freshman, Eisenhower warned us about the Military-Industrial-Complex in his Farewell Address, now the Military-Industrial-Intelligence-Media Complex. I was more rudely fully awaken when that very Complex killed John Kennedy, and later, his Brother, Robert, and then Martin Luther King, and thus I started formulating lines in sand. Others will not awake or realize such lines exist until it is too late to usefully do so, and they have been crossed to no good end. What a rude awakening that will prove to be!
My personal lines in the sand
Martial Law and Suspension of the Constitution: There are variables in any such action which may or may not validate the event as worthy of sparking revolt. Read the prior post and the hesitancy will make a lot of sense. At the very least, however, any such event will force people who see the danger present to take steps to prepare for their defense and assure they retain an ability for offensive capabilities, because you can bet they will go door-t0-door to collect our guns.
Three key questions would be: are they relocating National Guard units to neighboring states, calling in the United Nations (real and/or bogus U.N. troops), or segregating units and sending some troops home and others abroad from the same units? Any of these three steps indicates an intent that there will be shooting of Americans who resist, per the prior article’s proof and the earlier cited proof from an Army manual.
Note to activists. You are already on a list of people to be watched. If Martial law is declared, there is an extremely high likelihood that all such persons will be rounded up and vanished. So THIS should DEFINITELY be one of your lines in the sand. Have an escape plan, as do I, and establish a network which will give you advance warning, because the roundup will take place BEFORE the actual announcement and commencement. The NDAA assures you of that.
Mandatory chipping: any order requiring a National ID Card, perhaps disguised as a driver’s license or health card, or actual implant of a biochip such as Digital Angel by Verachip, a CIA proprietary will set me off. These steps will allow unlimited tracking of individuals and are essentially THE Mark of the Beast or their forerunners, all of them based on RFID technology. When Biblic End-Time prophecy itself is fulfilled by government, the end is near, and the revolution which follows is not to save the nation from tyranny, but the World from the Antichrist and Armageddon. That kind of raises the stakes, does it not?
Calling for a CONCON and installing a new Constitution: A ConCon is a Congressional Constitutional rewrite effort whereby Congress can create whatever government they wish. As mentioned in the prior article, The Constitution of the NewStates of America has already written by a CIA think tank, so they need only ‘sign off’ on it and have it ratified. That’s why they have worked so hard to gain control of individual States in elections. If pressed, I could cite several examples where CIA sponsored candidates for Governor and State and Federal Congressional posts, and so forth, have been fielded. Bribery and blackmail work well on yet others. So if they hold a ConCon, you can bet the ratification is not far behind, no matter what you or I might say or do to argue against. Such a document will enable the North American Union, and be a stepping stone to a one-world government, which in turn enables the seating of the Antichrist. Really hot water, again.
A Pandemic and forced inoculations, or closing the borders: The topic is far too broad to be covered well, here. But my research into the 50 Dead Microbiologists as detailed in Fatal Rebirth, and a mountain of other material which has since become public, convince me that any such Pandemic is merely a tool to seize power, and it will very quickly escalate to include Martial Law, and all that goes with it. I fear that the inoculations will be a death sentence for the Politically incorrect, and a means for vanishing us. There is also a significant possibility it will allow covert injection of race-specific pathogens to target Muslims, Blacks, or Asians. Such terror bio weapons have been developed. Closure of borders is a sure warning sign that events akin to these concerns is about to come down. I have a contingency in place. Do you?
Sedition legislation or executive orders or other takeover or closure of the Internet: If they move to make it illegal for citizens to criticize government, or take away our ability to freely do so without penalty or censorship by decree or technical means, it is war. Period. For me, as an author and activist, that also means any assault on my personal ability to so outreach, such as shutting down or seizing my server or taking actions (e.g., dirty tricks) to destroy me financially.
Currently, for example, I’ve been hit with a huge tax bill out of the blue which I have no hope of paying off in the manner being demanded. While I have friends who have owed more than this for more than a decade, I’m being asked to pay it all off within a year. It’s only a few thousand dollars, but I’m unemployed more than two years, now, and, because of disability and my age, not likely to find a job. If they force the matter with garnishment of my Wife’s meager income, the hardship would likely foreclose on my ability to make myself heard. Anyone have about $6,000 they don’t need? I could handle the tax on that. I take PayPal, by the way 🙂
Any personal attacks against me or my family: This I suppose is a kind of catch all. Being arrested and subjected to TSA/HSA/FBI style abuses, for instance, might represent such a line. More likely, however, depending on outcome and steps employed, it will merely make me martyr and sponsor a growth in my following which makes me more dangerous to their tyranny than I am now. So I’m not expecting this to be a problem, though I have contingency plans in place. So should you, if activist.
What lines will you draw, how will you respond if crossed?
I cannot speak for you. I cannot tell you what to think, or what to do. I can only warn you that if you do not draw a line, have it in mind, and speak openly about it with others, you risk that line being crossed and catching you unawares. As stated earlier, that is not an enviable place to be. But by being open, you and others become aware, including government. They need the warning, you see, that they might understand that they are playing that game of Russian Roulette every time they elect a Draconian act. At some point, we might reasonably hope, they will see the error of their ways by our vocal protests, and recant. That’s what being a Citizen is all about; effect government by your voice — not just at the ballot box, but in polls and blogs and Facebook and Twitter and face-to-face with everyone you can.
In the face of tyranny, activism is not an option if you want freedom instead
So you see, none of this dialog, nor anything in my book, is calling for revolution. Instead they seek to avoid it by warning of it. Not warning just you, the reader, but those in government who need to hear it most. Also understand ONLY YOU can make that so, by in turn engaging in such dialog with others. Smokey the Bear might say, ‘Only YOU can prevent Fascism.’ He would be right. So be mindful, be active, and be prepared.
If a line is crossed, consider your method of resistance. Some will choose the gun. Others will find other ways to fight, many not involving combat at all. All will be aggressively targeted by government, but few will be easily defeated if they have contingency plans in place and networks of allies. PLEASE, if considering what you will do, especially if aggressive in nature, read Fatal Rebirth, because it contains logical rules of engagement intending to reduce loss of life and assure popular support. It covers both defensive and offensive considerations. Again, keep in mind it was written as fiction and not calling for revolt, but depicting what might happen if government forced it. Still, the great bulk of it is appropriate for tactical consideration in exactly such a case.
I hate that it should prove so.
The other side has blinked, their wall of deceit cracking
There are signs the edifice of tyranny is starting to crack under our constant cries of unjust an unconstitutional behavior. They blinked when the 99% took to the street, but then played Russian Roulette and passed a law making such protests illegal when inconvenient to government. The World-wide protests have made the NWO realize they cannot continue their power hungry course without opposition. This makes them exceptionally dangerous and unpredictable, perhaps forcing them to move their plans forward while their strength is still in tact. If you don’t know what lines in the sand you will not allow them to cross, you may fall victim if they do. Beware. Be informed. Be alert. Be ready.
And I’d like to help. I’ve lifted the copyright restrictions on Fatal Rebirth and reduced the price. I assure you there is a wealth of more solid, useful information there than in all my blogs and tweets combined. If buying the ebook set on CDR, the purchaser can copy and distribute it to others at no charge. There are stipulations. Learn more, in this post on Federal Reserve criminality.
Please comment with the lines in the sand you feel important!
Related articles
- Military Viewpoint: We are Six People Away From Revolution (proparanoid.wordpress.com)
- What Does It Take to Start A Revolution? (proparanoid.wordpress.com)
- Do We Need and Should We Start a Second American Revolution? (godfatherpolitics.com)
- On Routine Political Assassination of U.S. Citizens; a Simple Remedy (proparanoid.wordpress.com)
- 24 Campaign Planks; H. Michael Sweeney for President of the United States? (proparanoid.wordpress.com)
- Guest Post: Americans Are Being Prepared For Full Spectrum Tyranny (zerohedge.com)
- We Live in a Gestapo State (lewrockwell.com)
- Stand Your Ground: Revolution of the Working-Class (fidlerten.com)
- Obama’s DHS Monitors Liberty Loving “Terrorists” (freemadd.wordpress.com)
Military Viewpoint: We are Six People Away From Revolution
High Ranking Military Says Martial Law Likely,
Armed Conflict with Citizens On The Horizon
by H. Michael Sweeney
In an earlier article we reviewed just how easy it is to start a revolution, how few people it takes, and how remarkably little it can cost in lives. That was based on such a revolution being initiated by popular revolt of the people. In this article, we examine the possibility that such a revolution could be sponsored by military action, either an outright military coup against which the people rally in protest to restore the Constitution, or in which the government is indeed taken over and becomes a military police state without useful resistance. I sure hope neither path could be true, but there is a lot to make one wonder…
In my book, Fatal Rebirth (proparanoidpress.com), I quote U.S. Army General Tommy Franks on this topic. You remember him? He’s the guy that commanded the flame throwing tank at WACO that first injected lethal gas into their underground bunkers where the children and women were, and then burned most of the rest of the Davidians alive.
You know BATF were pretty badly threatened by those darned Bible thumpers, because all the videos showed gunfire in only one direction… in. Not one bullet hitting a vehicle or the ground from which the ‘good guys’ that later bulldozed the place and concealed all possible evidence were shooting from. Here’s my footnote from Fatal Rebirth on what Franks had to say on topic.
4 Newsmax, Nov. 21, 3003: US Army General Tommy Franks, who led the coalition invasion of Iraq to oust Saddam Hussein, is reported to have described in an interview to be printed in the Dec. issue of Cigar Aficionado, that the results of another attack by terrorists with weapons of mass destruction would result in our Constitutional form of government being replaced by a Military government. Don’t cry for us, Argentina!
An aside about the tank at WACO. That tank came from the local national guard which had a number of units ready to go, and one unit that was in the shop. Why, do you suppose, did Franks, instead of having them get one of the tanks ready to go, to instead send a truck for the tank in the shop… which he then had trucked to a CIA/DOD contractor for ‘special work,’ and then sent directly to the Davidian farm? I hope you have nothing in your hand to throw at the computer screen when you read the answer…
Because the tank in the shop was the only one on the base that was a flame throwing variant. This was all reported by activist/lawyer Linda Thompson, who even acquired the serial number to prove it. She also reported that the few survivors were not taken into BATF custody, but to the same CIA proprietary where the tank was modified for ‘rigorous debriefing.’ That’s how you get the really good confessions!
Franks is not our only source. The above cited footnote was in a section talking about the military’s use of the “Shoot Americans questionnaire‘ given to various military units which I reproduced in my book, The Professional Paranoid Defensive Field Guide. Of course, the military called it a ‘Combat Arms Survey,’ and claimed it was not official, used only once with a room full of guys from one unit, and intended only to help some Lieutenant write a thesis. Too bad GIs began popping up out of the woodwork at dozens of other units and multiple branches of the military to counter those claims, or we might actually believe the DOD tells the truth once in a while. Operation Northwoods had nothing to do with Sept. 11, right guys? Right.
This ‘one time’ thingie was a ‘rating’ questionnaire, which means that answer choices were ‘Strongly Agree,’ ‘Agree,’ ‘Disagree,’ ‘Disagree Strongly,’ and ‘No Opinion.’ Check out some of the questions, some paraphrased or concatenated for space conservation. The first batch relate to use of military for illegal use against citizens in violation of Posse Comitatus:
Do you feel that U.S. combat troops should be used within the United States for (several things to be answered individually followed): Drug enforcement; Security at national events (e.g. Olympic Games, Super Bowl); Substitute teachers in public schools; Federal and State prison guards; National emergency police force; Advisors to SWAT units, FBI, BATF, etc.
A number of questions related to United Nations loyalty
U.N. Combat troops should be allowed to serve in U.S. military training exercises under U.S. command or vice versa? The President of the U.S. has the authority to pass his responsibilities as Commander-in-Chief to the U.N. Secretary General? I feel there is no conflict between my Oath to serve and serving as a U.N. soldier? U.S. units should be permanently assigned to the United Nations? I would swear to this oath: “I am a United Nations fighting person. I serve in the forces which maintain World peace and every nation’s way of life. I am prepared to give my life in their defense.”

This image is decades old: WWII trucks with UN markings on U.S. highway
An aside about United Nations involvement. For more than twenty years there has been an unending stream of concern that U.N. Troops might be called in to suppress U.S. Civilians in a civil unrest situation. We can thank, I suppose, Henry Kissinger for the fear, because it was he who said, “Today America would be outraged if UN troops entered Los Angeles to restore order. Tomorrow they will be grateful! This is especially true if they were told that there was an outside threat from beyond, whether real or promulgated, that threatened our very existence. It is then that all people of the world will plead to deliver them from this evil. The one thing every man fears is the unknown. When presented with this scenario, individual rights will be willingly relinquished for the guarantee of their well being granted to them by the World Government.”
He is frequently quoted as saying that at the 1991 Bilderberger meeting. If you don’t know who they are, stop reading and close your eyes some more. It will all be over before you know it. In part perhaps, because over the twenty years there have also been a steady stream of reports and photographs of fleets of U.N. vehicles on truck convoys, long trains of flatbed rail cars, and stored in massive lots behind guarded fences protected by Men in Black. The Spotlight newspaper in Washington, D.C., now defunct, was awash with them. The thing about these U.N. vehicles is that they were almost always WWII U.S. issue or Soviet surplus, neither of which are used by United Nations troops. So if and when you seen them deployed, know that whomever is driving them is NOT a U.N. Soldier. Hmmm… Such disguises in times of war (revolution is war) calls for a firing squad.
In all, there were 46 questions. The last was the big one:
The U.S. government declares a ban on possession, sale, transportation of firearms. After 30 days to turn in weapons to authorities, a number of citizen groups refuse. I would fire on U.S. citizens who refuse or resist confiscation of firearms?
The final tally?
The answers to the test (the original bunch of guys — 264 in all) were scary: 1 in four Marines would shoot you. Four out of five will Police you at Super Bowl or hassle you for drugs. And 85 percent of them would happily become a National Police force. Apparently very few had ever heard of the Posse comitatus Act of 1878 forbidding military use against citizens without declaration of Martial Law.
All of the above crap, from Franks to the questionnaire, evolves out of something called the Revolution in Military Affairs, or simply RMA; the notion that the mechanics and nature of warfare have changed so much because of advances in technology and societal change that it was time to examine the military belly button. What they came up with was scary as hell, and it is expressed in a whole new catalog of military terms never before used. I list rather a lot of them in the Defensive Field Guide as part of a list of 500 Political Control Technology terms and technologies. Here are just a few of the RMA terms which reveal military’s thinking about their role and yours in our near future. You won’t like it.
People’s War.This term first appeared in an article on RMA in Parameters, the Army War College publication. It was quoted in The Spotlight, now defunct. From memory I paraphrase with no liberties taken. None are needed. It stated that People’s War was one of the most likely kind of war on the immediate horizon that would be new and unique. It defined it specifically as combat with Constitutionalists, ex military, survivalists, the poor and disenfranchised, and patriots. Excuse the hell out of me? How does that jive with their oath of office? Why should we allow them to retain force of arms with that kind of fuzzy logic running around loose under their helmets?
Here’s another term. 21st Century Politico-Military Force Matrix. That means that there are a range of alternative ‘forces’ which can be applied by politicians against a target group (e.g., civilians) to effect and enforce ‘policy.’ Police, military, intelligence, lethal, non lethal, psyops, disinformation, and on and on, are elements which can be employed: He who uses the best and most appropriate choices wins. Yeah… like Franks won at WACO!
But what does this all have to do with six people, and who are they?
Simple. The five Joint Chiefs of Staff, and one other person are the six, and they are all that is needed to launch a takeover via martial law in this country. The sixth could be any one of several people. The President of the United States is the most logical sixth, but the Vice President and the Speaker of the House, and a finite list of others could also be the sixth depending on who is incapacitated in that list, be it intentionally arranged for convenience’s sake, or by happenstance. But that is not all.
There are numerous laws passed by Congress and Presidential Executive Orders which have been passed to create and activate FEMA, the Federal Emergency Management Agency. Currently, the United States still stands in a State of Emergency declared by President Bush for 9-11 which has never been rescinded. Technically, the head of FEMA could arbitrarily pick up the phone and arrange for martial law, but again, this would not likely take place without first eliminating the President. In fact, a terrorist event which eliminated the President might be just the things… allowing both Tommy Franks and FEMA to go marching along the same goose-step toward a Fascist police state. Of course, it could be FEMA which gets the phone call from someone in the Pentagon… “We are going ahead according to plan tomorrow morning at 0800 Zulu.”
Welcome to the NewStates of America. Oh, didn’t you know? The Constitution of the NewStates of America has already been written. Remember Bill Cooper, former Naval Intelligence Officer turned whistleblower. He uncovered it. You can find it in his book, Behold a Pale Horse, or in my book, Fatal Rebirth, where it is fully analyzed to reveal the Fascist tool it is. Bill said they spent $25M writing the document at an intelligence community (NWO) sponsored think tank. You don’t suppose they would go to all that trouble if they didn’t think they had a way to use it, do you?
Now take a look at the final post in this series: The Citizen’s Viewpoint.
Related articles
- U.N. ATT treaty, if ratified, would surrender U.S. sovereignty by shredding the 2nd amendment (illinoisreview.typepad.com)
- What Does It Take to Start A Revolution? (proparanoid.wordpress.com)
- U.S. soliders forced to wear U.N. logo? (wnd.com)
- ‘Newly Leaked’ Army Manual Trains MP’s to Kill US Protestors – Without Firing Warning Shots (patriotsandpaulies.wordpress.com)
- 24 Campaign Planks; H. Michael Sweeney for President of the United States? (proparanoid.wordpress.com)
- Army Begins Training MPs To Drive Tanks on U.S. Streets (zazenlife.com)
- Russian Troops To Target Terrorists in America As Part of Drill…Joint U.S.-Russian anti-terror exercise stokes fears of martial law… (projectworldawareness.com)
- Real Red Dawn? US Calls for Russian Troops To Take and Hold Denver Airport (survivalblogs.com)
- Has the POTUS declared Martial Law in America? (greenreview.blogspot.com)
- Media Promotes Troops On Streets to “Cut Down on Crime” (informationliberation.com)
The Olympics and Political Control Technology; Formula for Control
A Method to Control Athletes as Well as You and Me
by H. Michael Sweeney
A contract Journalist named Terri Hansen recently published an article through Mother Earth Journal the deserves our attention. Titled Intentional Radiofrequency Targeting Affects Olympic Performance, Leaves No Trace, it cites insider information which reveals a serious threat no one has previously suspected. She cites the warning words of wisdom from insider to British military and intelligence community covert electronic weapons development and deployment, retired Physicist Barry Trower — from an interview for ICAACT, the International Center Against Abuse of Covert Technologies.
A former Cold Warrior, Barry has in recent months become quite outspoken about not only the dangers present in weaponized technology of this type, but also, civilian use of non weapon sister technologies, such as cell phones. Learn more about what he has to say along those lines in this transcript of an interview with a South African radio station.
I’m writing here to confirm the validity of this story and to add key detail
As published author with seven books generally on topic and two specifically on topic, it will be easy to do. In fact, in my book, The Professional Paranoid, 2nd Edition (2005 — proparanoidpress), a defensive handbook for targeted individuals, I wrote about a CIA/DOD contractor VSE Corp. which, according to Public Relations material provided by them on line, actually took an unmarked van to a Winter Olympics (in an unspecified year prior to 2001) for testing their newly developed LADS system on Athletes. I quote from their own information, below, which predates 2001, when I first mentioned it in my newsletter.
LADS stands for Life Assessment Detector System and is supposed to be used for finding signs of life in rubble (e.g., collapsed buildings) or locating villains behind walls for the benefit of SWAT or military sharpshooters. It is only one of several ‘see-through-the-wall’ (or other barrier) technologies developed in the last few decades. It is sophisticated enough that it can identify one human from another if needed, provided pre surveillance of the target subject has captured the needed data. This entire project had, since the publishing of my book, apparently gone dark as VSE deemed to remove all references to it from their Web site shortly thereafter. While, perhaps thanks to me, you can find lots of information about LADS from other sources on line, you won’t at their own Web site. Quote on:
LADS consists of a sensor, neural network, and control/ monitor modules. The sensor module is an x- band (10 GHz) microwave transceiver with a nominal output power of 15 mw, operating in the continuous wave (CW) mode. The neural network module device can store many complex patterns such as visual waveforms and speech templates, and can easily compare input patterns to previously “trained” or stored patterns. The control/monitor module provides the L A DS’ instrument controls, such as on-off switches, circuit breakers, and battery condition, as well as motion, heart- beat waveform, pulse strength, and pulse rate displays. End of VSE quote.My book further states; They talk about a test, for instance, at the U.S. Olympics. What sense does that make, you ask? They parked an unmarked van near the Alpine Skiing and Shooting event’s shooting positions, and used LADS on the competitors. The goal was to measure and IDENTIFY each shooter by their own individual biometrics (i.e., EEG, breathing pattern, pulse rate, etc.,) WHILE SHOOTING. Thus they have both individual patterns to allow them to recognize specific shooters, but also, information useful to identify (based on the aggregate or average readings) anyone entering into an aim and shoot situations. In other words, they can tell when someone is about to use a weapon. End of quote from book — but clearly, this means EACH competitor had to have earlier been surveilled by this same technology well in advance of the test. Scary.
But there are things even scarier
In the broader view, I have variously written in my books and newsletters describing over 500 terms relating to Political Control Technology such as LADS, perhaps more than two dozen of which are related to LADS in design, capability, or purpose, at least as offshoots or predecessors, if not outright evolved supersets. The LADS tests at Olympics were harmless enough only because LADS was a ‘sense only’ technology. However, part and parcel of this kind of technology, which might be called ‘remote physical’ capability, which is to say, it senses things about the subject at distance as if hooked up directly to medical test gear… is EEG brainwave monitoring.
Note: for a free sample copy of my newsletter which features 250 such terms, including LADS, email proparanoid at century link net.
The interesting thing about EEG monitoring is that a ‘catalog’ of brainwave patterns can, in LADS-like fashion, be used not only to identify individuals and their specific physiological and mental states in select states of mind and body, or tasks undertaken, but to feed it back to them for instant adaptation, a phenomenon called ‘entrainment.’ All they need to is to rebroadcast the signals back at them at stronger levels than their own body would be able to generate. The human brain instantly entrains to such a signal. Of course, the brain’s state definitely impacts the remaining physiological functions of the body accordingly. Now that’s truly scary!
Such technology is quite frequently found to be in use against politically incorrect citizens, generally to cause yo-yo mood swings, and bounce them back and forth between sleepiness and wakefulness in ways which mimic general torture methods based on sleep deprivation and denial of self. I work with such people as consultant every day (you may also ask for a free Helps Kit if you fear you may be such a victim). If used by one country in an Olympics against foreign competitors, it would be quite simple to ‘throw their game off’ sufficiently to allow an easier victory. It could also be used on one’s own athletes to better insure ‘top game’ performance. It is, sadly, undetectable except by the most sophisticated of TSCM equipment (Techincal Security CounterMeasures), and so doing requires perhaps a million dollars worth of gear and well trained experts, generally costing many tens of thousands of dollars per deployment. Even then, given the covert development of this technology, there is a risk they would mistake it for something less insidious and give a thumb’s up.
This technology is currently down to the size of a cell phone for portability in applications where the subject is within close range, perhaps 50-200 feet or less, and powerful tripod systems can accurately target people where there is line-of-sight capability from many thousands of feet, and even miles away. It is perhaps important to mention that one reason this is so easy to employ is that the signals are highly directional and narrow in beam. Another is that the signals can be so highly matched to the target subject that even when accidentally hitting a bystander, they do not have the same effect. But the most important reason is that, except where the individual has been trained to sense the signals (I train my clients in such methods, where possible), or they are already hypersensitive to radio frequencies, they have no understanding the attacks are taking place. It all seems natural. Unpleasant or unwanted, but natural.
Political Control for the Masses
The real question is not ‘Is this technology being used at the Olympics?’ because it most likely is given the ease of deployment and the tremendous value placed on success in Olympic events by nations and corporations. This equipment is in the hands of almost every industrialized nation on Earth, and not just in government hands. Corporations and perhaps even criminal groups have access at least to older versions. Even technically skilled civilians using information available on line can build devices in this family. That kind of technology in the hands of a major betting parlor would be worth millions, and in in similar ways greatly amplifies the value of advertising dollars for corporate sponsorships.
No, the real question is, ‘Will the Olympic authorities choose to believe there is a Boogyman and do what it takes to defend against them, or not?’
To do so would fly in the face of over half a century of ‘logic’ by authorities of all manner who, when approached by persons targeted with such technology, preferred instead to simply deem them Paranoid or even Schizophrenic, and shove them aside and deny aid with jokes about ‘tin-foil hats.’ Sad, because such hats work, and that’s one reason such joke are so mainstream — to make anyone in need feel and look foolish using them. For any authority, it is far easier to let the Boogyman run free, than admit the possibility of existence. Besides, any public statement of detectible use of such technology would undermine the ‘notion of fair play’ expected in the Games. It is one thing to have rules for athletes to follow and tests to insure they do not abuse drugs for a competitive edge, but quite another to set rules and employ tests for government’s fairness in play.
Yet to do nothing may well eventually lead to the revelation that there is no purpose at all in watching or competing in the Olympics, because the entire affair was nothing short of a puppet show, more a colorful, scripted charade than a sports competition. But that thought brings us to another unpleasant notion. The real value of the Olympics in the first place is its power to distract and control the masses globally, and promote globalist corporate interests. Those of us glued to the TV will not be busy protesting the G-12 or WTO gatherings, or occupying more than our living rooms, closer to a functional zero than a potent 99%.
So what do the globalists care if the Games are on the up and up, or not? Zzzzzap! Score!
Related articles
- Effort to ‘read’ Hawking’s brain (bbc.co.uk)
- How Sci-Fi Becomes Reality – Mental Manipulation (theurbn.com)
- Synthetic Telepathy And The Early Mind Wars (powersthatbeat.wordpress.com)
- Wes Moore ~ Television: Opiate of the Masses (Thanks, C) (shiftfrequency.com)
How to Deal With Terrorism (How to Love Obama bin Laden)
A Privacy/Security Consultant’s Personal Advice in ten steps
farcical advice, that is, by H. Michael Sweeney permission to duplicate in full with all links and credits in tact, and a link back to proparanoid.wordpress.com hereby grantedHow to deal with terrorism by Obama bin Laden
Updated Sept. 16, 2012 to add 8th ~ 10th Steps, and supporting links and notes
In the face of the horror of September 11 and all the dire plots thwarted or predicted since that time, what can you do as an individual to best deal with and be prepared for terrorism? With seven books generally on topic, here is my considered professional advice in answer to that question:
 1) Yawn. Even including the casualties of Sept. 11, you are statistically in far greater danger of being killed or seriously injured by a Policeman or National Guardsman than some crazed and largely imaginary terrorist. That is a fact. They would have to pretty much wipe out all of Los Angeles in order to have equal odds.
1) Yawn. Even including the casualties of Sept. 11, you are statistically in far greater danger of being killed or seriously injured by a Policeman or National Guardsman than some crazed and largely imaginary terrorist. That is a fact. They would have to pretty much wipe out all of Los Angeles in order to have equal odds.
2) Prepare for the worst. Even though the Terrorist is not likely to get you, there is a growing threat to your personal security and longevity which is tied to the ‘terrorist threat.’ It’s called Fascism, variously described as a Police State, or Military Dictatorship, or the New World Order. If your prefer, think Martial Law, FEMA Camps, UN Occupation, Chinese Invasion, our next (overdue?) Revolution, intentionally Bankrupt Banks or, (gasp!) mass Walmart Closures. Regardless of manifestation or name (I prefer Shadow), and regardless of what you believe, such disaster is a more real threat. And regardless of final form, it is going to impact everyone, not just those attacked by Police, National Guard, Terrorists, and unemployed Wallmart staff.
3) Increase key supply reserves. You must presume in time of National emergency that water, foods, gasoline, weapons and munitions, and money will be very hard to come by. A smart man will stockpile. Warning. The government has defined that persons who stockpile are to be considered terror suspects, even Mormons. Weapons, especially, are a problem, as is being a member of NRA or talking about the Right to Bear Arms in public. Rural Texans, should especially beware, since they own more guns on average per family than some Swat Teams.
*note: while this is not specifically on FBI’s list, it is clear in the wake of the Aurora shooting that government is watching who buys weapons, and suspicious of anyone who collects. The WACO standoff and massacre was staged for just such cause; the ‘illegal’ weapons BATF claimed on their warrant included descriptions made up to include things which no one could possibly own because there was no such thing ever in existence.
4) Educate yourself. You must be alert to news around you from as many resources as possible. When the Sh** hits the fan, it won’t be NBC or your newspaper that gives advance warning, it will be something on the Internet or an email from someone on the front lines. Establish as many contacts in as broad an informational network as possible, especially to include Activists, who will be the first to feel the Iron Fist when it comes. Warning: The government has determined that persons who make any form of contact, subscription, or affiliation with such politically incorrect sources (like me), even when seemingly accidental, are to be considered terror suspects. Oops… too late for you, now!
•note: this is not exaggerated. As far back as COINTEL and COINTELPRO days under Nixon, government was tracking such matters, and Hoover’s FBI before that. In point of fact, illegal political spying was launched against people (including me — details of surveillance tails of my activities by up to five operatives at a time) who subscribed to select newspapers (i.e., the now defunct Washington D.C.Spotlight — the only newspaper in America to never be proven wrong in a story, and to which I subscribed), and such information was being freely traded between CIA, local Police, and the Anti Defamation League/B’nai B’rith/Mossad — and sold to anyone for a price.
5) Avoid credit, use cash. Credit creates obligations which in a time of disaster and an inability to work or access bank accounts could mean foreclosures and other negative financial harm before remedy could be managed. Warning: The government has determined that persons who pay with cash are to be considered terror suspects.
6) Form group defenses. Find others, be they family members, friends, or simply like-minded individuals to form mutual defensive relationships designed to cover each other’s back and increase the ability to withstand external threats. Warning: The government applies the principle of guilt by association and the notion that whenever two or more citizens get together a conspiracy is afoot, and must presume them a terror suspect.
*note: This exaggerated point is based on the fact that everyone on Facebook and other social media is being spied upon by a paranoid government to see who else they are in contact with, and what they are saying/doing.
7) Have a plan of escape. Consider getting out of the country to Canada or some other nation, or escaping into the countryside as a survivalist might do, or at the very least relocating to another community or staying on the road at length. A moving target is harder to hit. Warning: The government has determined that persons who travel extensively*, and especially survivalists, may be terrorists and should thus be put on watch lists.
*note: the couple arrested were told one reason they were being interrorgated (deliberate spelling) was because they were traveling so much. Another was, they were asking too many questions about why they were being questioned! But their actual arrest was ‘for threatening an agent’ by ASKING “Am I in danger, here?”
8) Document everything. There are many reasons you should photograph almost everything, and keep good records. Insurance claims you may need to file, for instance, and proofs of ownership. On the assumption terrorism might destroy public buildings and key infrastructure, it might be good for posterity’s sake, and art’s sake, to photograph key locations to ensure future generations will be able to remember. Wish I had that picture I took of the World Trade Center some years back. Warning: FBI has told police to target anyone taking pictures of public places as potential terrorists.
9) Educate your children. If our way of life is threatened, it will be more important than ever to insure our children will know what it means to be an American so they can carry on. Help them with homework to insure they understand the political processes and political choices, and are able to grasp concepts like Free Speech and the differences between Republicans, Democrats, and Ron Paul. Warning: FBI has visited and questioned school children who’s’ school report mentioned freedom of speech and Ron Paul, and subjected them to psychological profile questions to see if they or their parents were terrorists.
10) Buy Gold and Silver. If the money collapses because of massive bank closures under Martial Law or terrorism which kills the banking system, you will need a safe investment alternative. Warning: FBI has indicated people who buy precious metals should be considered terror suspects.
In summary, you would be far safer, rather than attempting the above defensive steps, to actually join Al Qaeda in the first place. The number of terrorists killed or arrested by government is, after all, practically non existent compared to the number of Policemen killed by criminals. Of course, that could change under NDAA, which makes murder of US Citizens legal if you are named Obama bin Laden. So at the same time, join the ACLU, as well as the patriotic Republican AND Democratic parties, and consider those memberships as insurance policies. The former to watch out for you if arrested, and the later to provide a kind of insulation against it regardless of which party is in control of the nation: they won’t want ‘one of their own’ to make the news as a terrorist, now, will they?
No. That’s when assassination is the better option. But don’t worry too much about that. Just watch the Matrix repeatedly until you can master all their defensive moves, especially the ones dodging bullets.
Sorry, but if I hadn’t misplaced my Al Qaeda membership application, I’d post it here for your convenience. That’s OK, I’m sure the CIA, who created the infamous group with the help of the U.S. Army, can provide you with a copy on request.
Related articles
- Al-Qaeda a tool for West’s political/military adventures (alethonews.wordpress.com)
- Will insurance cover you if terrorists strike? (insurance.com)
- DHS Characterizes Patriotic Americans as Terrorists (moonbattery.com)
- Osama bin Laden and the 911 Illusion – Part I of 3 (vaticproject.blogspot.com)
- Bin Laden realized the truth: Terrorism just doesn’t work (juneauempire.com)
How FED Conspirator Bank Robs the Poor, and Their Dead
Bank of America Insults my Patriotism by Their Very Name
So does the Federal Reserve
by H. Michael Sweeney
I had just finished posting a blog about the fraudulent means and deceit employed by the founders of the Federal Reserve Banking System which has raked in trillions of dollars of profits at taxpayer expense since founded in 1910… when the very first reader of the post wrote something which set me aback. This is not just because of the injustice visible on the surface, but because the bank involved is a co conspirator with the FED to profit even further at taxpayer expense. That would be, as you by now rightly assume, the Bank of America.
So… after screwing the Federal Government and every single citizen for a $25 billion share of the TARP bailout… and after that bailout money additionally profited them ten times the amount of the bailout (they can loan ten times their cash reserves)… and after they will earn obscene usury (meaning excessive, in that they have no money actually at risk in the loans as they are made out of thin air) interest on all those loans for decades to come… and yet are further conspiring with the FED to dump even more faulty (read bogus) derivatives from Bank liability sheets (and guess who will pay for that in a ‘round two TARP bailout‘?), they still want to steal $500 from a dead woman and her heirs?
If none of the above makes any sense, please see the earlier post, The Federal Reserve, an Appearance of the Fourth Kind, and this story (The Federal Reserve and Bank of America Initiate a Coup to Dump Billions of Dollars of Losses on the American Taxpayer). I think you will then find the following story doubly abhorrent:
This is a true accounting of an actual incident I’ve verified underway in Oregon with Bank of America, but it is presumed all large banks have similar policies and procedures in place. I am open to correction by anyone who knows otherwise regarding any specific bank. What follows is a description of various devious methods applied to siphon off extra money from the accounts of deceased persons when the survivors are of ultra-low income. Actually, the matter would also seem to include an almost conspiratorial partnership with County agencies, at least in this case, so this article could have been entitled, How Banks and Counties Conspire to Rob the Dead and the Poor.
To explain the rip off, we need first to have a basic grasp of how it things should transpire according to law. But to be clear, there is no violation of law yet visible, though violation of fiduciary responsibilities, user agreements, and moral ethics is still an issue. While laws vary in detail from State to State, the following simplified description is generally accurate.
When someone dies, there is either a Will which establishes an Executor of the Estate, or there is not. When there is not, the matter goes into Probate Court and the State determines the final resolution of the Estate. Where there is an Executor, that person is charged with closing all accounts of the deceased, liquidating any property not a specified gift in the Will, distribution of such inheritances, and paying of remaining debts. There will almost always be some funds involved, either from actual cash or bank deposits, or the sale of personal goods or property.
An Executor, often a family member who is also an heir, will be entitled to reasonable compensation for their services which comes from such funds. Such fees are commonly well over $1,000, plus expenses. This and any taxes owed are the only charges against such funds which have ultimate priority for ‘first-payee’ status. Next come creditors, who must be paid in full or, where there are insufficient funds, be paid a pro rated share according to the size of the individual debts involved. Any remaining funds become inheritance, and may be subject to income taxes after the fact.
In a large estate, which in most legal definitions involves Real Property (real estate) or other assets worth more than some specified sum (the lowest I’ve seen is $250,000, but the sum for the State of Oregon I’m told is $2.5M), there are some fairly stringent procedures involving the Court which must be followed. But this does not apply to the poor, does it?
Think of the millions of elderly in nursing homes, for instance. They tend to own no property of consequence, and upon their death, most personal possessions consist of brick-a-brack, polyester clothes from the 60s, a TV, and some personal things such as photos and keepsakes. They tend to have some money resources, but often quite minimal in nature. Often, the Executor named and heirs are also poor, or they might have had a nicer place to live out their last days. Such is the case in the Oregon example:
We are talking about a woman named Wordy Mae, last name omitted for cause. She was 87, legally blind, had Diabetes and several other troublesome ailments, and an income of $1,100 a month, of which all but $150 went to pay for her nursing home. Medicine and personal care came out of the $150. Hers was a good Southern name, one especially common to Blacks and poor rural whites a few generations ago. She died with debts of several thousand but only about $500 in her checking account. Her personal things, other than keepsakes, had no resale value and all went to Goodwill.
Check out her artwork, right, one of her unique keepsakes. Though blind, she would spend countless hours hunched over with a heavy illuminated high-power magnifier and see the color sparkles well enough to glue bits of junk jewelry and plastic into artistic patterns.
So, the big question: did her family or the Executor get anything at all? No. The Bank of America is usurping it with clever ploys.
Wordy’s Son was her named Executor. He has three school-age daughters, also named heirs, but it looks like they will not see a penny, not even to recoup expenses as provided by law. This is unfortunate, because he is unemployable due to a disability for which he has no income allowance (why it should take more than eight years to get official disability is yet another rip-off article which should perhaps be written). He lives on about $1,000 a month Social Security from forced early retirement — which in and of itself cost nearly $400 a month in lost income from his full entitlement.
So we are talking about a family that has to choose between food or gasoline perhaps twice a month, and as result frequently has a diet of hot dogs for lunch and dinner, or Raman noodles every day, often skipping a meal altogether. It took nearly six weeks to come by enough money to buy an ink cartridge so he could write (futile) letters seeking resolution. This is also a family, by the way, which had lost their home in the Mortgage crunch during our recent financial debacle which resulted in the banks being paid billions of dollars in the first place. So they are doubly upset with Bank of America, which played a role in that fiasco, as well.
Here is exactly how Bank of America has managed to steal from them further:
Step one: the Bank somehow knew immediately about the death. Well before Wordy’s Son could notify them, the Bank notified him that the account had been closed ‘for protection of the funds.’ One wonders how the bank was notified so quickly, by whom, and how they knew which bank to notify. I’m working on a possible future blog, Banks Own Your Social Security Number and NAME, for one possible answer.
Step two: the Bank sent him a form to be filled out by the Executor. The seeming purpose of the form was to let the bank know how the Estate would be handled. Reasonable… but it redirects correspondence to a centralized and dedicated department of the Bank out of State. No one local to deal with, providing a mechanism for delays which prove valuable to the Bank, as we shall see.
Step three: delay and silence. Bank statements stop being issued, which seems to make sense, given the account was closed. There is no reply from the special department… though non was particularly expected, except that when the form was mailed, the Executor also sent a copy of the Death Certificate and a final accounting of the Estate, with request of release of the funds to cover Executor fees and his expenses in closing the Estate, which were not inconsequential and which had been difficult to manage without personal hardships. There were not even sufficient funds in the closed account to cover this, so all of Wordy’s funds should have gone to him, calling it inheritance or fees as you please. There were zero taxes due.
Step four: two months later, the special department then sent a letter stating that it was prepared to release the funds but was requiring an original copy, not a certified copy, of a County Court document before they could so proceed. Curiously, they did not specify the nature or name of the document requested. Because they did not, and the Oregon Revised Statutes made no reference to any legal requirement for any such document, the Executor contacted the County in an attempt to learn what was required and how to go about it.
Step five: The County did not respond. Repeated inquiries went unanswered for weeks. Eventually, it was discovered that there was a simple form, not much different than already provided the bank in purpose and content. There was associated with it an outrageous filing fee of $112.00 as well as other fees. This was to cover the cost of… well, ‘filing it’ in a filing cabinet. It was not possible to obtain the original, but only to obtain a certified copy. WTF?
Step six: about this same time, the Bank resumed mailing monthly statements. SURPRISE! The ‘no-fee’ checking account which had been closed was now enjoying a $12 a month service charge for… NOTHING. Perhaps the Bank has a filing cabinet to pay for, too?
Step seven: because the Executor could not possibly afford the filing fees, much less obtain an original copy at any price, it seems the Bank will therefore never have a legal obligation (we would presume that their ultimate argument) to release the funds, and will slowly absorb them until they are absorbed entirely through arbitrary monthly fees — which we might presume will be used to fatten Bank Executive Bonus Checks.
It is stories like this, including some personal experiences, which caused me to close my accounts with Wells Fargo and Bank of America when the 99% suggested it was one way to confront the System. I’d go further if I had the bravado and skills… and become a modern-day Robin Hood — and I thought for a moment I could avoid getting caught (I’d not be very good with a bow and arrow against the FBI). But that’s just my anger talking.

Image from reportyourcomplaint.com, where other BOA customers have their own issues to talk about (click)
If if moves you to sufficient anger to close your account, tell them Wordy Mae sent you. If you feel compelled to send a buck or two to Wordy’s heirs, send it by PayPal to wordymaeheirs at century link net, an addy I’ve established for the purpose.
I’ll match every dollar contributed from my book sales profits for this year. I’m thinking it might change their diet for a while. And if enough people did that, it would make news, and that would further embarrass the System toward useful redress for all who might be in similar difficulties with Banks and local County governments, which are really for-profit corporations in their own right (look yours up in Dunn and Bradstreet if you don’t believe me).
I also suggest you tweet/repost/email this post far and wide. I am lifting all copyrights upon it if reproduced in full unedited, links in tact, but would appreciate an adviso of any such reproduction in the form of a comment to this post. Appreciate you!
Related articles
- The Federal Reserve: an Appearance of the Fourth Kind (proparanoid.wordpress.com)
- Estate planning: Taking care of your executor (business.financialpost.com)
- Bank of America’s $40 Billion Mistake – WSJ.com (raptureimminent.wordpress.com)
- The Many Ways Banks Commit Criminal Fraud (americankabuki.blogspot.com)
- Bank of America: Too Crooked To Fail (drx.typepad.com)
- Bank of America slapped with $300k sanction (setexasrecord.com)
The Federal Reserve, an Appearance of the Fourth Kind
The best scrutiny of the Federal Reserve, yet
by H. Michael Sweeney, a commentary on remarks and book by G. Edward Griffen
I just watched a video of a presentation by G. Edward Griffen, an author and film maker of the investigative kind , his topic being the creation of Federal Reserve. I’ve been looking at the Federal Reserve Banking System for almost a decade in realization it was a banking industry scam: it is neither Federal (it is a privately held corporation), it has no reserves (it makes money out of thin air), is not a Bank (it is a board of governors who dictate bank policy), nor a System (despite having buildings and employees across the country, all of its functions are centrally controlled, and all of its assets centrally held). Thus what it is, is a pure deception most heinous, even in its name.
 But his video opened my eyes wider and provided more revelation than any other Web or book resource to date. I had not heard of or read his own book, of course, The Creature from Jekyll Island, which is the story of the secret efforts of creation of the Federal Reserve in 1910. I urge you to watch this lengthy video, which he opens with a clever and apt quote from a circa 60AD philosopher on the nature of the appearance of things, and it is from this whence comes my choice of title for this post:
But his video opened my eyes wider and provided more revelation than any other Web or book resource to date. I had not heard of or read his own book, of course, The Creature from Jekyll Island, which is the story of the secret efforts of creation of the Federal Reserve in 1910. I urge you to watch this lengthy video, which he opens with a clever and apt quote from a circa 60AD philosopher on the nature of the appearance of things, and it is from this whence comes my choice of title for this post:
Appearances to the mind are of four kinds. Things either are what they appear to be; or they neither are, nor appear to be; or they are, and do not appear to be; or they are not, and yet appear to be. Rightly to aim in all these cases is the wise man’s task.
— Epictetus (c. 60 AD), Discourses, Book i, Chap. xxvii
If you do watch this video, you will see Griffin eloquently illustrate that the Federal Reserve is perhaps all of these in various ways, but above all else and foremost, is an Appearance of the Fourth Kind: it is not, and yet appears to be. You will, thereby, learn some things not commonly known or spoken of elsewhere regarding its evil:
You will learn that there are seven key problems with the Federal Reserve which describe its function or lack of function… as I summarize here, along with some additional information Mr. Griffin did not reveal but which I have acquired in my own research, or drawn from Griffin’s totality of statements — with or without his own direct inference. Such information will be in italics. That may mean simply combining disparate elements of his presentation as if unified, or adding something new or left unsaid, but implied.
1) It is incapable of meeting its stated objectives (but has met all of its secret objectives set by those who designed it — the seven international bankers who already controlled one-fourth of the World’s money).
2) It is a secret cartel operating against public interest in the guise of operating for the public interest (and operating under the guise of government control with the purpose of controlling governments).
3) It is a supreme instrument of usury (the making of obscene profits in the form of perpetual interest on debt created out of nothing).
4) It is the root cause of our most unfair tax (and other taxes such as required to fund bailouts and loans to the International Monetary Fund, foreign nations, and corporations. The same ‘tax’ concept is true of the national debt which it ever increases, over half of all actual tax revenues going to the banks to pay this interest to the banks).
5) It is a tool and key sponsor of and participant in Totalitarianism, Fascism, Dictatorships, endless wars, and Globalism and the New World Order. As such, it seeks to undermine and destroy the national sovereignty of the United States in preparation for a one-world government… owned or controlled by the banks.
6) It was a tool designed to give New York Banks (ONLY) a means to control and limit the power and growth of any and all banks outside of New York, which was exactly the opposite of intent when Congress moved to create the Fed, thinking instead they were limiting the growth of power of the New York Banks which was already considered too great and a threat to the nation.
You will further learn how much secrecy and fraud, and downright skullduggery was involved in the creation and perpetuation of the Fed, and who was involved. There were seven Men, all extremely powerful banking moguls who had, until this point, been competitors duking it out for supremacy. Formation of the Fed was to be the ultimate monopolistic cartel, one contrary to every precept of American fair play, free enterprise, and legal prohibition on topic. I name additional conspirators.
1) Senator and Republican Whip, Chairman of the National Monetary Commission (to reform banking), Nelson Aldrich. He was the Father-in-law of Nelson Rockefeller and thus quite tied to the Banking Industry he was supposed to help regulate. He is the one who called together the six other men it extreme secrecy. You won’t believe how much trouble they went to maintain that secrecy, and why it was necessary.
2) Abraham Fiat Andrew, then Secretary of Treasury, and friend to the others.
3) Frank Vanderlift, President of the National City Bank of New York, a bank so large it held assets for both Rockefeller and Loeb investments.
4) Henry Davidson, Senior Partner for J.P. Morgan, one of the largest of the N.Y. Banks, better known as Chase Manhattan, today.
5) Charles Norton, President of the 1st National Bank of New York, another huge bank of the day, the original ‘Chase’ Bank, but now Citibank. We thus in Chase Manhattan now have two of the conspirators.
6) Benjamin Strong of J.P. Morgan Banker’s Trust, who would become the first head of the Federal Reserve.
7) And the granddaddy thought to be the true architect, Paul Warburg, Partner in the Loeb Banking concerns, the Rothchild Bank, and Brother to Max Warburg who ran sister banks in Germany and elsewhere. This is why you often hear that (incorrectly) the Fed is owned by foreign banks. The belief is only true to the extent of influence involved, but not actual ownership. It is also true that the FED can now loan money to any other international bank at American taxpayer expense.
8) A de facto partner of sorts, would be Nelson Rockefeller, who in addition to the banking ties already mentioned, owned the railroad which provided the train to pull the private railroad car used by Nelson Aldrich to convene and transport the Cabal from New York to their final meeting place at Jekyll Island in Brunswick, GA. Certainly, his Banks became partner (owned shares) in the Fed once created, and profited thereby.
9) Other possible de facto partners could arguably be the Brown Brothers Bank and Harriman Brothers Bank, who would soon merge to form Brown and Harriman, and later evolve to include Harriman and Bush Banks (yes, that Bush family, starting with Prescott Bush, then George Bush, and the younger George). Harriman owned the company that made the rail car pulled by the train. It is interesting to note that fully half of the senior partners of Brown and Harriman were members (8 in all) of Skull and Bones, including Prescott Bush, and later, his Son and Grandson, future Presidents all. Harriman and Bush would later be convicted of conspiring to aid the Nazi war effort during WWII under the Trading With the Enemy Act. But that’s OK, so was AT&T.
All these banks also participated in the Fed.
You will additionally learn just how these 7 men, on behalf of at least as many New York banks, conspired to trick Congress and the People into thinking creation of the Fed was the opposite of what it really was, and how they profited thereby (both the Government and the Fed member banks):
1) Government got access to unlimited money supply on demand, and had the ability to impose effective taxes without publicly levying tax and risking voter ire. Inflation caused by printing money out of thin air (fiat currency) is nothing more than a tax in that it funds government spending and takes money out of the pocket of citizens in the form of reduced spending power in order to fund government.
2) The banks got to capture and grow the lending market as a monopoly, and control interest rates to their advantage, which even when extremely low and next to nothing, would still reap huge profits because instead of having to lend based on money of their own being put at risk, they were able to charge interest on money created out of nothing at zero risk.
3) The banks got to have access to collateral they could repossess when a borrower failed to repay as agreed, which was far more valuable than the interest. Thus bad loans were to their advantage, instead of being a true risk.
4) The banks were assured they would be bailed out by government if they ever got into trouble, and better still, would be able to profit whenever government bailed out anyone, made loans to other nations, etc.
5) The banks acquired access to an unlimited and ever growing (exponential) supply of wealth (profits with no overhead or seed money on their part) which are being use to buy power in all high places World-wide. They are both the fulcrum and the lever for the 1%, the Bilderbergers, the New World Order, all.

Mr. G. Edward Griffin
Mr. Griffin is an excellent speaker with good charisma and I highly recommend this video. Upon watching, at the end, some viewers might suddenly get a bad taste in their mouth, however, as it turns out the speech is given before a group meeting of the John Birch Society, and some of the comments are encouragements of their efforts.
Please do not let the disinformation and rhetoric which exists for the purpose of discrediting the JBS as some kind of evil right-wing extremist group dissuade you from the valuable truths and facts revealed by Mr. Griffin. If for some reason you view the JBS as ‘bad,’ I suggest you review any of their own material and compare it to the bad things said about them, and you will see disinformation at work. I’ve yet to find anything JBS has done or said which fits the negative commentaries. I have yet to find bad things said which did not turn out to be disinformation or mere political rhetoric in support of contrary views (e.g. politicians guilty of eroding the Constitution attempting justification through vilification of their critics — the JBS).
That said, I’ve also yet to make up my own mind if they are 100% aligned with my own beliefs, but when it comes to the FED, we certainly can agree: End the Fed. That brings us to yet one more key point made by Griffin: It does no good whatsoever to attack the Fed or expose its evil. In point of fact, they themselves fund groups who do just that, that they may control their direction and insure they do not do the one thing which really matters, which is TO PROPOSE A WORKABLE ALTERNATIVE. Griffen shows how futile the more commonly proposed alternatives would be, such as an audit proposed by Ron Paul.
With that said, I would further point out that my own proposed alternative may interest you, as found at my blog post on 24 Campaign Planks: H. Michael Sweeney for President. Just how to end the Fed is quite well addressed there (while several planks are part of the total answer, start with plank 3). Hope you like it.
Related articles
- How FED Co Conspirator Bank Robs the Poor and Their Dead (proparanoid.wordpress.com)
- 24 Campaign Planks: H. Michael Sweeney for President (proparanoid.wordpress.com)
- CLASS ACTION LAWSUIT AGAINST THE FEDERAL RESERVE BANK, 4/26/ 2011 – (and duly ignored) – thanks to P. (jhaines6.wordpress.com)
- Federal Reserve Directors’ Banks and Businesses Took $4 Trillion in Bailouts: Report (commondreams.org)
- Ron Paul’s Federal Reserve Audit Approved by House Committee (sgtreport.com)
A Glimpse of Fatal Rebirth (from the Preface)
Fatal Rebirth,
a four-book set by H. Michael Sweeney
Copyright © 1996 All righs reserved.
From The Preface
 Truth cannot live on a diet of secrets, withering within entangled lies. Freedom cannot live on a diet of lies, surrendering to the veil of oppression. The human spirit cannot live on a diet of oppression, becoming subservient in the end to the will of evil. God, as truth incarnate, will not long let stand a World devoted to such evil. Therefore, let us have the truth and freedom our spirits require, or let us die seeking these things, for without them, we shall surely and justly perish in an evil world.
Truth cannot live on a diet of secrets, withering within entangled lies. Freedom cannot live on a diet of lies, surrendering to the veil of oppression. The human spirit cannot live on a diet of oppression, becoming subservient in the end to the will of evil. God, as truth incarnate, will not long let stand a World devoted to such evil. Therefore, let us have the truth and freedom our spirits require, or let us die seeking these things, for without them, we shall surely and justly perish in an evil world.
Now we have a dark, difficult to see Shadow across the land. It is a secret Shadow, one built upon and operated by lies disguised as truth, dedicated to the works of tyranny and oppression in the guise of freedom’s cause, and driven by the darkest of evil wearing the mask of good intent. This Shadow lusts for and worships power, and applies it with great and frequent abuse to acquire even greater power. It wants the ultimate power to control the World, to decide who lives and who dies, and to directly or indirectly own and control all things. Many do not yet see it, and sadly, will not, until it is too late. Untold millions more will die never knowing why. Who or what is Shadow? Read and learn, learn and decide.
This author was once an ordinary man eking out an ordinary existence. This was my happy state and my presumed ongoing fate — until I came into possession of an innocuous and incredulous document. It was unbelievable: a tremendously conspiratorial document detailing many sins of the empowered elite and their minions within government — especially within the intelligence community. Preposterous as it seemed on the surface, something within that document must have been true, for merely mentioning its existence transformed my ordinary life into an extraordinary 007 nightmare.
They spent perhaps $250,000 a month in surveilling me and manipulating my life in devious ways. What about that document, unless it be the conspiracies detailed therein, so frightened them that they took such measures against me? Indeed, what was the purpose of the document — why was it ever written? More key, as the document itself attests, who were the people behind the conspiracies, and what dark motive drove their actions? Who are they that should so fear mere words on paper? They are Shadow. This book is their story. It is my story. It is the story of other Americans also caught in Shadow’s web. It is your story — a story of your historical past revealed to be lies, and of a dark future, if you do not take care.
 This book is an attempt at revealing the true nature of a Shadow manipulated past, the true Shadow fostered dangers of our present time, and the all-too possible future Shadow plans for us all. It must be said up front that this author began this work completely unawares of the social and political realities perceived by any of the many organizations that exist on the political fringes to the left and right of the staid Republican and Democratic parties. As an overly naive and easily pacified American, there was no understanding of what CFR or NSA was, what a constituted a leftist or extreme right point of view, a Populist or Elitist, nor of little in between. Huntly-Brinkly were my sole political enlightenment, and the balm and ointment of my few political fears and concerns. I was mere fodder for the engines of media manipulation: Hear Ye, Hear Ye, believe and obey. I believed. I obeyed. But then came proof of Shadow.
This book is an attempt at revealing the true nature of a Shadow manipulated past, the true Shadow fostered dangers of our present time, and the all-too possible future Shadow plans for us all. It must be said up front that this author began this work completely unawares of the social and political realities perceived by any of the many organizations that exist on the political fringes to the left and right of the staid Republican and Democratic parties. As an overly naive and easily pacified American, there was no understanding of what CFR or NSA was, what a constituted a leftist or extreme right point of view, a Populist or Elitist, nor of little in between. Huntly-Brinkly were my sole political enlightenment, and the balm and ointment of my few political fears and concerns. I was mere fodder for the engines of media manipulation: Hear Ye, Hear Ye, believe and obey. I believed. I obeyed. But then came proof of Shadow.
Shadow is a secret society with its own secret government. Shadow is a secret business community with its own secret monetary system. Shadow is a secret intelligence community with its own secret police. Shadow has a secret agenda achieved with secret resources. At Shadow’s darkest, innermost place lies a black, satanic religion whose secret roots are the very essence evil — so dark as to have origin beyond mere mortal man. Shadow’s branches are everywhere, and its greatest branch may ultimately prove to be the anti-Christ.
With combined resources of unimaginable wealth, influence, and power, there is likely no high place Shadow does not control or sway in some way or to some degree. Shadow’s greatest tool and protector lies in secret works and an invisibility to detection, thus making it impervious to would-be enemies. We would be Shadow’s natural enemy, would we recognize it for what it is. As we do not, we remain its prized and willing victims. We are no more wary than a gnat buzzing about a spider’s ever growing web. Save some awakening of our dull wit and even duller senses, it’s only a matter of time…
Legend tells us that thousands of years ago, Diogenes searched a lifetime with his lantern held high in a futile search for just one honest man. The centuries do not seem to have changed the odds in his favor. But in our modern times and societal infrastructures, should there not be some source of truth and honesty? Is there no place where we can seek the essence of righteousness? If not, then as the opening suggests, we are doomed to evolve or collapse into a kind of world-wide tyranny wrought by those that thrive in lies and secrets. Indeed, everything points to that eventuality becoming reality. The military-industrial-intelligence-media complex, in an unholy alliance with what many term the super-elite of the one-world crowd, steadily remakes us into a fascist-like corporate-manipulated state. Sweeping statements, yes.
Such sweeping statements need explanation if we are to understand the nature and identity of Shadow. To start with, many people today do not understand what a fascist is — thinking it some irrelevant term from a bygone past. They should look up the word, especially if from among the poor or minorities, for they already are suffering under the first signs of its growing yoke. Fascism holds a special, unkind place for them under its unbridled reign. Indeed, perhaps for us all. Failure to understand and accept the existence of Shadow and their dark crimes may very well mean a kind of death through slavery to a dark will – the difference between all good things which the reader desires and believes in and the loss of all hope that they might come to pass. Fascism favors the moneyed elite, and Shadow’s head is formed largely from among the leadership of the megacorporate giants. The reader cannot turn away from these notions unless and until satisfied beyond all Shadow of doubt that they are untrue.
Want to know more? Read Fatal Rebirth!
Related articles
- The 33 Axioms of Fascism, a Primer (proparanoid.wordpress.com)
- The New Faces of Fascism (theconservativemind.net)
- Shadow Executive Orders (rockelement.typepad.com)
- Media Beast To America: Bow Down To Military Police, Your New Lord And Savior (disquietreservations.blogspot.com)
- Guest Post: Americans Are Being Prepared For Full Spectrum Tyranny (zerohedge.com)
What Does It Take to Start A Revolution?
What Does It Take to Start A Revolution?
(Are we in danger of having one?)

From The Pennsylvania gazette, 9 May 1754. Abbreviations used: South Carolina, North Carolina, Virginia, Maryland, Pennsylvania, New Jersey, New York, and New England. This is a somewhat odd division: New England was four colonies, and Delaware and Georgia are missing (Photo credit: Wikipedia)
by H. Michael Sweeney
This and future blog posts on the theme of revolution (martial law, etc.) are herein intended to serve as building-block guideposts to both citizens and anyone in government who will listen to reason. Citizens so they become more aware of their rights, obligations, and options under the law as citizens. Government so that they might realize their errant ways are leading us all toward that day when the Camel’s back is broken by a straw event of their own making, and revolution breaks out as the people’s only remaining recourse. I do not believe they realize how dangerous their criminal actions have been in this respect. While I do not call for revolution, and merely warn it nears, were it to happen tomorrow I would be forced to join in it.
I fear such a day looms near, and that it may even now already be to late to prevent it. If true, it is your fault, reader, for allowing things to progress that far. Worse than revolution by the oppressed and disenfranchised, there is also the possibility that an armed revolution will be required to restore the government from a military takeover, which is addressed in part two and three of this triune post. Don’t you dare think for a moment it is not a possibility (read on).
In fact, I so fear the possibility might be true that I’m lifting the copyright on my book set Fatal RebirthSoon (stipulated limitation: purchased ebook versions may be duplicated and delivered to relatives and personal friends or coworkers, who must purchase if wishing to do the same), which contains considerable detail on these topics and specifically offers advice about what to do if it actually does come to pass. The goal is to reduce violence, save lives, and yet assure any battle for restoration of a Constitutional government is successful. Details at the end of each blog post.
This first post consists of several parts:
- The Right and Duty of Revolution;
- A Closer Look at Revolutionary Processes;
- About Redress of Grievances;
- The Start and Aftermath Revolution (a review of several actual revolutions);
The Right and Duty of Revolution

English: Painting, 1856, by Junius Brutus Stearns, Washington at Constitutional Convention of 1787, signing of U.S. Constitution. (Photo credit: Wikipedia)
First of all, regardless of the nation-state involved, when no other recourse remains, it is one’s right and duty to self, family, and to fellow citizens and the nation to revolt against tyranny in its various forms. It is one’s right by virtue of self defense, always. But here in America, it is also our right by law, according to the Constitution. In a true working democracy, the right to armed revolution does not (should not, according to scholars) exist as such, replaced instead by the opportunity to vote in a new government, a kind of redress which is its own kind of revolution when sweeping house occurs (like that ever actually happens). However, if that democracy is thwarted by systemic manipulation such that said opportunity is wired against the people, the right and duty yet again surfaces for armed revolt.
Only so long as the democracy does not violate its charter for power (in America, the Constitution and Bill of Rights), writes just laws in accordance with the charter (laws are Constitutional), and obeys the laws itself, is it safe from armed revolt. Unfortunately, the United States has embarked on a steady course of rapid-fire issuance of unjust, oppressive, and unconstitutional laws in opposition to the charter, and has itself regularly disobeyed and abused its own laws and, and for the matter, International treaties on related matters (another discussion for another day, perhaps).
In any nation, this is rightly called tyranny, and nullifies all law in the end, though we must yet speak of redress as part of the equation. Sans such redress, the nation ceases to exist as defined by its charter, which is a legal contract between the people and the government which was hence broken by government’s wrongful acts. The just penalty is forfeiture of power, and when failing to yield and relying upon force of arms, will surely require armed rebellion to right the wrongs. It is that simple (unfortunately).
A given revolt may be of any flavor or level of intensity; civil disobedience or peaceful protest which causes the government to fail or resign, simply voting out the worst rascals and replacing them with hopefully better rascals; or when no other course works, and when matters are simply no longer tolerable, actual armed revolution. Revolution, for governments, is the bullet in the gun they continually wave about called power, the gun used in a de facto game of Russian Roulette they play every time they misuse their power. Eventually, if the game continues long enough, they shoot themselves in the head and earn their just reward. Our government has been pulling that trigger time and time again since before the September 11 attacks, and more so, since. Again, that is your fault, not theirs. You allowed it by your silence. They may be criminal, but you were negligent.
The firing of a bullet when they squeeze the trigger depends on lines in the sand drawn by those among the citizenry who are the angriest. Sometimes a citizen does not realize such a line exists (they do not premeditate it) until it is crossed, and sometimes a citizen will fear the event in advance and draw the line in bitter anticipation. When government crosses that line, whatever it may be, that citizen begins to work in earnest toward revolt. When sufficient numbers… remarkably few in count as we shall see, are so moved, a revolt can be easily triggered. Unbelievably easy, in fact. Defining appropriate lines in the sand is covered in a companion post.
Depending on what line one might choose, armed revolution in America may actually be overdue, in which case this warning is all but too late. Again understand: I do not hereby call for revolution, but shout warnings that it may soon be forced upon us by government actions and inactions. They have been playing roulette for some time, now, and many lines in the sand have already been crossed as judged by countless people I’ve talked with at public gatherings. Any day the final pull of the trigger could transpire, and yet those in government seem Hell bent to spin the chamber yet again and again, the most recent on March 1 when every Senator and Congressman except Ron Paul voted to pass the Federal Restricted Buildings and Grounds Improvement Act, which essentially ends the right to protest or freely assemble at any location near anything having to do with government, including elections, as government deems useful to retain total control; another stab through the heart of the Constitution and Bill of Rights.
A Closer Look at Revolutionary Processes
Most revolutions would seem to stem from economic and social inequities brought on by an uncaring or overbearing government which favors a power elite over the needs and rights of its people. In more recent history, such practice was given a name, and that name is Fascism. Surely, even Sheeple can be made to see that paradigm is at work in the United States, today, as perhaps best made clear by the variety and nature of complaints fielded by the Occupy movement, which very nearly was the catalyst for a revolution according to some viewpoints. Certainly many wished it had sparked one or feared it might. The ‘R’ word was definitely being tossed about in commentaries far and wide.
What most people do not realize is that revolution is actually a very simple thing to engineer (though spontaneous combustion is more often the mechanism involved) — when the situation is ripe for it. When tyranny, oppression, or general grievances with government are strong enough, almost anything can spark a revolution, and it does not actually take a lot of people to get a roaring fire started. In the snapshots below, we see that an incredibly small number of people can, by the right actions and in right circumstances, sponsor, though not necessarily their intent, full-scale revolutionary responses in the general population. They need not even be carrying guns to do so, which is why the 99% were considered worthy of the ‘R’ word.
The notion of governmental suicide via Russian Roulette should be restated and underscored, for governments truly dig their own graves at their own risk. In like analogy, governments in power tend to make their own noose with respect to the outcome of a revolution, building their own platform, and then to jumping off the platform on cue to insure the success of the revolution. The platform could invariably be described as their construct of oppressive laws and abuse of power, the noose as their own unwillingness to operate within their own laws and policy, all generally to the profit of a power elite at the expense of the common citizen. They then, like a mindless Lemming, jump off the platform by coming down hard and heavy on any early revolutionary event (generally, a peaceful event where government response is violent), creating martyrs for the cause. We see this in almost every case, as the central-most thing which galvanizes support of the masses for the revolutionary cause. Spontaneous combustion results, and government’s neck gets snapped with a sudden jolt.
That is one reason the Occupy Movement failed to spark a full-scale revolution; the level of violence by government was rather minimal (say, in comparison to the kind of over-the-top response seen in the smaller-scale WTO protests such as in Seattle and in Europe). That the Federal government did not take action and no State Governor took actions involving National Guard or Martial Law were restraints which also helped keep things from boiling over.
One can also make the argument that a controlled media and other trickeries served to help keep public opinion from galvanizing sympathetic support under the unfortunate levels of violence which were present. However, their ‘polite’ and sneakier responses (including media manipulation and the FRGBI Act) was their own underhanded way of eliminating any future Occupy movement as well as WTO protests, etc., and that is why it was a bit more than just another pull of the trigger. I, for one, am hopping mad, and wondering how much the price of guns are going to go up with the increase in demand.
About Redress of Grievances
Yet another reason the Occupy movement did not ignite open revolt is that actual revolution was never its intent, though it is likely true that sub groups within the movement might have thought or hoped otherwise. Rather, the movement in general simply sought public exposure of a collective of grievances in hopes of sponsoring useful redress by government. In point of fact, redress of grievances is what activism, protest, and even revolution is all about. We should be well informed on this topic to understand what it means to be under a government, and especially so as an American, as redress is a key part of our very foundation as a democratic nation (in Republic form).
Redress of grievances, when ignored by government, is the sponsor of ALL revolutions. The United States Constitution and Bill of Rights specifically address redress as a major element of that covenant between the People and Government. Where any government fails to insure its obligations to satisfactorily resolve issues of redress remain fully functional and available to citizens, they make themselves liable to revolution as the only remaining alternative for the people. In the U.S., redress is, unfortunately, absolutely flat-out null and void; the Bill of Rights and Constitution have been all but formally discarded, and the systems in place for such redress have been neutered and rendered ineffective.
For example, the notion of challenging unconstitutional laws through the Courts is rendered impractical when it costs millions of dollars and takes toward a decade to see it through to finish… and Congress writes such laws ten times faster than they can be dealt with. Two such Bills in roughly four weeks time! That is not redress, it is premeditated manipulation of a weakness in the system. Whirr… Click! Whirrrrr,,,
When political heros are assassinated and groups of people are murdered en mass again and again by government acts and a cover up ensues, there is no redress. Whirr… Click!
When lip-service white-washing Warren Commission/9-11 Commission and bogus Congressional Investigations serve as cover up tools (e.g., sealing records, refusing/discounting testimoney/evidence, magic bullet explanations), there is no redress. Whirr… Click!
When whistleblowers are targeted instead of heeded, there is no redress. Whirr… Click!
When government rewards criminal bankers and others who rape the common man and sends the bill to the victims, and they steal more money from Social Security to help offset the sticker price, there is no redress. Whirr… Click!
When wars for oil and other profits are based on lies but no one even apologizes, there is no redress. One could go on, as nowhere do I see useful redress in evidence. All I hear is Whirr… Click! What do you hear? Certainly seems you do not hear your own voice shouting out a loud “Enough!” At least not yet. Whirrrr…
The Start and Aftermath of Revolution
So, how easy is it to spark a revolution? The answer will help measure how close we may be to having one. Lets take one good case example which is quite parallel in many ways to the situation in the United States, today, and then run some numbers for it and several other famous (major) revolutions for comparison. A revolution is actually easy to come by, if the right ducks are in a row, heaven please forbid such a need.
The French Revolution 1848…
France had a population of about 38 million at the time and was suffering a Monarchy quite uncaring of its people in favor of the wealthy. It was a kind of Fascism where nobility tended to be the most wealthy and most prominent of ‘corporate’ powers. High unemployment and underemployment rates of deep double digits forced the Middle and lower classes into poverty, in part fueled by a shift in focus by Industry to part time employment for those few able to keep their jobs. Sound familiar?
General economic crisis caused a surge in bankruptcies and small business failures at the hands of the larger corporations of the day. An unusually severe Winter brought on by a Greenlandic volcanic ash cloud which severely damaged crops that year was fueled by a shortage of coal and food brought on by the economic crisis. Almost the entire populace was in dire straights, unless wealthy or of noble birth. France wold fall almost overnight before the year’s end. Let them eat cake? What cake?
The government continued to be both unable and unwilling to address problems and instead fueled them with solutions which either failed to be useful or which were actually profit opportunities for the wealthy. The military was time and again pressed into service to police and stem protests (they jumped off their platform). Instead of quelling and calming the public, these responses fueled them and fostered a unison of anger.
In June of 1848 the French Revolution was essentially started by 577 citizens (commoners referred to as the Third Estate, which is, by the way, a designation system used by Royals: the Royals are the First Estate, whereby Barons and Lords are the Second Estate, citizens the Third Estate, and from which media has since often been called the Fourth Estate), who in outrage over being denied their legal appearance at court for redress, met in conference (known as The Tennis Court Oath) to protest. This was their 99% moment, and they agreed (577 out of 578) in an Oath which established themselves as a governmental authority (The National Assembly) seeking Constitutional reforms which eventually would lead to the drafting of the Declaration of the Rights of Man, a document quite similar in character to the Bill of Rights.
This revolutionary act (the Oath), and the to-be-expected heavy-handed response by military so useful for the purpose, indeed galvanized splintered groups into a unified resistance which quickly evolved into people taking to the streets in Paris and elsewhere, eventually to storm the Bastille and force the Crown to retire in favor of forming The French Republic. It took less than two weeks for the government to fall. It was the best of times, it was the worst of times (Dickens; A Tale of Two Cities.)
The 577 who took a stand represented a mere .000015% of the nation’s populace, or about one in 7,000 persons. But the mood of the people was sympathetic to their aims, and when government reacted in murderous opposition instead of simply ignoring them, an unstated rally call was heard and heeded by the people. In France, the civil and military powers had guns and cannons, and the people only had pitchforks, swords, rocks, and scant few firearms. But they had anger and numbers which quickly forced capitulation, though at a cost of life on both sides – about 300,000 souls, or just under 1% of the population. Not all revolutions are even that costly.
Other Revolutions
The American Revolution began with a similar meeting of just 56 Men from the 13 Colonies, the population of the Colonies at the time about 2 million. That was the 1st, and later, the 2nd Continental Congress, and we know where that led in short order. That means about .000028% or one in 3,500 persons was all it took. King George, of course, jumped off the platform big time, leading to Lexington, and the resulting loss of life for both sides combined was about 34,000, or 1.5%.
The U.S.S.R. Revolution of 1991 began with 36 delegates of the Baltic Republic of Estonia and Latvia who, along with several hundred ‘Intellectuals’ signed a demand of autonomy from the Soviet Union (that would be like a Texas and California demanding Secession from the Union). This forced the Russian Communist Party (their government) to consider their redress and to attempt a compromise to hold Russia together, as other States were also wanting to flee the Union, but in the end, it would not be — the ship was clearly sinking. The population of the U.S.S.R. at the time was about 290 million. That works out to .0000015 or about 1 in 70,000.
A lot of things happened stepwise, but the important aspect is that violence was quite mitigated because government did not exactly jump off the platform. Instead, the military almost immediately sided with the revolutionaries, and such violence was not needed as a catalyst because the grievances were many and hatred of the System already abounded universally, even among the military, which at best, had split loyalties. Deaths were virtually unreported they were so few, though civil unrest in power struggles within, between, or with the various Soviet States which elected autonomy in the years following would result in significant loss of life at levels on par with other revolutions. Yet these deaths were not truly the price of freedom for Russia herself. Thus one of the greatest tyrannical governments of all time, a government itself established by a bloody revolution not 100 years earlier, was deposed with hardly a shot fired. Bravo!
![]() The Indian Revolution for freedom from British Rule led by Ghandi in 1919 could arguably be described as a revolution fostered by one man from a population of about 250 million, though in his triumphant ‘March to the Sea to make salt, an illegal act by British decree in attempt to force Indians to pay a salt tax, he set out with 78 followers. By the time he reached the Sea, there were untold thousands. Even so, that defiance was the start of the revolution in real terms, involving only one in about 316,000 persons. The loss of life in the shooting part, which was one-sided as the entire revolution was one of non-violent protest, was about 1,000. These were from British atrocities such as British troops trapping 10,000 unarmed men, women, and children in a public courtyard in Amritsar and opening fire (scene from movie, Ghandi) without warning, expending 1,650 rounds of rifle fire before withdrawing without providing medical aid.
The Indian Revolution for freedom from British Rule led by Ghandi in 1919 could arguably be described as a revolution fostered by one man from a population of about 250 million, though in his triumphant ‘March to the Sea to make salt, an illegal act by British decree in attempt to force Indians to pay a salt tax, he set out with 78 followers. By the time he reached the Sea, there were untold thousands. Even so, that defiance was the start of the revolution in real terms, involving only one in about 316,000 persons. The loss of life in the shooting part, which was one-sided as the entire revolution was one of non-violent protest, was about 1,000. These were from British atrocities such as British troops trapping 10,000 unarmed men, women, and children in a public courtyard in Amritsar and opening fire (scene from movie, Ghandi) without warning, expending 1,650 rounds of rifle fire before withdrawing without providing medical aid.
Ironically, the commanding Officer in that event did more to set India free than perhaps Ghandi with respect to World opinion and political fallout. That is the power and importance of government’s role in their own revolutionary downfall.
Inversely, however, it is no guarantee of success to be sure. Revolutions are a dicey thing.

Single man armed with bag of groceries defies a column of more than 50 Chinese tanks and stops them cold while the World held its breath in fear for him. From thehoopla.com.
By example, Red China did not fall as a result of the Tiananmen Square revolution in 1989, in part, because the Red Chinese attempted a total media blackout while they killed 7,000 unarmed students gathered in peaceful protest. With a population of 1.1 billion, that is still only .000006%.
But here is the important part, a singular event which took place after the carnage. One man defied the full might of the Army in an unimaginable act of defiant bravery, and got away with it, If, on the other hand, they had rolled their tank column over the lone civilian deliberately blocking their path… which had been managed to be captured by media… I suspect China would now be a true Republic free of Communist rule. If so, one man would have taken the credit in my book. This showed the World the power of the individual voice. That, my friend, would be your voice… SHOULD be YOUR VOICE… with as much of his demonstrated power as you care to assume in using it.
Thus we see that most revolutions require relatively little bloodshed, typically less than 1-2% in population loss, and relatively little original effort by a mere handful of citizens… provided the government truly lives up to tyrannical expectations and resists with all the forces at its disposal. As you continue (please) on to read the other posts associated with this post, keep this in mind, and judge for yourself how close to revolution we may or may not be. Decide which side you would choose to support if shooting does start, and make plans for your family’s safely transitioning through any such upheaval. I can only provide a warning and advice on what to consider and what to do… but only you can make the critical decisions that matter.
And they do matter… to you and your family… and to the nation in which you must seek to pursue happiness and whatever destiny awaits us all, every one.
Related articles
- On the Impossibility of Limited Government and the Prospects for a Second American Revolution – Hans-Hermann Hoppe – Mises Daily (gunnyg.wordpress.com)
- ‘Europe on the brink of armed-revolution’ (rt.com)
- 13 Reasons Why The Revolution Might Start with Obamacare (blacklistednews.com)
- Why the Occupy Movement Frightens the Corporate Elite (truth-out.org)
- GOP Newsletter Calls for Armed Revolution if Obama Re-Elected (alan.com)
- A Stealth Coup d’État in the United States (english.pravda.ru)
24 Campaign Planks; H. Michael Sweeney for President of the United States?
No one would, I hope, consider me a serious candidate, and certainly no one mainstream would consider my ‘extreme’ planks as reasonable… though that would show they have no clue as to what true conservative politics are. I am neither left nor right wing, though I have been called both. All I seek is to restore the country to the state it was in before government got so powerful it managed to destroy the country, a kind of political time warp going back some 50 to 100 years. In simpler terms, I’d restore the government of the United States to a Constitutional government as envisioned by our founding fathers. How left- or right-winged is that?
Indeed, all the policies put in place in that time span which have gone awry and led us astray would by those governmentals in power at the time would surely have seemed to be the radical (both to the left and the right) notions in the eyes of the likes of Jefferson, Hamilton, and Franklin, et. al. Our country had run just fine for more than 100 years without such changes, and is now on the verge of extinction because of them. So why not fix it? Because it’s radical?
But that all means is that I’m a a strict Constitutionalist, which also means I am per the current use of the term by media not just a radical extremist, but even a terrorist by some standards, which I take as a badge of honor in the face of the tyranny of an unconstitutional and lawless government. But then, so are you, too, just for reading this, because endless Draconian legislation and the public rhetoric of power brokers desperately seeking to retain status quo must consider you guilty by association. FBI, in fact, now considers ANY contact with ‘extremist or terrorist’ groups as justification for surveillance targeting. I’ve written about that extensively in my books on personal privacy and security.
You have no right to use your mind as you see fit, and are a become part of a growing danger to the status quo (keep it up!). The government spies on everybody, and in their reasonable paranoia (because the angst of the 99% is nothing compared to the disgust felt by the many who did not hit the street out of fear). And it is that; they use fear of terrorism and of government heavy-handedness (Police, TSA, FBI, NSA, CIA, and others, to include even the military, of late) to tighten their grip, and event to get us to spy on each other. Replay of Nazi Germany tit for tat. Got your Brown Shirt and armband handy?
Because those of us who are fed up with the status quo… with the New Boss being the same as the Old Boss (and largely lost to their power-mad tyranny)… fed up with the corruption, the pork, the endless signing of Bills without even reading them (largely lost to their greed-driven treason)… and fed up with the steady march toward a New World Order and a Police State mentality (largely lost to their Globalist Fascism)… will LOVE my planks.
But since I am not running, let’s just say it is for mere entertainment and intellectual exercise that I present my planks… which might be described in a motto, ‘Restore the Republic.’ It would effectively de-centralize the Federal government’s power for all except things which were critical to National viability. What most of the Federal agencies are and their functions can be done better and less expensively, and more gently, by the States, or is best left undone at all. I seek to undo.
Unworkable? Unrealistic? Nieve? Sure. But the best ideals ever adopted by humanity through history started out that way. It was, in point of fact, one such ‘unrealistic’ ideal which drove both the French and US revolutions and their resulting Constitutional structures. Those revolutions were driven by a multitude of nieve ideals, just one of which was stated in mutual paraphrase by both Jefferson and Montesquieu, here.

King John of England signing Magna Carta on June 15, 1215, at Runnymede; coloured wood engraving, 19th century. (Photo credit: Wikipedia)
This, and many other like remarks summed ‘radical notions’ unheard of before the Magna Carta, quite unworkable and unrealistic in face of the virtually unlimited power then held by Kings. But when ideals and goals are lofty enough, idealists everywhere will find a way to make them workable, and make them real, despite any ignorances in the beginning. Stumble along the way as we learn, say I. Far better to stumble going forward up a tough hill than to take easier path; sliding down the slippery slope of despair into the total ruination which seems now so near at hand for our once fair Land.
So you can’t vote for me (write in’s excepted), but you can try to pressure candidates to adopt these planks or some other workable overhaul, and vote for the ones that come closest to meeting your wishes. Right now, for me, that would be Ron Paul, in my opinion. Or you can give up and let the NWO win. Or you can pick up a gun and start a revolution with no guarantees of surviving the effort. There are no other choices, the later two so frightening and yet so near on the horizon by the clues at hand that I pray to God for a miracle to prevent them. I suspect we would agree some kind of an overhaul is in order, so humor me then, please, with an overview of the planks… not presented in any order intending to imply priority. Moreover, they are but a small sampling of wrongs in need of righting…
Plank Number One: Critical Review and Reversal of Presidential Executive Orders
In the first 90 days I would move to review thousands of Executive Orders since Lincoln with an intention of reversal of those which have quietly modified the institution of Government in ways which have proven to be tragic in the long run. For all my love for Lincoln, he started us down the path of ever growing, unchecked Federal power, the bulk of which resides in the Presidency. Some tweaking is in order, it would seem. We don’t know about every E.O., because untold hundreds of them are not for public consumption (which makes me nervous about their purpose and result.) But some of them we do know about, as they tend to make their way into the Federal Register (on line). Here are just a few examples… one of which curiously needs enforcement, rather than revocation.
Revoke EO 7933-A By Franklin D. Roosevelt. It allowed the IRS to investigate the finances of those under suspicion of unamerican activities, a provision in support of the McCarthy witch hunt in the Red Scare. Since it is still in place, even though the House Committee on Unamerican Activities no longer exists, this EO may represent a potential source of political targeting by the IRS against Muslims and the politically incorrect among us by our paranoid government.
Order the enforcement of EO 111110 by John F. Kennedy, which was intended to restore the power of the U.S. government to issue money, and end the ability of the private bank of the Federal Reserve from making loans in the form of Treasury Notes to the U.S. government and charging interest. THIS, is where the National Debt comes from. This EO was never enforced, perhaps because JFK’s assassination rendered it ‘unknown’ in some way, or irrelevant under the helm of Lyndon Johnson. However, it has never been revoked, but was ‘nullified’ by a sneaky E.O. 1208 by Ronald Reagan, which needs to be revoked. Upon such corrections, therefore, a new EO would be appropriate which denies that portion of the National Debt accrued since the signing of 111110 June 4, 1963. It is, by EO 111110, stolen money, ill-gotten gains. Go fish, Globalist bankers.
Revoke EO 6102 by Franklin D. Roosevelt, which prohibits citizens and corporations to ‘hoard’ Gold. Ostensibly to allow the U.S. Government to protect and enhance its own Gold reserves in backing of U.S. Currency, the EO remains non functional given that the U.S. no longer employs the Gold Standard, preferring instead to pay huge sums of interest for printing endless IOUs to the privately held Federal Reserve Bank, which is not a government agency. Revocation would allow free ownership and barter of all forms of Gold and Silver by any citizen or corporation for any purpose. Use it or lose it. Moreover, as President, I would demand a tour and inspection of content at Fort Knox to see if there is actually any gold left there, at all, or if it is now fake to cover a suspected theft.
Revoke EO 12148 by Jimmy Carter (and roughly 15 related E.O.s) which would disband F.E.M.A. A replacement agency which truly represented emergency management and did not represent a potential tool for total power grab and abuse of power as the agency has so faithfully exhibited as its true purpose or limit in ability (next paragraph). I would propose that each STATE have its own local FEMA replacement entity under local State Government oversight cojoined by a centralized Federal oversight body to insure that once activated, the State’s best interests were maintained with respect to cooperation in aid between States and the Federal level. Each State, however, is its own boss as to how and where such aid is delivered internally.
Few people realize how insidiously powerful FEMA becomes in the event of Martial Law or even a simple localized emergency declaration. They will control EVERYTHING including how much food you have on your shelf, if you can travel ANYWHERE (even to work), or if you can buy or possess ANYTHING, and much more. They gain control of all aspects of social life, including your kids, your medical choices, etc. And as seen in the aftermath of Katrina and in the wildfires of Texas, FEMA is NOT our friend, but our mortal enemy. Worse, that State of Emergency is already declared, and has been since 2001, and you will not believe what FEMA’s role is to be should they choose to act on their power. Under Reagan, plans were discussed at the highest levels of government for FEMA to intern blacks in concentration camps. You can bet there is an E.O. somewhere adding Muslims to that list. WTF? Now all those conspiracy theories about FEMA camps don’t seem quite so ‘theory.’
FEMA must die as a NWO Fascist instrument, which means a lot of E.O.s must be revoked.
Revoke EO 13158 by Bill Clinton and EO 13575 by Barack Obama, and others, which transfers large tracts of U.S. wild lands, rural and Agricultural lands to control of the United Nations with loss of sovereignty — no Congressional approval sought. The former to establish 47 ‘biospheres‘ where U.S. citizens have been threatened (by signs, mostly, but at times, by armed military types from unknown units and sometimes speaking foreign languages) with severe punishment for tresspass. Such acts had been reported frequently over the years in the now defunct Spotlight newspaper, with further documented covert military operations and/or Soviet made military hardware storage was taking place at biospheres, ostensibly U.N. related. Yet the U.N. officially states it has no such operations or equipment in the U.S.
The later has (Obama gave up rural/agriculture land) to do with something called Agenda 21 — which essentially sponsors corporate monopolies of the food supply, but which is seen as an extension to the biosphere scheme and heir apparent to Codex Alimentarius, which is its own matter to be undone in another plank. Agenda 21 is also quite related to massive depopulation and eugenics programs which would make Hitler’s attempts to eliminate Jews seem a mere cursing in the wind. Obama is further moving in that same direction in an attempt to turn over all agriculture to control in the U.S. to a few corporations spearheaded by Monsanto. Under Agenda 21, private ownership of land is not be allowed, nor is growing your own food, nor for the matter, growing natural food; all must be genetically modified and/or irradiated.
Plank Two: Force Congress to DO IT’S JOB
E.O.s are SUPPOSED to be reviewed by Congress and approved or denied, becoming de facto law if not denied. Congress has fallen down on the job, and my Plank would include requesting a law forcing Congress to… well, do what it should. It must debate, in closed hearing if necessary, each and every new E.O. and come to a decision within a narrow time line. In like manner, each Congressman MUST read every page of every bill. Only by being fully informed may one debate and decide legislation in a way useful to the nation and its people. And finally, no Bill may be passed which contains buried legislation unrelated to the Title of the Bill, thus ending Pork Barrel and time bombs waiting to be discovered. It it deserves to be law, let it be its OWN law unto itself, alone, or let it be non existent lest it foster ignorance of the law by its buried nature. If there was a way, I’d want the law to read that any Congressman who voted for a Bill which was found by the Supreme Court to trample on the Constitution would be subjected to an immediate recall vote (but that would likely also require State law changes).
Plank Three:
a) End the FED, b) establish a GNP Monetary System where money is c) controlled and printed entirely by the government and d) tied to the nation’s financial health.
Campaign poster showing William McKinley holding U.S. flag and standing on gold coin “sound money”, held up by group of men, in front of ships “commerce” and factories “civilization”. (Photo credit: Wikipedia)
Based on the Gross National Product and the value of labor and goods, it is a bit complex to explain, here. The basic concept is that money supply cannot exceed the GNP (the value of the output of labor and goods). The GNP is to the number of workers a relationship by which the standard of living is evolved. More workers and lower GNP means lower standard of living, and less money minted, as does a constant GNP and more workers. But more workers and more GNP means a fairly stable standard of living, and money supply, while any boost in GNP greater than the increase in workers means a higher standard of living and more money. Interest rates would tend to remain constant or suffer mild fluctuations in all but the most severe of economic swings.
Minimum wage and adjustments thereto for promotions and the like would, in addition to performance merits, be based on a baseline GNP determination, not unlike the way we use a baseline Prime Lending Rate from which all other lending rates are devined. The price of goods would be based on the cost of production which includes the cost of labor, vs. the contribution the goods represent to the GNP. And then, of course, there is the matter of taxes – see next plank.
Plank Four: End the IRS as we know it
No more Federal personal income tax! No more Federal corporate tax! Instead a value added tax in the manufacturing processes. Raw material collection (taxed when sold to processors); raw materials processed (taxed when sold to manufacturers); processed materials made into components (taxed when sold to product manufacturers); products and assembled goods (taxed when sold to distributors/retailers), purchased by resellers to consumers – tax free except by State tax options. States would be encouraged to adopt the same model. The actual tax rate would be quite small, but 100% of all GNP commerce other than services would effectively be taxable and generate sufficient revenue to allow the Cost of Goods sold to cover the tax. Services are NOT taxed, and therefore, all such labor contributes 100% toward the GNP tax free.
Yes, you would pay more at the store for the goods you buy, perhaps offset somewhat by the lack of corporate taxes which are already causing prices to be higher, but you would no longer have 1/3 or more of your income eaten up by separate tax payments and you would have NO REPORTING OR FEDERAL SNOOPING, INDEPENDENT IRS COURT SYSTEM, and NO IRS TO WRITE ITS OWN LAWS, etc. And remember, much of the National Debt has been wiped out in Plank One, so taxes actually go to funding government operations, not to retire a bit of the national debt owed the banks for all that illegally printed money. A huge chunk of tax revenue today (up to 75% of taxes) goes directly to the banks as interest payments.
Plank Five: Make the nation pay for What it Buys When it Buys It
You want to buy a tank, Mr. Army? Want to build a spy satellite, Mr. CIA? Want to build a highway or dam, Mr. Congressman? Use the money you actually have in hand from tax collection, or you can’t have it. Don’t even think about writing legislation you can’t finance from taxes. A balanced budget with ZERO National Debt should be the law of the land. This also means that Social Security funds must be reimbursed and payments updated to reflect where they should have been prior to the looting process (SS is its own plank.)
It does NOT mean that you raise taxes to buy something you can’t afford at the moment. Since taxes are collected DAILY, the Congressional ‘checkbook’ has an income stream against which you may write legislative checks as you need them. Live within your means, Congressmen. Emergency funding for dire circumstance is handled by borrowing from the banks only to the extent that payments are clearly within the ability to pay from the monthly income stream. So I suppose the fat bankers can still sponge a bit off government, but it would in such a case also be to the advantage of government and to the people, where as currently there is only the one winner at the piggy trough.
Plank Six: End the Alphabet Soup Intelligence Agencies
The TSA, DOJ, FBI, DEA, CIA, NSA, DOD, DIA, HSA, etc., etc. represent a top heavy superstructure of spying on Americans that MUST stop. I’d rather completely fire all these people and deal with the aftermath of villains running amuck than put up with the crap I’ve seen first hand as victim of endless COINTEL PRO style targeting (of myself and my clients). This is the number one source of fear of government in America, exactly as it was in the Soviet Union before their revolution.
But that extreme is not required. Cleaning house, redefining goals, and placing checks-and-balance style limitations on them will, in most cases, be a good fix. In some cases, like HSA, NSA, CIA, the housecleaning will be so significant that they may feel like they were done away with, but their root defined core jobs will be left in tact. In other cases, redundancy is found to exist and that can be eliminated, and in yet others, there is simply no just purpose not better served by some other means. This plank would be a literal death warrant for any candidate so proposing, I’ve been repeatedly told. I mean assassination. So what does that tell you when U.S. Citizens fear their government such they believe it would assassinate civilian politicians to preserve status quo?
Plank Seven: Give the Indians Back Their Land

English: United States Department of the Interior advertisment offering ‘Indian Land for Sale’. The man pictured is a Yankton Sioux named Not Afraid Of Pawnee (Photo credit: Wikipedia)
I would offer to the stoic Tribes of American Indians complete responsibility and control of all Federal Lands not used as military reservations. This would end the BLM, Fish and Wildlife, and assorted other agencies, and place forested and wild lands, national parks, and other lands in the care of the people who loved it most, and took far better care of it than have we. Much of the current budgets of these agencies would go to the Indians to fund that management. They would be required, of course, to allow free access to public lands, but empowered to stipulate rules of use to insure the lands were not fouled or abused. They would inherit the resources and manpower of the aforementioned agencies as tools they may freely mold and reshape as they see fit. All treaties would be rewritten to undo prior treacheries as well as could be managed, the new lands being added to their reservations under joint ownership, but useful to their communities to include relocation and new settlements. I would not intend Casinos or industrialization of the type now all too easily approved on these lands, or other uses not now allowed, but all other good use to the Tribes would be their right.
Plank Eight: End Corporate Personhood As it Exists Today
Not quite an ending… but I’d move to make corporations more like real people. For one thing, that means they have a life time to live, and a means of producing children to survive them. At the end of their life, their children (spin off corporations) carry on the same family name, clients, products and services. Like real people, they also must be held accountable for their actions with real impact to the corporation as well as its Boards and Officers, and in a manner consistent with the same acts if committed by a real human. Toward the end of longevity (say 100 years), a corporation would split into one or more sub corporations (children), which would give all employees who ever worked for the corporation, even if just for one month, a pro rated share equal to their contribution in labor to be credited toward stock OPTIONS at the prior value of the original firm when they were FIRST hired. Over time, ownership falls more and more to employees and less and less to moguls and block stock investors.
By such a scheme retirement programs might be eliminated, providing a nest egg for retirees without increasing corporate obligations over time, and the ‘children’ would gain fresh funding for a growth spurt during their formative years. I would seek controls of Boards of Directors which prevent the same men from sitting on multiple Boards in a manner which puts too much control of a sector into too few hands. I would end the revolving door; seeking a ten-year waiting period for government personnel before allowing them to work for firms in any sector in which they held a position of related service in government, and in like manner disallow any member of an industry to serve as more than advisor to government, certainly not as administrator in any government oversight of that industry’s affairs. To be hired by a firm as a former government employee, and vice versa, should be based on expertise born of their experience and not clout and pull still in place with staffs remaining in recently vacated offices. Period!
Plank Nine: Establish a Free Press and Transparency in Government
Currently there exists a kind of de facto partnership in America (and a mirror situation in other ‘free’ countries) between the Military, Industrial, Intelligence, and Media sectors… forming MIIM, the Military-Industrial-Intelligence-Media complex. Media is controlled by a small handful of individuals who are largely in bed with the other sectors. At one time (at the time of the friendly fire shoot-down of flight 800), all three major television networks were outright subsidiaries of military contractors, which is why they fired any reporter who said anything on air about friendly fire.
Currently, there still remains employed within media, which includes the entertainment and advertising sectors, thousands, if not tens of thousands, of CIA and other agency personnel, to include military proponents serving as mouthpieces for the very undue influence President Eisenhower warned of when he left office (listen carefully to his Farewell Address video and you will see that he warned us about almost everything these planks address). This was a direct outgrowth of CIA Operation Mockingbird, and only the tip of the current iceberg.
If a means of insuring that ownership has no impact on editorial and reporting departments cannot be easily found, I’d just as soon provide equal funding to alternative underground news sources. All employees who were government shills would need to resign or face charges of treason if uncovered after the fact, because disinformation is treasonous in any government of the people, by the people, and for the people. Thus media must have good access to government, and government must be frank with media. While national security can make it important not to reveal the full truth of a given matter, lies should never be national policy, at home, or abroad. Even an enemy MUST know we are truthful that they not misread our intentions, and we should never betray a friend by a lie, especially our best friends, our very own citizens.
Plank Ten: End Foreign Aid and Foreign Policy as We Know It

National Security Action Memorandum No. 6 Plan of Reorganization of the Foreign Aid Program – NARA – 193406 (Photo credit: Wikipedia)
Foreign Policy and any resulting aid should be about helping those in time of great need. It should be about bolstering defenses of weaker nations against predator nations. It should be about encouraging free Republics and free enterprise (not Democracy, and not capitalism or free trade – there are significant differences). It should be about bootstrapping struggling nations that they might become financial and social partners in World building (not New World Order building). It should be about assuring health and wellbeing of human kind ((not the wellbeing of the big pharma firms), and done regardless of race or political creed.
It should not be about politics, fat military contracts, or quid quo pro deals for fat cats. Israel is a strong, wealthy, proud, and fully independent nation. Mutual defense agreements, yes. Arms sales at competitive prices, yes. But the billions must stop flowing to them and other nations as a means of buying loyalties, funding MIIM, and aiding the march of the NWO. You don’t buy friends and good neighbors, you build good neighbor relationships and cement friendship by actions, by standing by them in a time of need, and by being fair. You don’t take food out of your own children’s mouth and give it to the neighbors when they have their own.
Plank Eleven: Fix Health Care and Confront Pharma
Step one is to forbid Pharma to advertise to the public. Doctors, perhaps, via medical journals. This will lower prescription prices. Step two is to forbid insurance companies from forcing deductibles or co-pay minimums at term start, which effectively eliminates the poor from getting health care even when they have insurance. I myself have insurance which I and my children cannot use for this cause. Step three is to stop the fat-cat billing schemes inherent in Medicaid and Medicare which allow hospitals and doctors to rake in tons of money for outrageous charges and unnecessary procedures. These need to be replaced with a monitoring system that rewards discovery of overcharges and excessive billing.
In my own extended family I can cite countless thousands of dollars in endless examples both at private practice and hospital levels. Step four is to establish government oversight, which will never work unless the FDA and CDC is eliminated and replaced with a body that protects the people rather than the corporations. Step five is to FULLY investigate the origins of HIV, Avian, and other man made virus,’ including Cancer, and to ALLOW alternative medicine cures to be explored.
Step six (step one, really) is to shred Codex Alimentarius, Agenda 21, and related NWO efforts. GMO crops should be illegal unless passing stringent tests by outside agencies. Currently, it seems, no GMO crop could pass such a test and represent a greater long-term health threat than the Black Plague. A Congressional investigation of Monsanto actions is in order.
Plank Twelve: Fix Agriculture and Immigration
Step one is to make it illegal for any firm to control more than 15% (or some number which assures competition still thrives) of a food supply or aspect of production and distribution — no monopolies such as enabled by GMO and Agenda 21. Step two is to enforce current labor laws against employers instead of focusing only on illegal workers, which would tend to make illegal migrant emigrants less of a an issue. Step three is to naturalize all current illegal aliens who can pass minimum tests for language, non criminality, and health, and simultaneously truly seal the borders and evict all who do not pass the standards. Step three is to allow conditional work visas for would-be emigrant migrant workers based on a system of work demand vs. worker supply such that if non emigrants will take the jobs, they may more easily do so without competition from illegals. Step five is to stop teaching mainstream courses in multiple languages in our schools. You must know English to go to school, where if you wish to learn a second language as its own course, you may do so. So if you want to be a migrant worker crossing the border, learn English first or leave your kids behind.
Plank Thirteen: Stop the RFID Technology Threat
If you do not understand the nature and threat which Radio Frequency Identification Devices represent to your personal liberty, then you have not read my books or been paying good attention to the Web. I suggest you can ‘catch up’ by listening to my Webinar interview with Republic Magazine… about 32 minutes into the interview. The one simple way to stop RFID as a threat is to simply require them to be removable or destroyed at point of purchase, and that all such product be prominently labeled.
Plank Fourteen: Stop Canamex COLD, Kill NAFTA/CAFTA and Job Exportation
This is a broad topic beyond the scope of usefulness in this (already too-long) an article. I would simply repeal or renegotiate the agreements in place and write Canamex out of existence. See my blog post on Lion Dance, or request my free newsletter on Canamex for an eye opening explanation of why this is a critical step; email proparanoid at comcast net.
Plank Fifteen: End the Drug War and decriminalize illicit drugs, empty the prisons.
America, with a population on par with Europe, has a half million people behind bars for drug related matters, more prisoners per capita in this one category than most other nations have for all crimes combined. It is a fake drug war prosecuted by a CIA front agency (the DEA was founded by top CIA operatives) as a tool to protect illicit drug sales by sanctioned CIA conduits. It forces the price (and profits) artificially high, and fosters a prison-based economy to the delight of corporate greedsters. Take away the criminality and replace it with treatment, and it will cost our economy one tenth as much, boost GNP, and make it less profitable for Cartels and CIA alike. Pushers stay in jail, users walk.
Plank Sixteen: Fix Voting and Census
The Census is very critical to certain functions of government, including Districting for voter representation and the voting process. But the Census can be done in a way which is not invasive and a violation of privacy, and is kinder to those less disposed to cooperate. The solution is similar to a solution I have in mind for fixing the less-than-trustworthy voting system. These solutions are too complex to fit a paragraph or two, but essentially decouple raw information from the identity of the individual after a simple verification process, which is to say, that in the passing of information, identity verification simultaneously dissociates the information with the individual. Additionally, a verification process facilitates the individual’s ability to verify their vote or census material was correctly tallied and attributed as intended, all the way up the ladder to the final tally. The general method may be loosely described as being similar to certain email encryption schemes involving keys in possession of both the sender and the recipient.
Plank Seventeen: Get at and Expose the Truth
JFK, RFK, MLK, Peltier, Riconosciuto, Christic Institute’s Secret Team, Mena, OKC, Waco, S&L, CIA/DOD mind control, MJ-12 and UFOs, and above all, 9-11 and the Derivatives Scam. Conspiracy theories, my a**. If the official facts are in conflict with themselves and defy reality and/or logic, but are accepted and tendered as truth, that is a kind of proof of a cover up, and any time you have a cover up, it is automatically a conspiracy as a matter of fact. It therefore justifies further investigation by independent and unbiased participants. Truthers will out.
Plank Eighteen: End Globalist Traitor Domination of Government(s)
You cannot be a patriot and serve fellow citizens in office if your true allegiance is to a Globalist agenda which would seek the end of national sovereignty. An oath of political office should include declaration of non alliance, affiliation, membership, or sympathy for the goals of Globalist organizations such as the Bilderbergers, Tri-Lateral Commission, Council on Foreign Relations, Skull and Bones, and the like. To violate the oath would make one subject to prosecution and imprisonment.
Plank Nineteen: Kill the Military-Industrial-Intelligence-Media Complex
While this has already been addressed in part above, I would additionally want every black operation and military and intelligence project currently in works or previously undertaken reviewed. Where such operations were deemed either in support of a New World Order or in support of MIIM profiteering or power grabs, all persons associated with it at management level would be subject to investigation and possible prosecution for treason.
Plank Twenty: Fix Social Security
This is easy to do. As we see in planks 3 and 4, funding SS as it was intended will be quite doable, with additional help by easing of government costs resulting from many of the other planks. Further, plank 8 gives employees of corporations a built-in retirement program vastly superior to SS, and thus SS obligations now active would be come locked in or ‘grandfathered,’ but it would become a voluntary program at each new employment opportunity. Further, I would enforce the law regarding SS numbers and force the elimination of all electronic data and forms outside of the Social Security Office of said numbers. It has no place in credit reports and other records.
Plank Twenty One: Explore an alternative to Daylight Savings Time; Social Time
Our highways are clogged, unemployment is high, classrooms are crowded, stress is high. A long list of such social complaints can be offered. I propose a review of what I call Social Time, presented here in oversimplified explanation; a work day definition is cut to seven and a half hours paid, plus another hour for lunch and breaks, but the bulk of social infrastructure both private and governmental would be expanded from ‘a day’s work’ to a full 24 hour work cycle. That would mean, with broad participation (voluntary for the most part), that businesses and agencies would be open at all hours, which would dramatically reduce volume of client traffic at any given hour and spread it out somewhat evenly over the whole clock.
This would allow some reduction in manpower needs on an hourly basis, yet often provide new jobs to support the extra hours. As time progresses, the work day for an individual would start 90 minutes later each day, thus revolving everyone through all twenty-four hours over the space of just under a month — 14 times a year. We would not need to build more schools to reduce classroom crowding, or more transportation systems to handle population growth, etc. GNP and employment could only benefit, and make the country more competitive. Part and parcel of this idea is to END PART TIME EMPLOYMENT loopholes for employers who don’t want to offer benefits. EVERYONE GETS BENEFITS, but under the various planks outlined above, the cost to employers for benefits will decrease.
Plank Twenty Two: Establish True Redress and an Initiative Process
Whistleblowing shall not be punished. Lawsuits against government for violation of rights or constitutional violations shall be funded by government. In balance, should government win the case, the costs will fall back to the plaintiff. Any citizen can propose a law for consideration in a process similar to that found in several states, such as Oregon. If such proposed law meets constitutional tests, is written to legal requirements, well defined and stated, and can earn popular support (signatures of citizens who so support), it can be sent to Congress for debate and possible passage. In Oregon, the law goes to the ballot for vote by the people, as does all legislation proposed by State legislators. See next Plank on how this might play at a national level.
Plank Twenty Three: Review of possible Constitutional Change from Republic to Advocated Democracy
Especially where initiative process (prior plank) is in play, the use of the Internet could allow, with careful creation of safeguards as also addressed in earlier planks, a way to allow the people to vote on Bills rather than Congressmen. This would be an Advocated Democracy, where elected Representatives (the Republic style) would instead merely propose or debate initiative proposed laws. This would be broadcast and each citizen would then decide to vote for or against the legislation. No more pork barrel, no more bribed Senators, no more fat cats, no more buried language, no more end-run legislation. Just pure simple will of the people.
Plank Twenty Four: End Non Consensual Testing on unwitting subjects, and use of Political Control Technology (PCT)
Last but perhaps foremost in terms of being close to my heart. While current laws prohibit non consensual testing or use of weapons, drugs, and procedures on citizens, there are far too many loopholes which allow it to take place. In my books I cite countless examples, and as consultant I work with victims of it every day. Worse, the very agencies established for the purpose or which otherwise have authority to enforce such laws, are compromised by intent or by lack of training and resources, not to mention handicapped by their very belief structures. It is a sin that Police, for instance, automatically presume one crazy for hearing voices in their head when it is a known fact that CIA and Department of Defense has spend billions to develop technology which allows anyone to be targeted with such experiences, generally with the express purpose of discrediting the target by making them seem mentally imbalanced.
I’ve already proposed language for laws which properly address this topic, and submitted them in written testimony to the Massachusetts State Legislator when they were considering such a Bill. Currently, the military and CIA are developing new PCT faster than we can learn of it, generally under the guise of antiterrorism and funded through Homeland Security. It is a joke to presume that any of this technology can in any way prevent terrorism. It can only enable political control of the population, and nothing more.
Related articles
- The Best: Tracking You and Your Family Just Got a Whole Lot Easier (whiskeyandgunpowder.com)
- How Roosevelt Sold Us to the Higher Bidder: the Federal Reserve (myvoice2012.wordpress.com)
U.S. Military: ‘The Best Defense’ & Your Future In Their Eyes
On Military Thinking About ‘The Best Defense’ and Your Future in Their Eyes
by H. Michael Sweeney,
copyright © 2011, ProparanoidPress, all rights reserved permissions to reproduce by request to pppbooks at comcast (net) military thinking Dateline Portland, OR Nov 16, 2011 military thinkingPartnership of the Military and the New World Order
We all want a strong military to defend our country, and we would not wish to deny them tools for a ‘best defense,’ but we would prefer that be their only role. Unfortunately, one cannot fear the New World Order without also fearing the U.S. Military Establishment (along with a bunch of other people). The role of the Military in meeting the goals of the NWO to establish a one-World government ruled by (we must logically deduce) the Antichrist has often been made clear. As any Truther will likely tell you, and if not, I will tell you, the 9-11 attacks would surely seem to be such an example, though many other examples are easier to reveal. We must rightly therefore question what the military sees for your future in their eyes. We know what that future is, and I’ve written of it often, but all-too few of us have gotten the message.
And there are other examples. For one, their fascination with development of ‘antiterrorism’ weapons with Homeland Security funding or through DARPA (Defense Advanced Research Project Agency) or any number of quasi-governmental think tanks such as SIAC (Science International Applications Corp.). As I have shown in my books and newsletters time and again (listing hundreds of examples in The Professional Paranoid’s Defensive Field Guide), the overwhelming majority of such research clearly has nothing to do with terrorists but everything to do with either or both crowd control or mind control, or spying in support thereof (Political Control Technology, PCT).
This includes everything from swarms of flying insect-sized spy devices to the mammoth HAARP (High Altitude Auroral Research Program) associated with everything from Weather War (earthquakes, killer storms) to regional mind control to deep-sea communications with submarines and other legitimate defense applications. In fact, it even seems tied to the possible application of HAARP and like facilities around the World for the suspected and feared Project BlueBeam, a NWO plot thought to employ massive global in-air projections of holographic images along with in-head audio to simulate the second coming of Christ… only it will be to help seat the Antichrist. These capabilities would indeed seem to be within HAARP and associated system abilities as seen in my YouTube vid.
We can also add to the list concerns about development of race-specific pathogens and bio weapons based on zoonotics (new never-before existing man-modified animal virus‘ so that man can be infected with little or no hope of a vaccine being developed quickly: e.g., Avian Flu, Swine Flu, Aids, etc.) and nanotech and the deliberate release (testing) of strains on civilian populations, and for the matter, a history of testing such weapons on U.S. Citizens going back more than 100 years. The Defensive Field Guide has pages of such testing listed, and my book set Fatal Rebirth takes a very close look at bio-weapons development and use, though recent investigations reveal that the scary picture emerging on those pages is merely the tip of the iceberg. Those who already know the NWO for what it is know all about the concept of Eugenics and deliberate population reduction with soft and hard kill technologies. How else do you expect them to get us down to 500 million population?
So when I ran across a very simple and innocent blog article by staff writer Skyler Frink in Military & Aerospace Electronics questioning what is ‘the best defense’ strategy for the military, I felt I had to weigh in. They were kind enough to allow me to post a comment to their blog pages (uncensored) with my own viewpoints. I wrote with admitted restraint, citing concerns about the Revolution in Military Affairs (RMA). Since I cannot reproduce their blog here without permissions, I suggest you take a few moments to read it on their site, and my gentler response. Three minutes total read to compare what the rank and file within the military-industrial complex itself presumes to describe our Military’s role and best defense as opposed to the picture painted, here. Then you may continue reading here what I wish I could have said there, but which would have been inappropriate and unwelcome to the point of likely rejection.
military thinking
The Revolution in Military Affairs
RMA was a concept very logical in its basis and would have simply addressed a viable need in a reasonable way, except for one thing. Those responsible for its evolution and results included NWO shills (I’m being polite). Just one example would be the avowed Satanist and U.S. Army Lt. Col. Michael Aquino. Aquino holds a Doctorate Political Science and founded the Temple of Set, a splinter group of the Church of Satan, all of which are organized (like many cults) along Masonic models such that they have a public side (relatively prim and proper, even for Satanic public relations) and a darker, secretive NWO cabal side.
Aquino has been involved in everything from a psychological warfare support role in Operation Phoenix, the Army/CIA mass civilian assassination program in Vietnam said to have claimed as many as 40,000 persons, to mind control projects there and here in the U.S., to child molestation cases involving the military (see note), and more, including a project to ‘unify all religions’ into a single religion suitable for political control (think THX-1138, where you ‘confess your sins’ to the government’s priest). The devilish (literally) concept and early stage development to combine religions were undertaken at the military occupied Presidio, and continues even today as being associated with the Presidio — which is where Aquino’s child molestation cases came to make news which some say threatened to expose a pedophile ring within the Pentagon itself.
Note: As detailed in depth in my book MC Realities, ritual sexual and Satanic abuse of young children is part and parcel of building Manchurian Candidate-style sleeper agents and super soldiers (Delta). CIA, DOD, and many other organizations have employed this method for centuries and is the one central core technology which enables the tracking of the history of mind control back through time all the way to the Crusades and the Knights Templar, which evolved to hide within the Masons stone worker’s guild, and eventually took it over to become Free Masonry. It is from within that body whence came the Illuminati, the originators of the NWO movement to seat the Antichrist in an extremely long-term game plan which still unfolds today. What DOD has also learned it seems, as also explored in the book, is that it is possible to use fake alien abductions to do the same job with adults.
With top Pentagon clearance Aquino has been described as instrumental in guiding RMA. His power was so considerable (some say he is actually now a General, though retired) and remains in force such that you will not even find an entry for him at Wikpedia, but rather, only an entry for the Temple of Set. There was an entry, but it was removed and is the stuff of conspiracies. Thus his role in RMA must surely have been considerable, and no doubt there were others along side him of like ilk who’s names are unknown to us. Charges are that the military is rife with Satanism and NWO mentality, and based on the outcome of RMA, I must conclude it likely so:
Paramaters, the U.S. Army War College publication some years ago had a short piece on RMA which has since gone into the black hole. It was, however, reproduced in part in The Spotlight Newspaper in Washington D.C., itself also since gone into the black hole. The article cited Parameters description of just one small aspect of RMA which should be of utmost concern to us here: the definition of the kinds of wars the military should expect to face in the near future (NEAR future). One of these was termed as The People’s War. Another related term was Politico-Military Force Matrix. These and dozens of inter-related RMA terms are including among the hundreds of PCT terms found in the Defensive Field Guide. But these two we need to look at, here and now.
military thinking
21st Century Politico-Military Force Matrix
Nonlethal technology (all of which can kill, and has), when coupled with traditional forms of lethal weaponry and general tactical options available to government, the military, and law enforcement, allow for the application of short-term incapacitation, long-term incapacitation, and deadly force against the physical and mental perceptual attributes of human targets as well as the hardware and software attributes of machine targets. The overall collective of advanced types of weapons and psychological mind control methods form an array which can be expressed in a matrix which defines Political and Military options. He who best utilizes the matrix, or has more options within the matrix, wins.
This has been published by the USAF Institute for National Security Studies, and has been well applied in recent Middle East wars and continues during the occupations. The oil and opium must flow (with apologies to Dune author, Frank Herbert and his phrase, “The Spice must flow,” which justified the Emperor’s launching a war intent on planet-wide genocide.) Fiction becomes reality, it seems.
It also portends the Military Police State, as these same matrix elements are viewed as key to retaining power and control of a nation. Its all about PCT, which is where this article started. But the few articles available on the Web regarding the finite details of the Matrix seem to have gone the way of the black hole, too. We do have one military look at it which carefully avoids (perhaps because of not being aware of those aspects) such references. Yet it frames the concept nicely.
military thinking
The People’s War
It was defined by RMA (and is cited in Fatal Rebirth and The Defensive Field Guide) essentially as an EXPECTED conflict with “Constitutionalists, militia, ex-military, patriots, survivalist, and the poor and politically disenfranchised.” In short, the 99%. Add to this quote the factual existence and use of a ‘Shoot Americans Questionnaire‘ given to select military units to see if they would: fire on U.S. Citizens who refused to turn over their guns; obey a United Nations Commander; and supplant Police services (and other NWO useful questions). The entire questionnaire and analysis of answers provided by troops is in The Defensive Field Guide, as well. None of these things are Constitutional, legal, or moral options, though various Presidential Executive Orders and military edicts have pre staged to allow for them (another blog post in works will address this and become linked – subscribe to my blog posts to be informed automatically).
Add also that Dick Cheney authorized the DOD to establish a special group to kidnap and assassinate American Citizens, or enter their homes covertly (for any dark purpose including theft or sabotage, vandalism or arson). The story broke in the Toronto Sun who has seen fit for some reason to vanish the article, which is reproduced here. In similar vein, of course, the White House (despite Obama election campaign promises) and DOD have deemed to allow torture and detainment of suspects without due process or trial, though we ‘politely’ ship our prisoners elsewhere for torture so we can have clean hands. How neat and tidy, and we even give it a pretty sounding name, rendition. For all these reasons and more, I ask in Fatal Rebirth…
“Do you, as an American citizen, care that the military thinks gun seizure a likely enough future mission to ask this question of troops? If a member of the economic underclass, do you think your conditions will be improving in the near future if the military thinks taking away guns will become their job? Why should the military be allowed to think this way and still hold the power of arms, themselves? Perhaps the only proper gun control is to take them away from a military run amuck that it might target citizens. If this is our national defense force at work, does it not ring of fascism?”
military thinking
The Best Defense?
Thus the way I might have preferred to end my piece at M&AE would have been to suggest that the best defense is the total rework of the Military chain of Command to include sweeping out the trash and putting better controls into place. I’m not even so sure that the Pentagon shouldn’t be leveled to the ground and replaced with the pre WWII system of Command. I’ll admit that I’m not enough the expert to make that call, but by God, if I were President, I’d get some advice on it right away… unless of course, I happened to be just another standard issue NWO Cabal member President, myself. Hmmm…
But the way I answered the article was suitable to the need, and important enough to repeat here, given that one of the highest ranking soldiers in the Land has already publicly stated that nationwide Martial Law is expected soon. US Army General Tommy Franks, who led the coalition invasion of Iraq to oust Saddam Hussein, and who commanded the siege and mass murder at Waco as well as the burial of the evidence with bulldozers… described in an interview for Cigar Aficionado that the results of another attack by terrorists with weapons of mass destruction would result in our Constitutional form of government being replaced by a Military government. We also know that the new Constitution for such an event has already been written. The Constitution of the NewStates of America, with analysis suggesting surprise America is not spelled with a ‘k,’ is also reproduced in Fatal Rebirth. Don’t cry for us, Argentina!
So I repeat from my response to M&AE: Since we cannot rely on absolute power to police itself, the best defense in my opinion as student of military thinking is, perhaps, improved observation and control of the planners. Actually, I would prefer a means of divorcing centralized control of National Guard in any such action and instead allowing State’s Governors to be the sole local commanders. And no, I don’t trust FEMA in that role given their less-than-zero-performance track record.
In more direct terms, the only way to insure defense against domestic enemies, in my opinion, is to declare the Pentagon a potential enemy and allow the State Militias (the National Guards and even the citizen militia groups under volunteer command of the Guard) to be responsible for any such Martial Law. That would PREVENT and refuse subservience to any Military government, even to the point of succession from the Union pending reformation of the nation under the Constitution. Tommy Franks, Dick Cheney, Aquino, and a long list of others could then be put on trial for treason, murder, etc.
But that’s in that perfect World that we don’t live in, at least not yet.
Related articles
- The Best Defense is… (Military & Aerospace Electronics)
- Now Even MAINSTREAM MEDIA Is QUESTIONING HAARP’S TRUE PURPOSE: SEE FOR YOURSELF! (thetruthabout1111.wordpress.com)
- Former CIA Black Ops member confesses NWO plan (newsworldwide.wordpress.com)
- Is The Church In America Prepared For Red Alert / Martial Law?? (zionistoutrage.com)
The NWO Class War on the Non Elites/Professionals
The NWO Class War on Non Elites: The Temp Agencies
by H. Michael Sweeney,
copyright © 2011, ProparanoidPress, all rights reserved permissions to reproduce by request to pppbooks at comcast (net) Class War Dateline Portland, OR Oct 12, 2011 Class WarIf you are not an Elite, watch out, as even professionals can find themselves out of work and victim of Class War.Class War
Official unemployment figures are unreliable because they deliberately stop tracking people who no longer draw unemployment insurance payments, and people who do not qualify drop off the list the same month they are reported. How we, as a nation, allow government to cook figures in such a way so that they may continue in power, is beyond me. Since you are reading this, I’m presuming you are not quite that dumbed down by media.
They do this, of course, so we won’t know how bad things really are. Here’s how bad they really are: Portland, Oregon, a population of about 1.8 M, had a total of 300 new jobs listed with the State Employment Offices for (as I recall, June of 2011). The official chart shows UE at 9% in June (6th vertice), which means about 150,000 people were competing for 300 Jobs!
If everyone applied only for one job, that’s 500 per job. But its worse than that, because over half the jobs require specific skills in the Medical industry or other technical disciplines which decreases the opportunities for those without the needed skills.
The unemployment stats seem to be improving in the chart, by the way, not because more people are going back to work, but because more people are dropping off the chart than are being laid off. But none of this is what motivates this article, it is merely background information. I’m not even motivated to write this not because I’ve suffered the Class War depicted herein as related to unemployment issues, even though I have.
No. I’m motivated because my balcony overlooks a portion of parking lot for one of those low-rent Temp Employment joints. You know, the kind of place where the unemployed go to stand around like illegal immigrants waiting for a farmer’s truck to drive by and choose workers for the day. As distasteful as the image sounds, it is very close to the mark for those who rely on such sources for meager opportunities to earn a little money. Its really another example or clue regarding the very real Class War being waged by the NWO against anyone not of their ‘ilk.’ And again, as distasteful as the image sounds, that’s not the worst of it, and not my motivation.
The motivation stems from observations made both from the balcony, and by talking with those found in the lot and within the office. There are two aspects. One is what I see them do, and one is what I hear them say.
Class War
Here is what I see them do:
• Live in their cars, junker vehicles typically on the edge of being mistaken for scrap. Cars that have plastic over busted windows, no working heater, no working starter, a door that can only be opened from the outside, missing fenders, hoods, bumpers, you name it. The NWO wars on the poor with taxes, fines, and fees on automobiles, as well as safety, environmental, and insurance regulations which are weighted to impact the poor more seriously than the rest of us.
A single moving violation can wipe them off the face of the earth, as if they can’t afford the $300 minimum, they lose their license, and if caught driving suspended, their car is towed and lost forever, as they cannot get it back without their license.
• Sleep overnight in the parking lot in sleeping bags they hide, along with the backpack or shopping cart out of which they are living, behind the building. There seems to be some kind of ‘honor’ among them such that those who do not get to work watch over the goods of those that do… most of the time. The NWO wars on the homeless by systematically ‘cleaning house’ on their camps as discovered, taking their possessions and throwing them away as trash, and often arresting, roughing up, harassing, or forcefully ejecting them from the community. The idea is to make some other community more attractive, we might presume. I’ve talked to some who say they have been routed out of a dozen cities or more, in some cases the very night they arrive.
• Urinate and defecate in the lot, as it is too far to make it to the nearest gas station or restaurant when pressed, and most of them have already been kicked out of those establishments as ‘non customers,’ given that they can’t afford to buy anything most of the time they need to use the facilities. Every few days they risk being thrown out and use a public restroom to ‘bath’ themselves in the sink, and once a month, perhaps, if it can be afforded, toss one of their two sets of clothes into a laundromat’s machine. The NWO wars on the homeless by placing profits of their consumer outlets above the most basic humane considerations most people would afford an animal.
Unless you are my age, you may not be aware: they actually had to pass a law to force restaurants to offer water to non paying customers. Despite this, they can get away with charging for the paper cup if a fast-food joint.
• Show up hours before the place opens; those lucky enough to have homes or places to crash will want to be next in line after those who slept there overnight. Many walk or ride a bike, some take the bus if they can afford it. A few have cars. It seems to be a first-come, first-serve matter when the jobs available require no skills, which is almost all that is made available through these kinds of low-rent places.
Just as the illegal alien migrant workers are oppressed into perpetual impoverishment by the farmer’s methods of employment, the NWO’s oppressive Class War simulates that method in the nature of temp agencies. They sell hope, they deliver crumbs, and of course, take a portion of the wages for themselves that would not be lost if the firms would simply advertise the job directly. Ah, but that would mean actual hiring, wouldn’t it, and that would mean some level of benefits would need to be paid.
• Everyone will wait endless hours. Since there is little room inside, most sit on the curb, the fender of their car or in it, or bring their own chairs. By two or three PM, it is clear that those remaining (typically more than half) will get no work for the day, so they leave to forage for bottles and cans on the road, or do whatever else they do to survive. I shudder to think, but the Police, a primary tool of the NWO, will surely hassle them whenever they see an opportunity. Again, they would like them to consider some other community a better choice.
Class War
Here is what they say:
• Less than one in ten is drawing unemployment. They therefore ‘do not exist’ in government unemployment statistics. Vanishing the problem this way is a War tactic, because if no one knows there are victims of a War, no one will protest the War and insist it be ended. There is no useful reason to lie so harmfully beyond this. Judge your civilization by how civilized it is toward the unfortunate.
• Most of them have mouths to feed which is why they try so hard for so little. Bless them and love them for not turning to crime. At best, they tend to work 1-3 days a week, but suffer those statistics because they are TOLD and they hope and pray for a chance to be ‘hired’ by the company for whom they will be a temp if they can just get a shot at it.
That is an illusion. Statistically less than one in ten will be asked to hire on as an actual employee. The NWO corporations are more and more relying on part time and temp workers because they get to avoid paying benefits and retirement programs, one way they War on the lower classes.
• More than half have health problems which will likely never be addressed until they keel over and someone calls an ambulance. While perhaps 15 percent may have insurance benefits, they cannot afford the copays or deductibles. That, too, is by NWO design, as almost all insurance programs are set up so only people with money can play, and others stay away, even when forced to keep up the premiums. That is a whole other blog post, because there is a lot to talk about, there.
• Only about one in four admit to being homeless due to bad choices in life, such as gambling, drinking, or crime and punishment, or divorce or other personal matters gone awry. Of the balance, most blame the Banks and Commercial Credit, the financial debacle, and the economy as having made it impossible to keep their home. That is the NWO war at its finest.
And when Obama came to give help, how did he do it? Did it give money to allow these people to get back into their homes? No. he gave money to the very banks that evicted them… and he gave money to others still in their home to help pay those banks. Everyone else gets the pavement or, if they haven’t lost them, their cars. Welcome to the cold night of political reality, now please leave town because we don’t want you here if you can’t pay anymore money to the banks and other NWO businesses (syndrome).
Class War
I’m sure there are more upscale Temp Agencies (bigger) who will hopefully be able to offer a better snapshot than the one presented. But they cater to the more skilled workers, the ones who should be holding good paying jobs, but who, through the Temp process, will earn less than minimum wage for the year. The ‘upscale’ nature of it does not improve the picture all that much, it only increases the money they shave off the wages.
As for the low end of the spectrum, I find it troubling that there are two such Temp agencies within walking distance of my home, some six blocks apart. There 120 temp agency offices in the greater Portland area according to City Search, so close together in some cases you can’t see them on the Map (core area shown).
The Occupy Wall Street (and everywhere else) people have it right. Anonymous even has most of it right (one can argue about ethics of hacking). The Truthers have it right. Most activists have it right. I urge you to join them when the opportunity arises. If you are waiting for things to get better, I have news for you:
YOU are what you’ve been waiting for.
Related articles
- Laurie Penny: This is a class war disguised as a generation war (independent.co.uk)
- Is There Really a Looming Global Class War? (genomega1.wordpress.com)
- Obama’s off-target class war (politico.com)
- Wall Street Protests (robertlindsay.wordpress.com)
- 6 Ways the Rich Are Waging a Class War Against the American People | The 2012 Scenario (lucas2012infos.wordpress.com)
On Anonymous, Anonymous Methods, and Anonymous Targets
On Anonymous,
Anonymous Methods,
and Anonymous Targets
by H. Michael Sweeney,
copyright © 2011, ProparanoidPress, all rights reserved permissions to reproduce by request to pppbooks at comcast (net) V is for Vendetta Dateline Portland, OR Sept 26, 2011V is for Vendetta
“We are Anonymous; V is for Vendetta” Anonymous, the hacker group, should perhaps be both feared and revered, depending on… POVV is for Vendetta
Introduction… Who is Anonymous?
 A shadowy freedom fighter using terrorist/assassin methods known only as ‘V‘ was originally the concept and character of DC Comics, in a comic book series which lasted for only ten issues in March of ’82 through May of ’89. Called V for Vendetta, it was written by Alan Moore and relied on the wonderful artwork of David Lloyd. V, as a character, described himself as Anonymous (the 1st, if you will). A viral hacker group has hence adopted the name, the mask and other graphical elements of the character, and elements of V’s tactical modus operandi (vendetta, for one) for their own use. And they seem all powerful thereby.
A shadowy freedom fighter using terrorist/assassin methods known only as ‘V‘ was originally the concept and character of DC Comics, in a comic book series which lasted for only ten issues in March of ’82 through May of ’89. Called V for Vendetta, it was written by Alan Moore and relied on the wonderful artwork of David Lloyd. V, as a character, described himself as Anonymous (the 1st, if you will). A viral hacker group has hence adopted the name, the mask and other graphical elements of the character, and elements of V’s tactical modus operandi (vendetta, for one) for their own use. And they seem all powerful thereby.
Not just the hacker group, Anonymous, but a much greater group of seeming millions of would-be revolutionaries (I include myself, of late) seeking to right things wrong with the World and its ‘System,’ who in all likelihood are at least sympathetic with the goals of the hackers, if not their methods. Anonymous is, after all, a symbol, an idea, and not merely a fictional character, or even a hacker group. It is something which has taken on its own living persona as a collective of human expression as much as any idealistic movement in history, intangible and shapeless, and yet indelible and impacting. In the sixties, it was the Peace Symbol and a raised pair of fingers to form a ‘V’ behind which we rallied. Today, it is a mask and a V within a circle, arguably, the circle of the peace symbol as it reflects the non violence philosophy embraced by Anonymous.
Certainly, a typical person is quite enamored with the romantic image of rogue defiance of injustice, a popular theme in art and life. But we many who take up the mask have no direct affiliation with Anonymous beyond such visages and ideals… have no such power or ability to take direct action against the system as hackers… and most lack the desire to risk the kind of bravado exhibited by Anonymous, and shrink at the notion of criminality required. The later determinations are highly personal, of course, and undoubtedly vary person to person, but we all share the dream with the hackers, all share the visual trappings. Thus we all may rightly claim, “We are legion. We are Anonymous.” It is a kind of Political statement, a slogan behind which to rally and taunt the enemy called the New World Order.
An unstated but important message to the System is, however, that this could change at any time. Should the system wax even more repressive or make one false move, it could easily find that the greater army of mask wearers would unite and act in ways resulting in an actual revolution of the kind which replaces governments. Such an army could grow manifold overnight, like a flash flood, in fact, because for everyone willing to adopt the Mask, there are likely 10 or even 100 who teeter on the edge of doing so, and even more who like the idea but simply think it is not appropriate for them at the time. All can change in an instant depending on the stimuli. The System should rightly fear and respect that possibility, and behave accordingly, and not transgress. That is the great logic and genius at work within the idea of Anonymous.
V is for Vendetta
Hollywood screenplay and distant history drive the movement
In 2006, a screen adaptation by Warner Bros was produced which has become a cult classic. As such, it became a kind of springboard for the ideas which led to the Hacker group and those who share their goals. The film is revered and promoted almost as if a recruitment tool by those fed up with the New World Order, Fascism, and corruption in government and corporate machines. There are several places where one can watch the movie on line if they do not mind endless popups and commercial interruptions. I refuse to recommend a specific site for this reason. Go buy or rent the film, it is well worth it. In the watching you will learn truths about America and much of the World which you may have overlooked if not yet awaken to the fact that you have been lied to consistently by media and government for decades. It can be a Sheeple eye opener.
The film reveals these things despite a setting in a future Great Britain, a nation by then an outright Police State. Interestingly, one bit of dialog sounds very much like a reverse of the Boston Tea Party in description, where goods from the U.S. are to be dumped into the London Harbor, and the American government is decried as corrupt and overbearing as was the King of England in 1776. The screenplay, by the way, was written by Larry and Andy Wachowski, better known for their stunning work in The Matrix series, which is perhaps why some popular Web depictions of V or related graphics such as the mask sometimes bear an uncanny ‘green’ resemblance to the tumbling Matrix symbols so frequently seen in those films.
V must wear a mask because of disfigurement, not unlike the Phantom of the Opera. And in many respects he is a bit superhuman because of non consensual genetic manipulations on prisoners by a foul government experiment gone terribly wrong. There is also a hint of his being mentally unhinged to a ‘useful degree’ as well, especially a fixation upon a particular date and a poetic line repeated in the film: “Remember, remember, the fifth of November, the gunpowder treason and plot. I know of no reason why the gunpowder treason should ever be forgot.” This is in turn based on a real historical plot on Nov. 5, 1605, to kill King James I and the full House of Parliament by blowing up the Bailey, a building of Parliament. It was called the gunpowder rebellion.
It was a foiled plot, undertaken by a lone revolutionary named Guy Fawkes, hoping to spark followers by his act. Like V, Fawkes was imprisoned and tortured, but unlike V, eventually executed. Actually, the plot was Jesuit orchestrated and tied to the fact that the government of England was at the time Protestant, and Queen Elizabeth I had been excommunicated, along with the rest of England’s non Catholics. This may be more than we need to know, but it is fascinating background, more so because V himself suffered horrifically on the same date (we know not exactly the future year), at which time he also manages to escape and be reborn as Anonymous. He then sets about establishing revenge for both himself and for Guy Fawkes… starting with blowing up the Bailey on the next available Nov. 5th he can manage.
This is followed by a subsequent invitation for the Sheeple to join with him on that same date one year hence — if they approve of and appreciate his efforts on their behalf. His efforts include much education on the lies and sins of their Fearless Leader, not to mention a lot of assassinations. As it happens, Anonymous is following a similar course of action, sans violence, as we shall see.
V is for Vendetta
Come now the NWO, and a real World version of V
The World depicted in the movie would seem to have come to pass in many respects in just four or five years since the film’s release. Some very specific events in the film are especially haunting to anyone who is fully informed on the criminal actions of the New World Order. No wonder then, perhaps, that someone should get the idea to reincarnate V in principle, theory, and in fact.
That would be, of course, the hacker group, which while rather small, appears to be globally based. Being a hacker is not conducive to making lots of friends and freely sharing risky ideas, especially when any use of such ideas means direct head-to-head confrontation with vast armies of sophisticated enemies — enemies who work tirelessly 24/7 and have an endless budget (e.g., government intelligence agencies). But the ideals expressed by V and Anonymous have indeed additionally infected millions of savvy Web users who have, for one reason or another, elected to employ the mask or some other symbol of V as their iconic avatar in various social media groups such as Facebook. Millions more take the mask into the street as political statement at protests, and thereby thwart FBI and Police cameras pending some abusive act to remove the mask by force.
They are everywhere, and even I am one who has elected such graphical trappings. It is not illegal, though repressive minds may move to make it so in their fear of an idea.
V is for Vendetta
A terrorist group with a Public Relations effort

One feels empowered by the Mask... it's own statement
Knowing the value of spreading the word, Anonymous seems fond of issuing videos to promote themselves. Like bin Laden videos, there are undoubtedly fakes claiming to be the real deal. But there are YouTube vids which promote and explain Anonymous which certainly seem to be created by them much in the same way as V employed himself in the film to educate the public and attempt to rally the people in support. Such works are compelling and intriguing, if not disturbing to watch. Out of fear the government or YouTube itself may eventually pull the works, I herewith outline one of the more key videos, detailing their hacking activities along the way:
V is for Vendetta
- It starts with a quotes from V “Each of us has our own path,” and adds “but we share the same goal: a Free Humanity.”
- A series of newscasts detail its hacking victories in Vendetta for government’s assault on WikiLeaks
- Hacks crashing VISA and MasterCard financial services in Vendetta for suspending WikiLeaks accounts
- Hacks of 51 government sites in Malaysia overnight in Vendetta for Internet censorship
- Hacks of HB Gary, a Federally contracted Web security firm in Vendetta for boasting it would catch Anonymous
- Hack of HB Gary posted thousands of confidential emails and forced resignation of their CEO
- Hacks of government Web sites in Egypt, Libya, and Tunisia during unrest there, literally powering the revolution
- Public statement “We are Anonymous. We are Legion, We do not forgive, We do not forget. Expect us.”
- They threaten attacks in Vendetta for mistreatment of Bradley Manning (WikiLeaks source of DOD documents)
- A news commentary describing Anonymous as ‘a new way to fight back… direct peaceful resistance.’
- Quotes from John Kennedy regarding undue intrusion by government into privacy and censorship
- A statement purpose for non violent restoration of the rule of law and fight the organized criminal class
- A PBS interview describing Anonymous methods as highly democratic in deciding what targets to hit, and why
- A quote from Sun Tzu’s Art of War, “Supreme excellence consists in breaking the enemy’s resistance without fighting.”
- A long list of Cabalistic NWO entities and projects (e.g., HAARP, Controlled Media, Globalist Groups) as enemy
- A Russian TV news clip warning all that governments can do to stop them is shut down the Internet
- … and the advice that when that happens, the people will rise up to shut down the government
- Closing quotes, “The resistance has begun,” and an introduction of a plan similar to V’s own…
V is for Vendetta
A Plan is hatched and you’re invited to play a role

That you in the back? No, its me. No, its the real Anonymous!
That year began June 15th and features it’s own Web site (whatistheplan.forumotion.com) where all who wish to participate may do so more actively as an actual member of, presumably, Anonymous. Going there, you are redirected (http://www.whatis-theplan.org/). Though considered an expert in privacy/security, I do not claim to be an expert in Web security. Yet I do know the redirect does not appear to offer anonymity and thus joining as invited may not be wise without additional precautions.
There are ways to visit ‘anonymously,’ such as afforded by first going to (natch) an anonymous surfing resource such as (natch) anonymous.org. Once using their free service, your Web activities cannot be tracked by the activities themselves. You can then only be tracked by having already been put under a full surveillance net. But the site clearly states that hacking and other illegal activities are not to be discussed, and thus one might be moved to presume that as long as they merely put about and keep their nose clean, they could care less that Big Brother is watching. Yet, under the Patriot Act, one cannot depend on government failing to define the act of registering at this site as ‘supporting terrorists’ in some way. Fascists love to persecute the soft targets of the unsuspecting as form of building their personal power within the system.
Else why would they murder poor Troy Davis? This one matter, alone, would drive me to consider being an Anonymous hacker, had I the skills. That is the power of a Martyr, it moves people to act and becomes its own backlash.
Regardless of the dangers in open surfing, I will myself join and report further as my opinion is molded by the experience. I’ve done battle with the FBI and the other agencies already, and I suspect they will not wish to target me further for reasons not useful to this article, though such detail might enamor the reader to me and result in more book sales. Relax — I’ll not abuse the reader thus.
Anonymous advises: “It is time we start becoming our own legends… If you feel something inside you pushing you toward acting on the plan… (join us.)” They describe a three phase plan. Phase II starts five months (November), they say, but neither it nor phase III are described. CBS is reporting they plan to shut Facebook down on Guy Fowkes day, as it is known in England (I would be happy to endure such an attack if it resulted in Facebook decoupling itself from the intelligence community — see my post on FascistBook) as described in a related article listed at page bottom, here.
Anonymous continues in exactly the strategic manner of V; “So if you see nothing, if the crimes of governments remain unknown to you, then we would suggest you allow this year to pass unmarked. But if you see what we see and you feel as we feel, and you would seek as we seek, then you too, are Anonymous. Stand beside us this year as we execute the plan, and together we shall give them a year which shall never be forgot. We are anonymous, united as one, divided by zero.”
If finally ends with one of the closing lines of the film, “Beneath this Mask… there is no flesh. Beneath this Mask is… an idea,” for which the punch line is, to underscore, “...and ideas are bullet proof.” That is true. You can kill a man for expressing an idea, but having had listeners, the idea lingers on long after his passing. Indeed, it is amplified in his martyrdom. That is one reason the Pen of Truth is mightier than the Sword of Lies. And when the one wielding the Pen is Anonymous, the Sword has nowhere to swing usefully, and it instead lashes forth in recklessly to cause collateral damage, and making martyrs of all in its path.
That speeds its undoing, for at noting the carnage, those nearby take warning, and consider the idea with more interest and, almost always, adopt it, and being quickly educated to the truth, and seeking to overpower the sword’s obvious evil. That is what Anonymous seeks to do. Unite us behind one idea… the idea that the day of tyrants and thieves in government is over. The New World Order is self-rendered as obsolete by their own greed, wanton murder, and their lashing out. They will extinguish themselves with just a little Anonymous help.
Are you that help?
V is for Vendetta
Target rich environment
I’d hate to be Anonymous and faced with trying to set priorities among all the possible deserving targets guilty of tyranny. They already have their own list of course, and I find it interesting (and appropriate) that amongst their list is the quasi-religious cult, Scientology, which has been linked to CIA and mind control projects in my research. But the problem of choosing targets as faced by a hacker group is just as huge for any legal form of targeting by activism, protest, or media efforts. My book, The Professional Paranoid Defensive Field Guide list over 1,000 CIA fronts, half of which have engaged in illegal mind control projects or other criminal enterprise, such as drug smuggling, illegal weapons sales, etc. It also has page after page listing illegal non consensual bioweapon and similar experiments on unwitting Americans, some not terribly dissimilar from those inflicted upon V as Guinea Pig.
My book set Fatal Rebirth details the truth behind decades of dark news events which dot the American historical landscape from 1947 forward, to include Sept. 11, which it predicted. I’ve personally gone head-to-head with a lot of these people and might reasonably and rightly claim I owe a Vendetta, for the personal cost has been high. But it is not about me. It is about the crimes against countless others, and whole nations, races, and classes of people. Why? Because the NWO is at its heart Satanic and thus hates all who have faith. Because the NWO is at its heart racist and hates non whites. Because the NWO at its heart is greed driven and hates any competition for ownership of each existent dollar. Because the NWO is at its heart fascist and hates freedom. Because the NWO hates Free WIll and life itself, and seeks death for all who have it.
As consultant to countless victims of electronic weapons of Political Control Technology and organized stalking, I’ve encountered groups, organizations, and agencies deserving of targeting for the grievous suffering they have caused thousands. They have relentlessly destroyed individual lives with nightmares well beyond anything ever depicted in any documentary or commercial film, and which defy mere verbal description. As investigative writer, even more such criminal power brokers have been discovered. And, of course, there are the major criminal events of our time; false flag operations, fraudulent financial debacles and bail outs, behind the scenes deals. These events are exposed endlessly, and yet they continue on and on and on. Not all these people and groups can be touched in a direct way by Anonymous hacking, but they can be touched by you and me by our activism. Anonymous proposes that such activism is empowered by the use of their Mask and name. Thus far, I tend to agree.
In Fatal Rebirth I offer my own advice which, I suppose, could easily be adapted by an Anonymous group. It talks about who the enemy is, what the rules of engagement should be with a focus on nonviolent opportunities as well as what they should be in any eventual armed confrontation (revolution) forced by the other side. I would hope that it would deter at least one person for making a tragic mistake which results in loss of life. Other elements of my advice may serve to be a kind of challenge to Anonymous: the creation of an easy to use and spread… and quite ultimate encryption tool to allow completely safe Web communications without fear of prying government eyes even being aware of encryption. The basic design construct is laid out, and awaits only one talented person to create and distribute it. But of course, such is already illegal under Dracos law.
There is even advice in The Professional Paranoid on how to react when dealing with arrest and detention, interrogation, etc.
V is for Vendetta
Being Anonymous is not child’s play

Arrested at Anonymous Protest
So one should not casually join or support anonymous unless confident they may actually do so Anonymously or otherwise have in place some useful level of immunity from investigative reprisals. And there is one other thing: one must ask if a given Anonymous contact, either from the hacker group or the greater public body of mask wearers is the real deal, or if they are a government operative seeking entrapment.
Half the people in jail for ‘terrorism’ would never have considered doing anything criminal except for being duped into it, or worse, framed by agent provocateurs pretending to be terrorists themselves. You can earn $100,000 cash setting someone up for arrest, so entrapment has become ‘big business‘ among the low lifes so employed. You can bet governments will freely use such methods to trap actual hackers through their less savvy supporters, even if they have to threaten or actually prosecute innocents along the way. So if you are going to be Anonymous, don’t forget your mask, and don’t tell anyone you have it.
Me? I’ve already gone on record as having a mask (albeit mere artwork at the moment). So the FBI, CIA, DIA, NSA, HSA, and any other initial set may freely seek me out if they wish. Just know that my insurance policies still remain in place, and that there will be Vendetta of another sort should their hand (sword) be too heavily applied. They’ve already targeted me both intensively and randomly over the decades, sometimes devastatingly. But that was before I got the goods on some of their matters. Since then we’ve coexisted fairly peacefully in the same cyberspace. I don’t mind that they are in the woodwork, and they don’t mind that I talk about them. The Mask shouldn’t change things that much. Having dared to write this, I guess we will soon enough see.
Yet there is also safety in numbers. They can start lists of people who visit a Web site and register. They can make lists of people on the Internet to use Anonymous symbology and phraseology. They can make all the lists they wish, and add to them as many names as they wish, and what I wish, is that they do so, endlessly. Because the more names there are on the lists, and the more lists they have, the more meaningless and useless they become. We outnumber them millions to one. No matter how big their budgets, they cannot target us all for investigation and surveillance, much less arrest, prosecute, and jail us. And to attempt any of it detracts from their resources and abilities to go after Anonymous, the hackers. Thus there is only one possible way to logically end this article:
We are legion. Expect us.
V is for Vendetta
YouTube Vids of interest
- What We Are Capable OF – This is Anonymous!
- Message from Anonymous: FBI Arrests
- Anonymous vs FBI, Anonymous Wins (Russian TV)
- Scientology is Afraid of Anonymous
- Scientologists handing out fake Anonymous flyers
- How to Join Anonymous (not)
Related articles
- Anonymous to take down Facebook on Guy Fawkes Day, who is Guy Fawkes? (cbsnews.com)
- How Time Warner Profits from the ‘Anonymous’ Hackers (newsfeed.time.com)
- FBI Arrests LulzSec and Anonymous Hackers (it.slashdot.org)
- ‘Anonymous’ hackers target BART, Fullerton police (latimesblogs.latimes.com)

































































































































REVOLUTION 2.0: Would Military back Constitutionalists or Socialist/Communist?
May 16
Posted by Author H. Michael Sweeney
Progressive leftist/fascists seem to be pressing for armed-conflict by trashing the 2nd Amendment (and other atrocities), confident they own the military’s loyalty. They don’t, but that simple answer is worthless, and for a long list of scary reasons.
by H. Michael Sweeney proparanoid.wordpress.com Facebook proparanoid.net
Dateline, March, 16, 2019, from the Olympic Peninsula, in the shadow of Califoregoshington
copyright © 2019, all rights reserved. Permission to repost hereby granted provided entire post with all links in tact, including this notice and byline, are included. Quote freely, links requested. Please comment any such repost or quote link to original posting.Reading, you will learn:
An important question
The question I have posed in my books since before the turn of the Century was this: what would happen if there is an attempt to take over the government by some form of coup, or to subvert/destroy the Constitution, such as seizure of guns from citizens or abandoning of National Sovereignty to the North American Union and the New World Order? The simple answer is a civil war, or what I term Revolution 2.0. There is both a right and duty of revolution, which reveals this truth: when a Country makes laws which fly in the face of logic, natural law, Constitutional law, and the laws of your lawfully chosen faith… and endanger the nation’s future and safety, it’s time to overthrow that government. That answer itself leads to many more questions, such as, what does it take to start a revolution, and how close are we to having one? But the most important one to participants in any such civil unrest, and which this post attempts to answer, is this:
which side will the military back in such a revolution, and how real is the possibility that the military might choose wrongly?
This post is an in-depth analysis, and as result, is about a 30 minute read with some important, unexpected, and revealing content… surprising even me, in fact… and I’ve been writing (in warning) on this topic for nearly two decades. If you are the sort who prefers sound bite news, just skip to the last section (In Summary), so you can simply confirm your belief bias without gaining any actual knowledge, be it agreeing with me, or discounting my findings in your ignorance of the facts which lead to that conclusion. That is your choice, to make, and your responsibility to choose. The same will be true of Revolution 2.0, where wrong choice based on ignorance could have serious consequences for you, your family, your country, and the World.
In seeking an answer, it should be noted that fascist-minded megalomaniacs have existed within all Militaries since the dawn of the institution; such personalities are naturally drawn to military and Police, and tend to rise in the ranks to positions of command. Regardless of any outer political views they wear on their sleeves, they tend to be fascist/police-statists in their thinking. More so, in America, perhaps, since 1947, when the DOD and CIA were founded, and the Military Industrial (and Intelligence) Complex was ‘invented.’ I have since added the liberal media cabal to the complex, resulting in the nick-name, MIIM. Every generation has them; people who find fascism more useful to their rise to power than they see in guarding your freedom and rights. There are several important illustrations of this in our history, and they reveal that some among US military leadership are well capable of siding with the wrong side… perhaps even engineering a reason for a conflict which might enable or excuse a coup.
Some call it a ‘Deep State mentality.’ I call it New World Order thinking.
Note: while this post is made in an America where, at the moment, the greatest threat capable of forcing civil conflict comes from progressive leftists… and while that group embodies and employs elements of the Deep State, Fascism, and globalist New World Order agenda… the Deep State, Fascism, and the New World Order has allies on both the left and right, almost always in the extremest versions, thereof — in almost EVERY country on the planet. You can’t tell your players without a program, and while some players stick out visibly on both sides, no one is publishing a program. Trust no establishment politician, international corporation, or anyone promoting extreme liberalism, socialism, communism, or extreme conservativism or nationalism. Ferris Bueller was right: “A person shouldn’t believe in isms. They should believe in themselves.”
We know, for instance, that the Military has worried about a possible not-so ‘civil war’ between the branches, between units within a branch, or individual soldiers within a unit, for some time. The rank and file of the military is by and large duly patriotic, mindful that they are not to obey unlawful orders, and understand and honors their Oaths to uphold and protect the Constitution. Yet they are also trained to obey without question. No military in the World can do both well, simultaneously, in times of conflict. Unlawful orders transpire, and are obeyed by most, and to disobey can be seriously punished, with any such incidents typically swept under the carpet. No one wants to be a vanquished martyr for a silenced and unheard cause.
The proof of military’s concern over this paradoxical is in the form of a questionnaire since referred to as the ’Shoot Americans Questionnaire,’ which has been given to various sampled units in various branches over the years. The good news is, not too many soldiers indicated they would obey orders to fire on Americans who, for instance in just one of several scenario questions, “refused to turn in their guns.” Other questions about use of deadly force related to other causes or issues of some concern, here, such as if the soldier would be willing to swear allegiance to United Nations Commanders, in deference to US law (it did not mention US law).
That questionnaire arose out of our second evidence, the Revolution in Military Affairs. RMA is the notion that as modern technology and political realities evolve, the military needs to adapt its war fighting policies, tactics, and capabilities to maximize efficiency and reduce chances of failures. Nothing wrong with that; all militaries do it. However, in the 70s and 80s, it literally became a field of think-tank study within the military, and frequently a common topic of discussion the the U.S. Army’s War College publication, Parameters. Within its pages, according to an article which appeared in the now defunct Washington D.C. Newspaper, The Spotlight, was an RMA based article which defined the ‘new face’ of America’s next new war. In fact, as I recall, the piece was titled ‘America’s New War,’ which was, ironically, exactly the propagandist terms media used to describe the war to liberate Kuwait.
In the quotes from the Parameters pages, the next new kind of warfare which needed to be planned for would be with “former military, militia, patriots, constitutionalists, and the poor and disenfranchised.” Excuse me? Since when are such the enemy of the State? When did the military start thinking the government is so far afield from righteousness that the military must plan for waring with upset citizens? Why should any who so think be allowed the command of force of arms? But that is not all. RMA also established something called the “21st Century Politico-Military Force Matrix,” which is largely the marriage of local law enforcement and military actions in a matrix of options for dealing with unruly civilian populations. Then there is MOOTW, “Miltary Operations Other Than War,” which provides clear operating strategies for interactions with citizens as potential combatants, including use of force of arms. It has also been called “The People’s War” by the military… for dealing with a civilian uprising.
Finally, there is the dramatic increase in development of psychological warfare technologies (mind control) and non-lethal weaponry… for military application against civilian populations. This is sometimes referred to as the Forth Epoch War, and I’ve written whole books on that, and one of them, The Professional Paranoid Defensive Field Guide, lists nearly 500 technical terms which represent the sum total of such weaponry, methodologies, and strategies. Among them are terms representing the construction and use of whole fake communities which can in no way be taken for anything but American towns, where training exercises regularly take place in door-to-door searches, traffic blockade/check point vehicle searches, and storming of buildings in SWAT-like operations.
If that were not enough, there have been actual training exercises in a long list of major and lesser American cities (i.e., LA, Houston, Chicago, etc.), much to the alarm of citizens who were NOT informed of the operations until AFTER they are completed… event though in some cases direct citizen confrontation, detainment, and questioning had been involved… often by Psychological Warfare units. At times, civil rights had been violated or citizen’s safety put at risk. This has been going on for more than four decades, and it has been getting more blatant and frequent every four years or so (an interesting characteristic, given election cycles).
Finding clues within previous coup attempts
The answer as to which side the military would take in such a scenario, is the same as would seem to worry the Pentagon, based on the questionnaire and their significant focus on civilian confrontation in RMA. I have always believed, that the inescapable answer is BOTH — resulting in rebellions amid the military, itself, both within and between branches, and within units. There have been two well-played-out but failed attempts at a military coup in America which serve as models of any such scenario, and these deserve some scrutiny. The first one was real (the 1933/34 Business Plot to depose President Roosevelt and establish a Fascist government), and served as a model for the second, which is where we will start for reasons beneficial to context of any Revolution 2.0. The most recent was a fictional depiction written by Political writer/researcher (Fletcher Knebel) and a former Editor of a major newspaper (Charles W. Bailey II). I’ll start there.
The movie was produced in the shadow and conspiratorial clouds leading to the assassination of John Kennedy, of which many people wondered if that ugly scar in America’s history was a plot involving some sort of political coup. Indeed, many clues uncovered over time pointed to military involvement. One was that the usual way the local National Guard military participation in Presidential visits was ordered to stand down, not unlike what happened in the Clinton/Obama Benghazi debacle resulting in the deaths of Marines and Embassy Officials, there. Another was the intrigue and conflict between Kennedy and the Joint Chiefs over the war in Vietnam, the Cuban Missile Crisis and the Bay of Pigs Invasion; the war hawks thought him soft on Communism.
Moreover, Kennedy had turned down the Joint Chiefs plan to fake a series of false-flag ‘Cuban terrorism’ events to justify an full out invasion and ousting of Castro, called Operation Northwoods… which also happens to be the blueprint visibly in play in the terror events leading to 9-11 attacks and the series of Middle East oil wars predicted in my book set, Fatal Rebirth — which predicted both the WTC downing by false-flag jetliner terrorism and the resulting oil wars in 1999, nearly two years before the attack. The Knebel/Bailey book itself was also written as a kind of harbinger of possible things to come based on many of the above difficulties between Kennedy and the Chiefs, and, ironically, Kennedy himself was quite fond of the book, likely recognizing aspects of the plot line to his own mirrored reality.
Sadly, he did not give it enough due, or he might have been able to foresee the deadly future which lay ahead for him… and perhaps, even forestall the use of Northwoods in our more recent history. The name Northwoods itself, by the way, was based on WWII Nazi operations of like false-flag nature… and the name Northwoods references Germanic translation, ‘Wald Im Norden’ (woods in/of the north) which also describes the invasion of Poland, which began WWII… the German Army swarmed into Poland from the forests to it’s North as did the air Blitzkrieg which overflew it. The fascists would, thereby, engulf the World in flame for a second time.
Note: Should the reader doubt any prime point within this post, they should hold final opinion until watching Seven Days in May. It will be well worth your time on an entertainment basis, alone. It is absolutely critical to understand the relationship of the various branches of service, how troop movement, material (weapons, munitions, supplies) and funding are manipulated within the context of the Department of Defense, and Presidential/Congressional oversight. The education, alone, is also motivation enough to watch the movie… as is the fact that much of the dialog is quite unhappily the same you are hearing on TV from commentators and politicians today; treason is afoot, for real, and as in the film as well as in 1933. But the key point in common with both the film/book and partially true in the Business Plot (there was no Air Force in ’33), was the absolute need to include the Marines and Air Force in key roles on one side or the other… and a means to ‘exclude’ non participants in the plot from interference as the coup unfolded.
Fascism brings us back to the Business Plot, which was undertaken by fascist business leaders of the most famous kind, including Bush, Harriman, Singer, DuPont, Hearst, Heinz, Mellon, Morgan, and others. But it was deemed that the plot could not succeed without a (then retired) Marine, one General Smedley Butler, who was the most popular military figure in the country, at the time. Butler was approached and ‘recruited’ to lead an uprising of unhappy Veterans who were owed money by the Government and unable to collect because of the Great Depression, which was also the source of unhappy ire of the businessmen. Butler’s role, if undertaken as intended, was to lead some 500,000 Veterans in ‘revolt,’ to seize the Capitol and depose or destroy the President, and hold Congress hostage, pending satisfactory reformation of a new government model.
Such a plot could not dare being risked unless assured that the military would both be unable to respond quickly enough to prevent the coup, and once in place, would not dare confront Butler and his civilian army (called the Bonus Army), or their fascist backers. Clearly, the backers of the plot must have had some private assurances from at least the Army, if not the Navy, that there would be no objection. The Chief of Staff (highest ranking General in command of the Army) in 1933 was Douglas MacArthur, who clearly did not get along well with Roosevelt, and was thought to be a fascist at heart. His counterpart in the Navy, Chief of Naval Operations, was Admiral William V. Pratt, who was very unhappy with the depression, as it had forced severe reduction of Naval forces, and threatened to merge the Coast Guard and the Navy, an idea which he opposed vehemently. The Commandant of the Marine Corps, Ben Herbard Fuller, also a JCS equivalent, was similarly suffering retrenchment because of the depression, and deeply respected Butler and MacArthur. To be clear, neither Fuller or Pratt have ever been accused of fascist leanings, as had been MacArthur, but a change in power favoring the military would not have hurt their wishes for a stronger military to command.
Thankfully, Smedley was a patriot who refuse the recruitment, and he instead exposed and thwarted the plot before it could get off the ground… though there was also a failed assassination attempt involving an Italian immigrant of fascist viewpoints in 1933. And, in the TV series, City of Angels (a TV spin-off of the Movie Chinatown, staring Wayne Rogers), the greater plot line in a three-part season opener (The November Plan) featured a foiled attempt to assassinate Roosevelt in a trip to California. That ‘fictional’ plot line was based in factual realities (subject to Hollywood license, of course), and did involve Smedley Butler as well as soldiers in uniform intent on betraying Roosevelt. The screenplay was by well respected researcher and writer of crime/detective drama, Stephen J. Cannell.
Now let us similarly disect the 1963 example…
The other key player in Seven Days of May was an Air Force General. Modern troop and material movement requires the coordinated support of the US Air Force. It was, in fact, this critical role which was the underlying plot mechanism of Seven Days in May, and quite critical to our understanding of what it would take for a modern coup to succeed. Therefore, with respect to Revolution 2.0, and Deep State influence over possible military opposition against Constitutionalists, those seeking to destroy the Constitution will need to include support of the Air Force, as well. The Army is less a concern, because the bulk of the standing Army is in deployment, and because each State’s National Guard is available to the Governors of each State in case of ‘civil unrest,’ which is what they would call the matter, seeking to hide the truth from the public: that any revolution was to save and restore Constitutional law against traitors.
If the State was run by liberals, the National Guards could be activated by the Governor against the ‘rebels,’ as they might also be termed for political propaganda expediency. If the State was conservative, the DOD could order the Guard to stand down (so as not to aid the ‘rebels’) or be activated at the Federal level to oppose the patriots. That could be true only if the majority of Joint Chiefs were on board with the unconstitutional effort underway. Stateside regular Army could potentially be directed to fill in where National Guard units or their Governor refused to stand down or comply with Federal activation. That would be an example of ‘civil war’ between elements within a given branch of the Military, and it is expected that any such use of troops, regardless if acting on Federal or gubernatorial orders, would experience conflict within their ranks, seriously inhibiting their efficiency.
In like manner, the Navy is largely out of the picture; the bulk of it is also on station around the World, and it is not well poised to impact ground actions within the borders of the US, short of coastal regions. In Seven Days of May, the Navy simply stood down. The same should be true of the Coast Guard, perhaps more so. Amid all of this, there is an added problem which provides a logical reason to stand down. Specifically, in such a coup, the military still needs to insure unfriendly actors such as China, N. Korea, Iran, or even Russia… did not take advantage of an America engaged in civil war. They might, for instance, choose to wax adventurous against allies, or even against US forces. Ergo, the Navy and much of the strategic Air Force would need to devote their attention to World affairs; standing down from any major role in the revolution would be tactically wise. And, in the next section, we will see ample reason for concern over their ability handle two conflicts simultaneously, both at home and abroad.
Perhaps we ought take a close look at Obama’s JCS, still now in place, and see what’s going on with them, in like-comparison.
What about today’s Joint Chiefs?
We must compare the two historical examples against today’s potential for replay. Looking back to 1933 and 1963, what about 2023, or some other current time frame? How does today’s situation compare, to then? Politically, there were fascist undercurrents mainly in the business community in 1933, where in 1963, the fascists were additionally present in the military industrial (and intelligence community) complex. They still exist to some degree in both sectors, today… but there is more afoot. Today, we see socialist/communist/anarchists and progressives on the Left using fascist tactics, including members of Congress. They are pitching socialism, but acting like fascists.
Today’s environment, then, is not so different from the past, and is perhaps worse, in final analysis… so what about the key military players at the Pentagon? How do they, and their resources, compare to the 1933 and 1963 scenarios?
In 1933, Butler was retired, the most likely candidate to orchestrate such a coup. Today, the pro liberal/progressive/fascist forces would likely be stirred to replay 1933 with the likes of Retired Army General Tommy Franks, who was Clinton’s right-hand military man… the man who ordered the flame throwing tank and commanded at Waco. As such, he enjoys free access to anyone in the Pentagon on at least an informal basis, and still holds a security clearance. As a Deep State operative, he could become the organizing and communications agent in any such modern-day plot. He also has many friends and contacts within the military industrial (MIIM) complex. He meets the 1933 model, as a recruitment target/tool — one I feel unlikely to adopt Butler’s patriotic response.
And the plot in 1963 required at least the bulk of the Joint Chiefs to participate, or be cowered into silence. The Joint Chiefs today consist of one four-star General to represent each branch of service, including someone to represent the Coast Guard and the National Guard, plus a Chairman and vice Chairman, for a total of seven top-echelon decision makers. Today, thanks to Obama, the JCS consists of two Marines and three US Air Force Generals to form a ‘heavy weighting’ of representation to the same two branches deemed important in 1963. I say thanks to Obama, because he conducted a purge of some 266 top-ranking military officers, and oversaw a rapid series of promotions necessary to put his personally approved people into the JCS chairs.
One Marine, General Joseph Dunford, Chairman of the Joint Chiefs, owes his position to that purge with a series of four rapid-paced promotions and appointment to the post by Obama. He is the most powerful man in the military, the counterpart to the 1963 role played by Burt Lancaster in film, though a Marine, instead of Air Force. The Vice Chairman, however, is Air Force (Paul J. Selva), also appointed by Obama with six rapid promotions. The Joint Chief of the Marines, General Robert Neller, had three promotions under Obama to his post, making two Marines in total.
The Joint Chief of the Air Force, General David L. Goldfein, enjoyed five promotions under Obama, and Air Force General Joseph L. Lengyel (making the third Air Force General) is JCS representing the National Guard. He had five promotions under Obama, while Admiral John M Richardson, Navy’s JCS, had only one promotion under Obama… it perhaps being understood in the 1963 model that the Navy is a non-critical player in a coup. In like relationship, the Commandant of the Coast Guard, Admiral Karl L Schultz, a de facto 8th JCS… appointed by President Trump, as was General Mark A Milley, the Army’s Joint Chief. Again, the Army is a conflicted player, both by virtue of deployments and National Guard complications, the one branch of the services most likely to be at war with itself in a coup-like or Revolution 2.0 scenario.
And, it would appear that Obama’s bevy of purge-replacement military officers have been quietly sabotaging the military in ways which make national defense abroad that much harder, perhaps shifting capabilities to a homeland conflict (I hate using that fascist term, ‘homeland’). In fact, difficult enough that the Air Force, by way of example, might not be able to provide any aid to patriots, or be a factor against them, at all, outside of material and troop transport. If today’s Air Force capabilities analysis is any clue, President Trump no longer has a full deck of military cards to play. A conflict at home and abroad would tax any Trump effort to support Constitutionalists, even were the DOD not under the control of Deep State plants.
Monkey wrench conspiracy theories
One tool the Air Force has which could prove extremely troublesome if aligned with treason, is Command Solo. There are 21 Command Solo aircraft, all based at Pennsylvania’s National Guard; specially modified C-130s capable of significant mind control capabilities via Political Control Technology (PCT). I find it troubling that such capabilities are National Guard, rather than Regular Army or Air Force, making it all that much easier to use against citizens. A single plane can impact a two-five State region, depending on State sizes. All of them fly regular training flights, unless in use overseas in a combat theater.
Human brainwaves for emotions operate at ultra low frequencies, and are roughly the same across population samples. If the desired emotional state of being is broadcast at signal strengths greater than that of the brain, the brain adopts them as its own (is entrained). By combining subliminals with emotional state manipulation, such as an abiding and overwhelming fear, Command Solo can impact tens or hundreds of thousands of people while in the air. In such use, it can fly 24/7 with required stops for refueling and crew changes, or in rotation with another Command Solo aircraft.
The training flights they fly involve preprogrammed mission tapes representing ‘harmless’ subliminals and EEG patterns to be used, but not even the operators on board, or their commanders, have any way of knowing what the content actually is (presumed to be ’empty’ of content.) So when they fly training missions, they could very well be telling Democrats to be outraged about everything, violent, etc., and no one would be the wiser, except the person who ordered the tapes to be made, and used, and the computer operator who created the tapes.
Watching your emotions and being alert for changes in that and any unexpected thought patterns which represent something contrary to your original belief structures, is your only clue the plane is being used. The average person won’t question. The strong-willed and alert, can detect, and can resist, if strong minded and inwardly alert. The other clue is seeing the aircraft in the air. A good spotting scope, rifle scope, or telephoto lens can easily recognize if a suspected plane is a C-130 with the Command Solo configuration. Command Solo, and other PCT are well covered in terms of detection and defense in my book, MC Realities.
Another wildcard conspiracy theory is “UN Intervention,” and I here draw upon the ten years of research documented in my book set, Fatal Rebirth. There have largely been two waves or versions of this theory, and both are based in demonstrable facts nonetheless consistently denied by both US military and the UN, itself. The first took hold back the 1990’s and a bit before, with origins earlier than that, tied to far-right thinkers and political forces, such as retired General and US Senator, Barry Goldwater, who foresaw the New World Order’s rise through the U.N. In the 90’s, large numbers of people were seeing and reporting long trainloads of flatbed cars loaded with white U.N. military vehicles, as well as similar on river barges and tractor-trailer units, sometimes in convoys on American highways. Other reports talked of holding areas with hundreds of units parked in neat rows, typically surrounded by military quality fencing and guard stations manned by ‘Men in unmarked black uniforms.’
Most of the 43 United Nations ‘Biospheres’ in some cases rendered off-limits to citizens and subject to UN control as part of Agenda 21.
This was also the same time frame when people hiking in select wilderness areas were encountering armed soldiers, also in unmarked black uniforms who were apparently conducting some kind of drill or operation. Invariably, they were said to have been speaking both English and a foreign language of some sort, and ordering civilians away at gunpoint, advising they had entered a military compound. Many of these reports of vehicles and soldiers made the newspapers in one form or another, sometimes with pictures, but the military and the UN denied any validity. Some of these events and UN vehicle stockpiles were indeed in ‘wilderness’ areas tied to the 43 United Nations Biospheres regions, which is its own Agenda 21 conspiracy topic.
The U.N., for instance, has officially insisted it has no men or vehicles in North America, and does not use the types of vehicles being spotted. Most were identifiable as American WWII era, or more modern US Army vehicles, and many more were of Soviet manufacture. And, at the time, large numbers of Soviet military equipment, including helicopters, trucks, tanks, rocket batteries, and even specialized units such as CBRN (Chemical Biological, Radiological, and Nuclear) decontamination trucks were being brought into the country by someone, sighted variously in transit or storage in either original Soviet or UN colors… no unit or national markings lest it simply be ‘UN.’
Let’s take just one very interesting and well documented case (my 1990 research, plus the Spotlight in the same timeframe), to drive the point home. It involves Soviet ARS-14 biological/chemical warfare trucks shipped from West Germany through the firm Beesh Merkator to Gulfport, MS, then by barge to Scranton, Iowa to a company, Airmar Resources, Corp, operated by Lt. Col. A. R. Koval Sr., USAF, retired. Koval told the Spotlight that the units were purchased for Germany and destined for UN forces in Europe after refurbishing, contrary to UN statements it does not, by policy, use Soviet equipment of any kind.
These units have been in the U.S. for nearly a decade. US made, mfg says they are for use overseas, but UN denies using US vehicles or having inventory in America.
The investigation continued, revealing that from Scranton, they were transited to various destinations in America through firms named Newway and Scranton Manufacturing. The later firm, contrary to Airmar Resources claims, said the trucks were being converted to ‘garbage trucks,’ but the EPA said it would be impossible for those vehicles to be made to meet vehicle standards. Scranton responded that they were destined for European markets, but one has to ask about the cost effectiveness of buying and shipping trucks from Europe to America for modifications, and then shipping them back to Europe. Scranton at the time indeed offered a line of new garbage trucks, but none were of Soviet origin. All were, like the Soviet units, painted white, of course. A nifty cover story that almost works, if you don’t look too closely.
And, as stated, the modified trucks were tracked to US destinations, not Europe. One, in fact, spotted in California on a flatbed truck, was leaking noxious smelling liquids which made the witness sweat profusely and ill to his stomach. Marked with a sign “Quarantined by US Department of Agriculture,” the fluid was being drained into a trench by men in protective clothing. Both Newway and Scranton Manufacturing are alternate names for a small but troubled firm associated with Bede Jet Corp, the maker of small fiberglass civilian jets (build-it-yourself kits) like the one James Bond (Roger Moore) used to attack Castro’s air base in the opening sequence of Octopussy. Newway, in fact, also made Bede-designed, Honda-powered, fully enclosed two-seat motorcycle-car kits, also of fiberglass.
The more recent wave of UN concerns is fare easier to demonstrate (the images above, for instance), and involves UN intervention officially in place. It comes from the Obama Administration’s invitation for the UN sponsored program referenced as the Strong Cities Network. Based on selling fear of terrorism, in particular, ‘home-grown extremists,’ the program calls for United Nations help to member Cities in the Network. The help goes directly to and influences the Police Departments within the network, as well as city management. On the surface, as sold to citizens in the fear mongering, it sounds like a way to gain some expertise in combating terrorism. But that is a deliberately false narrative.
Interesting: Obama is said to be slated to be next Secretary General of the UN…
Conspiracy theorists early-on tried to warn people it was a dreadful mistake and a trap. Now, even non theorists are proving the conspiracy is no theory, and far more serious than even early theorists, had thought. It turns out that the Strong City Network acts as its own Law Enforcement Agency, and is empowered to actually govern member cities. Cities which join the network essentially are subject to UN Rule of law, rather than the US Constitution. Currently, New York, Atlanta, Denver, and Minneapolis are members, and a push is underway for Boston, west-coast cities, and elsewhere, to follow suit. In the event of a civil war/revolution scenario, the framework and base structure for a UN interference will already be in place. All they need to do, is to make the announcement, and fly in their people and equipment to make it stick. Because it was blessed by Obama, it would be difficult for anyone to object, including the military — unless and until President Trump or some other President revokes the program and so orders, at least.
There is a final ‘conspiracy’ matter which counters the other two, in impact: a secret military within the military. When researching my book, Fatal Rebirth, I was contacted by an active Officer of high rank in the US Military who knew of my work through my appearance on Coast to Coast with George Noory. He advised that there was, within each branch of the service, a secret group of Officers of some importance, and positioned across the full spectrum of unit function (i.e., Intelligence, combat, support, communications, etc.) Their purpose was to be prepared for, on watch for, and to activate should there be any unlawful (unconstitutional) effort to effect a coup or military takeover. He in fact invited me to become a member, as they did have associations with civilian counterparts they deemed useful. Accepting, they said, I would then have access to information he assured me would be valuable to my book.
However, as the covert security aspects of membership were extremely hight, I did not feel I could manage them… and, I was unwilling to accept responsibility for receipt of classified military or governmental information, which would risk being charged with a crime, if caught. But I was pleased that such men were in place to help insure that unlawful orders against citizens would meet with both covert and overt resistance. I reference this covert patriot group as the ‘Turtle,’ (as in, Revenge of the Turtle, America’s first submarine war vessel used in the Revolutionary war. The Turtle is, and like the Turtle sub, is invisible and hard to find, until it bites.
In summary
We see then, that the makeup of the current JCS team engineered by Obama, almost exclusively, is quite weighted to Marine and Air Force, suspiciously Deep State tied, and more than mirrors the key aspects of both the 1933 and 1963 scenarios. We see that was an Obama (Democrat) arrangement through a purge, as part of setting up his Deep State. We see that Obama has set the stage for potential UN interference and further partnerships or concessions to authority from the next progressive President to take power. We see that the military and its MIIM Complex, the business sector, and the political spectrum is well laced with both fascist and liberal/progressive politics which border on fascism, and employ fascist tactics. We see that Deep State and establishment politicians collectively ‘hate Trump’ regardless of party affiliation, and in many cases, would rather see the country come to harm than to allow him to continue in office. We see now why the progressives think they own the military, which could in fact be poised for a last-ditch full-blown military coup take over if Trump wins, again.
The final conclusion is, all the pieces are in place, and while the leftists do own the military at the top, they do not, top-down. How then, can we say we are not ripe for a coup, or Revolution 2.0, should the progressives come to power, again — for they still believe they do own the military? Assuming the left does not reform itself into a more logical and viable political entity akin to the old Democratic party of the 1950’s and 60’s, if they cannot be kept from ever again obtaining power, armed conflict must indeed be our future. I foresee no other possible outcome.
Returning to the original question, then, the military is well poised at the command level (JCS) to participate against patriots, but not necessarily well positioned to do so without difficulties, rank and file. We see the Navy and Coast Guard are weak players in such a scenario. We see the Marines, despite any leadership which might be opposed to Patriots, are perhaps the most likely to themselves, at rank and file levels, join with patriots, and refuse unlawful orders. We also see the Turtle groups would do likewise. We see army has its own confusions and situational roadblocks to a unified and obedient command against patriots, tied to the complex relationship with National Guard units. And, we also see the Air force, along with Navy and to a degree, Marines, must be somewhat aloof to such conflict, in order to prevent third-actor States from taking advantage of an American military distracted at home.
I therefore do not see the relatively small numbers of US armed forces, if arrayed against the large number of 2nd Amendment defenders and others of the “former military, militia, patriots, constitutionalists, and the poor and disenfranchised,” being sufficiently strong enough to prevent a patriot victory. That, however, is based on additional assumptions not yet in evidence or proven true: a) that mind control technology will be used effectively; b) that progressives will prove to be better armed and organized than expected; c) that other groups might join in, such as illegal immigrants and Muslims seeing the conflict as a way to advance their own causes, or real or fake UN troops; d) that China (by this means/scenario) or Mexico, perhaps even Canada, might elect to enter into the fray; e) that some other totally unexpected plot element is afoot and impossible to evaluate.
Therefore, if when at bat with an unfriendly pitcher on the Mound, be ready to smack the ball as hard as you can… but also… “Watch out for in your ear,” with a deliberately wild and hurtful pitch (apologies for stealing Ray Liotta’s line).
If you agree… there is yet one more unanswered question: what will the rules of engagement be for patriots, when they will face and odd mix in the battlefield (cities and countryside)? It will be a strange mix of citizens + law enforcement + military on both sides, and in many cases, there will be times when it will not be known which side a combatant force is on. How should such a war be prosecuted? For the answer to that… and in foreseeing this time coming more than 20 years ago… I wrote the book set, Fatal Rebirth. The answers are there, and have been, all along.
Share this:
Posted in Abuse of Power, Conspiracy, Government, military, News Events, Political Commentary, Uncategorized
Leave a comment
Tags: Constitution, military, military coup, patriots, resolution, takeover, UN troops, UN warehouse, unconstitutional